Introduction to SAST Fortify Introduction August 2015 1






- Slides: 16

Introduction to SAST Fortify Introduction August 2015 1 © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Where does it fit?

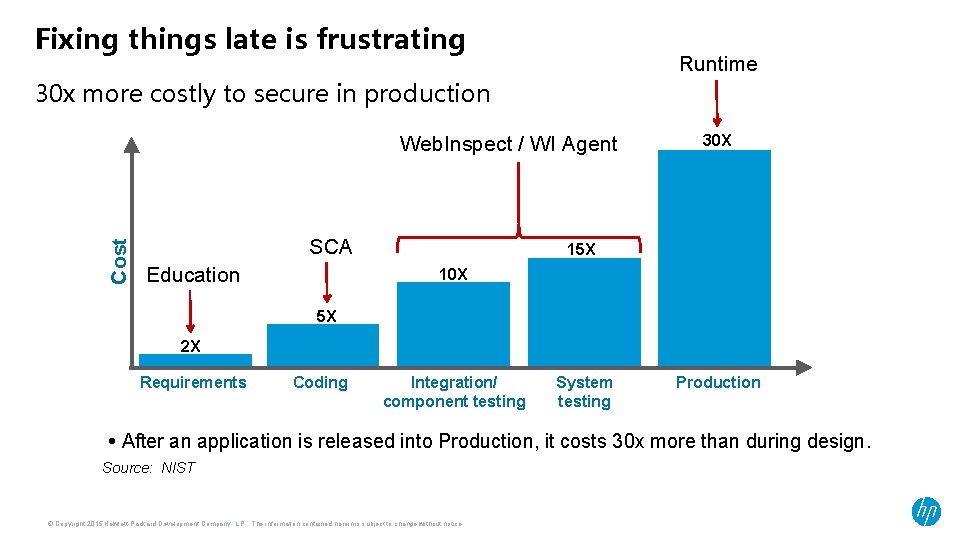
Fixing things late is frustrating Runtime 30 x more costly to secure in production Cost Web. Inspect / WI Agent SCA Education 30 X 15 X 10 X 5 X 2 X Requirements Coding Integration/ component testing System testing Production • After an application is released into Production, it costs 30 x more than during design. Source: NIST © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

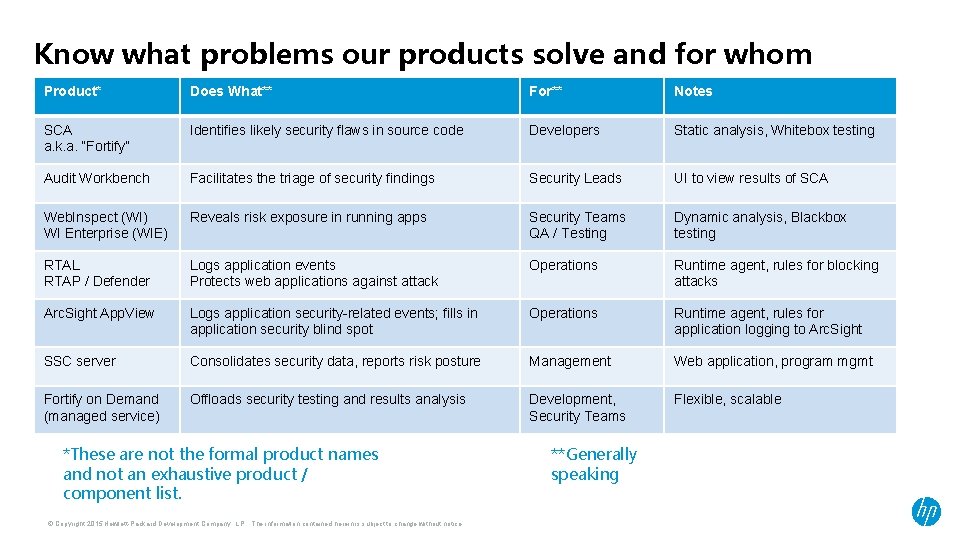
Know what problems our products solve and for whom Product* Does What** For** Notes SCA a. k. a. “Fortify” Identifies likely security flaws in source code Developers Static analysis, Whitebox testing Audit Workbench Facilitates the triage of security findings Security Leads UI to view results of SCA Web. Inspect (WI) WI Enterprise (WIE) Reveals risk exposure in running apps Security Teams QA / Testing Dynamic analysis, Blackbox testing RTAL RTAP / Defender Logs application events Protects web applications against attack Operations Runtime agent, rules for blocking attacks Arc. Sight App. View Logs application security-related events; fills in application security blind spot Operations Runtime agent, rules for application logging to Arc. Sight SSC server Consolidates security data, reports risk posture Management Web application, program mgmt Fortify on Demand (managed service) Offloads security testing and results analysis Development, Security Teams Flexible, scalable *These are not the formal product names and not an exhaustive product / component list. © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. **Generally speaking

