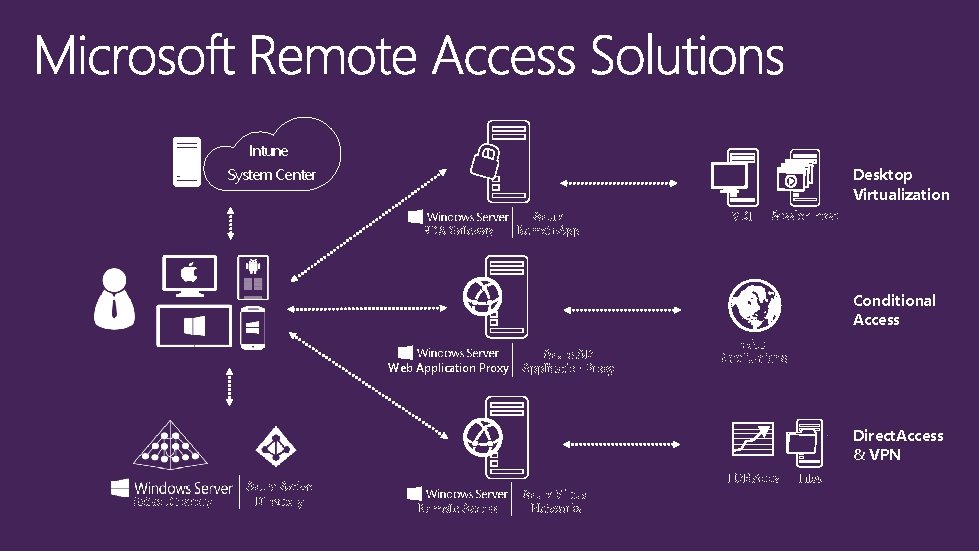
Intune System Center Desktop Virtualization RDS Gateway Azure





















- Slides: 41





Intune System Center Desktop Virtualization RDS Gateway Azure Remote. App VDI Session host Conditional Access Web Application Proxy Azure AD Application Proxy Web Applications Direct. Access & VPN Active Directory Azure Active Directory LOB Apps Remote Access Azure Virtual Networks Files

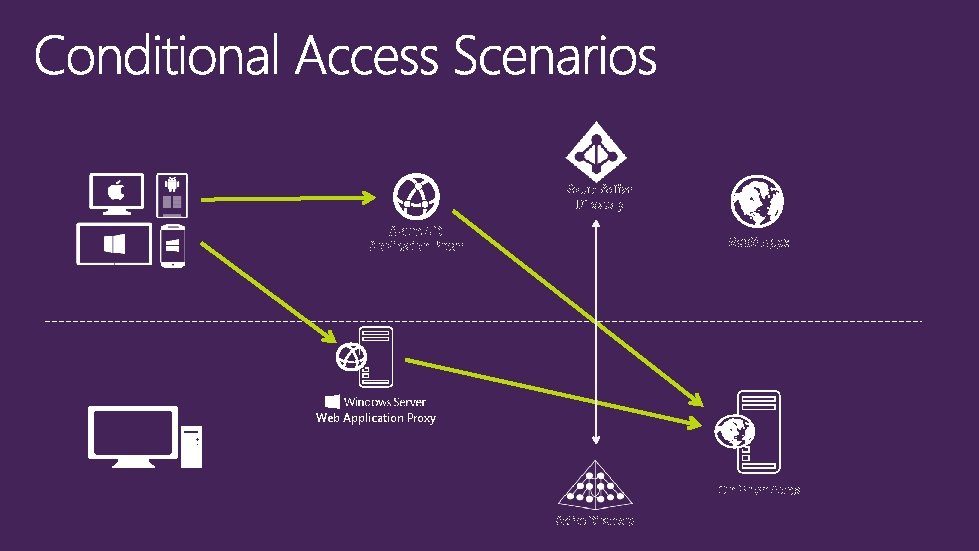
Azure Active Directory Azure AD Application Proxy Saa. S Apps Web Application Proxy On-Prem Apps Active Directory


