Investigating Clone Metrics of Merged Code Clones in




![Refactoring Detection • Use REF-FINDER[Prete 2010] to detect refactoring – REF-FINDER : A tool Refactoring Detection • Use REF-FINDER[Prete 2010] to detect refactoring – REF-FINDER : A tool](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-14.jpg)


![Detecting Code Clone: usim [Mende 2010] (1/3) • determine the similarity between two sequences. Detecting Code Clone: usim [Mende 2010] (1/3) • determine the similarity between two sequences.](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-18.jpg)
![Detecting Code Clone: usim [Mende 2010] (2/3) : a normalized sequence : length of Detecting Code Clone: usim [Mende 2010] (2/3) : a normalized sequence : length of](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-19.jpg)
![Detecting Code Clone: usim [Mende 2010] (3/3) • If usim value is over 40% Detecting Code Clone: usim [Mende 2010] (3/3) • If usim value is over 40%](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-20.jpg)



- Slides: 34

Investigating Clone Metrics of Merged Code Clones in Java Programs Inoue Laboratory Eunjong Choi Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 1

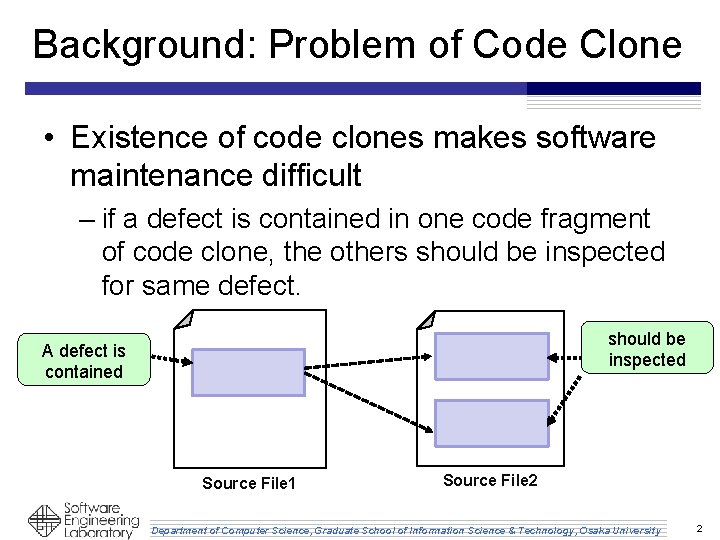
Background: Problem of Code Clone • Existence of code clones makes software maintenance difficult – if a defect is contained in one code fragment of code clone, the others should be inspected for same defect. should be inspected A defect is contained Source File 1 Source File 2 Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 2

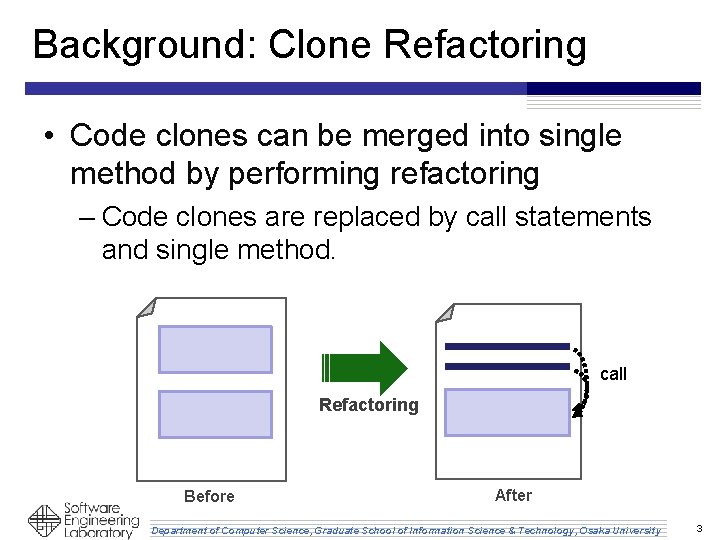
Background: Clone Refactoring • Code clones can be merged into single method by performing refactoring – Code clones are replaced by call statements and single method. call Refactoring Before After Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 3

