Its your data are you sure its safe











- Slides: 14

It’s your data – are you sure it’s safe? Team Mag 5 Valerie Buitron Jaime Calahorrano Derek Chow Julia Marsh Mark Zogbaum

Every company needs places to store institutional knowledge and data. Frequently that data contains proprietary information Personally Identifiable Data Employee HR Data Financial Data The security and confidentiality of this data is of critical importance.

There are four key issues in the security of databases just as with all security systems Availability Authenticity Integrity Confidentiality

Data needs to be available at all necessary times Data needs to be available to only the appropriate users Need to be able to track who has access to and who has accessed what data

Need to ensure that the data has been edited by an authorized source Need to confirm that users accessing the system are who they say they are Need to verify that all report requests are from authorized users Need to verify that any outbound data is going to the expected receiver

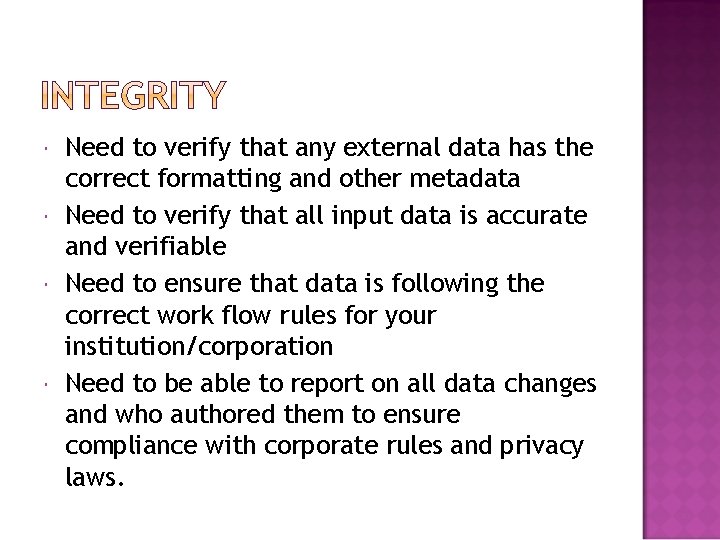
Need to verify that any external data has the correct formatting and other metadata Need to verify that all input data is accurate and verifiable Need to ensure that data is following the correct work flow rules for your institution/corporation Need to be able to report on all data changes and who authored them to ensure compliance with corporate rules and privacy laws.

Need to ensure that confidential data is only available to correct people Need to ensure that entire database is security from external and internal system breaches Need to provide for reporting on who has accessed what data and what they have done with it Mission critical and Legal sensitive data must be highly security at the potential risk of lost business and litigation

Although the 4 pillars are of equal importance we are focusing on Confidentiality due to the prevalence of data loss in financial and personal areas We are going to review solutions for Internal data loss External hacking Securing data if hardware stolen Unapproved Administrator Access

Another set of security issues come from middleware that sits between the user and the data Single sign on authentication Allows users to just have one password to access all systems but also means that theft of one password endangers all systems

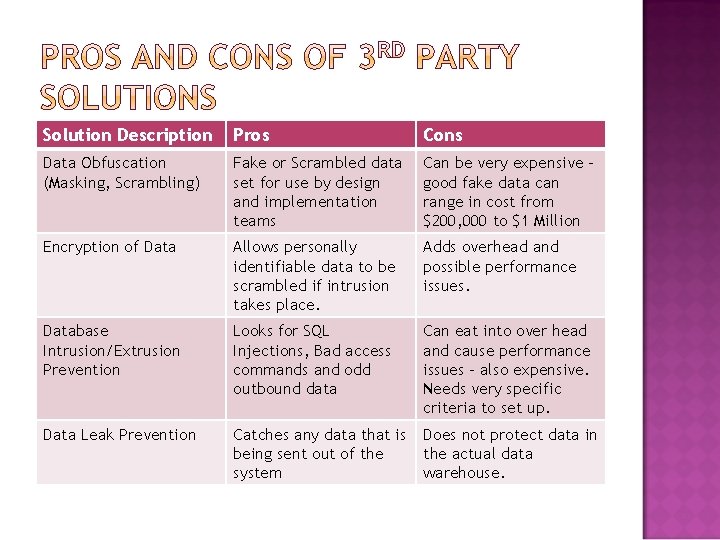
Most companies have several types of databases so to ensure total security across databases they hire 3 rd party Database Security Vendors such as Guardium, Inc. and Imperva, Inc. Those companies have solutions for Database Activity Monitoring (DAM) Prices range from $20 K to $1 Million Another option is data masking – buying a fake data set for development and testing.

Solution Description Pros Cons Data Obfuscation (Masking, Scrambling) Fake or Scrambled data set for use by design and implementation teams Can be very expensive – good fake data can range in cost from $200, 000 to $1 Million Encryption of Data Allows personally identifiable data to be scrambled if intrusion takes place. Adds overhead and possible performance issues. Database Intrusion/Extrusion Prevention Looks for SQL Injections, Bad access commands and odd outbound data Can eat into over head and cause performance issues – also expensive. Needs very specific criteria to set up. Data Leak Prevention Catches any data that is being sent out of the system Does not protect data in the actual data warehouse.

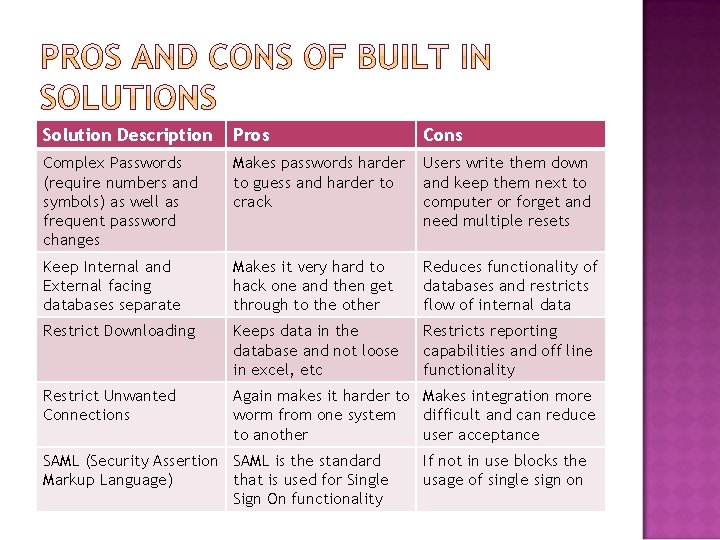
Vendors such as Oracle, Microsoft and IBM know that security is a big concern for data systems. They create built in solutions such as: Password Controls Data access based on roles and profiles IP restrictions for off site access Auditing capabilities of who has run what reports Security logging

Solution Description Pros Cons Complex Passwords (require numbers and symbols) as well as frequent password changes Makes passwords harder to guess and harder to crack Users write them down and keep them next to computer or forget and need multiple resets Keep Internal and External facing databases separate Makes it very hard to hack one and then get through to the other Reduces functionality of databases and restricts flow of internal data Restrict Downloading Keeps data in the database and not loose in excel, etc Restricts reporting capabilities and off line functionality Restrict Unwanted Connections Again makes it harder to Makes integration more worm from one system difficult and can reduce to another user acceptance SAML (Security Assertion SAML is the standard Markup Language) that is used for Single Sign On functionality If not in use blocks the usage of single sign on

Will we be able to keep the data secure while keeping the users happy? Tune in Week 10 to find out! Same Bat Time Same Bat Channel