Introductory Concepts 1 Principles of Computer Network Design






- Slides: 39

Introductory Concepts 1

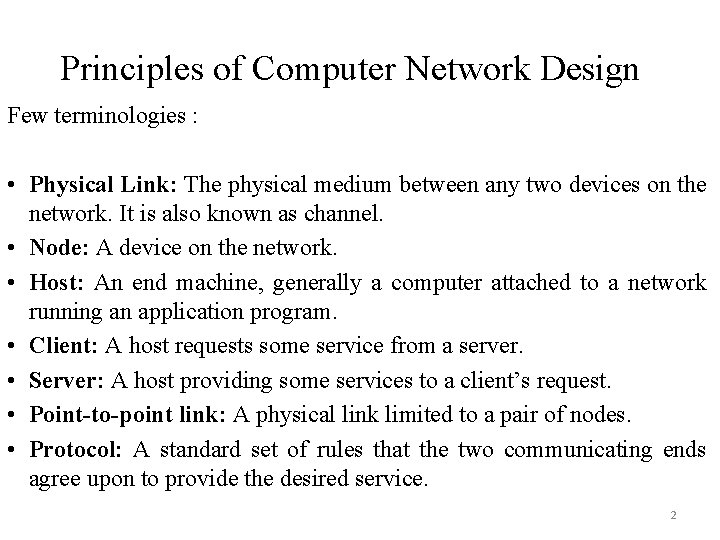
Principles of Computer Network Design Few terminologies : • Physical Link: The physical medium between any two devices on the network. It is also known as channel. • Node: A device on the network. • Host: An end machine, generally a computer attached to a network running an application program. • Client: A host requests some service from a server. • Server: A host providing some services to a client’s request. • Point-to-point link: A physical link limited to a pair of nodes. • Protocol: A standard set of rules that the two communicating ends agree upon to provide the desired service. 2

Contd… The link in network may belong to either of the following category: • Full-duplex link: This link is capable of transmitting information in both directions simultaneously. • Simplex link: This link is capable of transmitting information in one direction only. • Half-duplex link: This link is capable of transmitting information in both directions, but not simultaneously. Client-server model for computer network 3

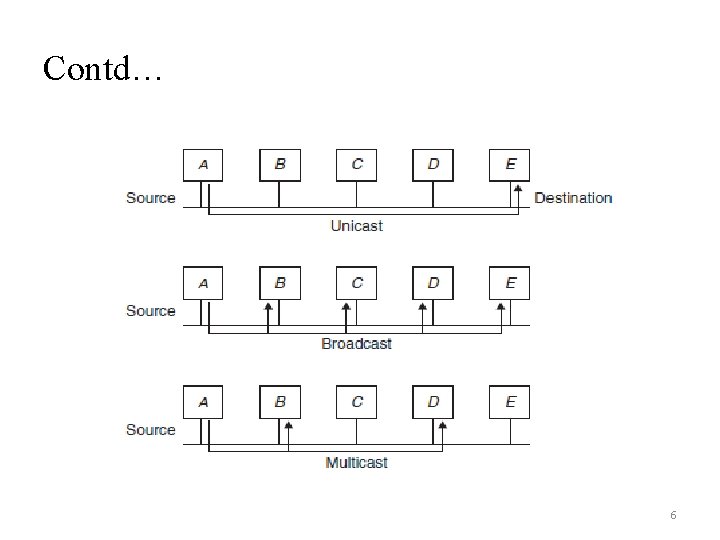
Contd… • A computer network is created using several nodes and links such that when a client sends a request message to a server, then this message may traverse through several nodes and links before reaching server. • The server replies to that request by sending the requested data. • The nodes in a computer network may run several protocols for providing services to a client. • The destination of transmitted data could be either one host or more than one host, or all hosts on that network. • Therefore, we have the concept of unicast, multicast, and broadcast transmission, respectively. 4

Contd… Unicast transmission: • The packet is sent from the sender toward one destination. • These transmissions are logically point to point. • Example- Most applications on the internet are of this type only. Broadcast transmission: • A packet sent by the sender will reach all hosts bon that network simultaneously. • Example- Application where a sender wants to send a message to hosts on a network. Multicast transmission: • A packet sent by the sender will not all but only certain number of hosts on that network simultaneously. • These transmissions are logically point to multipoint. • Example- Videoconference on the internet. 5

