ITUT Recommendation X 805 Security Architecture for Systems







- Slides: 20

ITU-T Recommendation X. 805 Security Architecture for Systems Providing End-to-End Communications IETF 63 meeting Zachary Zeltsan, Bell Laboratories, Lucent Technologies Rapporteur of Question 5 SG 17

Outline § Origin of the ITU-T Recommendation X. 805 - Security Architecture for Systems Providing End-to-End Communications § § § Three main issues that X. 805 addresses Security Dimensions Security Layers Security Planes ITU-T X. 805 Security Architecture ITU-T Recommendation X. 805 as a base for security work in FGNGN Security Capability WG 2

Origin of the ITU-T Recommendation X. 805 • ITU-T Recommendation X. 805 Security architecture for systems providing end‑to‑end communications had been developed by ITU-T SG 17 (ITU-T Lead Study Group on Telecommunication Security) and was published in October 2003. • The group has developed a set of the well-recognized Recommendations on security. Among them are X. 800 Series of Recommendations on security and X. 509 - Public -key and Attribute Certificate Frameworks. 3

Three main issues that X. 805 addresses The security architecture addresses three essential issues: 1. What kind of protection is needed and against what threats? 2. What are the distinct types of network equipment and facility groupings that need to be protected? 3. What are the distinct types of network activities that need to be protected? 4

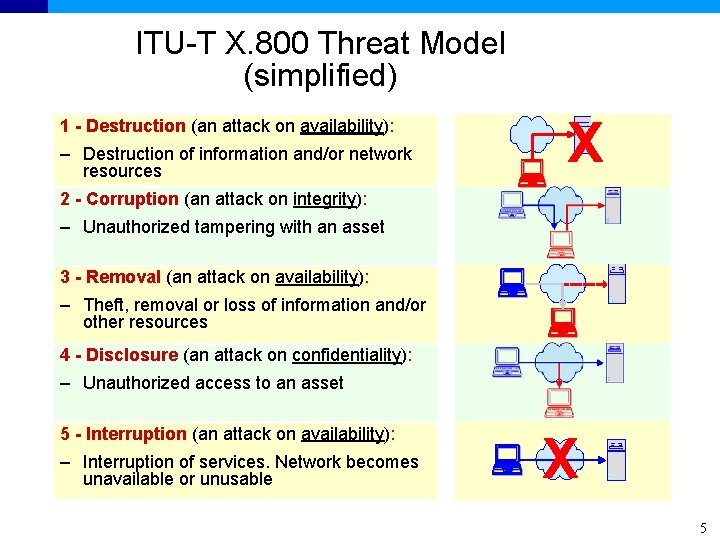
ITU-T X. 800 Threat Model (simplified) 1 - Destruction (an attack on availability): – Destruction of information and/or network resources X 2 - Corruption (an attack on integrity): – Unauthorized tampering with an asset 3 - Removal (an attack on availability): – Theft, removal or loss of information and/or other resources 4 - Disclosure (an attack on confidentiality): – Unauthorized access to an asset 5 - Interruption (an attack on availability): – Interruption of services. Network becomes unavailable or unusable X 5

