IP Switching Tag Switching MPLS All rights reserved






























































- Slides: 93

IP Switching Tag Switching MPLS Ó All rights reserved. No part of this publication and file may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without prior written permission of Professor Nen -Fu Huang (E-mail: nfhuang@cs. nthu. edu. tw). 國立清華大學資訊系黃能富教授 1

Networking Trends More Bandwidth, - New Technology, The Internet! …. . Users need more Bandwidth Bridges - Routers - Switches The Internet & Intranetworking 國立清華大學資訊系黃能富教授 2

Network Waves Leading to IP Switching PC Networks Proliferate time Bridges Routers Internet Networking Trends ATM & Fast Ethernet 國立清華大學資訊系黃能富教授 3

Network Waves Leading to IP Switching Routers PC Networks Proliferate time Bridges Routers Internet Networking Trends ATM & Fast Ethernet 國立清華大學資訊系黃能富教授 4

Network Waves Leading to IP Switching ATM & Internet Routers PC Networks Proliferate time Bridges Routers Internet Networking Trends 國立清華大學資訊系黃能富教授 5

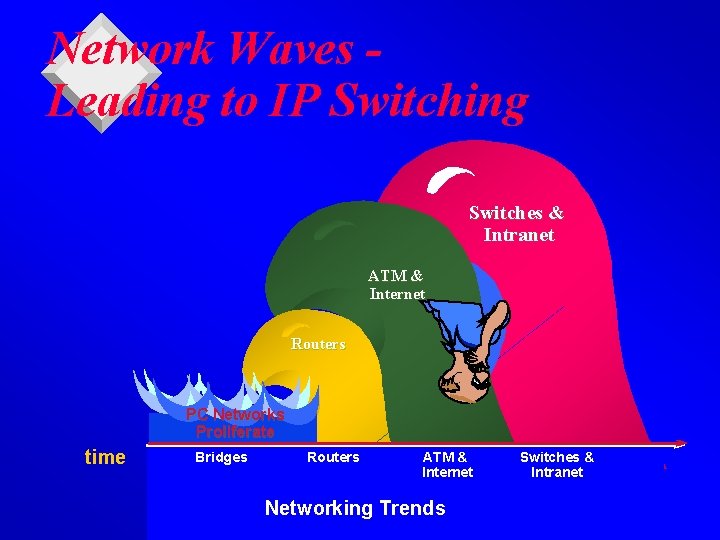
Network Waves Leading to IP Switching Switches & Intranet ATM & Internet Routers PC Networks Proliferate time Bridges Routers ATM & Internet Networking Trends Switches & Intranet 國立清華大學資訊系黃能富教授 6

Network Waves Leading to IP Switching Switches & Fast Ethernet ATM & Internet Routers PC Networks Proliferate time Bridges Routers ATM & Internet Networking Trends Switches & Fast Ethernet IP Switching 國立清華大學資訊系黃能富教授 7

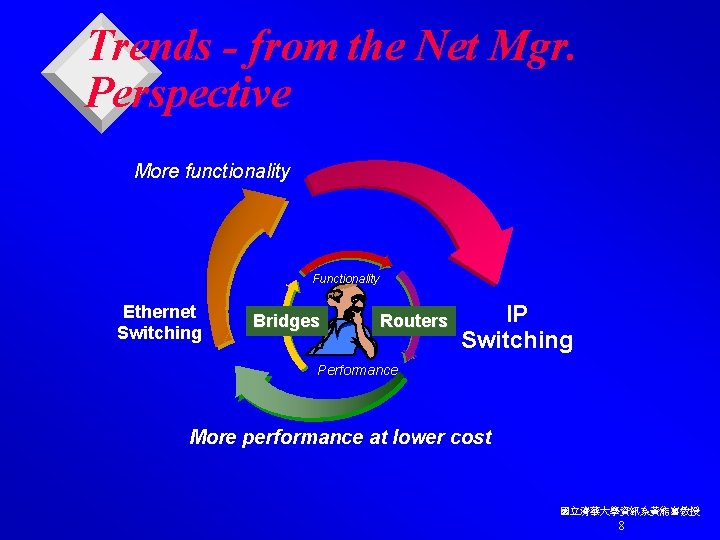
Trends - from the Net Mgr. Perspective More functionality Functionality Ethernet Switching Bridges Routers IP Switching Performance More performance at lower cost 國立清華大學資訊系黃能富教授 8

Introduction to IP Switching 國立清華大學資訊系黃能富教授 9

A Typical Routed Network Today End Stations ATM/Ethernet/Optical Switches Routers (typically) Switches or Routers 國立清華大學資訊系黃能富教授 10

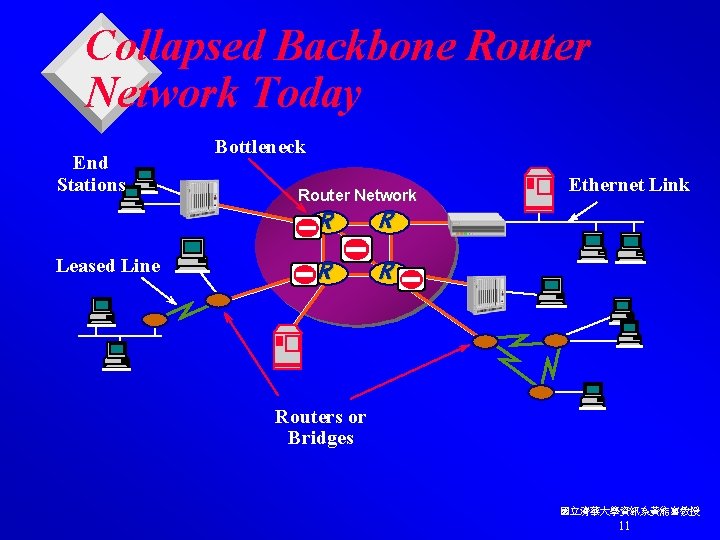
Collapsed Backbone Router Network Today End Stations Leased Line Bottleneck Router Network R R Ethernet Link Routers or Bridges 國立清華大學資訊系黃能富教授 11

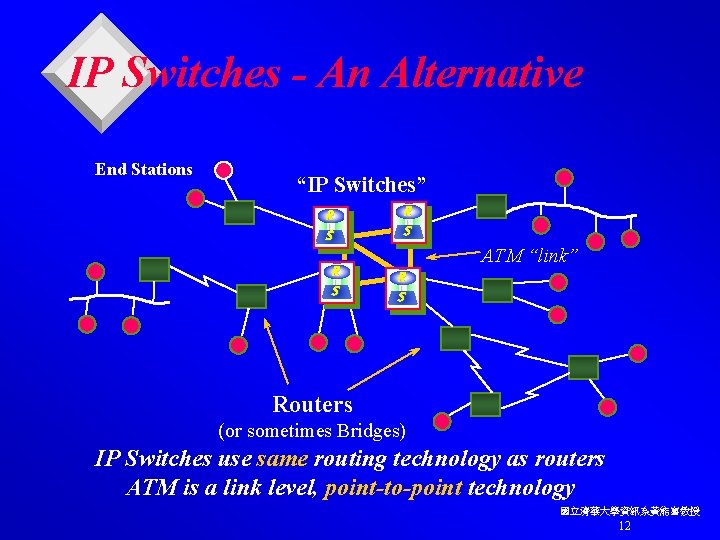
IP Switches - An Alternative End Stations “IP Switches” R S R S ATM “link” R S Routers (or sometimes Bridges) IP Switches use same routing technology as routers ATM is a link level, point-to-point technology 國立清華大學資訊系黃能富教授 12

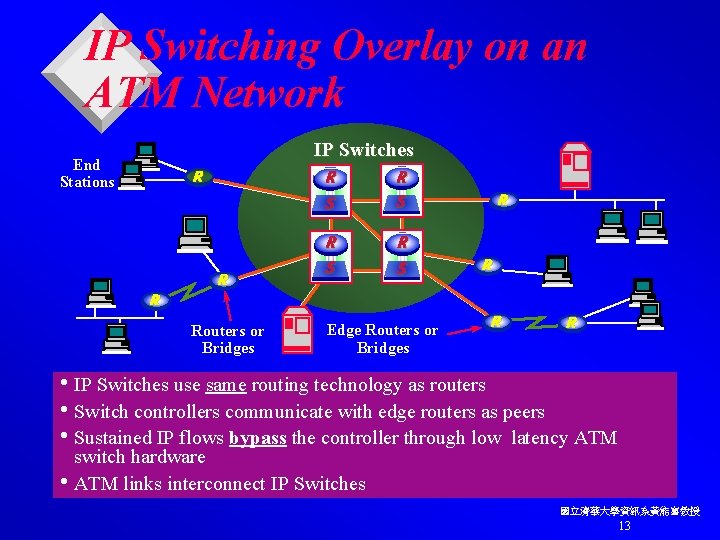
IP Switching Overlay on an ATM Network End Stations IP Switches R R S S R R R S R Routers or Bridges Edge Routers or Bridges R R • IP Switches use same routing technology as routers • Switch controllers communicate with edge routers as peers • Sustained IP flows bypass the controller through low latency ATM switch hardware • ATM links interconnect IP Switches 國立清華大學資訊系黃能富教授 13