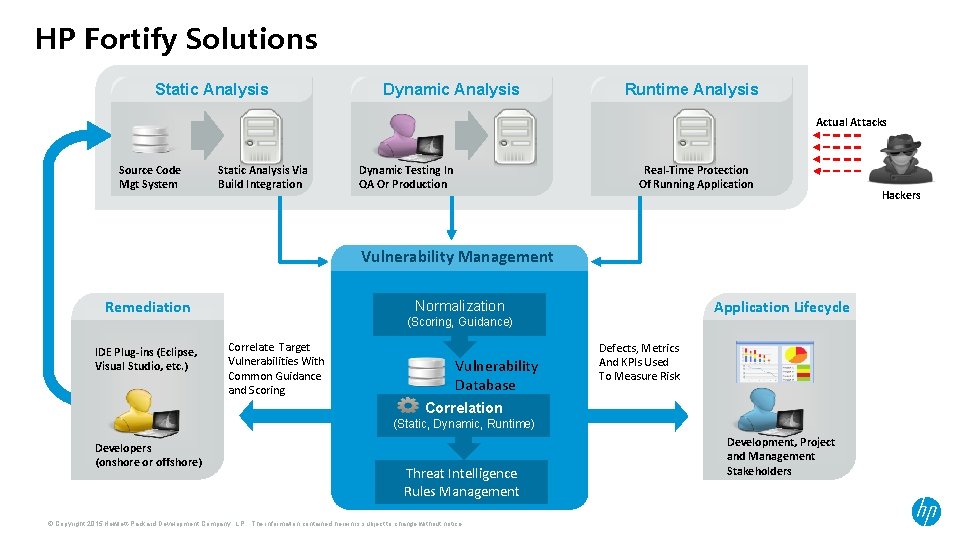
HP Fortify Solutions Static Analysis Dynamic Analysis Runtime Analysis Actual Attacks Source Code Mgt System Static Analysis Via Build Integration Dynamic Testing In QA Or Production Real-Time Protection Of Running Application Vulnerability Management Remediation IDE Plug-ins (Eclipse, Visual Studio, etc. ) Application Lifecycle Normalization (Scoring, Guidance) Correlate Target Vulnerabilities With Common Guidance and Scoring Vulnerability Database Defects, Metrics And KPIs Used To Measure Risk Correlation (Static, Dynamic, Runtime) Developers (onshore or offshore) Threat Intelligence Rules Management © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Development, Project and Management Stakeholders Hackers

