IT SYSTEM CONTROL AND AUDIT TYPES OF AUDITING









































- Slides: 58

IT SYSTEM CONTROL AND AUDIT TYPES OF AUDITING METHODS MANAGEMENT AUDITS OF IT IN AN ORGANIZATION PRESENTERS JBIMS q q q SUJIT SHETTY [150] KUNAL WAKCHAURE [158] ROHAN GHONGE [162] VISHAL DESHMUKH [112] SANDEEP NAIR [130] PRAVIN JAISWAL [118]

INTRODUCTION TO AUDITING Systematic process that finds and assesses evidence regarding the performance of a process/project/systems/products • Errors, efficiency and compliance with regulation • Funds • Qualified Professional • IS Audit - Automated information systems IT SYSTEM CONTROL AND AUDIT JBIMS

TYPES OF AUDIT - GENERAL Financial - On all processes that deal with monetary transactions of an organization - Check and improve accuracy of financial statements - Correct and eliminate material misstatements found in records Operational - Increase efficiency and reduce waste - The company's internal systems and procedures are tested for efficiency and effectiveness - Inefficient use of resources or capital are located and suggestions for improvement are made Compliance - Regulatory guidelines, whether internally-developed or government imposed - Ensure information technology security policies are effective and being enforced - Checks how secure critical systems are Statutory - Evaluate whether the organization is providing a fair and accurate representation of its financial position - Legally required audit is performed by an external auditor IT SYSTEM CONTROL AND AUDIT JBIMS

TYPES OF AUDIT - GENERAL Internal - Performed by auditors who are employed by the organization, but operate independently from other departments - Consider risks facing the organization and what is being done to manage those risks - Help the organization achieve its business objectives External - Performed by an independent body - Often ordered by shareholders - Helps potential investors as well as current investors IT SYSTEM CONTROL AND AUDIT JBIMS

IT AUDIT v. Examination and evaluation of an organization's information technology infrastructure, policies and operations v. Determine whether IT controls protect corporate assets, ensure data integrity and are aligned with the business's overall goals v Also known as “Automated Data Processing (ADP) audits" IT SYSTEM CONTROL AND AUDIT JBIMS

OBJECTIVES OF IT AUDIT ØEvaluate the systems and processes in place that secure company data ØDetermine risks to a company's information assets, and help identify methods to minimize those risks ØEnsure information management processes are in compliance with IT- specific laws, policies and standards ØDetermine inefficiencies in IT systems and associated management ØCheck availability, security, integrity of companies valuable asset i. e Information IT SYSTEM CONTROL AND AUDIT JBIMS

SPECTRUM OF IT AUDITS v. Systems and Applications Audit v. Information Processing Facilities Audit v. Systems Development Audit v. Management of IT and Enterprise Architecture v. Client/Server, Telecommunications, Intranets, and Extranets IT SYSTEM CONTROL AND AUDIT JBIMS

INFORMATION SECURITY AUDITS v. Internal & External v. Considers all the potential hazards and controls in information systems v. IT General Controls v. Application Controls : Input , Processing , Output , Integrity & Management trail v. Application controls are specific to application but general controls are common across all IT SYSTEM CONTROL AND AUDIT JBIMS

PHASES OF INFORMATION SYSTEM AUDIT METHODOLOGY üAUDIT PLANNING üRISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS üPERFORMANCE OF AUDIT WORK üREPORTING IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 1 AUDIT PLANNING • In this phase we plan the information system coverage to comply with the audit objectives specified by the Client and ensure compliance to all Laws and Professional Standards. • Authority and accountability of the Information Systems Audit function as follows: üResponsibility üAuthority üAccountability • The Audit Charter should be approved and agreed upon by an appropriate level within the Client’s Organization. IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 1 AUDIT PLANNING • In addition to the Audit Charter, we should be able to obtain a written representation (“Letter of Representation”) from the Client’s Management acknowledging: üTheir responsibility for the design and implementation of the Internal Control Systems affecting the IT Systems and processes üTheir willingness to disclose to the Information Systems Auditor their knowledge of irregularities and/or illegal acts affecting their organization pertaining to management and employees with significant roles within the internal audit department. üTheir willingness to disclose to the IS Auditor the results of any risk assessment that a material misstatement may have occurred IT SYSTEM CONTROL AND AUDIT JBIMS