Refactoring Patterns • • Extract Class Extract Method Extract Superclass Form Template Method Parameterize Method Pull Up Method Replace Method with Method Object Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 4

Refactoring Patterns • • Extract Class Extract Method Extract Superclass Form Template Method Parameterize Method Pull Up Method Replace Method with Method Object Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 5

An Example of Extract Method • If code clones are exist in the same class, they can be merged into single method in it. void print. Owing(double amount){ print. Banner(); System. out. println(“name: ”+ _name); System. out. println(“amount”+ amount); void print. Owing(double amount){ print. Banner(); print. Details(amount); } } void print. Assets(double amount){ print. Result(); print. Details(amount); System. out. println(“name: ”+ _name); System. out. println(“amount”+ amount); } Before } void print. Details(double amount){ System. out. println(“name: ”+ _name); System. out. println(“amount”+ amount); } After Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 6

An Example of Replace Method with Method Object • If code clones that use local variables are existed, they can be merged into single method in a new class Class Order. . . double price(){ double Primary. Base. Price; double secondary. Base. Price; double tertiary. Base. Price; . . } double discount(){ double Primary. Base. Price; double secondary. Base. Price; double tertiary. Base. Price; . . } Before Order price() discount() Price. Calculator primary. Base. Price secondary. Base. Price tertiary. Base. Price Compute() return new Price. Calculator(this). compute() After Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 7

Motivation of Study (1/3) • What kind of code clones were performed refactoring in the past? – Do not know what characteristics of code clones are appropriate for performing refactoring What characteristics of code clones? ? ? ? ? Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 8

Motivation of Study (2/3) • How code clones were performed refactoring? – Do not know which refactoring pattern is preferentially necessary for a tool support clone refactoring Which refactoring pattern? ? Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 9

Motivation of Study (3/3) • The following information is necessary – Characteristics of code clones that were performed refactoring – Refactoring patterns that were applied to code clones • Investigate history data of Java open source projects. • To implementate a tool support clone refactoring Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 10

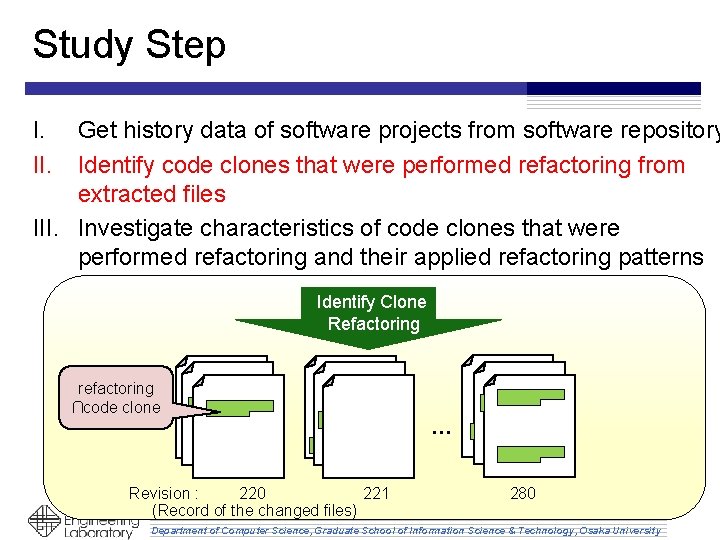
Study Step I. II. Get history data of software projects from software repository Identify code clones that were performed refactoring from extracted files III. Investigate characteristics of code clones that were performed refactoring and their applied refactoring patterns software repository extract Get … Revision : 220 221 280 (Record of the changed files) Department of Computer Science, Graduate School of Information Science & Technology, Osaka University

Study Step I. II. Get history data of software projects from software repository Identify code clones that were performed refactoring from extracted files III. Investigate characteristics of code clones that were performed refactoring and their applied refactoring patterns Identify Clone Refactoring refactoring ∩code clone … Revision : 220 221 280 (Record of the changed files) Department of Computer Science, Graduate School of Information Science & Technology, Osaka University

