Java for High Performance Computing Java RMI and












































- Slides: 85

Java for High Performance Computing Java RMI and RMI-Based Approaches for HPC 1

Remote Method Invocation u Java RMI is a mechanism that allows a Java program running on one computer to apply a method to an object living on a different computer. – RMI is an implementation of the Distributed Object programming model—similar to CORBA, but simpler and specialized to the Java language. u The syntax of the remote method invocation looks like an ordinary Java method invocation. – The remote method call can be passed arguments computed in the context of the local machine. It can return arbitrary values computed in the context of the remote machine. The RMI runtime system transparently communicates all data required. – In some ways Java RMI is more general than CORBA—it can exploit Java features like object serialization and dynamic class loading to provide more complete object-oriented semantics. 2

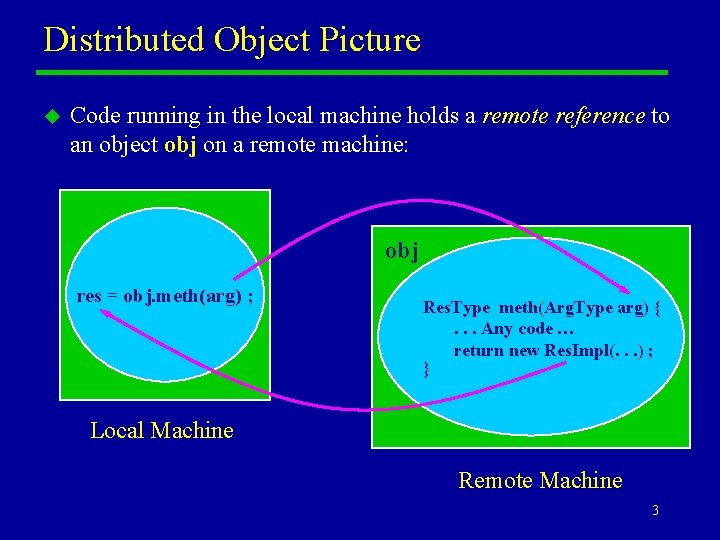
Distributed Object Picture u Code running in the local machine holds a remote reference to an object obj on a remote machine: obj res = obj. meth(arg) ; Res. Type meth(Arg. Type arg) {. . . Any code … return new Res. Impl(. . . ) ; } Local Machine Remote Machine 3

Java RMI References u Java RMI, Troy Bryan Downing, IDG books, 1998. u “Getting Started Using RMI”, and other documents, at: http: //java. sun. com/products/jdk/rmi/ u Java RMI Lectures in “Applications of IT” course, run at Florida State University, 2001: http: //aspen. ucs. indiana. edu/it 1 spring 01/ 4

A Simple Use of RMI 5

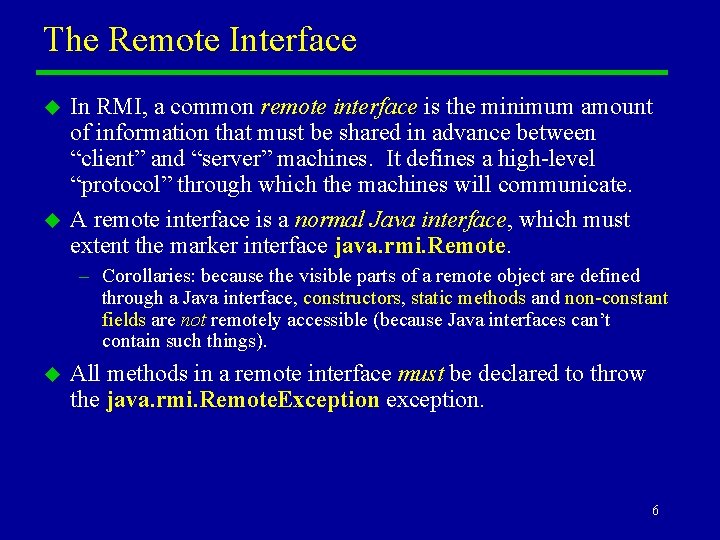
The Remote Interface u u In RMI, a common remote interface is the minimum amount of information that must be shared in advance between “client” and “server” machines. It defines a high-level “protocol” through which the machines will communicate. A remote interface is a normal Java interface, which must extent the marker interface java. rmi. Remote. – Corollaries: because the visible parts of a remote object are defined through a Java interface, constructors, static methods and non-constant fields are not remotely accessible (because Java interfaces can’t contain such things). u All methods in a remote interface must be declared to throw the java. rmi. Remote. Exception exception. 6

A Simple Example u A file Message. Writer. java contains the interface definition: import java. rmi. * ; public interface Message. Writer extends Remote { } u void write. Message(String s) throws Remote. Exception ; This interface defines a single remote method, write. Message(). 7

java. rmi. Remote u u The interface java. rmi. Remote is a marker interface. It declares no methods or fields; however, extending it tells the RMI system to treat the interface concerned as a remote interface. – In particular we will see that the rmic compiler generates extra code for classes that implement remote interfaces. This code allows their methods to be called remotely. 8

java. rmi. Remote. Exception u u Requiring all remote methods be declared to throw Remote. Exception was a philosophical choice by the designers of RMI makes remote invocations look syntactically like local invocation. In practice, though, it cannot defend from problems unique to distributed computing—unexpected failure of the network or remote machine. Forcing the programmer to handle remote exceptions helps to encourage thinking about how these partial failures should be dealt with. See the influential essay: “A Note on Distributed Computing” by Waldo et al, republished in The Jini Specification: http: //java. sun. com/docs/books/jini 9

The Remote Object u u A remote object is an instance of a class that implements a remote interface. Most often this class also extends the library class java. rmi. server. Unicast. Remote. Object. This class includes a constructor that exports the object to the RMI system when it is created, thus making the object visible to the outside world. Usually you will not have to deal with this class explicitly— your remote object classes just have to extend it. One fairly common convention is to name the class of the remote object after the name of the remote interface it implements, but append “Impl” to the end. 10

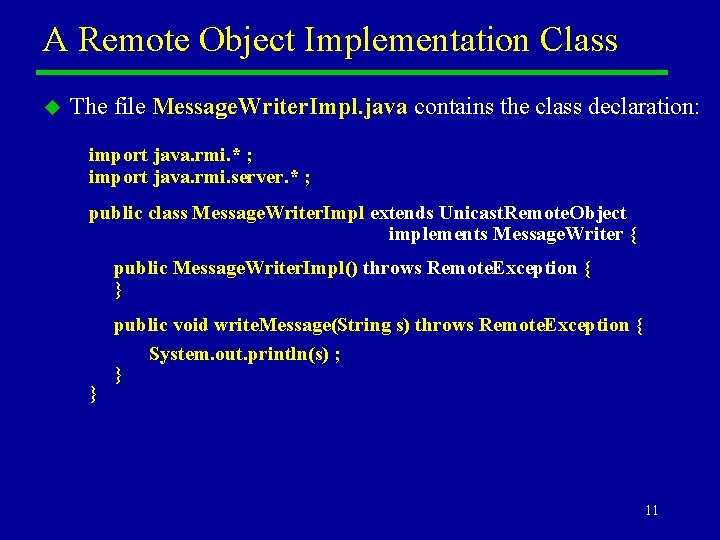
A Remote Object Implementation Class u The file Message. Writer. Impl. java contains the class declaration: import java. rmi. * ; import java. rmi. server. * ; public class Message. Writer. Impl extends Unicast. Remote. Object implements Message. Writer { public Message. Writer. Impl() throws Remote. Exception { } } public void write. Message(String s) throws Remote. Exception { System. out. println(s) ; } 11

