Investigating Intimate Partner Violence and Stalking May 8













































































- Slides: 84

Investigating Intimate Partner Violence and Stalking May 8, 2017 Jeffrey J. Nolan, J. D. STUDENT SEXUAL MISCONDUCT: ADDRESSING INSTITUTIONAL CULTURE AND COMPLIANCE Dinse, Knapp & Mc. Andrew, P. C. www. dinse. com NACUA FEBRUARY 2014 CLE WORKSHOP • FRIDAY, FEBRUARY 29 – SATURDAY, MARCH 1 • HILTON DOWNTOWN • MIAMI, FL DINSE / KNAPP / Mc. ANDREW www. dinse. com

What Have We Learned? • Since 2014/2015, Clery Act has required institutions to: – prohibit IPV and stalking – provide interim measures and accommodations – respond to complaints, and – Provide general awareness and risk reduction programs • What have we learned about IPV and stalking? www. dinse. com

What Do We Need to Know? www. dinse. com

IPV: Clery Act Requirements www. dinse. com

Annual Training Requirement Annual Security Report must include statements that: – Disciplinary proceedings will be conducted by officials who receive annual training on issues related to domestic violence, dating violence, sexual assault, and stalking and how to conduct an investigation and hearing process that “protects the safety of victims and promotes accountability” www. dinse. com

Clery Regulation Definition: Domestic Violence. (i) A felony or misdemeanor crime of violence committed: (A) By a current or former spouse or intimate partner of the victim; (B) By a person with whom the victim shares a child in common; (C) By a person who is cohabitating with, or has cohabitated with, the victim as a spouse or intimate partner; (D) By a person similarly situated to a spouse of the victim under the domestic or family violence laws of the jurisdiction in which the crime of violence occurred, or (E) By any other person against an adult or youth victim who is protected from that person’s acts under the domestic or family violence laws of the jurisdiction in which the crime of violence occurred. www. dinse. com

Clery Regulation Definition: Dating Violence Dating violence. Violence committed by a person who is or has been in a social relationship of a romantic or intimate nature with the victim. (i) The existence of such a relationship shall be determined based on the reporting party’s statement and with consideration of the length of the relationship, the type of relationship, and the frequency of interaction between the persons involved in the relationship. (ii) For the purposes of this definition— (A) Dating violence includes, but is not limited to, sexual or physical abuse or the threat of such abuse. (B) Dating violence does not include acts covered under the definition of domestic violence. www. dinse. com

IPV: The Scope of the Problem www. dinse. com

Ensuring Fairness to All Parties • The information below about statistics should be viewed in context of institutional disciplinary proceedings, in which: – Individual cases are not about statistics – Decision in every case must be based on preponderance of evidence presented – Cannot fill in evidentiary gaps with statistics, advocacy orientations or personal beliefs – Process must be fair and impartial to each party www. dinse. com

A Note on Language • Research findings on adjudicated cases, abstract case studies and examples, typologies and even statutes (e. g. , Clery Act) often use “perpetrator”, “victim” and “target”-type language • Use of those terms in this presentation reflects that reality • However, in all individual cases, whether or not person is responsible for misconduct is never presumed until investigation / adjudication procedures are completed • “Complainant”/”Respondent” language should always be used in individual cases www. dinse. com

NIPSV Survey Findings • 2010 CDC National Intimate Partner and Sexual Violence Survey of 16, 507 adults (9, 086 women, 7, 421 men) (“NIPSV”) found: – About 1 in 4 women (24. 3%) and 1 in 7 men (13. 8%) have experienced severe physical violence by IP at some point in lifetime – Nearly half of all women (48. 4%) and men (48. 8%) have experienced psychological aggression by IP in their lifetime www. dinse. com

NIPSV Survey Findings • NIPSV Survey found: – Among those who experienced rape, physical violence, or stalking by an intimate partner, 47. 1% of female victims and 38. 6% of male victims were between 18 and 24 when they first experienced violence by an intimate partner www. dinse. com

Dating Violence Statistics • Girls and young women between 16 and 24 experience highest rate of IPV (almost triple the national average) • Half of youth who have been victims of both dating violence and rape attempt suicide, compared to 12. 5% of non-abused girls and 5. 4% of non-abused boys • 33% of teens disclosed violent relationship • Source: love is respect. org www. dinse. com

Dating Violence Statistics • 2011 College Dating Violence and Abuse Poll – 43% of dating college women report experiencing some violent and abusive dating behaviors including physical, sexual, tech, verbal or controlling abuse – Over one in five college women (22%) report actual physical abuse, sexual abuse or threats of physical violence – 52% of college women report knowing a friend who has experienced violent and abusive dating behaviors including physical, sexual, tech, verbal or controlling abuse – More than half (57%) of college students who report having been in an abusive dating relationship said it occurred while they were in college www. dinse. com