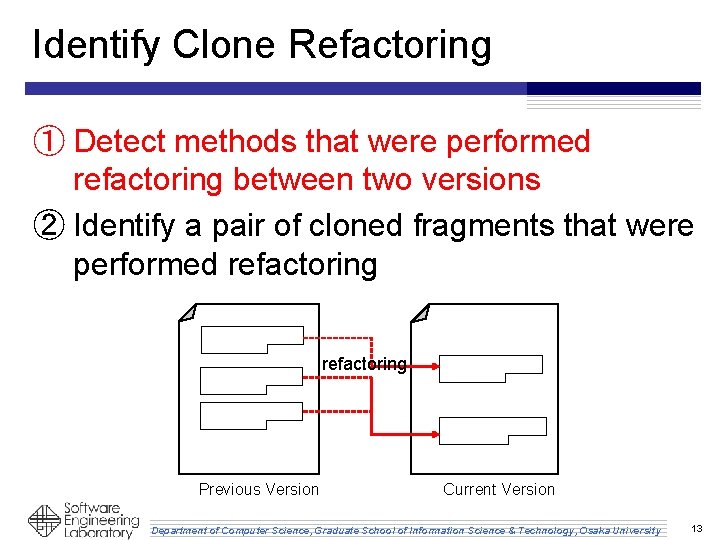
Identify Clone Refactoring ① Detect methods that were performed refactoring between two versions ② Identify a pair of cloned fragments that were performed refactoring Previous Version Current Version Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 13
![Refactoring Detection Use REFFINDERPrete 2010 to detect refactoring REFFINDER A tool Refactoring Detection • Use REF-FINDER[Prete 2010] to detect refactoring – REF-FINDER : A tool](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-14.jpg)
Refactoring Detection • Use REF-FINDER[Prete 2010] to detect refactoring – REF-FINDER : A tool that Identifies refactoring between two program versions – High recall and precision • Overall precision is 0. 79 and recall is 0. 95 [Prete 2010] Template-based Reconstruction of Complex Refactorings, K. Prete, N. Rachatasumrit, N. Sudan, and M. Kim, Proceedings of the 26 th IEEE International Conference on Software Maintenance, Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 14

Identify Clone Refactoring ① Detect methods that were performed refactoring between two versions ② Identify a pair of cloned method that were performed refactoring Previous version Current version Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 15

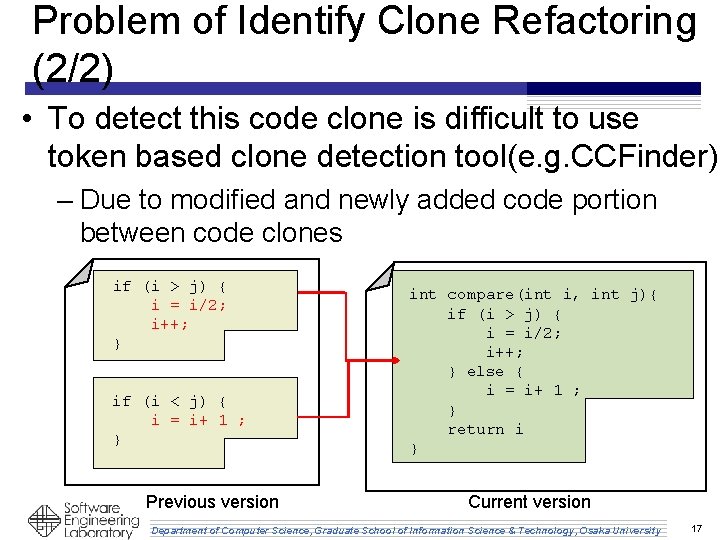
Problem of Identify Clone Refactoring (1/2) • Programmer often perform refactoring between code clones with low similarity if (i > j) { i = i/2; i++; } if (i < j) { i = i+ 1 ; } int compare(int i, int j){ if (i > j) { i = i/2; i++; } else { i = i+ 1 ; } return i } Previous version Current version Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 16

