January 2001 doc IEEE 802 11 01039 Use


- Slides: 9

January 2001 doc. : IEEE 802. 11 -01/039 Use of GSM SIM Authentication in IEEE 802. 11 System Submitted to IEEE 802. 11 TGe January 2001 H. Haverinen, J. P. Edney, Nokia Submission 1 Haverinen/Edney, Nokia

January 2001 doc. : IEEE 802. 11 -01/039 Use of GSM SIM Authentication in IEEE 802. 11 System - Submission to Task Group ‘e’ • Focus of 802. 11 has been mostly private ownership of WLAN networks (e. g. Corporate or home use) – New business opportunities can be created by enabling secure public access systems with deployment by nationwide operators. • Existing cellular phone systems form the legacy for public access authentication and security solutions – authorization infrastructure for cellular telecommunications (e. g. , GSM, 3 G) is standardized and widely deployed – Today, there is no simple way for IEEE 802. 11 to leverage this infrastructure in public access applications • This submission proposes how to fit cellular authentication within TGe baseline – Note: the current baseline already is very well in line with this target Submission 2 Haverinen/Edney, Nokia

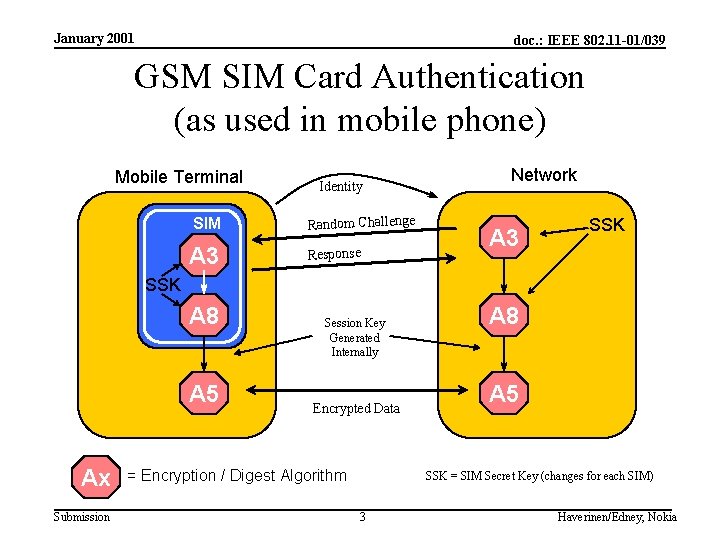
January 2001 doc. : IEEE 802. 11 -01/039 GSM SIM Card Authentication (as used in mobile phone) Mobile Terminal SIM A 3 Identity Random Challenge Response Network A 3 SSK A 8 A 5 Ax Submission Session Key Generated Internally Encrypted Data = Encryption / Digest Algorithm A 8 A 5 SSK = SIM Secret Key (changes for each SIM) 3 Haverinen/Edney, Nokia

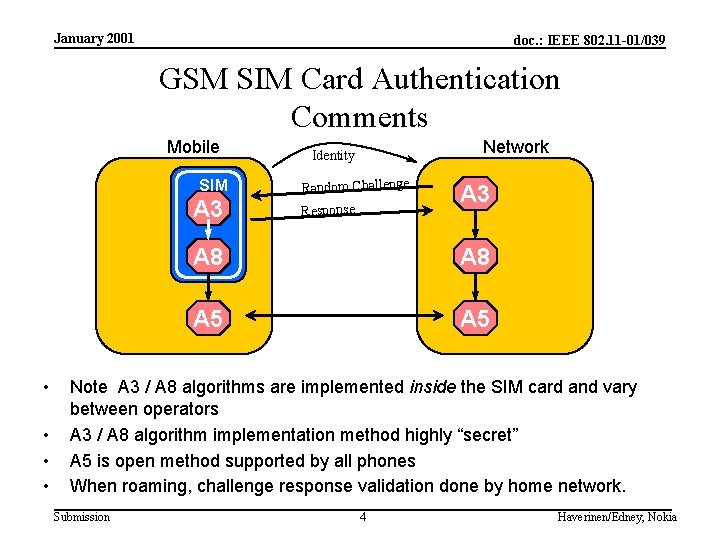
January 2001 doc. : IEEE 802. 11 -01/039 GSM SIM Card Authentication Comments Mobile SIM A 3 • • Network Identity Random Challenge Response A 3 A 8 A 5 Note A 3 / A 8 algorithms are implemented inside the SIM card and vary between operators A 3 / A 8 algorithm implementation method highly “secret” A 5 is open method supported by all phones When roaming, challenge response validation done by home network. Submission 4 Haverinen/Edney, Nokia