Compiling the Remote Object Class u To compile classes that implement Remote, you must use the rmic compiler. The reasons will be discussed later. For example: sirah$ rmic Message. Writer. Impl 12

Client and Server Programs u u u We have completed the Java files for the remote object class itself, but we still need the actual client and server programs that use this class. In general there are some pieces of administrivia one has to deal with—publishing class files and installing security managers. We initially make the simplifying assumption that both client and server have copies of all class files for Message. Writer (e. g. , they may share access through shared NFS directories). – Then “publishing class files” is not an issue, and we also don’t need a security manager, because all code is “local”, and therefore trusted. 13

A Server Program u We assume the file Hello. Server. java contains the class declaration: import java. rmi. * ; public class Hello. Server { public static void main(String [] args) throws Exception { Message. Writer server = new Message. Writer. Impl() ; } } Naming. rebind(“messageservice”, server) ; 14

Remarks u This program does two things: – It creates a remote object with local name server. – It publishes a remote reference to that object with external name “Message. Writer”. u The call to Naming. rebind() places a reference to server in an RMI registry running on the local host (i. e. , the host where the Hello. Server program is run). u Client programs can obtain a reference to the remote object by looking it up in this registry. 15

A Client Program u We assume the file Hello. Client. java contains the class declaration: import java. rmi. * ; public class Hello. Client { public static void main(String [] args) throws Exception { Message. Writer server = (Message. Writer) Naming. lookup( “rmi: //sirah. csit. fsu. edu/messageservice”) ; } } server. write. Message(“Hello, other world”) ; 16

Remarks u u u Again the program does two things: – It looks up a reference to a remote object with external name “Message. Writer”, and stores the returned reference with local name server. – Finally (!), it invokes the remote method, write. Message(), on server. The call to Naming. lookup() searches in a remote RMI registry. Its argument is a URL, with protocol tag “rmi”. This example assumes the remote object lives on the host “sirah”, and has been registered in the default RMI registry (which happens to listen on port 1099) on that machine. 17

Compiling and Running the Example u Compile Hello. Server and Hello. Client on their respective hosts, e. g. : sirah$ javac Hello. Server merlot$ javac Hello. Client u Either ensure client and server share the current directory, or copy all files with names of the form Message. Writer *. class to the client’s current directory. 18

Running Hello. Client/Hello. Server 19

The Mechanics of Remote Method Invocation 20

Is RMI a Language Extension? u u Invocation of a method on a remote object reproduces the “look and feel” of local invocation very well. But the internal mechanics of remote invocation are much more complex than local invocation: – Arguments—which may be objects of arbitrary complexity—are somehow collected together into messages suitable for shipping across the Internet. – Results (or exceptions) are similarly shipped back. u Perhaps surprisingly, RMI involves no modification to the Java language, compiler, or virtual machine. – The illusion of remote invocation is achieved by clever libraries, plus one relatively simple “post-processor” tool (rmic). 21

Exchanging Remote References u u A powerful feature of distributed object models like RMI is that references to other remote objects can be passed as arguments to, and returned as results from, remote methods. Starting with one remote object reference (presumably obtained from an RMI registry) a client can, for example, obtain references to additional remote objects—returned by methods on the first one. 22

Example: a Printer Registry u Suppose we are on a LAN and we need to get a Java driver for one of several available printers: public interface Printer extends Remote { void print(String document) throws Remote. Exception ; } public interface Printer. Hub extends Remote { Printer get. Printer(int dpi, boolean is. Color) throws Remote. Exception ; } u u u A client might initially obtain a Printer. Hub reference from the RMI registry. The remote object contains some table of printers on the network. An individual Printerface is returned to the client, according to specifications given in get. Printer(). Jini takes an approach similar to this. 23

Remote References have Interface Type u This is a powerful feature, but there is one interesting restriction: – If a particular argument or result of a remote method itself implements Remote, the type appearing in the method declaration must be a remote interface. – The declared type of an RMI argument or result cannot be a remote implementation class. – At the “receiving end” this reference cannot be cast it to the implementation class of the remote object. A Class. Cast. Exception will occur if you try. 24

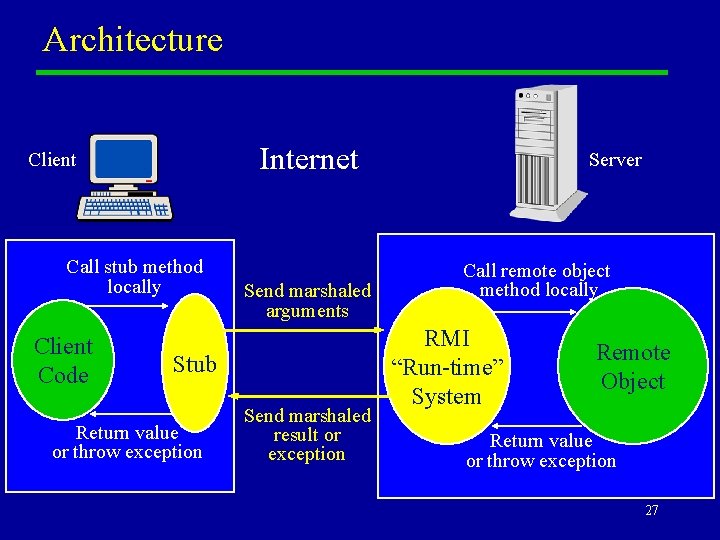
Stubs u What this tells us is that “remote references” are not literally Java references to objects in other virtual machines. u In fact they are Java references to local objects that happen to implement the same remote interfaces as the remote objects concerned. u The local Java object referenced is an instance of a stub class. 25

Some Important Parts of RMI u Stubs. – Each remote object class has an associated stub class, which implements the same remote interfaces. An instance of the stub class is needed on each client. Client-side remote invocations are “actually” local invocations on the stub class. u Serialization. – Arguments and results have to be “marshaled”—converted to a representation that can be sent over the Net. In general this is a highly non-trivial transformation for Java objects. Serialization is also used for distributing stubs. u The Server-side “Run-time System”. – This is responsible for listening for invocation requests on suitable IP ports, and dispatching them to the proper, locally resident, remote object. 26