Problem of Identify Clone Refactoring (2/2) • To detect this code clone is difficult to use token based clone detection tool(e. g. CCFinder) – Due to modified and newly added code portion between code clones if (i > j) { i = i/2; i++; } if (i < j) { i = i+ 1 ; } int compare(int i, int j){ if (i > j) { i = i/2; i++; } else { i = i+ 1 ; } return i } Previous version Current version Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 17
![Detecting Code Clone usim Mende 2010 13 determine the similarity between two sequences Detecting Code Clone: usim [Mende 2010] (1/3) • determine the similarity between two sequences.](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-18.jpg)
Detecting Code Clone: usim [Mende 2010] (1/3) • determine the similarity between two sequences. – Using Levenshtein distance [Levenshtein 1966] • measuring the amount of difference between two sequences – The minimal amount of changes necessary to transform one sequence of items into a second sequence of items • Levenshtein distance between survey and surgery is 2 [Baeza-Yates] +1 +1 survey → surgery [Mende 2010] an evaludation of code similarity identification for the grow-and-prune model, T. Mende, R. Koschke, and Felix Beckwermert, Journal of Software Maintenance 21(2): 143 -169 (2009) [Levenshtein 1966] Levenshtein VI. Binary codes capable of correcting deletions, insertions, and reversals. Technical Report 8, Soviet Physics Doklady, 1966. [Baeza-Yates] R. Baeza-Yates and B. Ribeiro-Neto. Modern Information Retrieval: The Concepts and Technology behind Search (2 nd Edition). Addison Wesley, 2010. Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 18
![Detecting Code Clone usim Mende 2010 23 a normalized sequence length of Detecting Code Clone: usim [Mende 2010] (2/3) : a normalized sequence : length of](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-19.jpg)
Detecting Code Clone: usim [Mende 2010] (2/3) : a normalized sequence : length of normalized sequence : number of items that have to be changed to turn function fx into fy • Levenshtein distance between two sequences are normalized by the maximum size between them [Mende 2010] an evaludation of code similarity identification for the grow-and-prune model, T. Mende, R. 19 Department of Computer Science, Graduate School of Information Science & Technology, Osaka University Koschke, and Felix Beckwermert, Journal of Software Maintenance 21(2): 143 -169 (2009)
![Detecting Code Clone usim Mende 2010 33 If usim value is over 40 Detecting Code Clone: usim [Mende 2010] (3/3) • If usim value is over 40%](https://slidetodoc.com/presentation_image_h/8a6a6a38be63e1801c754112a69d6d87/image-20.jpg)
Detecting Code Clone: usim [Mende 2010] (3/3) • If usim value is over 40% between two sequences, I define them as code clone[Mende 2010] an evaludation of code similarity identification for the grow-and-prune model, T. Mende, R. 20 Department of Computer Science, Graduate School of Information Science & Technology, Osaka University Koschke, and Felix Beckwermert, Journal of Software Maintenance 21(2): 143 -169 (2009)

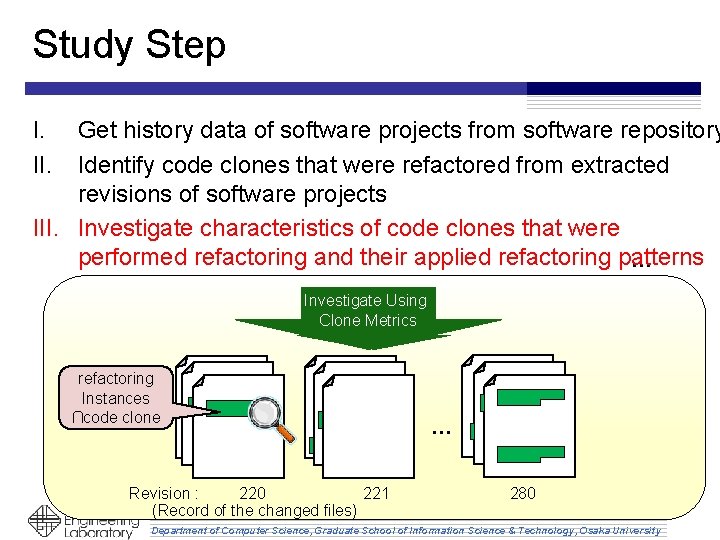
Study Step I. II. Get history data of software projects from software repository Identify code clones that were refactored from extracted revisions of software projects III. Investigate characteristics of code clones that were performed refactoring and their applied refactoring patterns … Investigate Using Clone Metrics refactoring Instances ∩code clone … Revision : 220 221 280 (Record of the changed files) Department of Computer Science, Graduate School of Information Science & Technology, Osaka University

