Io T in Industry ASSIST PROF RASSIM SULIYEV




















- Slides: 31

Io. T in Industry ASSIST. PROF. RASSIM SULIYEV ZHUMAN IYA Z MAMATNABI YEV WEEK 7

OUTLINE Io. T Networks and Protocols Types of networks Network mechanisms and processes Packet switching Converged networks Hosts Clients and servers Default gateway Network interface hardware Introduction to Packet Tracer Mobile wireless technologies

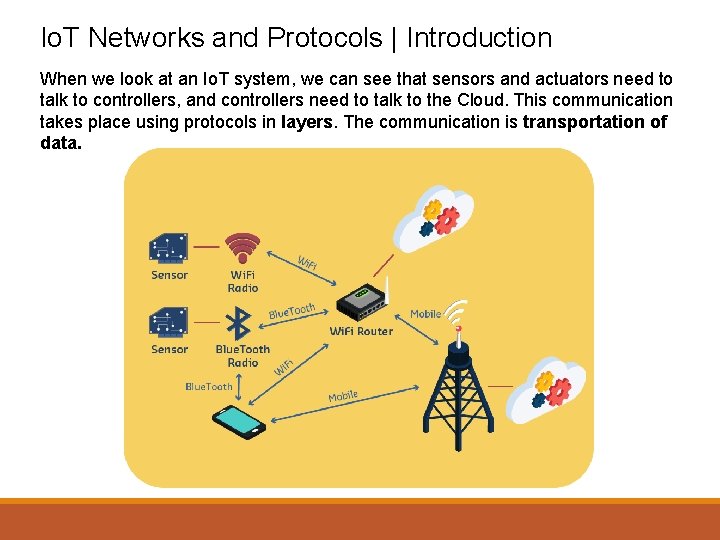
Io. T Networks and Protocols | Introduction When we look at an Io. T system, we can see that sensors and actuators need to talk to controllers, and controllers need to talk to the Cloud. This communication takes place using protocols in layers. The communication is transportation of data.

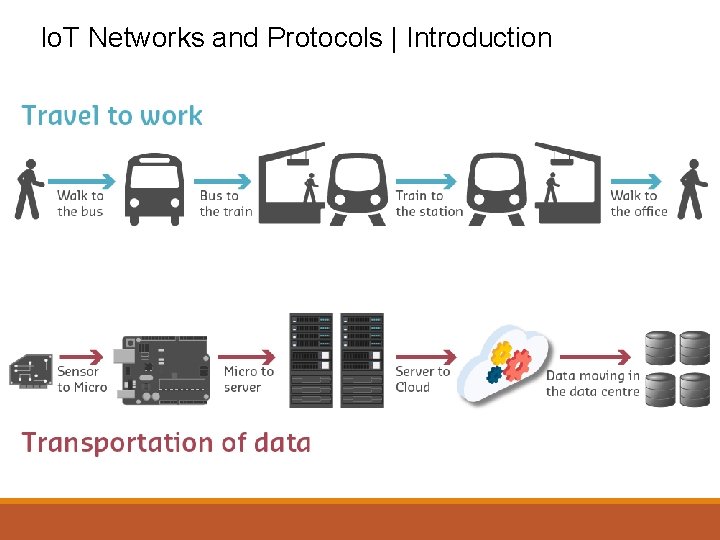
Io. T Networks and Protocols | Introduction

Types of networks The main objective of a network is to connect devices for data transmission. To achieve this objective, the interconnected networks are required to form the network of networks – known as the Internet.