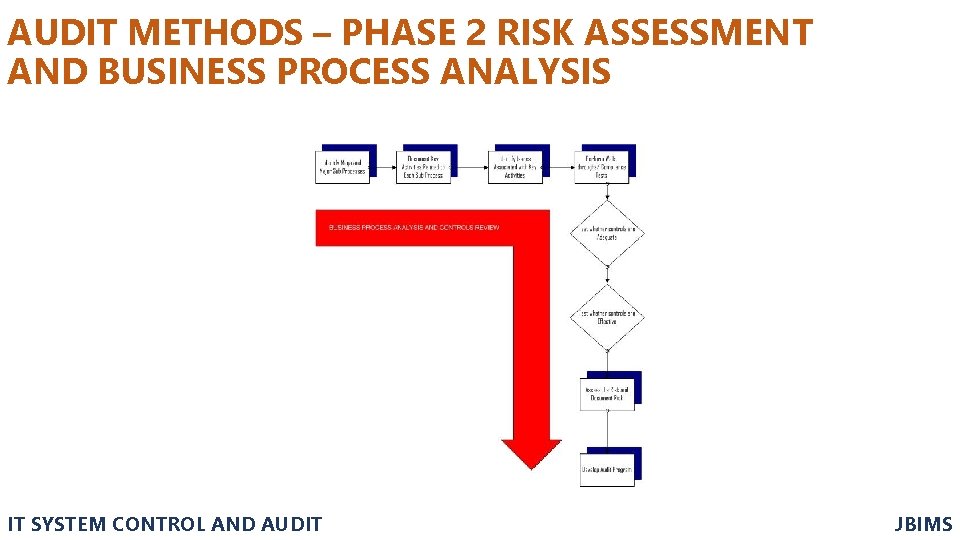
AUDIT METHODS – PHASE 2 RISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS • Risk is the possibility of an act or event occurring that would have an adverse effect on the organization and its information systems. Risk can also be the potential that a given threat will exploit vulnerabilities of an asset or group of assets to cause loss of, or damage to, the assets. It is ordinarily measured by a combination of effect and likelihood of occurrence. • More and more organizations are moving to a risk-based audit approach that can be adapted to develop and improve the continuous audit process. This approach is used to assess risk and to assist an IS auditor’s decision to do either compliance testing or substantive testing. IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 2 RISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS • The process of quantifying risk is called Risk Assessment is useful in making decisions such as: üThe area/business function to be audited üThe nature, extent and timing of audit procedures üThe amount of resources to be allocated to an audit • The following types of risks should be considered: üInherent risk üControl risk üDetection risk IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 2 RISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS • Inherent Risk: Inherent risk is the susceptibility of an audit area to error which could be material, individually or in combination with other errors, assuming that there were no related internal controls. In assessing the inherent risk, the IS auditor should consider both pervasive and detailed IS controls. • Some of the pervasive IS Controls that an auditor may consider include: ü The integrity of IS management and IS management experience and knowledge ü Changes in IS management ü Pressures on IS management which may predispose them to conceal or misstate information (e. g. large business-critical project over-runs, and hacker activity) ü The nature of the organization's business and systems (e. g. , the plans for electronic commerce, the complexity of the systems, and the lack of integrated systems) ü Factors affecting the organization's industry as a whole (e. g. , changes in technology, and IS staff availability) ü The level of third party influence on the control of the systems being audited (e. g. , because of supply chain integration, outsourced IS processes, joint business ventures, and direct access by customers) ü Findings from and date of previous audits IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 2 RISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS • Control Risk: Control risk is the risk that an error which could occur in an audit area, and which could be material, individually or in combination with other errors, will not be prevented or detected and corrected on a timely basis by the internal control system. For example, the control risk associated with manual reviews of computer logs can be high because activities requiring investigation are often easily missed owing to the volume of logged information. • The IS auditor should assess the control risk as high unless relevant internal controls are: üIdentified üEvaluated as effective üTested and proved to be operating appropriately IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 2 RISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS • Detection Risk: Detection risk is the risk that the IS auditor’s substantive procedures will not detect an error which could be material, individually or in combination with other errors. • In determining the level of substantive testing required, the IS auditor should consider the following: üThe assessment of inherent risk üThe conclusion reached on control risk following compliance testing IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 2 RISK ASSESSMENT AND BUSINESS PROCESS ANALYSIS IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 3 PERFROMANCE OF AUDIT WORK In the performance of Audit Work the Information Systems Audit Standards require us to provide supervision, gather audit evidence and document our audit work. We achieve this objective through: ü Establishing an Internal Review Process where the work of one person is reviewed by another, preferably a more senior person. ü We obtain sufficient, reliable and relevant evidence to be obtained through Inspection, Observation, Inquiry, Confirmation and re-computation of calculations ü We document our work by describing audit work done and audit evidence gathered to support the auditors’ findings. IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 3 PERFROMANCE OF AUDIT WORK contd. . USE OF COMPUTER AIDED AUDIT TECHNIQUES (CAATS) IN THE PERFORMANCE OF AN IS AUDIT CAATs may be used in performing various audit procedures including: ü Tests of details of transactions and balances(Substantive Tests) ü Analytical review procedures ü Compliance tests of IS general controls ü Compliance tests of IS application controls IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 3 PERFROMANCE OF AUDIT WORK contd. . MAJOR STEPS TO BE UNDERTAKEN BY THE IS AUDITOR IN PREPARING FOR THE APPLICATION OF THE SELECTED CAATS ARE: ü Set the audit objectives of the CAATs ü Determine the accessibility and availability of the organisation’s IS facilities, programs/system and data ü Define the procedures to be undertaken (e. g. , statistical sampling, recalculation, confirmation, etc. ) ü Define output requirements ü Determine resource requirements, i. e. , personnel, CAATs, processing environment (organisation’s IS facilities or audit IS facilities) IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 3 PERFROMANCE OF AUDIT WORK contd. . ü Obtain access to the clients' IS facilities, programs/system, and data, including file definitions ü Document CAATs to be used, including objectives, high-level flowcharts, and run instructions ü Make appropriate arrangements with the Auditee and ensure that: ü Data files, such as detailed transaction files are retained and made available before the onset of the audit. ü You have obtained sufficient rights to the client’s IS facilities, programs/ system, and data ü Tests have been properly scheduled to minimise the effect on the organisation’s production environment. ü The effect that changes to the production programs/system have been properly considered. IT SYSTEM CONTROL AND AUDIT JBIMS

