IT Management Frameworks An Overview of ISO 27001






- Slides: 13

IT Management Frameworks An Overview of ISO 27001: 2005 Massachusetts Digital Government Summit October 19, 2009

Speaker Curt Dalton, CISSP, CISM, ISMS Lead Auditor/Implementer Commonwealth ITD Security Office, Program Manager of the Enterprise Security Plan: – – EO 504 Adoption ISO 27001 Adoption IT Security Governance Security Architecture Improvements October 19, 2009 2

ISO 27001: 2005 Topics • • What is ISO 27001: 2005? What are its Components? What are its Origins & Purpose? How is it Implemented? Steps to Certification (optional) Summary Statement Contact Information October 19, 2009 3

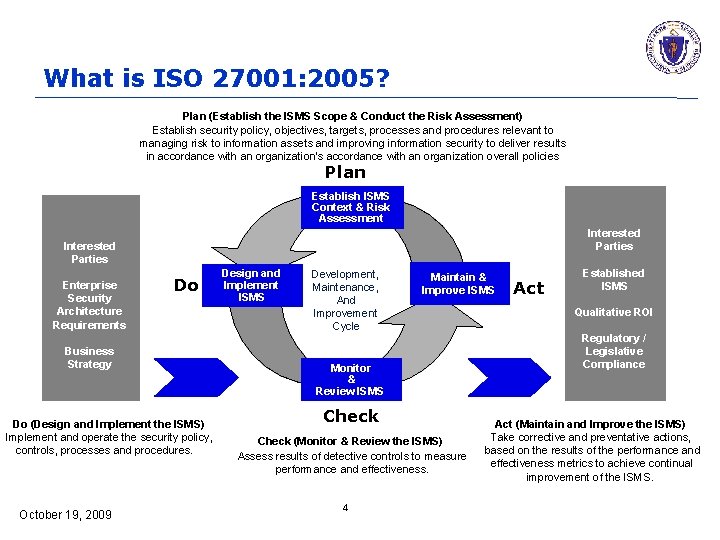
What is ISO 27001: 2005? Plan (Establish the ISMS Scope & Conduct the Risk Assessment) Establish security policy, objectives, targets, processes and procedures relevant to managing risk to information assets and improving information security to deliver results in accordance with an organization’s accordance with an organization overall policies Plan Establish ISMS Context & Risk Assessment Interested Parties Enterprise Security Architecture Requirements Do Business Strategy Do (Design and Implement the ISMS) Implement and operate the security policy, controls, processes and procedures. October 19, 2009 Design and Implement ISMS Development, Maintenance, And Improvement Cycle Maintain & Improve ISMS Monitor & Review ISMS Check (Monitor & Review the ISMS) Assess results of detective controls to measure performance and effectiveness. 4 Act Established ISMS Qualitative ROI Regulatory / Legislative Compliance Act (Maintain and Improve the ISMS) Take corrective and preventative actions, based on the results of the performance and effectiveness metrics to achieve continual improvement of the ISMS.

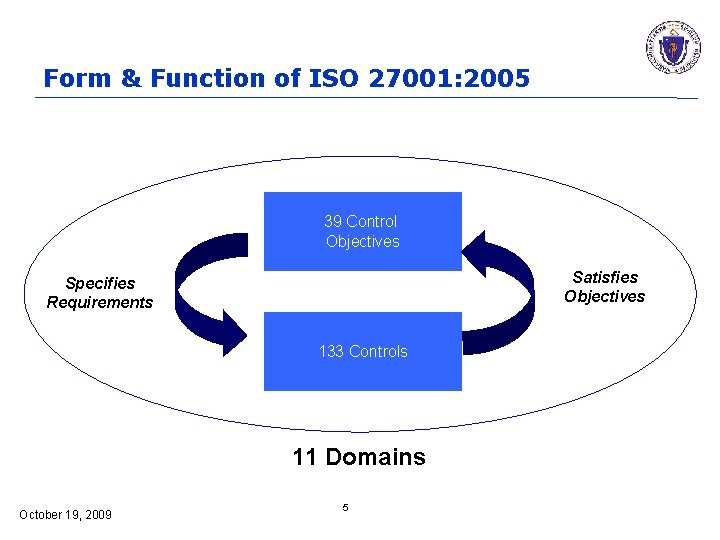
Form & Function of ISO 27001: 2005 39 Control Objectives Satisfies Objectives Specifies Requirements 133 Controls 11 Domains October 19, 2009 5