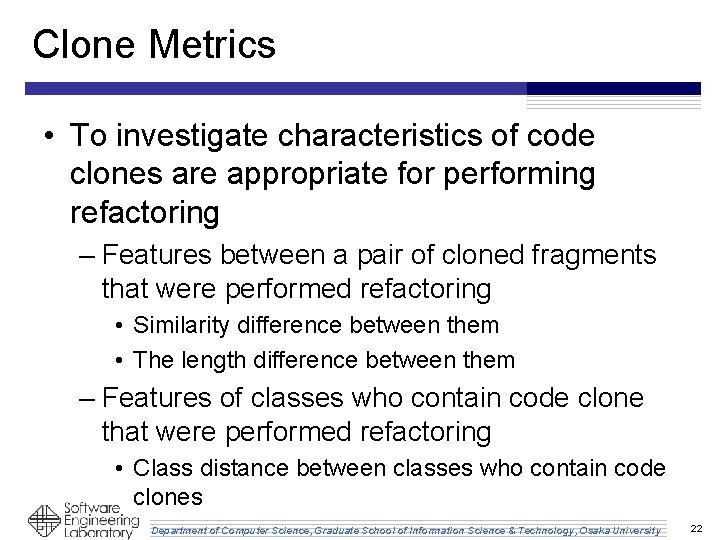
Clone Metrics • To investigate characteristics of code clones are appropriate for performing refactoring – Features between a pair of cloned fragments that were performed refactoring • Similarity difference between them • The length difference between them – Features of classes who contain code clone that were performed refactoring • Class distance between classes who contain code clones Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 22

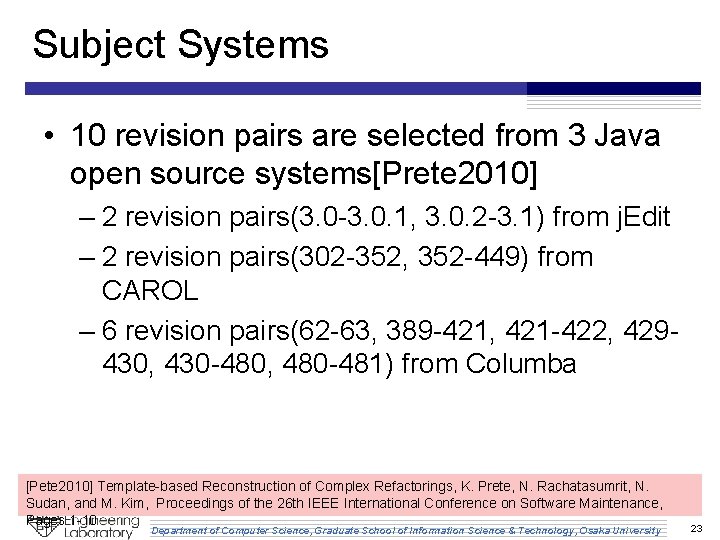
Subject Systems • 10 revision pairs are selected from 3 Java open source systems[Prete 2010] – 2 revision pairs(3. 0 -3. 0. 1, 3. 0. 2 -3. 1) from j. Edit – 2 revision pairs(302 -352, 352 -449) from CAROL – 6 revision pairs(62 -63, 389 -421, 421 -422, 429430, 430 -480, 480 -481) from Columba [Pete 2010] Template-based Reconstruction of Complex Refactorings, K. Prete, N. Rachatasumrit, N. Sudan, and M. Kim, Proceedings of the 26 th IEEE International Conference on Software Maintenance, Pages 1 -10 Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 23