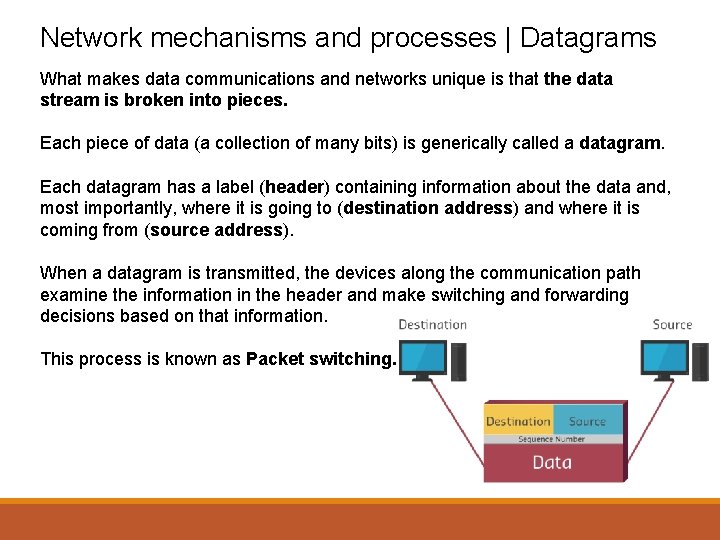
Network mechanisms and processes | Datagrams What makes data communications and networks unique is that the data stream is broken into pieces. Each piece of data (a collection of many bits) is generically called a datagram. Each datagram has a label (header) containing information about the data and, most importantly, where it is going to (destination address) and where it is coming from (source address). When a datagram is transmitted, the devices along the communication path examine the information in the header and make switching and forwarding decisions based on that information. This process is known as Packet switching.

Packet switching Transmitted datagrams effectively find their own way across an internetwork, because the intermediate devices decide where to send the datagram next based on the addressing information in each header. The process of packet switching, known as routing, will be explained further in Module 2. Advantages of packet switching include: Multiplexing enables multiple data streams to share a common network link by interleaving the datagrams of the different streams. Network resilience As each datagram is forwarded individually by each networking device, should one link to a destination become unavailable, subsequent datagrams addressed to that same destination can be re-directed along other links that provide a pathway to the same destination.

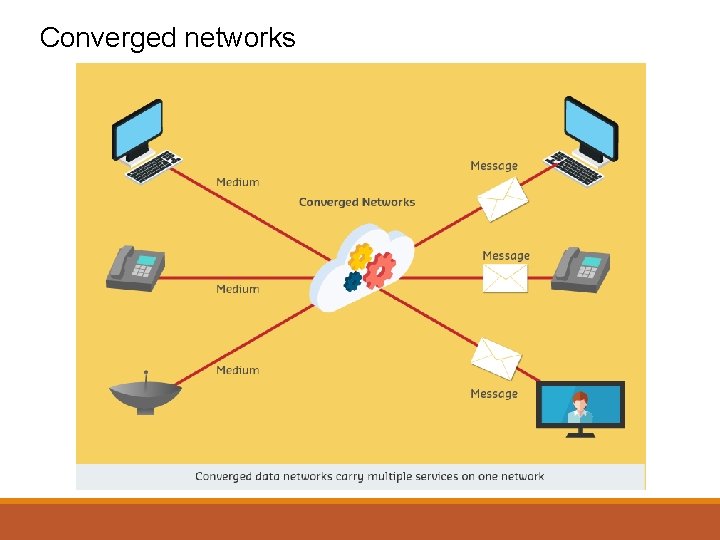
Converged networks

Hosts In networking, a host is an addressable (network identifiable) device that sends and receives datagrams. This includes individual devices such as PCs, laptops, printers, routers, smart phones, tables, sensors, cameras, and actuators. Note that these devices can be both actual hardware and virtualised (software) instances. Devices that only repeat or amplify datagrams without making switching decisions (repeaters and hubs), or that only interconnect devices (patch panels), are not considered to be hosts in this context. This means that in networking terms, the ‘things’ we connect are referred to as hosts.