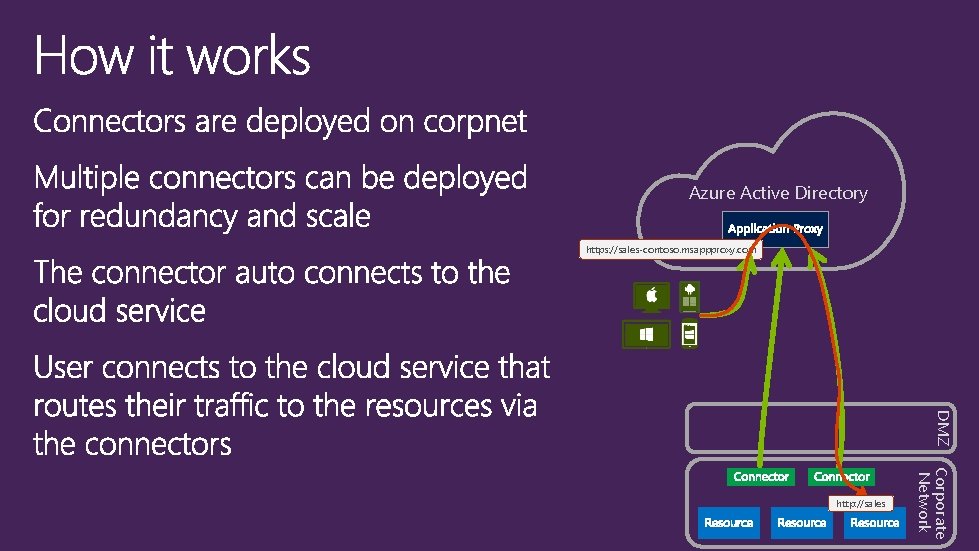
Remote Access as a Service Easily publish your on-prem applications to users outside the corporate network On-Premises Applications Extend Azure AD to on-prem Utilize Azure AD as a central management point for all your apps Azure Active Directory


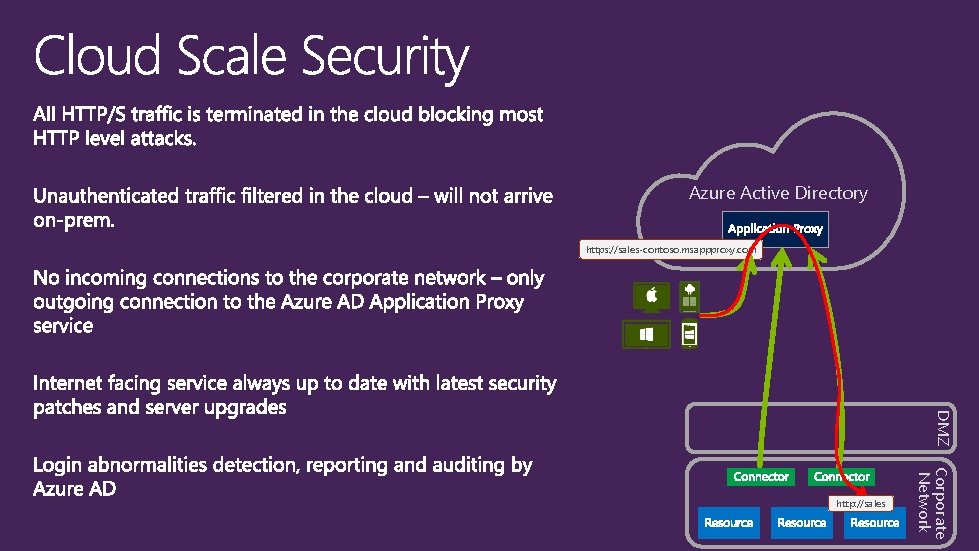
Azure Active Directory https: //sales-contoso. msappproxy. com DMZ Corporate Network http: //sales