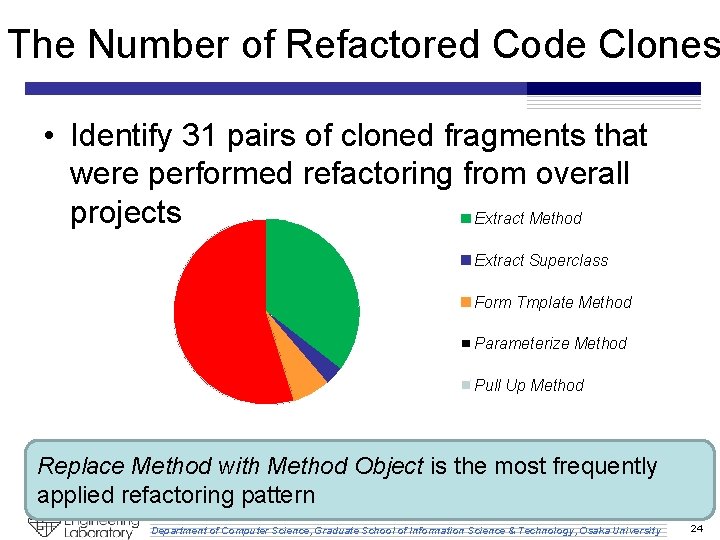
The Number of Refactored Code Clones • Identify 31 pairs of cloned fragments that were performed refactoring from overall projects Extract Method Extract Superclass Form Tmplate Method Parameterize Method Pull Up Method Replace Method with Method Object is the most frequently applied refactoring pattern Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 24

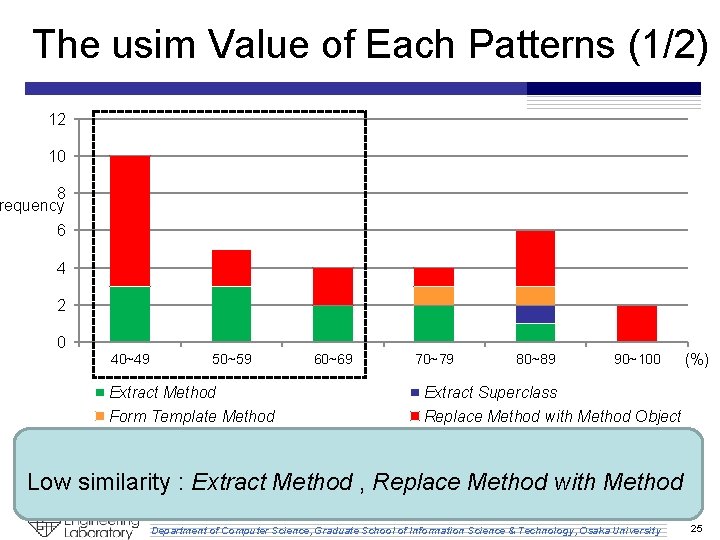
The usim Value of Each Patterns (1/2) 12 10 8 requency 6 4 2 0 40~49 50~59 Extract Method Form Template Method 60~69 70~79 80~89 90~100 (%) Extract Superclass Replace Method with Method Object Low similarity : Extract Method , Replace Method with Method Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 25

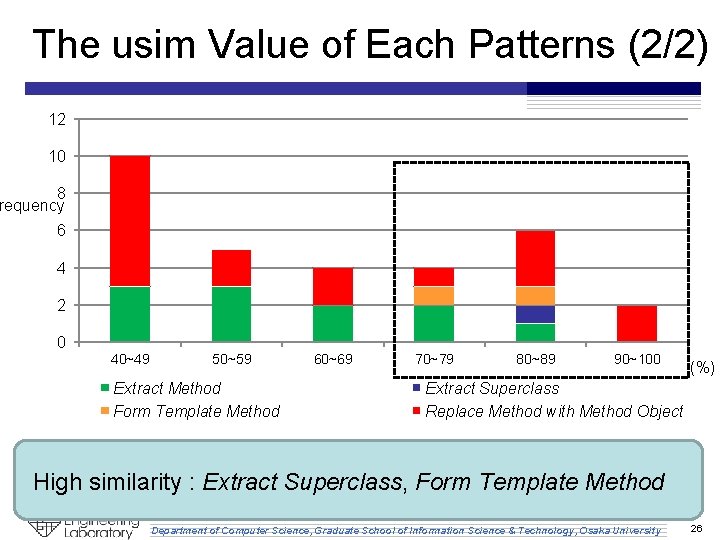
The usim Value of Each Patterns (2/2) 12 10 8 requency 6 4 2 0 40~49 50~59 Extract Method Form Template Method 60~69 70~79 80~89 90~100 (%) Extract Superclass Replace Method with Method Object High similarity : Extract Superclass, Form Template Method Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 26