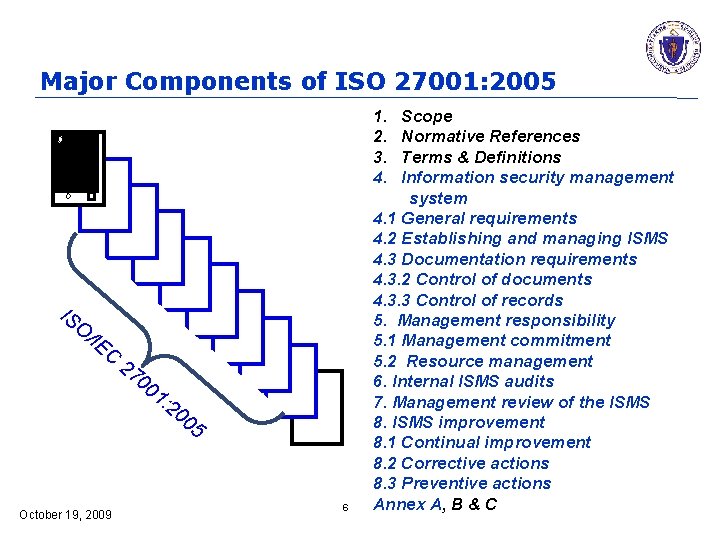
Major Components of ISO 27001: 2005 1. 2. 3. 4. IS O /IE C 27 00 October 19, 2009 1: 20 0 5 6 Scope Normative References Terms & Definitions Information security management system 4. 1 General requirements 4. 2 Establishing and managing ISMS 4. 3 Documentation requirements 4. 3. 2 Control of documents 4. 3. 3 Control of records 5. Management responsibility 5. 1 Management commitment 5. 2 Resource management 6. Internal ISMS audits 7. Management review of the ISMS 8. ISMS improvement 8. 1 Continual improvement 8. 2 Corrective actions 8. 3 Preventive actions Annex A, B & C

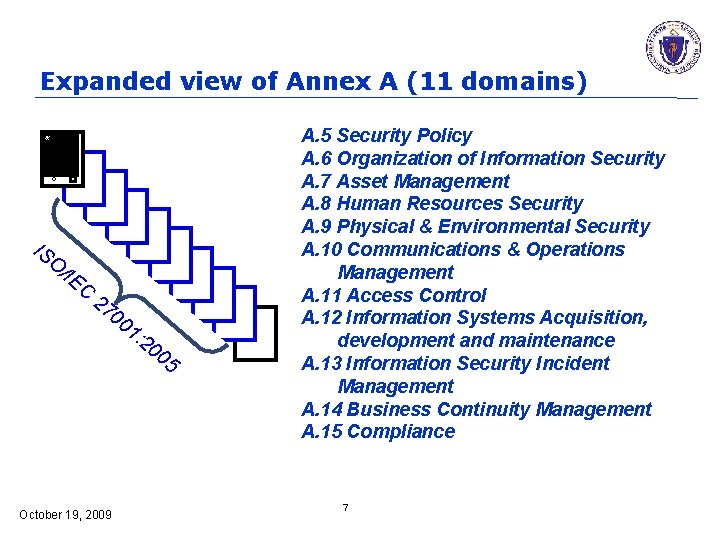
Expanded view of Annex A (11 domains) IS O /IE C 27 00 1: 20 05 October 19, 2009 A. 5 Security Policy A. 6 Organization of Information Security A. 7 Asset Management A. 8 Human Resources Security A. 9 Physical & Environmental Security A. 10 Communications & Operations Management A. 11 Access Control A. 12 Information Systems Acquisition, development and maintenance A. 13 Information Security Incident Management A. 14 Business Continuity Management A. 15 Compliance 7

Origins of the 27001: 2005 Standard Provides a framework for a risk based security management system that can be independently certified ISO/IEC 27001: 2005 (circa 2005)ISO Derived from BS 7799 (circa 1999). Defines security requirements for certification to the Standard. ISO/IEC 27002: 2005 (formerly ISO 17799) A Code of practice for information security management with implementation advice. Provides comprehensive implementation advice on the 133 security controls found in ISO/IEC 27001: 2005 October 19, 2009 8

