ITIS 61678167 Network Security Weichao Wang Contents ICMP



































- Slides: 55

ITIS 6167/8167: Network Security Weichao Wang

Contents • ICMP protocol and attacks • UDP protocol and attacks • TCP protocol and attacks 2

3

• ICMP: Internet Control Message Protocol • Motivation – IP may fail to deliver data because • Destination is unavailable • TTL expires • Routers become congested – Sender needs to know the condition – ICMP is a part of IP 4

• Purpose – ICMP allows routers or hosts to send error reports or control messages to other routers or hosts – ICMP is for reporting but not correction – ICMP provides communication b/w IP software modules 5

• Restriction – ICMP messages are not generated for errors caused by ICMP error reporting messages. Why? – ICMP will only be sent to original sources. Why? 6

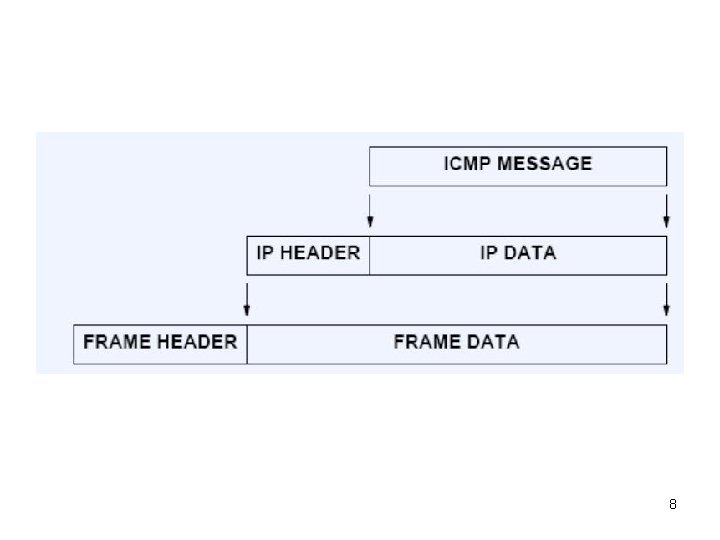
• ICMP encapsulation – It is within the IP packet, but the protocol is considered as a part of IP 7

8

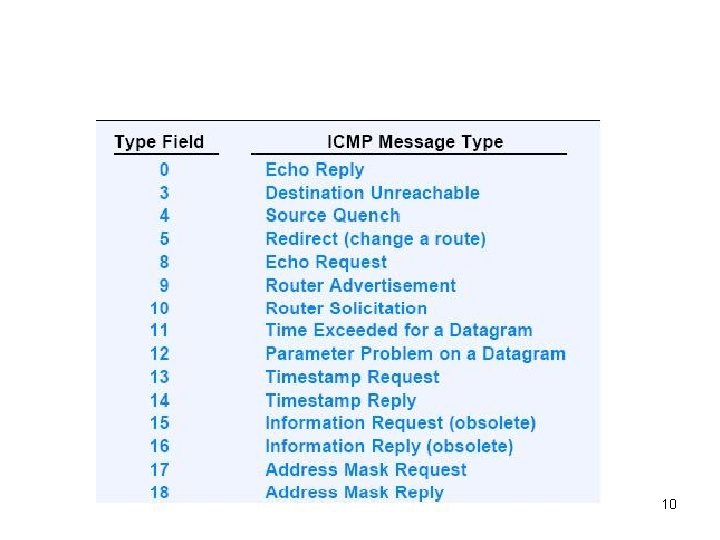
• ICMP messages • Common header – Each ICMP message has its own format, but all begin with the same three fields – TYPE (1 byte): identify the message – CODE (1 byte): more information about the message – Checksum (2 byte) – When an ICMP message report errors, it always include the IP header and first 64 bits of the original packet 9

10

• ICMP echo request and reply (ping) – Used to test reachability – Type 0 and 8 – Add identifier (2 byte) and sequence number (2 byte) after the checksum. Used by sender to match the request and reply and measure time – An echo request can contain some data part (the content does not matter) – The reply always replies with the same data part 11

