Intrusion Detection and Forensics for Selfdefending Wireless Networks





- Slides: 7

Intrusion Detection and Forensics for Self-defending Wireless Networks Yan Chen Dept. of Electrical Engineering and Computer Science Northwestern University Spring Review 2008 Award # : FA 9550 -07 -1 -0074

Technical Approach: Self-Defending Wireless Networks • Proactively search of vulnerability for wireless network protocols – Intelligent and thorough checking through combo of manual analysis + auto search with formal methods – First, manual analysis provide hints and right level of abstraction for auto search – Then specify the specs and potential capabilities of attackers in a formal language TLA+ – Then model check for any possible attacks • Defend against emerging threat – Worm: network-based polymorphic worm signature generations – Botnet: IRC (Internet relay chat) based C&C detection and mitigation

Technical Breakthroughs (I) • Intelligent vulnerability analysis – Focused on outsider attacks, i. e. , w/ unprotected error msgs – Checked the complete spec of 802. 16 e before authentication » Found some vulnerability, e. g. , for ranging (but needs to change MAC) – Checked the mobile IPv 4/v 6 » Find an easy attack to disable the route optimization of MIPv 6 ! – Checked the Wi. Fi 802. 11 » Find an easy attack to Do. S any new clients from joining the – Partnered with Motorola, very interested in the vulnerability found

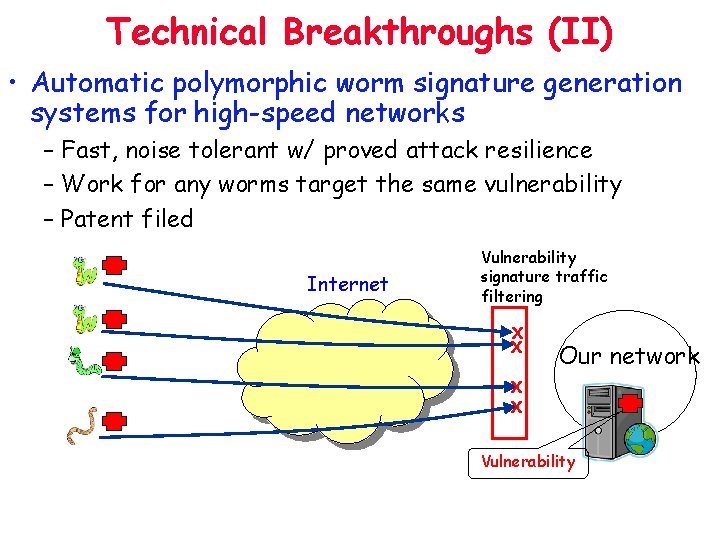
Technical Breakthroughs (II) • Automatic polymorphic worm signature generation systems for high-speed networks – Fast, noise tolerant w/ proved attack resilience – Work for any worms target the same vulnerability – Patent filed Internet Vulnerability signature traffic filtering X X Our network X X Vulnerability

Accomplishments of 2007 • Four conference papers, one journal paper and two book chapters – Accurate and Efficient Traffic Monitoring Using Adaptive Non-linear Sampling Method", to appear in the Proc. of IEEE INFOCOM, 2008 – Honeynet-based Botnet Scan Traffic Analysis, invited book chapter for Botnet Detection: Countering the Largest Security Threat, Springer, 2007. – Reversible Sketches: Enabling Monitoring and Analysis over Highspeed Data Streams, in ACM/IEEE Transaction on Networking, Volume 15, Issue 5, Oct. 2007. – Network-based and Attack-resilient Length Signature Generation for Zero-day Polymorphic Worms, in the Proc. of the 15 th IEEE International Conference on Network Protocols (ICNP), 2007. – Integrated Fault and Security Management, invited book chapter for Information Assurance: Dependability and Security in Networked Systems, Morgan Kaufmann Publishers, 2007. – Detecting Stealthy Spreaders Using Online Outdegree Histograms, in the Proc. of the 15 th IEEE International Workshop on Quality of Service (IWQo. S), 2007. – A Suite of Schemes for User-level Network Diagnosis without Infrastructure, in the Proc. of IEEE INFOCOM, 2007

Why AFOSR Support Important • Wireless networks prevalent and mission critical for AF GIG – Security particularly important for defense • AFOSR support opens door for collaboration with AFRL researchers – Annual PI meeting is a great venue for fostering collaboration – Currently working with Dr. Keesook Han for analyzing the next generation C&C of botnet – Obtain binary/source from Dr. Han – Plan to use the testbed developed at AFRL • Enable technology transfer to better secure AF wireless networks

Collaborations for Real Impact • Dr. Keesook Han from AFRL • Dr. Judy Fu from Motorola Labs – Talk to real product group on system implementations – Potential tech transfer to make more secure wireless network products