IPv 6 and Spam 2009 MIT Spam Conference












- Slides: 22

IPv 6 and Spam 2009 MIT Spam Conference Peter Kosik, Patrik Ostrihon and Reza Rajabiun reza@comdomsoft. com 1 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Spam Economics End user and network costs of spam ITU (2008): Economic implications of malware and spam (bandwidth, processing, storage, annoyance, etc. ) This paper: A more pernicious problem Spam also limits incentives to adopt efficiency enhancing technologies and standards 2 Specifically: Constrains the diffusion of IPv 6 at the AS level Implications: Technological sclerosis and network fragmentation Why? Alters the relative capacities of attackers/defenders © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

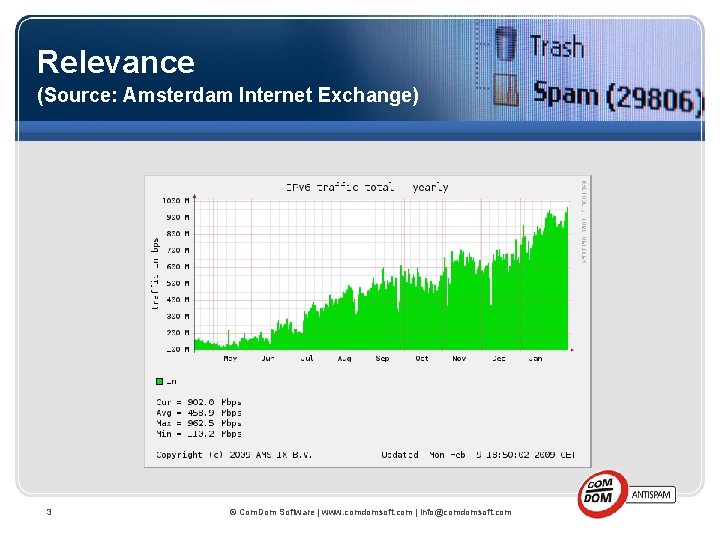
Relevance (Source: Amsterdam Internet Exchange) 3 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

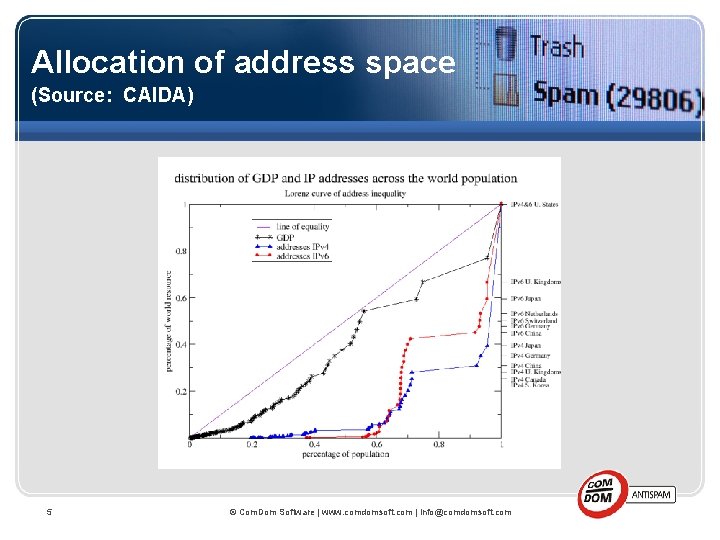
IPv 6 Economics Demand: Address space exhaustion (128 v. 32 bit design) Network Address Translation leads to fragmentation (big problem in developing countries in particular) Supply: Very limited even in countries with more to gain from a switch Less than 1% in all countries (Google, 2008), Leaders in deploying IPv 6: Entities with need for large space: DOD, cable operators (IPv 6 lite) 4 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Allocation of address space (Source: CAIDA) 5 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