Contd… 6

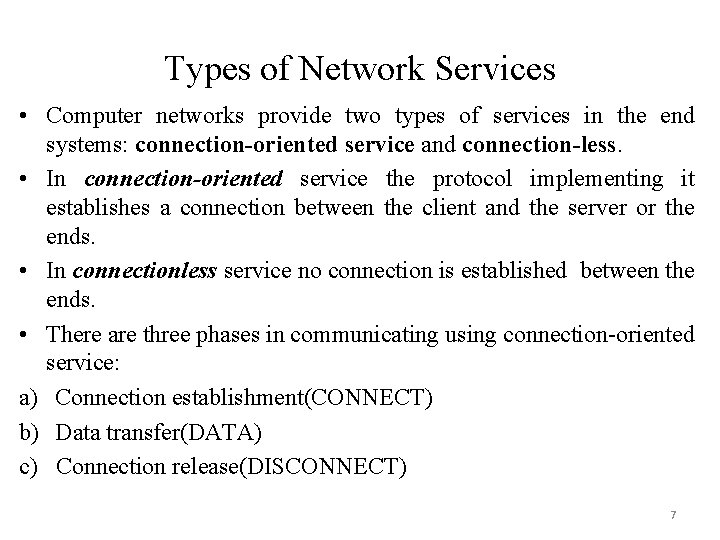
Types of Network Services • Computer networks provide two types of services in the end systems: connection-oriented service and connection-less. • In connection-oriented service the protocol implementing it establishes a connection between the client and the server or the ends. • In connectionless service no connection is established between the ends. • There are three phases in communicating using connection-oriented service: a) Connection establishment(CONNECT) b) Data transfer(DATA) c) Connection release(DISCONNECT) 7

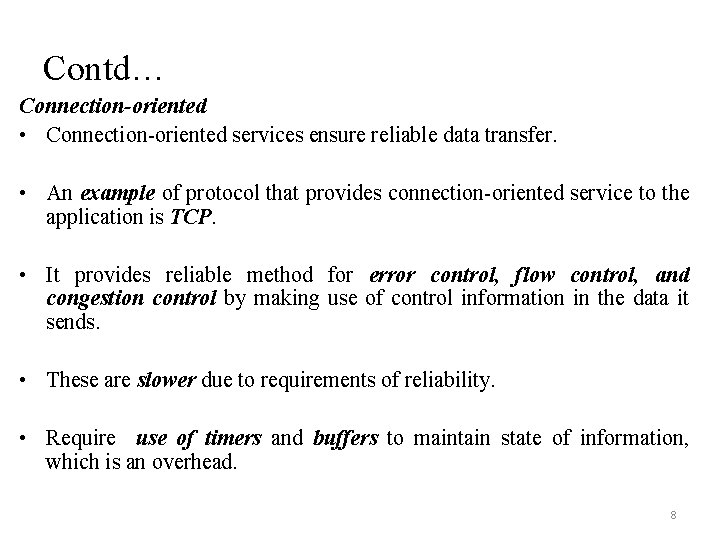
Contd… Connection-oriented • Connection-oriented services ensure reliable data transfer. • An example of protocol that provides connection-oriented service to the application is TCP. • It provides reliable method for error control, flow control, and congestion control by making use of control information in the data it sends. • These are slower due to requirements of reliability. • Require use of timers and buffers to maintain state of information, which is an overhead. 8

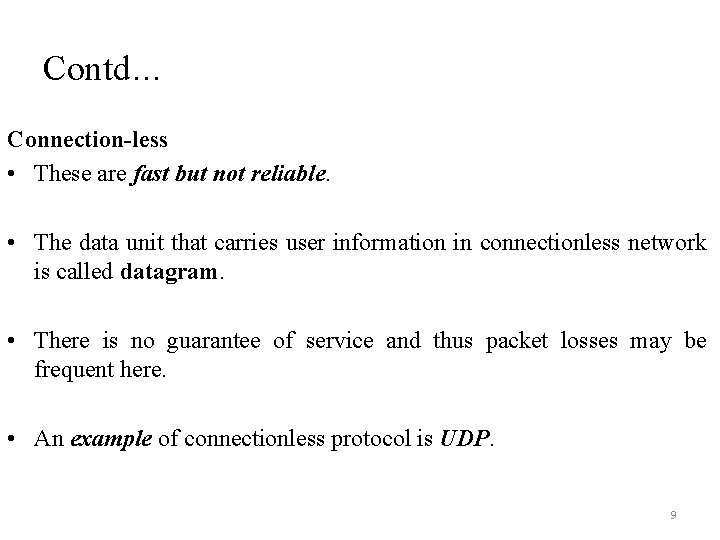
Contd… Connection-less • These are fast but not reliable. • The data unit that carries user information in connectionless network is called datagram. • There is no guarantee of service and thus packet losses may be frequent here. • An example of connectionless protocol is UDP. 9

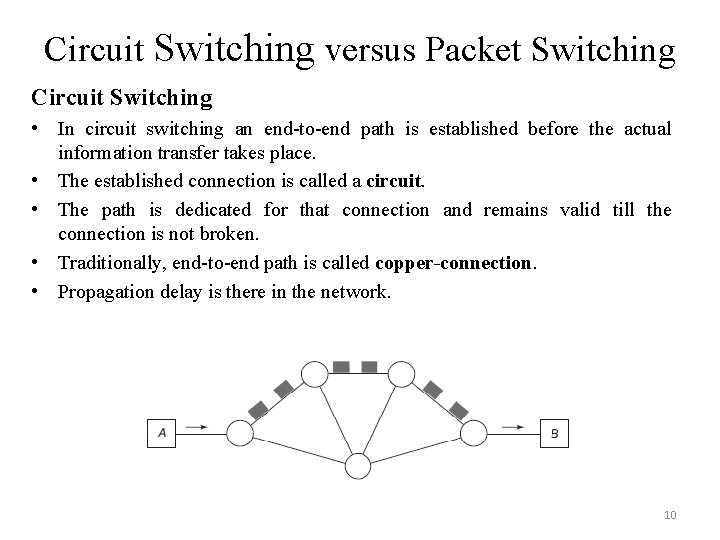
Circuit Switching versus Packet Switching Circuit Switching • In circuit switching an end-to-end path is established before the actual information transfer takes place. • The established connection is called a circuit. • The path is dedicated for that connection and remains valid till the connection is not broken. • Traditionally, end-to-end path is called copper-connection. • Propagation delay is there in the network. 10