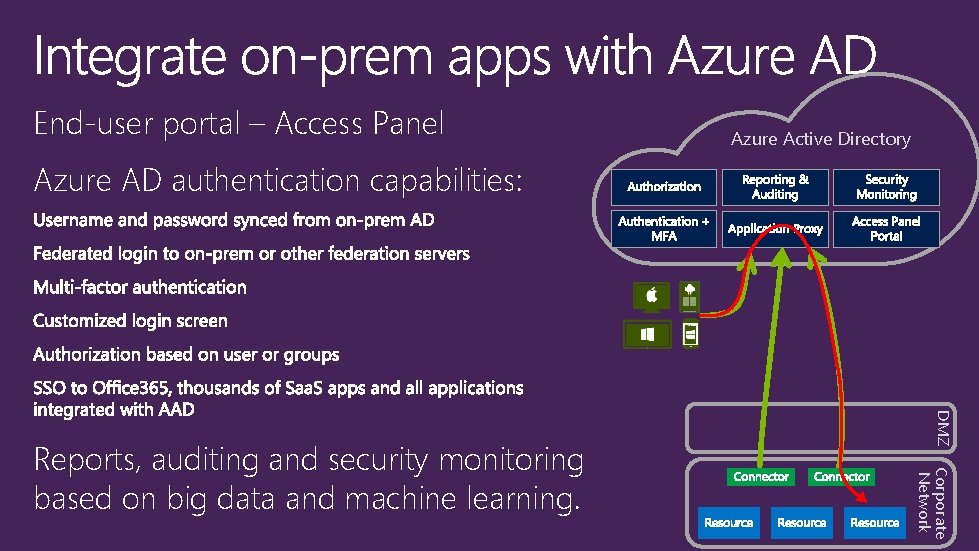
End-user portal – Access Panel Azure Active Directory Azure AD authentication capabilities: DMZ Corporate Network Reports, auditing and security monitoring based on big data and machine learning.

Azure Active Directory https: //sales-contoso. msappproxy. com DMZ Corporate Network http: //sales


https: //myapps. microsoft. com/ User: juan@contoso 25. onmicrosoft. com Password: Pass 1234





https: //*. sp-apps. contoso. com





http: //blogs. technet. com/b/ad/ http: //blogs. technet. com/b/applicationproxyblog/ http: //msdn. microsoft. com/en-us/library/azure/dn 768219. aspx http: //technet. microsoft. com/en-us/library/dn 584107. aspx aadapfeedback@microsoft. com

Tue, Oct 28 3: 15 PM-4: 30 PM EM-B 214 Privileged Access Management for Active Directory Wed, Oct 29 8: 30 AM-9: 45 AM EM-B 316 Directory Integration: Creating One Directory with Active Directory and Azure Active Directory Wed, Oct 29 3: 15 PM-4: 30 PM EM-B 319 Microsoft Identity Manager v. Next Overview Wed, Oct 29 3: 15 PM-4: 30 PM CDP-B 210 Cloud Identity: Microsoft Azure Active Directory Explained Thu, Oct 30 10: 15 AM-11: 30 AM CDP-B 312 Microsoft Azure Active Directory Premium, in Depth Thu, Oct 30 12: 00 PM-1: 15 PM EM-B 310 Active Directory + BYOD = Peace of Mind Thu, Oct 30 5: 00 PM-6: 15 PM DEV-B 322 Building Web Apps and Mobile Apps Using Microsoft Azure Active Directory for Identity Management Fri, Oct 31 8: 30 AM-9: 45 AM CDP-B 207 Securing Organizations: Azure Active Directory Intelligence as a Differentiator Fri, Oct 31 10: 15 AM-11: 30 AM EM-B 410 Advanced Active Directory Federation Services and Web Application Proxy Troubleshooting Fri, Oct 31 2: 45 PM-4: 00 PM EM-B 313 Microsoft Azure Multi-Factor Authentication Deep Dive: Securing Access on Premises and in the Cloud

http: //channel 9. msdn. com/Events/Tech. Ed www. microsoft. com/learning http: //microsoft. com/technet http: //developer. microsoft. com

http: //aka. ms/enterprise mobilitysuite http: //aka. ms/microsoftintune http: //aka. ms/configmgr http: //aka. ms/hi http: //aka. ms/aip http: //aka. ms/virtualdesktop





