Introduction to Practical Cryptography Lectures 34 Stream Ciphers






























- Slides: 54

Introduction to Practical Cryptography Lectures 3/4 Stream Ciphers 1

Agenda • Properties • Building Blocks • Competitions • Examples 2

Uses • Encryption of streaming data • Random bit generation 3

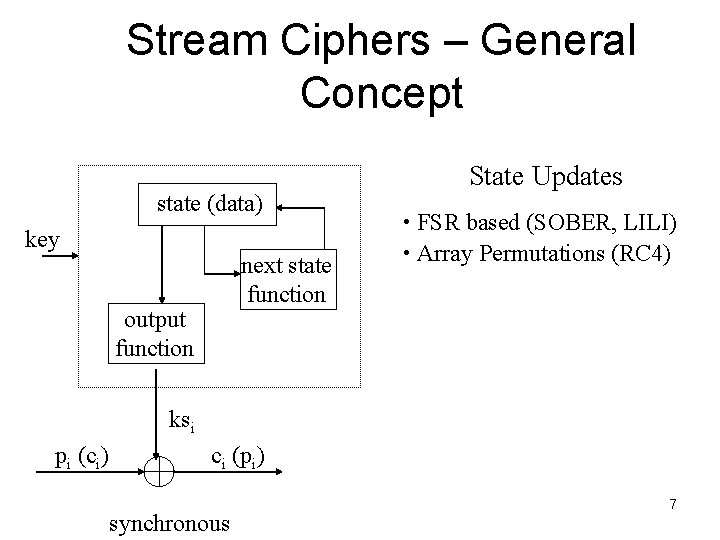
Stream Ciphers • Stream cipher outputs keystream, KS • KS produced by a function, F, that is initialized with a key, k • C = Ek(P) = P KS • P = C KS • k can be used only once • • C 1 = Ek 1(P 1); C 2 = Ek 2(P 2) C 1 C 2 = P 1 KS 1 P 2 KS 2 = P 1 P 2 if KS 1 = KS 2 Will know when P 1 and P 2 have identical bits If know part of P 1 (if packet headers, format information), then can obtain part of P 2 • Period – how long is KS before it starts repeating? • repeating is equivalent to reusing a key 4

Stream Ciphers • Speed • Initialization • Keystream generation • Resources – memory, power, cpu • Hardware, software suitability 5

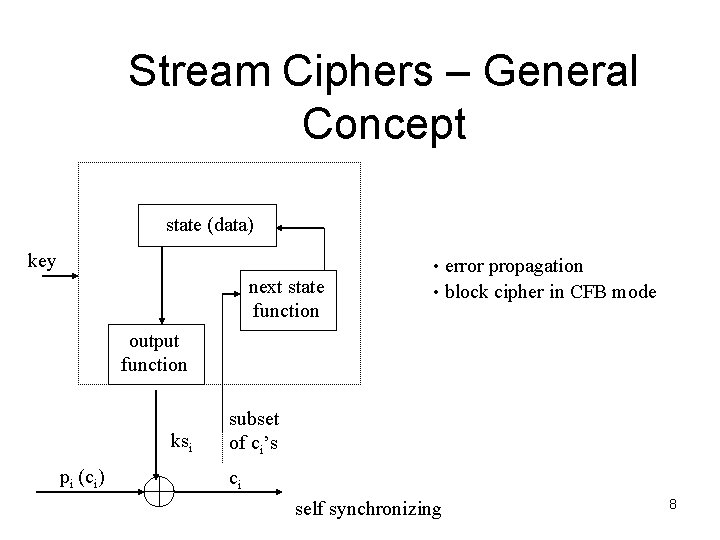
Stream Ciphers • Synchronous stream cipher • • • Sender and receiver must be in-synch Lost bit garbles all subsequent bits unless synch up Flipped bit garbles only one bit Can precompute key stream Example: RC 4, block cipher in OFB mode • Self-synchronizing stream ciphers • • • Use n previous ciphertext bits to compute keystream Lost bit: synch up after n bits Flipped bit : next n bits garbled Can’t precompute keystream Example: Block cipher in ciphertext feedback (CFB) mode 6

