Introduction to Practical Cryptography Redaction Proxy Cryptography 1
















![Make Two Words Non Redactable "Did you ever see an unhappy [N]horse? Did you Make Two Words Non Redactable "Did you ever see an unhappy [N]horse? Did you](https://slidetodoc.com/presentation_image_h/fdd63064bf38c0b1234d038a2a10485a/image-29.jpg)
![Alter Content "Did you ever see an unhappy [N]horse? Did you ever see a Alter Content "Did you ever see an unhappy [N]horse? Did you ever see a](https://slidetodoc.com/presentation_image_h/fdd63064bf38c0b1234d038a2a10485a/image-30.jpg)












![Attack Overview [Kaliski, et. al. ] • Attack due to Birthday Paradox: – Given Attack Overview [Kaliski, et. al. ] • Attack due to Birthday Paradox: – Given](https://slidetodoc.com/presentation_image_h/fdd63064bf38c0b1234d038a2a10485a/image-53.jpg)
- Slides: 59

Introduction to Practical Cryptography Redaction Proxy Cryptography 1

Agenda • Redaction • Proxy Cryptography 2

Redaction • Process of removing sensitive or confidential information from a document without distorting the meaning of the document. • Portion of a document may be redactable, others may be non redactable. • Should provide indication when something has been redacted; otherwise, meaning of the document can be altered by removing portions of the content. 3

Redaction • Removal of information from documents, media … The project involved people with a budget of • Image with brand name that must be removed 4

Redaction Example • Original content: – John Doe testified that Al Smith did not commit the crime. • After redaction: – [REDACTED] testified that Al Smith did not commit the crime. – testified that Al Smith did not commit the crime. • If redaction is not indicated, the meaning can be changed: – John Doe testified that Al Smith did commit the crime. 5

Redaction Examples • Government documents • classified information is removed prior to public release • Financial documents • mortgage application: different people need subsets of the information appraiser doesn’t need to see income • Legal documents • some information remains under attorney client privilege • Medical Records • Different employees access different information • Corporations • different employees have access to subsets of information • Public records • towns in US that place mortgage, property tax information online – remove personal information 6

Mistakes • Changing the background color to match the font color underlying text is still there, can be retrieved by changing the color • Changes saved automatically by program as part of revision history • Drawing a black box over the text – box can be removed 7

Information Leakage • Length of redacted area • The budget for project is • The first name of the witness is . . . • Inferred content • • Name Address Date Value • Human error • Forget to redact/overlook one or more pieces 8

Formatting • Altering length of redacted area to reduce information leakage changes format • Alters length of document • Re align paragraphs, page breaks • If alter number of pixels in an image, can garble display of rest of image 9

Authenticating Document • How to sign a document? • Hash then encrypt doesn’t work – sign the original then redact invalidates signature • If document signed after redaction, what indicates information was not altered in the process? 10

Authenticating a Document • How to sign a document? • “The witness is John Smith” • Hash: 07 ed 235678 a 3 b 4 de 0075 • Encrypt with RSA: 453872907 • Redact • The witness is • Send redacted documented and signature 11

Authenticating a Document • Recipient receives • The witness is • Signature 453872907 • Recipient tries to verify signature • Decrypt signature: 07 ed 235678 a 3 b 4 de 0075 • Hash received text: 3245 cea 1 eded 01821111 • Doesn’t match decrypted signature 12

Authenticating a Document • How to verify information that was not suppose to be redacted was left intact? • The problem is not only how to authenticate what remains in the clear, but that information that was suppose to remain in the clear was not redacted 13

Authenticating a Document • Need to authenticate non redacted information is unchanged from the original • How? • Need to authenticate that information was not improperly removed • How? 14