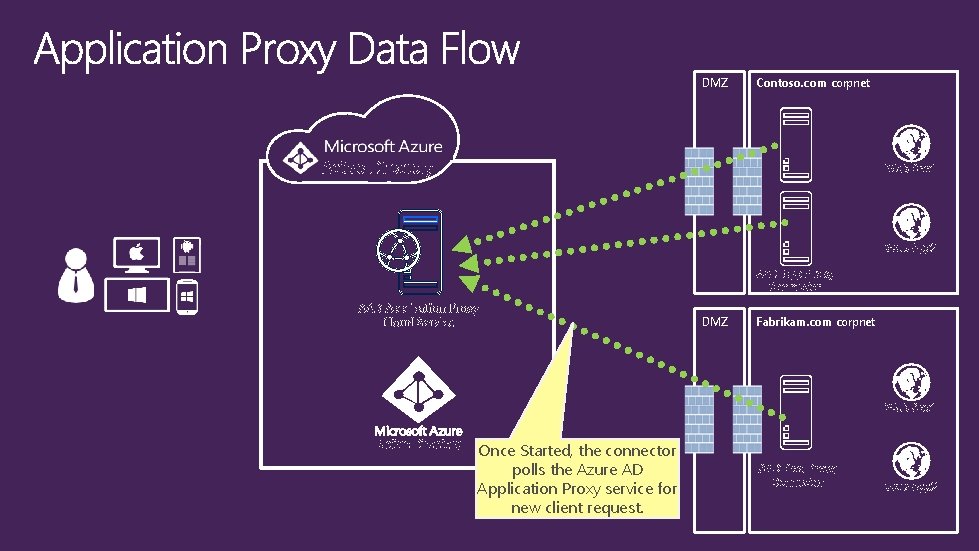
DMZ Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service DMZ Fabrikam. com corpnet Web App 1 Active Directory Once Started, the connector polls the Azure AD Application Proxy service for new client request. AAD App Proxy Connector Web App 2

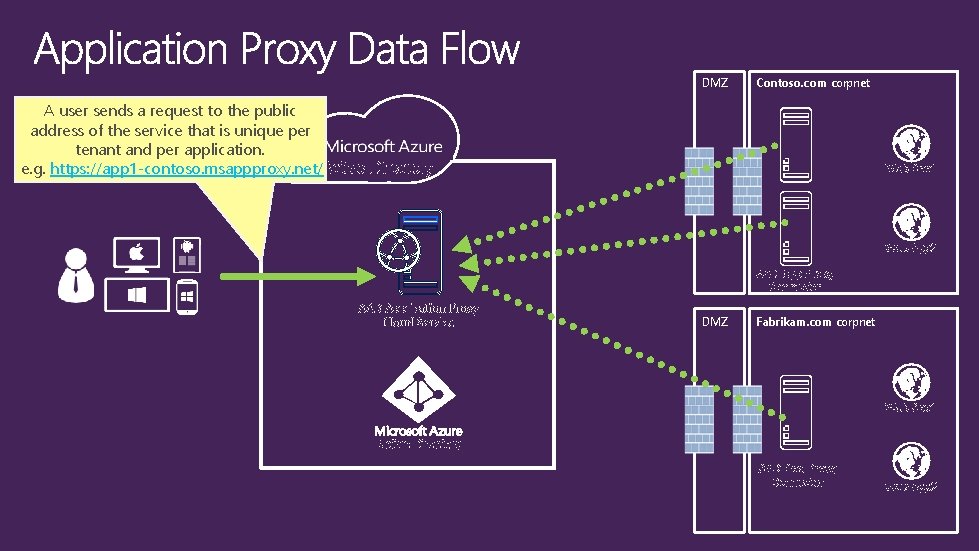
DMZ Contoso. com corpnet A user sends a request to the public address of the service that is unique per tenant and per application. e. g. https: //app 1 -contoso. msappproxy. net/Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service DMZ Fabrikam. com corpnet Web App 1 Active Directory AAD App Proxy Connector Web App 2