• Destination unreachable (type 3) – When the router cannot forward or deliver the IP packet, it sends a destination unreachable message back to the original source. – Codes used • • • 0: network unreachable 1: host unreachable 2: protocol unreachable 3: port unreachable 4: fragment needed but DF (no fragment) set 5: source route fails 12

• More codes of destination unreachable – 6: destination network unknown – 7: destination host unknown – Etc • Add 2 byte of zero, and two bytes of the next hop MTU after the checksum. Then attach the IP header and the first 64 bits of data 13

• Source quench (type=4) – To deal with congestion and datagram flow control – When routers are overrun with traffic, it is called congestion • May be caused by difference in line speed • May be caused by converge of multiple traffic flows – Use source quench to report congestion to the sources – There is no ICMP message to achieve the reverse effect. The host will slowly increase the rate when no source quench requests are received. – Have been shown that this does not work very well 14

• In the source quench ICMP packet – Add 32 bits of zero after the checksum – Attach the IP header and the 64 bits of data of the discarded packet 15

• Router redirect (type=5) – Routers periodically exchange information. Hosts usually do not – Hosts will start with a minimum amount of routing information and learn from routers – A router will send an ICMP redirect packet to host if it knows a better path so the host can change its routing table – Limited to the host and routers in a directly connected network (same Ethernet segment) 16

• After the type, code and checksum – Attach the router’s IP address on the better route – Attach the packet’s IP header and first 64 bits 17

• TTL expires (type=11) – Can be caused by TTL = 0 or the fragment reassemble expires – Attach 32 bits of zero, the IP header, and the first 64 bits of data in the original packet 18

• Timestamp request and reply (type 13, 14) – Needs identifier and sequence number to match the request and reply – Will contain the sender’s clock reading when the packet is sent, the receiver’s clock when it is received, and when the reply is transmitted. 19

• Information request and reply (type 15, 16) – Used to get IP address – Have been replaced by RARP and BOOTP • Getting subnet mask (type 17, 18) – For subnet functionality 20

21

• Attacks on ICMP – ICMP does not contain authentication mechanism – The first 64 bits of data is not enough for authentication, and sometimes not enough information will be contained 22

• Attack 1: mapping network topology – This is an important part for following attacks. – Discover the live hosts for future scan or exploits – Can be accomplished by ping – Can send ICMP echo request to broadcast address – Can send ICMP subnet mask request to better determine the subnet 23

• Smurf attack (attack 2) – Ping a broadcast address with a spoofed IP. That node will become a victim – All hosts respond to the victim, and that node is overwhelmed – Keys: amplification and IP spoofing – Many implementations ignore ping to broadcast address these days – Similar attacks in TCP, UDP, etc 24

• Ping to death (attack 3) – ICMP echo with fragment – Maximum ICMP echo packet is 65535 – 20 (IP header) – 8 (ICMP echo header) – Fragmentation may bypass this requirement: offset + length > 65535 – Reassembled packet cannot be fit into buffer – OS may crash 25

• ICMP redirect attack (attack 4) – Ask a host to send the packet to the target “router”. – Useful for man-in-the-middle attack – Winfreeze • • Windows ICMP redirect: you are the quickest path to node Z Host changes the routing table entry for Z to itself Send packet to itself in an infinite loop 26

• Timestamp attack (attack 5) – Mess with the local clock of computer – Many random number generator depends on the local clock 27

Conclusions • You don’t need most of ICMP unless you need to troubleshoot your network • ICMP is very useful to attackers, rarely useful to legitimate users. –Except Path MTU discovery –e. g. , OS fingerprinting • Blocking ICMP by default in critical networks, and logging ICMP messages instead of acting upon them automatically, is safer

29

• UDP: User Datagram Protocol • Why we need UDP or TCP – IP provides a channel b/w two machines – There might be multiple applications on a machine expecting data – IP only identifies host, not applications – Using process number or handle will not serve the purpose – We need another thing to distinguish the applications 30