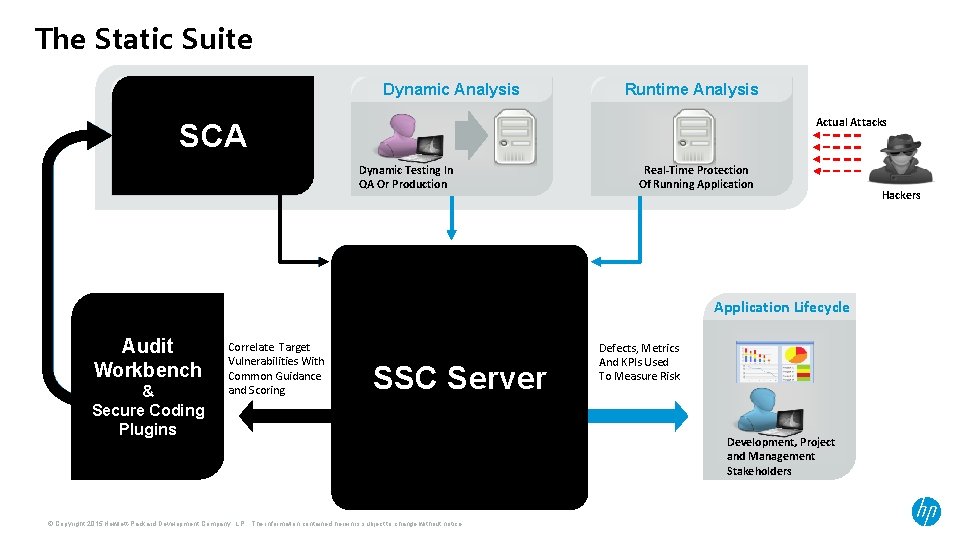
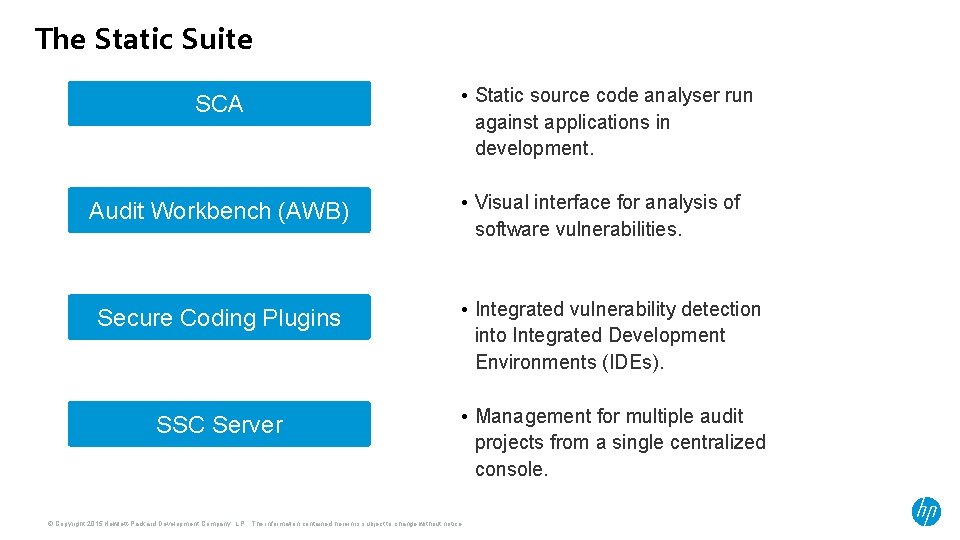
The Static Suite

The Static Suite Static Analysis Dynamic Analysis Runtime Analysis Actual Attacks SCA Source Code Mgt System Static Analysis Via Build Integration Dynamic Testing In QA Or Production Real-Time Protection Of Running Application Vulnerability Management Remediation Audit Workbench IDE Plug-ins (Eclipse, Visual Studio, etc. ) & Secure Coding Plugins Developers (onshore or offshore) Application Lifecycle Normalization (Scoring, Guidance) Correlate Target Vulnerabilities With Common Guidance and Scoring Vulnerability Database SSC Server Defects, Metrics And KPIs Used To Measure Risk Correlation (Static, Dynamic, Runtime) Threat Intelligence Rules Management © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Development, Project and Management Stakeholders Hackers

The Static Suite SCA Audit Workbench (AWB) • Static source code analyser run against applications in development. • Visual interface for analysis of software vulnerabilities. Secure Coding Plugins • Integrated vulnerability detection into Integrated Development Environments (IDEs). SSC Server • Management for multiple audit projects from a single centralized console. © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