Architecture Internet Client Call stub method locally Client Code Send marshaled arguments Stub Return value or throw exception Send marshaled result or exception Server Call remote object method locally RMI “Run-time” System Remote Object Return value or throw exception 27

The Role of rmic u u The only “compiler” technology peculiar to RMI is the rmic stub generator. The input to rmic is a remote implementation class, compiled in the normal way with javac (for example). The stub generator outputs a new class that implements the same remote interfaces as the input class. The methods of the new class contain code to send arguments to, and receive results from, a remote object, whose Internet address is stored in the stub instance. 28

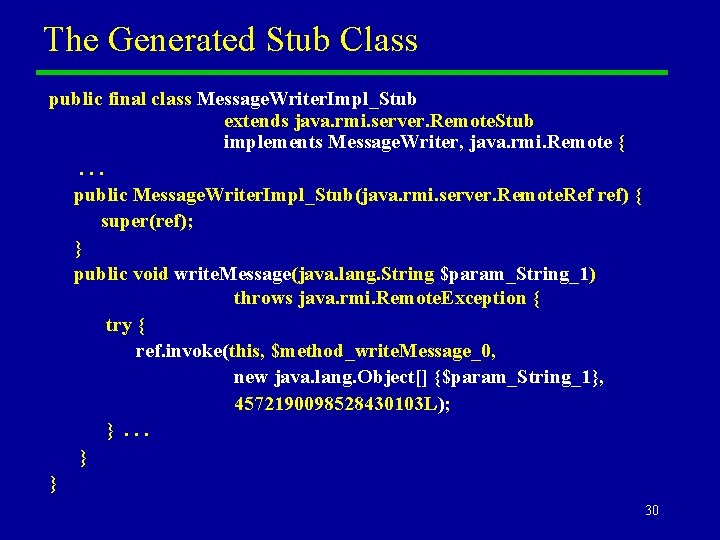
Example Operation of rmic u An earlier example of a remote implementation class: public class Message. Writer. Impl extends Unicast. Remote. Object implements Message. Writer {. . . public void write. Message(String s) throws Remote. Exception {. . . } } u We issue the command: rmic –keep Message. Writer. Impl – The flag –keep causes the intermediate Java source to be retained. 29

The Generated Stub Class public final class Message. Writer. Impl_Stub extends java. rmi. server. Remote. Stub implements Message. Writer, java. rmi. Remote {. . . public Message. Writer. Impl_Stub(java. rmi. server. Remote. Ref ref) { super(ref); } public void write. Message(java. lang. String $param_String_1) throws java. rmi. Remote. Exception { try { ref. invoke(this, $method_write. Message_0, new java. lang. Object[] {$param_String_1}, 4572190098528430103 L); }. . . } } 30

Remarks on the Stub Class u The stub class includes an inherited field ref, of type Remote. Ref. – Essentially the stub class is just a wrapper for this remote reference. u Remote methods are dispatched through the invoke() method on ref. – This is passed an array of Objects holding the original arguments (in general it also returns an Object). – It is also passed arguments to identify the particular method to be invoked on the server. u Essentially the stub wrapper is providing compile-time type safety. The actual work is done in library classes that don’t know the compile-time type in advance. 31

Marshalling of Arguments u Objects passed as arguments to invoke() must be marshaled for transmission over the network. u Java has a general framework for converting objects (and groups of objects) to an external representation that can later be read back into an arbitrary JVM. u This framework is Object Serialization. 32

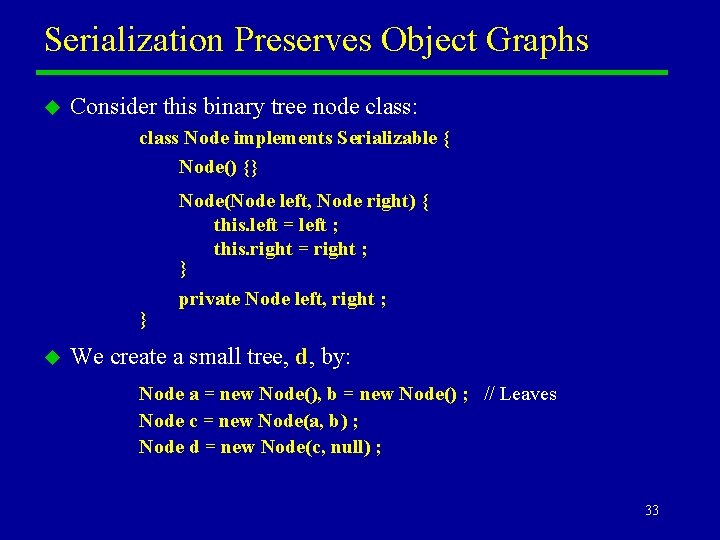
Serialization Preserves Object Graphs u Consider this binary tree node class: class Node implements Serializable { Node() {} Node(Node left, Node right) { this. left = left ; this. right = right ; } } u private Node left, right ; We create a small tree, d, by: Node a = new Node(), b = new Node() ; // Leaves Node c = new Node(a, b) ; Node d = new Node(c, null) ; 33

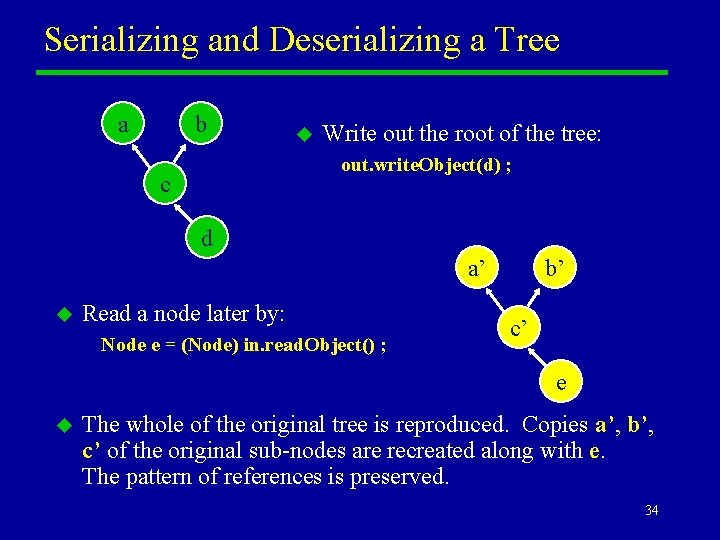
Serializing and Deserializing a Tree a b u Write out the root of the tree: out. write. Object(d) ; c d a’ u Read a node later by: Node e = (Node) in. read. Object() ; b’ c’ e u The whole of the original tree is reproduced. Copies a’, b’, c’ of the original sub-nodes are recreated along with e. The pattern of references is preserved. 34

