IT 221 Classical and Modern Encryption Techniques Lecture




![Characteristics of ‘Good’ Ciphers • Claude Shannon’s Characteristics of ‘Good’ Ciphers [1]: üPrinciple 1: Characteristics of ‘Good’ Ciphers • Claude Shannon’s Characteristics of ‘Good’ Ciphers [1]: üPrinciple 1:](https://slidetodoc.com/presentation_image_h2/5eb94228b634dfb1d0cacd10568ecc12/image-13.jpg)
![DES Round Details • DES Algorithm [1]: ü(1) Blocks are transformed using a 64 DES Round Details • DES Algorithm [1]: ü(1) Blocks are transformed using a 64](https://slidetodoc.com/presentation_image_h2/5eb94228b634dfb1d0cacd10568ecc12/image-21.jpg)


![Resources • [1] Pfleeger, Charles. Security In Computing, Prentice Hall, 1997. Chapter 2 -3. Resources • [1] Pfleeger, Charles. Security In Computing, Prentice Hall, 1997. Chapter 2 -3.](https://slidetodoc.com/presentation_image_h2/5eb94228b634dfb1d0cacd10568ecc12/image-25.jpg)
- Slides: 25

IT 221: Classical and Modern Encryption Techniques Lecture 2: Classical and Modern Encryption Techniques For Educational Purposes Only Revised: September 4, 2002

Encryption Question • Context: üYou are a consultant working for a larger private-sector client. Your team is responsible for managing a network that supports a CRM (Customer Relationship Management) application, which often contains highly sensitive, often encrypted, financial information. A Hacker figures out the algorithm your client is using to encrypt outgoing emails and internal, sensitive information, and posts the algorithm on the Internet. • Questions: üShould this situation be of serious concern? Why or why not? üWhat are some of the next steps your team should take? 1 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Chapter 2 Outline • Chapter 2: üTerminology and Background üEncryption Algorithms üModel of Conventional Encryption Process üCryptography Defined üDimensions of Cryptography üUnconditional and Computational Security üExample 1: Caesar Cipher üExample 2: Columnar Transposition üCharacteristics of ‘Good’ Ciphers 2 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Terminology and Background • Context: üSuppose S (Sender) wants to send a message to R (Receiver). S entrusts the message to T (Transmission Medium) who will deliver it to R. An outsider O might try to access the message by Blocking, Intercepting, Modifying, or Fabricating it. [1]. • Terminology: üEncryption: Process of encoding a message so that its meaning is not obvious. [1] üDecryption: The reverse process of Encryption – transforming an encrypted message into its normal, plaintext form. [1] üCryptosystem: A system for Encryption and Decryption. [1] 3 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Encryption Algorithms • Encryption Algorithms: üSome algorithms use a key K, so that the ciphertext message depends on both the original plaintext message and the key value, denoted C = E(K, P) [1]. -Symmetric: Encryption and Decryption keys are mirror processes. -Asymmetric: Decryption key inverts the Encryption process, such that converting ciphertext back to plaintext is not simply the reversing of the encryption steps. • Key Secrecy: üSecurity depends on the secrecy of the key, and not the secrecy of the algorithm. Key Size No of Alt Keys Time Req @ 106 Decryption/µs 32 232 = 4. 3 x 109 2. 15 milliseconds 56 256 = 7. 2 x 1016 10 hours 128 2128 = 3. 4 x 1038 5. 4 x 1018 years 168 2168 = 3. 7 x 1050 5. 9 x 1030 years 4 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