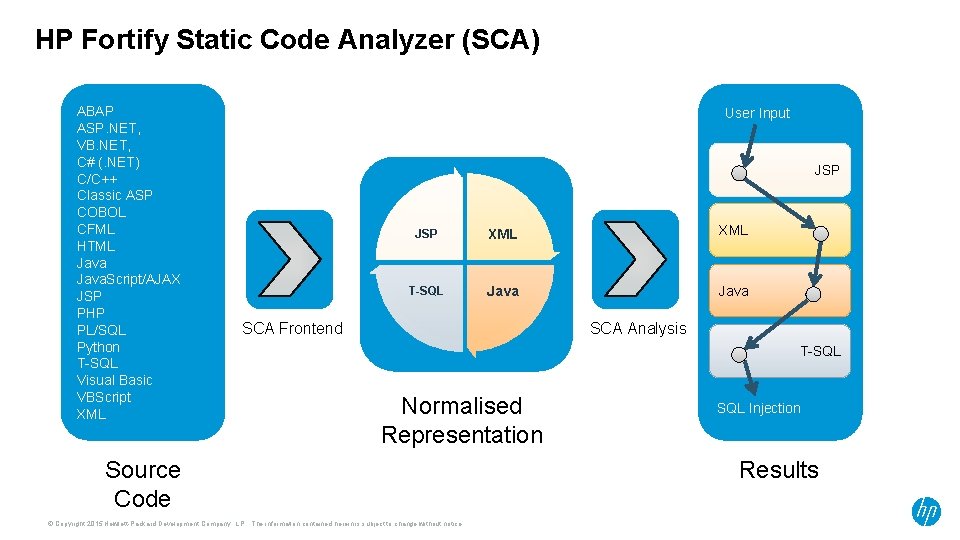
HP Fortify Static Code Analyzer (SCA) ABAP ASP. NET, VB. NET, C# (. NET) C/C++ Classic ASP COBOL CFML HTML Java. Script/AJAX JSP PHP PL/SQL Python T-SQL Visual Basic VBScript XML User Input JSP XML T-SQL Java SCA Frontend SCA Analysis T-SQL Normalised Representation Source Code © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. SQL Injection Results

Audit Workbench (AWB) and the Secure Coding Plugins © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

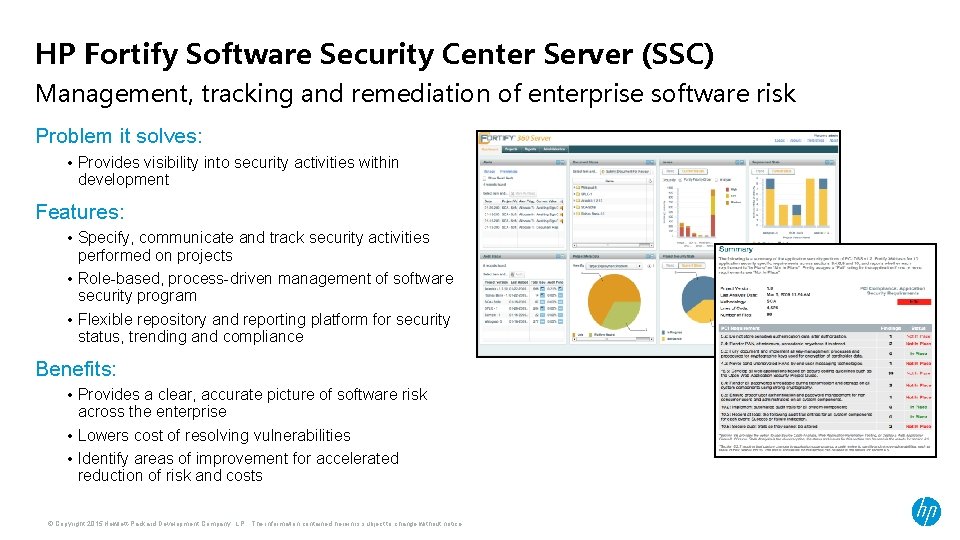
HP Fortify Software Security Center Server (SSC) Management, tracking and remediation of enterprise software risk Problem it solves: • Provides visibility into security activities within development Features: • Specify, communicate and track security activities performed on projects • Role-based, process-driven management of software security program • Flexible repository and reporting platform for security status, trending and compliance Benefits: • Provides a clear, accurate picture of software risk across the enterprise • Lowers cost of resolving vulnerabilities • Identify areas of improvement for accelerated reduction of risk and costs © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Piecing it Together