Clients and servers

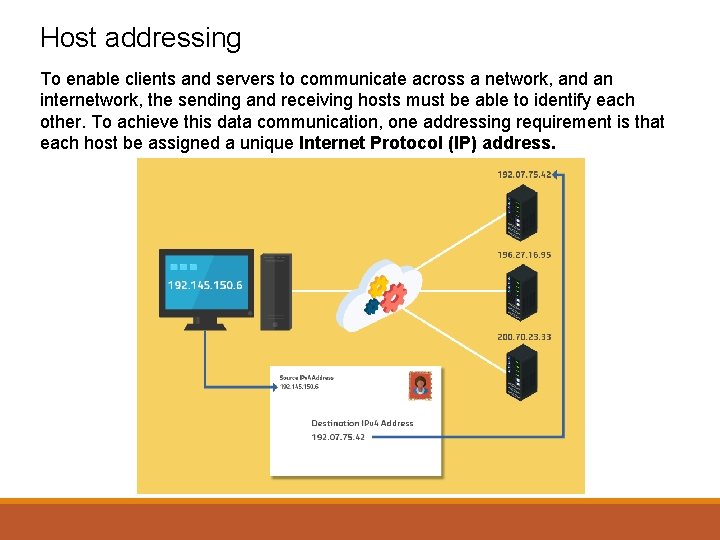
Host addressing To enable clients and servers to communicate across a network, and an internetwork, the sending and receiving hosts must be able to identify each other. To achieve this data communication, one addressing requirement is that each host be assigned a unique Internet Protocol (IP) address.

Default gateway The default gateway for a host is the IP address of the router interface that all hosts on one network are connected to. The router interface used as the default gateway for a network is literally that: a gateway. It is through this interface that all data traffic destined for other networks is sent, and through which all data traffic from other networks enters this network. Each host on the same network has a unique IPv 4 address, but all share the same subnet mask, and the same default gateway IPv 4 address.

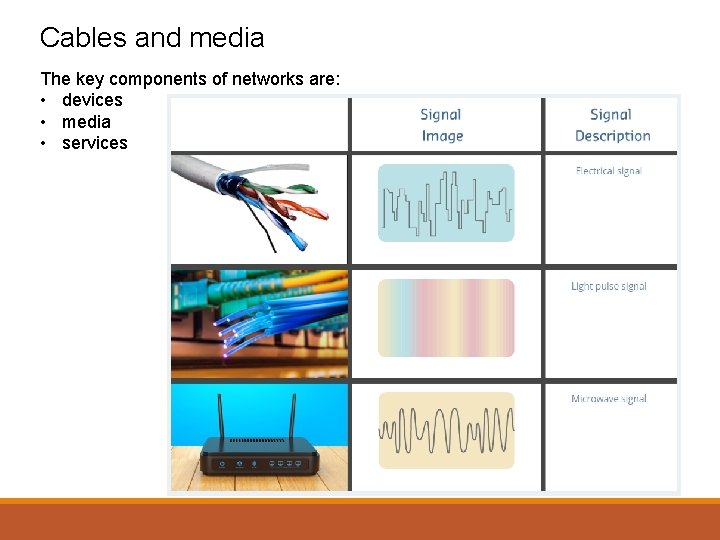
Cables and media The key components of networks are: • devices • media • services

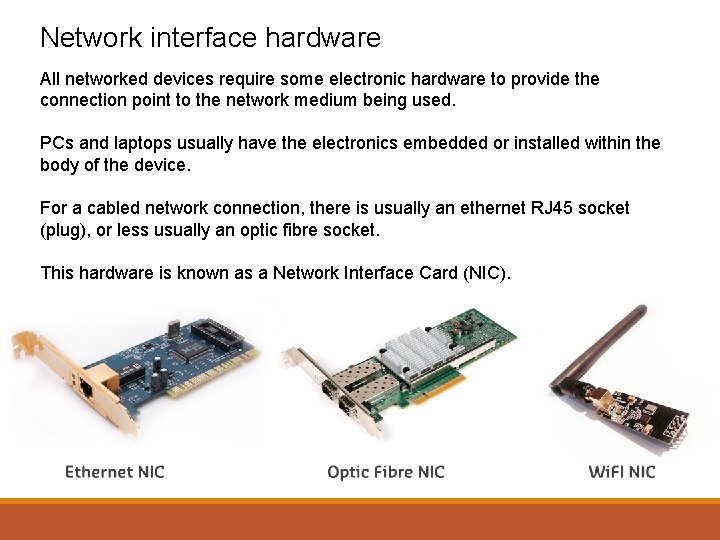
Network interface hardware All networked devices require some electronic hardware to provide the connection point to the network medium being used. PCs and laptops usually have the electronics embedded or installed within the body of the device. For a cabled network connection, there is usually an ethernet RJ 45 socket (plug), or less usually an optic fibre socket. This hardware is known as a Network Interface Card (NIC).