• TCP and UDP use protocol port number. Applications bind them to port numbers • Some port numbers are reserved or well known ones. While the others are free to assign or use 31

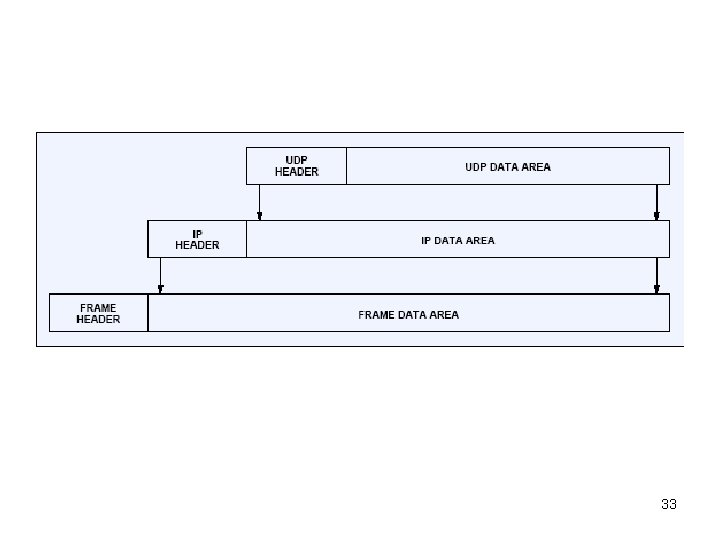
• UDP (User Datagram Protocol) – Transport layer protocol – Connectionless service – Best-effort delivery as IP • Packets can be delayed, lost, or duplicated • Packets can arrive out of order – Applications accepts full responsibility for errors – UDP based applications • • DNS: DNS server queries Streaming video, Vo. IP Games SNMP, DHCP, RIP 32

33

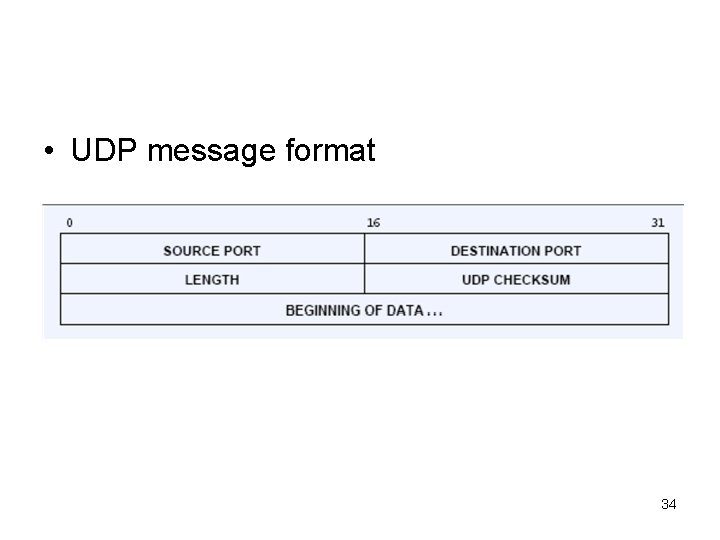
• UDP message format 34

• Both source and destination ports have 16 bits (65536). The port number below 1024 are usually reserved. • The “length” contains the count of byte in UDP packet, including UDP header and the user data. The minimum length is 8 byte. 35

• Checksum – The checksum field is optional. – IP header checksum does not cover the data part. So a checksum at higher layer is good. – What if the computed checksum is zero? How can we tell the difference? – Checksum (pseudo header, UDP header, user data) 36

• UDP pseudo header – The UDP checksum also covers a pseudo header – Pseudo header is not transmitted or counted in the length – Why we need a pseudo header • Make sure it is the correct destination • Consists of an IP and a port number • Real UDP header does not contain IP address 37

