ISA 562 Internet Security Theory Practice Access Control


























- Slides: 46

ISA 562 Internet Security Theory & Practice Access Control ISA 562

Objectives and References n n n General (from ISC 2 CBK Material ): Discuss Access Control mechanisms, measures and threats Details (from Bishop’s Chapters 2): Access control assurance methods General (from ISC 2 CBK Material ): Intrusion detection/ intrusion prevention 2

Requirements & Concepts n Some basic requirements of an access control: n n n Avoid disclosing sensitive data to unauthorized users (Confidential) Provide sensitive information to authorized users (Available) Reliable and dependable (Integrity preserving) Scalable and expandable (long life) Some of the key concepts in Access control systems are: n n n Separation of duties Least privilege Need-to-know Need-to-share (a contemporary buzz-phrase) Handle with care 3

What to protect? : Information classification n n Based on business risk of content released to malactors Example the US government classification n n Unclassified Confidential Secret Top secret Will be discussed in detail 4

Kinds of Access Control n Preventive Access controls n n Detective n n n Prescribe punishment for noncompliance Recovery n n Dictated by higher authority in laws or regulations or those specified in organization policy Deterrent n n Remedy circumstances that enabled the unwanted activity. Return to state prior to the unwanted activity. Directive n n Identify unwanted actions or events after they occur. Corrective n n Avoid having unwanted actions/events by blocking the ability to do them. Restore lost computing resources or capabilities. Compensating n Reinforce or replace normal controls that are unavailable 5

3 Types of access controls n Administrative n n Physical n n Examples: fences, alarms, badges, CCTV, etc Technical n n Examples: separation of duties, dual control, etc Examples: antivirus, antis-spam, logs, etc Further examples in ISC 2 book show controls map to the access control types. 6

Steps in Accessing Systems n Authentication n Use a unique identifier– n n n 3 main datum used for authentication Something requester know n n n n Biometrics Physical characteristics Something the requester has n n Passwords Pass-phrases Something the requester is n n Example: user ID, Account number, PIN Tokens (one-time passwords, time synchronized token) Smart Cards USB Tokens Authorization Accounting 7

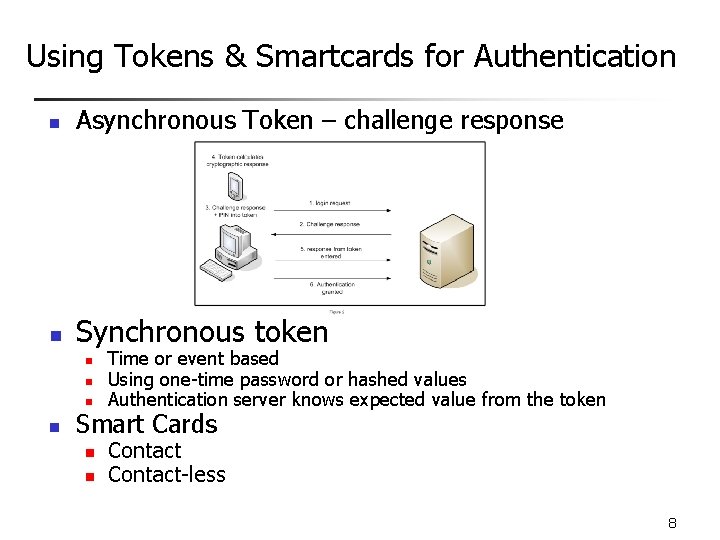
Using Tokens & Smartcards for Authentication n Asynchronous Token – challenge response n Synchronous token n n Time or event based Using one-time password or hashed values Authentication server knows expected value from the token Smart Cards n n Contact-less 8

Using Biometrics for Authentication n Have false (rejection, acceptance) rates. Crossover = they are equal, both tunable to need. Examples static biometrics n n Fingerprint or palm print Hand Geometry Retina Example Dynamic biometrics n n n Face /gesture Recognition Keystrokes Voice pattern 9

Identity Management n What is Identity management? n n When is it needed? n n For manual service provisioning Manage sophisticated and complex environments To comply with regulations What are the major challenges? n n Set of technologies used to manage user identity information. Reliability of user profiles Consistency of user profiles across different systems/devices Scalability by supporting data volumes and peaks More details in the IC 3 book 10

