ITECH 1102 Networking and Security Topic 5 The






- Slides: 33

ITECH 1102 Networking and Security Topic 5 – The Internet (Network) layer

Last week we: • • • Investigated the Data Link layer Data Link sends and receives data from network media The Network Interface Card (NIC) is responsible for Media Access NICs have a globally unique 48 bit MAC address NICs filter traffic (only broadcast and station traffic are passed to the operating system) Data Link frames encapsulate all upper layer protocols (ULP) Broadcast addresses ( FF FF FF ) are processed by all computers. Two media access methods are CSMA/CD & CSMA/CA ARP (Address Resolution Protocol) is used to determine local MAC addresses (We will investigate this a bit more this week) Frame headers change after crossing a router ITECH 1102 Networking & Security 2

More about ARP (Address Resolution Protocol) Last week we introduced ARP determines the MAC address of a machine on the local network with a specific IP address. ARP sends a broadcast asking the question, Who has IP Address 192. 168. 123 (or other IP address) If the targeted machine responds, the MAC address is known and is entered in the ARP cache. ITECH 1102 Networking & Security 3

ARP commands (in Windows) To observe the ARP cache contents: arp –a To delete an entry: arp –d < ip address > Eg. arp –d 141. 132. 196. 22 To delete all arp entries: arp –d * Note – some entries will remain (router, multicasts etc. ) Some of these functions require administrative privilege and so will not work on lab machines. You can try this on your home machine if you like. Linux syntax is slightly different –a is not required to look at arp cache. ITECH 1102 Networking & Security 4

When are entries added and deleted. A successful ARP command will result in a new entry being added to the arp cache. This will be a new local MAC address/IP address pair. New entries are only added as the result of local traffic, packets to remote locations exit via the local router and so will not result in a new entry in the arp cache. ARP entries age out after a set period of time. (The time varies depending on the Operating System) ITECH 1102 Networking & Security 5

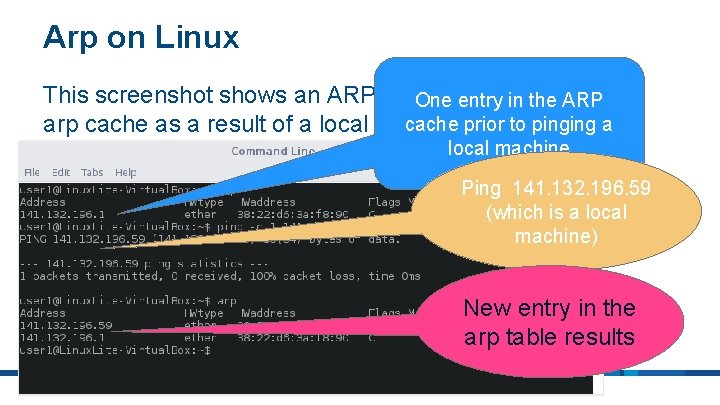
Arp on Linux This screenshot shows an ARP entry added to the Onebeing entry in the ARP cache prior to pinging a arp cache as a result of a local ping local machine Ping 141. 132. 196. 59 (which is a local machine) New entry in the arp table results ITECH 1102 Networking & Security 6

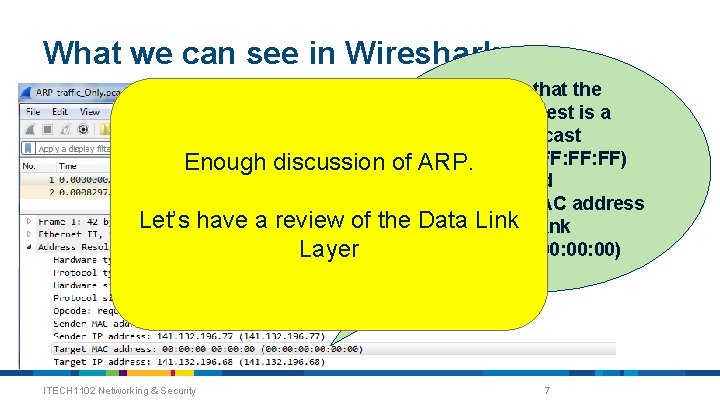
What we can see in Wireshark Enough discussion of Let’s have a review of the Layer ITECH 1102 Networking & Security Notice that the ARP request is a broadcast (FF: FF: FF: FF) ARP. and The target MAC address Data Link is blank (00: 00: 00: 00) 7