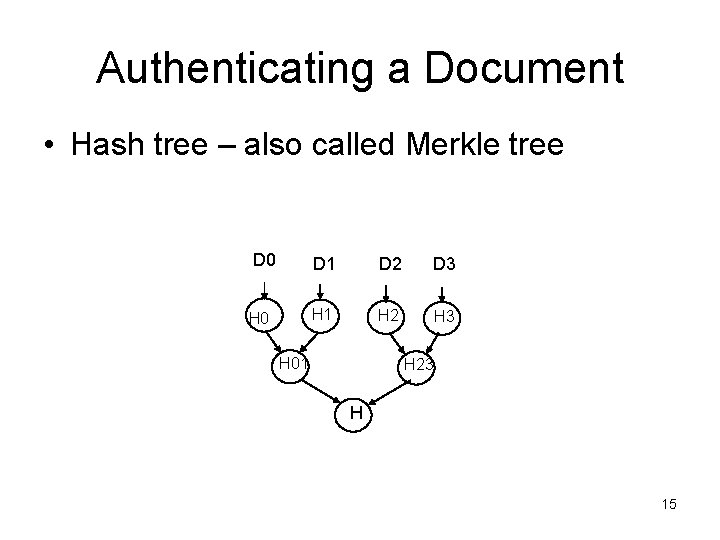
Authenticating a Document • Hash tree – also called Merkle tree D 0 D 1 D 2 D 3 H 0 H 1 H 2 H 3 H 01 H 23 H 15

Algorithm • Uses 4 binary trees • Roots of two trees are used for the signature • Retain nodes which allow the roots to be recomputed. • Nodes retained depends on which subdocuments are redacted and which ones are non redactable. • Easiest way to explain is via diagrams … 16

R and X Trees r 11 seed r’s formed by random bit generation using parent node as seed r 22 r 21 r 31 hash (mi || r 4 i) x’s formed by hashing children r 33 r 32 r 34 r 41 r 42 r 43 r 44 r 45 r 46 r 47 r 48 m 1 m 2 m 3 m 4 m 5 m 6 m 7 m 8 x 41 x 42 x 43 x 44 x 46 x 47 x 48 x 31 x 45 x 32 x 33 x 34 x 11 x 21 x 11 root 17

S and Y Trees s 11 seed s’s formed by random bit generation using parent node as seed s 22 s 21 s 31 y 4 i = hash (s 4 i) y’s formed by hashing children s 33 s 32 s 34 s 41 s 42 s 43 s 44 s 45 s 46 s 47 s 48 y 41 y 42 y 43 y 44 y 45 y 46 y 47 y 48 y 31 y 32 y 33 y 34 y 22 y 21 y 11 root 18

How Trees are Used • Sign(x root || y root) • Original document: include r seed and s seed. – Recipient can recompute all xi, yi to verify signature. • Redact mi: delete path of r nodes to xi, include xi and siblings of deleted r nodes. • Non redactable mi: delete path of s nodes to yi , include yi and siblings of deleted s nodes. • If both children of an x node are included, save parent node instead; likewise for y nodes. 19

Redacted Subdocument r 11 seed r 22 r 21 r 31 m 2 is redacted r 42 must be “removed” r 33 r 32 r 34 r 41 r 42 r 43 r 44 r 45 r 46 r 47 r 48 m 1 m 3 m 4 m 5 m 6 m 7 m 8 x 41 x 42 x 43 x 44 x 46 x 47 x 48 x 31 x 45 x 32 x 33 x 34 x 22 x 21 x 11 root 20

Adjacent Redacted Subdocuments r 11 seed r 22 r 21 r 31 m 1 and m 2 are redacted r 33 r 32 r 34 r 41 r 42 r 43 r 44 r 45 r 46 r 47 r 48 m 0 m 1 m 3 m 4 m 5 m 6 m 7 m 8 x 41 x 42 x 43 x 44 x 46 x 47 x 48 x 31 x 45 x 32 x 33 x 34 x 22 x 21 x 11 root 21

Non Redactable Subdocument s 11 seed m 5 is non redactable s 45 must be “removed” s 22 s 21 s 33 s 32 s 11 s 42 s 43 s 44 s 45 s 46 s 47 s 48 y 41 y 42 y 43 y 44 y 45 y 46 y 47 y 48 y 31 y 32 y 33 y 34 y 22 y 21 y 11 root 22

Adjacent Non Redactable Subdocuments s 11 m 5 and m 6 are non redactable seed s 22 s 21 s 33 s 32 s 34 s 41 s 42 s 43 s 44 s 45 s 46 s 47 s 48 y 41 y 42 y 43 y 44 y 45 y 46 y 47 y 31 y 32 y 33 y 34 y 22 y 21 y 11 root 23

Architecture • Allow different document processing applications (document editors and viewers) to utilize the redaction software through a common API. • Permit the application to decide what information must be signed and verified – e. g. content only, content and some formatting, content and all formatting • Permit the application to decide what constitutes a subdocument 24