Stream Ciphers – General Concept state (data) key next state function output function State Updates • FSR based (SOBER, LILI) • Array Permutations (RC 4) ksi pi (ci) ci (pi) synchronous 7

Stream Ciphers – General Concept state (data) key next state function • error propagation • block cipher in CFB mode output function ksi pi (ci) subset of ci’s ci self synchronizing 8

Keystream Properties • Period of 232 repeats after ~ 8. 5 minutes when encrypting 1 MB/sec • Random appearance: • Runs of 1’s or 0’s: ½ with length 1, ¼ with length 2, 1/8 have length 3 … • Test – little or no compression • Dissipates statistics of plaintext • Complexity: • Low ability to define a bit as a linear expression (or algebraic expression) of bits < period bits away • No discernable relation to key (seed/initial state) bits 9

Agenda • Properties • Building Blocks • Competitions • Examples 10

Stream Ciphers - Approaches • Feedback Shift Register (FSR) based – useful in hardware • Block cipher – CTR, CFB, OFB modes • Components similar to those found in block ciphers 11

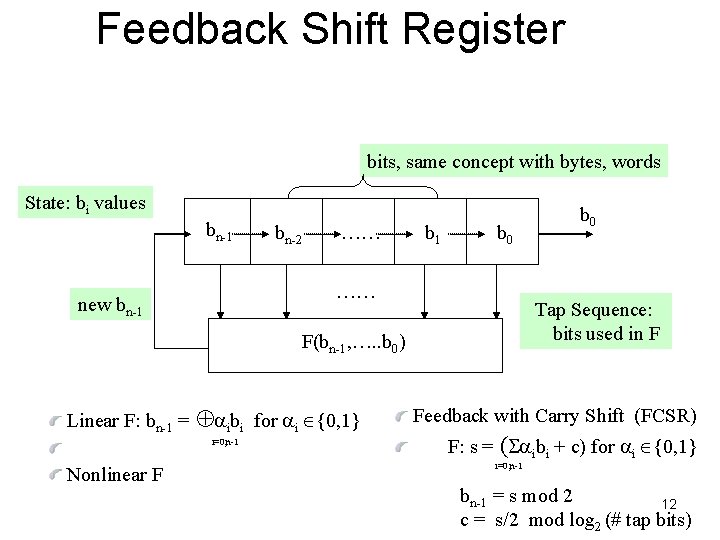
Feedback Shift Register bits, same concept with bytes, words State: bi values bn-1 bn-2 …… b 1 b 0 …… new bn-1 Tap Sequence: bits used in F F(bn-1, …. . b 0) Linear F: bn-1 = ibi for i {0, 1} i=0, n-1 Nonlinear F b 0 Feedback with Carry Shift (FCSR) F: s = ( ibi + c) for i {0, 1} i=0, n-1 bn-1 = s mod 2 12 c = s/2 mod log 2 (# tap bits)

Feedback Shift Registers • Period • LFSR of n bits: Maximum 2 n – 1 • FCSR: depends on initial state • Non-linear FSR: depends on function, initial state • Inefficient in Software • Small # of bits in tap sequence, easier to break. • Large # of bits in tap sequence, slow. • Security • Berlekamp-Massey Algorithm: 2 n output bits needed to reproduce the LFSR in O(n 2) time. • Non-linear FSR: avoid linear approximations 13

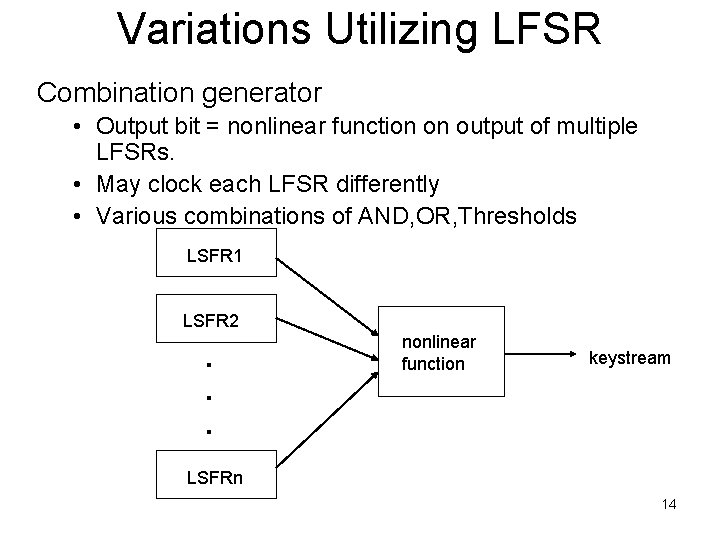
Variations Utilizing LFSR Combination generator • Output bit = nonlinear function on output of multiple LFSRs. • May clock each LFSR differently • Various combinations of AND, OR, Thresholds LSFR 1 LSFR 2 . . . nonlinear function keystream LSFRn 14