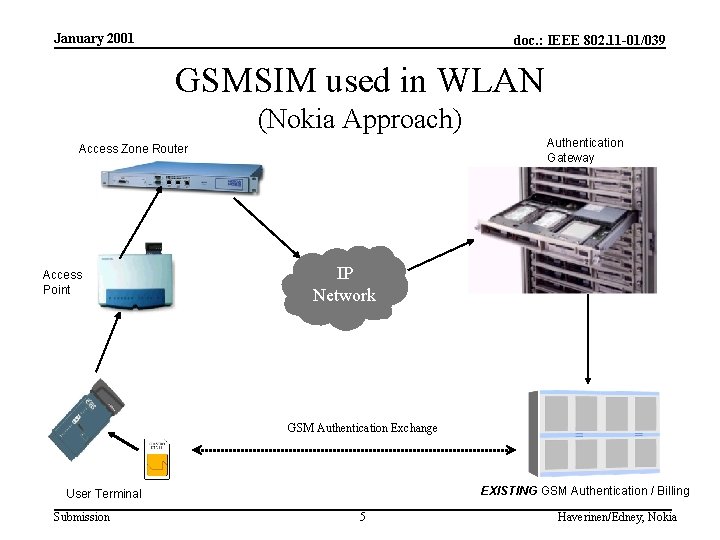
January 2001 doc. : IEEE 802. 11 -01/039 GSMSIM used in WLAN (Nokia Approach) Authentication Gateway Access Zone Router Access Point IP Network GSM Authentication Exchange EXISTING GSM Authentication / Billing User Terminal Submission 5 Haverinen/Edney, Nokia

January 2001 doc. : IEEE 802. 11 -01/039 Integration to TGe Baseline • GSM SIM authentication can be transmitted as an EAP authentication type (EAP/GSMSIM) – – EAP Request/Response : Identity EAP Request/Response : GSMSIM/Start EAP Request/Response : GSMSIM/Challenge EAP Success / Fail • EAP/GSMSIM supports mutual authentication – Client sends a nonce to network – Network accompanies challenge with an authenticator • EAP/GSMSIM will be published as an Internet-Draft Submission 6 Haverinen/Edney, Nokia

January 2001 doc. : IEEE 802. 11 -01/039 Key-Generating EAP types • As part of the authentication procedure, EAP/GSMSIM securely distributes a session key to the client – EAP/GSMSIM is equivalent to EAP/TLS (RFC 2716) • Use several GSM challenges to generate long keys • Baseline should allow negotiation of key-generating EAP as an alternative to the default mechanism (EAP/GSSAPI/IAKERB) – The EAP authentication type makes no difference to the access point, as long as a key is generated • Key distribution between access points needs to be agreed upon Submission 7 Haverinen/Edney, Nokia

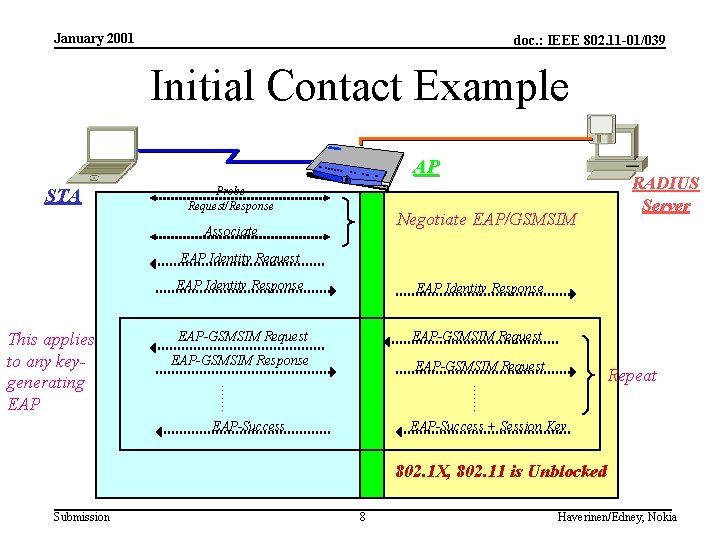
January 2001 doc. : IEEE 802. 11 -01/039 Initial Contact Example AP STA Probe Request/Response Negotiate EAP/GSMSIM Associate RADIUS Server EAP Identity Request EAP Identity Response EAP-GSMSIM Request EAP-GSMSIM Response EAP-GSMSIM Request Repeat ……. This applies to any keygenerating EAP Identity Response EAP-Success + Session Key 802. 1 X, 802. 11 is Unblocked Submission 8 Haverinen/Edney, Nokia

January 2001 doc. : IEEE 802. 11 -01/039 Summary • Baseline should include any EAP authentication type that generates a key – EAP/TLS, EAP/GSMSIM and others • • Submission Need to determine a method to negotiate key-generating EAP type Need to agree on a key distribution mechanism 9 Haverinen/Edney, Nokia