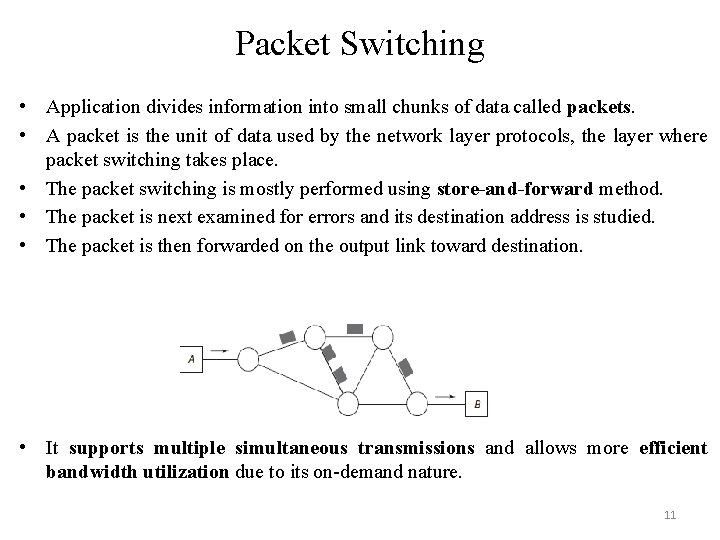
Packet Switching • Application divides information into small chunks of data called packets. • A packet is the unit of data used by the network layer protocols, the layer where packet switching takes place. • The packet switching is mostly performed using store-and-forward method. • The packet is next examined for errors and its destination address is studied. • The packet is then forwarded on the output link toward destination. • It supports multiple simultaneous transmissions and allows more efficient bandwidth utilization due to its on-demand nature. 11

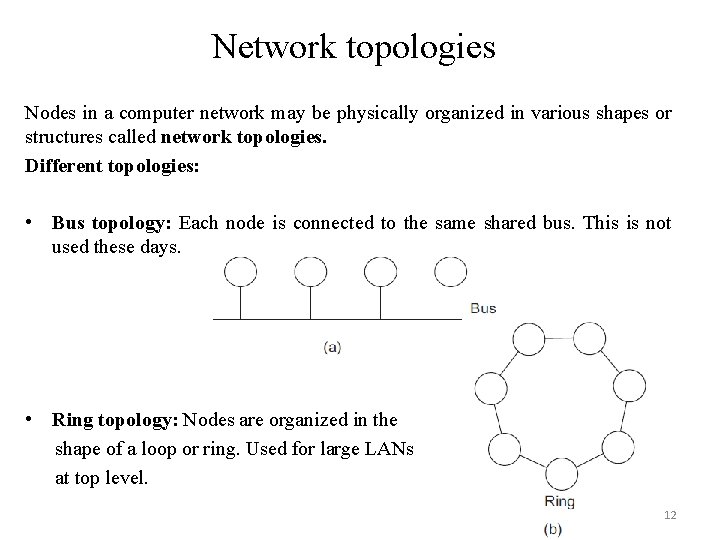
Network topologies Nodes in a computer network may be physically organized in various shapes or structures called network topologies. Different topologies: • Bus topology: Each node is connected to the same shared bus. This is not used these days. • Ring topology: Nodes are organized in the shape of a loop or ring. Used for large LANs at top level. 12

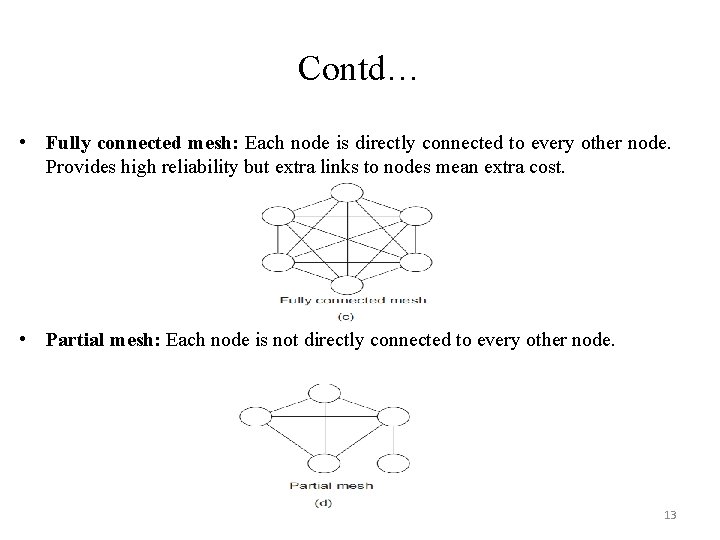
Contd… • Fully connected mesh: Each node is directly connected to every other node. Provides high reliability but extra links to nodes mean extra cost. • Partial mesh: Each node is not directly connected to every other node. 13