Variations Utilizing LFSR • Clock controlled generator • Move to next state only on some clock cycles. • Move to next state on every cycle but only output bit on some clock cycles. • 2 nd LFSR may control clock. • Clock control that affects output is also called stuttering 15

Clock Control Examples • Stop and Go: • 2 LFSRs • LFSR 1’s output clocks LFSR 2 • Alternating Stop and Go: • 3 LFSRs • output of LFSR 1 indicates whether to clock LFSR 2 or LFSR 3 • output is of LFSR’s 2 and 3 • Bilateral Stop and Go: • 2 LFSRs • output = of both outputs • clock LSRFs depending on their output values • Self-Decimated Generators: • control their own clock – some function of their state bits controls clock 16

Clock Control Examples • Shrinking Generator: • 2 LFSRs • always clock • if LFSR 1 outputs 1, use LFSR 2’s output, else no output on that cycle • called “shrinking” because fewer output bits than clock ticks • Self Shrinking Generator: • similar to shrinking generator but use 2 different bits from 1 LSFR instead of 2 LFSRs • Cascade: • output of 1 st level (may be single or combination of generators) controls clock of next level • usually not secure due to some relationship between 1 st level output and final output. 17

Agenda • Properties • Building Blocks • Competitions • Examples 18

NESSIE Stream Cipher Submissions • None recommended • BMGL – too slow, small internal state – time/memory tradeoff attack • Leviathan - distinguishing attack • LILI-128 – attack O(271) • SNOW – distinguishing attack • SOBER-t 16 – distinguishing attack • SOBER-t 32 – distinguishing attack • Both Sober algorithms thought to be subject to side channel analysis 19

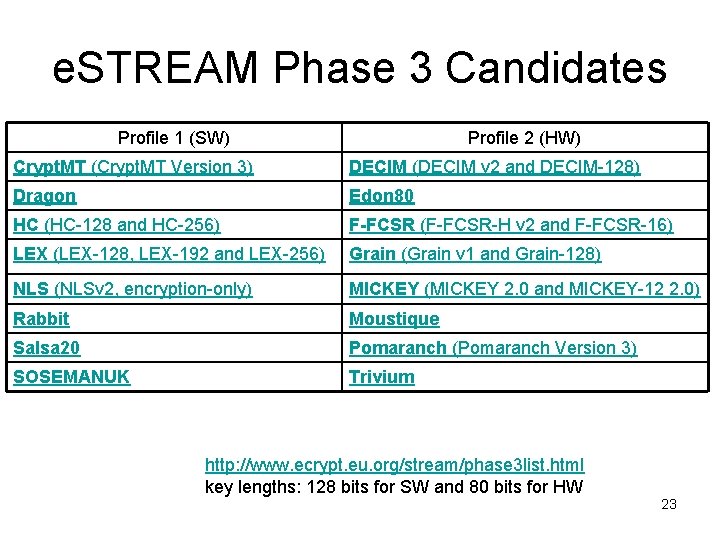
ECRYPT’s e. Stream Contest • Just ended (3 rd round of evaluations finished, winners selected) • 4 for software, 4 for hardware • In third round of evaluations • 16 candidates • 3+ years from time of call for proposals to final report • originally November 2004 to January 2008 • Just ended • ECRYPT: European Network of Excellence for Cryptology 20

e. Stream Overview • Categories • key length of 128 bits and an IV length of 64 and/or 128 bits • key length of 80 bits and an IV length of 32 and/or 64 bits • Separate software and hardware categories within each • Evaluation • Security • Free of licensing requirements … • Performance, range of environments • Committee is only collecting submissions. Evaluations are done by the general cryptographic community. 21