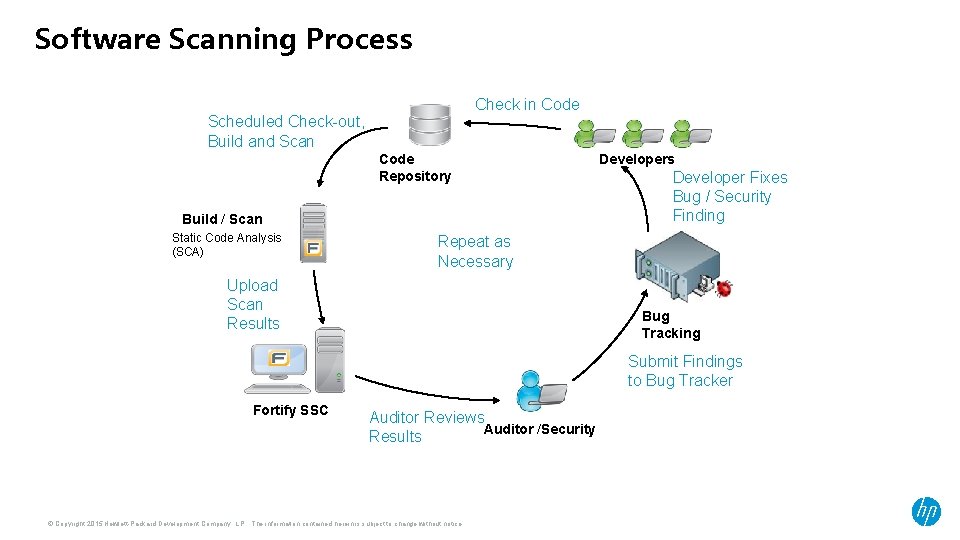
Software Scanning Process Check in Code Scheduled Check-out, Build and Scan Code Repository Build / Scan Static Code Analysis (SCA) Developers Developer Fixes Bug / Security Finding Repeat as Necessary Upload Scan Results Bug Tracking Submit Findings to Bug Tracker Fortify SSC Auditor Reviews Auditor /Security Results © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

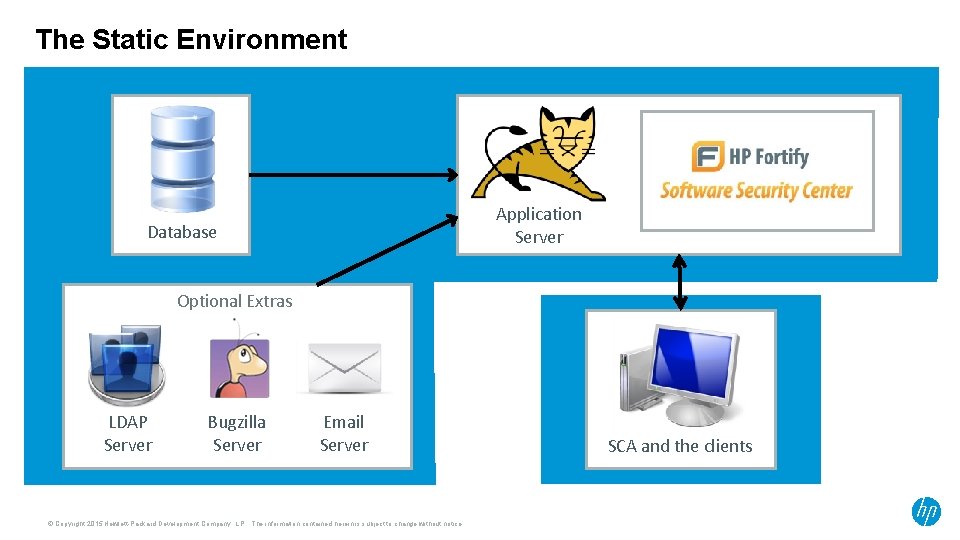
The Static Environment Application Server Database Optional Extras LDAP Server Bugzilla Server Email Server © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. SCA and the clients

Questions? 15 © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Follow up tasks… Review the Resources on the SCA homepage: • http: //www 8. hp. com/uk/en/software-solutions/static-code-analysis-sast/index. html Review sections 1 and 2 of a Technical Intro to HP Fortify SA Solutions: • https: //hp. sabacloud. com/Saba/Web_spf/HP/common/leclassdetail/regdw 000000032438835 16 © Copyright 2015 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.