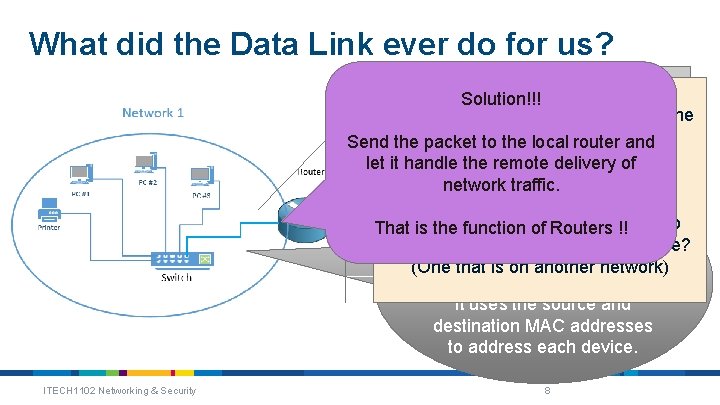
What did the Data Link ever do for us? The Router is also on this network. Solution!!! Therefore it can data also to communicate So we can deliver any machine withonany device on the local thethe local network. Send the packet to local router and network let it handle the remote delivery of Yippee network traffic. !!!!!! The problem Data Link implements The next solve is!!how to That is the function ofto. Routers communication between communicate with a remote machine? machines the (Oneany thattwo is on anotheron network) local network. It uses the source and destination MAC addresses to address each device. ITECH 1102 Networking & Security 8

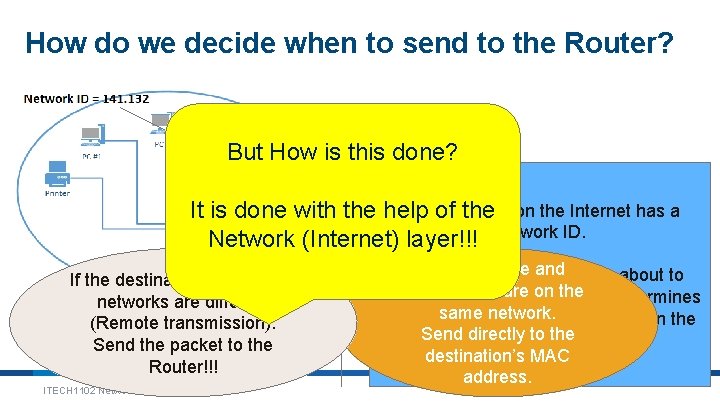
How do we decide when to send to the Router? But How is this done? Eachofnetwork It is done with the help the on the Internet has a Network (Internet) layer!!! network ID. If the destination and source networks are different (Remote transmission). Send the packet to the Router!!! ITECH 1102 Networking & Security the source and Each. If time your computer is about to on the senddestination a network are packet it first determines same and network. if the source destination are on the Send to thenetworks. samedirectly or different destination’s MAC address. 9

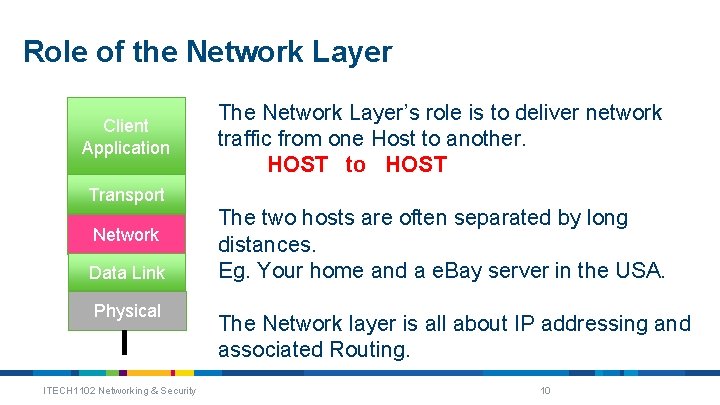
Role of the Network Layer Client Application The Network Layer’s role is to deliver network traffic from one Host to another. HOST to HOST Transport Network Data Link Physical ITECH 1102 Networking & Security The two hosts are often separated by long distances. Eg. Your home and a e. Bay server in the USA. The Network layer is all about IP addressing and associated Routing. 10