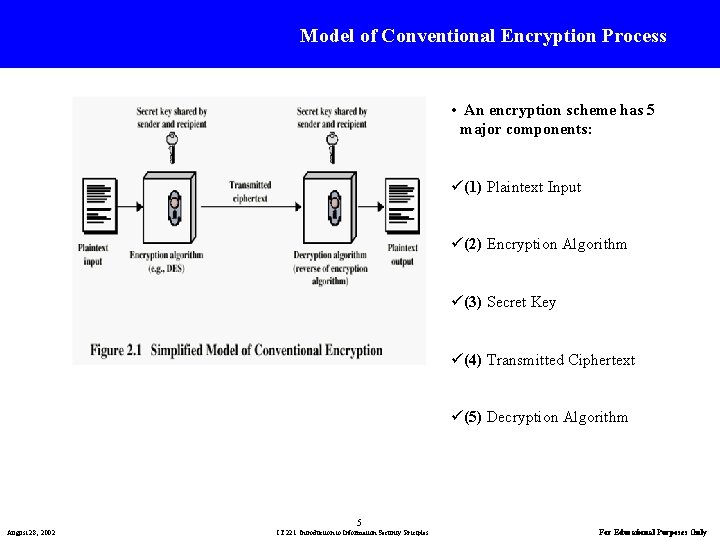
Model of Conventional Encryption Process • An encryption scheme has 5 major components: ü(1) Plaintext Input ü(2) Encryption Algorithm ü(3) Secret Key ü(4) Transmitted Ciphertext ü(5) Decryption Algorithm 5 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Cryptography Defined • Cryptography Defined: üCryptanalysis: The process of attempting to discover X and/or Y, with the Ciphertext message X and the Encryption Key K. [2] üCryptanalyst studies encryption and encrypted messages, with the objective of revealing the hidden messages of the messages [1]. 6 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Dimensions of Cryptography • Cryptographic Systems generally fall along three independent dimensions: üThe type of operations used for transforming plaintext to ciphertext. üThe number of keys used. - If both sender and receiver use the same key, the key is referred to as symmetric, single key, secret key, or conventional encryption. - If the sender and receiver each uses a different key, the system is referred to asymmetric, two key, or public-key encryption. üThe way in which the plaintext is processed. 7 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

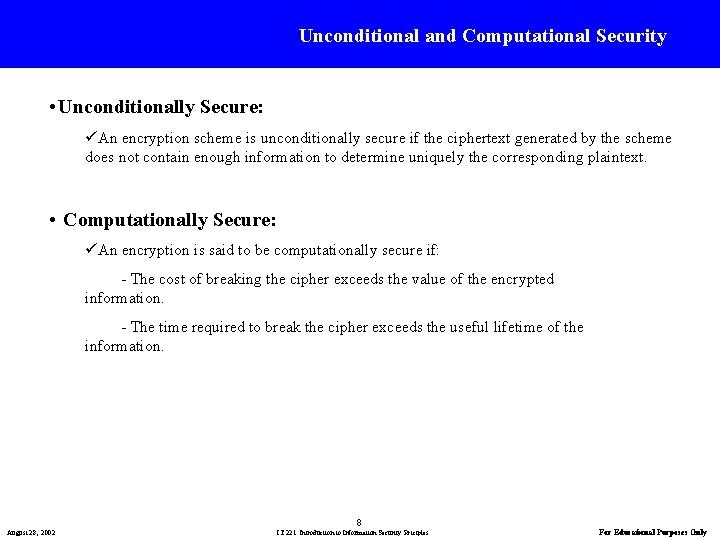
Unconditional and Computational Security • Unconditionally Secure: üAn encryption scheme is unconditionally secure if the ciphertext generated by the scheme does not contain enough information to determine uniquely the corresponding plaintext. • Computationally Secure: üAn encryption is said to be computationally secure if: - The cost of breaking the cipher exceeds the value of the encrypted information. - The time required to break the cipher exceeds the useful lifetime of the information. 8 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Classical Encryption Techniques • Classical Techniques are based on two building blocks: üSubstitution: The letters of plaintext are replaced by other letters or by numbers or symbols. Of the plaintext is viewed as a sequence of bits, then substitution involves replacing plaintext bit patterns with ciphertext bit patterns [2]. üTransposition: Some sort of permutation is performed on the letters of plaintext [2]. 9 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