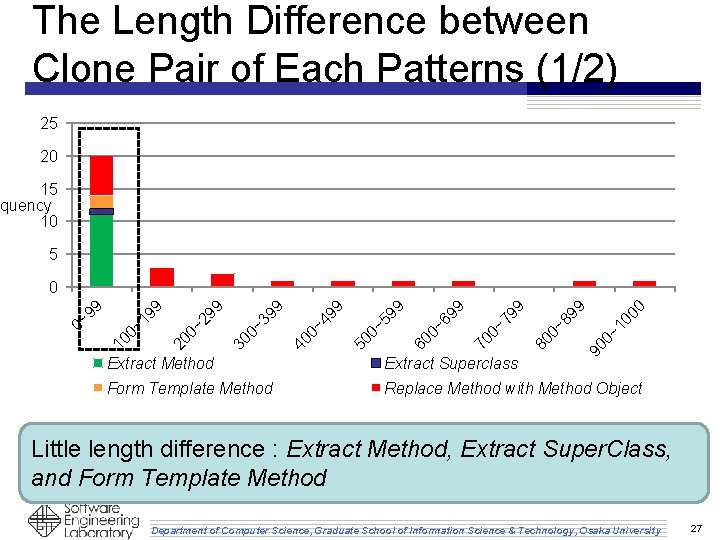
The Length Difference between Clone Pair of Each Patterns (1/2) 25 20 15 quency 10 5 00 10 90 0~ 0~ 89 9 80 0~ 79 9 70 0~ 69 9 60 0~ 59 9 50 0~ 49 9 40 0~ 39 9 30 0~ 29 9 20 0~ 19 9 10 0~ 9 9 0 Extract Method Extract Superclass Form Template Method Replace Method with Method Object Little length difference : Extract Method, Extract Super. Class, and Form Template Method Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 27

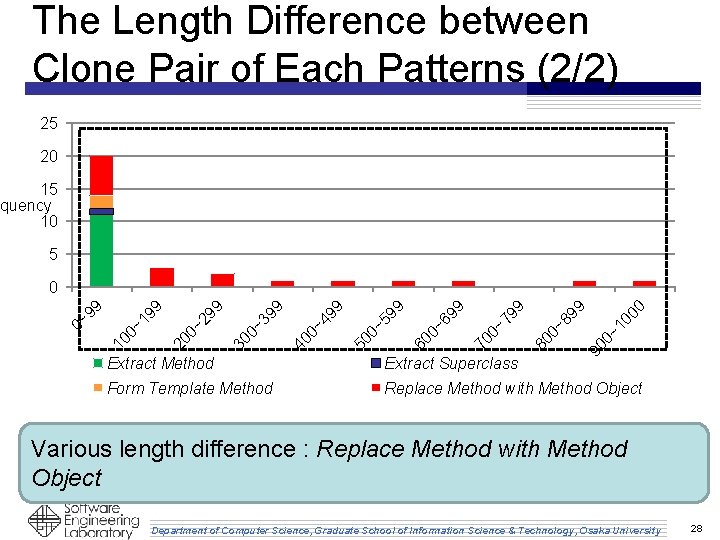
The Length Difference between Clone Pair of Each Patterns (2/2) 25 20 15 quency 10 5 00 10 90 0~ 0~ 89 9 80 0~ 79 9 70 0~ 69 9 60 0~ 59 9 50 0~ 49 9 40 0~ 39 9 30 0~ 29 9 20 0~ 19 9 10 0~ 9 9 0 Extract Method Extract Superclass Form Template Method Replace Method with Method Object Various length difference : Replace Method with Method Object Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 28