IP (Internet Protocol) addressing Each device on an IP network requires an IP address. There are two types of IP address: 1. IPv 4 address 2. IPv 6 address For now we will just consider IPv 4 addressing. The IP address of a machine must uniquely identify that machine from all others on the Internet. ITECH 1102 Networking & Security 11

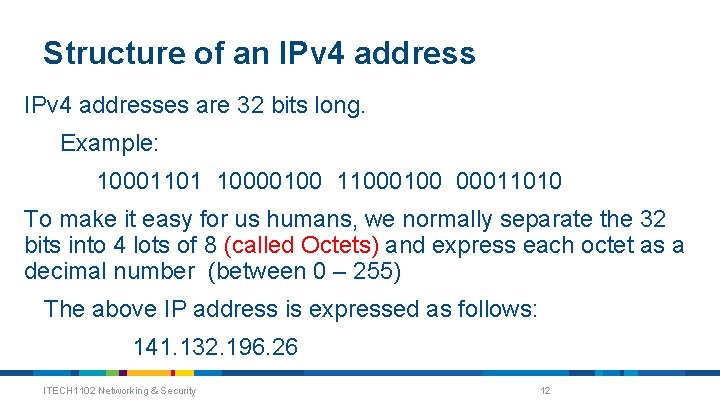
Structure of an IPv 4 addresses are 32 bits long. Example: 10001101 10000100 11000100 00011010 To make it easy for us humans, we normally separate the 32 bits into 4 lots of 8 (called Octets) and express each octet as a decimal number (between 0 – 255) The above IP address is expressed as follows: 141. 132. 196. 26 ITECH 1102 Networking & Security 12

How do computers get an IP address? The Operating System holds a machine’s IP address. It can be configured manually or automatically. Manual administration (static addressing) A user enters the IP settings into the machine’s OS. Automatic administration (dynamic addressing) A DHCP (Dynamic Host Configuration Protocol) server allocates IP settings to the machine. When the machine boots it sends a broadcast requesting IP settings. The networks local DHCP server responds with associated IP address, subnet mask and other settings. ITECH 1102 Networking & Security 13

Other important IP settings To communicate on an IP network a machine requires: 1. 2. 3. An IP address Local router’s address - Called Default Gateway on Windows - Called Default Router on Linux Subnet mask The 4 th setting which is not essential but particularly useful is the DNS (Domain Name System Server) IP address. DNS servers are responsible for converting IP addresses to names. (Example 172. 217. 26. 4 < --- > www. google. com) ITECH 1102 Networking & Security 14

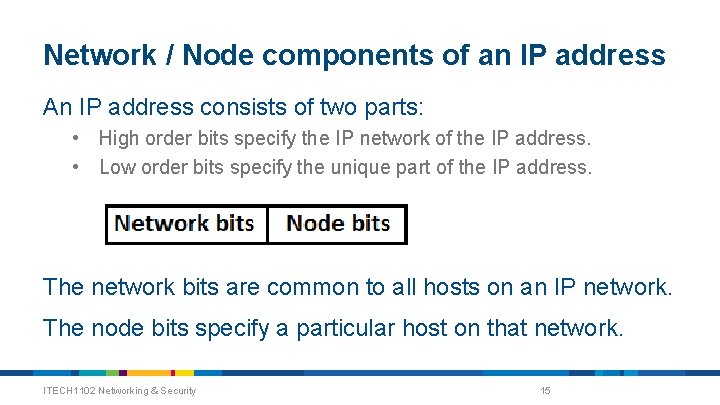
Network / Node components of an IP address An IP address consists of two parts: • High order bits specify the IP network of the IP address. • Low order bits specify the unique part of the IP address. The network bits are common to all hosts on an IP network. The node bits specify a particular host on that network. ITECH 1102 Networking & Security 15