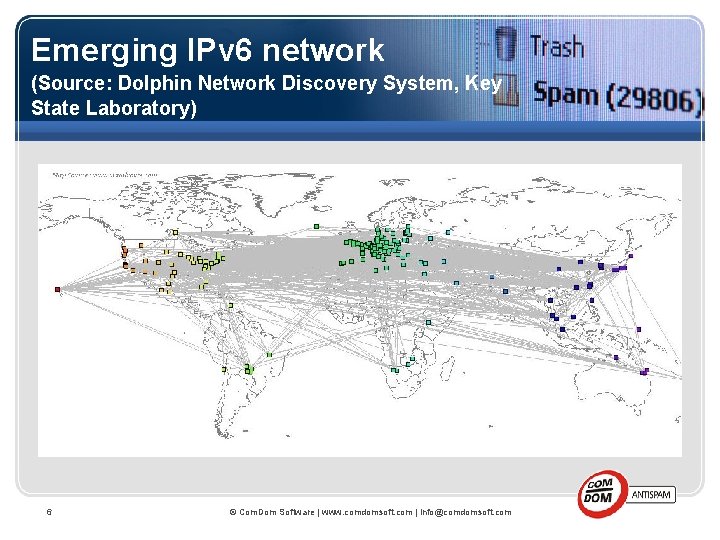
Emerging IPv 6 network (Source: Dolphin Network Discovery System, Key State Laboratory) 6 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

IPv 6 Diffusion Not an end user problem: End users usually do not make choices about IP Technology bundling: Transition between Windows XP to Vista required to stimulate ISP investment in IPv 6 specific infrastructure. Vista necessary, but not sufficient for IPv 6 diffusion Why? Positive network externalities: Multiple equilibrium problem in the level of diffusion Central variable: Decisions by Autonomous Systems/upstream operators 7 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Technological decisions Traditional diffusion model S-curve: A small proportion of population adopt first, then rate increases --> Deterministic Elmore et al. (2008): Significant resistance to IPv 6 adoption. Possible solutions: 8 Public subsidies Partial mandates Technological bundling © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Technological decisions AS decision interdependence Game theoretical perspective --> Stochastic process In the presence of positive network externalities/strategic complementarities: 9 Decisions by sellers/firms reinforce each other Possibility of a stable (inefficient) Nash equilibrium with persistent low penetration Possibility of rapid shifts from sub-optimal Nash to Pareto efficient states © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Decision processes AS IPv 6 decisions 1) Delay/not delay investment 2) Full /IPv 6 lite General model of diffusion of binary decisions in network games. Jackson and Yariv (2007): In the presence of strategic complementarities, Bayesian Nash equilibrium exists and conveyance behavior monotone (up/down) Let x – Prob. of random network i adopting IPv 6 Let d – Degree distribution for network i (links) 10 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

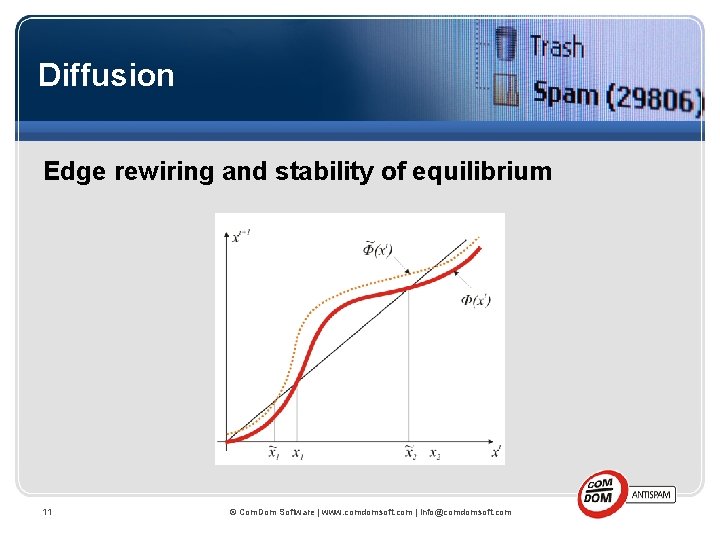
Diffusion Edge rewiring and stability of equilibrium 11 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