Issues • Format converter – Difficulty varies per editor/viewer pdf vs ASCII – Opening file of same format in different editors can unintentionally modify the content • User interface – What should be a subdocument? – Should white space matter? – How to indicate to the user a subdocument has been redacted and a subdocument is non redactable? – If redaction is indicated, length provides hint to the user about the deleted content. However, changing the length can alter the appearance and any white space in the content. 25

Original Text "Did you ever see an unhappy horse? Did you ever see a bird that has the blues? One reason why birds and horses are not unhappy is because they are not trying to impress other birds and horses. " Dale Carnegie 26

Subdocuments <"Did><you><ever><see><an><unhappy><horse? > <Did><you><ever><see><a> <bird><that><has><the><blues? ><One><reason> <why><birds><and><horses> <are><not><unhappy><is><because><they><are> <not><trying><to><impress><other><birds><and> <horses. “><Dale> <Carnegie> 27

Redact Author’s Name "Did you ever see an unhappy horse? Did you ever see a bird that has the blues? One reason why birds and horses are not unhappy is because they are not trying to impress other birds and horses. " [R] 28
![Make Two Words Non Redactable Did you ever see an unhappy Nhorse Did you Make Two Words Non Redactable "Did you ever see an unhappy [N]horse? Did you](https://slidetodoc.com/presentation_image_h/fdd63064bf38c0b1234d038a2a10485a/image-29.jpg)
Make Two Words Non Redactable "Did you ever see an unhappy [N]horse? Did you ever see a [N]bird that has the blues? One reason why birds and horses are not unhappy is because they are not trying to impress other birds and horses. " [R] 29
![Alter Content Did you ever see an unhappy Nhorse Did you ever see a Alter Content "Did you ever see an unhappy [N]horse? Did you ever see a](https://slidetodoc.com/presentation_image_h/fdd63064bf38c0b1234d038a2a10485a/image-30.jpg)
Alter Content "Did you ever see an unhappy [N]horse? Did you ever see a [N]bird that has the blues? One reason why birds and horses are not unhappy is because they are not trying to impress other people and horses. " [R] 30

Examples http: //www. nsa. gov/public/crypt_spectrum. cfm 31

Proxy Cryptography 32

Proxy Cryptography • Convert ciphertext from encryption with one key to encryption with another key: – Encrypt with one key, let recipient decrypt with some other key • Similar notion for signatures: sign with one key, let recipient verify with another key. 33

Proxy Cryptography • Allows an intermediate entity (proxy) to convert ciphertext between two keys without exposing the plaintext A C 1 = Eka(P) C 1 Proxy C 2 = Hkab(C 1) C 2 B P = Dkb(C 2) • Proxy converts C 1 to C 2 – A, B publish kab – ka, kb private keys 34

Proxy Cryptography • VPNs • File servers • Transform A’s signature into B’s signature 35

Proxy Cryptography • Applied to public key ciphers • El Gamal, RSA [Okamoto, Mambo, ‘ 97; Blaze, et. al. ‘ 98] 36

Blaze, et. al • similar in structure to El. Gamal encryption • but with the parameters used differently and the inverse of the secret used to recover the message • the speed of the scheme is comparable to standard El. Gamal encryption, although initial key generation requires the additional calculation and storage of a parameter a 1 37

Cryptosystem X (encryption) • • • Parameters p is a prime of the form 2 q + 1 for a prime q g is a generator in Z*p p and g are public A’s private key – A's private key: a, 0 < a < p 1, randomly picked from Z*2 q (a is relatively prime to p 1) – A calculates inverse: a 1 mod 2 q. – A’s public key: (ga mod p, g, p) 38

Cryptosystem X (encryption) • Encryption – Select a unique random k from Z*2 q , k is secret – To encrypt message m with A's key, compute and send ciphertext values (c 1, c 2): • c 1 = mgk mod p • c 2 = (ga)k mod p • Decryption: – A (knows a 1) calculates gk and recovers m: • c 2(a) 1= gk (mod p), solve for gk • Compute (gk) 1 mod p • m = c 1 ((c 2(a) 1) 1 ) mod p 39