Subnet mask A subnet mask applies to all machines (hosts) on an IP network. The format of a subnet masks is: • A series of binary 1 bits (indicating the network portion) followed by • A series of binary 0 bits (indicating the node portion) Hence a subnet mask tells us how many bits of an IP address is devoted to the network portion and how many to the node portion. ITECH 1102 Networking & Security 16

Determining the network address of an IP address. Two ways: If we replace all node bits of an IP address with zeros we get that IP addresses network address. If we do a bitwise AND of the IP address with the subnet mask we also get the IP addresses network address. ITECH 1102 Networking & Security 17

CIDR – Classless inter-Domain routing Another way to express the number of network bits of an IP address is to use CIDR notation. Example: 192. 168. 22. 56 /24 The number following the / is the number of network bits. The IP address above therefore has 24 bits devoted to its network address. It is equivalent to a subnet mask of 255. 0 ITECH 1102 Networking & Security 18

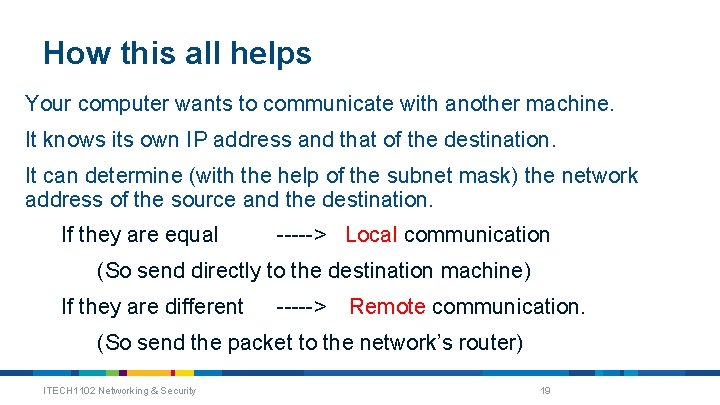
How this all helps Your computer wants to communicate with another machine. It knows its own IP address and that of the destination. It can determine (with the help of the subnet mask) the network address of the source and the destination. If they are equal -----> Local communication (So send directly to the destination machine) If they are different -----> Remote communication. (So send the packet to the network’s router) ITECH 1102 Networking & Security 19

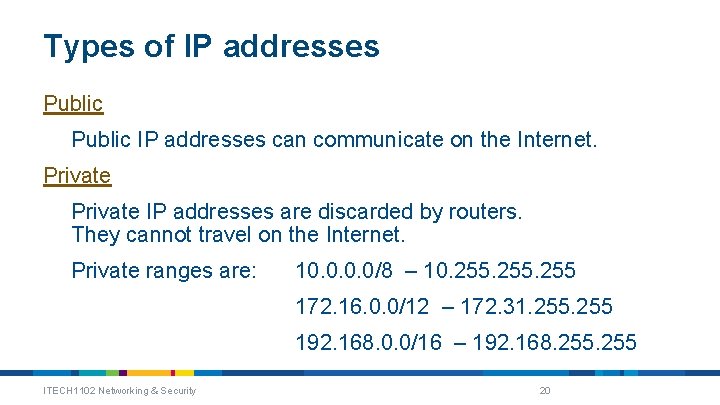
Types of IP addresses Public IP addresses can communicate on the Internet. Private IP addresses are discarded by routers. They cannot travel on the Internet. Private ranges are: 10. 0/8 – 10. 255 172. 16. 0. 0/12 – 172. 31. 255 192. 168. 0. 0/16 – 192. 168. 255 ITECH 1102 Networking & Security 20