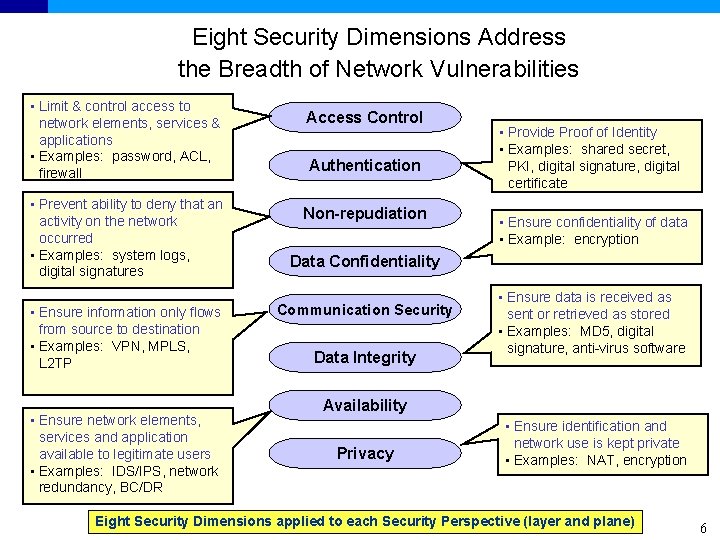
Eight Security Dimensions Address the Breadth of Network Vulnerabilities • Limit & control access to network elements, services & applications • Examples: password, ACL, firewall • Prevent ability to deny that an activity on the network occurred • Examples: system logs, digital signatures • Ensure information only flows from source to destination • Examples: VPN, MPLS, L 2 TP • Ensure network elements, services and application available to legitimate users • Examples: IDS/IPS, network redundancy, BC/DR Access Control Authentication Non-repudiation • Provide Proof of Identity • Examples: shared secret, PKI, digital signature, digital certificate • Ensure confidentiality of data • Example: encryption Data Confidentiality Communication Security Data Integrity • Ensure data is received as sent or retrieved as stored • Examples: MD 5, digital signature, anti-virus software Availability Privacy • Ensure identification and network use is kept private • Examples: NAT, encryption Eight Security Dimensions applied to each Security Perspective (layer and plane) 6

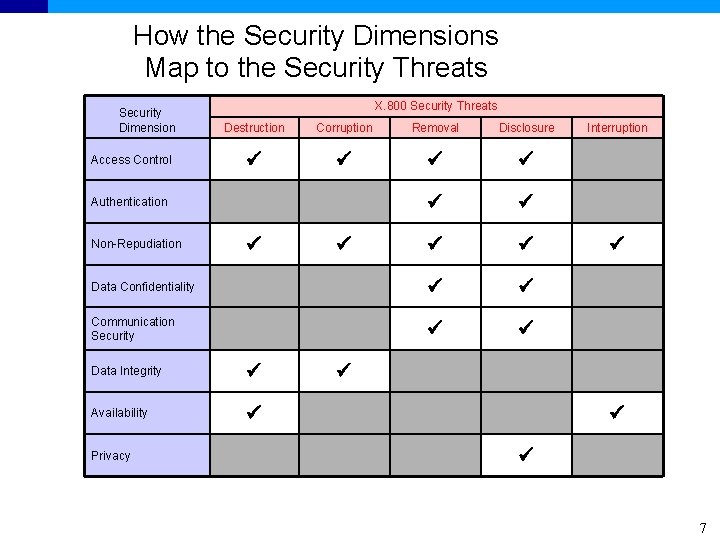
How the Security Dimensions Map to the Security Threats Security Dimension X. 800 Security Threats Destruction Corruption Removal Disclosure Data Confidentiality Communication Security Access Control Authentication Non-Repudiation Data Integrity Availability Privacy Interruption 7

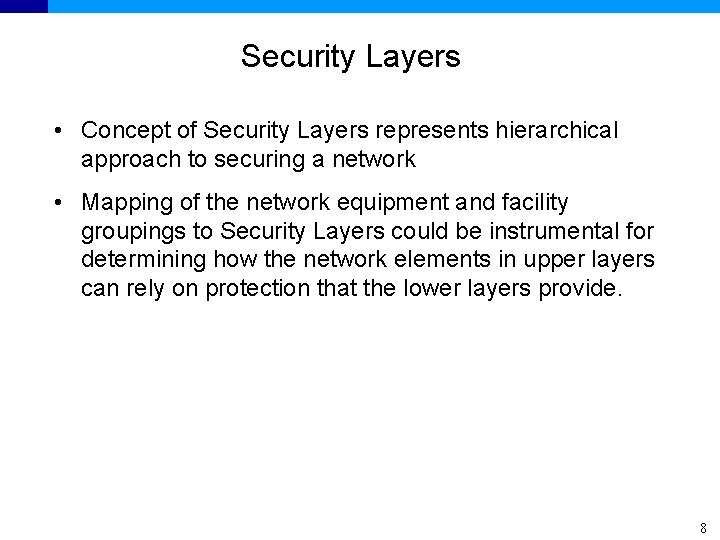
Security Layers • Concept of Security Layers represents hierarchical approach to securing a network • Mapping of the network equipment and facility groupings to Security Layers could be instrumental for determining how the network elements in upper layers can rely on protection that the lower layers provide. 8