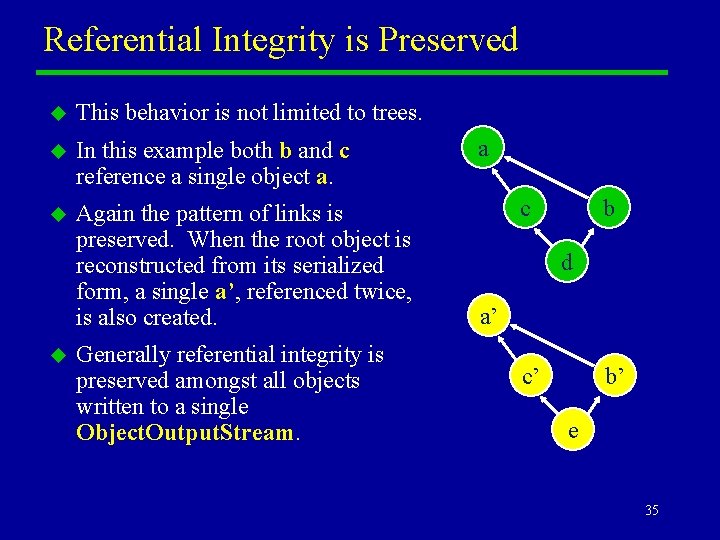
Referential Integrity is Preserved u This behavior is not limited to trees. u In this example both b and c reference a single object a. u Again the pattern of links is preserved. When the root object is reconstructed from its serialized form, a single a’, referenced twice, is also created. u Generally referential integrity is preserved amongst all objects written to a single Object. Output. Stream. a c b d a’ c’ b’ e 35

The Serializable Interface u Serializable is another marker interface. An object’s class must implement Serializable if it is to be passed to write. Object() (the library method that actually does serialization). If it doesn’t, a Not. Serializable. Exception will be thrown. – Arrays are serializable if their elements are. – Many (most? ) of the utility classes in the standard Java library are serializable. – For example container classes as complex as Hash. Maps can readily be serialized (assuming the user data stored in them is serializable), and thus passed as arguments and returned as results of RMI methods. 36

Argument Passing in RMI: Summary u In general any object-valued argument or result of a remote method must either implement Remote or Serializable. u If the argument or result implements Remote, it is effectively passed by (remote) reference. u If it implements Serializable, it is passed by serialization and copying. Referential integrity is preserved within the limits of the arguments of a single invocation, as described above. 37

Mechanics of RMI: Summary u u In principle most of the features that have been discussed in this section are hidden inside the implementation of RMI. In an ideal world you would not have to know about them. In practice, to successfully deploy an RMI-based application, you will probably need to at least be aware of some fundamental issues. You need to be aware of the existence of stub objects, and the basic working of object serialization. You should be aware that references to remote objects are normally produced by creating a stub object on the server, then passing this stub to registry and clients in serialized form. 38

Dynamic Class Loading 39

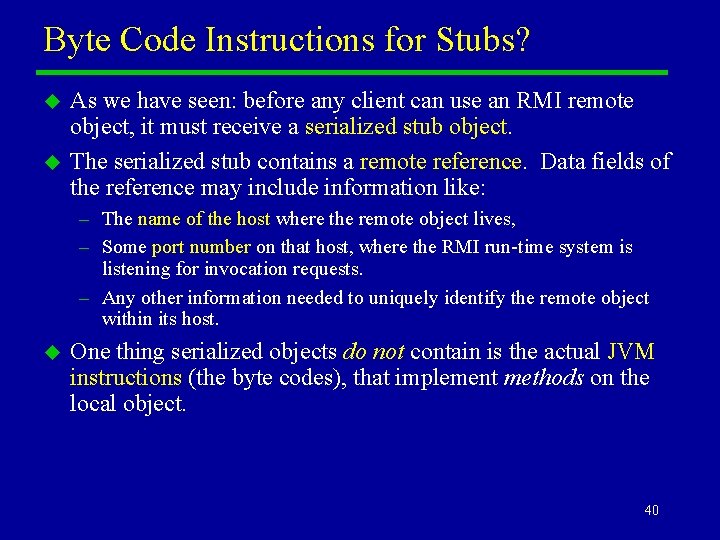
Byte Code Instructions for Stubs? u u As we have seen: before any client can use an RMI remote object, it must receive a serialized stub object. The serialized stub contains a remote reference. Data fields of the reference may include information like: – The name of the host where the remote object lives, – Some port number on that host, where the RMI run-time system is listening for invocation requests. – Any other information needed to uniquely identify the remote object within its host. u One thing serialized objects do not contain is the actual JVM instructions (the byte codes), that implement methods on the local object. 40

Serialization Only Saves the Data u In general the Java serialization process stores all data fields from the original object. u It does not store any representation of the code associated with the methods in the object’s class. u When an object is deserialized (e. g. on some client), the client JVM must have some way of loading a class file that does contain this information. – If it cannot find a suitable class file, the deserialization process will fail. You will see a java. rmi. Unmarshal. Exception thrown, with a nested java. lang. Class. Not. Found. Exception. – When you are doing development using RMI, you will probably see this exception a lot! 41

Copying Stub Class Files u In RMI, there at least two ways to get the class files to the client. u The straightforward approach is to manually copy class files for all stub classes to the client: either put them in the current directory on the client, or in some directory on the client’s CLASSPATH. – This approach is reliable, easy to understand, and perhaps the best approach for initial experiments with RMI. u But eventually you may find this too limiting. One of the benefits of the OO approach is supposed to be that the user code (here the client) doesn’t need to know the exact implementation class in advance—only the interface. But stubs are associated with the implementation class. 42

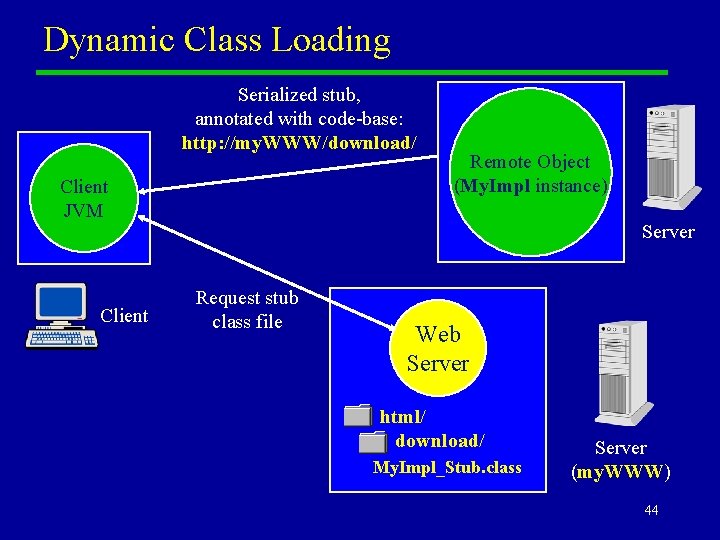
Dynamic Class Loading u u u A more general approach is to publish implementation class files that may be needed by clients on a Web Server. Although the serialized representation of an object does not contain the actual information from the class file, the representation can be annotated with a URL. This specifies a Web Server directory from which the class file can be downloaded. When the object is deserialized, the client Java Virtual Machine transparently downloads the byte codes from the Web Server specified in the annotation. On the client side, this process happens automatically. 43