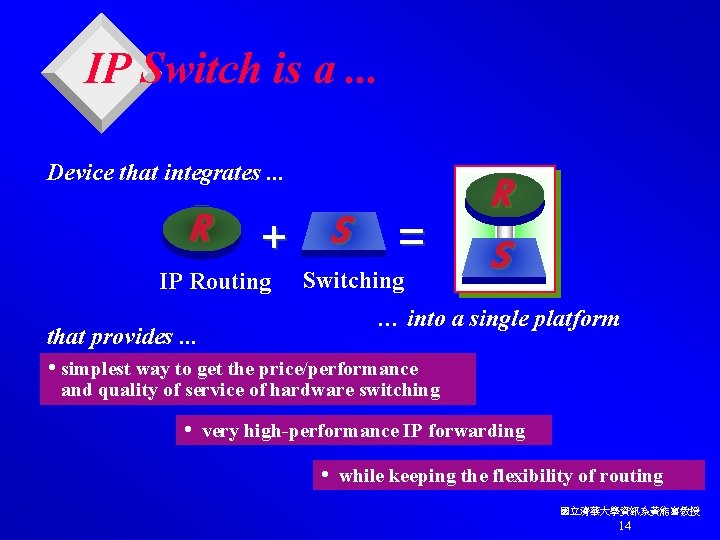
IP Switch is a. . . Device that integrates. . . R + S IP Routing = Switching R S … into a single platform that provides. . . • simplest way to get the price/performance and quality of service of hardware switching • very high-performance IP forwarding • while keeping the flexibility of routing 國立清華大學資訊系黃能富教授 14

IP Switching Technology IP Switch Gateway IP Switch R IP Switch Controller ATM Links S Legacy LANs or WANs ATM Switch with IP Switching Code IP Router with IP Switching enhancements IP Switch Host Driver 國立清華大學資訊系黃能富教授 15

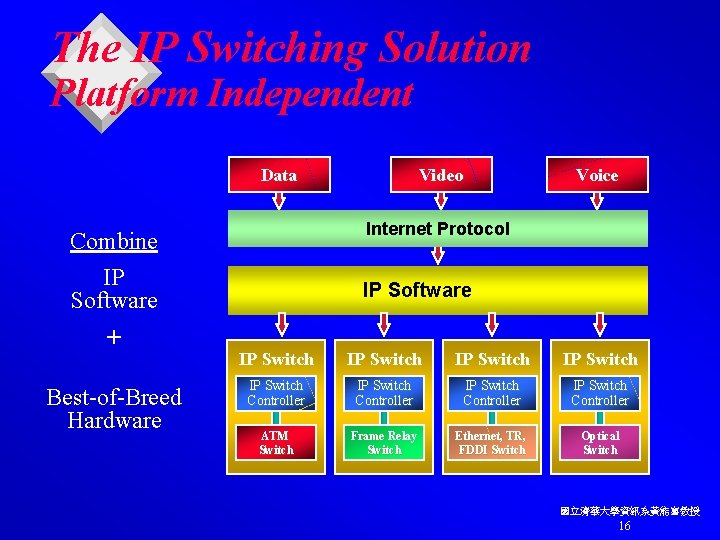
The IP Switching Solution Platform Independent Data Best-of-Breed Hardware Voice Internet Protocol Combine IP Software + Video IP Software IP Switch IP Switch Controller ATM Switch Frame Relay Switch Ethernet, TR, FDDI Switch Optical Switch 國立清華大學資訊系黃能富教授 16

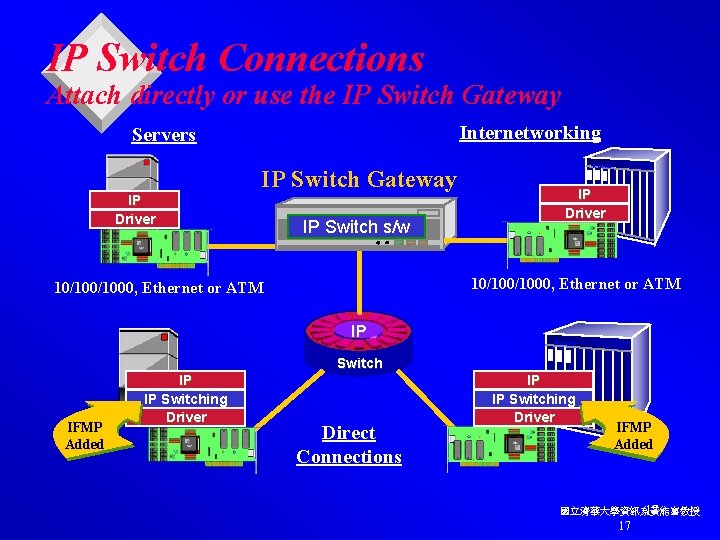
IP Switch Connections Attach directly or use the IP Switch Gateway Internetworking Servers IP Driver IP Switch Gateway IP Switch s/w Router IP Driver 10/100/1000, Ethernet or ATM IP Router Switch IFMP Added IP IP Switching Driver Direct Connections IP IP Switching Driver IFMP Added 國立清華大學資訊系黃能富教授 17 17

IP Switching Protocols R S Upstream Node IFMP General Switch Management Protocol (GSMP) l. Simple protocol that provides call setup, tear-down, and call status l. Supported on ATM Switch l. Supported on IP Switch Controller GSMP Downstream Node IFMP IP Flow Management Protocol (IFMP) l. Protocol between multiple IP Switches or hosts l. Protocol used to send flow redirection messages 國立清華大學資訊系黃能富教授 18

IP Switch Operation Initial Path v IP packets are forwarded hop-by-hop using a default virtual channel (VC). v. ATM cells are reassembled into IP packets at each hop. v. The IP Switch Controller makes a flow classification decision according to the IP packets. IP Switch Controller Direct Host ATM Node Gateway Upstream Node Œ ATM Cells ATM Fabric IP Switch Downstream Node ATM Cells 國立清華大學資訊系黃能富教授 19

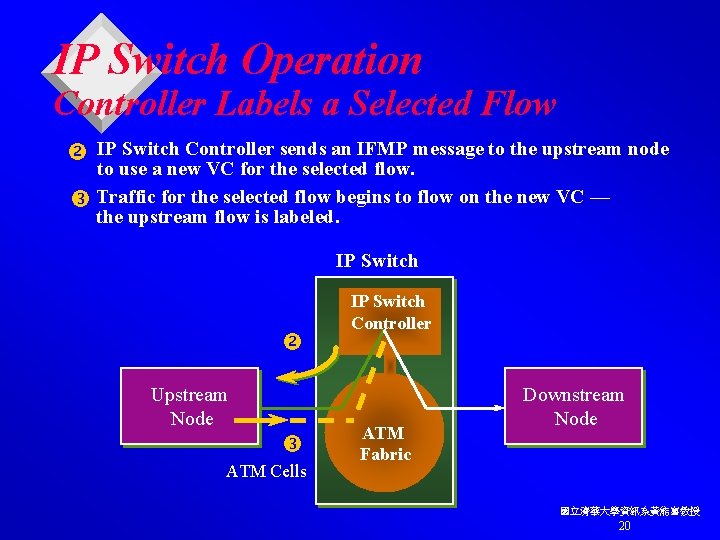
IP Switch Operation Controller Labels a Selected Flow IP Switch Controller sends an IFMP message to the upstream node to use a new VC for the selected flow. Traffic for the selected flow begins to flow on the new VC — the upstream flow is labeled. IP Switch Upstream Node ATM Cells IP Switch Controller ATM Fabric Downstream Node 國立清華大學資訊系黃能富教授 20

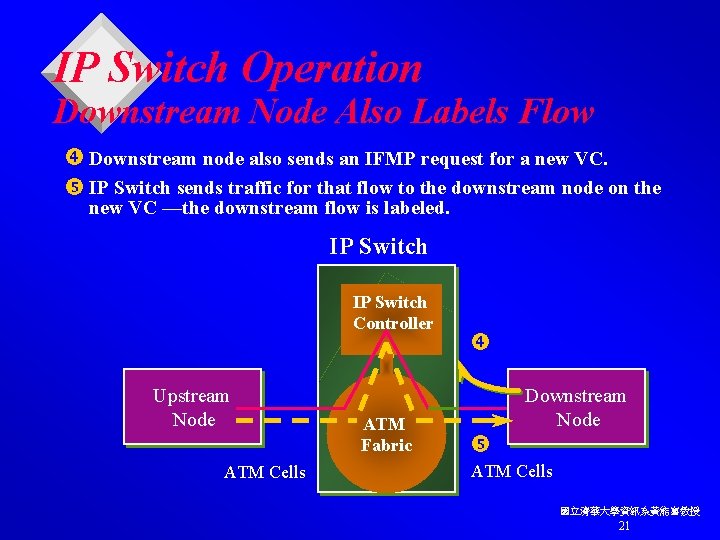
IP Switch Operation Downstream Node Also Labels Flow Downstream node also sends an IFMP request for a new VC. IP Switch sends traffic for that flow to the downstream node on the new VC —the downstream flow is labeled. IP Switch Controller Upstream Node ATM Cells ATM Fabric Downstream Node ATM Cells 國立清華大學資訊系黃能富教授 21