Three Security Layers Applications Security THREATS Services Security VULNERABILITIES Destruction Corruption Removal Disclosure Vulnerabilities Can Exist In Each Layer Infrastructure Security Interruption ATTACKS 3 - Applications Security Layer: • Network-based applications accessed by end -users • Examples: – Web browsing – Directory assistance – Email – E-commerce 1 - Infrastructure Security Layer: 2 - Services Security Layer: • Fundamental building blocks of networks services and applications • Examples: – Individual routers, switches, servers – Point-to-point WAN links – Ethernet links • Services Provided to End-Users • Examples: – Frame Relay, ATM, IP – Cellular, Wi-Fi, – Vo. IP, Qo. S, IM, Location services – Toll free call services • Each Security Layer has unique vulnerabilities, threats • Infrastructure security enables services security enables applications security 9

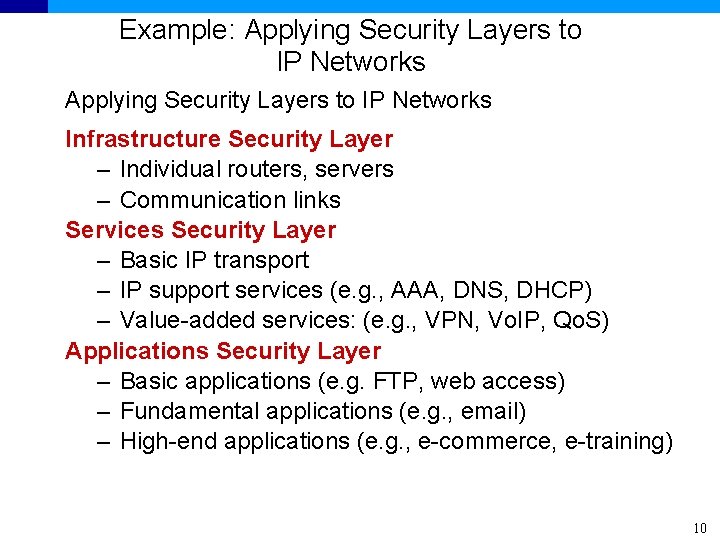
Example: Applying Security Layers to IP Networks Infrastructure Security Layer – Individual routers, servers – Communication links Services Security Layer – Basic IP transport – IP support services (e. g. , AAA, DNS, DHCP) – Value-added services: (e. g. , VPN, Vo. IP, Qo. S) Applications Security Layer – Basic applications (e. g. FTP, web access) – Fundamental applications (e. g. , email) – High-end applications (e. g. , e-commerce, e-training) 10

Security Planes • Concept of Security Planes could be instrumental for ensuring that essential network activities are protected independently (e. g. compromise of security at the Enduser Security Plane does not affect functions associated with the Management Security Plane). • Concept of Security Planes allows to identify potential network vulnerabilities that may occur when distinct network activities depend on the same security measures for protection. 11