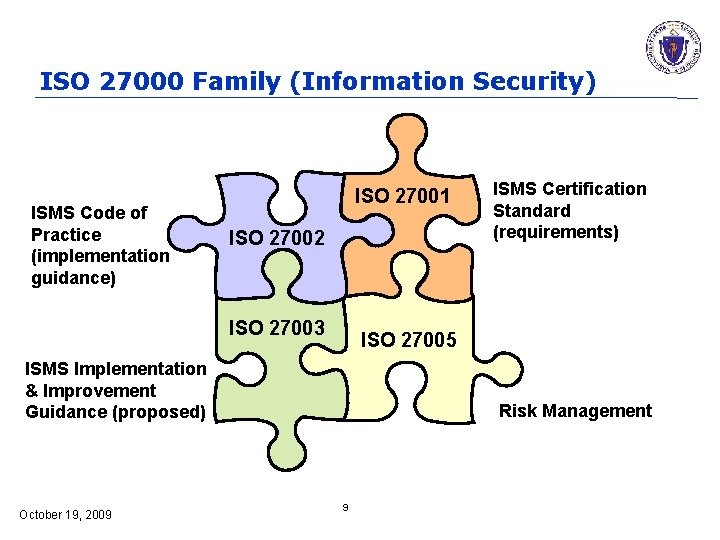
ISO 27000 Family (Information Security) ISMS Code of Practice (implementation guidance) ISO 27001 ISO 27002 ISO 27003 ISO 27005 ISMS Implementation & Improvement Guidance (proposed) October 19, 2009 ISMS Certification Standard (requirements) Risk Management 9

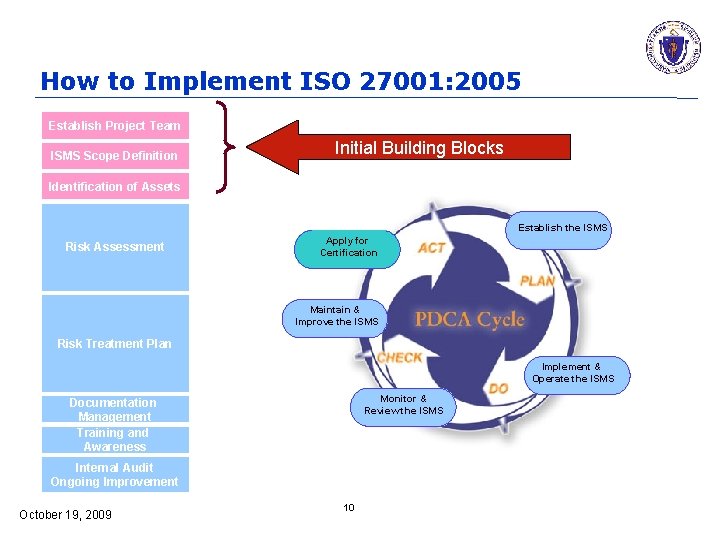
How to Implement ISO 27001: 2005 Establish Project Team ISMS Scope Definition Initial Building Blocks Identification of Assets Establish the ISMS Risk Assessment Apply for Certification Maintain & Improve the ISMS Risk Treatment Plan Implement & Operate the ISMS Monitor & Review the ISMS Documentation Management Training and Awareness Internal Audit Ongoing Improvement October 19, 2009 10

Steps to Certification (optional!) Inquire to Registrar (BSI) Develop Quotation Complete an Application BSI Assessment Team Appointed Conduct Pre-assessment (Optional) Stage 1 Audit Stage 2 Audit Certification Recommendation Bi-annual/annual Surveillance Visits October 19, 2009 1. Provide information about your business and ISMS 2. Detailing all costs involved 3. Sign contract 4. Assessors have industry experience 5. A “dry run” assessment, helps identify gaps 6. Documentation review & high level walk through 7. Detailed review of the system in action 8. Confirmation of certification and delivery of certificate (or denial!) 9. Partial audit every 6 months or every year 11

Summary Statement • One statement can sum up the main goal of the ISO 27001 framework: Reduce the likelihood of human error by replacing ad hoc procedures with repeatable processes. October 19, 2009 12

Questions? Contact Information: Curt Dalton ITD Security Office, Commonwealth of Massachusetts Program Manager, Enterprise Security Plan Office: (617) 626 -4423 Email: Curtis. Dalton@State. MA. US Personal Email: Curtis. EDalton@gmail. com October 19, 2009 13