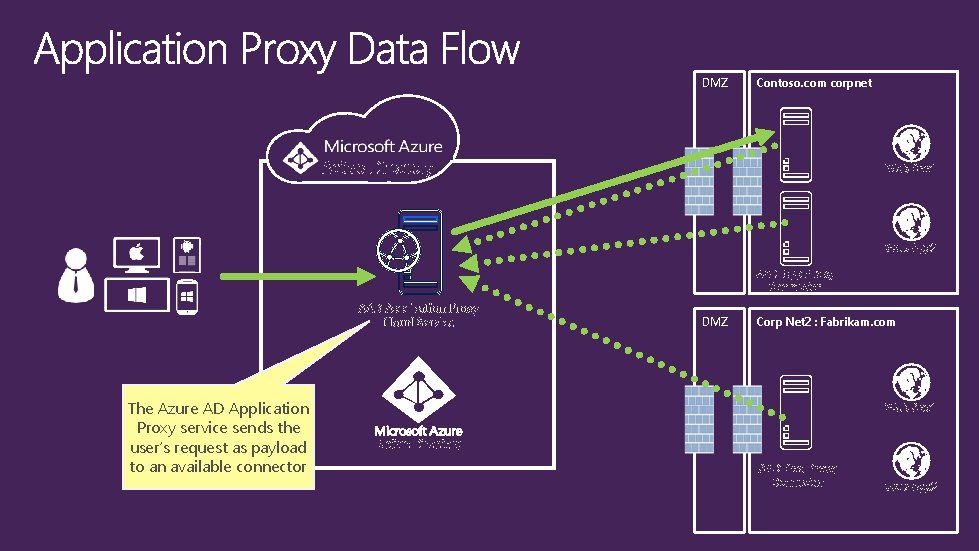
DMZ Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service The Azure AD Application Proxy service sends the user’s request as payload to an available connector DMZ Corp Net 2 : Fabrikam. com Web App 1 Active Directory AAD App Proxy Connector Web App 2

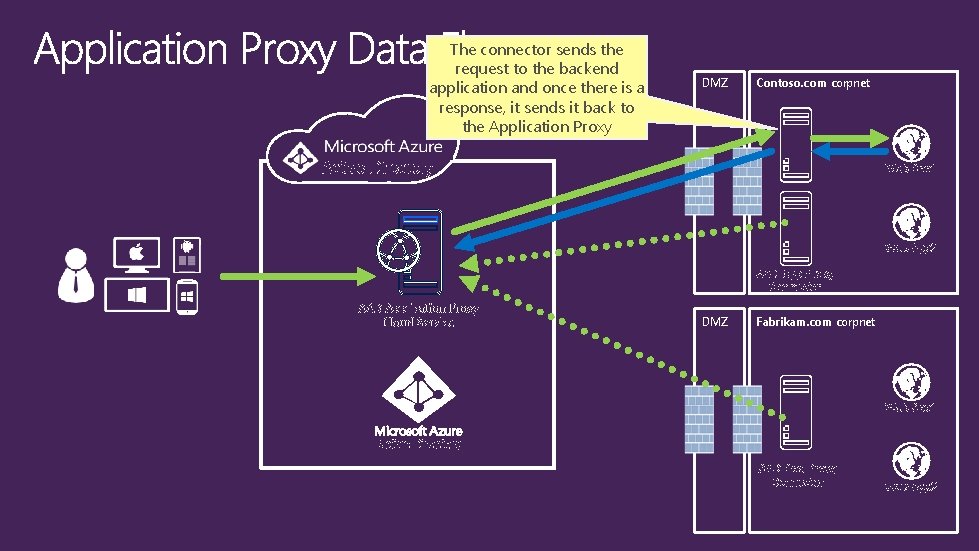
The connector sends the request to the backend application and once there is a response, it sends it back to the Application Proxy DMZ Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service DMZ Fabrikam. com corpnet Web App 1 Active Directory AAD App Proxy Connector Web App 2