e. Stream Evaluation • Security Criteria • Any key-recovery attack should be at least as difficult as exhaustive search. • Distinguishing attacks • Interest to the cryptographic community • Relative importance of high complexity distinguishing attacks is an issue for wider discussion • Clarity of design • Implementation Criteria • • Software and hardware efficiency Execution code and memory sizes Performance Flexibility of use 22

e. STREAM Phase 3 Candidates Profile 1 (SW) Profile 2 (HW) Crypt. MT (Crypt. MT Version 3) DECIM (DECIM v 2 and DECIM-128) Dragon Edon 80 HC (HC-128 and HC-256) F-FCSR (F-FCSR-H v 2 and F-FCSR-16) LEX (LEX-128, LEX-192 and LEX-256) Grain (Grain v 1 and Grain-128) NLS (NLSv 2, encryption-only) MICKEY (MICKEY 2. 0 and MICKEY-12 2. 0) Rabbit Moustique Salsa 20 Pomaranch (Pomaranch Version 3) SOSEMANUK Trivium http: //www. ecrypt. eu. org/stream/phase 3 list. html key lengths: 128 bits for SW and 80 bits for HW 23

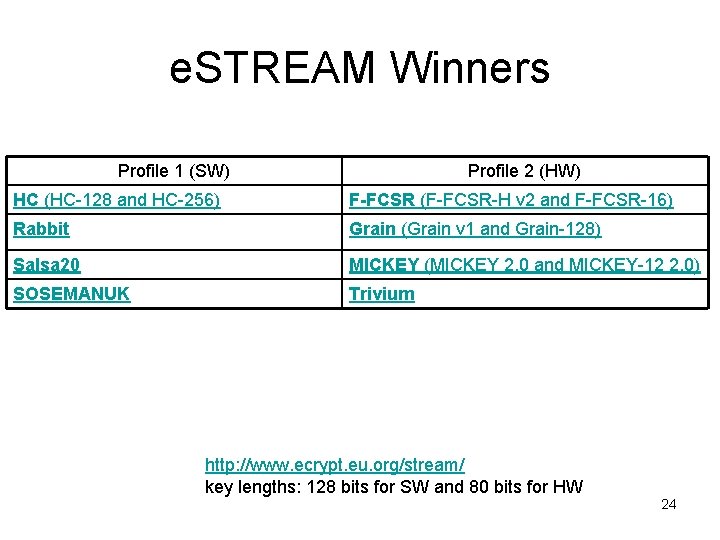
e. STREAM Winners Profile 1 (SW) Profile 2 (HW) HC (HC-128 and HC-256) F-FCSR (F-FCSR-H v 2 and F-FCSR-16) Rabbit Grain (Grain v 1 and Grain-128) Salsa 20 MICKEY (MICKEY 2. 0 and MICKEY-12 2. 0) SOSEMANUK Trivium http: //www. ecrypt. eu. org/stream/ key lengths: 128 bits for SW and 80 bits for HW 24

Agenda • Properties • Building Blocks • Competitions • Examples 25

Stream Cipher Examples • Lists • http: //en. wikipedia. org/wiki/Stream_cipher • http: //www. ecrypt. eu. org/stream/ • RC 4 • A 5/1 • A 5/3 • LILI • Sober • Trivium • Lex 26