DV/Sexual Assault/Stalking Interaction • CDC NIPSV found: – Among those who experienced rape, physical violence, or stalking by an intimate partner during their lifetime, male victims were significantly more likely (92. 1%) than female victims to experience physical violence only – Among female victims, 14. 4% experienced physical violence and stalking, 8. 7% experienced both rape and physical violence, and 12. 5% experienced rape, physical violence and stalking www. dinse. com

Possible Characteristics of Some Abusive Relationships • Much research has been done regarding characteristics of IPV • Research findings can never be substituted for evidence in particular cases – Each case must be based on evidence and policy elements, by applicable standard of proof • Understanding possible characteristics can however help us plan investigations www. dinse. com

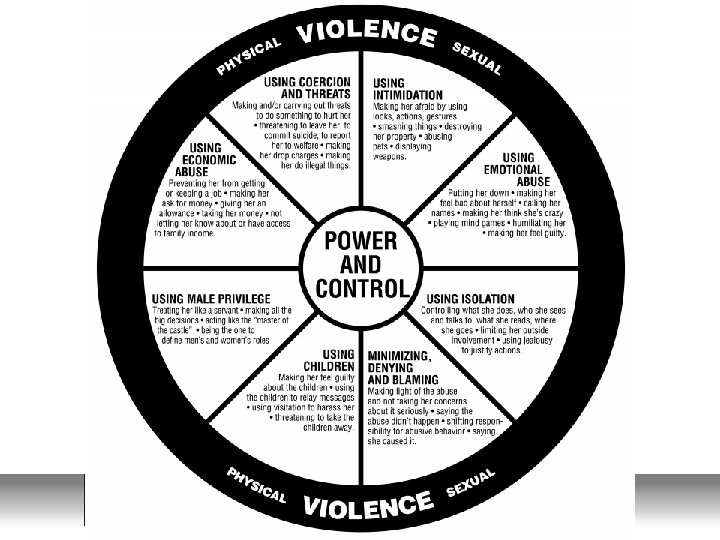
Perspectives on “Power and Control Wheel” • Commonly-cited “power and control wheel” uses gendered language • People of any gender can be perpetrators or victims of power and control behavior • Sometimes, both parties to a relationship engage in power and control behaviors www. dinse. com

www. dinse. com

Acknowledgment • Thanks to Marisa Randazzo, Ph. D. and Dorian Van Horn of Sigma Threat Management Associates for contributions to following slides on domestic/dating violence and stalking www. dinse. com

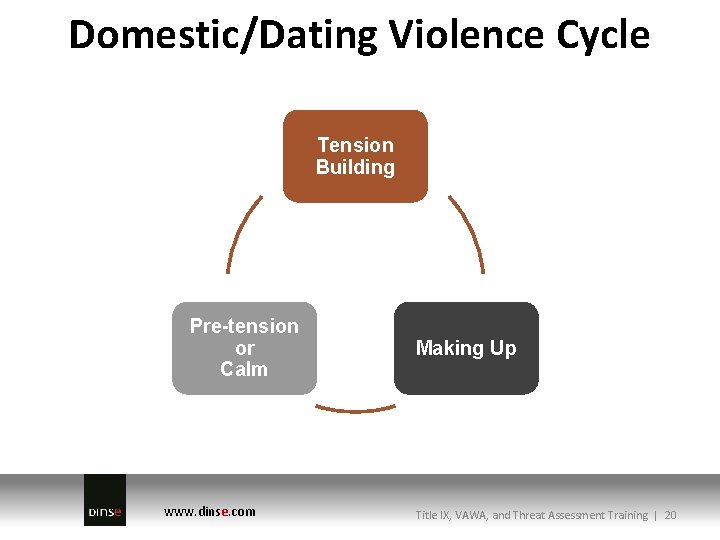
Domestic/Dating Violence Cycle Tension Building Pre-tension or Calm www. dinse. com Making Up Title IX, VAWA, and Threat Assessment Training | 20

Domestic/Dating Violence Cycle Tension Building • Abuser starts to get angry • Verbal abuse may begin • Violence against things • Breakdown of communication • Victim feels the need to keep the abuser calm • Tension becomes overwhelming • Victim feels like “walking on egg shells” www. dinse. com Title IX, VAWA, and Threat Assessment Training | 21

Domestic/Dating Violence Cycle Making Up • Abuser may… • Apologize for abuse • Promise it will never happen again • Blame the victim for causing the abuse • Deny abuse took place or say it was not as bad as the victim claims www. dinse. com Title IX, VAWA, and Threat Assessment Training | 22

Domestic/Dating Violence Cycle Pre-tension or Calm • Abuser acts like the abuse never happened • Physical abuse may not be taking place • “Making-up” promises may be met • Victim often hopes that the abuse is over • Abuser may give gifts to victim • Can then lead back to tension building stage www. dinse. com Title IX, VAWA, and Threat Assessment Training | 23