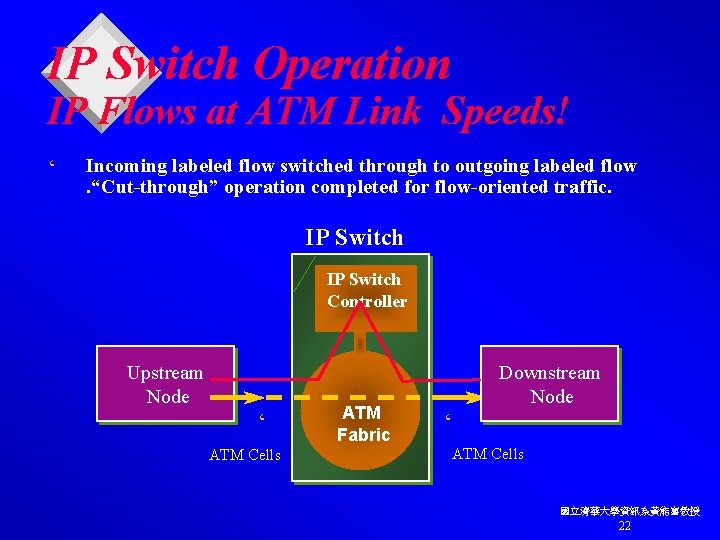
IP Switch Operation IP Flows at ATM Link Speeds! ‘ Incoming labeled flow switched through to outgoing labeled flow. “Cut-through” operation completed for flow-oriented traffic. IP Switch Controller Upstream Node ‘ ATM Cells ATM Fabric Downstream Node ‘ ATM Cells 國立清華大學資訊系黃能富教授 22

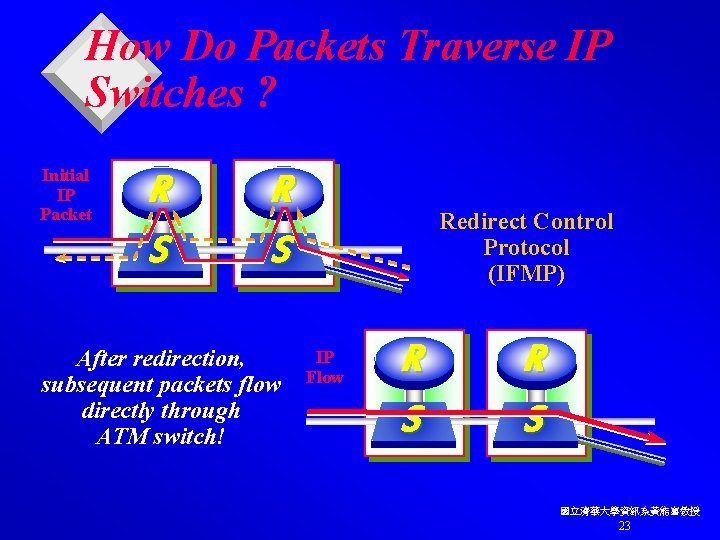
How Do Packets Traverse IP Switches ? Initial IP Packet R S After redirection, subsequent packets flow directly through ATM switch! Redirect Control Protocol (IFMP) IP Flow R S 國立清華大學資訊系黃能富教授 23

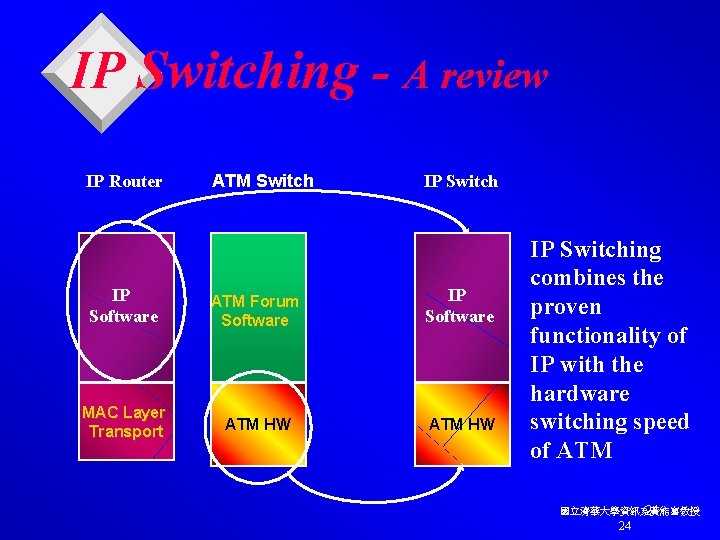
IP Switching - A review IP Router ATM Switch IP Software ATM Forum Software IP Software MAC Layer Transport ATM HW IP Switching combines the proven functionality of IP with the hardware switching speed of ATM 國立清華大學資訊系黃能富教授 24 24

Flow-Oriented Traffic v Flows consist of multiple, similar packets, for example, the same source/destination addresses, type of service, protocol v Long-lived flows are ideal for cut-through switching v Short-lived transactions are ideal for datagram forwarding v Over 90% of bytes can be switched, less than 10% routed! Flow-Oriented Traffic • • • File transfer (FTP) Telnet HTTP Web image downloads Multimedia audio/video Short-Lived Traffic • • • Name look-ups (DNS) Network Time Protocol E-mail (SMTP) Post Office Protocol (POP) SNMP 國立清華大學資訊系黃能富教授 25

IP Switching Protocols v. IFMP ( IP Flow Management Protocol ) Two associated RFCs l RFC 1953 specifies IFMP l RFC 1954 provides transmission specifics l v. GSMP (General Switch Management Protocol) Between the controller and the Switch l Call Setup and tear down l Add and delete leaves in point-to-multipoint connection l manage switch ports l configuration and statistics l 國立清華大學資訊系黃能富教授 26

Tag Switching Outline v. Tag Switching Overview v. Tag Switching Components v. Tag Distribution Protocol 國立清華大學資訊系黃能富教授 27

Tag Switching Overview v Tag Switching fuses the intelligence of routing with the performance of switching to scale existing networks to meet future growth demands. v Tag Switching uses a form of label swapping across packet or cell-based networks. l units of data (packet or cell) carry a short, fixed length label (tag) that tells switching nodes how to process the data. v A Tag Switching internetwork consists of the following elements : l Tag edge routers l Tag switches l Tag Distribution Protocol (TDP) 國立清華大學資訊系黃能富教授 28

Fusing Routing and Switching Cisco Introduces Tag Switching + = v. Combining l Layer 3 routing—scalability and flexibility l Layer 2 switching—high performance of ATM v. Leveraging l Cisco’s existing core router and ATM switch platforms 國立清華大學資訊系黃能富教授 29

Tag Switching Cisco Technology v. Enhancement to Cisco’s IOS ™ IOS Tag Switching l Common thread for all Cisco routing and switching platforms v. Software-only upgrade to existing Cisco products l Investment protection for existing Cisco customers l Migration options for new customers 國立清華大學資訊系黃能富教授 30

Tag Switching Overview Tag Distribution Protocol (TDP) Tag Edge Routers (apply/strip Tag) Tag Switches (ATM Switch or Router) 國立清華大學資訊系黃能富教授 31

Tag Switching Internetwork Elements v Tag Edge Routers Tag edge routers are full-function Layer 3 routing devices located at the edge of a tag switching network l They apply tags to incoming packets and remove tags from outgoing packets. l They also apply value-added Layer 3 services, such as security, accounting, and Qo. S classification. l v Tag Switches Tag switches are the core of the tag switching internetwork. l They switch tagged packets or cells based on the tags. l Tag switches may also support full layer 3 routing or layer 2 switching. l v Tag Distribution Protocol (TDP) l TDP is used to distribute tag information between devices in a tag switching internetwork. 國立清華大學資訊系黃能富教授 32

Tag Edge Routers Tag bindings v Full-function Layer 3 routers l Security l Quality of Service l Traffic management l Net. Flow switching • Per destination prefix Specified paths for traffic engineering • Per QOS class • Per source/destination flow v Apply tags to packets based on Tag Information Base (TIB) v Variety of link types l Packet-over-SONET, HSSI l ATM l Future FE/GB Ethernet v Cisco IOS upgrade for existing Cisco routers 國立清華大學資訊系黃能富教授 33

Tag Switches v Routers or ATM switches v Tags is placed in the VPI/VCI fields of cells Switching on Tags • Simplified lookup on tag • Tag label swap on forwarding • ATM switches performing tag switching do not need to handle high call setup rates. v Multiple routing protocols l OSPF, IS-IS, EIGRP, BGP v Multiprotocol support 國立清華大學資訊系黃能富教授 34