Dynamic Class Loading Serialized stub, annotated with code-base: http: //my. WWW/download/ Client JVM Client Remote Object (My. Impl instance) Server Request stub class file Web Server html/ download/ My. Impl_Stub. class Server (my. WWW) 44

Remarks u u In simple examples, the serialized stub will probably be obtained through an RMI registry running on the server (the same server where the remote object is running). The two servers—the server where the remote object is running, and the Web Server publishing the class files—may, of course, be physically the same machine. 45

The java. rmi. server. codebase Property u u We need a way to cause serialized object representations to be annotated with suitably chosen URLs. In principle this is straightforward. We set a property called java. rmi. server. codebase in the JVM where the stub (or serialized object in general) originates. The value of this property is a code-base URL. The RMI serialization classes read the code-base property, and embed the URL they find there in the serialized representation of arguments or results. – Unless this JVM itself downloaded the class file for the object from a Web server, in which case they embed the URL from which the class was originally loaded. 46

Setting the Code-base u For example, our original Hello. Server example might be run as follows: java –Djava. rmi. server. codebase=http: //sirah. csit. fsu. edu/users/dbc/ Hello. Server u This sets the java. rmi. server. codebase property to: http: //sirah. csit. fsu. edu/users/dbc/ This URL gets embedded in serialization streams created by the Hello. Server program. u If an object is subsequently recreated by deserialization in a different JVM (and that JVM cannot find a local copy of the associated class file) it will automatically request it from the Web server sirah, looking in the document directory users/dbc/. 47

Security Managers u u u There is one more thing we need to worry about. Before a Java application is allowed to download code dynamically, a suitable security manager must be set. This means a security policy must also be defined. In general this is a complicated topic. We won’t go into any detail: just give a recipe you can follow. 48

Setting the Security Manager u In an RMI application, if no security manager is set, stubs and classes can only be loaded from the local CLASSPATH. u To enable dynamic loading, issue the command: System. set. Security. Manager(new RMISecurity. Manager()) ; at the start of the program. u You should do this in any application that may have to download code—in the simple examples considered so far this means RMI clients that need to download stubs. u This isn’t the end of the story. You also have to define a new property: the java. security. policy property. – In simple cases this property is needed for clients, whereas java. rmi. server. codebase is needed for servers. 49

Defining a Security Policy u The simplest security policy you can define is a plain text file with contents: grant { permission java. security. All. Permission “”, “” ; }; u This policy allows downloaded code to do essentially anything the current user has privileges to do: – Read, write and delete arbitrary files; open, read and write to arbitrary Internet sockets; execute arbitrary UNIX/Windows commands on the local machine, etc. – It is a dangerous policy if there is any chance you may download code from untrustworthy sources (e. g. the Web). – For now you can use this policy, but please avoid dynamically loading code you cannot trust! 50

The java. security. policy Property u If the text file containing our security policy is called (for example) policy. all, the original Hello. Client example might now be run as follows: java –Djava. security. policy=policy. all Hello. Client u Alternatively this property can be set inside the program using System. set. Property(). 51

Using Dynamic Loading: Summary u In principle, modifying your RMI application to allow dynamic loading of stub classes is now straightforward: – Install the stub classes in a Web Server document directory. – Set the java. rmi. server. codebase property for the server application, to reference that Web Server directory. – Create a security policy file on the client. – Set the java. security. policy property for the client application. – Set a security manager in the client. u This also works for any classes (not just stubs) whose serialized form may be communicated via remote method calls. – You just need to reinterpret “server” and “client” application according to the direction the serialized object moves—as “source” and “destination” application. 52

Remarks u u It probably seems a lot of work—just to avoid manually copying one stub file from the server to the client. But this facility for dynamically down-loading class files has more far-reaching implications. It is applicable not only to stubs, but any object passed through a remote method call, where the class of the actual object received is a specialization (subclass or implementation class) of the type declared in the remote interface. One can argue this kind of polymorphism is at the heart of object-oriented programming. In this sense dynamic class loading is a prerequisite for doing true object-oriented programming with remote objects. 53

Other Features of RMI 54

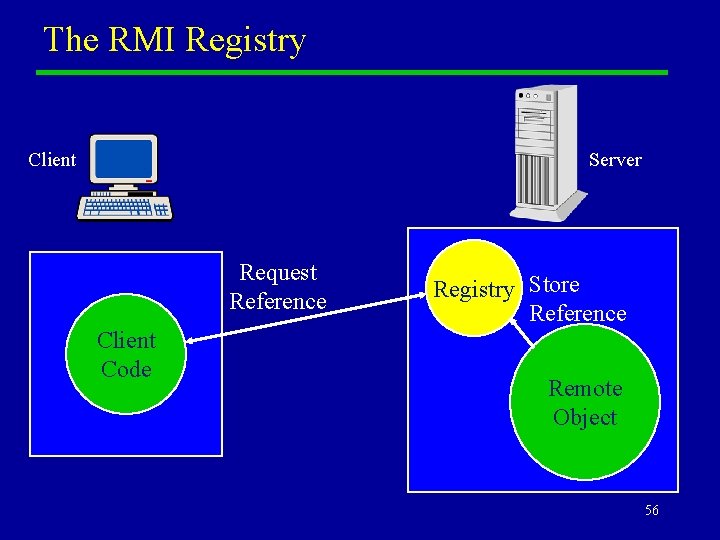
The RMI Registry u u The RMI registry is a process that normally runs on the server. At first sight the registry seems to have a privileged role in RMI. Actually it is “just another” remote object. 55

The RMI Registry Client Server Request Reference Client Code Registry Store Reference Remote Object 56

Example: Jini u u u Sun’s Jini is a framework for spontaneous discovery of services that exist in a LAN (for example), and for reliable federation of these services. It makes essential (and creative) use of aspects of RMI like dynamic class loading and call-backs (discussed next). The Jini lookup services generalize the RMI registry. In Jini an arbitrary proxy object is installed in the lookup services. – The proxy is not restricted to be an RMI stub. It can be any serializable object, typically including remote references to an actual server object. u The code for the proxy is downloaded dynamically by the client, on lookup. 57

Example: Call-backs u A client can itself provide a remote interface, by creating its own remote object. u It can then pass a reference to itself to a server. Now the server can initiate communication by calling remote methods on the client. These are sometimes called call-backs. u In general we see that RMI allows one to create complex “webs” of interacting objects. 58

Synchronization u u Where multiple clients may interact with the same object (this means most useful services), one needs to pay attention to issues of interference. Remote invocations from different clients may execute concurrently—in different threads—in the server program’s JVM. It can be a good idea to declare the implementation of remote methods (in the definition of the implementation class) with the synchronized modifier. This avoids the dangerous situation in which methods are being invoked simultaneously on a remote object by several clients. – Other clients will have to wait until the currently executing method has completed—they will be serviced in turn. – But now you must be wary of possible deadlocks. 59

