January 2013 doc IEEE 802 11 130133 r





- Slides: 17

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Higher Layer Setup Ad-hoc Summary Date: 2013 -01 -15 Authors: Name Affiliations Address Phone email Hitoshi MORIOKA Allied Telesis R&D Center 2 -14 -38 Tenjin, Chuo-ku, Fukuoka 810 -0001 JAPAN +81 -92 -771 -7630 hmorioka@root-hq. com George Cherian Qualcomm 5775 Morehouse Dr, San Diego, CA, USA +1 858 651 6645 gcherian@qti. qualcomm. com Rene Nehru Hiroki Submission Slide 1 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Abstract This document is the summary of higher layer setup adhoc held on Tue. PM 2, Wed. PM 1 and Thu. AM 1. Submission Slide 2 Hitoshi Morioka, Allied Telesis R&D Center

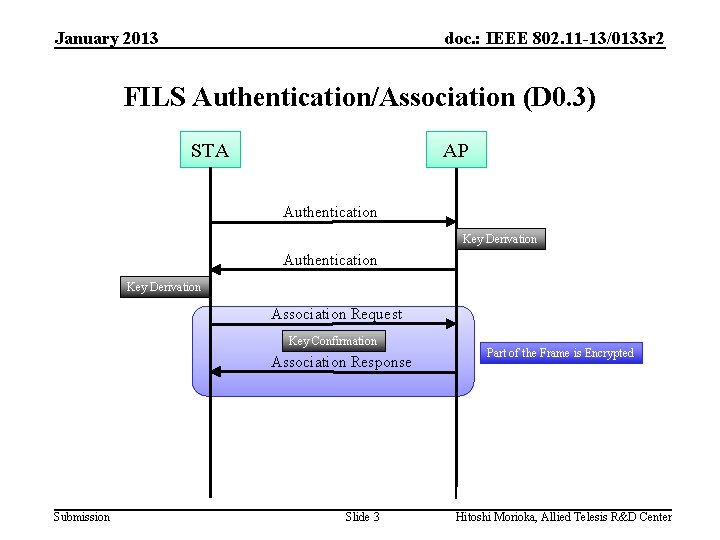
January 2013 doc. : IEEE 802. 11 -13/0133 r 2 FILS Authentication/Association (D 0. 3) STA AP Authentication Key Derivation Association Request Key Confirmation Association Response Submission Slide 3 Part of the Frame is Encrypted Hitoshi Morioka, Allied Telesis R&D Center

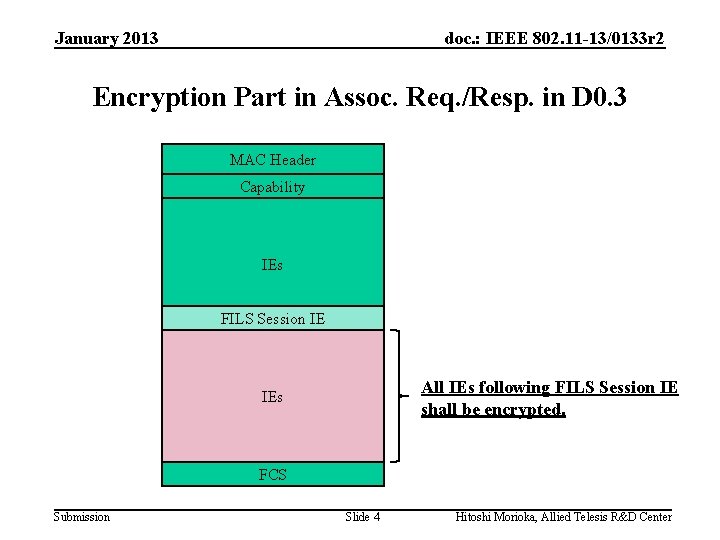
January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Encryption Part in Assoc. Req. /Resp. in D 0. 3 MAC Header Capability IEs FILS Session IE All IEs following FILS Session IE shall be encrypted. IEs FCS Submission Slide 4 Hitoshi Morioka, Allied Telesis R&D Center