AUDIT METHODS – PHASE 4 REPORTING Upon the performance of the audit test, the Information Systems Auditor is required to produce and appropriate report communicating the results of the IS Audit. An IS Audit report should: ü Identify an organization, intended recipients and any restrictions on circulation ü State the scope, objectives, period of coverage, nature, timing and the extend of the audit work ü State findings, conclusions, recommendations and any reservations, qualifications and limitations ü Provide audit evidence IT SYSTEM CONTROL AND AUDIT JBIMS

Management Audit IT SYSTEM CONTROL AND AUDIT JBIMS

Meaning And Definition Management Audit is an assessment of methods and policies of an organization's management in the administration and the use of resources, tactical and strategic planning, and employee and organizational improvement. IT SYSTEM CONTROL AND AUDIT JBIMS

Objectives of Management Audit Ø IT audit is important because it gives assurance that the IT systems are adequately protected, provide reliable information to users and properly managed to achieve their intended benefits. Ø Many users rely on IT without knowing how the computers work. A computer error could be repeated indefinitely, causing more extensive damage than a human mistake. Ø IT audit could also help to reduce risks of data tampering, data loss or leakage, service disruption, and poor management of IT systems. IT SYSTEM CONTROL AND AUDIT JBIMS

Importance of Management Audit Ø Management functions and processes in order to improves its efficiency. Ø The success or failure of business or company depends fully on the quality of management. Ø The management audit is necessary to find out the best method of improving efficiency. Ø Each company wants to minimize the cost of production by eliminating wastage and utilizing full manpower to make in the competitive business world. Ø Management audit assists the foreign collaborators to asses the progress and performance of the management of the concern with which collaboration has been undertaken. IT SYSTEM CONTROL AND AUDIT JBIMS

Advantages of Management Audit Management audit provides information about strong and weak point of the management after reviewing policies and programs. So, it helps to the smooth operation of an organization. Management audit provides suggestions to the management which helps to maintain effective management. Management audit helps the management providing suggestions to attain goal of an organization. IT SYSTEM CONTROL AND AUDIT JBIMS

Information Technology Audit An information technology audit, or information systems audit, is an examination of the management controls within an Information technology (IT) infrastructure. The evaluation of obtained evidence determines if the information systems are safeguarding assets, maintaining data integrity, and operating effectively to achieve the organization's goals or objectives. These reviews may be performed in conjunction with a financial statement audit, internal audit, or other form of attestation engagement. IT SYSTEM CONTROL AND AUDIT JBIMS

Information Technology Audit Process IT SYSTEM CONTROL AND AUDIT JBIMS

Overview • IT Audit Process • Common IT Audit Observations • So What Should We Do IT SYSTEM CONTROL AND AUDIT JBIMS

IT Audit Process IT SYSTEM CONTROL AND AUDIT JBIMS

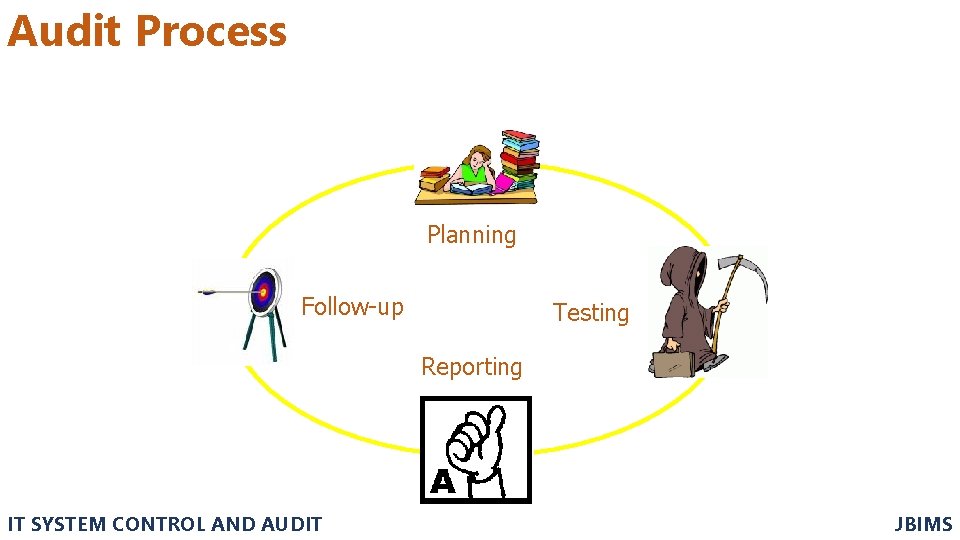
Audit Process Planning Follow-up Testing Reporting IT SYSTEM CONTROL AND AUDIT JBIMS

Planning • Periodic Risk Assessment • Preliminary Audit Plan • Board of Directors Approval • Notification and Request for Information • Understand Your Risks and Controls • Opening Conference IT SYSTEM CONTROL AND AUDIT JBIMS

Testing • Security • Backup & Recovery • Resource Management • Web Site IT SYSTEM CONTROL AND AUDIT JBIMS