Garbage Collection u u For Java, an important issue is garbage collection, which automatically deallocates memory for local objects. Remote objects are also garbage collected as follows: – A remote reference layer on the server keeps a reference count for each locally held remote object implementation. – A remote reference layer on the client notifies the server when its locally held references to the object are no longer in use. – When all references from all clients have gone (i. e. when the reference count is zero), the server object is garbage collected. u But what if a client fails to notify the server? – A client with a remote reference must periodically renew a lease with the run-time system on the server. – If the client holding the reference exits prematurely (without notifying the server) it will also stop renewing its leases. If a lease is not renewed on time, the server assumes the client has died, and the reference count is decremented anyway. 60

Java RMI Performance 61

RMI for Parallel Programming u Some research groups developed software to support use of RMI for parallel programming on non-shared-memory platforms. – Typically aimed at clusters with high-speed (e. g. Myrinet) interconnect. u Well-known projects are Java. Party from Karlsruhe and Manta from Vrije Universiteit (Amsterdam). – Java. Party takes a more “purist” approach, in that it targets standard Java Virtual Machines. – Manta is based on a native compiler for the Java language. 62

The Problem u u u From the outset, the main problem these approaches must tackle is the slowness of standard RMI. The following benchmark results are quite old, but the basic message probably hasn’t changed dramatically. Taken from More Efficient Serialization and RMI for Java Michael Phillipsen, Benard Haumacher, and Christian Nester ACM 1999 Java Grande Conference 63

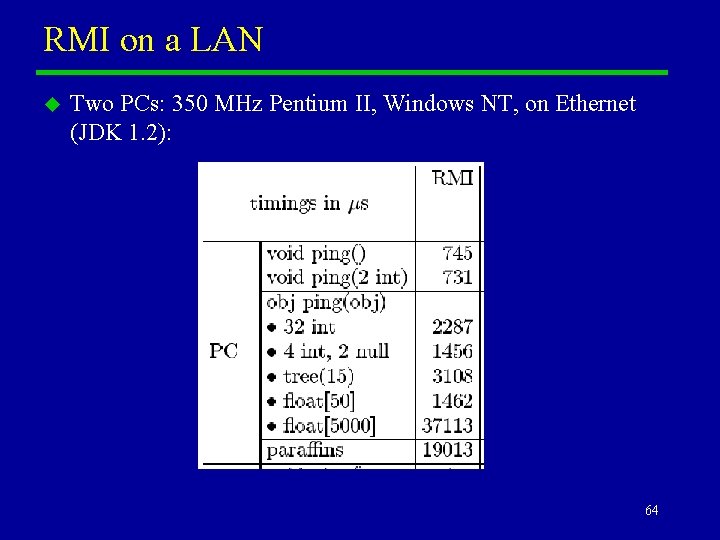
RMI on a LAN u Two PCs: 350 MHz Pentium II, Windows NT, on Ethernet (JDK 1. 2): 64

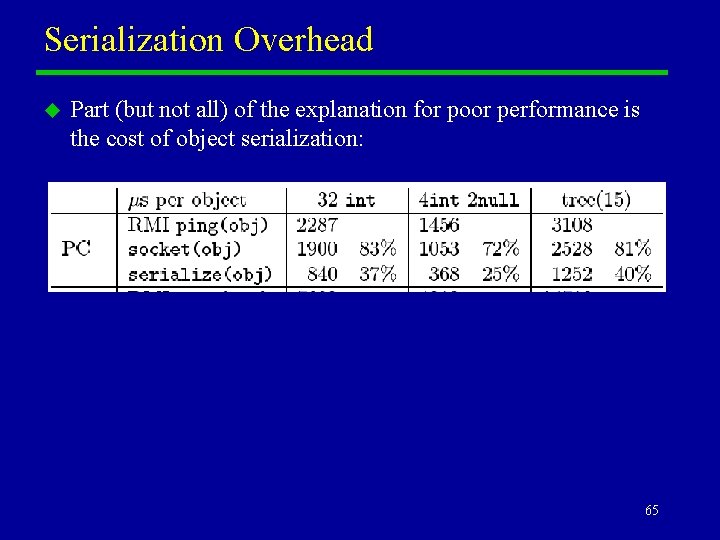
Serialization Overhead u Part (but not all) of the explanation for poor performance is the cost of object serialization: 65

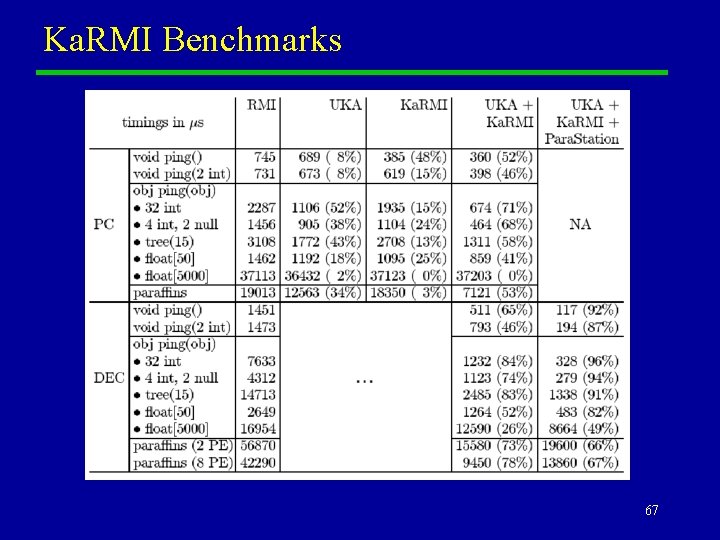
Ka. RMI u u As part of the Java. Party project, researchers from Karlsruhe produced Ka. RMI, a “drop-in replacement” for Sun’s RMI. Ka. RMI provides an optimized version of object serialization (UKA-Serialization), and also improves the implementation of the rest of the RMI stack. – Greatly reduces the number of temporary objects created for a remote method invocation. – Eliminates some JNI calls. – Reduces number of hash-tables used. u It also supports fast network hardware without going through TCP/IP. – Myrinet 66

Ka. RMI Benchmarks 67

Remarks u u On Ethernet, Ka. RMI saves around 50% the overhead of standard RMI (according to these timings). The DEC results were obtained with a particularly ancient JDK, and are certainly out of date. The reason for presenting them is that they illustrate the ability of Ka. RMI to exploit Myrinet-based communication technology like Para. Station. – For HPC on clusters, this is probably the most important point! u As emphasized you can use Ka. RMI “standalone”, but it is especially natural to use it in the framework of Java. Party. – Speed of UKA-serialization dependent on existence of write. Object()/write. External() methods, which are generated automatically for Java. Party remote classes. u In any case Ka. RMI can be downloaded as part of the Java. Party release, from: http: //www. ipd. uka. de/Java. Party/ 68