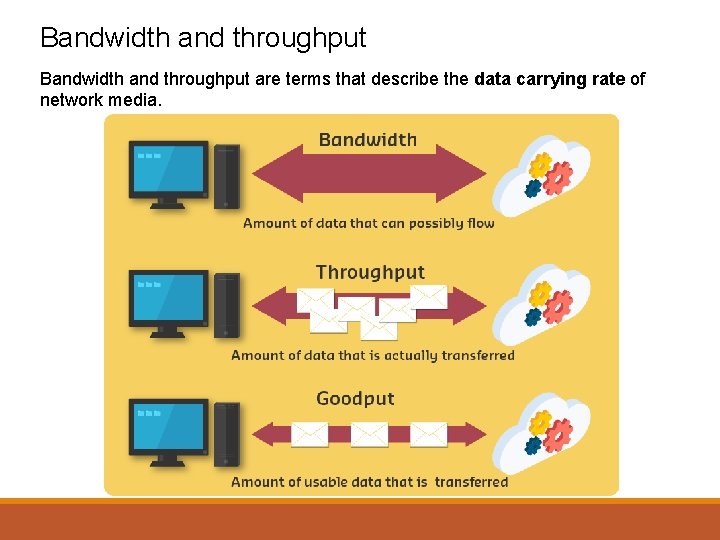
Bandwidth and throughput are terms that describe the data carrying rate of network media.

Bandwidth is the specified (or ideal maximum) capacity of a medium to carry data. Digital bandwidth measures the amount of data that can flow from one place to another in a given amount of time. Bandwidth is typically measured in kilobits per second (kb/s), megabits per second (Mb/s), or gigabits per second (Gb/s). The practical bandwidth of a network is determined by: • The properties of the physical media • The technologies chosen for transmitting and detecting the signals on the media

Throughput and Goodput Throughput is the measure of the actual transfer of bits across the media for a given period. Throughput usually does not match the specified maximum bandwidth of a physical layer implementation. Factors that influence throughput include: • The amount of traffic • The type of traffic • The latency (delay) created by the number of network devices between source and destination In an internetwork or network with multiple segments, throughput cannot be faster than the slowest link in the path from source to destination. Goodput is a term sometimes used to describe the transfer rate of actual, usable data.

Introduction to Packet Tracer installation instructions: • Installing Packet Tracer 7. 1 on Windows and Linux • Installing Packet Tracer 7. 1 on Mac • Creating an Ubuntu Virtual Machine