Identity Management: benefits and technologies n Benefits n n n Increasing productivity Reducing head-counting Technologies n Found in systems that support the identity management process and managing data consistently and efficiently across multiple systems within an organization n n Directories Web Access Management Password Management Legacy single sign-on’s 11

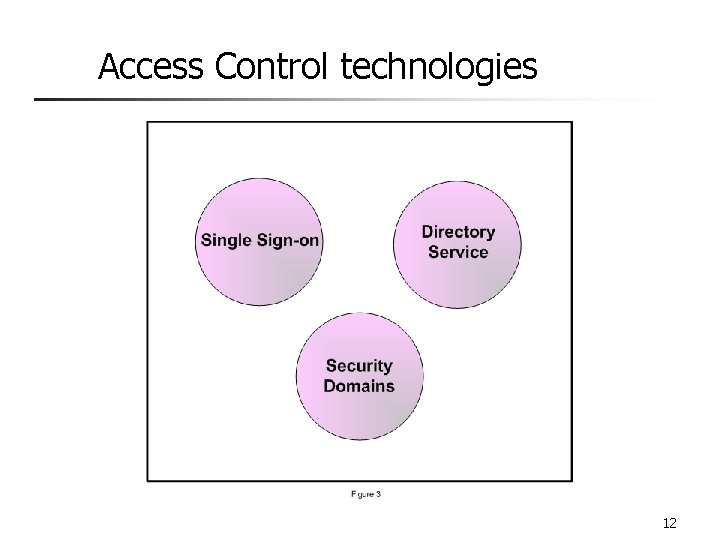
Access Control technologies 12

Single Sign-on n How they work n n Benefits n n One user ID and password for multiple application servers through an authentication server. Efficient log-on process Users may create stronger passwords No need for multiple passwords Major Drawback n A compromised password allows intruder into all resources of the owner of that account 13

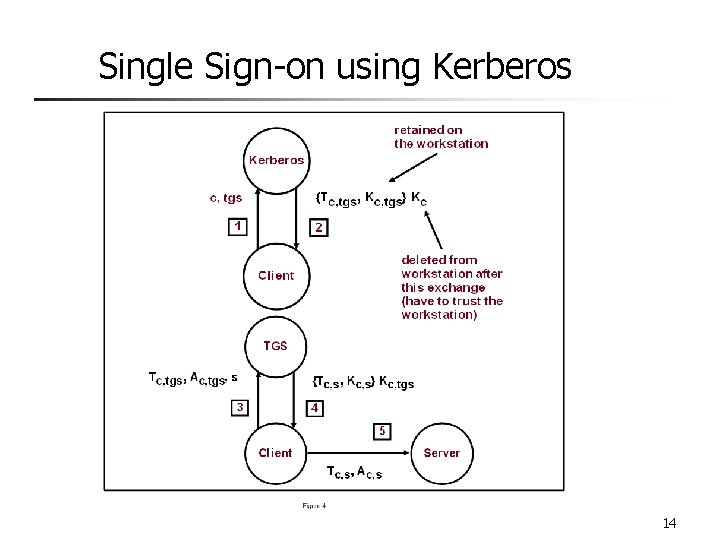
Single Sign-on using Kerberos 14

Single Sign-on – Kerberos and SESAME n Kerberos Key Distribution Center serves two functions n n n Kerberos Issues n n n Authentication Server (AS) Ticket Granting Server (TGS) Security depends on careful implementation and maintenance Lifetime for authentication credentials should be as short as feasible using time stamps to minimize threat of replayed credentials The KDC must be physically secured, it could be a point of single failure Redundancy is recommended The KDC should be hardened and not allow any non-Kerberos activity SESAME n n Stands for Secure European System for applications in a multi-vendor environment Developed to address some of the Kerberos weaknesses Supports SSO Improves key management by using both Symmetric and Asymmetric keys 15

Directory Service and Security Domains n Directory Services n n Consist of applications that provide the means to hierarchically organize and manage information about network users and resources and to retrieve the information by name association Security Domains n Set of objects that a subject in an information system is allowed to access n n Hierarchical domain relationship Equivalence classes of subjects 16

Access Control & Assurance n Mechanisms used to assure that access control mechanisms are in place and in a good standing: n Audit Trail analysis and monitoring n n is a record of system activities Assessment tools n Audit tools cover a wide spectrum of cost, complexity, etc and must be tailored to the specific goals of the audit 17