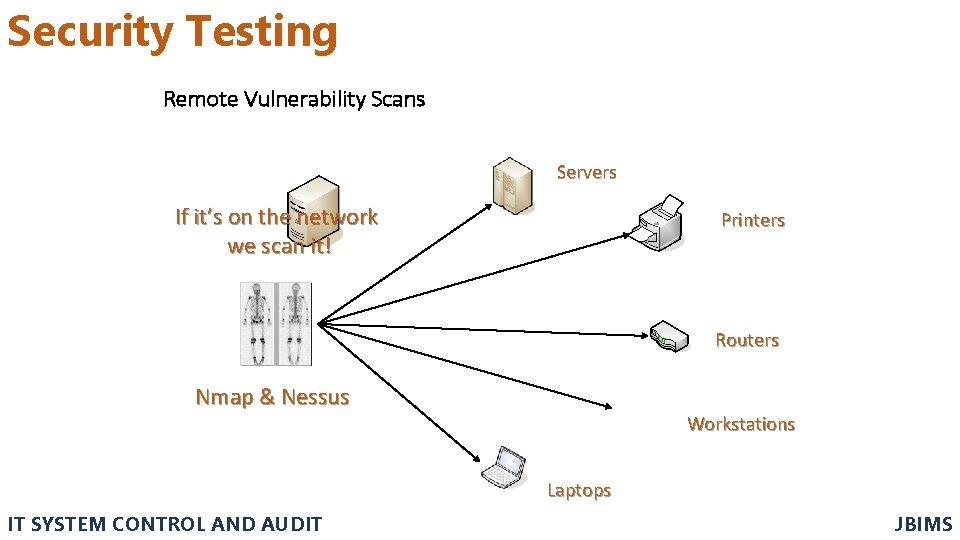
Security Testing Remote Vulnerability Scans Servers If it’s on the network we scan it! Printers Routers Nmap & Nessus Workstations Laptops IT SYSTEM CONTROL AND AUDIT JBIMS

Backup & Recovery Testing You Must Have Effective Controls to Backup & Recover “Critical Data” IT SYSTEM CONTROL AND AUDIT JBIMS

Resource Management Testing Computer Hardware & Software Procurement through Surplus IT SYSTEM CONTROL AND AUDIT JBIMS

Web Site Testing • University Relations Web Guidelines & Procedures • Web Development Best Practices • Content Recommendations • Templates • Privacy Statement (Policy 7030) • Web Server & Application Security IT SYSTEM CONTROL AND AUDIT JBIMS

Reporting Observations When Unexpected Results are Noted We Solicit Your Comments IT SYSTEM CONTROL AND AUDIT JBIMS

Reporting Recommendations We May Recommend Opportunities To Improve Your Controls IT SYSTEM CONTROL AND AUDIT JBIMS

Reporting Management Action Plans You Develop Plans, Schedules, and Priorities To Implement Solutions IT SYSTEM CONTROL AND AUDIT JBIMS

Reporting A Final Report is Sent to The Board of Directors IT SYSTEM CONTROL AND AUDIT JBIMS

Follow-Up • Follow-Up Actions are Based on Your “Management Action Plan” • Progress is Monitored • Some Re-Testing May be Necessary • Board of Directors is Updated • Audit is closed IT SYSTEM CONTROL AND AUDIT JBIMS

Common Audit Observations Weak Security Settings Windows Operating System IT SYSTEM CONTROL AND AUDIT JBIMS

Common Audit Observations Missing Security Patches Operating Systems Applications Databases IT SYSTEM CONTROL AND AUDIT JBIMS

Common Audit Observations Misconfigured Anti-Malware Tools Out-of-Date Threat Signatures Scans Not Scheduled IT SYSTEM CONTROL AND AUDIT JBIMS

Common Audit Observations Inadequate Access Controls Weak Passwords & File Permissions IT SYSTEM CONTROL AND AUDIT JBIMS

Common Audit Observations Open Communication Ports The Hacker’s Point of Entry IT SYSTEM CONTROL AND AUDIT JBIMS