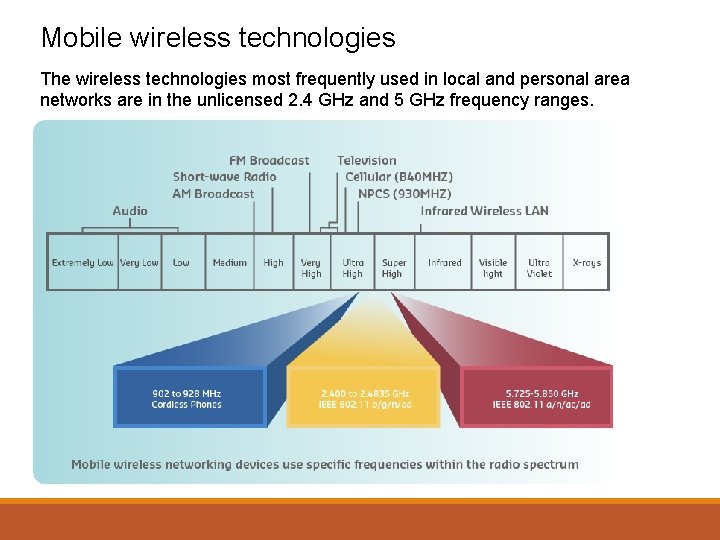
Mobile wireless technologies Wireless technologies use electromagnetic waves to carry information between devices. Electromagnetic waves (electromagnetic radiation) travel through space-time (i. e. they don’t need a medium like water or air), and they carry electromagnetic radiant energy. Because they are waves they have a frequency and wavelength. Visible light is part of the electromagnetic spectrum, as are X-rays and microwaves. The part of the spectrum used by mobile wireless technologies are radio waves and microwaves. Radio waves are the waves of the spectrum that have the longest wavelength and the shortest frequency.

Mobile wireless technologies

Mobile wireless technologies The wireless technologies most frequently used in local and personal area networks are in the unlicensed 2. 4 GHz and 5 GHz frequency ranges.

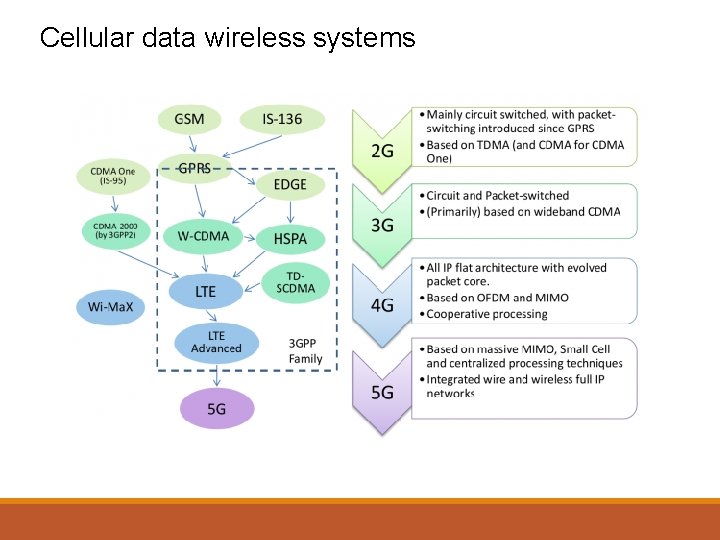
Cellular data wireless systems Unlike other wireless technologies, public switched cellular telecommunications operate within licensed bands of the radio spectrum, which requires licensing from the relevant government authority. Mobile cellular telephone systems began to be used for digital data communications (in addition to voice and SMS services) from the late 1990 s, with the development of technologies such GPRS. Cell phone and data technologies have been labelled in ‘generations’ - G 1, G 2, G 3, G 4, and G 5 - but these are just marketing names for groups of technologies, not specified standards.

Cellular data wireless systems

Cellular data wireless systems Cell and smart phones are specifically switched to enable high speed 4 G/LTE broadband Internet data services where available, in addition to voice communications. Given the often-wide coverage of 4 G services available from telecommunications providers suitable for personal data usage (video streaming, for example), some use cases exist for Io. T 4 G/LTE applications. For example, building-monitored security and alarm systems may not have access to the appropriate public telecommunications cabling, so the sensor controller communicates with a central office using a 4 G data service. Private 4 G/LTE data services are also found in some remote mining operations. Public 4 G/LTE services are typically not commercially available in these locations, so a private solution offers improved performance and range compared to traditional Wi-Fi solutions.