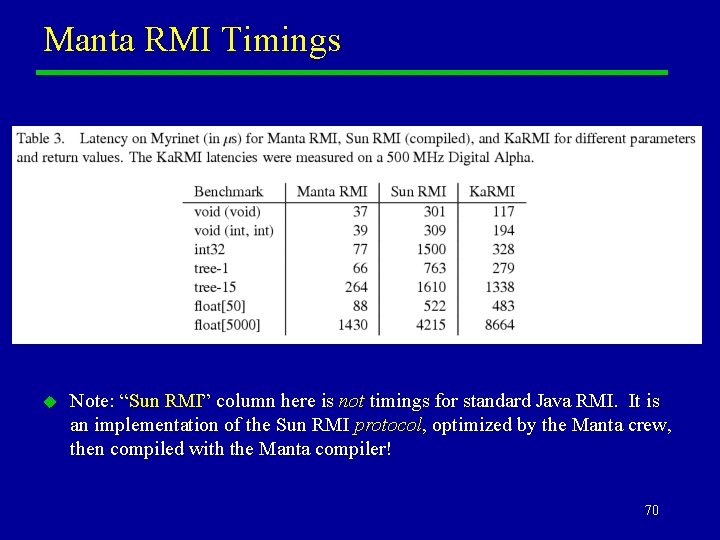
Manta u Because Manta is a compiled language, a great deal of optimization of RMI and serialization can be done at compile time. This results in dramatically faster RMI implementation. – A possible downside is that you must buy into the compiled Manta mindset. This is rather different from the way most of the Java world does things. u Information here is taken from “Efficient Java RMI for Parallel Programming”, Jason Maassen, Rob van Nieuwpoort, Ronald Veldema, Henri Bal, Thilo Kielmann, Ceriel Jacobs, Rutger Hofman, 2000. 69

Manta RMI Timings u Note: “Sun RMI” column here is not timings for standard Java RMI. It is an implementation of the Sun RMI protocol, optimized by the Manta crew, then compiled with the Manta compiler! 70

Remarks u u As advertised, these latencies are dramatically smaller than for other RMI implementations, and in a good ball-park for HPC applications. The Manta software is available for download from: http: //www. cs. vu. nl/manta/ – Note it is provided in source form only, for compilation on a Linux platform. 71

Special Topic: Java. Party 72

Transparent Remote Objects u The authors of Java. Party—Transparent Remote Objects in Java Michael Philippsen and Matthias Zenger observed that Java doesn’t provide a straightforward mechanism for parallel programming on distributed memory machines, like clusters. u Although method invocations on remote objects was considered a natural Java approach, the Java. Party team note that Java RMI has significant programming overheads. – Writing separate interface and implementation code, initiating server objects on multiple hosts, registering them and looking them up, etc. u Java. Party effectively specializes RMI to cluster-like environments, and provides a preprocessor and run-time environment to do much of this work automatically. 73

The remote keyword u u Java. Party makes one innocent-looking change to the Java language—a new modifier is allowed in class declarations: remote. The Java. Party runtime will automatically allocate a remote object (any instance of a remote class) to a host in the cluster environment. – Typically different to the host that create the object. u u Any method called on a remote object is implicitly a remote method invocation. So there is no need to initiate servers manually, or register remote objects: they are created and referenced in a program exactly like ordinary Java objects. – This doesn’t necessarily mean they behave exactly like ordinary Java objects, see later discussion. 74

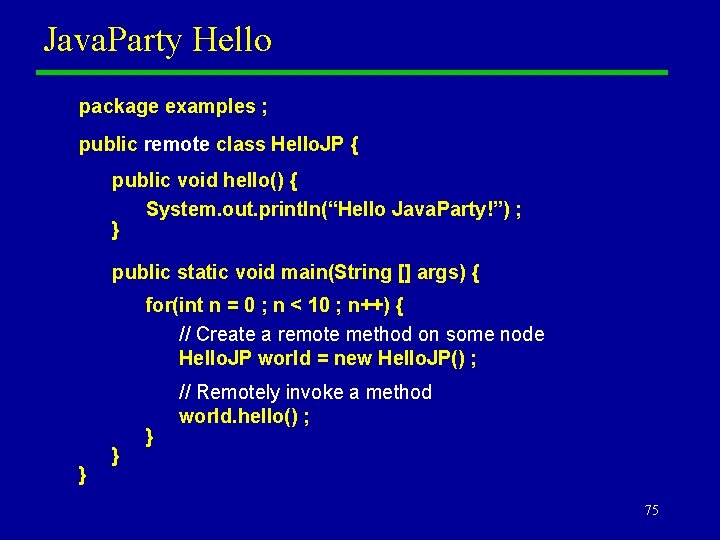
Java. Party Hello package examples ; public remote class Hello. JP { public void hello() { System. out. println(“Hello Java. Party!”) ; } public static void main(String [] args) { for(int n = 0 ; n < 10 ; n++) { // Create a remote method on some node Hello. JP world = new Hello. JP() ; } } } // Remotely invoke a method world. hello() ; 75

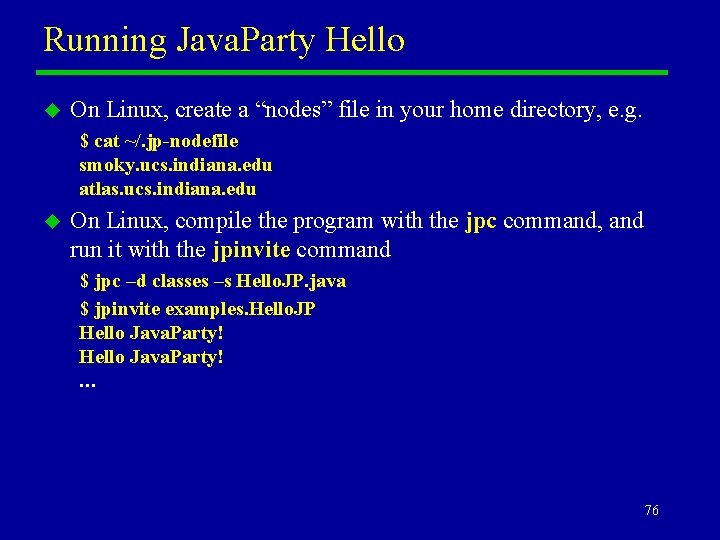
Running Java. Party Hello u On Linux, create a “nodes” file in your home directory, e. g. $ cat ~/. jp-nodefile smoky. ucs. indiana. edu atlas. ucs. indiana. edu u On Linux, compile the program with the jpc command, and run it with the jpinvite command $ jpc –d classes –s Hello. JP. java $ jpinvite examples. Hello. JP Hello Java. Party! … 76

Remarks u u Compared with using RMI, this is impressively straightforward. Note, however, that it is specialized to a cluster-like environment. For example it assumes a shared file system. – This simplifies various problems that arise in the distributed setting. For example the complexities of dynamic class loading from Web servers aren’t required (or supported) in Java. Party. u u To run on a LAN under Linux, ensure ssh login to remote nodes is possible without password, ensure no intervening firewalls. In my experience the classes/ folder should be added to the CLASSPATH as an absolute file name, in your ~/. bashrc or equivalent. 77