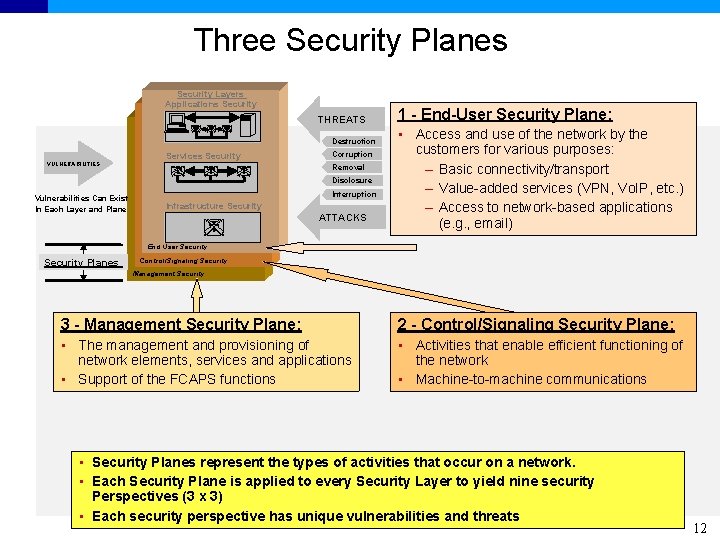
Three Security Planes Security Layers Applications Security THREATS Destruction Services Security VULNERABILITIES Corruption Removal Disclosure Vulnerabilities Can Exist In Each Layer and Plane Interruption Infrastructure Security ATTACKS 1 - End-User Security Plane: • Access and use of the network by the customers for various purposes: – Basic connectivity/transport – Value-added services (VPN, Vo. IP, etc. ) – Access to network-based applications (e. g. , email) End User Security Planes Control/Signaling Security Management Security 3 - Management Security Plane: 2 - Control/Signaling Security Plane: • The management and provisioning of network elements, services and applications • Support of the FCAPS functions • Activities that enable efficient functioning of the network • Machine-to-machine communications • Security Planes represent the types of activities that occur on a network. • Each Security Plane is applied to every Security Layer to yield nine security Perspectives (3 x 3) • Each security perspective has unique vulnerabilities and threats 12

Example: Applying Security Planes to Network Protocols End User Security Plane Activities • End-user data transfer • End-user – application interactions Protocols • HTTP, RTP, POP, IMAP • TCP, UDP, FTP • IPsec, TLS Control/Signaling Security Plane Activities • Update of routing/switching tables • Service initiation, control, and teardown • Application control Protocols • BGP, OSPF, IS-IS, RIP, PIM • SIP, RSVP, H. 323, SS 7. • IKE, ICMP • PKI, DNS, DHCP, SMTP Management Security Plane Activities • Operations • Administration • Management • Provisioning Protocols • SNMP • Telnet • FTP • HTTP 13

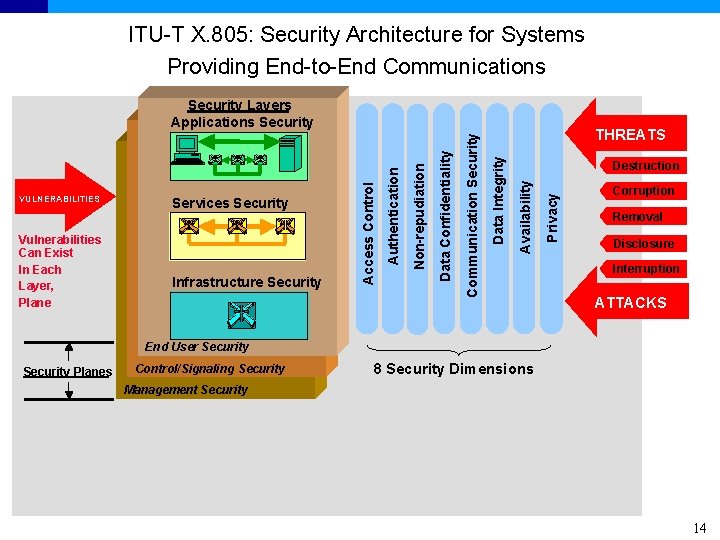
ITU-T X. 805: Security Architecture for Systems Providing End-to-End Communications THREATS Privacy Destruction Availability Integrity Data Integrity Communication Security Data Confidentiality Infrastructure Security Non-repudiation Vulnerabilities Can Exist In Each Layer, Plane Services Security Authentication VULNERABILITIES Access Control Management Security Layers Applications Security Corruption Removal Disclosure Interruption ATTACKS End User Security Planes Control/Signaling Security 8 Security Dimensions Management Security 14

