ITUT Workshop on New challenges for Telecommunication Security






- Slides: 13

ITU-T Workshop on “New challenges for Telecommunication Security Standardization" V 1. 0 Geneva, 9(pm)-10 February 2009 Identity Management Anthony M. Rutkowski V-P, Regulatory Affairs and Standards Veri. Sign, Inc. Geneva, 9(pm)-10 February 2009 International Telecommunication Union

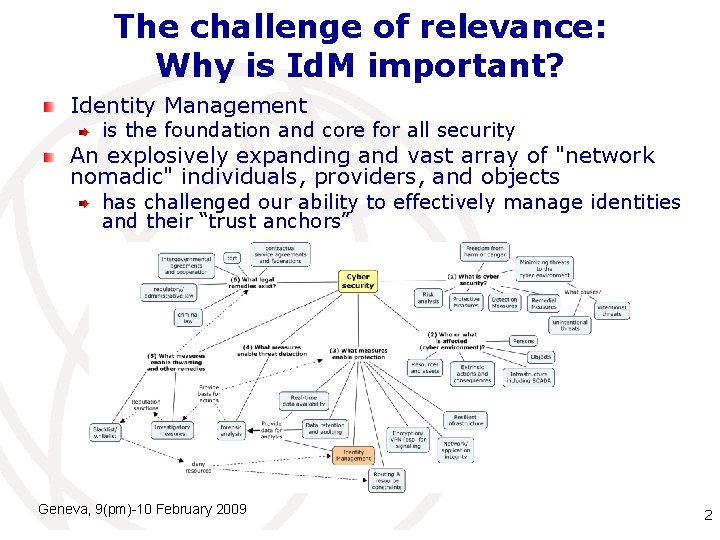
The challenge of relevance: Why is Id. M important? Identity Management is the foundation and core for all security An explosively expanding and vast array of "network nomadic" individuals, providers, and objects has challenged our ability to effectively manage identities and their “trust anchors” Geneva, 9(pm)-10 February 2009 International Telecommunication Union 2

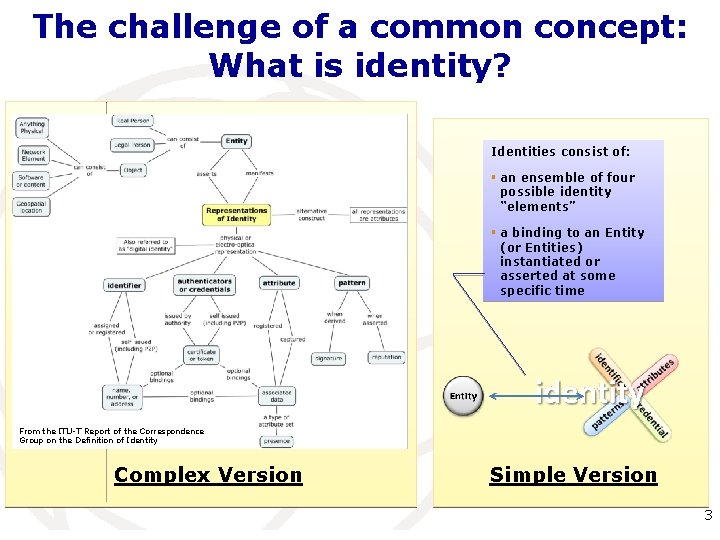
The challenge of a common concept: What is identity? Identities consist of: § an ensemble of four possible identity “elements” § a binding to an Entity (or Entities) instantiated or asserted at some specific time From the ITU-T Report of the Correspondence Group on the Definition of Identity Complex Version Simple Version International Telecommunication Union 3

The challenge of diversity: Disparate identity communities Operators and providers Focussed on revenue opportunities, infrastructure protection, network management forensics, fraud mitigation Business end-users Focussed on minimizing costs, employee support, fraud mitigation, inventory and supply chain management Individual end-users Focussed on social networking, convenience, identity services (esp. location based services) and portability, controlling unwanted intrusions and mitigating identity theft Security Focussed on infrastructure protection, homeland security, NS/EP needs, consumer protection, law enforcement forensics, meeting public policy and legal mandates including personal identity credentials and biometrics Privacy and anonymity Spans a broad spectrum from personal identity protection and intrusion minimization to extreme views on complete anonymity, anti-government paranoia and control of all personal identity elements International Telecommunication Union 4

The challenge of focus and vision: What is important? Discovery of authoritative sources of identities and structured means to query source information Structured identity ontologies and data models for interoperability Critical to sharing of identities Protected identity management “signalling” infrastructure in NGNs Means to support inter & intra federation identity capabilities Inter-federation mechanisms are non-existent Providing for a range of trust relationships (no trust to PKI-based high assurance trust) Supporting Peer-to-Peer platforms Implementing trusted Open Identity Architectures as a means of achieving “Identity Network Neutrality” Achieving effective “trust anchors” Identity Identity proofing lifecycle management status checking on-demand security management auditing International Telecommunication Union 5

Capabilities that will make a difference in 2009 THE CHALLENGE OF DELIVERABLES International Telecommunication Union 6