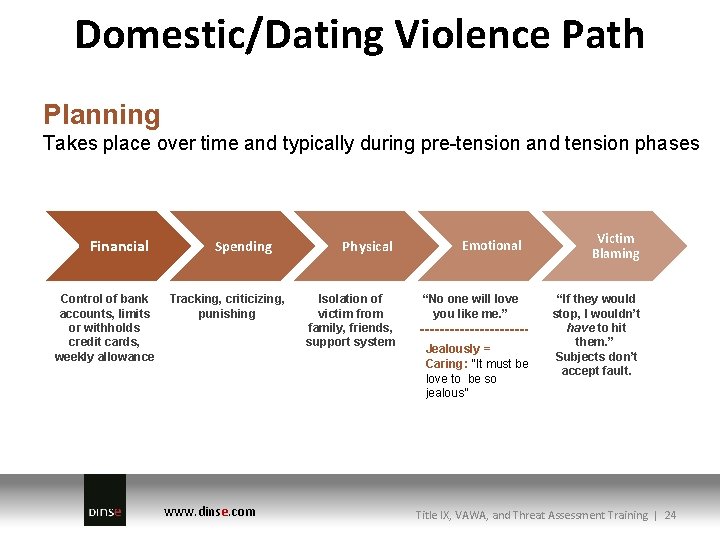
Domestic/Dating Violence Path Planning Takes place over time and typically during pre-tension and tension phases Financial Control of bank accounts, limits or withholds credit cards, weekly allowance Spending Tracking, criticizing, punishing www. dinse. com Physical Isolation of victim from family, friends, support system Emotional “No one will love you like me. ” Jealously = Caring: “It must be love to be so jealous” Victim Blaming “If they would stop, I wouldn’t have to hit them. ” Subjects don’t accept fault. Title IX, VAWA, and Threat Assessment Training | 24

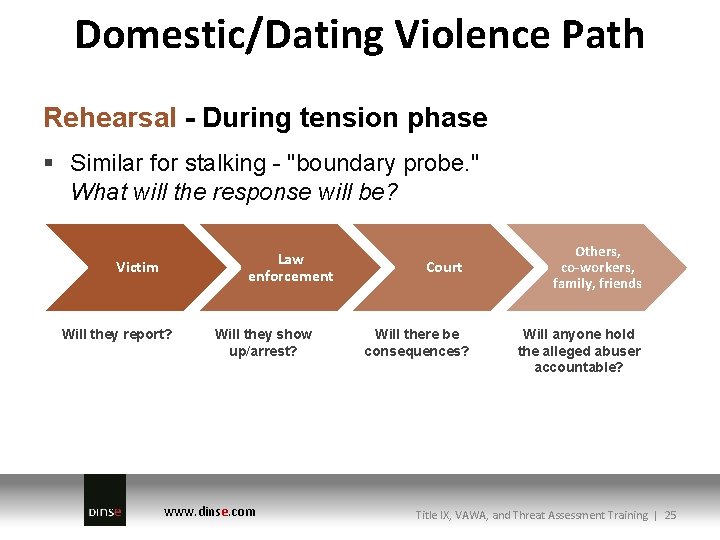
Domestic/Dating Violence Path Rehearsal - During tension phase § Similar for stalking - "boundary probe. " What will the response will be? Law enforcement Victim Will they report? Will they show up/arrest? www. dinse. com Court Will there be consequences? Others, co-workers, family, friends Will anyone hold the alleged abuser accountable? Title IX, VAWA, and Threat Assessment Training | 25

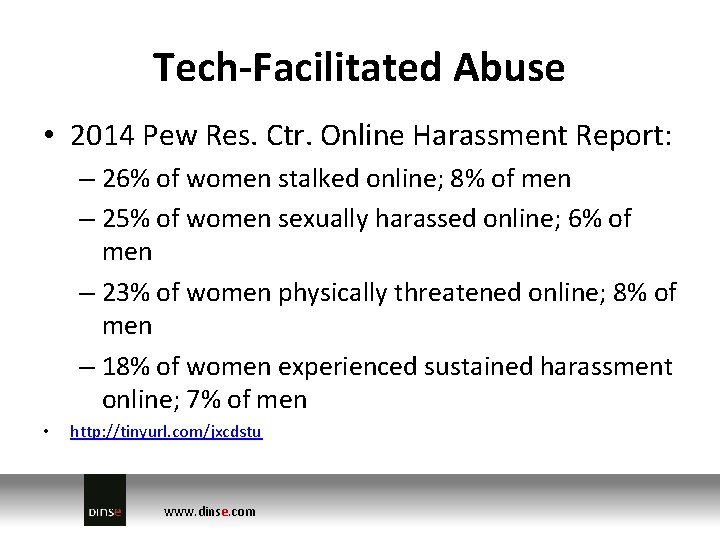
Tech-Facilitated Abuse • 2014 Pew Res. Ctr. Online Harassment Report: – 26% of women stalked online; 8% of men – 25% of women sexually harassed online; 6% of men – 23% of women physically threatened online; 8% of men – 18% of women experienced sustained harassment online; 7% of men • http: //tinyurl. com/jxcdstu www. dinse. com