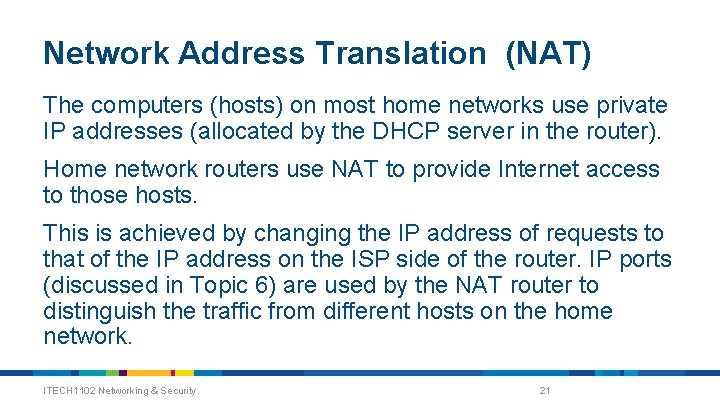
Network Address Translation (NAT) The computers (hosts) on most home networks use private IP addresses (allocated by the DHCP server in the router). Home network routers use NAT to provide Internet access to those hosts. This is achieved by changing the IP address of requests to that of the IP address on the ISP side of the router. IP ports (discussed in Topic 6) are used by the NAT router to distinguish the traffic from different hosts on the home network. ITECH 1102 Networking & Security 21

The role of routers!!! The path between your computer and a distance web or other server could be many router hops away. For example. Traffic from my office PC to www. google. com traverses 13 routers. The role of a router is to: Move a network packet forward 1 step towards its destination. Analogy Like a game of netball. The GD (goal defence) makes a decision as to the best player to pass the ball to and then does it. That player decides the next player to pass the ball to and does it. Etc. etc. Routers work in a similar fashion, moving packets forward 1 step at a time. The route can change from packet to packet. ITECH 1102 Networking & Security 22

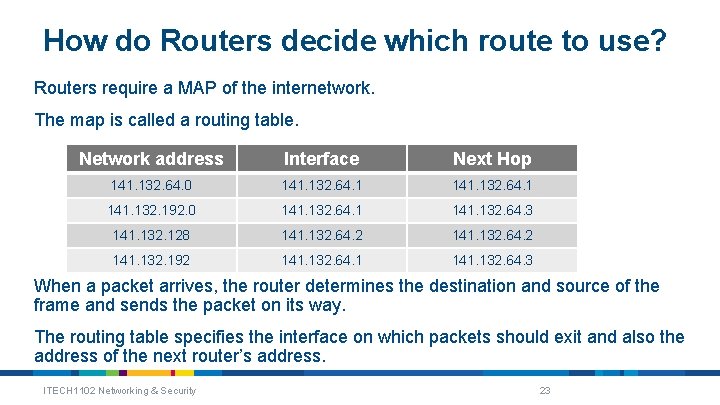
How do Routers decide which route to use? Routers require a MAP of the internetwork. The map is called a routing table. Network address Interface Next Hop 141. 132. 64. 0 141. 132. 64. 1 141. 132. 192. 0 141. 132. 64. 1 141. 132. 64. 3 141. 132. 128 141. 132. 64. 2 141. 132. 192 141. 132. 64. 1 141. 132. 64. 3 When a packet arrives, the router determines the destination and source of the frame and sends the packet on its way. The routing table specifies the interface on which packets should exit and also the address of the next router’s address. ITECH 1102 Networking & Security 23

What if the network configuration changes? Routers communicate with one another to ensue all routers know about network changes, for instance: • • • A router is offline A particular route is overloaded New routes added or removed Common Routing Protocols include: • OSPF (Open shortest Path First) [used on the Mt Helen campus network] • RIP (Routing Information Protocol) [older protocol mostly replaced by OSPF] • BGP (Border Gateway Protocol) [used on the Internet] Routing protocols update routing table entries as required. ITECH 1102 Networking & Security 24