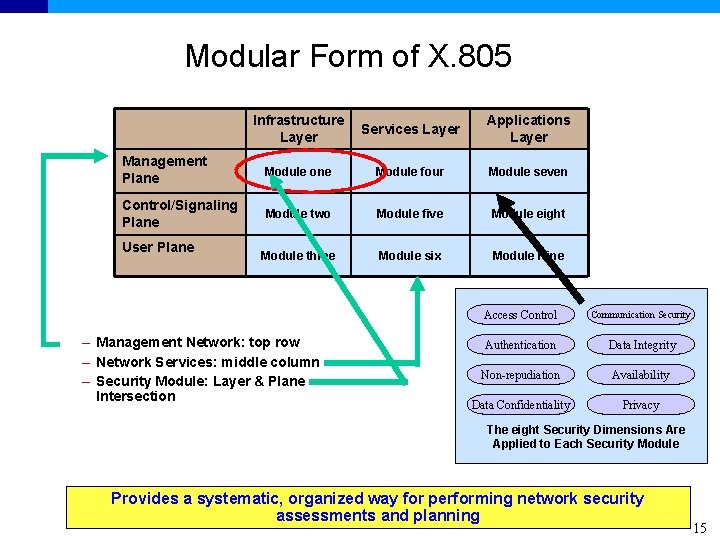
Modular Form of X. 805 Infrastructure Layer Services Layer Applications Layer Management Plane Module one Module four Module seven Control/Signaling Plane Module two Module five Module eight Module three Module six Module Nine User Plane – Management Network: top row – Network Services: middle column – Security Module: Layer & Plane Intersection Access Control Communication Security Authentication Data Integrity Non-repudiation Availability Data Confidentiality Privacy The eight Security Dimensions Are Applied to Each Security Module Provides a systematic, organized way for performing network security assessments and planning 15

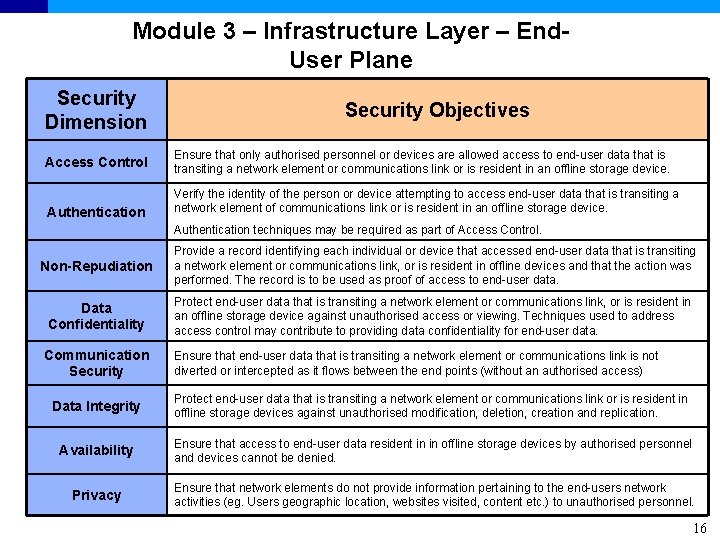
Module 3 – Infrastructure Layer – End. User Plane Security Dimension Access Control Authentication Security Objectives Ensure that only authorised personnel or devices are allowed access to end-user data that is transiting a network element or communications link or is resident in an offline storage device. Verify the identity of the person or device attempting to access end-user data that is transiting a network element of communications link or is resident in an offline storage device. Authentication techniques may be required as part of Access Control. Non-Repudiation Provide a record identifying each individual or device that accessed end-user data that is transiting a network element or communications link, or is resident in offline devices and that the action was performed. The record is to be used as proof of access to end-user data. Data Confidentiality Protect end-user data that is transiting a network element or communications link, or is resident in an offline storage device against unauthorised access or viewing. Techniques used to address access control may contribute to providing data confidentiality for end-user data. www. lucent. com/security Communication Security Ensure that end-user data that is transiting a network element or communications link is not diverted or intercepted as it flows between the end points (without an authorised access) Data Integrity Protect end-user data that is transiting a network element or communications link or is resident in offline storage devices against unauthorised modification, deletion, creation and replication. Availability Ensure that access to end-user data resident in in offline storage devices by authorised personnel and devices cannot be denied. Privacy Ensure that network elements do not provide information pertaining to the end-users network activities (eg. Users geographic location, websites visited, content etc. ) to unauthorised personnel. 16