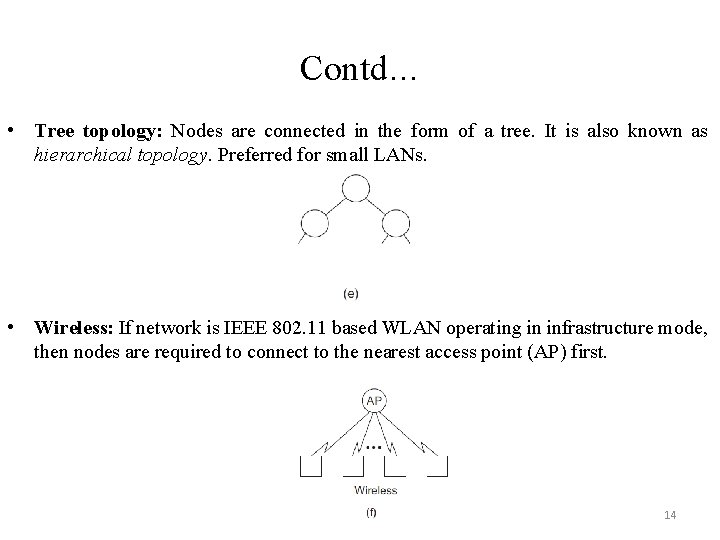
Contd… • Tree topology: Nodes are connected in the form of a tree. It is also known as hierarchical topology. Preferred for small LANs. • Wireless: If network is IEEE 802. 11 based WLAN operating in infrastructure mode, then nodes are required to connect to the nearest access point (AP) first. 14

Network Architecture Open systems interconnection reference model was published in 1984 by the ISO as the standard ISO-7498. Layered approach to Network Architecture: Layering divides the entire problem into small pieces. Principles behind using layered approach are as follows: a) Each layer performs various well-defined functions. b) Each layer provides services to the higher layer. c) No. of layers should neither be too many nor too less. d) At the same time a layer should be created where a different level of abstraction is needed. 15

Service versus Protocol • Each layer offers its services in the form of primitives which is the unit of information which is sent from one layer to the other. • A protocol working at a particular layer exchanges messages with its peer. The collection of protocols defining the various interfaces is called the protocol stack. • The service primitives are of four types: a) Request primitive: It is passed from layer N+1 to N for requesting that a certain service be initiated. b) Indication primitive: It is an event that is passed to layer N+1 from N that notifies that an action has been initiated by layer N. 16

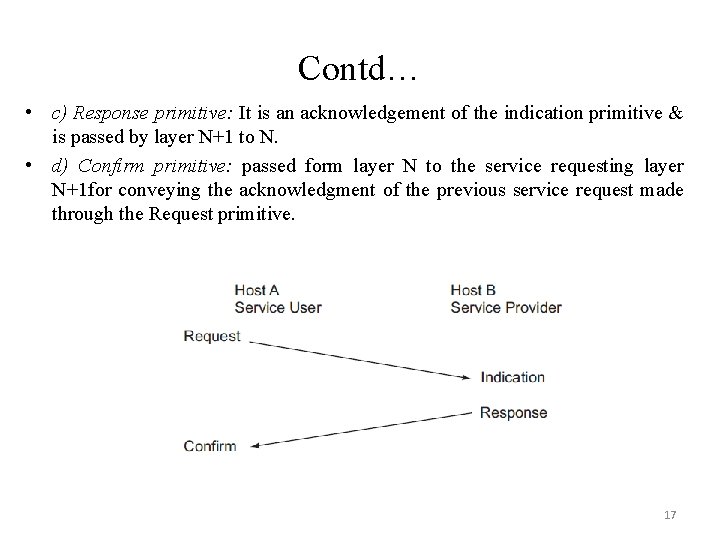
Contd… • c) Response primitive: It is an acknowledgement of the indication primitive & is passed by layer N+1 to N. • d) Confirm primitive: passed form layer N to the service requesting layer N+1 for conveying the acknowledgment of the previous service request made through the Request primitive. Service primitives 17

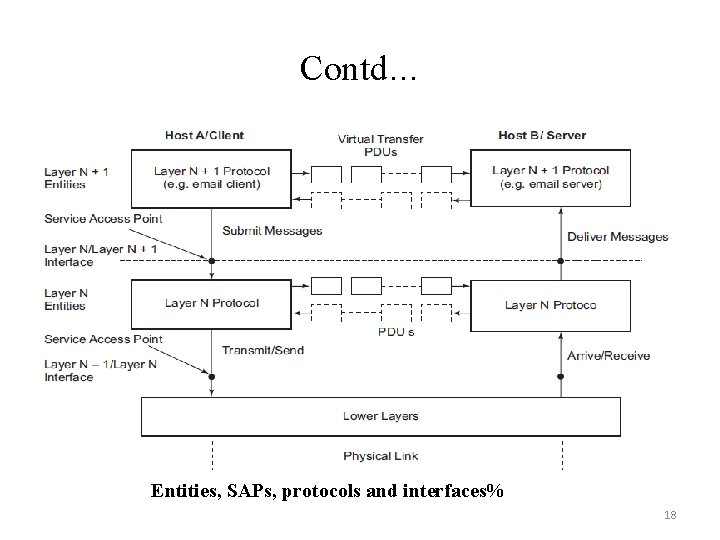
Contd… Entities, SAPs, protocols and interfaces% 18