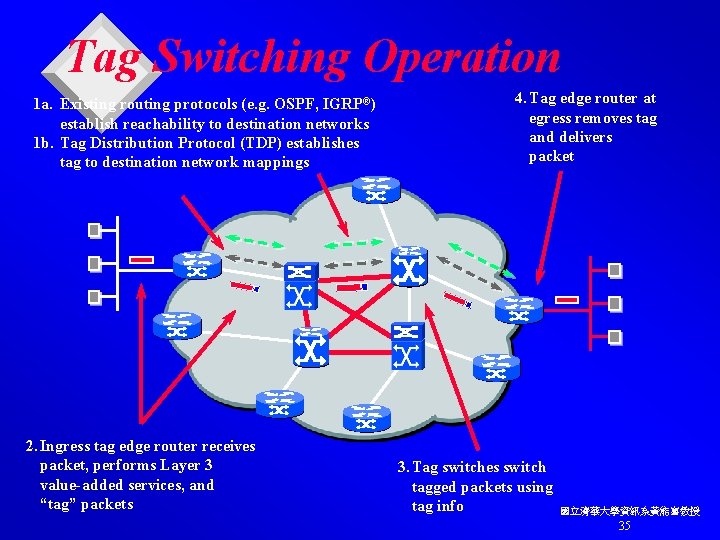
Tag Switching Operation 1 a. Existing routing protocols (e. g. OSPF, IGRP®) establish reachability to destination networks 1 b. Tag Distribution Protocol (TDP) establishes tag to destination network mappings 2. Ingress tag edge router receives packet, performs Layer 3 value-added services, and “tag” packets 4. Tag edge router at egress removes tag and delivers packet 3. Tag switches switch tagged packets using tag info 國立清華大學資訊系黃能富教授 35

Tag Switching Operations v Tag edge routers and tag switches use standard routing protocols (BGP, OSPF) to identify routes through the network. v Edge routers and switches use table generated by the routing protocols to assign and distribute tag information via the TDP. Edge routers receives the TDP information and build a forwarding database which makes use of the tags. v When an edge router receives a packet forwarding across the tag network, it analyzes the network layer header, selects a route for the packet from its routing tables, applies a tag, and forwards the packet to the next hop tag switch. 國立清華大學資訊系黃能富教授 36

Tag Switching Operations v. The tag switch receives the tagged packet and switches the packet based solely on the tag, without re-analyzing the network layer header. v. The packet reaches the edge router at the egress point of the network, where the tag is stripped off and the packet delivered. 國立清華大學資訊系黃能富教授 37

Tag Switching Components v. Tag Switching consists of two components: forwarding and control. v. Forwarding Component l The forwarding component uses the tag information (tags) carried by packets and the tag forwarding information maintained by a tag switch to perform packet forwarding. v. Control Component l The control component is responsible for maintaining correct tag forwarding information among a group of interconnected tag switches. 國立清華大學資訊系黃能富教授 38

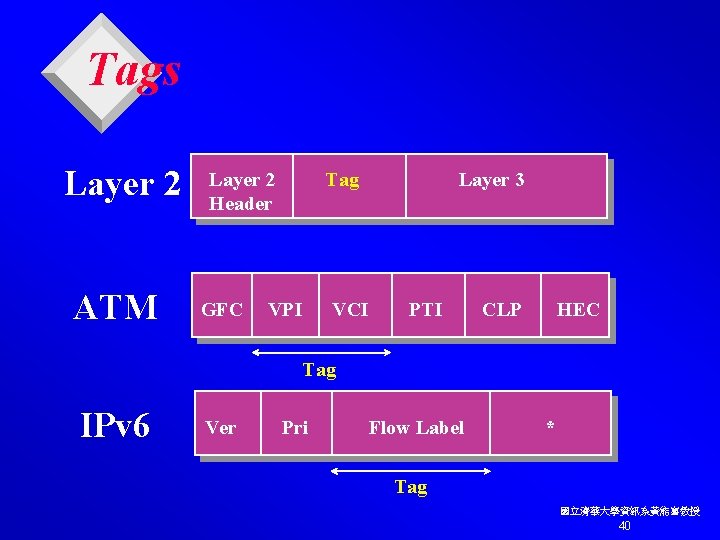
Forwarding Component v. Label swapping is the fundamental forwarding paradigm employed by tag switching. v. Tag switching requires a tag to be carried in each packet. v The tag can be carried in a variety of ways: l as a small “shim” tag header inserted between the layer 2 and the Network Layer headers. l as part of the layer 2 header, if the layer 2 header provides adequate semantics (e. g. , Frame Relay, or ATM). l as part of the Network Layer header (e. g. , using the Flow Label field in the IPv 6 with appropriately modified semantics). 國立清華大學資訊系黃能富教授 39

Tags Layer 2 ATM Layer 2 Header GFC Tag VPI Layer 3 VCI PTI CLP HEC Tag IPv 6 Ver Pri Flow Label * Tag 國立清華大學資訊系黃能富教授 40

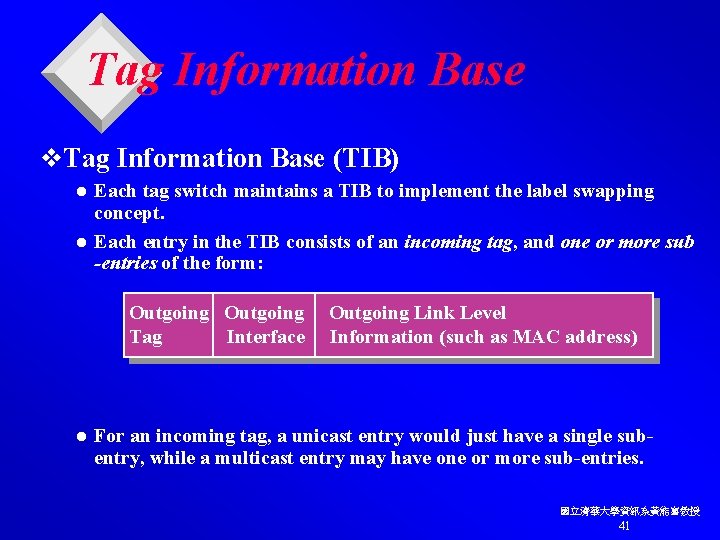
Tag Information Base v. Tag Information Base (TIB) Each tag switch maintains a TIB to implement the label swapping concept. l Each entry in the TIB consists of an incoming tag, and one or more sub -entries of the form: l Outgoing Tag Interface l Outgoing Link Level Information (such as MAC address) For an incoming tag, a unicast entry would just have a single subentry, while a multicast entry may have one or more sub-entries. 國立清華大學資訊系黃能富教授 41

Forwarding Algorithm v When a packet with a tag is received by a tag switch, the switch uses the tag as an index in its TIB. v If the switch finds an entry with the incoming tag equals to the tag carried in the packet, the switch replaces the tag in the packet with the outgoing tag, replaces the link level information (e. g. MAC address) in the packet with the outgoing link level information, and forwards the packet over the outgoing interface. v If no entry is found, or the entry exists with empty outgoing tag , and the entry does not indicate local delivery to the switch, the switch may either (a) discard the packet, or (b) strip the tag information, and submit the packet for network layer processing. 國立清華大學資訊系黃能富教授 42

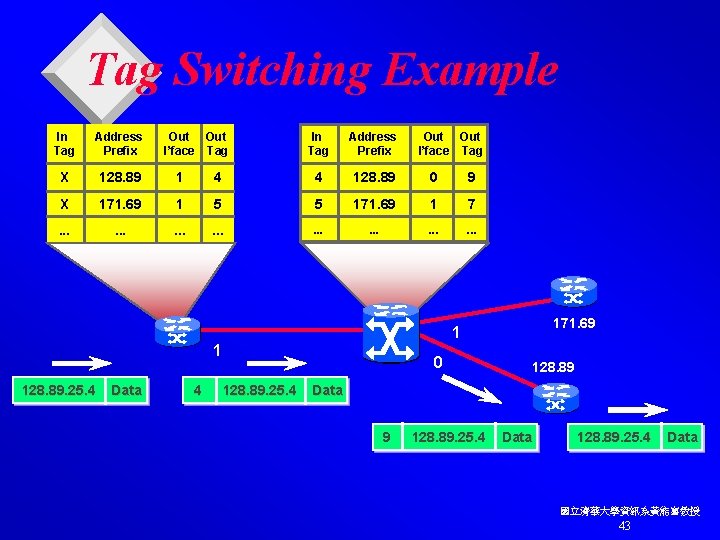
Tag Switching Example In Tag Address Prefix Out I’face Tag In Tag Address Prefix X 128. 89 1 X 171. 69 . . . Out I’face Tag 4 4 128. 89 0 9 1 5 5 171. 69 1 7 . . . . 171. 69 1 1 128. 89. 25. 4 Data 4 0 128. 89. 25. 4 128. 89 Data 9 128. 89. 25. 4 Data 國立清華大學資訊系黃能富教授 43

Advantages of the Forwarding Algorithm v. Advantages of the forwarding algorithm: l The forwarding decision is based on the exact match algorithm using a fixed length, fairly short tag as an index. This enables a simplified forwarding procedure, relative to longest match forwarding traditionally used at the network layer. l The same forwarding algorithm applies to both unicast and multicast. l The forwarding procedure is decoupled from the control component of tag switching. New routing (control) functions can readily be deployed without disturbing the forwarding paradigm. 國立清華大學資訊系黃能富教授 44

Control Component v Essential to tag switching is the notion of binding between a tag and Network Layer routing (routes). v The control component is responsible for creating tag bindings, and distributing the tag binding information among tag switches. v Creating a tag binding involves allocating a tag, and then binding a tag to a route. v The distribution of tag binding information among tag switches could be accomplished via several options piggybacking on existing routing protocols l using a separate Tag Distribution Protocol (TDP) l 國立清華大學資訊系黃能富教授 45