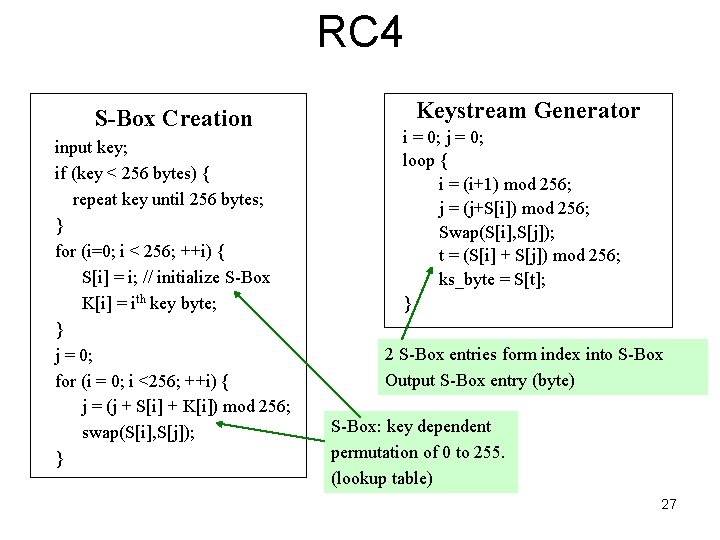
RC 4 S-Box Creation input key; if (key < 256 bytes) { repeat key until 256 bytes; } for (i=0; i < 256; ++i) { S[i] = i; // initialize S-Box K[i] = ith key byte; } j = 0; for (i = 0; i <256; ++i) { j = (j + S[i] + K[i]) mod 256; swap(S[i], S[j]); } Keystream Generator i = 0; j = 0; loop { i = (i+1) mod 256; j = (j+S[i]) mod 256; Swap(S[i], S[j]); t = (S[i] + S[j]) mod 256; ks_byte = S[t]; } 2 S-Box entries form index into S-Box Output S-Box entry (byte) S-Box: key dependent permutation of 0 to 255. (lookup table) 27

RC 4 Cryptanalysis • Initial keystream byte highly correlated with first few key bytes • Recommendations to discard first 256 or 512 output bytes • Distinguish from random: O(230. 6) bytes needed • Attempts to backtrack to initial state from keystream Keystream Generator i = 0; j = 0; loop { i = (i+1) mod 256; j = (j+S[i]) mod 256; Swap(S[i], S[j]); t = (S[i] + S[j]) mod 256; ks_byte = S[t]; } 28

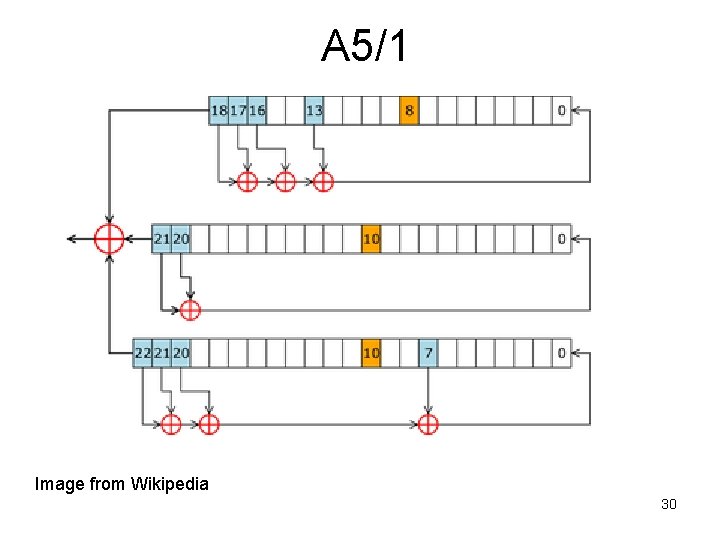
A 5/1 • Used in Global System for Mobil Communications (GSM) • Example of a cipher manufacturers tried to keep secret, it was leaked and also reversed engineered within 5 years • A 5/2 – weaker cipher used in some countries due to export rules • GSM phone conversations are sent as sequences of frames. • One 228 bit frame is sent every 4. 6 milliseconds: 114 bits for the communication in each direction. • A 5/1 produces 228 bits to XOR with the frame • Initialized using a 64 -bit key combined with a publicly-known 22 -bit frame number. • In some GSM implementations, 10 key bits are fixed at zero - effective key length is 54 bits. • A 5/1 is based around a combination of three LFSRs with irregular clocking. 29

A 5/1 Image from Wikipedia 30

A 5/1 LSRFs • 19 bits • x 19 + x 5 + x 2 + x + 1 • clock bit 8 • tapped bits: 13, 16, 17, 18 • 22 bits • x 22 + x + 1 • clock bit 10 • tapped bits 20, 21 • 23 bits • x 23 + x 15 + x 2 + x + 1 • clock bit 10 • tapped bits 7, 20, 21, 22 • Least significant bit numbered 0 • Tapped bits of each LSRF are XORed to create value of next 0 bit. • Output bits of the three LSRFs are XORed to form the keystream bit 31