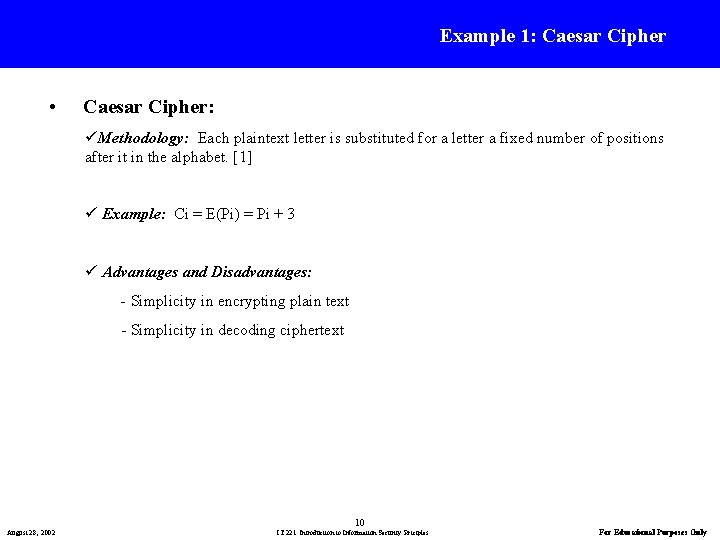
Example 1: Caesar Cipher • Caesar Cipher: üMethodology: Each plaintext letter is substituted for a letter a fixed number of positions after it in the alphabet. [1] ü Example: Ci = E(Pi) = Pi + 3 ü Advantages and Disadvantages: - Simplicity in encrypting plain text - Simplicity in decoding ciphertext 10 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

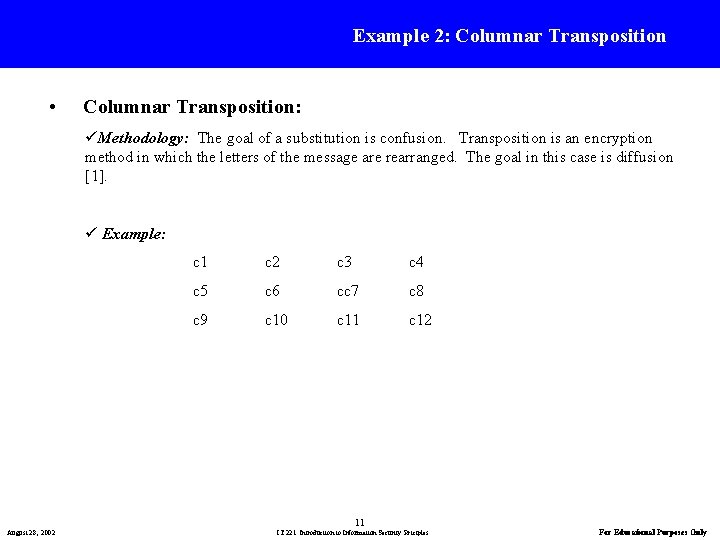
Example 2: Columnar Transposition • Columnar Transposition: üMethodology: The goal of a substitution is confusion. Transposition is an encryption method in which the letters of the message are rearranged. The goal in this case is diffusion [1]. ü Example: c 1 c 2 c 3 c 4 c 5 c 6 cc 7 c 8 c 9 c 10 c 11 c 12 11 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only
![Characteristics of Good Ciphers Claude Shannons Characteristics of Good Ciphers 1 üPrinciple 1 Characteristics of ‘Good’ Ciphers • Claude Shannon’s Characteristics of ‘Good’ Ciphers [1]: üPrinciple 1:](https://slidetodoc.com/presentation_image_h2/5eb94228b634dfb1d0cacd10568ecc12/image-13.jpg)
Characteristics of ‘Good’ Ciphers • Claude Shannon’s Characteristics of ‘Good’ Ciphers [1]: üPrinciple 1: The amount of secrecy needed should determine the amount of labor appropriate for the encryption and decryption. üPrinciple 2: The set of keys and the enciphering algorithm should be free from complexity. üPrinciple 3: The implementation of the process should be as simple as possible. üPrinciple 4: Errors in ciphering should not propagate and cause corruption of further information in the message. üPrinciple 5: The size of the enciphered text should be no larger than the text of the original message. 12 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Chapter 3 Outline • Chapter 3: üBackground üStream and Block Ciphers Defined üFeistel Cipher Structure üFeistel Algorithm üDES Structure üDES Algorithm üDES Round Details üDES Weaknesses üTime To Break A Code üBlock Cipher Modes of Operations 13 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Background • Context: üChapter 2 introduced the basic concepts of encryption and cryptanalysis. These approaches are suitable for short, simple messages, but are inappropriate for situations requiring more complex security requirements. 14 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Stream and Block Ciphers Defined • Stream and Block Ciphers: üStream Cipher: Encrypts a digital data stream one byte at a time [2]. üBlock Cipher: Encrypts blocks of plaintext, treated as a whole and used to produce a ciphertext block of equal length [2]. 15 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Feistel Cipher Structure • Stream and Block Ciphers: üVirtually all symmetric block encryption algorithms in current use, including DES, are based on the Feistel block cipher [2]. üRealization of the Feistel Network depends on the choice of the following design factors: -Block size: larger block sizes mean greater security -Key Size: larger key size means greater security -Number of rounds: multiple rounds offer increasing security -Subkey generation algorithm: greater complexity will lead to greater difficulty of cryptanalysis. -Fast software encryption/decryption: the speed of execution of the algorithm becomes a concern 16 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