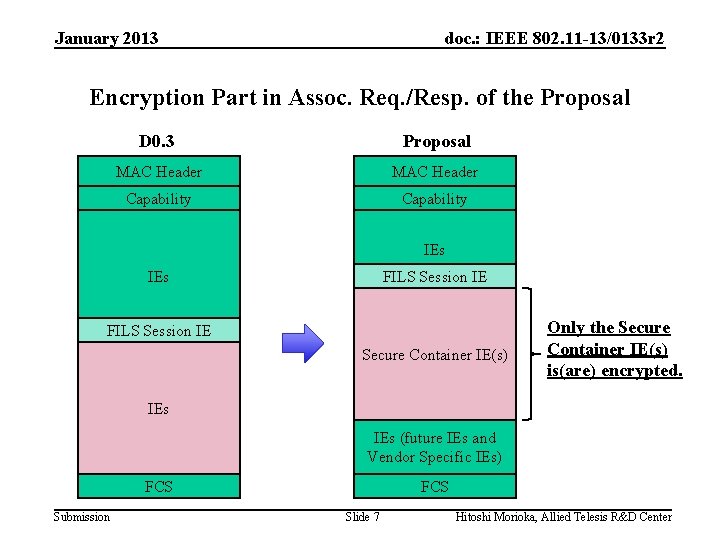
doc. : IEEE 802. 11 -13/0133 r 2 Problem Description • Draft 0. 2, section 11. 2. 4 says: – “The input ciphertext shall be the contents of the Association Response frame that follow the FILS Session element” • What does it mean? – All vendor specific IEs will need to be encrypted – All IEs added in the future will need to be encrypted – We should remain the ability to add unencrypted IE in the future. Submission

doc. : IEEE 802. 11 -13/0133 r 2 Proposal • Define a new IE in Association Req/Resp that can be used to carry a set of TLVs (that include higher layer information etc. ) – Will need the ability to encrypt the content – Will need the ability to fragment the content • Because – Higher Layer Information shall be protected. – Higher Layer Information is larger than 255 octets. Submission

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Encryption Part in Assoc. Req. /Resp. of the Proposal D 0. 3 Proposal MAC Header Capability IEs FILS Session IE Secure Container IE(s) Only the Secure Container IE(s) is(are) encrypted. IEs (future IEs and Vendor Specific IEs) FCS Submission FCS Slide 7 Hitoshi Morioka, Allied Telesis R&D Center