Provider Identity Trust Anchors Number one “low-hanging” Identity Management/cybersecurity capability with far reaching positive impact A universal global means for establishing trust in all organizations that have a network presence For communications, transactions, software, and secure transport layer Significant implementation has already occurred Based on Extended Validation (EV) Digital Certificate standard implementation of ITU-T X. 509 platform (also known as EV SSL) Developed in 2007 by the CA/Browser Forum Certificates initially issued and browser updates pushed out to most computers in 2008 Consists of the best combination of identity assurance techniques and platforms Initial identity proofing based on ETSI standards Basis for organization trust in Liberty Alliance assurance specifications Used by the ITU itself! Upcoming EV enhancements in 2009 Being extended to all kinds of services and software distribution in 2009, including SIP Being introduced into ITU-T SG 17 through liaison process Substantial ongoing regional activity to meet localization requirements worldwide Being considered as an NGN network address enhancement Cryptography being upgraded to ECC Embeds many diverse organization identifiers, including ITU-T Object Identifiers (OIDs) that have become Internet global “enterprise ID” of choice Enhances individual privacy and broadly benefits everybody May become a global regulatory mandate for cybersecurity International Telecommunication Union 7

Object trust anchors Real-time Object IDentifier resolution system Provides a DNS-based means for discovering information about any Object Id OIDs becoming increasingly important for Network elements (especially forensic acquisition locations in a network) Terminal devices, software, RFID tagged objects, sensors, biometric scanners, e-health, power management, and intellectual property Creation of a new DNS top level domain – OID Initial implementations occurring in 2009 based on specifications developed in ITU-T and ISO Real-time token validation protocol systems Verifying the current status of all object credentials is essential Allows implementation of “when things go wrong” capabilities Online Certificate Status Protocol (OCSP) has emerged as means of choice and being mandated by some trust implementations Similar RSA protocols for token use are being extended International Telecommunication Union 8

Personal identity trust anchors The world is awash in a sea of countless personal identities Many personal identities have little or no trust anchors Diverse expectations exist among people, organizations, and nations concerning the use and availability of identities – many subject to law Expectations are highly context dependent and often conflicting Potential “identity network neutrality” challenges abound Significant contemporary personal identity needs e. Health Homeland security Nomadicity and social networking Significant technical platforms are emerging Interoperable and Trust Third Party platforms Open. ID Personal Identity Portals National e. IDs, especially the EU’s STORK (Secure Identity Across Borders Linked) initiative One time password tokens Encrypted biometrics A major impediment for personal identity trust is lifecycle maintenance Bears the initial and lifecycle costs, including indemnification Providing real-time status checking Accommodating enormously broad assurance spectrum International Telecommunication Union 9

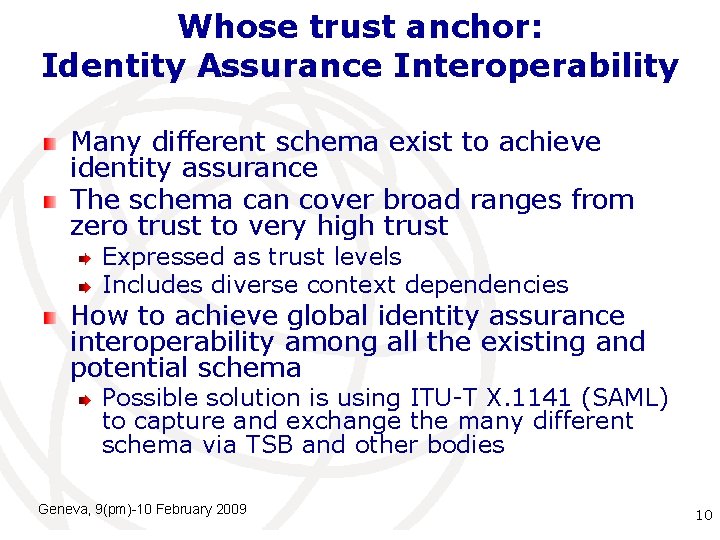
Whose trust anchor: Identity Assurance Interoperability Many different schema exist to achieve identity assurance The schema can cover broad ranges from zero trust to very high trust Expressed as trust levels Includes diverse context dependencies How to achieve global identity assurance interoperability among all the existing and potential schema Possible solution is using ITU-T X. 1141 (SAML) to capture and exchange the many different schema via TSB and other bodies Geneva, 9(pm)-10 February 2009 International Telecommunication 10 Union

Trust Anchors begin at home: Standards and spawned identities Challenge is to enhance identity management trust anchors by enabling structured discovery and on-demand public access to Standards Registrations and assignments specified in standards Real-time access to standards Most standards bodies now allow global public access to their specifications Network Id. M/security standards not publicly available have little value Next step is make them discoverable, versioned, and accessible with a click Real-time access to registrations and assignments Standards result in many secretariats and other bodies creating identities Few provide structured, real-time means for discovery and access Both ITU TSB and IETF IANA are building capabilities Can serve as models for other bodies and administrators worldwide International Telecommunication 11 Union