Tech-Facilitated Abuse • Abusers may: – Stalk, monitor victims through social media, tracking apps – Create fake websites and social media profiles posing as victims, inviting sexual harassment and other abuse – Post compromising photos of victims – Send fraudulent or compromising messages/photos to victims’ family and friends • ”The Internet and Intimate Partner Violence, ” Criminal Justice, Summer 2016 www. dinse. com

Strangulation and IPV § One of the most lethal forms of IPV § One of the best predictors for the subsequent homicide of victims of domestic violence and interpersonal violence § Most often seen in IPV cases and in serial murders www. dinse. com Title IX, VAWA, and Threat Assessment Training | 28

IPV Investigations www. dinse. com

IACP IPV Response Policy and Training Content Guidelines • International Association of Chiefs of Police Guidelines suggest policy elements and investigation approaches • Investigation suggestions for law enforcement: – In initial questioning, remember that victim ”may struggle with gaps in memory” – “Ask open-ended questions that invite a narrative response” • Essentially, use FETI style trauma-informed approach www. dinse. com

IACP IPV Response Policy and Training Content Guidelines • Investigation suggestions for law enforcement: – In initial questioning, do not: – Ask leading questions – Push for chronological account – Ask victim-blaming questions (“why did you? ”; “why didn’t you? ”) • Again, this is consistent with a trauma-informed approach • Of course, in university context, will ultimately have to interview for clarification to ensure fairness to all parties www. dinse. com

IACP IPV Response Policy and Training Content Guidelines • Investigation suggestions for law enforcement: – Ask about and document any current, recent and past physical signs and symptoms of injuries – Contact EMS if strangulation occurred or was attempted – In interviewing victim: • Address any immediate safety concerns • Ask if suspect attempted to intimidate victim not to contact police www. dinse. com

IACP IPV Response Policy and Training Content Guidelines • Investigation suggestions for law enforcement: – In interviewing victim: • Address any immediate safety concerns • Ask if suspect attempted to intimidate victim not to contact police • Check for existence of protection orders • Ask about any stalking behaviors • Ask about social media, texting, other e-evidence • Collect any physical evidence • Do danger and lethality assessments www. dinse. com

IACP IPV Response Policy and Training Content Guidelines • Investigation suggestions for law enforcement re identifying the predominant aggressor: – Does either party threaten, intimidate, isolate, emotionally abuse the other? – Is there sexual abuse by one partner of other? – Is there a physical size difference? – Severity of each party’s injuries? – Either have access to weapons? – Fear expressed by one or other? – Other witness evidence? www. dinse. com

Implications for Investigations • Can use knowledge of IPV patterns to plan investigation • Evidence in each case will dictate path and results of investigation, but knowledge of patterns that may be present in some IPV cases can help investigators do more complete, nuanced inquiry www. dinse. com

Implications for Investigations • As in sexual assault cases, corroboration is critical in cases with no other witnesses and two adverse parties • “It’s ‘he said/she said’” is not an acceptable conclusion in IPV cases! www. dinse. com

Particular Challenges in IPV Cases • Parties (that is, both of them) may break mutual no-contact orders – May be due to continued animosity that parties can’t or won’t control – May be “setting each other up” – May be due to continuing affection for each other • Remember “DV Cycle” graphic above? • Might want to consider having alternative, faster process for adjudicating reported NCO violations www. dinse. com

Mutual No-Contact Order Analogy • In study of large number of judicial protection orders in San Diego County, researchers found: – Protection orders did appear to deter criminal and violent criminal offenses to protectees – Non-mutual service of protective orders “substantially and significantly increased the risk of both violent and nonviolent victim-related arrests subsequent to service” • Meloy, et al. , “Domestic Protection Orders and the Prediction of Subsequent Criminality and Violence Toward Protectees, ” in The Scientific Pursuit of Stalking (2006) www. dinse. com

Particular Challenges in IPV Cases • Complainant may become ambivalent about continuing investigation or may ask that it be stopped – Again, remember “DV cycle” graphic above? • Complainant may not want respondent to receive sanctions commensurate with finding www. dinse. com

Particular Challenges in IPV Cases • • May have to identify predominant aggressor May receive “cross complaints” May have to investigate both parties’ conduct Dealing with requests for accommodations where complainant does not want to participate in investigation www. dinse. com

Stalking: Clery Act Requirements www. dinse. com

Clery Regulation Definition: Stalking. (i) Engaging in a course of conduct directed at a specific person that would cause a reasonable person to— (A) Fear for the person’s safety or the safety of others; or (B) Suffer substantial emotional distress. www. dinse. com

Clery Regulation Definition: Stalking (ii) For the purposes of this definition— (A) Course of conduct means two or more acts, including, but not limited to, acts in which the stalker directly, indirectly, or through third parties, by any action, method, device, or means, follows, monitors, observes, surveils, threatens, or communicates to or about a person, or interferes with a person’s property. (B) Reasonable person means a reasonable person under similar circumstances and with similar identities to the victim. (C) Substantial emotional distress means significant mental suffering or anguish that may, but does not necessarily, require medical or other professional treatment or counseling. www. dinse. com Title IX, VAWA, and Threat Assessment Training | 43