• UDP pseudo header – Contain 12 bytes – Source IP (4), destination IP (4), padding (1), protocol (1 byte with value of 17), and UDP length (2 byte, not include the pseudo header) 38

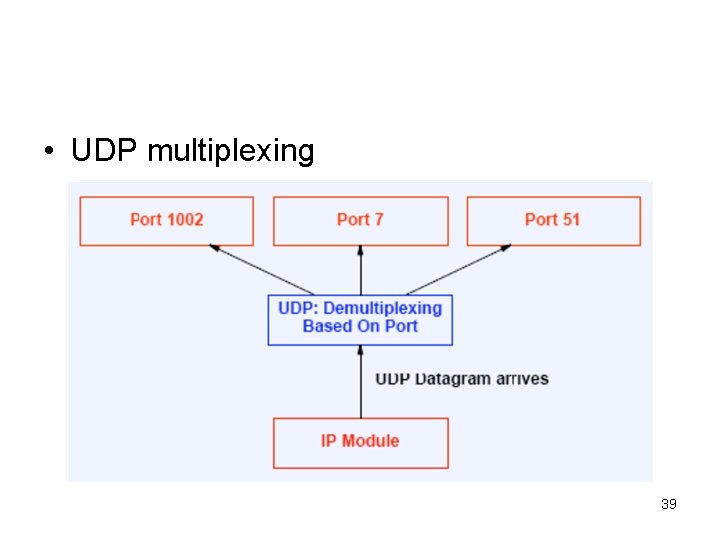
• UDP multiplexing 39

• UDP ports – Small numbers are reserved for special purposes • Called well-known ports • Same interpretation across the Internet • Used by server software – Large numbers are not reserved 40

• UDP ports – – – – – 7: echo 13: daytime 42: name-server (name) 53: Domain (DNS) 67: BOOTP server 68: BOOTP client 69: TFTP 111: SUN RPC 123: NTP (network time protocol) 41

42

• UDP attacks – Attack on echo service (Fraggle) • • Broadcast UDP packet to “echo” service All computers reply (amplification) Source IP was spoofed, victim overwhelmed Similar to ICMP smurf attack 43

• UDP Ping-Pong – Some service will issue a UDP reply no matter what is the input packet – Set the source and destination ports of a UDP packet to be one of the following ports • 13: daytime • 37: time – Will cause a ping-pong effect b/w the source and destination 44

• Do. S attack – Small request causes large packet reply (games) • Battlefield 1942 • Quake 1 • Unreal Tournament – Hosts can be attacked by using these applications as amplifiers, with forged IP address 45

46

• TCP: Transmission Control Protocol – The most loved and hated protocol – Various protocols have been developed to replaced it, but not work very well 47

• The need for stream delivery – Out of order – Packet delay – Packet loss – Packet duplicate 48

• TCP’s properties – Stream orientation • TCP thinks data as continuous flow of bits or bytes • The sequence of the sent and received data are exactly the same – Virtual circuit connection – Buffered transfer • Application can determine the size of the pieces of the information it wants to transfer • Protocol software will divide the information into packets • Usually use a packet with a reasonable size • Can use “push” option to force transfer without buffering 49

• Unstructured stream – TCP does not honor structured data stream – It is the application’s responsibility to understand the data structure • Full duplex connection: transfer in both directions (can close one direction while keeping the other active) • Reliability – Positive acknowledgement with retransmission 50