A 5/1 • Each cycle, look at the three clock bits. The majority value, cm, is determined. • In each LSRF, if the clock bit matches cm, the registers are clocked. • In each cycle, 2 or 3 LSRFs will be clocked. 32

A 5/1 Initialization • Registers set to all 0’s • Incorporate the key and frame number: • For 64 cycles, the key is mixed in by XORing the ith key bit with the least significant bit of each register • For 22 cycles, the 22 bit frame value is mixed in – same as with key value • Normal clocking used • 100 cycles are run using the majority clocking, the output is discarded • End result is the initial state 33

A 5/1 • Three short LSFRs • Not many tap bits to guess 34

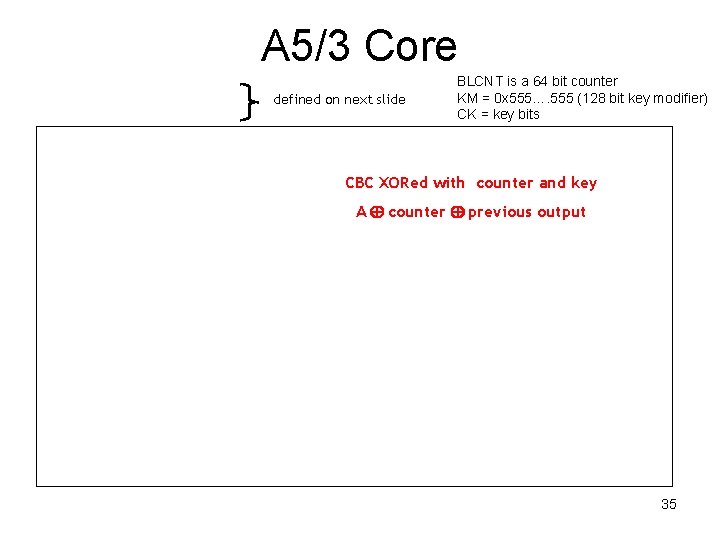
A 5/3 Core • defined on next slide BLCNT is a 64 bit counter KM = 0 x 555…. 555 (128 bit key modifier) CK = key bits • CBC XORed with counter and key • A counter previous output 35

A 5/3 GSM • Kc = key • http: //www. gsmworld. com/using/algorithms/docs/a 5_3_and_gea 3_specifications. pdf 36

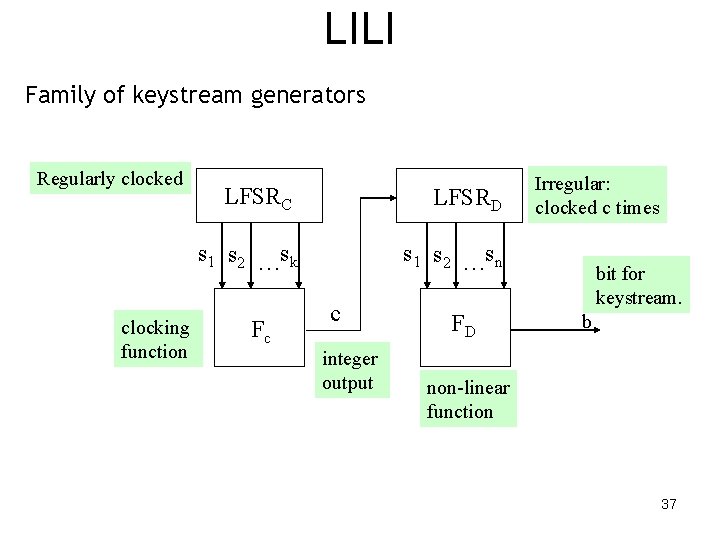
LILI Family of keystream generators Regularly clocked clocking function LFSRC LFSRD s 1 s 2 …sk s 1 s 2 …sn Fc c integer output FD Irregular: clocked c times bit for keystream. b non-linear function 37