Stalking: Scope of the Problem www. dinse. com

Cultural Depictions of “Stalking” • ”Fatal Attraction” • “Every Breath You Take” (The Police) • Plots of Dozens of Rom/Com Movies: Perseverance means you really care, and pursued person eventually relents and lives happily ever after? • ”Stalking” often referred to as a joke • How do prevention efforts square with our cultural environment? www. dinse. com

Stalking Statistics • Persons aged 18 -24 years experience the highest rate of stalking • 3 in 4 stalking victims are stalked by someone they know • 66% of female stalking victims and 41% of male victims are stalked by a current or former intimate partner • 46% of stalking victims experience at least one unwanted contact per week • Stalking Resource Center www. dinse. com

Stalking and Intimate Partner Femicide • 76% of intimate partner femicide victims had been stalked by their IP • 67% had been physically abused by their IP • 89% of femicide victims who had been physically assaulted had also been stalked in the 12 months before their murder • 79% of abused femicide victims reported being stalked during the same period that they were abused • 54% of femicide victims reported stalking to police before they were killed by their stalkers • Mc. Farlane, et al. , “Stalking and Intimate Partner Femicide, ” Homicide Studies, Vol. 3 No. 4 (Nov. 1999) www. dinse. com

Stalking Typologies • Putting typologies in context: – Typologies should not be used to decide individual cases – Cases are decided based on elements delineated in institutional policy – Typologies can however help investigators develop investigative strategies www. dinse. com

Stalking Typologies • Zona Typology: – Simple obsessional stalkers • Most common • Some prior interpersonal relationship • Stalker is often socially immature, low in self-esteem, insecure, prone to jealousy • Zona, Sharma, Lane (1993) www. dinse. com

Stalking Typologies • Zona Typology: – Simple obsessional stalkers • Most common • Some prior interpersonal relationship • Stalker is often socially immature, low in self-esteem, insecure, prone to jealousy • Stalker often male; victim often female • Zona, Sharma, Lane (1993) www. dinse. com

Stalking Typologies • Zona Typology: – Simple obsessional stalkers • Violence used to maintain control during relationship, stalking is means to continue control after relationship ends • Motive: forcing ex-partner into relationship/revenge • Frequently attempt to contact victim face-to-face, which represents significant violence risk factor • Zona, Sharma, Lane (1993) www. dinse. com

Stalking Typologies • Zona Typology: – Love obsessional stalkers • • No prior relationship between stalker and victim Mere acquaintances or total strangers Stalker often suffers from mental illness Seeks to create relationship Less likely to attempt face-to-face contact E. g. : John Hinckley, Jr. /Jodie Foster Zona, Sharma, Lane (1993) www. dinse. com

Stalking Typologies • Zona Typology: – Erotomanic stalkers • Stalker is delusional • Believes victim loves them, and that relationship already exists • Stalker often female; victim often male • Less likely to seek face-to-face contact • Lower risk of violence • E. g. : Margaret Ray (stalked David Letterman) • Zona, Sharma, Lane (1993) www. dinse. com

Stalking Typologies • RECON Typology: Focuses on RElationship and CONtext – Intimate Stalkers: Have prior intimate relationship • • • ”Most malignant” Often have criminal records, abuse stimulants/alcohol Rarely psychotic Often no major mental illness (except depression) Approach targets Mohandie, Meloy, et al. , “The RECON Typology of Stalking, ” J. Forensic Sci, Vol. 51, No. 1 (2006) www. dinse. com

Stalking Typologies • RECON Typology: – Intimate Stalkers: • Insult, interfere, threaten and are violent • In sample of 1005 cases, over one-half physically assaulted target, and one-third evidenced suicidal ideation or behavior • Prior sexual relationship increases risk of violence • Heightened danger days/weeks after separation • Risk management: intensive supervision • Mohandie, Meloy, et al. , “The RECON Typology of Stalking, ” J. Forensic Sci, Vol. 51, No. 1 (2006) www. dinse. com

Risk Factors for Violence/Further Violence in Stalking, IPV Cases • ”Most important predictive factor of violence in stalking cases may be the presence of a prior sexually intimate relationship between the perpetrator and the victim. ” • Most common motive for murder of spouse by her husband is her leaving abusive relationship • Most women murdered by husbands are stalked before murder • Meloy, et al. , “Risk Factors for Violence Among Stalkers, ” in Scientific Pursuit of Stalking (2006) www. dinse. com

Risk Factors for Violence/Further Violence in Stalking, IPV Cases • Greatest risk of spousal homicide is in days and weeks following separation • Explicit threats are significantly related to violence, but should not be used as major predictive factor in violence risk among stalkers: – Most stalkers threaten; – Most threats are not acted upon • Meloy, et al. , “Risk Factors for Violence Among Stalkers, ” in Scientific Pursuit of Stalking (2006) www. dinse. com