• Parameters – – – Example p = 23 = 2 x 11 + 1 g = 5 (generates {5, 2, 10, 4, 20, 8, 17, 16, 11, 9, 22, 18, 21, 13, 19, 3, 15, 6, 7, 12, 14, 1}) a=3 a 1 = 15 (15*3 = 45 = 1 mod 22) a 3 g mod p = 5 mod 23 = 10 • • Encrypt m = 2 using k = 7 gk mod 23 = 17 c 1 = mgk = 2*57 mod 23 = 11 c 2 = (ga)k = 107 mod 23 = 14 • • Decrypt c 2 ^ ((a^ 1)) = 1415 mod 23 (142 mod 23 = 12, 127 * 14 mod 23, 122 = 6 mod 23) = 63*12*14 mod 23 = 17 c 1 = m*g^k mod 23: 11 = m*17 mod 23 11*17 1 mod 23 = m (17 1 mod 23 = 19) 11*19 mod 23 = 2 • • • 40

Proxy Function for X • c 1 ciphertext component produced by Cryptosystem X is independent of the recipient's public key. • Recipient A's key is embedded only in the c 2 exponent • Proxy function to convert ciphertext for A into ciphertext for B – remove A's key a from c 2 and replace it with B's key b. – similar to the first step of the decryption function, raising c 2 to a 1 to remove a. – then contribute a factor of b to the exponent. • simply raising c 2 to a 1 and then to b would accomplish this • but does not qualify as a secure proxy function; anyone who examines the proxy key learns the secret keys for both A and B. • This problem is avoided by combining the two steps into one. Hence, the proxy key A B: (a 1)b – the proxy function is simply c 2 A B 41

Symmetric proxy function for X • Note that this is a “symmetric” proxy function; – A and B must trust one another bilaterally. – B can learn A's secret (by multiplying the proxy key by b 1 ) – A can similarly discover B's key. • This proxy function is also translucent – the proxy key does not directly reveal A or B, but anyone can verify a guess by encrypting a message with A's public key, applying the proxy function, and comparing the result with the encryption of the same message (with the same k) with B's public key. • Applying the proxy function is more efficient than decryption and re encryption, in that only one exponentiation is required. 42

Proxy Signature • Signature will verify with key other than that of the original signer 43

Conversion and Proxy Functions for Symmetric Key Ciphers 44

Or more appropriately … why a symmetric key cipher that is closed under functional composition is useful for applications but undesirable from a security perspective 45

Motivation • Each Ai wants to exchange ciphertext with each Aj • Size of data requires use of a symmetric key cipher • Collectively, the Ai’s do not share a key A 2 A 3 A 4 A 2 A 5 A 1 A 8 A 7 A 6 Pair wise establishment or sharing of keys A 3 A 4 A 1 A 5 A 8 A 7 A 6 Gateway converting ciphertext between keys 46

Motivation A C 1 = Ek 1(P) C 1 Gateway C 2 = Ek 2(Dk 1(C 1)) C 2 B P = Dk 2(C 2) • Converting from encryption under one key, k 1, to encryption under another key, k 2: – For example, VPN gateways • Is there a way to perform the conversion that – Is faster than decrypting with k 1 and encrypting with k 2? – Avoids exposing the plaintext during the conversion? 47

Notation • • • S: a symmetric key cipher K: key space of S |K|: size of K k, ki: element of K E: encryption function of S D: decryption function of S Ek: encryption using key k Dk: decryption using key k Gkg: conversion function using key kg P: plaintext C: ciphertext 48

Overview • Conversion function G for symmetric key cipher S – Gkg(Ek 1(P)) = Ek 2(P) plaintext P • Such that – kg dependent on k 1 and k 2 – P may or may not be exposed during the conversion – G is a secure conversion function if P is not exposed • G exists: (trivially) use Ek 2(Dk 1(C)) • Existence of G requiring less work than Ek 2(Dk 1(C)) has implications on security of S 49