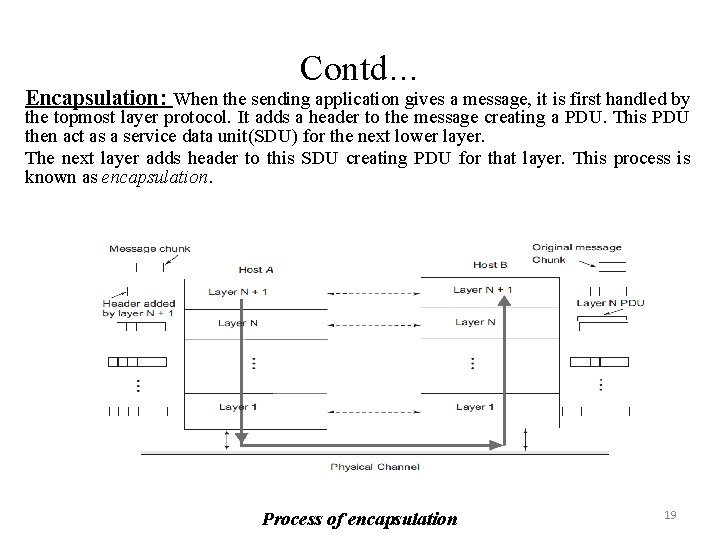
Contd… Encapsulation: When the sending application gives a message, it is first handled by the topmost layer protocol. It adds a header to the message creating a PDU. This PDU then act as a service data unit(SDU) for the next lower layer. The next layer adds header to this SDU creating PDU for that layer. This process is known as encapsulation. Process of encapsulation 19

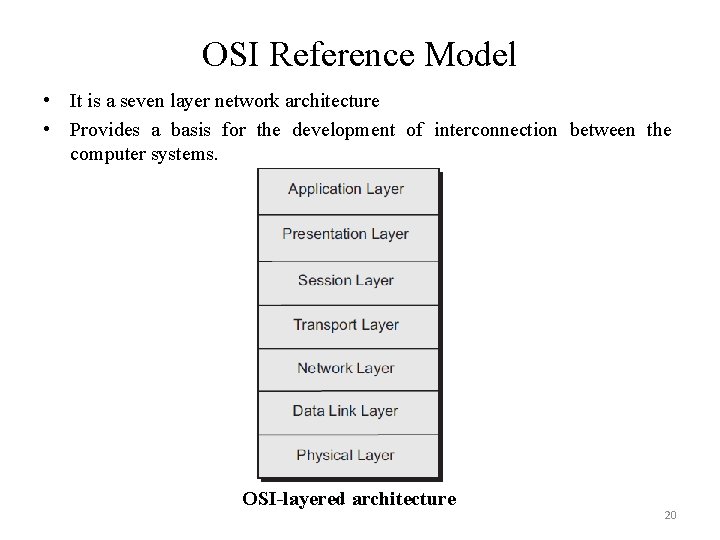
OSI Reference Model • It is a seven layer network architecture • Provides a basis for the development of interconnection between the computer systems. OSI-layered architecture 20

Contd… 1. • • Physical Layer: Lowermost layer of the OSI model. Uses signaling and encoding methods. Defines physical, mechanical and electrical interfaces of the network. Connects to the media-wired or wireless. Eg: RJ-45, V. 24 2. Data Link Layer: • Establish a link between the two communicating ends. • Responsible for framing, flow control and error control at the link layer level. OSI model divides the DLL into two sublayers: • Upper sublayer is known as the medium access control(MAC) sublayer. • Lower sublayer is known as the logical link control(LLC) sublayer. Eg: IEEE 802. 3, IEEE 802. 11 21

Contd… 3. Network Layer: • Provides functionality for connection establishment and maintenance. • Also provides connectionless service. • Each node is identified by its logical address. • Packets follow route as selected by the routing algorithm. • Packet fragmentation & reassembly and internetworking. • Eg: IS-IS 4. Transport Layer: • Connection oriented. • Provides efficient and reliable services to the session layer. • Responsible for end-to-end connection management, flow control, error control and congestion control. • Multiplexing and demultiplexing. 22

Contd… 5. Session Layer: • Dialog control and synchronization between entities at application layers. • Manage the login-logout of the session users. • Eg: SQL 6. Presentation Layer: • Purpose is protocol conversion, syntax transformation, encryption/decryption and compression/decompression for the application data. • Responsible for converting data representation format of one end to that of the other end. 7. Application Layer: • Provides mainly library functions & data reliability to the end user applications such as file transfer, e-mail, remote login and network management. • Eg: TELNET, FTP, SMTP 23