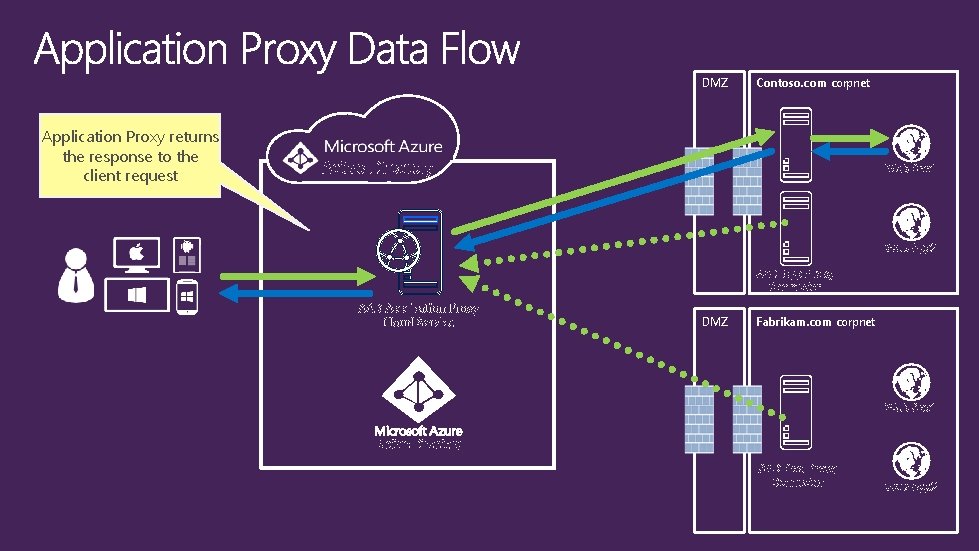
DMZ Application Proxy returns the response to the client request Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service DMZ Fabrikam. com corpnet Web App 1 Active Directory AAD App Proxy Connector Web App 2

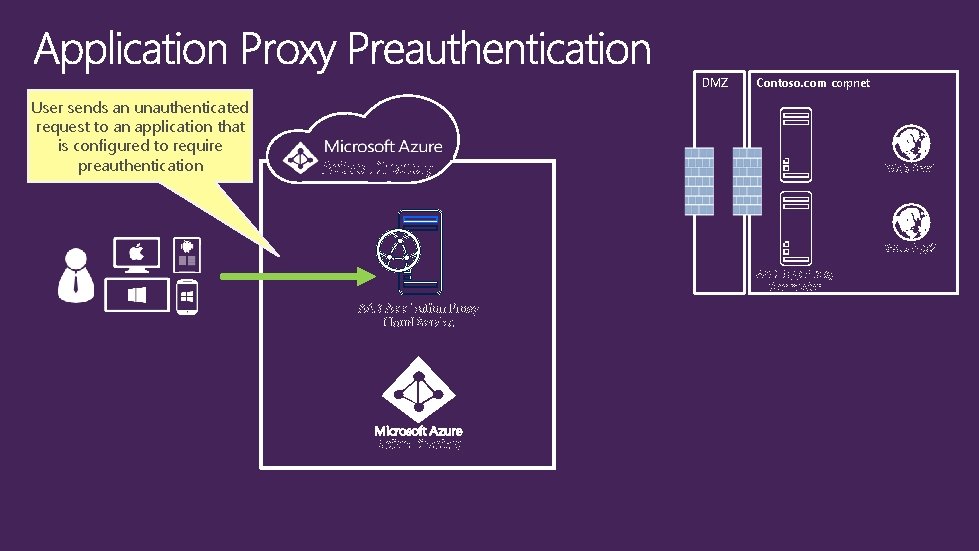
DMZ User sends an unauthenticated request to an application that is configured to require preauthentication Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service Active Directory