Stalking Typologies • RECON Typology: – Acquaintance Stalkers: • No prior intimate relationship • In study of 1005 cases: – 21% were women – One-third assaulted target or damaged their property • Risk management: interdiction and mental health treatment • Mohandie, Meloy, et al. , “The RECON Typology of Stalking, ” J. Forensic Sci, Vol. 51, No. 1 (2006) www. dinse. com

Stalking Typologies • RECON Typology: – Public Figure Stalkers: • Vast majority have major mental disorder • In study of 1005 cases: – 27% were women – Very low frequency of violence (2%) • Mohandie, Meloy, et al. , “The RECON Typology of Stalking, ” J. Forensic Sci, Vol. 51, No. 1 (2006) www. dinse. com

Stalking Typologies • RECON Typology: – Private Stranger Stalkers: • In study of 1005 cases: – Many were mentally ill men – One-third violent toward person or property • Risk management: interdiction and mental health treatment • Mohandie, Meloy, et al. , “The RECON Typology of Stalking, ” J. Forensic Sci, Vol. 51, No. 1 (2006) www. dinse. com

Stalking Typologies • Stalking Risk Profile Typology: – Rejected Stalker: • Context: breakdown of a close relationship • Motivation: – attempting to reconcile relationship and/or – exacting revenge for rejection • Maintaining behavior can be substitute for past relationship as it allows the stalker to continue to feel close to the victim • In other cases behavior is maintained because it allows stalker to salvage their damaged self-esteem and feel better about themselves • Mullen, Pathe, Purcell (see www. stalkingriskprofile. com) www. dinse. com

Stalking Typologies • Stalking Risk Profile Typology: – Resentful Stalker: • Stalker feels as though they have been mistreated or that they are the victim of some form of injustice or humiliation • Victims are strangers or acquaintances who are seen to have mistreated the stalker • Can arise out of a severe mental illness when perpetrator develops paranoid beliefs about victim and uses stalking as a way of ‘getting back’ at the victim • Initial motivation for stalking is the desire for revenge or to ‘even the score’ • Stalking is maintained by sense of power and control that stalker derives from inducing fear in the victim • Mullen, Pathe, Purcell (see www. stalkingriskprofile. com) www. dinse. com

Stalking Typologies • Stalking Risk Profile Typology: – Resentful Stalker: • Stalker feels as though they have been mistreated or that they are the victim of some form of injustice or humiliation • Victims are strangers or acquaintances who are seen to have mistreated the stalker • Can arise out of a severe mental illness when perpetrator develops paranoid beliefs about victim and uses stalking as a way of ‘getting back’ at the victim • Initial motivation for stalking is the desire for revenge or to ‘even the score’ • Stalking is maintained by sense of power and control that stalker derives from inducing fear in the victim • Mullen, Pathe, Purcell (see www. stalkingriskprofile. com) www. dinse. com

Stalking Typologies • Stalking Risk Profile Typology: – Intimacy Seeking Stalker: – Context: loneliness, lack of close confidante – Victims are usually strangers or acquaintances who become target of stalker’s desire for relationship – Frequently stalkers’ behavior is fueled by severe mental illness involving delusional beliefs about the victim, such as the belief that they are already in a relationship, even though none exists (erotomanic delusions) – Initial motivation is to establish an emotional connection and an intimate relationship – Stalking is maintained by the gratification that comes from the belief that they are closely linked to another person. • Mullen, Pathe, Purcell (see www. stalkingriskprofile. com) www. dinse. com

Stalking Typologies • Stalking Risk Profile Typology: – Predatory Stalker: – Context: deviant sexual practices and interests – Perpetrators are usually male and victims are usually female strangers in whom the stalker develops a sexual interest – Stalking behavior usually initiated as way of obtaining sexual gratification (e. g. , voyeurism targeting a single victim over time), but can also be used a way of obtaining information about the victim as a precursor to a sexual assault – In this sense the stalking is both instrumental and also gratifying for those stalkers who enjoy the sense of power and control that comes from targeting the usually unsuspecting victim • Mullen, Pathe, Purcell (see www. stalkingriskprofile. com) www. dinse. com

Stalking Typologies • Stalking Risk Profile Typology: – Incompetent Suitor Stalker: • – Context: loneliness or lust – Targets strangers or acquaintances – Unlike Intimacy Seeker, initial motivation is not to establish a loving relationship, but to get a date or a short term sexual relationship – Usually stalk for brief periods, but when they do persist their behavior is usually maintained by the fact that they are blind or indifferent to the distress of victim – Sometimes this insensitivity is associated with cognitive limitations or poor social skills consequent to autism spectrum disorders or intellectual disability Mullen, Pathe, Purcell (see www. stalkingriskprofile. com) www. dinse. com

Stalking and ASDs • Some research has found that individuals with ASDs: – May have lack of empathy, understanding in social contexts, difficulty in reading social cues – May pursue romantic interest longer than typical despite no response or negative reaction – May develop obsession, perseveration • Social skill development may help address these behaviors • Source: “Understanding Stalking Behaviors by Individuals with [ASDs] and Recommended Prevention Strategies for School Settings, ” J. of Autism and Dev. Disorders Dec. 2012 (citing Stokes et al. 2007) www. dinse. com