The Access Control Matrix Model Chapter 2 from Bishop’s book

Chapter 2: Access Control Matrix n n Overview Access Control Matrix Model n n n Protection State Transitions n n n Boolean Expression Evaluation History Commands Conditional Commands Special Rights n Principle of Attenuation of Privilege

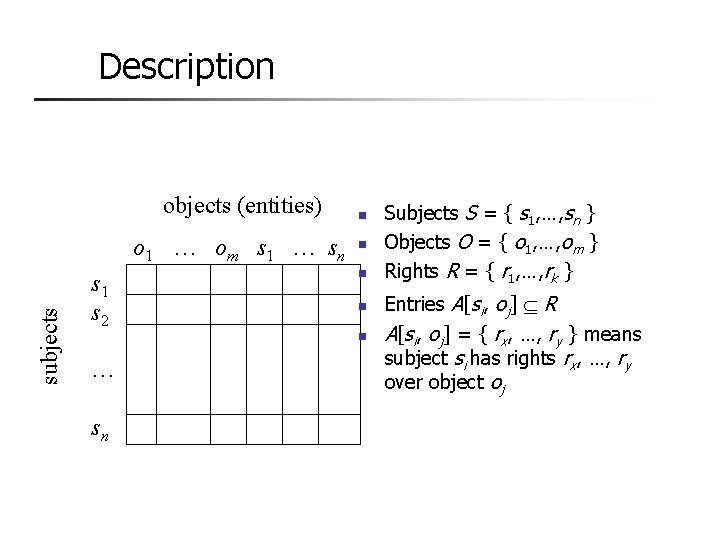
Overview n Protection state of system n n Describes current settings, values of system relevant to protection Access control matrix n n n Describes protection state precisely Matrix describing rights of subjects State transitions change elements of matrix

Description objects (entities) subjects o 1 … om s 1 … sn s 1 s 2 n n n … sn Subjects S = { s 1, …, sn } Objects O = { o 1, …, om } Rights R = { r 1, …, rk } Entries A[si, oj] R A[si, oj] = { rx, …, ry } means subject si has rights rx, …, ry over object oj

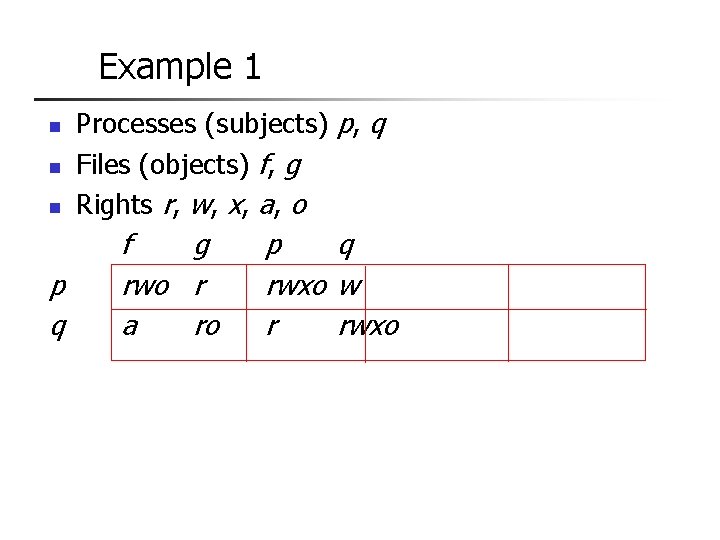
Example 1 n n n p q Processes (subjects) p, q Files (objects) f, g Rights r, w, x, a, o f g rwo r a ro p q rwxo w r rwxo

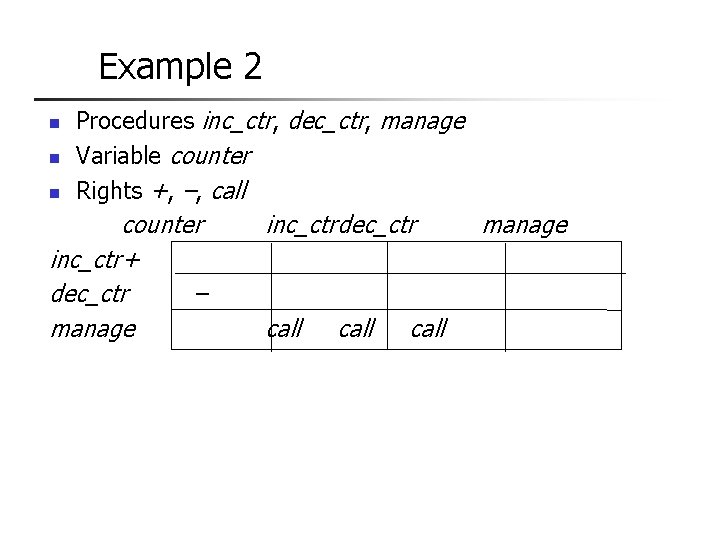
Example 2 n n n Procedures inc_ctr, dec_ctr, manage Variable counter Rights +, –, call counter inc_ctr+ dec_ctr – manage inc_ctrdec_ctr call manage