Characteristics of the Control Component v Creation of tag binding is driven primarily by control traffic rather by data traffic. minimizes the amount of control traffic needed to distribute tag binding. l independent and insensitive to the data traffic profile/pattern. l tags are precomputed (prebound) before data traffic arrives. l v Supporting wide range of forwarding granularities: A tag could be associated to a group of routes. l A tag could also be bound to an individual flow (e. g. , an RSVP flow) l A tag could be bound to a multicast tree. l 國立清華大學資訊系黃能富教授 46

Control Component Modules v. Control component is organized as a collection of modules designed to support a particular routing function l Destination-based routing, Hierarchy of routing knowledge, Multicast, Quality of service, Flexible routing (explicit routes) v. Destination-based routing A router makes a forwarding decision based on the destination address carried in a packet and the information stored in the Forwarding Information Base (FIB, or routing table). l A router constructs its FIB by using the information it receives from routing protocols (e. g. , OSPF, BGP). l To support destination-based routing with tag switching, a tag switch, just like a router, participates in routing protocols, and constructs its FIB. 國立清華大學資訊系黃能富教授 l 47

Destination-based Routing v There are three permitted methods for tag allocation and TIB management: (a) downstream tag allocation, (b) downstream tag allocation on demand, and (c) upstream tag allocation. l In all cases, a switch allocates tags and binds them to address prefixes in its FIB. l v Downstream tag allocation The tag is generated and bound to a prefix by the switch at the downstream end of the link (with respect to the direction of data flow). l For each route in its FIB the switch allocates a tag, creates an entry in its TIB with the incoming tag set to the allocated tag, and then advertises the binding to other adjacent tag switches. l When a tag switch receives tag binding information for a route, and that information was originated by the next hop for that route, the switch places the tag into the outgoing tag of the TIB entry associated with the route. l 國立清華大學資訊系黃能富教授 48

Downstream Tag Allocation 1. Establish the FIB via existing routing protocols (e. g. OSPF, IGRP®) In Tag Address Prefix Out I’face Tag In Tag Address Prefix X 128. 89 1 X 171. 69 . . . Out I’face Tag 4 4 128. 89 0 9 1 5 5 171. 69 1 7 . . . . 1 Upstream 0 1 Downstream 171. 69 128. 89 2 a. Downstream Switch determines the Tag for each prefix (route), 2 b. Deliver the Tag information to upstream switches. 國立清華大學資訊系黃能富教授 49

Destination-based Routing v Downstream tag allocation on demand On demand allocation means that tags will only be allocated and distributed by the downstream switch when it is requested to do so by the upstream switch. l Most useful in ATM networks. l For each entry in its FIB, the switch identifies the next hop for that route. It then issues a request (via TDP) to next hop for a tag binding. The rest operations are similar to downstream allocation. l v Upstream tag allocation Tags are allocated and bound at the upstream end of the link. l For each route in its FIB whose next hop is reachable via one of its interfaces, the switch allocates a tag, creates an entry in its TIB with the outgoing tag set to the allocated tag, and then advertises to next hop (via TDP) the binding l The next hop switch places the tag into the incoming tag of the TIB entry. 國立清華大學資訊系黃能富教授 l 50

Control Component Modules v Hierarchy of routing knowledge l Tag switching allows complete decoupling of interior and exterior routing. Only border tag switches have to maintain exterior routing information. v Multicast l We need to associate a tag with a multicast tree. v Quality of service Packets are classified into classes with different Qo. S requirements. l A tag corresponding to a traffic class is applied to the packet. l v Flexible routing (explicit routes) Explicit routes provide forwarding paths that are different from the paths determined by destination-based routing. l Allow TDP to carry information about an explicit route. l 國立清華大學資訊系黃能富教授 51

Tag Distribution Protocol v. TDP provides the means for tag switches to distribute, request, and release tag binding information for multiple network layer protocols. v. TDP is a two party protocol that requires a connection oriented transport layer with guaranteed sequential delivery. v. Currently TCP is used. v. The TDP specification defines its state transition table and message format. 國立清華大學資訊系黃能富教授 52

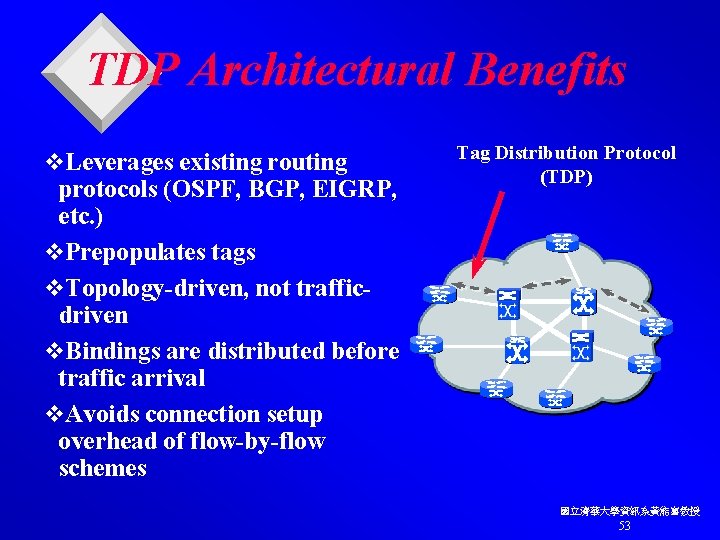
TDP Architectural Benefits v. Leverages existing routing protocols (OSPF, BGP, EIGRP, etc. ) v. Prepopulates tags v. Topology-driven, not trafficdriven v. Bindings are distributed before traffic arrival v. Avoids connection setup overhead of flow-by-flow schemes Tag Distribution Protocol (TDP) 國立清華大學資訊系黃能富教授 53

Switched Router Backbones Without Tag Switching With Tag Switching v Layer 2 ATM core with routers u. Tag switching core with tag routers v ATM are transparent u. Tag switches are routing peers v All routers are neighbors u. All packets tagged v Signaling performance issues u. Minimizes signaling overhead v Scalability is limited u. Increased scalability 國立清華大學資訊系黃能富教授 54

Router Backbones—Internet v Software upgrade to Load balancing existing routers (e. g. , 75 xx) v Enables new traffic management capabilities Load balancing l Enhanced QOS l v High performance links including Packet-over-SONET (POS) and ATM v Extensible to multigigabit routing platforms 國立清華大學資訊系黃能富教授 55

Tag Switching and ATM Services Co-Existing on Same Platform! v. ATM services for real-time services PNNI/UNI signaling l Voice trunking l Circuit Emulation (CES) IP IP l ATM • Tag switching for data traffic FR FR IP l Offloads signaling-intensive traffic l Reduces call set-up dependencies 國立清華大學資訊系黃能富教授 56

Tag Switching vs. Other Approaches IP Switching (Ipsilon) Tag Switching Connection Setup—Per Flow Tag Prepopulated Gateway v Layer 3 gateway in data path l Route processor out of data path v Faster path after flow classified l All packets use fast path v Latency may exceed flow duration l Tag are prepopulated v Connection setup per flow source/destination v Excessive signaling overhead v Support IP only v Not using ATM Forum standard l Tag assigned per destination l Leverages routing protocols l Multiprotocol support l Using ATM Forum standard 國立清華大學資訊系黃能富教授 57

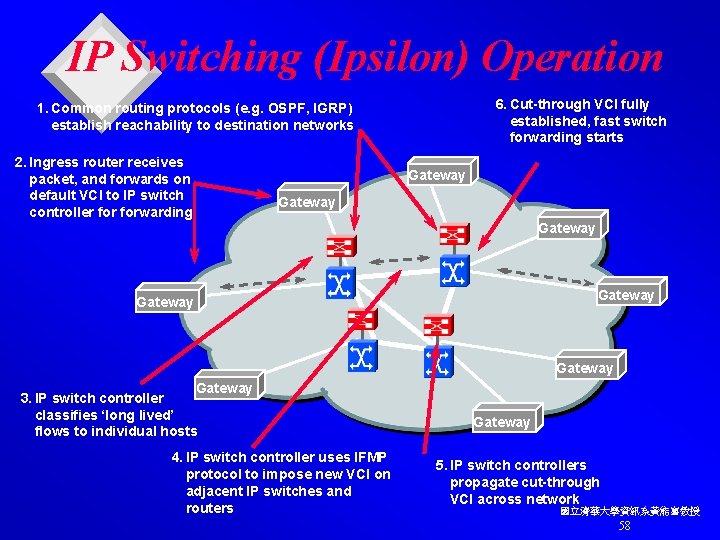
IP Switching (Ipsilon) Operation 6. Cut-through VCI fully established, fast switch forwarding starts 1. Common routing protocols (e. g. OSPF, IGRP) establish reachability to destination networks 2. Ingress router receives packet, and forwards on default VCI to IP switch controller forwarding Gateway Gateway 3. IP switch controller classifies ‘long lived’ flows to individual hosts 4. IP switch controller uses IFMP protocol to impose new VCI on adjacent IP switches and routers Gateway 5. IP switch controllers propagate cut-through VCI across network 國立清華大學資訊系黃能富教授 58