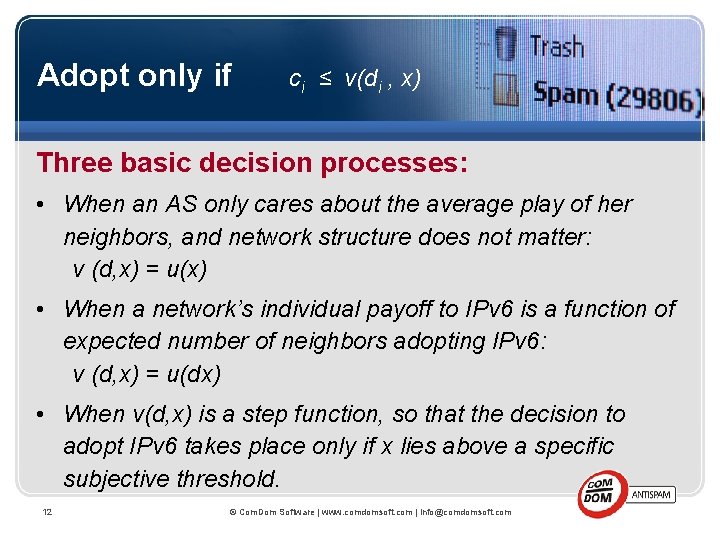
Adopt only if ci ≤ v(di , x) Three basic decision processes: • When an AS only cares about the average play of her neighbors, and network structure does not matter: v (d, x) = u(x) • When a network’s individual payoff to IPv 6 is a function of expected number of neighbors adopting IPv 6: v (d, x) = u(dx) • When v(d, x) is a step function, so that the decision to adopt IPv 6 takes place only if x lies above a specific subjective threshold. 12 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Interpretation If degree distribution matters: Hypothesis: Decisions by networks with the largest number of linkages will determine the equilibrium level of diffusion. Xiao et al. (2009): Empirical analysis of emerging topology 13 Degree distribution of IPv 6 ASs follows power law distribution Power law exponent is around 1. 2 (much lower than Ipv 4, at approx. 2. 2) IPv 6 connectivity less uniformly distributed --> Big © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com networks have to move first

IPv 6 and Complexity (Source: Dolphin NDS) 14 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Spam and Technological Decisions Kimakova and Rajabiun (2008) War of attrition: More spam with more antispam (another example of strategic complementarities) Kanich et al. (2008): Very low conversion rates (in both responses to mass advertisements and infections) O'Donnell (2008): Strong incentives to switch to new channels for extracting value from targets (OS vulnerabilities, other messaging applications) Key question: How does IPv 6 change relative capacities of attackers and defenders? 15 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

IPv 6 angles of attack Three specific channels: OS/application specific vulnerabilities – usually patched quickly by vendors (See: US-CERT database) Large address space makes it easier to hide – Erosion of value of sender information » Accuracy: BGP Spectrum Agility techniques and one shot mailings » False positives: Reputation hijacking 16 Auto configuration and neighbor discovery © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

IPv 6 and Spam IP evolution: Davis et al. (2006): IPv 6 may help with the spam problem, if: 1) A property regime could be created to make reputation of senders more credible Would lead to more reputation hijacking and not realistic 2) The near infinite address space made it more difficult for spammers to probe the network for vulnerabilities 17 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Downstream admin. Passive Decisions MS Exchange 2007 Antispam and Antivirus Functionality: “…strongly recommend against configuring Receive connectors to accept anonymous connections from unknown IPv 6 addresses. If your organization must receive mail from senders who use IPv 6 addresses, create a dedicated Receive connector that restricts the remote IP addresses to the specific IPv 6 addresses that those senders use. If you configure a Receive connector to accept anonymous connections from unknown IPv 6 addresses, the amount of spam that enters your organization is likely to increase. ” 18 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

(Semi) Autonomous Systems Active Decisions ISPs with large d's: their IPv 6 decisions matter most to diffusion Problem: Reliant on DNSRBLs and reputation based filtering (5060% of the spam/total load) If IPv 6 large address space erodes reputation, then 1) Forgone investments in spam defenses 19 2) Increases in infrastructure costs since reputation is perceived to be cheaper than content analysis (processing, storage, etc. ) © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Rational expectations and transition to IPv 6 Port scanning and information gathering: Bellovin et al. (2006): Using a two stage search process IPv 6 neighborhood discovery logs can be used to collect necessary info. In addition to active scanning techniques, ASs expect that in an IPv 6 world: Target discovery and worm propagation: Relatively easy since computers in IPv 6 space will likely live near each other (given adjacent addresses by ISPs). Much like agglomeration of people in cities. 20 © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Spamming in IPv 6 Shifting targeting paradigm Most computers in the world already protected by NATs from active and passive scanning Result: Spammers devise techniques that let their prey come to them! 21 Place malicious code on WWW servers. Infiltrate routers of big ISPs. Use BGP to redirect traffic. © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com

Implications and Discussion IPv 6 lite implementation will not help address the strategic decisions that influence aggregate diffusion rates (edges using NATs and IPv 4) IPv 6 diffusion requires complementary changes in technologies for spam processing 22 Stronger sender authentication (DKIM, etc. ), or Accountable Internet Protocol (AIP) as in Andersen et al. (2008). Increased emphasis on content analysis and statistical filters. © Com. Dom Software | www. comdomsoft. com | info@comdomsoft. com