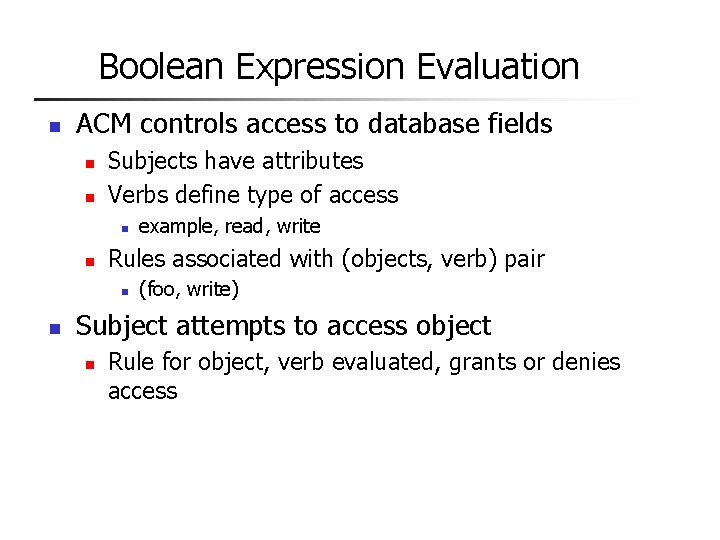
Boolean Expression Evaluation n ACM controls access to database fields n n Subjects have attributes Verbs define type of access n n Rules associated with (objects, verb) pair n n example, read, write (foo, write) Subject attempts to access object n Rule for object, verb evaluated, grants or denies access

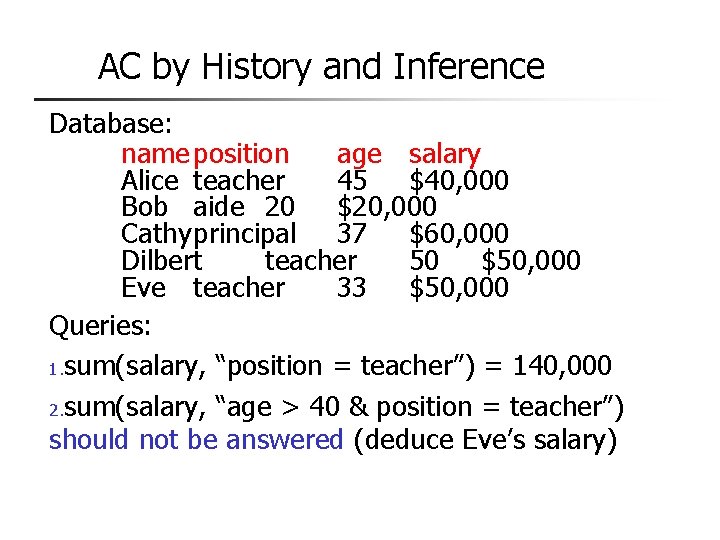
Example n Subject Alice n n Verb paint n n Attributes role (artist), groups (creative) Default 0 (deny unless explicitly granted) Object picture n Rule: paint: ‘artist’ in subject. role and ‘creative’ in subject. groups and time. hour ≥ 0 and time. hour < 5

ACM at 3 AM and 10 AM … picture … paint … annie … At 10 AM, time condition not met; ACM is: … annie … At 3 AM, time condition met; ACM is:

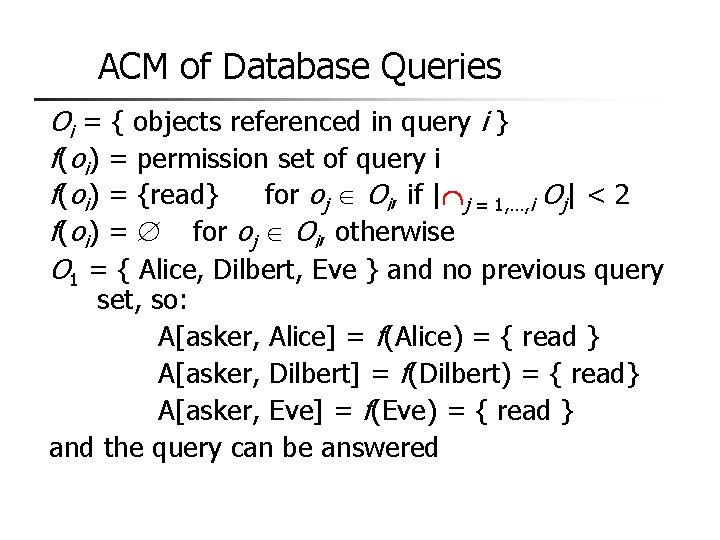
AC by History and Inference Database: name position age salary Alice teacher 45 $40, 000 Bob aide 20 $20, 000 Cathyprincipal 37 $60, 000 Dilbert teacher 50 $50, 000 Eve teacher 33 $50, 000 Queries: 1. sum(salary, “position = teacher”) = 140, 000 2. sum(salary, “age > 40 & position = teacher”) should not be answered (deduce Eve’s salary)

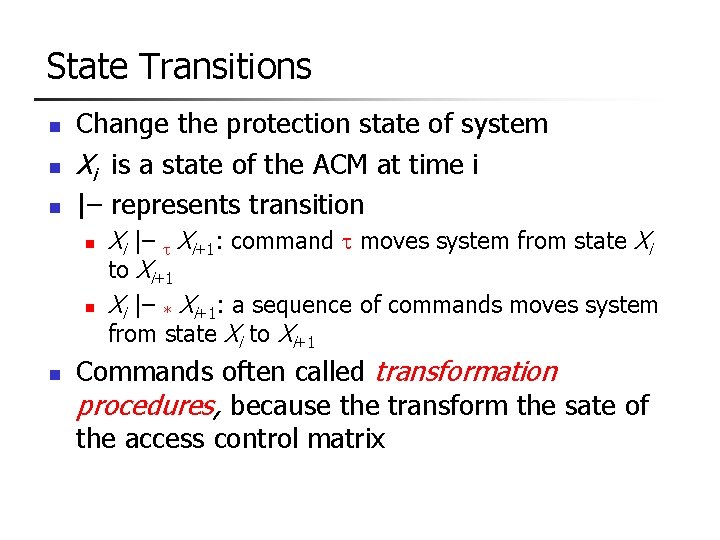
ACM of Database Queries Oi = { objects referenced in query i } f(oi) = permission set of query i f(oi) = {read} for oj Oi, if | j = 1, …, i Oj| < 2 f(oi) = for oj Oi, otherwise O 1 = { Alice, Dilbert, Eve } and no previous query set, so: A[asker, Alice] = f(Alice) = { read } A[asker, Dilbert] = f(Dilbert) = { read} A[asker, Eve] = f(Eve) = { read } and the query can be answered

But Query 2 From last slide: f(oi) = { read } for oj in Oi, if | j = 1, …, i Oj| <2 f( o i) = for oj in Oi, otherwise 2. O 2 = { Alice, Dilbert } but | O 2 O 1 | = 2 so A[asker, Alice] = f(Alice) = A[asker, Dilbert] = f(Dilbert) = and query cannot be answered

State Transitions n n n Change the protection state of system Xi is a state of the ACM at time i |– represents transition n Xi |– Xi+1: command moves system from state Xi to Xi+1 Xi |– * Xi+1: a sequence of commands moves system from state Xi to Xi+1 Commands often called transformation procedures, because the transform the sate of the access control matrix

Primitive Operations n create subject s, create object o n n destroy subject s, destroy object o n n Deletes row, column from ACM; deletes column from ACM enter r into A[s, o] n n Creates new row, column in ACM; creates new column in ACM Adds r rights for subject s over object o delete r from A[s, o] n Removes r rights from subject s over object o