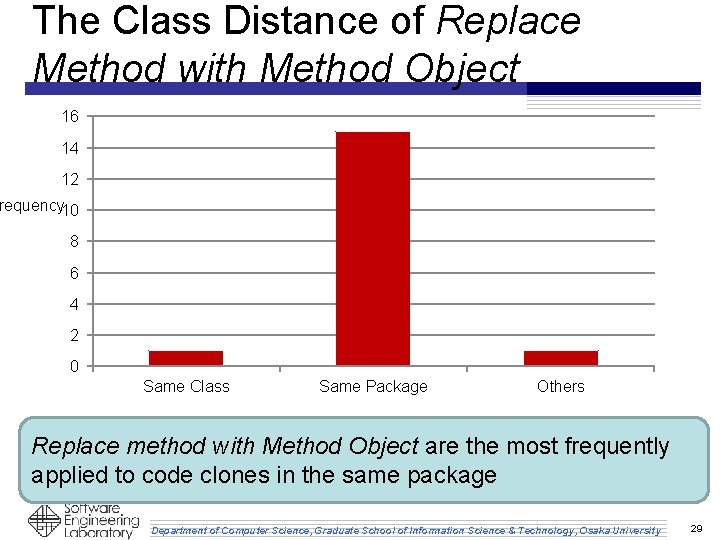
The Class Distance of Replace Method with Method Object 16 14 12 requency 10 8 6 4 2 0 Same Class Same Package Others Replace method with Method Object are the most frequently applied to code clones in the same package Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 29

Conclusion • Investigate characteristics of code clones that were performed refactoring – From 3 Java open source software. – Use REF-FINDER to detect refactoring – Use usim to identify code clones • The most frequently applied refactoring pattern is Replace Method with Method Object – They are applied to a pair of cloned fragment with little similarity – They are applied to various length difference in the same package Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 30

Study Plan (1/3) • The first year : investigate a predictor future code clone refactoring Can predict future refactoring activity? Cloned code Cloned code Current Future Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 31

Study Plan (2/3) • The second year : suggest metrics to measure clone refactoring Can metric measure clone refactoring? refactoring Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 32

Study Plan (3/3) • The third year : develop a tool support clone refactoring Can a tool support clone refactoring? refactoring Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 33

Thank you for paying attention Department of Computer Science, Graduate School of Information Science & Technology, Osaka University 34
 Steps of gene cloning
Steps of gene cloning Medicine wheel clones
Medicine wheel clones Book about clones used for organs
Book about clones used for organs Clone evolution code
Clone evolution code Suggested upper merged ontology
Suggested upper merged ontology History of wearing floral designs as personal adornment
History of wearing floral designs as personal adornment Ffa history timeline
Ffa history timeline Northern renaissance thinkers merged humanist ideas with
Northern renaissance thinkers merged humanist ideas with Busceral
Busceral Plenty of fish clone
Plenty of fish clone Cdna library diagram
Cdna library diagram Lets clone a mouse
Lets clone a mouse Clone stamp tool photoshop definition
Clone stamp tool photoshop definition Scientists show dna from
Scientists show dna from Fluod
Fluod Human clone
Human clone Wordle map
Wordle map Zerto offsite clone
Zerto offsite clone Slim new clone is
Slim new clone is Teachable clone
Teachable clone Ictsas305
Ictsas305 Gpio
Gpio Modern genetics human inheritance answer key
Modern genetics human inheritance answer key Clone relationship dynamics 365
Clone relationship dynamics 365 Investigating system requirements
Investigating system requirements What shape is this
What shape is this Oxbow lake formation
Oxbow lake formation Investigating graphs of polynomial functions
Investigating graphs of polynomial functions 6-7 investigating graphs of polynomial functions
6-7 investigating graphs of polynomial functions Thomas edison lesson
Thomas edison lesson Investigating polynomials
Investigating polynomials Investigating the properties of sound
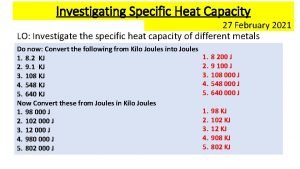
Investigating the properties of sound Investigating specific heat capacity
Investigating specific heat capacity 6-7 investigating graphs of polynomial functions
6-7 investigating graphs of polynomial functions Unit 14 investigating customer service assignment 1
Unit 14 investigating customer service assignment 1