Summary: X. 805 Provides a Holistic Approach to Network Security § Comprehensive, end-to-end network view of security § Applies to any network technology – Wireless, wireline, optical networks – Voice, data, video, converged networks § Applies to variety of networks – Service provider networks – Enterprise (service provider’s customer) networks – Government networks – Management/operations, administrative networks – Data center networks § Is aligned with other security ITU-T Recommendations and ISO standards 17

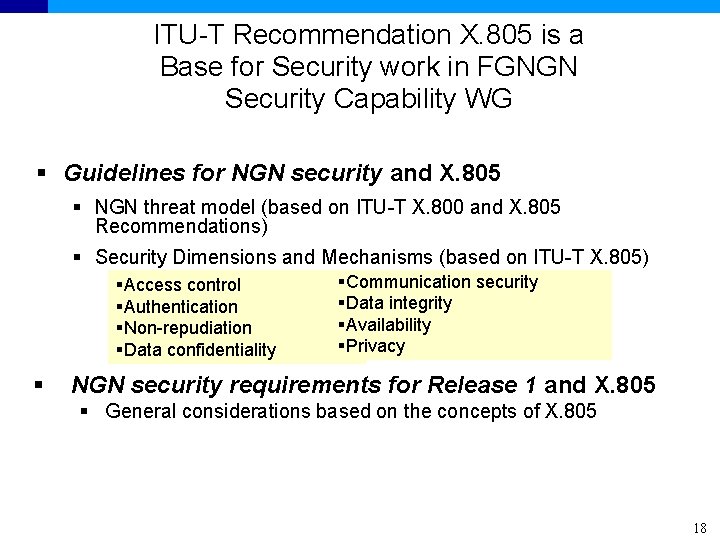
ITU-T Recommendation X. 805 is a Base for Security work in FGNGN Security Capability WG § Guidelines for NGN security and X. 805 § NGN threat model (based on ITU-T X. 800 and X. 805 Recommendations) § Security Dimensions and Mechanisms (based on ITU-T X. 805) §Access control §Authentication §Non-repudiation §Data confidentiality § §Communication security §Data integrity §Availability §Privacy NGN security requirements for Release 1 and X. 805 § General considerations based on the concepts of X. 805 18

Acronyms AAA Authentication, Authorization, Accounting L 2 TP Layer Two Tunneling Protocol ACL Access Control List MPLS Multi-Protocol Label Switching ATM Asynchronous Transfer Mod NAT BC OSPF Open Shortest Path First Business Continuity Network Address Translation BGP Border Gateway Protocol PIM Protocol-Independent Multicast DHCP Dynamic Host Configuration Protocol PKI Public Key Infrastructure DNS Domain Name Service POP Post Office Protocol DR Disaster Recovery Qo. S Quality of Service RIP Routing Information Protocol FCAPS Fault-management, Configuration, Accounting, Performance, and Security FTP File Transfer Protocol HTTP Hyper Text Transfer Protocol ICMP Internet Control Message Protocol IDS Intrusion Detection System IKE Internet Key Exchange protocol IM Instant Messaging IMAP Internet Message Access Protocol IPS Intrusion Prevention System IPsec IP security (set of protocols) IS-IS Intermediate System-to-Intermediate System (routing protocol) RSVP Resource Reservation Setup Protocol RTP Real-time Transport Protocol SIP Session Initiation Protocol SMTP Simple Mail Transfer Protocol SNMP Simple Network Management Protocol SS 7 Signaling System 7 TCP Transmission Control Protocol TLS Transport Layer Security protocol UDP User Datagram Protocol Vo. IP Voice over IP VPN Virtual Private Network 19

Thank you! 20