Access control requests n n Transforms sate of the access control matrix An access control request can be precisely defined using n n n Use notation (from Z) n n n Pre-conditions Post-conditions Pre-state without primes Post-state with primes Example: pre-state - A[alice, file 1] is the permission set of Alice to file 1 before a requests, and A’[alice, file 1] is a post-state

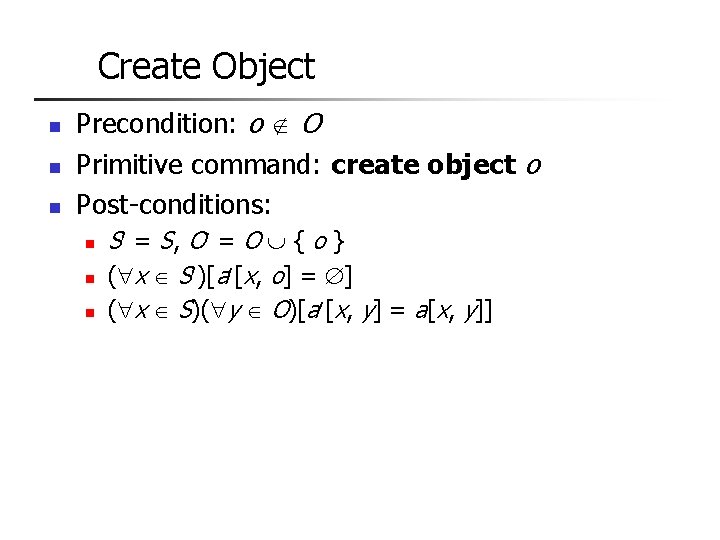
Create Subject – pre and post conditions n n n Pre-condition: s S Primitive command: create subject s Post-conditions: n n S = S { s }, O = O { s } ( y O )[a [s, y] = ] ( x S )[a [x, s] = ] ( x S)( y O)[a [x, y] = a[x, y]]

Create Object n n n Precondition: o O Primitive command: create object o Post-conditions: n n n S = S, O = O { o } ( x S )[a [x, o] = ] ( x S)( y O)[a [x, y] = a[x, y]]

Add Right n n n Precondition: s S, o O Primitive command: enter r into a[s, o] Post-conditions: n n S = S, O = O a [s, o] = a[s, o] { r } ( x S )( y O – { o }) [a [x, y] = a[x, y]] ( x S – { s })( y O ) [a [x, y] = a[x, y]]

Delete Right n n n Precondition: s S, o O Primitive command: delete r from a[s, o] Postconditions: n n S = S, O = O a [s, o] = a[s, o] – { r } ( x S )( y O – { o }) [a [x, y] = a[x, y]] ( x S – { s })( y O ) [a [x, y] = a[x, y]]

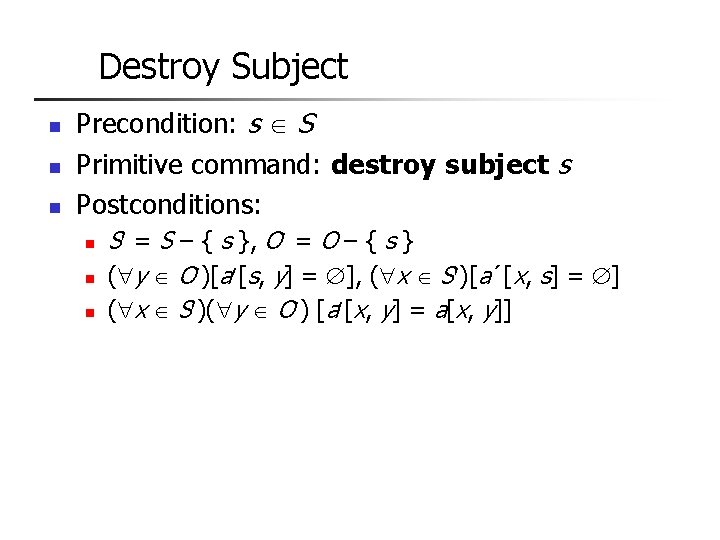
Destroy Subject n n n Precondition: s S Primitive command: destroy subject s Postconditions: n n n S = S – { s }, O = O – { s } ( y O )[a [s, y] = ], ( x S )[a´[x, s] = ] ( x S )( y O ) [a [x, y] = a[x, y]]

Destroy Object n n n Precondition: o O Primitive command: destroy object o Postconditions: n n n S = S, O = O – { o } ( x S )[a [x, o] = ] ( x S )( y O ) [a [x, y] = a[x, y]]