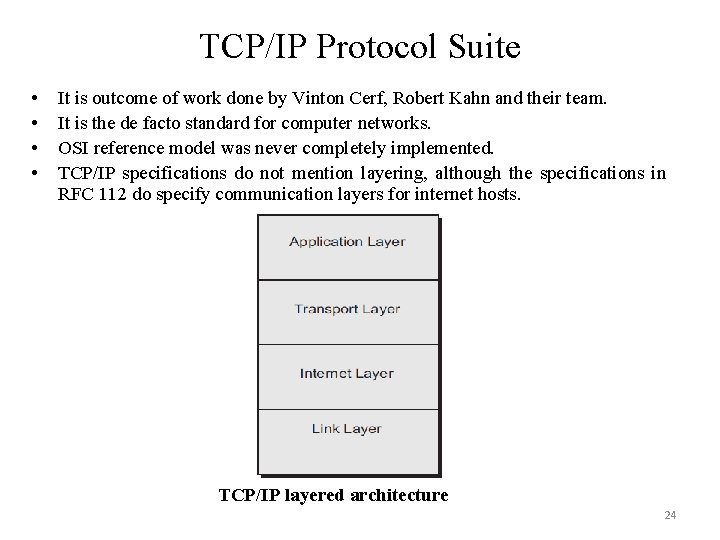
TCP/IP Protocol Suite • • It is outcome of work done by Vinton Cerf, Robert Kahn and their team. It is the de facto standard for computer networks. OSI reference model was never completely implemented. TCP/IP specifications do not mention layering, although the specifications in RFC 112 do specify communication layers for internet hosts. TCP/IP layered architecture 24

Contd… 1. Link Layer: • Performs the functions of DLL plus physical layer of the OSI model. • It interfaces host to the network and hence communication protocols of link control & media access are part of this layer. • Eg: Ethernet, ARP, RARP, PPP 2. Internet Layer: • Helps transport protocols to carry out data transfer from source end to the destination end. Internet Protocol is responsible for it • IP also provides addressing, routing, & type-of-service specification. • Does not provide any end-to-end delivery guarantees. • Eg: IPv 4, IPv 6, ICMP and Ipsec 25

Contd… 3. Transport Layer: • Provides end-to-end communication services for applications. • Two important protocols are TCP and UDP. • TCP provides reliable connection-oriented transport service, flow control and congestion control. • UDP is connectionless transport service but faster than TCP. 4. Application Layer: • Top layer of the TCP/IP suite of protocols. • Function of presentation layer of OSI model is also performed here. • The application layer protocols may either use TCP or UDP to run the host application program. • Eg: DNS, DHCP, HTTP, FTP, POP 3 etc. 26

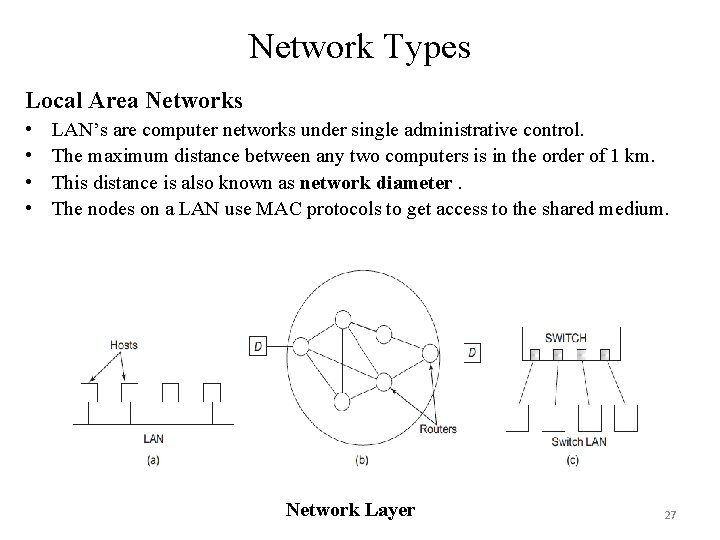
Network Types Local Area Networks • • LAN’s are computer networks under single administrative control. The maximum distance between any two computers is in the order of 1 km. This distance is also known as network diameter. The nodes on a LAN use MAC protocols to get access to the shared medium. Network Layer 27

Contd… • • • In LANs the entire communication between ends is possible between machines without using network or transport layer. A LAN could be either wired or wireless. Ethernet, Fast Ethernet, Gigabit Ethernet, and Token Ring are examples of MAC technologies for wired LANs. Metropolitan Area Networks • Connects computers in a city or a metropolitan. • Size of a MAN is typically in the order of 10 km. • MAN uses optical media for interconnecting LANs or LAN with a WANlike internet. • It is possible to create wireless MAN 28