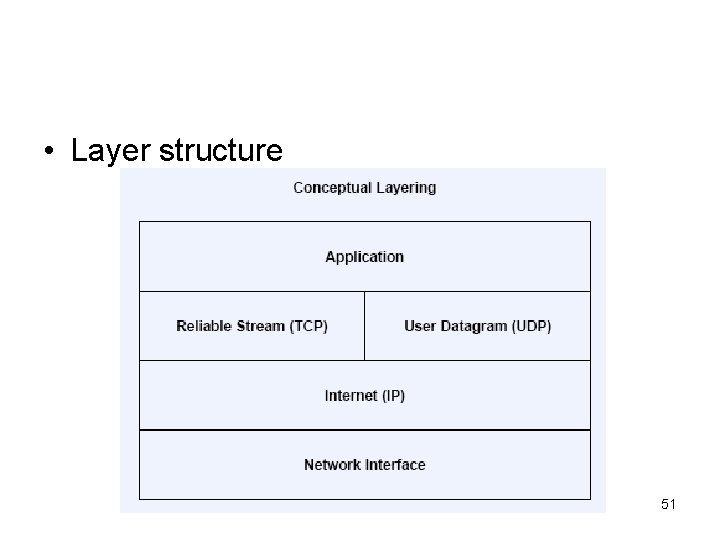
• Layer structure 51

• TCP ports – TCP uses ports to identify applications – A connection is identified by four items • Source IP and protocol port number • Destination IP and protocol port number – A given TCP port number can be shared by multiple connections on the same machine because they will have different source IP and port numbers 52

• Reserved TCP port number – Port number can be 0 to 65535 – 0 to 1024 are reserved for well known services • • 7: echo 13: Daytime 21: FTP 22: SSH 23: TELNET 25: SMTP 79: Finger 80: HTTP 53

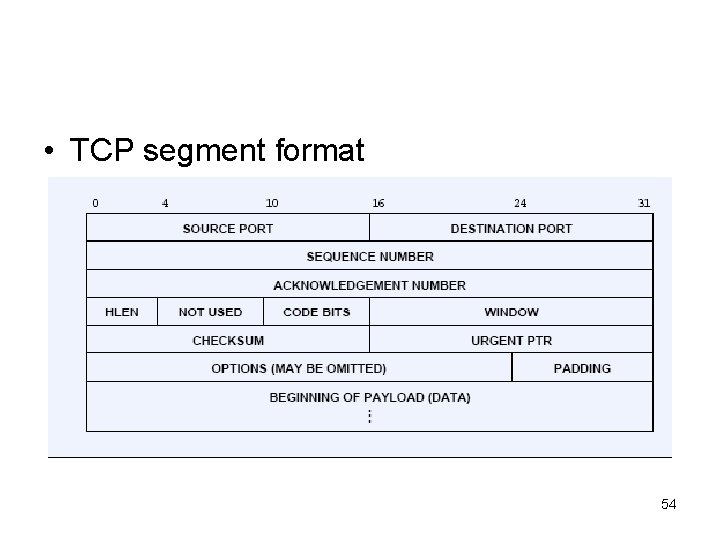
• TCP segment format 54

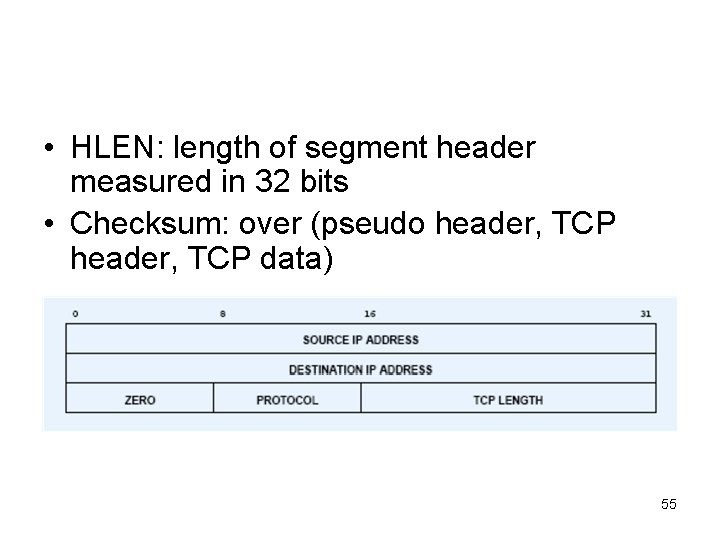
• HLEN: length of segment header measured in 32 bits • Checksum: over (pseudo header, TCP data) 55