Tag Switching Benefits l. Multi-protocol l. Provides support load balancing l. Enhanced QOS l. Improves scalability 國立清華大學資訊系黃能富教授 59

Tag Switching Advantages v. Scalability Destination tagging l Topology-driven, not traffic-driven l No flow VC management overhead l v. High performance Utilizes ATM core for tag switching l Simplified forwarding for future gigabit interfaces l v. Evolution Existing and new products that leverage standard protocols l Open, emerging IETF Multi-Protocal Label Swapping standard l 國立清華大學資訊系黃能富教授 60

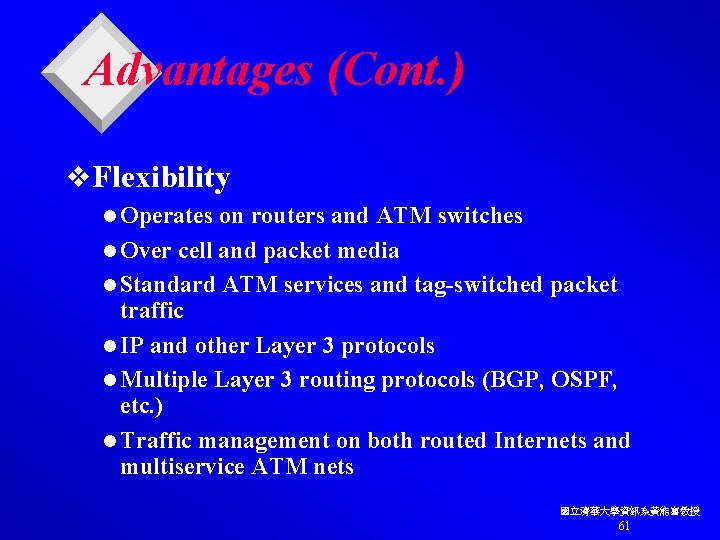
Advantages (Cont. ) v. Flexibility l Operates on routers and ATM switches l Over cell and packet media l Standard ATM services and tag-switched packet traffic l IP and other Layer 3 protocols l Multiple Layer 3 routing protocols (BGP, OSPF, etc. ) l Traffic management on both routed Internets and multiservice ATM nets 國立清華大學資訊系黃能富教授 61

Multi-Protocol Label Switching (MPLS) Outline v. Prior Work v. MPLS Overview v. MPLS Framework v. MPLS Architecture v. Conclusion 國立清華大學資訊系黃能富教授 62

Prior Work v. Tag Switching (Cisco) v. Aggregate Route-Based IP Switching (ARIS, IBM) v. IP Navigator v. IFMP-IP Switching (Ipsilon) v. Cell Switching Router (CSR, Toshiba) 國立清華大學資訊系黃能富教授 63

Prior Work v Tag switching is based on the control-driven approach. The set up of LSPs (Label Switched Paths) closely follows control messages such as routing updates and RSVP messages. v Aggregate route-based IP switching (ARIS) is also based on the control-driven approach. Very similar to tag switching. ARIS introduces the concept of an “egress identifier” (FECs) to express the granularity of LSPs. v IP Navigator is again a control-driven protocol. Use OSPF as the internal routing protocol used within a routing domain. Explicit routing is used to setting up the VCs. 國立清華大學資訊系黃能富教授 64

Prior Work v Ipsilon Flow Management Protocol (IFMP) is a traffic driven protocol. When the number of packets from a flow exceeds a predertermined threshold, the controller uses IFMP to set up an LSP for the particular flow. v Cell switch router (CSR) proposal is similar to IP switching. CSR is primarily designed as a device for interconnecting ATM clouds. Within an LIS (logical IP subnet), ATM forum standards are used to connection hosts and switched together. v Multiple LISs are then interconnected with CSRs that are capable of running both IP forwarding and cell forwarding. The setup of LSPs is data-driven for best effort traffic and RSVP-driven for flows that require resource reservation. 國立清華大學資訊系黃能富教授 65

MPLS Overview v The IETF MPLS working group (created in 1997) is to standardize a base technology that integrates the label swapping forwarding paradigm with network layer routing. v RFC 3812 v Current status: Framework document have been published which discuss technical issue and requirements for the MPLS. l Architecture document have been published which contain a draft protocol architecture for MPLS. The proposed architecture is based on the MPLS framework document. l v Cisco is the major contributor to the MPLS working group. l substitute “Label” for “Tag” in Tag Switching @ MPLS 國立清華大學資訊系黃能富教授 66

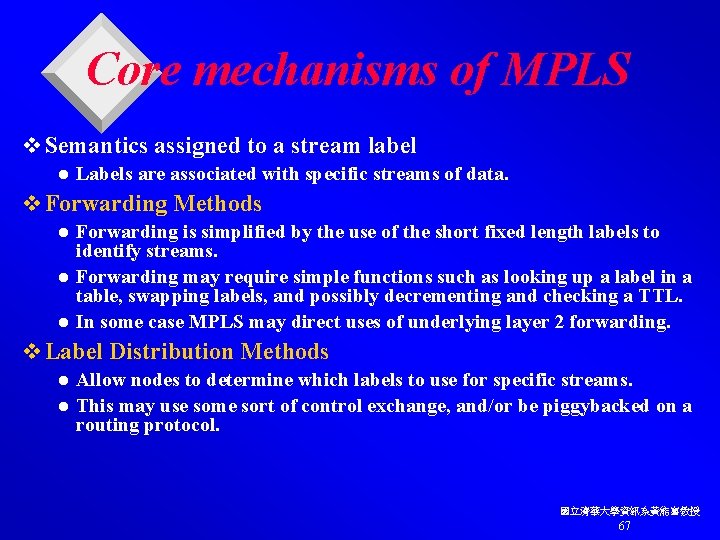
Core mechanisms of MPLS v Semantics assigned to a stream label l Labels are associated with specific streams of data. v Forwarding Methods Forwarding is simplified by the use of the short fixed length labels to identify streams. l Forwarding may require simple functions such as looking up a label in a table, swapping labels, and possibly decrementing and checking a TTL. l In some case MPLS may direct uses of underlying layer 2 forwarding. l v Label Distribution Methods Allow nodes to determine which labels to use for specific streams. l This may use some sort of control exchange, and/or be piggybacked on a routing protocol. l 國立清華大學資訊系黃能富教授 67

Motivation for MPLS v Benefits relative to use of a Router Core l l l l Simplified forwarding Efficient explicit routing Traffic reengineering Qo. S routing Complex mappings from IP packet to forwarding equivalence class (FEC) Partitioning of functionality Single forwarding paradigm with several level differentiation v Benefits relative to use of an ATM or Frame Relay Core Scaling of the routing protocol l Common operation over packet and cell media l Easier Management l Elimination of the ‘routing over Large Clouds’ issue l 國立清華大學資訊系黃能富教授 68

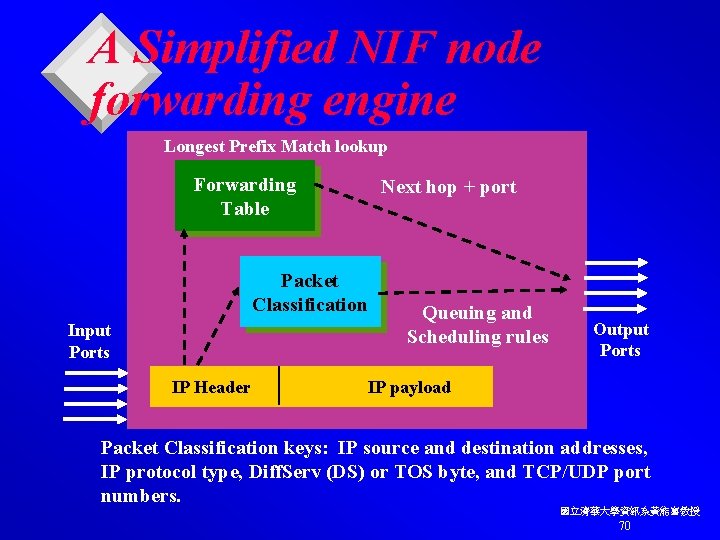
Native IP Forwarding v The term IP routing is often applied to both the packet forwarding and route determination process in an IP network. v To avoid confusion, we use Native IP forwarding (NIF) to specifically refer to hop-by-hop, destination-based packet forwarding. v IP routing for references to the topology and path discovery processes. v Each packet’s next hop and output port are determined by a longest-prefix-match forwarding table lookup (Destination IP address). v Additional packet classification may also be performed to derive output port queuing and scheduling rules. 國立清華大學資訊系黃能富教授 69

A Simplified NIF node forwarding engine Longest Prefix Match lookup Forwarding Table Next hop + port Packet Classification Input Ports IP Header Queuing and Scheduling rules Output Ports IP payload Packet Classification keys: IP source and destination addresses, IP protocol type, Diff. Serv (DS) or TOS byte, and TCP/UDP port numbers. 國立清華大學資訊系黃能富教授 70