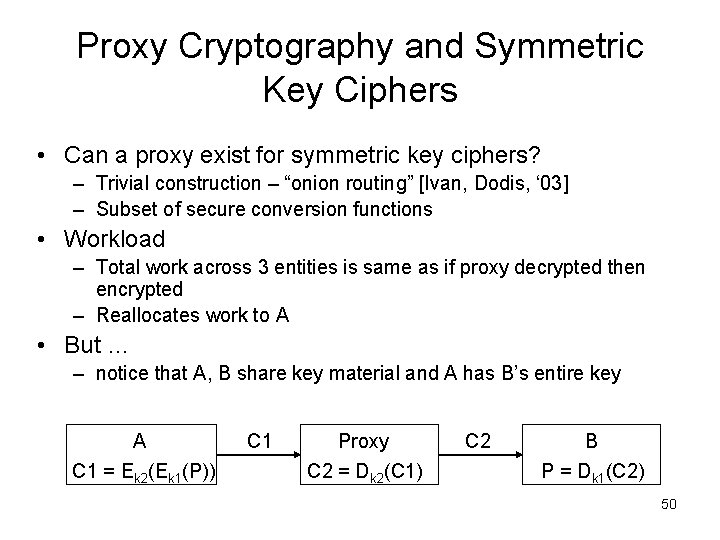
Proxy Cryptography and Symmetric Key Ciphers • Can a proxy exist for symmetric key ciphers? – Trivial construction – “onion routing” [Ivan, Dodis, ‘ 03] – Subset of secure conversion functions • Workload – Total work across 3 entities is same as if proxy decrypted then encrypted – Reallocates work to A • But … – notice that A, B share key material and A has B’s entire key A C 1 = Ek 2(Ek 1(P)) C 1 Proxy C 2 = Dk 2(C 1) C 2 B P = Dk 1(C 2) 50

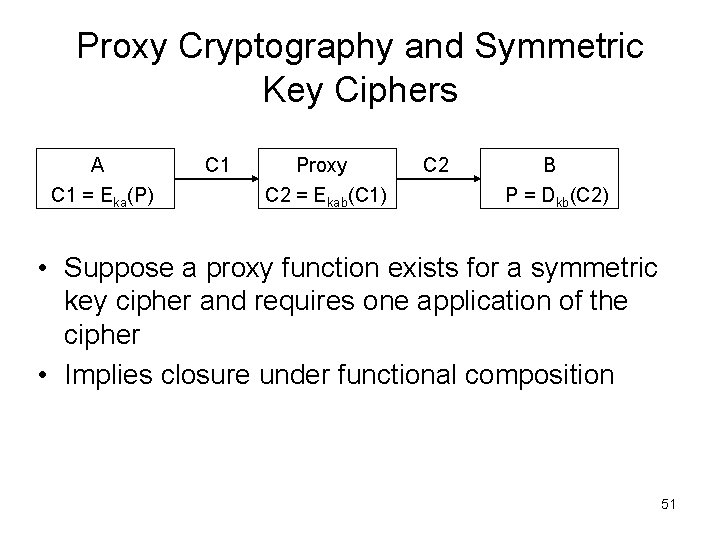
Proxy Cryptography and Symmetric Key Ciphers A C 1 = Eka(P) C 1 Proxy C 2 = Ekab(C 1) C 2 B P = Dkb(C 2) • Suppose a proxy function exists for a symmetric key cipher and requires one application of the cipher • Implies closure under functional composition 51

Implications of Group Property • Proof that DES is not a group [Kaliski, et. al. ‘ 88] • Recall a group is closed under functional composition • For a block cipher, this implies – for every k 1, k 2, a k 3 such that Ek 3(Ek 2(P)) = Ek 1(P) P – O(2 n/2) time required for a key search vs. O(2 n) for non group (n = key length) 52
![Attack Overview Kaliski et al Attack due to Birthday Paradox Given Attack Overview [Kaliski, et. al. ] • Attack due to Birthday Paradox: – Given](https://slidetodoc.com/presentation_image_h/fdd63064bf38c0b1234d038a2a10485a/image-53.jpg)
Attack Overview [Kaliski, et. al. ] • Attack due to Birthday Paradox: – Given a known (P, C) pair with C = Ek 2(P), finds k 1, k 3 to use in place of k 2 – Divide K into two subsets KA, KB – Randomly choose k 1 from KA, k 3 from KB – Check if Ek 3(Ek 1(P)) = C (i. e. Ek 1(P) = Dk 3(C) ) – O(2 n/2) time • Cycling attack: – Given P and C, randomly choose keys from K to form Ekai(… Eka 2(Eka 1(P))…) = Dkbj(… Dkb 2(Dkb 1(C)…) – Finds a series of keys to use in place of k 2 – O(2 n/2 + ) time for small 53