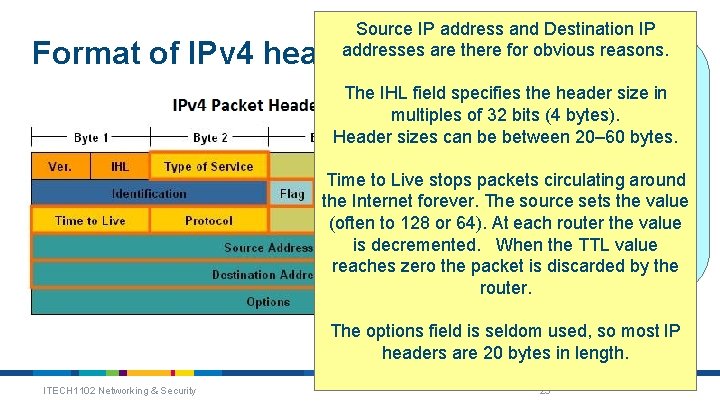
Source IP address and Destination IP addresses are there for obvious reasons. The information in the source IP header provides information The IHL field specifies the header size into routers and the(4 destination host multiples of 32 bits bytes). about the network packet. Header sizes can be between 20– 60 bytes. Important fields include: Sourcecirculating Address around Time to Live stops packets the Internet forever. Destination The sourceaddress sets the value (header size) [ 20 -60 bytes] (often to 128 IHL or 64). At each router the value Timethe to Live is decremented. When TTL value Header checksumby the reaches zero the packet is discarded router. Format of IPv 4 header The options field is seldom used, so most IP headers are 20 bytes in length. ITECH 1102 Networking & Security 25

Naming of Internet hosts Companies and organisations require a block of Public IP addresses to name their servers on the Internet. The block of addresses are associated with the organisations Domain Name. For example: Federation University’s Domain (federation. edu. au) has the IP range 141. 132. x. x allocated to it. (65536 IP addresses) The University’s address range was purchased many years ago. ITECH 1102 Networking & Security 26

Internet Assigned Numbers Authority (IANA) IANA is the overseeing body for the naming of Internet domains. IANA delegates naming for different geographical regions of the world to other naming authorities. For instance APNIC (Asia Pacific Network Information Centre) for the Asia Pacific region. ISP’s hold blocks of IP addresses and can allocate small IP ranges to their customers. Once an organisation has their domain name and associated IP addresses their server/s can be found on the Internet. ITECH 1102 Networking & Security 27

DNS (Domain Name System) Name resolution of Internet names is handled by DNS. Name resolution is the process of looking up the IP address of an Internet name, or for reverse lookups, determining the host name of a particular IP address. Resolution of names is handled by your local DNS server or that of your ISP’s DNS server. If the local DNS server cannot resolve a name, it requests the help of DNS servers that form part of the worldwide DNS server hierarchy. Name resolution is required each time you enter Internet names (eg. www. apple. com) into web browsers because IP addresses are required for network communication to take place. ITECH 1102 Networking & Security 28

IPv 6 (IP version 6) IPv 6 is the most recent version of the Internet Protocol. It was developed by the Internet Engineering Task Force (IETF) to deal with IPv 4 address exhaustion. In time IPv 6 is meant to replace IPv 4. Each IPv 6 address is 128 bits in length which gives IPv 6 an enormous addressing range. • 2128 possible different addresses • 3. 402 * 1038 • 4. 5 X 1015 addresses for every observable start in the universe. ITECH 1102 Networking & Security 29

We use Hexadecimal to express IPv 6 addresses Because IPv 6 addresses are so large we use hexadecimal to express them in 8 lots of 4. Example: FE 80: 0000: ACC 1: 44 F 9: 91 B 5: AC 1 B Most of the Internet only supports IPv 4 and so transitions mechanisms are required. The most important is tunnelling. ITECH 1102 Networking & Security 30

Tool Talk A closer look at IP settings on Windows and Linux • • Windows Linux command line: • • • cd ls. . . ~ notations Wireshark: • • • ARP (Local address resolution) DHCP DNS (name resolution) Capture filters Display filters ------- Demonstration ------- ITECH 1102 Networking & Security 31

Next Week The Transport layer: • TCP • • • Virtual Circuits 3 way handshake Sequence numbers and acknowledgements • UDP ITECH 1102 Networking & Security 32

Commonwealth of Australia Copyright Act 1968 Notice for paragraph 135 ZXA (a) of the Copyright Act 1968 Warning This material has been reproduced and communicated to you by or on behalf of Federation University Australia under Part VB of the Copyright Act 1968 (the Act). The material in this communication may be subject to copyright under the Act. Any further reproduction or communication of this material by you may be the subject of copyright protection under the Act. Do not remove this notice.