Contd… Wide Area Networks • • • It is a huge network that may or may not belong to one organization. The ARPAnet of 1960 s was actually a WAN. A WAN is created by connecting routers together using point-to-point links. On WANs, MAC protocols are not required because the links are point to point. WANs are based on packet switching technology. They work at Internet layer of TCP/IP model & use LLC sublayer protocols such as HDLC or PPP for flow control functions. Intranet • Network of computers that use Internet technologies, i. e. , TCP/IP for implementations. • With the widespread availability of services , we may say that LAN and WAN are getting converged. 29

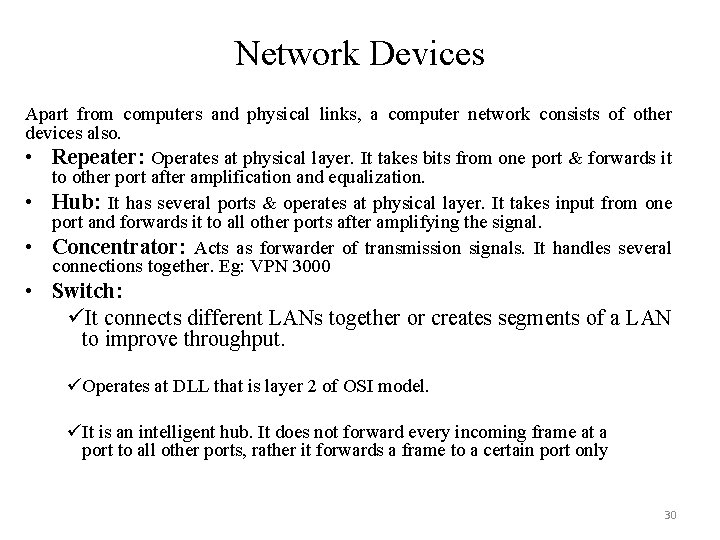
Network Devices Apart from computers and physical links, a computer network consists of other devices also. • Repeater: Operates at physical layer. It takes bits from one port & forwards it to other port after amplification and equalization. • Hub: It has several ports & operates at physical layer. It takes input from one port and forwards it to all other ports after amplifying the signal. • Concentrator: Acts as forwarder of transmission signals. It handles several connections together. Eg: VPN 3000 • Switch: üIt connects different LANs together or creates segments of a LAN to improve throughput. üOperates at DLL that is layer 2 of OSI model. üIt is an intelligent hub. It does not forward every incoming frame at a port to all other ports, rather it forwards a frame to a certain port only 30

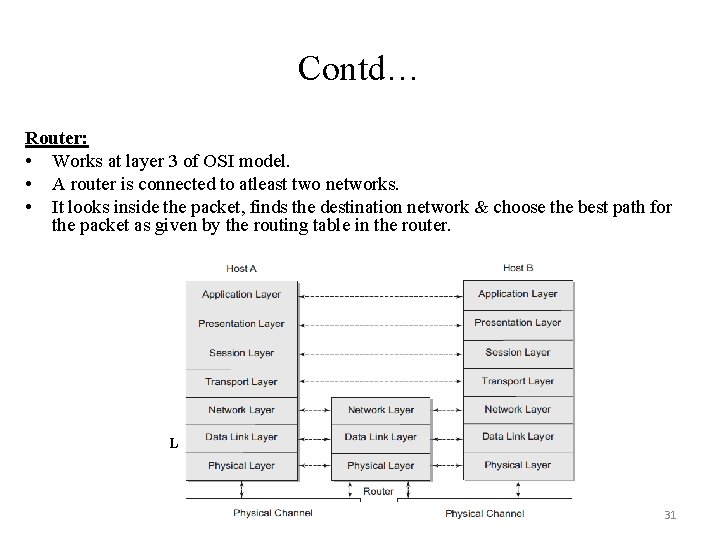
Contd… Router: • Works at layer 3 of OSI model. • A router is connected to atleast two networks. • It looks inside the packet, finds the destination network & choose the best path for the packet as given by the routing table in the router. Location of a router in the protocol stack 31