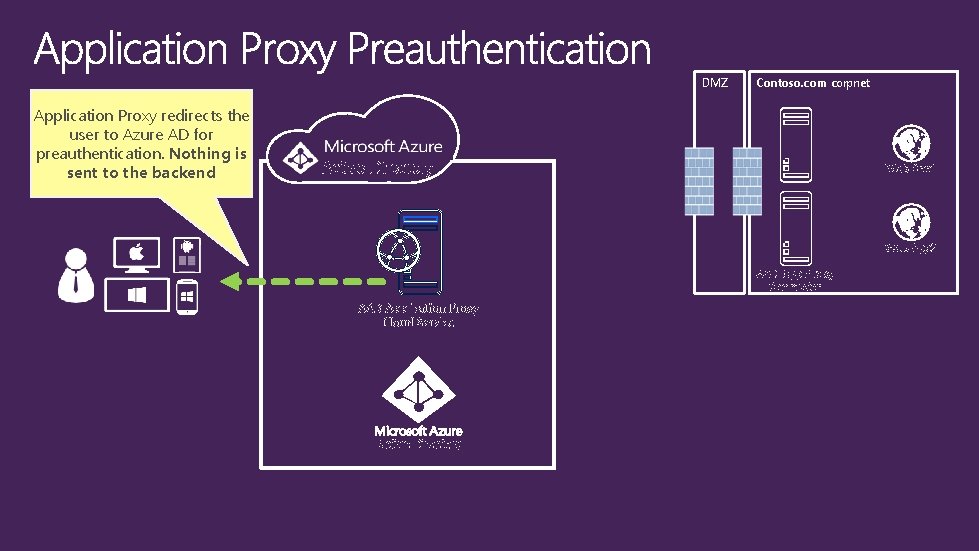
DMZ Application Proxy redirects the user to Azure AD for preauthentication. Nothing is sent to the backend Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service Active Directory

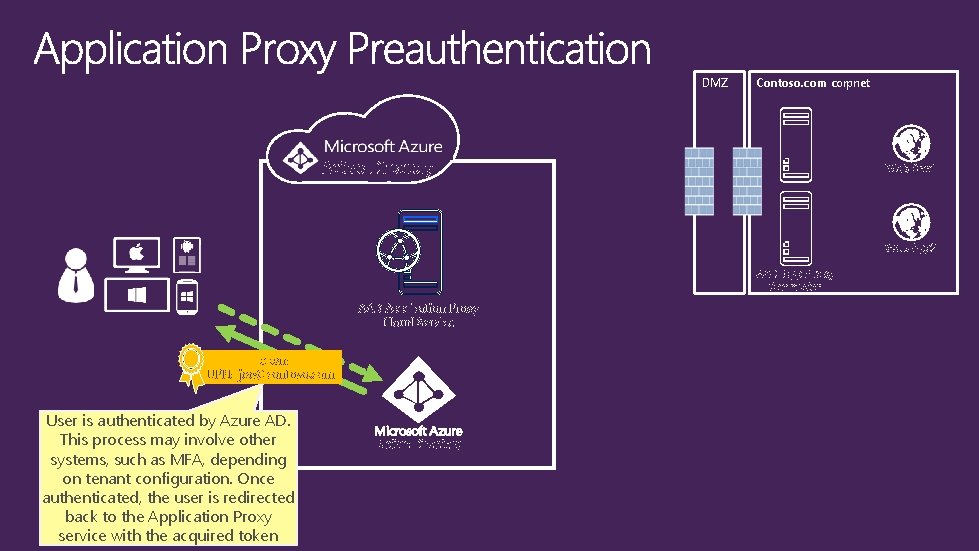
DMZ Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service Token: UPN=joe@contoso. com User is authenticated by Azure AD. This process may involve other systems, such as MFA, depending on tenant configuration. Once authenticated, the user is redirected back to the Application Proxy service with the acquired token Active Directory