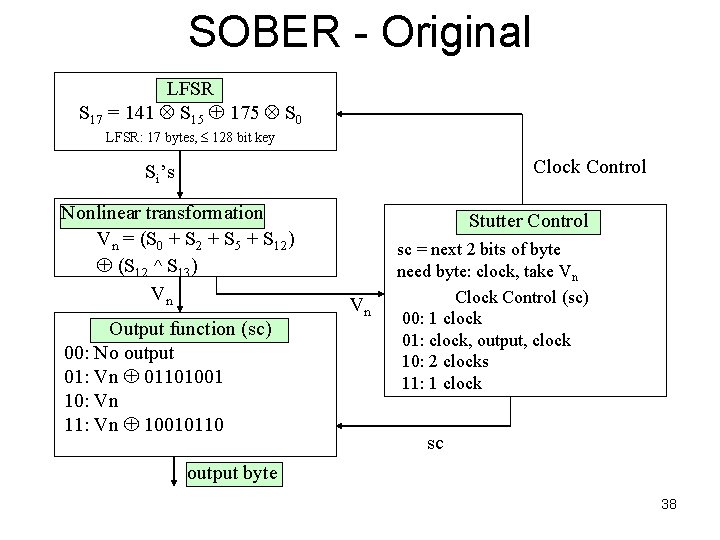
SOBER - Original LFSR S 17 = 141 S 15 175 S 0 LFSR: 17 bytes, 128 bit key Clock Control Si’s Nonlinear transformation Vn = (S 0 + S 2 + S 5 + S 12) (S 12 S 13) Vn Output function (sc) 00: No output 01: Vn 01101001 10: Vn 11: Vn 10010110 Stutter Control Vn sc = next 2 bits of byte need byte: clock, take Vn Clock Control (sc) 00: 1 clock 01: clock, output, clock 10: 2 clocks 11: 1 clock sc output byte 38

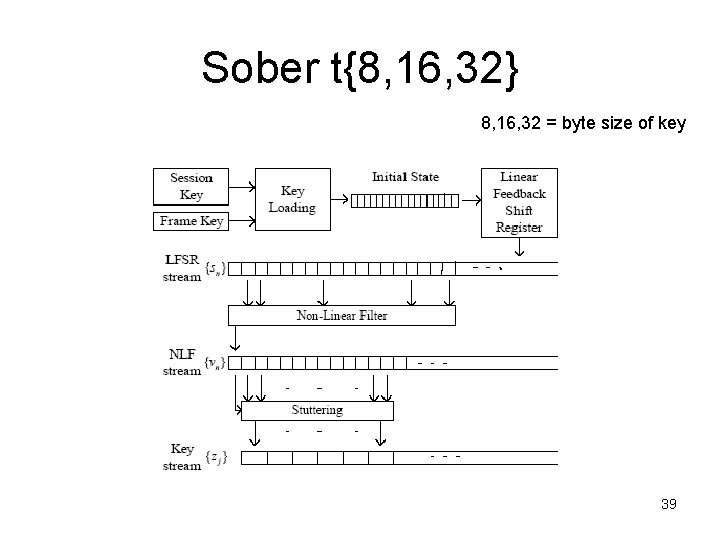
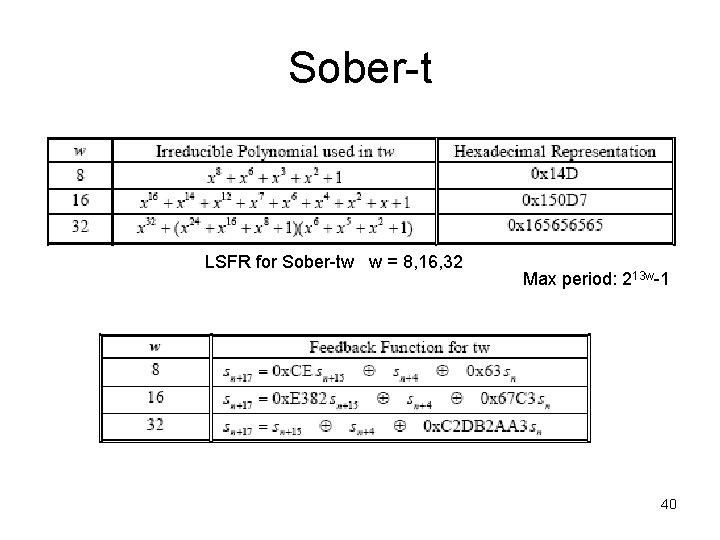
Sober t{8, 16, 32} 8, 16, 32 = byte size of key 39