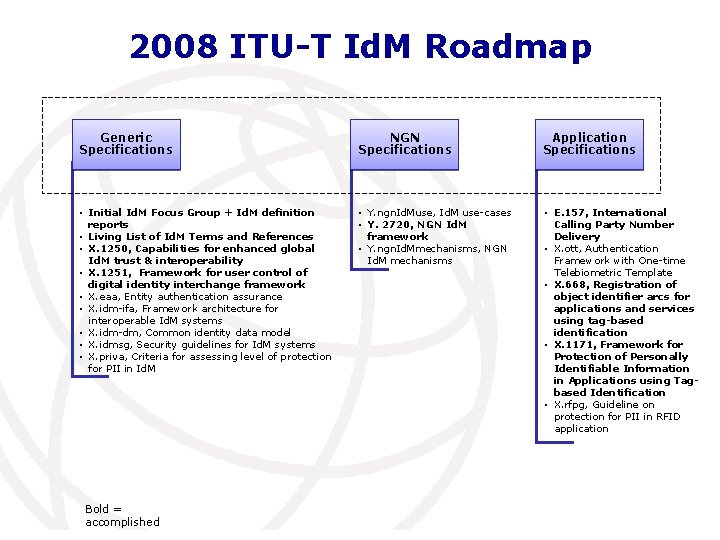
2008 ITU-T Id. M Roadmap Generic Specifications NGN Specifications Application Specifications • Initial Id. M Focus Group + Id. M definition reports • Living List of Id. M Terms and References • X. 1250, Capabilities for enhanced global Id. M trust & interoperability • X. 1251, Framework for user control of digital identity interchange framework • X. eaa, Entity authentication assurance • X. idm-ifa, Framework architecture for interoperable Id. M systems • X. idm-dm, Common identity data model • X. idmsg, Security guidelines for Id. M systems • X. priva, Criteria for assessing level of protection for PII in Id. M • Y. ngn. Id. Muse, Id. M use-cases • Y. 2720, NGN Id. M framework • Y. ngn. Id. Mmechanisms, NGN Id. M mechanisms • E. 157, International Calling Party Number Delivery • X. ott, Authentication Framework with One-time Telebiometric Template • X. 668, Registration of object identifier arcs for applications and services using tag-based identification • X. 1171, Framework for Protection of Personally Identifiable Information in Applications using Tagbased Identification • X. rfpg, Guideline on protection for PII in RFID application Bold = accomplished International Telecommunication Union

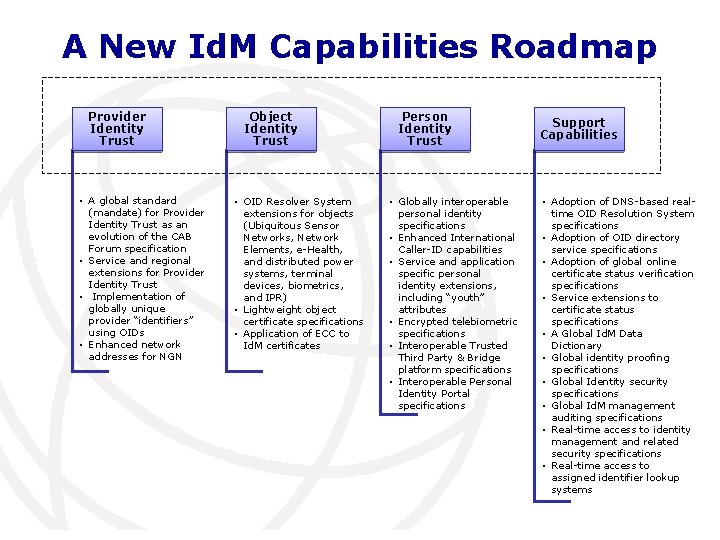
A New Id. M Capabilities Roadmap Provider Identity Trust • A global standard (mandate) for Provider Identity Trust as an evolution of the CAB Forum specification • Service and regional extensions for Provider Identity Trust • Implementation of globally unique provider “identifiers” using OIDs • Enhanced network addresses for NGN Object Identity Trust • OID Resolver System extensions for objects (Ubiquitous Sensor Networks, Network Elements, e-Health, and distributed power systems, terminal devices, biometrics, and IPR) • Lightweight object certificate specifications • Application of ECC to Id. M certificates Person Identity Trust • Globally interoperable personal identity specifications • Enhanced International Caller-ID capabilities • Service and application specific personal identity extensions, including “youth” attributes • Encrypted telebiometric specifications • Interoperable Trusted Third Party & Bridge platform specifications • Interoperable Personal Identity Portal specifications Support Capabilities • Adoption of DNS-based realtime OID Resolution System specifications • Adoption of OID directory service specifications • Adoption of global online certificate status verification specifications • Service extensions to certificate status specifications • A Global Id. M Data Dictionary • Global identity proofing specifications • Global Identity security specifications • Global Id. M management auditing specifications • Real-time access to identity management and related security specifications • Real-time access to assigned identifier lookup systems International Telecommunication Union