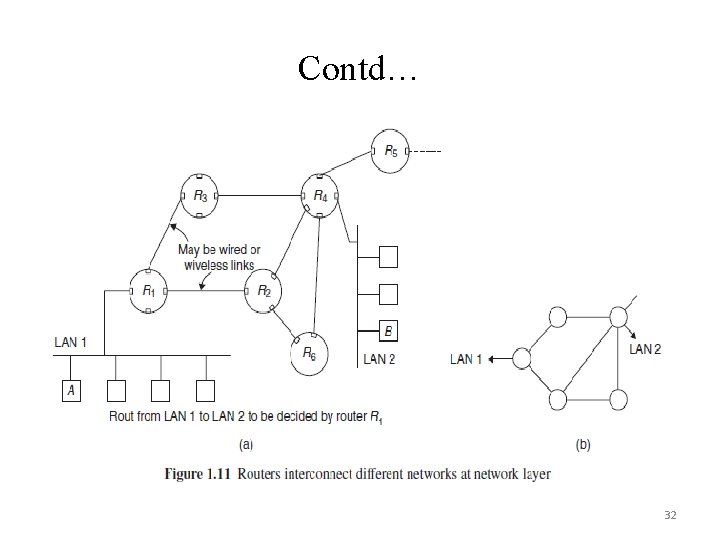
Contd… 32

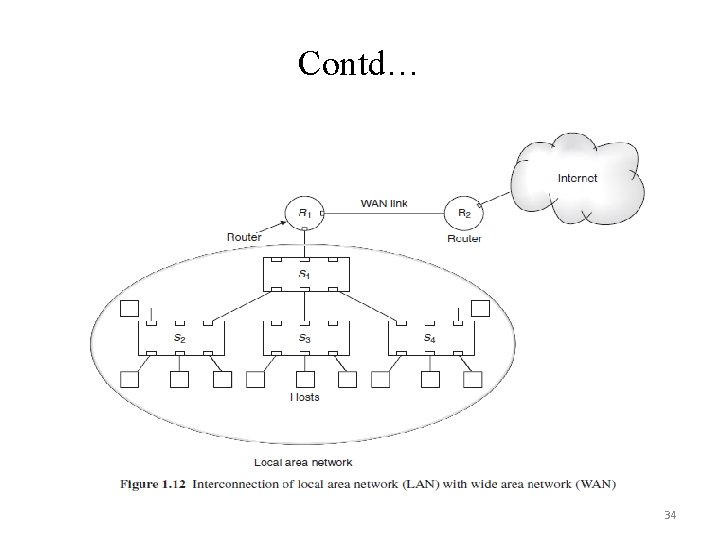
Network Design Considerations While designing a computer network, several factors are very important. • TCP/IP is standard protocol suite used to create LAN or WAN. • If a LAN is to be created, its size, how the nodes are going to be grouped & hierarchy of switches have to be looked into. • Cost of deployment will depend upon the physical links. • In a WAN, type of link, its bandwidth and capacity matters • No. of routers & their locations and configuration of routers have to be planned and implemented. • IP address may be fixed for a particular machine or taken by the machine when required. • Security is a major concern in any computer network. 33

Contd… 34

Performance Issues in Networks • Performance of a network measures some desired behavior of the system. • Throughput: • Amount of data transmitted over a period of time. • It is measured by counting the traffic over a suitable chosen interval. • Usually measured in Mbps or Gbps. • Bandwidth is theoretical maximum throughput of a link. • In communication systems, bandwidth is equal to the difference between the highest and the lowest frequencies in the signal that can be transmitted. • Bandwidth of a link should be high as it indicates its capacity. • Available bandwidth = Capacity-Utilized capacity • Channel utilization is the ratio of throughput and the channel capacity • Goodput is the arrival rate of undamaged packets. 35

Contd… • Delay or Latency: Latency is the time measured in units of elapsed time. Delay for a packet is the time elapsed between packet transmitted and packet received time. Round trip time(RTT) is the sum of two-way delay. It is the time between dispatch of a packet and receipt of its acknowledgment. Components of delay are: a) Processing time for taking action on a packet. b) Queuing delay. c) Transmission delay. d) Propagation delay. Transmission delay = Data size/Bandwidth Throughput = Data size/Total delay Propagation delay = Distance/Speed of light in the medium 36

Contd… • Jitter: Variation in delay is known as jitter. It may be due to variation in delay components. It is very important metric for multimedia applications namely online video and videoconferencing. • Packet Delivery Ratio: Ratio of no. of packets received by no. of packets transmitted on the channel. • Packet Loss Rate: Ratio of no. of packets lost to the no. of packets transmitted. • Delay-Bandwidth Product(DBP): It indicates volume of the data that may be carried by the channel before the sender expects ack from the receiver. If the sender does not fill the pipe with data equal to DBP, thenit is not utilizing the capacity of network. • Reliability: It is measured as the mean time between failures(MTBF) of the system or mean time to repair(MTTR) following a failure of the system Availability is based on the reliability of the individual component of a n/w Availability = MTBF/(MTBF+MTTR) 37

Network Traffic types 38

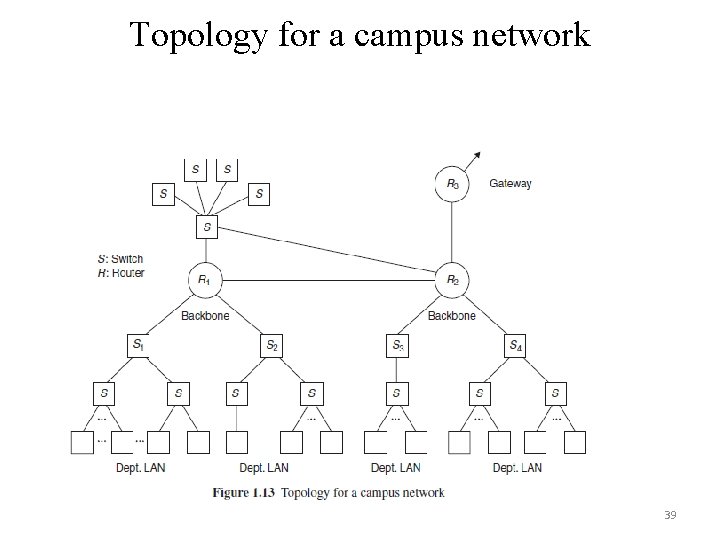
Topology for a campus network 39