Stalking Typologies • Putting typologies in context: – Again, typologies should not be used to decide individual cases – Cases are decided based on elements delineated in institutional policy – Typologies can however help investigators develop investigative strategies – Can also be helpful in threat management www. dinse. com

Stalking Continuum • Benign unwanted contacts to communicate a message • Harassing contacts to frustrate/annoy the victim • Threatening contacts deigned to instill fear • Property damage • Violence against the victim/third party www. dinse. com Title IX, VAWA, and Threat Assessment Training | 69

Implications for Investigations • Again, research on stalking patterns and statistics cannot be substituted for evidence in individual cases • Knowledge of observed patterns can however help investigators plan investigations and determine areas of inquiry www. dinse. com

Implications for Investigations • Examples: – Should inquire about entire history of contacts between parties, to possibly identify continuum of behaviors – Behaviors that initially seem innocuous could be part of course of conduct, and relevant if caused reasonable fear www. dinse. com

Implications for Investigations • Investigate for all of the elements: – Course of conduct that would cause a reasonable person to – Fear for the person’s safety or the safety of others; or suffer substantial emotional distress – Reasonable person means a reasonable person under similar circumstances and with similar identities to the complainant www. dinse. com

IPV, Stalking / Threat Assessment Interaction www. dinse. com

Resource on IPV, Sexual Assault & Stalking / TAM Interaction • “Addressing Intimate Partner Violence and Stalking on Campus: Going Beyond Legal Compliance to Enhance Campus Safety” in Emerging Issues in Campus Safety (Thomson Reuters/Aspatore, 2015), available at: • http: //www. dinse. com/resourcecenter/news/nolan-book-chapter-available-for -download-news. html www. dinse. com

IPV, Stalking / Threat Assessment Interaction • May be Threat Assessment and Management Team (“TAM”) overlap in DV, SA & stalking cases • TAM team can be valuable resource • Institutions should avoid a silo mentality • Institutions should utilize TAM team as necessary in conjunction with disciplinary processes www. dinse. com

Need for Collaboration • IPV and stalking disciplinary cases can involve ongoing safety concerns: – To complainant(s) – To others on campus – To other campuses – To university personnel • Remember research findings on when abused person is most at risk, and homicide despite reporting stalking to law enforcement? www. dinse. com

Need for Collaboration • Title IX Coordinator need not be solely responsible for determining, in potentially dangerous situations: – Whether to investigate due to safety concerns, over objection of reported victim – How to best implement no-contact orders – How to best implement interim measures and accommodations – Whether/how to impose interim suspension – How to best time steps in disciplinary process • Decisions about these complex issues can benefit from TAM team input www. dinse. com

Need for Collaboration • Threat assessment investigations that involve dating violence, domestic violence, sexual assault, and/or stalking need to involve: – Trauma-informed interviewing – Referral to Title IX coordinator – Parallel investigations • These investigations can benefit from expertise of Title IX investigators and others www. dinse. com Title IX, VAWA, and Threat Assessment Training | 78

Need for Collaboration • Failure to coordinate can lead to compartmentalized information, disjointed safety or intervention efforts • Lack of coordination can also result in multiple unnecessary contacts with complainant to obtain the same information • Coordinated efforts can yield enhanced information-sharing and integrated safety efforts www. dinse. com Title IX, VAWA, and Threat Assessment Training | 79

Obstacles to Collaboration • Lack of understanding of each other’s roles, responsibilities, and/or intentions • Lack of trust based on stereotypes • Lack of trust based on prior experience • Concerns or misunderstanding regarding confidentiality • Jurisdictional confusion www. dinse. com Title IX, VAWA, and Threat Assessment Training | 80

Enhancing Collaboration • Engage in liaison-building efforts • Work with individuals, rather than departments • Share information first, then ask for information • Invite other teams’ members to your meetings • Access legal counsel for confidentiality and jurisdiction questions • Meet face to face outside of a case www. dinse. com Title IX, VAWA, and Threat Assessment Training | 81

Using Knowledge of IPV/Stalking Interaction in TAM • Understand power and control at root of many IPV/stalking and sexual assault behaviors, and that cases may involve all three types of behaviors • TAM inquiries should gather information about all such behaviors • Knowledge about typologies and risk factors can inform threat management strategies www. dinse. com

Fairness in IPV, SA & Stalking-Related Threat Assessments • TAM is not an adversarial process • TAM investigations should occur in parallel to, and not instead of, Title IX/Clery investigations • TAM investigations should not determine outcome of Title IX/Clery investigations • Information gathered in TAM investigations that are not directly relevant to whether policy violation occurred in Title IX/Clery case under investigation should not be used against respondent www. dinse. com