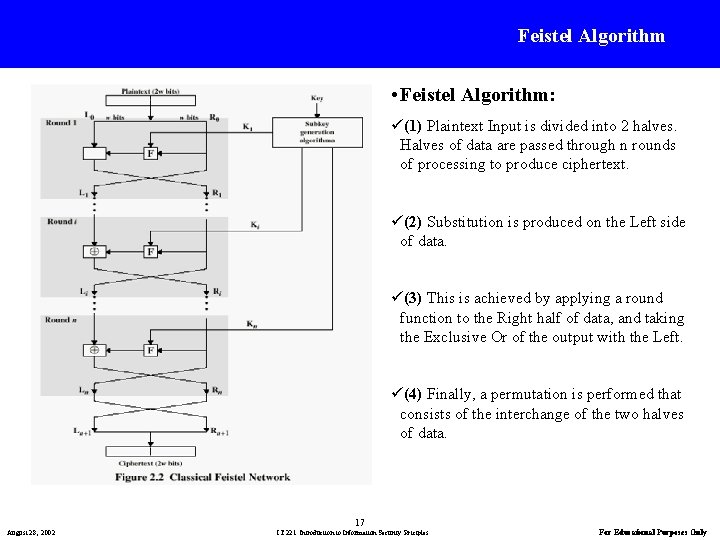
Feistel Algorithm • Feistel Algorithm: ü(1) Plaintext Input is divided into 2 halves. Halves of data are passed through n rounds of processing to produce ciphertext. ü(2) Substitution is produced on the Left side of data. ü(3) This is achieved by applying a round function to the Right half of data, and taking the Exclusive Or of the output with the Left. ü(4) Finally, a permutation is performed that consists of the interchange of the two halves of data. 17 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

DES Structure • Data Encryption Standard (DES): üThe most widely used encryption scheme üDES is a block cipher üThe plaintext is processed in 64 -bit blocks üThe key is 56 -bits in length üAchieves its strength from repeated rounds of substitution and permutation 18 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