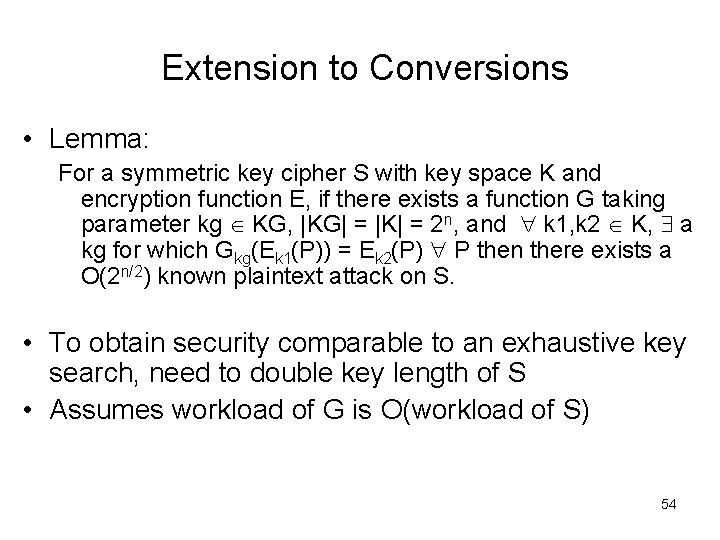
Extension to Conversions • Lemma: For a symmetric key cipher S with key space K and encryption function E, if there exists a function G taking parameter kg KG, |KG| = |K| = 2 n, and k 1, k 2 K, a kg for which Gkg(Ek 1(P)) = Ek 2(P) P then there exists a O(2 n/2) known plaintext attack on S. • To obtain security comparable to an exhaustive key search, need to double key length of S • Assumes workload of G is O(workload of S) 54

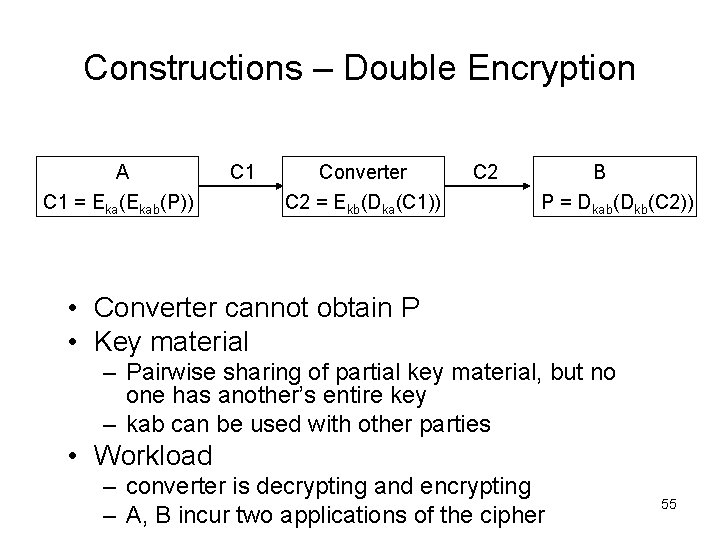
Constructions – Double Encryption A C 1 = Eka(Ekab(P)) C 1 Converter C 2 = Ekb(Dka(C 1)) C 2 B P = Dkab(Dkb(C 2)) • Converter cannot obtain P • Key material – Pairwise sharing of partial key material, but no one has another’s entire key – kab can be used with other parties • Workload – converter is decrypting and encrypting – A, B incur two applications of the cipher 55

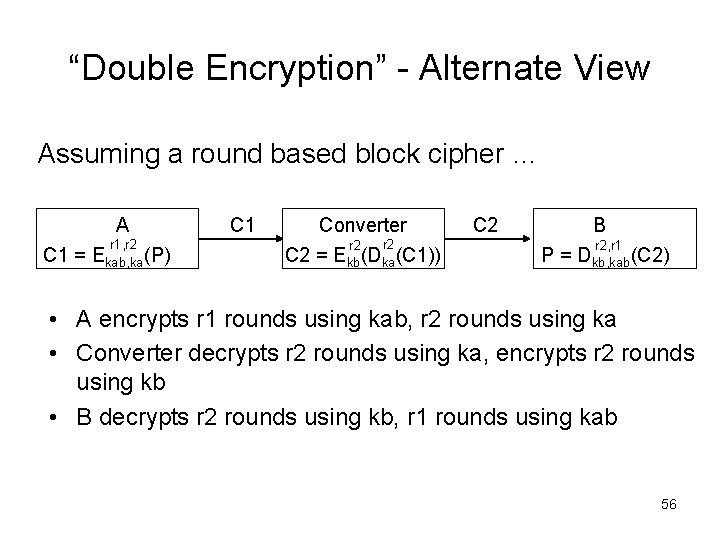
“Double Encryption” Alternate View Assuming a round based block cipher … A r 1, r 2 C 1 = Ekab, ka(P) C 1 Converter r 2 C 2 = Ekb(Dka(C 1)) C 2 B r 2, r 1 P = Dkb, kab(C 2) • A encrypts r 1 rounds using kab, r 2 rounds using ka • Converter decrypts r 2 rounds using ka, encrypts r 2 rounds using kb • B decrypts r 2 rounds using kb, r 1 rounds using kab 56