Questions? Jeffrey J. Nolan, J. D. Dinse, Knapp & Mc. Andrew, P. C. jnolan@dinse. com (802) 864 -5751 www. dinse. com
 Periwinkle doerfler
Periwinkle doerfler Slii framework stalking
Slii framework stalking He stalks in his vivid stripes rhyming scheme
He stalks in his vivid stripes rhyming scheme Stalking
Stalking Killing stalking chapter 10
Killing stalking chapter 10 Family life today
Family life today Define the relationship chapter 7
Define the relationship chapter 7 Love and communication in intimate relationships
Love and communication in intimate relationships Investigating and making a case for drug diversion
Investigating and making a case for drug diversion Cell theory contributors
Cell theory contributors Intimate distance
Intimate distance Intimate family chapter 6
Intimate family chapter 6 Intimate family chapter 6
Intimate family chapter 6 Meaning of initmacy
Meaning of initmacy Intimate family chapter 2
Intimate family chapter 2 Use of frozen register
Use of frozen register Dewgarden foaming intimate wash benefits
Dewgarden foaming intimate wash benefits Zones of space communication
Zones of space communication Intimate zone in communication
Intimate zone in communication Relaxed antonym
Relaxed antonym Me line 02 intimate
Me line 02 intimate Abcde of intimate relationship
Abcde of intimate relationship Intimacy after incarceration
Intimacy after incarceration Investigating the properties of sound
Investigating the properties of sound Investigating science hsc
Investigating science hsc Practice a investigating graphs of polynomial functions
Practice a investigating graphs of polynomial functions Investigating graphs of polynomial functions
Investigating graphs of polynomial functions Unit 14 investigating customer service
Unit 14 investigating customer service Investigating the world of work. lesson 1
Investigating the world of work. lesson 1 6-7 investigating graphs of polynomial functions
6-7 investigating graphs of polynomial functions Unit 14 investigating customer service assignment 2
Unit 14 investigating customer service assignment 2 Investigating the graph of an inequality
Investigating the graph of an inequality Creative imedia r082
Creative imedia r082 Investigating polynomials
Investigating polynomials Investigating system requirements
Investigating system requirements Module 1 review questions
Module 1 review questions How is a delta formed
How is a delta formed Investigating graphs of polynomial functions
Investigating graphs of polynomial functions Investigating quadratics
Investigating quadratics Investigating rivers
Investigating rivers Investigating skills thomas edison cause effect
Investigating skills thomas edison cause effect Methods of investigating behaviour
Methods of investigating behaviour Integrated science lab experiments
Integrated science lab experiments What is this called
What is this called Meaning of language
Meaning of language Investigating system requirements
Investigating system requirements Specific heat capacity question
Specific heat capacity question Chapter 8 estimating with confidence
Chapter 8 estimating with confidence Five modifiers of human acts
Five modifiers of human acts Domestic and family violence protection act 2012
Domestic and family violence protection act 2012 Gandhi king and mandela what made non-violence work dbq
Gandhi king and mandela what made non-violence work dbq Chapter 9 resolving conflicts and preventing violence
Chapter 9 resolving conflicts and preventing violence Chapter 27 anger aggression and violence
Chapter 27 anger aggression and violence Chapter 10 section 2 protest resistance and violence
Chapter 10 section 2 protest resistance and violence Domestic and family violence protection act 2012
Domestic and family violence protection act 2012 Chapter 9 resolving conflicts and preventing violence
Chapter 9 resolving conflicts and preventing violence Chapter 10 section 2 protest resistance and violence
Chapter 10 section 2 protest resistance and violence Framework agreement on harassment and violence at work
Framework agreement on harassment and violence at work Chapter 7 domestic and family violence assessment
Chapter 7 domestic and family violence assessment Workplace violence and harassment quiz answers
Workplace violence and harassment quiz answers Seceding states of the confederacy
Seceding states of the confederacy Academy on violence and abuse
Academy on violence and abuse Hci patterns may or may not include code for implementation
Hci patterns may or may not include code for implementation Indicators of potential workplace violence:
Indicators of potential workplace violence: Violent one hour
Violent one hour Violent crime is up thesis statement
Violent crime is up thesis statement Chapter 9 lesson 3 understanding violence
Chapter 9 lesson 3 understanding violence Florida coalition against domestic violence
Florida coalition against domestic violence Different types of violence
Different types of violence Expressive crimes definition
Expressive crimes definition Indicators of potential workplace violence
Indicators of potential workplace violence Borderline violence conjugale
Borderline violence conjugale Galtung's conflict triangle
Galtung's conflict triangle Three r's for stopping domestic violence
Three r's for stopping domestic violence Pyramid of gender based violence
Pyramid of gender based violence Fvip georgia
Fvip georgia Domestic violence kink
Domestic violence kink Adolescent family violence program
Adolescent family violence program Stamp workplace violence
Stamp workplace violence Liz kelly continuum of violence
Liz kelly continuum of violence Horizontal violence theory
Horizontal violence theory Physical violence against women
Physical violence against women Xxxxxx violence
Xxxxxx violence Domestic violence in the hispanic community
Domestic violence in the hispanic community De-escalation worksheet
De-escalation worksheet