Wi-Fi refers to the group of radio frequency (RF) standards used to provide data communications on a Wireless Local Area Network (WLAN). Wi-Fi operates in the unlicensed 2. 4 and 5 Gigahertz (Ghz) ranges of the RF spectrum. The group of standards generally offer ranges of 20 m (66 ft) to 250 m (820 ft), and data rates between 1 Mb/s to 20 Gb/s.

Bluetooth is a low power, short range (typically less than 10 m (33 ft) up to 100 m (330 ft)), personal area network wireless technology. It enables mobile devices to connect to each other, and to wireless accessories, with minimal configuration. Bluetooth Low Energy (BLE) is used in healthcare, fitness, beacons, security, and home entertainment applications. Compared to classic Bluetooth, Bluetooth Low Energy provides considerably reduced power consumption (longer battery life) and lower costs, while maintaining a similar communication range. Mobile operating systems now natively support Bluetooth Low Energy. Up to eight Bluetooth devices can be connected at any one time.

Bluetooth Some examples of how devices use Bluetooth include: • Hands-free headset • Keyboard or mouse • Stereo control • Car hands-free speakerphone • Tethering (network connection sharing) • Mobile speaker. Bluetooth can also offer some minimal level security for communications between connected devices. Public utility providers (for water, electricity, gas) can use handheld Bluetooth devices to remotely access the usage recording meter on house or business properties to read the customer's consumption from outside the property boundary.

Bluetooth

NFC Near-field communication (NFC) is a set of communication protocols that enable two electronic devices - typically portable devices such as smartphones - to establish low-speed communication by bringing them within 4 cm (1. 6 in) of each other. NFC devices are used in contactless payment systems, like those used in credit cards and electronic ticket smartcards. NFC-enabled devices can act as electronic identity documents and keycards. The tag can also be passive (require no power) and still be detected by the scanning device, provided that the tag is within range. This makes it suitable for Io. T applications. However, there is no default security (no pairing of devices like Bluetooth), so a tag could be read by an unauthorised device.

NFC

Any Questions?
 Als assist
Als assist Assist electrical
Assist electrical Cisco smart assist
Cisco smart assist Brake assist system
Brake assist system Second heart assist
Second heart assist Mission assist
Mission assist School mental health assist
School mental health assist Assist user guide
Assist user guide The whips assist the party leaders by
The whips assist the party leaders by Redcap choa
Redcap choa What cognitive strategies assist our problem solving
What cognitive strategies assist our problem solving Cough assist als
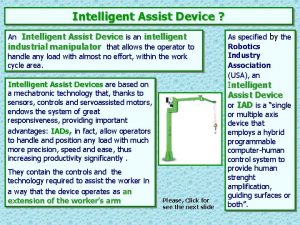
Cough assist als Intelligent assist device
Intelligent assist device Cisco smart assist
Cisco smart assist Thymosin and thymopoietin assist in the maturation of:
Thymosin and thymopoietin assist in the maturation of: Mediassistindia login
Mediassistindia login Travel guard ez tips
Travel guard ez tips Mcdp 1 states that trust between marines
Mcdp 1 states that trust between marines Gx assist side effects
Gx assist side effects One teach, one assist pros and cons
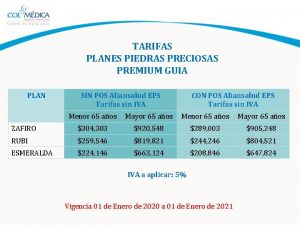
One teach, one assist pros and cons Plan esmeralda colmedica
Plan esmeralda colmedica Peer assist adalah
Peer assist adalah Info assist
Info assist Fire team formations
Fire team formations Pam eap
Pam eap Quality assist
Quality assist Park assist 2
Park assist 2 Pbx call assist 2
Pbx call assist 2 Unit 5 quiz 1 power assist systems
Unit 5 quiz 1 power assist systems Prof rinti banerjee
Prof rinti banerjee Pulmonary embolism
Pulmonary embolism Prof dr mehmet baykara
Prof dr mehmet baykara