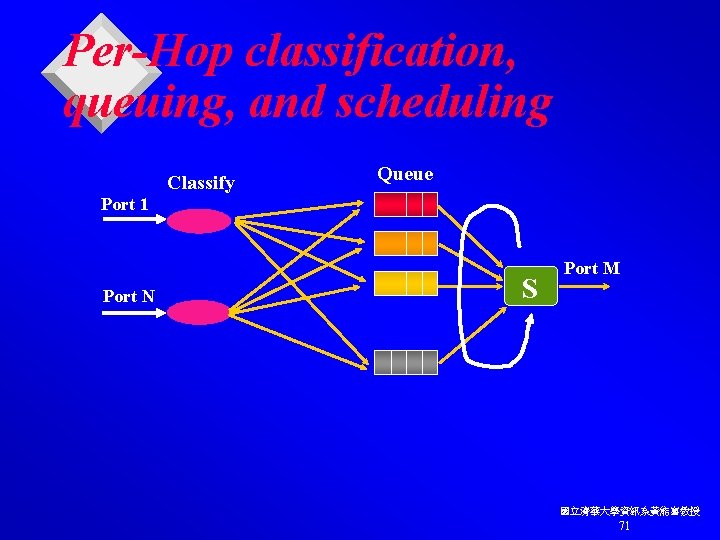
Per-Hop classification, queuing, and scheduling Classify Queue Port 1 Port N S Port M 國立清華大學資訊系黃能富教授 71

A Simplified LSR forwarding engine Switching Table Next hop + port Queuing and Scheduling rules Output Ports Input Ports MPLS label MPLS payload 國立清華大學資訊系黃能富教授 72

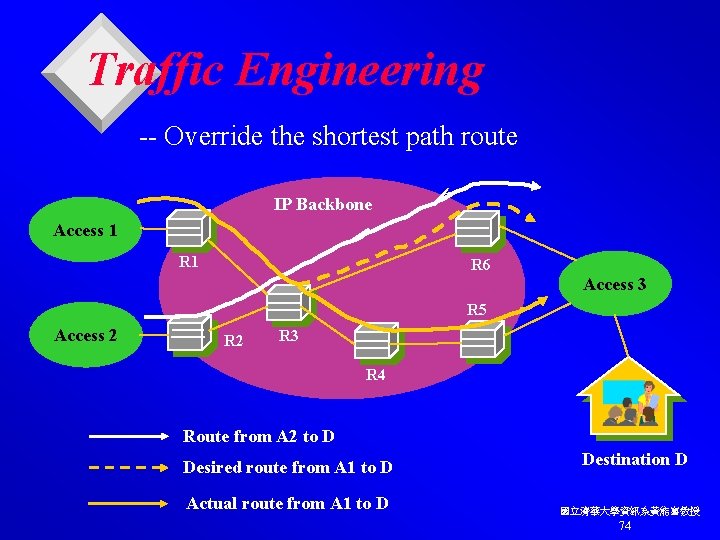
Traffic Engineering v Conventional IP routing attempts to find and follow the shortest path between a packet’s current location and its intended destination. v This leads to “hot spots” and packet loss rates, latency, and jitter increase as the average load on a router rises. v Solutions: (1) Faster routers, (2) Alternate routes. v For example. v Routing policy may also require traffic engineering. For example, the external link between R 6 and A 3 may have been funded solely by A 2 and A 3. Therefore, A 1’s traffic must not be allowed to traverse it. 國立清華大學資訊系黃能富教授 73

Traffic Engineering -- Override the shortest path route IP Backbone Access 1 R 6 Access 3 R 5 Access 2 R 3 R 4 Route from A 2 to D Desired route from A 1 to D Actual route from A 1 to D Destination D 國立清華大學資訊系黃能富教授 74

Signaling and Provisioning v The term signaling is typically applied when network (re)configuration can be requested by users at any time and achieved within milliseconds or seconds. v When the reaction time for (re)configuration becomes measured in minutes or hours, it is often referred to as provisioning. v In either case, the (re)configuring action involves establishing (or modifying) information used by routers or switches to control their forwarding actions, including forwarding (routing) information, classification rules, and/or queuing and scheduling parameters. v OSPF and BGP (Border Gateway Protocol) represent a form of free-running signaling. RSVP for signaling additional Qo. S 國立清華大學資訊系黃能富教授 informtion along existing paths. 75

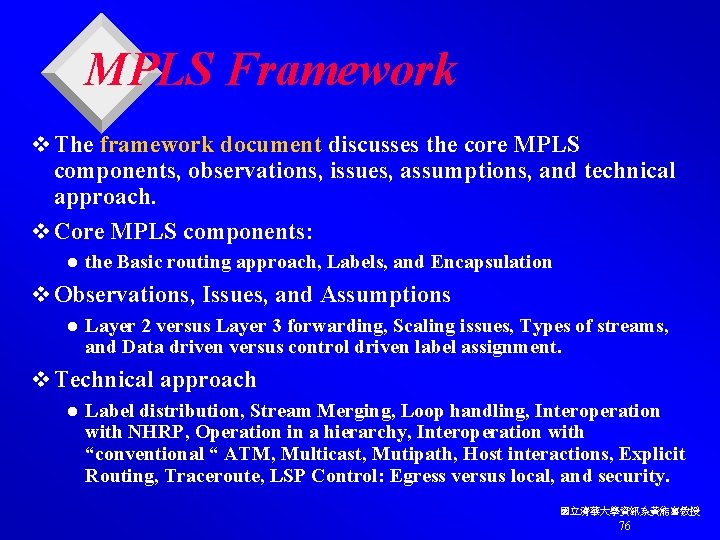
MPLS Framework v The framework document discusses the core MPLS components, observations, issues, assumptions, and technical approach. v Core MPLS components: l the Basic routing approach, Labels, and Encapsulation v Observations, Issues, and Assumptions l Layer 2 versus Layer 3 forwarding, Scaling issues, Types of streams, and Data driven versus control driven label assignment. v Technical approach l Label distribution, Stream Merging, Loop handling, Interoperation with NHRP, Operation in a hierarchy, Interoperation with “conventional “ ATM, Multicast, Mutipath, Host interactions, Explicit Routing, Traceroute, LSP Control: Egress versus local, and security. 國立清華大學資訊系黃能富教授 76

Core MPLS Components v. The basic routing approach Routing is accomplished through the use of standard L 3 routing protocols (e. g. OSPF and BGP). l The information maintained by the L 3 routing protocols is then used to distribute labels to neighboring nodes that are used in the forwarding of packets. l v. Labels l Label semantics, Label granularity, Label assignment, Label stack and forwarding operations. v. Label semantics The label is nothing more than a shorthand for an aggregate stream of user data. l The meaning of the label is a strictly local issue between two 國立清華大學資訊系黃能富教授 neighboring nodes. 77 l

Labels With this interpretation: (1) MPLS could be employed between any two neighboring nodes forwarding of data between those nodes, even if no other nodes in the network participate in MPLS. (2) When MPLS is used between more than two nodes, then the operation between any two neighboring nodes could be interpreted as independent of the operation between any other pair of nodes. l v Label granularity The device which will be using the label to forward packets will be forwarding all packets with the same label in the same way. l A Forwarding Equivalence Class (FEC) is a set of L 3 packets which are all forwarded in the same manner by a particular Label Switching Router (LSR). l 國立清華大學資訊系黃能富教授 78

Labels l For unicast IP traffic, the granularity of a label allows various levels of aggregation in a Label Information Base (LIB). l For IP multicast, the natural binding of a label would be to a multicast tree, or rather to the branch of a tree which extends from a particular port. v. Label assignment l Label assignment involves allocating a label, and then binding a label to a route. l Label assignment can be driven by control traffic or data traffic. (discussed later. ) l Label withdrawal is primarily a matter of garbage collection, that is collecting up unused labels so that they 國立清華大學資訊系黃能富教授 may be reassigned. 79

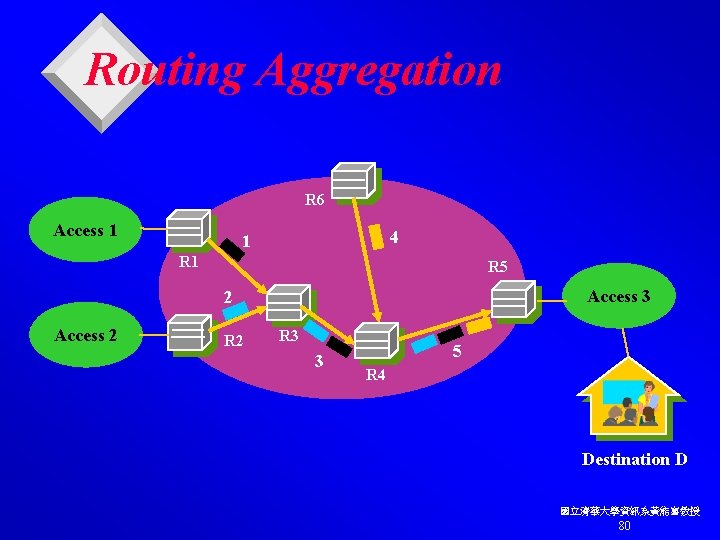
Routing Aggregation R 6 Access 1 4 1 R 5 Access 3 2 Access 2 R 3 3 5 R 4 Destination D 國立清華大學資訊系黃能富教授 80