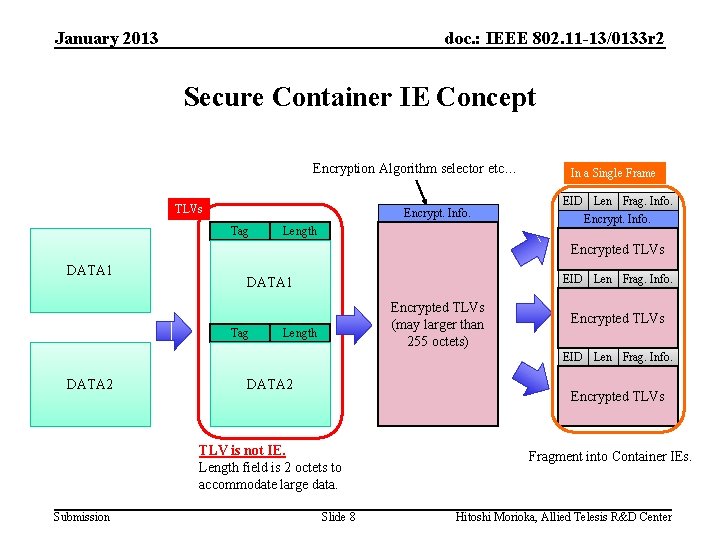
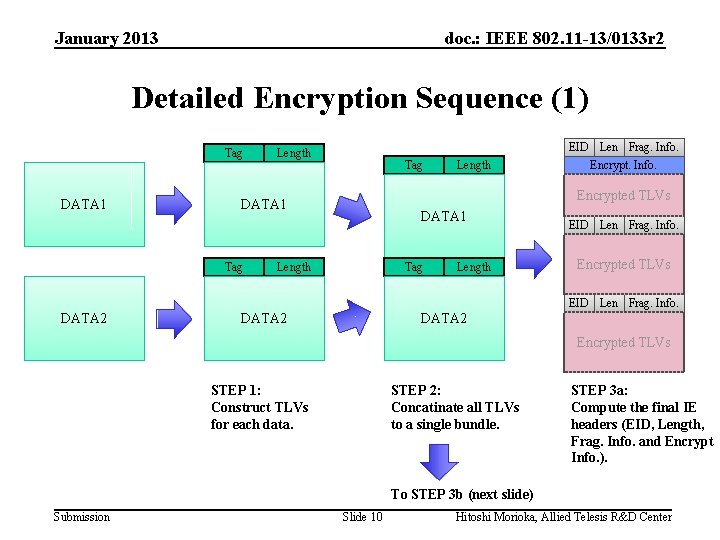
January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Secure Container IE Concept Encryption Algorithm selector etc… TLVs Encrypt. Info. Tag Length In a Single Frame EID Len Frag. Info. Encrypt. Info. Encrypted TLVs DATA 1 EID Len Frag. Info. DATA 1 Tag Encrypted TLVs (may larger than 255 octets) Length Encrypted TLVs EID Len Frag. Info. DATA 2 Encrypted TLVs TLV is not IE. Length field is 2 octets to accommodate large data. Submission Slide 8 Fragment into Container IEs. Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 More Requirements • The following information MUST be authenticated – – – Submission BSSID STA’s MAC Address AP Nonce STA Nonce Capability field All IEs Slide 9 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Detailed Encryption Sequence (1) Tag DATA 1 Length Tag Encrypted TLVs DATA 1 Tag Length EID Len Frag. Info. Encrypt. Info. DATA 1 Length Tag Length EID Len Frag. Info. Encrypted TLVs EID Len Frag. Info. DATA 2 Encrypted TLVs STEP 1: Construct TLVs for each data. STEP 2: Concatinate all TLVs to a single bundle. STEP 3 a: Compute the final IE headers (EID, Length, Frag. Info. and Encrypt Info. ). To STEP 3 b (next slide) Submission Slide 10 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Detailed Encryption Sequence (2) Encrypt. Info. MAC Header EID Len Frag. Info. Encrypt. Info. Capability Encrypted TLVs IEs EID Len Frag. Info. Encrypted TLVs (may larger than 255 octets) Encrypted TLVs EID Len Frag. Info. Secure Container IE(s) Encrypted TLVs STEP 3 b: Encrypt the TLVs. Key: KEK 2 Plaintext: TLVs AAD: BSSID, STA addr, AP Nonce, STA Nonce, Capability, IEs (not to encrypt), IE headers computed in STEP 3 a. Nonce: (AP->STA) 0, (STA->AP) 1 Submission STEP 4: Fragment the encrypted TLVs. Confirm the headers are same as computed in STEP 3 a. IEs (future IEs and Vendor Specific IEs) FCS STEP 5: Prepare the frame to transmit. Slide 11 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Straw poll • Do you support to change the encryption portion of Association Request/Response frame as described in this slide? • Result – – Submission Yes: No: Need more info: Don’t Care: Slide 12 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Backup Submission Slide 13 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Straw poll 1 • Do you support to modify the encryption of Association Request/Response? • Result (Y/N/A): 10/2/24 Submission Slide 14 Hitoshi Morioka, Allied Telesis R&D Center

January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Straw poll 2 • Do you support to create container IE for encryption and fragmentation? • Result (Y/N/Need more info): 8/2/24 Submission Slide 15 Hitoshi Morioka, Allied Telesis R&D Center