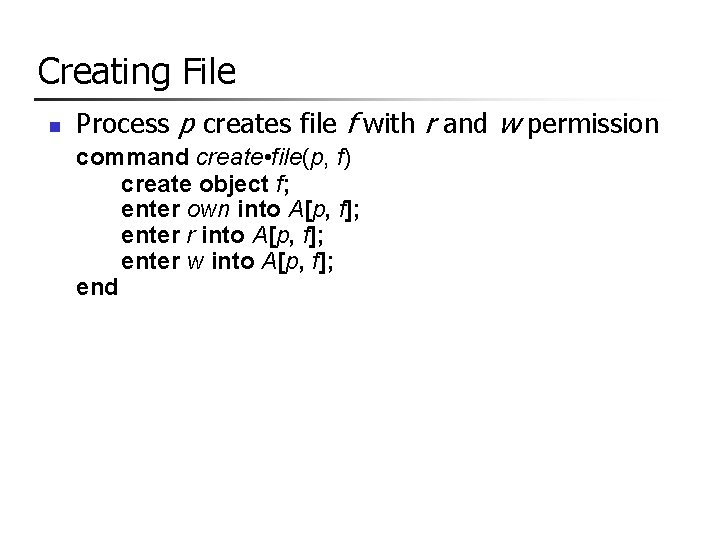
Creating File n Process p creates file f with r and w permission command create • file(p, f) create object f; enter own into A[p, f]; enter r into A[p, f]; enter w into A[p, f]; end

Mono-Operational Commands n Make process p the owner of file g command make • owner(p, g) enter own into A[p, g]; end n Mono-operational command n Single primitive operation in this command

Conditional Commands n Let p give q r rights over f, if p owns f command grant • read • file • 1(p, f, q) if own in A[p, f] then enter r into A[q, f]; end n Mono-conditional command n Single condition in this command

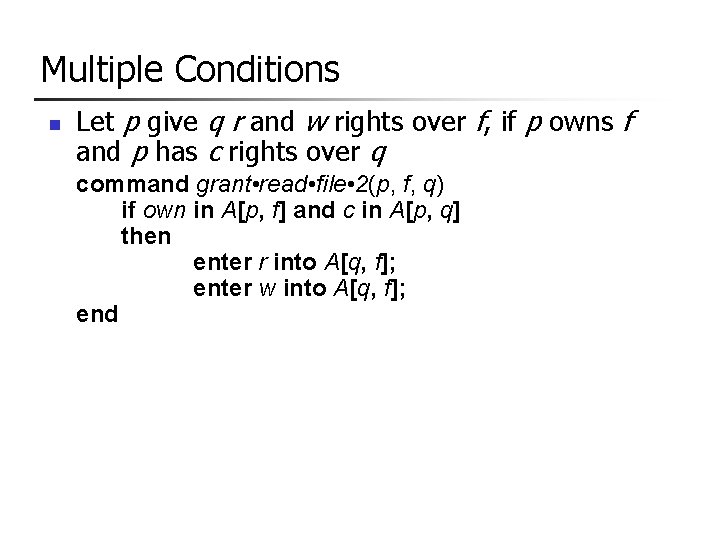
Multiple Conditions n Let p give q r and w rights over f, if p owns f and p has c rights over q command grant • read • file • 2(p, f, q) if own in A[p, f] and c in A[p, q] then enter r into A[q, f]; enter w into A[q, f]; end

Copy Right n n Allows possessor to give rights to another Often attached to a right, so only applies to that right n n n r is read right that cannot be copied rc is read right that can be copied Is copy flag copied when giving r rights? n Depends on the model and its instantiation

Own Right n Usually allows possessor to change entries in ACM column n n Owner of an object can add, delete rights for others May depend on what system allows n n Can’t give rights to specific (set of) users Can’t pass copy flag to specific (set of) users

Attenuation of Privilege n Principle says you can’t give rights you do not possess n n Restricts addition of rights within a system Usually ignored for owner n Why? Owner gives herself rights, gives them to others, deletes her rights.

Main Points n n n Access control matrix simplest abstraction mechanism for representing protection state Transitions alter protection state 6 primitive operations that alter the matrix n Transitions can be expressed as commands composed of these operations and, possibly, conditions