Forwarding Component v. Label Stack and Forwarding Operations l The basic forwarding operation consists of looking up the incoming label to determine the outgoing label, encapsulation, port, and any additional information which may pertain to the stream such as a particular queue or other Qo. S related treatment. This operation is referred as label swap. l When a packet first enters an MPLS domain, the packet is associated with a label. It is referred as a label push. When a packet leaves an MPLS domain, the label is removed. It is referred as a label pop. l The label stack is useful within hierarchical routing domain. 國立清華大學資訊系黃能富教授 81

Encapsulation v Label-based forwarding makes use of various pieces of information, including a label or stack of labels, and possibly additional information such as a TTL field. v These information can be carried in several forms. v The term “MPLS encapsulation” is used to refer to whatever form is used to encapsulate the label information and information used for label based forwarding. v An encapsulation scheme may make use of the following fields: l label, TTL, class of service, stack indicator, next header type indicator, and checksum 國立清華大學資訊系黃能富教授 82

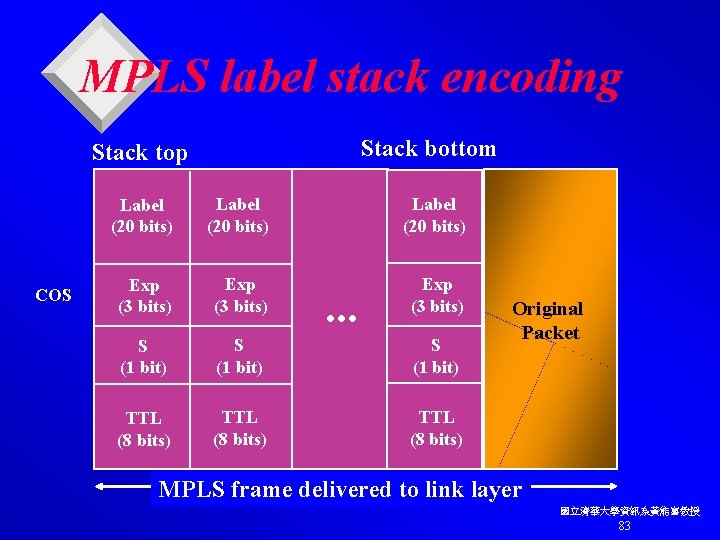
MPLS label stack encoding Stack bottom Stack top COS Label (20 bits) Exp (3 bits) S (1 bit) TTL (8 bits) . . . Original Packet MPLS frame delivered to link layer 國立清華大學資訊系黃能富教授 83

Label Assignment v. Topology driven (Tag) In response to normal processing of routing protocol control traffic l Labels are pre-assigned; no label setup latency at forwarding time. l v. Request driven (RSVP) In response to normal processing of request based control traffic l May require a large number of labels to be assigned. l v. Traffic driven (Ipsilon) The arrival of data at an LSR triggers label assignment and distribution. l Label setup latency; potential for packet reordering. l 國立清華大學資訊系黃能富教授 84

Label Distribution v. Explicit Label Distribution l Downstream label allocation » label allocation is done by the downstream LSR » most natural mechanism for unicast traffic l Upstream label allocation » label allocation is done by the upstream LSR » may be used for optimality for some multicast traffic l A unique label for an egress LSR within the MPLS domain » Any stream to a particular MPLS egress node could use the label of that node. 國立清華大學資訊系黃能富教授 85

Label Distribution v. Explicit Label Distribution Protocol (LDP) l Reliability : by transport protocol (TCP) or as part of LDP. l Separate routing computation and label distribution. v. Piggybacking on Other Control Messages l Use existing routing/control protocol for distributing routing/control and label information. l OSPF, BGP, RSVP, PIM l Combine routing and label distribution. v. Label purge mechanisms l By time out l Exchange of MPLS control packets 國立清華大學資訊系黃能富教授 86

Label Distribution Protocol v. LDP Peer: l Two LSRs that exchange label/stream mapping information via LDP v. LDP messages Discovery messages (via UDP) » announce and maintain the presence of LSR l Session messages » maintain session between LDP peers l Advertisement message » label operation (Label distribution) l Notification message » advisory information and signal error information » Error notification: signal fatal errors » Advisory notification: status of the LDP session or some previous 國立清華大學資訊系黃能富教授 message received from the peer. 87 l

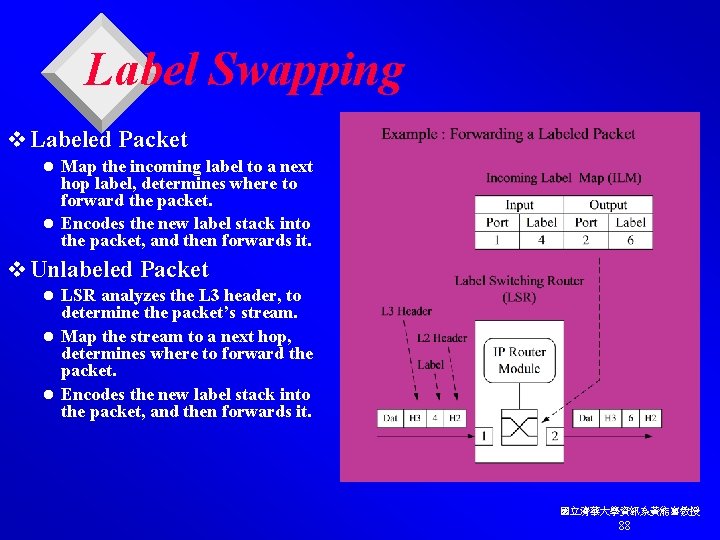
Label Swapping v Labeled Packet Map the incoming label to a next hop label, determines where to forward the packet. l Encodes the new label stack into the packet, and then forwards it. l v Unlabeled Packet LSR analyzes the L 3 header, to determine the packet’s stream. l Map the stream to a next hop, determines where to forward the packet. l Encodes the new label stack into the packet, and then forwards it. l 國立清華大學資訊系黃能富教授 88

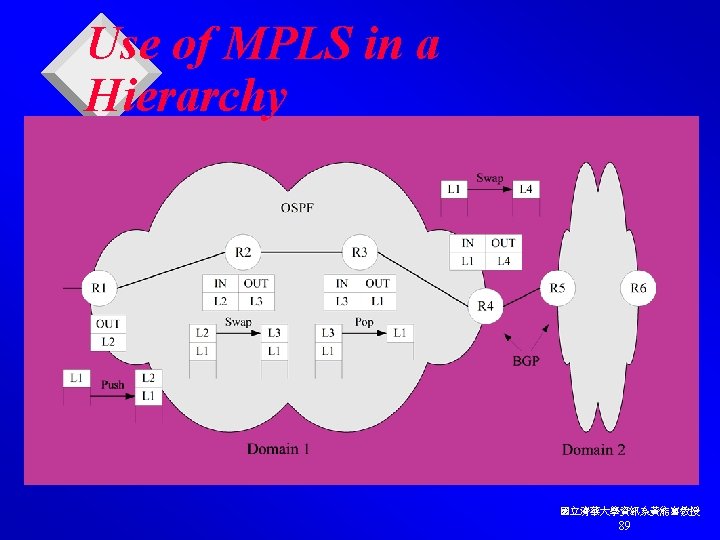
Use of MPLS in a Hierarchy 國立清華大學資訊系黃能富教授 89

Observations, Issues, and Assumptions v. Layer 2 versus layer 3 forwarding l MPLS uses L 2 forwarding as a way to provide simple and fast packet forwarding capability. l A node forwarding at L 3 must parse a (relatively) large header, and perform longest-prefix match to determine a forwarding path. l However, L 3 forwarding will be needed for a variety of reasons, including: » For scaling; to forward on a finer granularity than the labels can provide. » For security; to allow packet filtering at firewalls. » For forwarding at the initial router (when hosts don’t 國立清華大學資訊系黃能富教授 do MPLS). 90

Observations, Issues, and Assumptions v. Scaling issues l MPLS scalability is provided by two of the principles of routing. » Forwarding follows an inverted tree rooted at a destination » The number of destinations is reduced by routing aggregation. v. Types of streams Switched paths in the MPLS network can be of different types: » point-to-point, multipoint-to-point, point-to-multipoint, and multipoint-to-multipoint l The factors that determine which type of switched path is used are » the capability of the switches employed in a network » the purpose of the creation of a switched path; that is , the types of flows to be carried in the switched path. l 國立清華大學資訊系黃能富教授 91

Observations, Issues, and Assumptions v Data driven versus control traffic driven label assignment l l l Three strategies for label assignment: (1) driven by topology based control traffic (e. g. , Tag, and ARIS) » labels are assigned in response to normal processing of routing protocol control traffic (2) driven by request based control traffic (RSVP) » labels are assigned in response to normal processing of request base control traffic (3) driven by data traffic (CSR, and Ipsilon) » the arrival of data at an LSR “triggers” label assignment and distribution. In actual practice combinations of these methods may be employed. 國立清華大學資訊系黃能富教授 92

Conclusion v MPLS has emerged as a promising technology that will improve the scalability of hop-by-hop routing and forwarding, and provide traffic engineering capabilities for better network provisioning. v It decouples forwarding from routing and allows multiprotocol support without requiring changes to the basic forwarding paradigm. v RFC 3812 v Generalized MPLS (GMPLS) v λMPLS (Optical wavelength-based) 國立清華大學資訊系黃能富教授 93