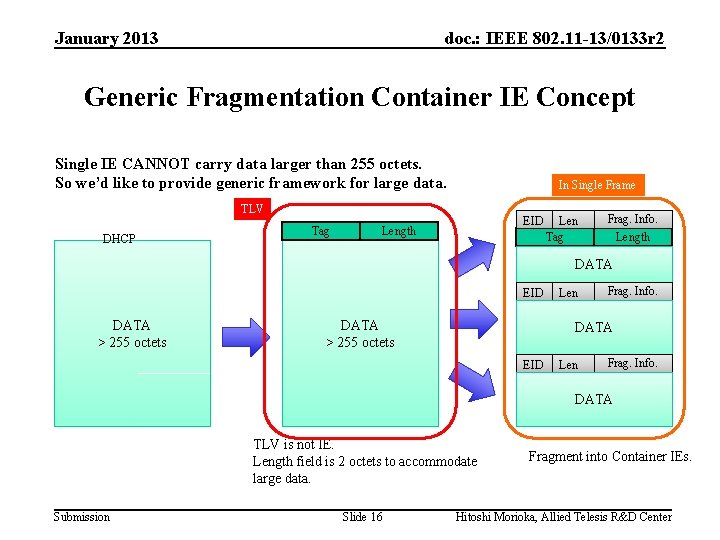
January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Generic Fragmentation Container IE Concept Single IE CANNOT carry data larger than 255 octets. So we’d like to provide generic framework for large data. In Single Frame TLV DHCP Tag EID Length Len Tag Frag. Info. Length DATA EID DATA > 255 octets Len Frag. Info. DATA EID Len Frag. Info. DATA TLV is not IE. Length field is 2 octets to accommodate large data. Submission Slide 16 Fragment into Container IEs. Hitoshi Morioka, Allied Telesis R&D Center

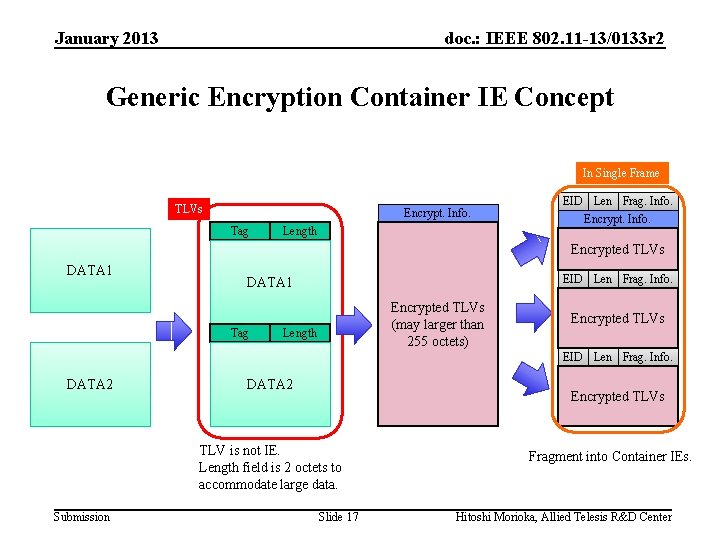
January 2013 doc. : IEEE 802. 11 -13/0133 r 2 Generic Encryption Container IE Concept In Single Frame TLVs Encrypt. Info. Tag Length EID Len Frag. Info. Encrypt. Info. Encrypted TLVs DATA 1 EID Len Frag. Info. DATA 1 Tag Encrypted TLVs (may larger than 255 octets) Length Encrypted TLVs EID Len Frag. Info. DATA 2 Encrypted TLVs TLV is not IE. Length field is 2 octets to accommodate large data. Submission Slide 17 Fragment into Container IEs. Hitoshi Morioka, Allied Telesis R&D Center
 Bridges from 802.x to 802.y
Bridges from 802.x to 802.y Bridges from 802.x to 802.y
Bridges from 802.x to 802.y Wlan standards
Wlan standards Arquitetura ieee 802
Arquitetura ieee 802 Modelo ieee 802
Modelo ieee 802 Ieee 802 standard
Ieee 802 standard 802 15
802 15 802 ieee
802 ieee Ieee 802
Ieee 802 Ieee 802 family
Ieee 802 family Ieee 802 3 compliance
Ieee 802 3 compliance Ruta de convivencia escolar ley 1620
Ruta de convivencia escolar ley 1620 Ley 1620 de 2013 situaciones tipo 1 2 y 3
Ley 1620 de 2013 situaciones tipo 1 2 y 3 Aritmatika sosial kelas 7 semester 2
Aritmatika sosial kelas 7 semester 2 802 701
802 701 Wireless lan 802
Wireless lan 802 Wlan 802
Wlan 802 Modulation coding scheme
Modulation coding scheme