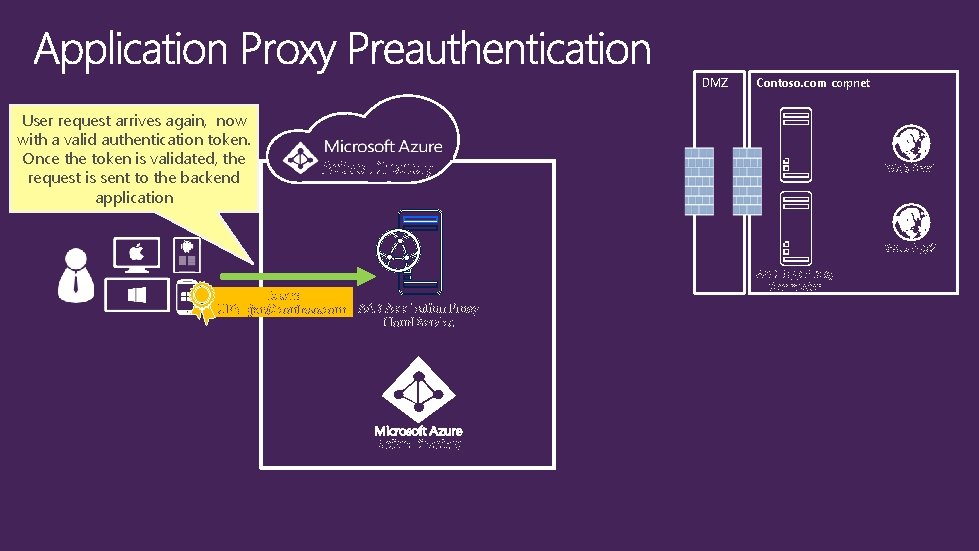
DMZ User request arrives again, now with a valid authentication token. Once the token is validated, the request is sent to the backend application Contoso. com corpnet Active Directory Web App 1 Web App 2 Token: UPN=joe@contoso. com AAD App Proxy Connector AAD Application Proxy Cloud Service Active Directory

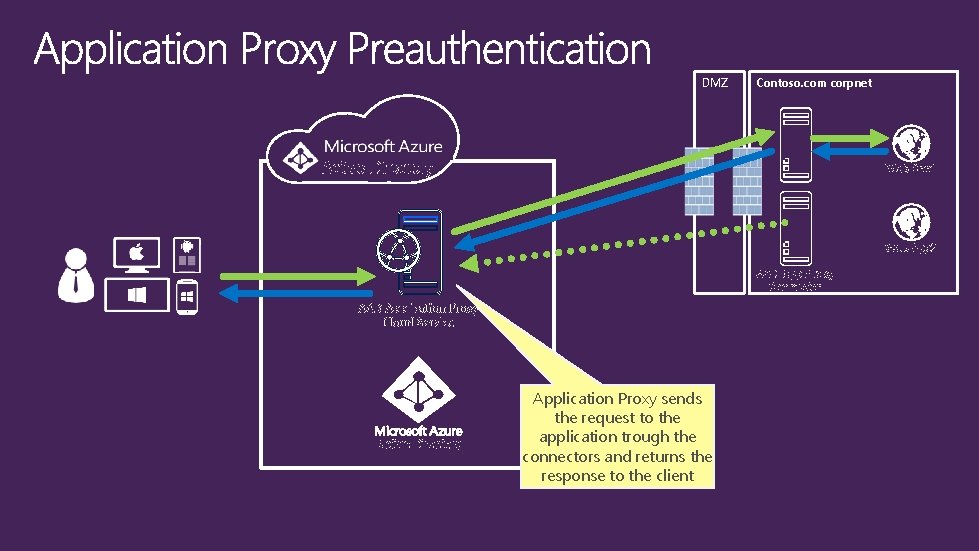
DMZ Contoso. com corpnet Active Directory Web App 1 Web App 2 AAD App Proxy Connector AAD Application Proxy Cloud Service Active Directory Application Proxy sends the request to the application trough the connectors and returns the response to the client