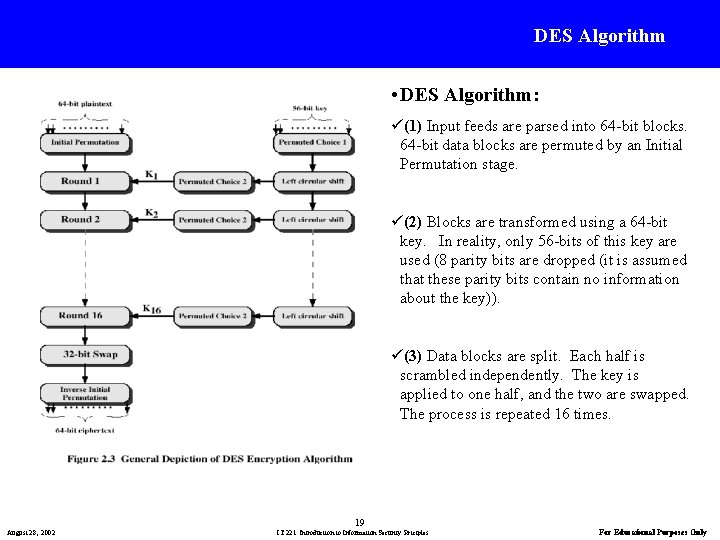
DES Algorithm • DES Algorithm: ü(1) Input feeds are parsed into 64 -bit blocks. 64 -bit data blocks are permuted by an Initial Permutation stage. ü(2) Blocks are transformed using a 64 -bit key. In reality, only 56 -bits of this key are used (8 parity bits are dropped (it is assumed that these parity bits contain no information about the key)). ü(3) Data blocks are split. Each half is scrambled independently. The key is applied to one half, and the two are swapped. The process is repeated 16 times. 19 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only
![DES Round Details DES Algorithm 1 ü1 Blocks are transformed using a 64 DES Round Details • DES Algorithm [1]: ü(1) Blocks are transformed using a 64](https://slidetodoc.com/presentation_image_h2/5eb94228b634dfb1d0cacd10568ecc12/image-21.jpg)
DES Round Details • DES Algorithm [1]: ü(1) Blocks are transformed using a 64 -bit key. ü(2) Blocks are broken into 32 -bit halves: Left and Right. The key is shifted by a number of bits and permuted. ü(3) 32 -Bit Right half is expanded to 48 bits, and combined with the Key. The result is condensed and combined with Left. 20 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

DES Weaknesses • Data Encryption Standard (DES): üComplements üWeak/Semi-Weak Keys üKey Clustering 21 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Time to Break a Code 22 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only

Block Cipher Modes of Operations • Block Cipher Modes of Operations: DES is a basic building block of security. Four ‘modes’ have been design to cover a wide range of possible DES applications. MODE DESC Electronic Cookbook (ECB) Each block of 64 plaintext is encoded independently using the same key. Cipher Block Chaining (CBC) Input to the algorithm is the XOR of the next 64 bits of plaintext and the preceding 64 bits of plaintext. Cipher Feedback (CFB) Input is processed J bits at a time. Preceding ciphertext is used as input to the algorithm to produce pseudorandom output, which is XORed with Plaintext to produce the next unit of ciphertext. Output Feedback (OFB) Similar to CFB, except that the input to the algorithm is the preceding DES output. 23 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only
![Resources 1 Pfleeger Charles Security In Computing Prentice Hall 1997 Chapter 2 3 Resources • [1] Pfleeger, Charles. Security In Computing, Prentice Hall, 1997. Chapter 2 -3.](https://slidetodoc.com/presentation_image_h2/5eb94228b634dfb1d0cacd10568ecc12/image-25.jpg)
Resources • [1] Pfleeger, Charles. Security In Computing, Prentice Hall, 1997. Chapter 2 -3. • [2] Stallings, William. Cryptography and Network Security, Prentice Hall, 1999. Chapter 2 -3 24 August 28, 2002 IT 221: Introduction to Information Security Priciples For Educational Purposes Only