Common Audit Observations “The System Administrator’s Dilemma” Convenience Security How Much Risk is Senior Management Willing to Accept? IT SYSTEM CONTROL AND AUDIT JBIMS

So What Should We Do? • Harden Security Settings • Keep Everything Patched • Install and Use Anti-Malware Tools • Enforce Strong Passwords • Close or Filter Communication Ports • Test Your Systems • Support Your System Administrator! IT SYSTEM CONTROL AND AUDIT JBIMS

Scope Following types of Audits are conducted for projects : • Project initiating Audit • Process Audit • Work-Product Audit • Closure Audit • Configuration Management Audit IT SYSTEM CONTROL AND AUDIT JBIMS

Process Practitioner • IQAT • Facilitator – For Project – Objective – Entry 1. Criteria 2. Input 3. Work Flow IT SYSTEM CONTROL AND AUDIT JBIMS

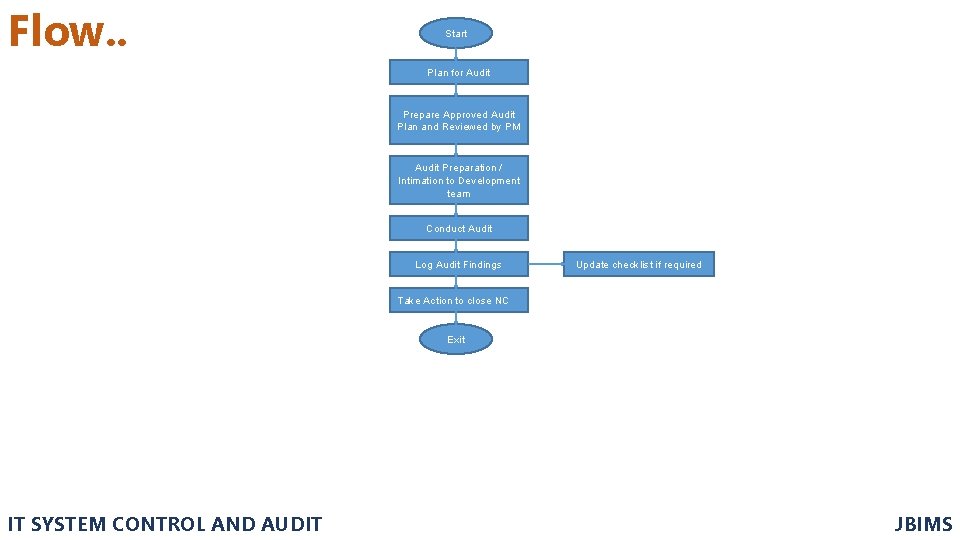
Flow. . Start Plan for Audit Prepare Approved Audit Plan and Reviewed by PM Audit Preparation / Intimation to Development team Conduct Audit Log Audit Findings Update checklist if required Take Action to close NC Exit IT SYSTEM CONTROL AND AUDIT JBIMS

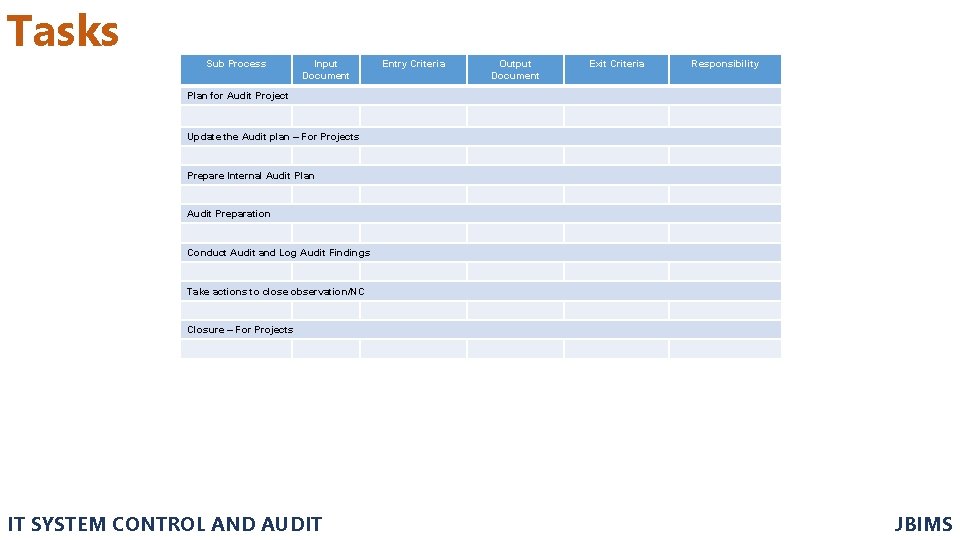
Tasks Sub Process Input Document Entry Criteria Output Document Exit Criteria Responsibility Plan for Audit Project Update the Audit plan – For Projects Prepare Internal Audit Plan Audit Preparation Conduct Audit and Log Audit Findings Take actions to close observation/NC Closure – For Projects IT SYSTEM CONTROL AND AUDIT JBIMS