Semantics of Java. Party u u Java. Party does more than just put syntactic sugar around the RMI model of remote objects. It doesn’t require remote operations to be specified through a Java interface. – It is classes that are remote. u Remote methods are not required to throw Remote. Exception. – According to Waldo et al (cited earlier) we can interpret this as meaning Java. Party is not exactly for distributed programming. u For these and other reasons, Java. Party can support several kinds of remote operations that simple RMI does not, e. g. : – Static methods can be called remotely. – Fields (instance and static) of remote classes can be accessed remotely, using just the ordinary Java syntax for field access. – Recent versions of Java. Party support a sophisticated feature called transparent distributed threads. u However all these things come at some cost, and there remain some significant differences between the semantics of a Java. Party program and the corresponding Java program (without the remote keywords). 78

Translation Issues u A Java. Party program is effectively translated to a Java program that uses standard RMI. Because of the semantics just discussed, the translation scheme is quite complex, e. g: – Remote method calls all need wrappers that handle Remote. Exceptions that are presumably never thrown. – Every remote class gives rise to several classes in the translated code, e. g. the interface and implementation class for a remote “class object” that handles static method, and acts as kind of a factory for remote instances. – Accessor methods (get/put) must be defined for fields of remote classes, and the translator must convert uses of these fields into calls to the accessor methods (need special accessors for array elements). u The current modern Java. Party compiler is an adapted version of the gj compiler (apparently not open source? ) 79

Some Features u u A significant difference between the semantics of a Java program and a similar-looking Java. Party program is that generally arguments and results of methods on remote objects are passed by value (because they reduce to RMI calls). Because access to remote fields goes through implicit accessors, which are remote methods, this feature also affects access to fields. As an odd case, suppose a is an object from a class with an array-valued field arr, then: int [] local. Arr = a. arr ; local. Arr [0] = 23 ; u If a is a Java object, this modifies the field a. arr. If a is a Java. Party remote object, it just modifies a copy—leaves the field unchanged. Sometimes Java. Party gets described as a distributed shared memory model. – This may be slightly misleading—if you naively wrote an Open. MP-style dataparallel program in Java. Party, it would probably be very inefficient because every access to a shared array would go through remote get/set methods. 80

Carta. Blanca u Carta. Blanca , from Los Alomos National Lab, is a general purpose nonlinear solver environment for physics computations on non-linear grids. “Parallel Operation of Carta. Blanca on Shared and Distributed Memory Computers” N. Padial-Collins, W. Vander. Heyden, D. Zhang, E. Dendy, D. Livescu. 2002 ACM Java Grande/ISCOPE conference. u u u It employs an object-oriented component design, and is pure Java. Parallel versions are based on partitioned meshes, and run either in multithreaded mode on SMPs, or on networks using Java. Party. Here we are interested in the latter. These results are a Linux cluster of Compaq DL 360 nodes, each with two 1 GHz pentiums. Network is Gig. E. – The following results are from a pre-publication version of the paper cited, and should presumably be taken as indicative only. 81

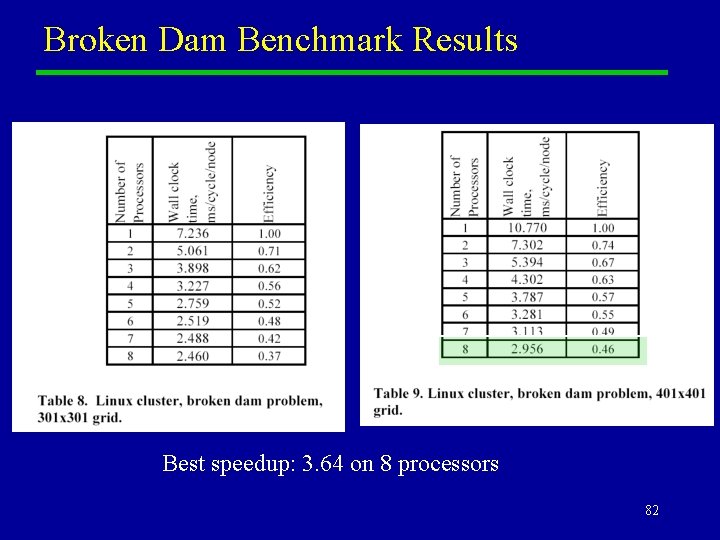
Broken Dam Benchmark Results Best speedup: 3. 64 on 8 processors 82

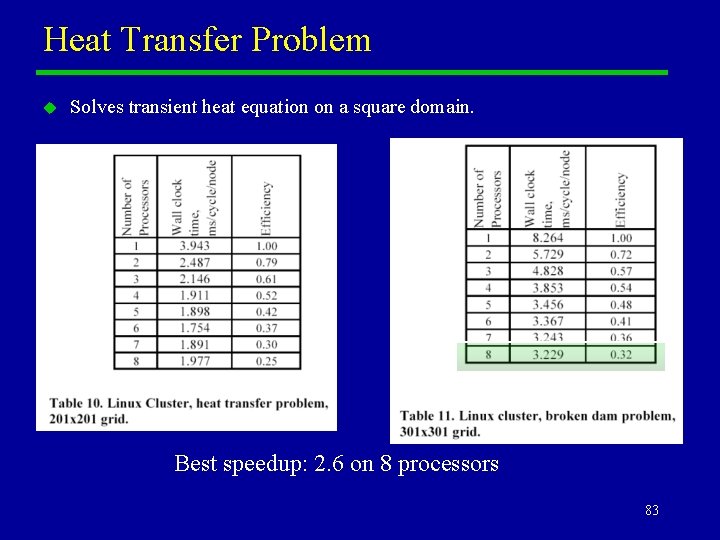
Heat Transfer Problem u Solves transient heat equation on a square domain. Best speedup: 2. 6 on 8 processors 83

Remarks u Operation of the program described as follows: – The main method spawns threads for each mesh partition. » In the RMI/Java. Party implementation, these threads will invoke a remote method to distributed the work. – The threads communicate through separate (remote) objects—calling getter and setter methods on these objects. – There is a “reduction” communication object for operations like summing data across all threads. – A boundary communication object is used to update edge nodes shared by adjacent partitions. u Source is available from www. lanl. gov/projects/Carta. Blanca/overview. html 84

Java. Party: Summary u If you are writing parallel programs for a cluster, writing the program using Java. Party will typically be much more convenient than using Java. RMI directly: – – u No need to create separate interface and implementations, and use rmic. No need to publish class files on Web servers. No need to explicitly use RMI registry. Don’t have to handle Remote. Exception. On the other hand, Java. Party only automates the distribution of code. It does not provide much help with parallelization. You still have to “manually” divide up the work, start Java threads, think about communication. 85