Alternate View continued A r 1, r 2 C 1 = Ekab, ka(P) C 1 Converter r 2 C 2 = Ekb(Dka(C 1)) C 2 B r 2, r 1 P = Dkb, kab(C 2) • Workload – Dependent on number of rounds • Security – If r rounds in cipher … – Require r 1+r 2 = r to eliminate potential of a reduced round attack at A, B – Security of intermediate result Dka(C 1), at converter depends on r 1, r 2 57

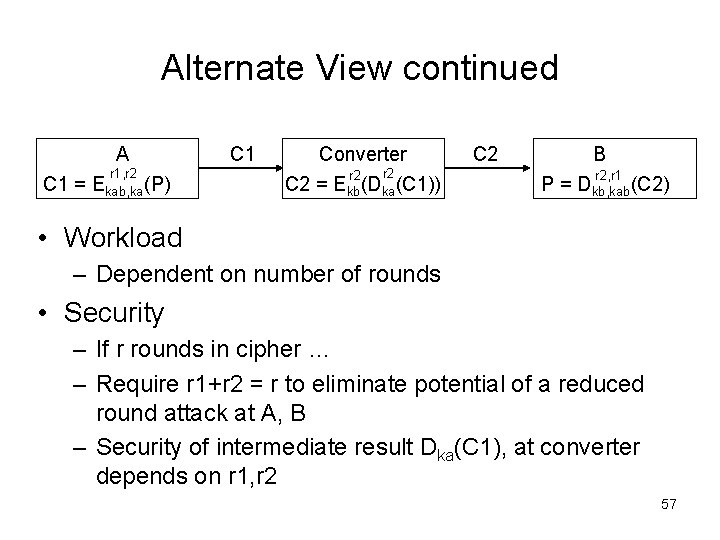
Constructions – Stream Cipher Converter A C 1 = KSa (P) • Workload C 1 C 2 = KSa (KSb (C 1)) or (KSa KSb) C 1 C 2 B P = KSb (C 2) – No extra work required of A, B • Security – A, B do not share key material – Converter does not expose P, but may have sufficient information to do so depending on how combined key streams are created – KSa, KSb can be computed in parallel 58

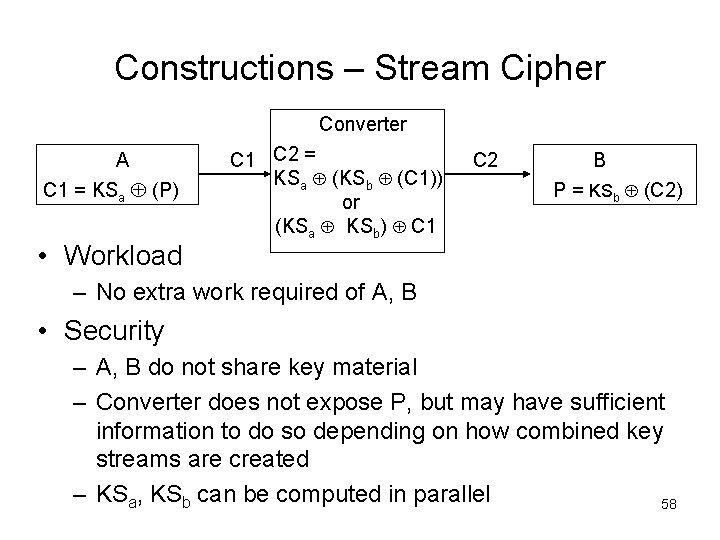
Constructions – Onion Routing A C 1 = Eka(Ekab(P)) C 1 Converter C 2 = Dka(C 1) C 2 B P = Dkab(C 2) • Workload – Total same as decrypting then encrypting – Moves work from converter to A • A, B share a key • Converter cannot obtain P 59