Guidelines • Following are guidelines for Auditors: • Project initiation Audit • Work product Audit(For Project / CCF) • Process Audit • Project Closure Audit • Configuration Management Audit • A Good Audit Report has to be : • Complete • Accurate • Concise • Effective • Appropriate IT SYSTEM CONTROL AND AUDIT JBIMS

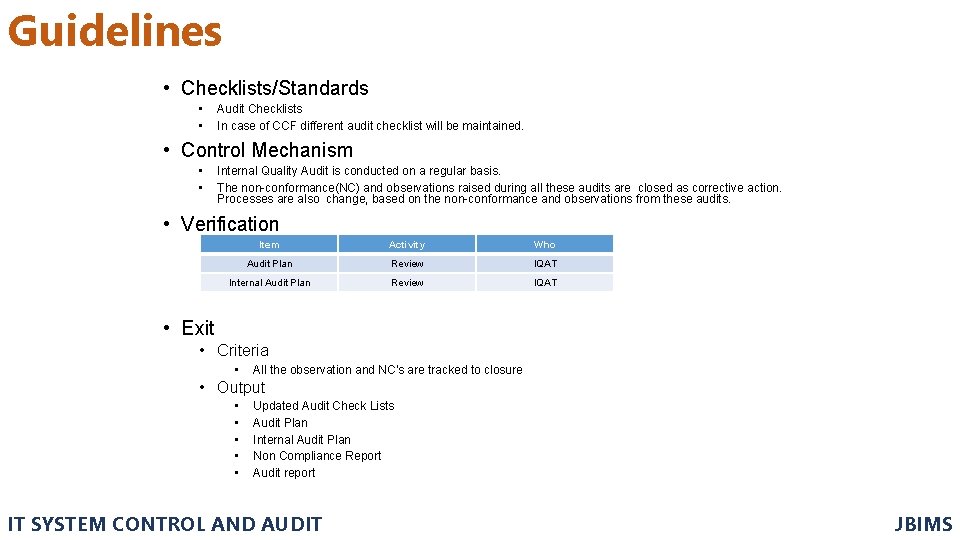
Guidelines • Checklists/Standards • • Audit Checklists In case of CCF different audit checklist will be maintained. • Control Mechanism • • Internal Quality Audit is conducted on a regular basis. The non-conformance(NC) and observations raised during all these audits are closed as corrective action. Processes are also change, based on the non-conformance and observations from these audits. • Verification Item Activity Who Audit Plan Review IQAT Internal Audit Plan Review IQAT • Exit • Criteria • All the observation and NC's are tracked to closure • Output • • • Updated Audit Check Lists Audit Plan Internal Audit Plan Non Compliance Report Audit report IT SYSTEM CONTROL AND AUDIT JBIMS

Live Examples • Document Template • Example 1 • Example 2 Audit_checklist. xls IT SYSTEM CONTROL AND AUDIT Audit Observations_DS_31 Mar 2015 V 1. 1_. xls JBIMS

Thank You