Sober-t LSFR for Sober-tw w = 8, 16, 32 Max period: 213 w-1 40

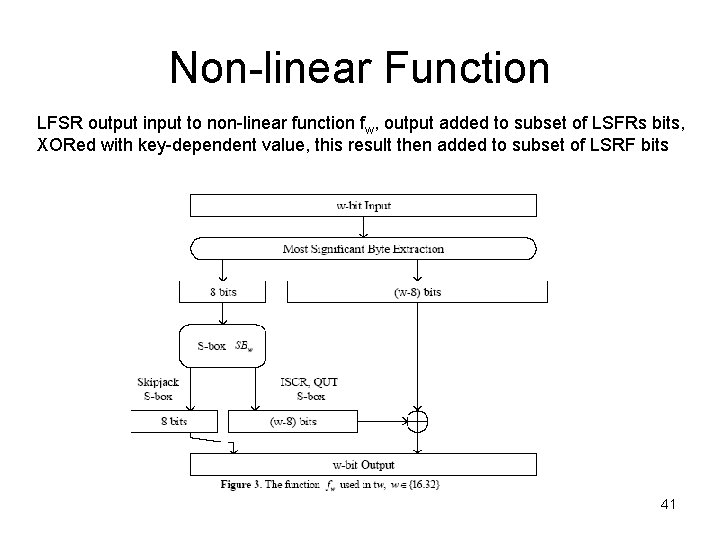
Non-linear Function LFSR output input to non-linear function fw, output added to subset of LSFRs bits, XORed with key-dependent value, this result then added to subset of LSRF bits 41

Trivium • Christophe De Canniere and Bart Preneel • hardware oriented synchronous stream cipher • Trivium generates up to 264 bits of key stream from an 80 -bit secret key and an 80 -bit initial value (IV). • Internal state is 288 bits 42

Trivium • IV and key used to initialize the state • Iterate state – extract values of 15 specific state bits and use them to update 3 bits of the state and to compute 1 bit of the key stream zi. – state bits then rotated and process repeats 43

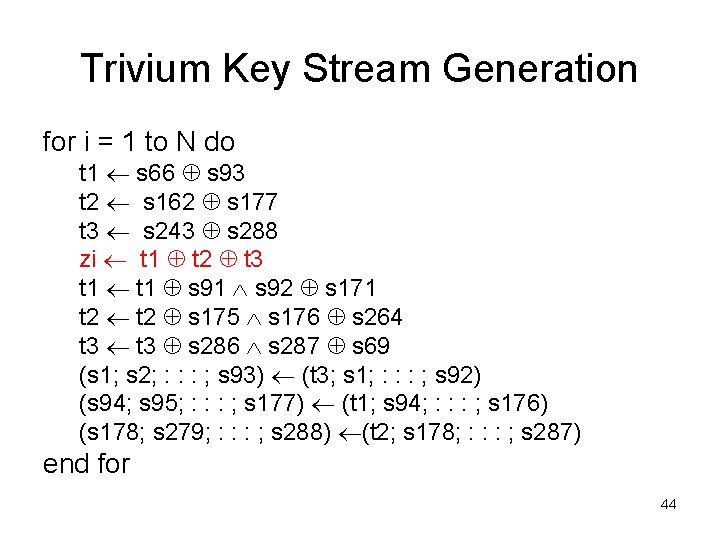
Trivium Key Stream Generation for i = 1 to N do t 1 s 66 s 93 t 2 s 162 s 177 t 3 s 243 s 288 zi t 1 t 2 t 3 t 1 s 91 s 92 s 171 t 2 s 175 s 176 s 264 t 3 s 286 s 287 s 69 (s 1; s 2; : : : ; s 93) (t 3; s 1; : : : ; s 92) (s 94; s 95; : : : ; s 177) (t 1; s 94; : : : ; s 176) (s 178; s 279; : : : ; s 288) (t 2; s 178; : : : ; s 287) end for 44

Trivium Initialization • load 80 -bit key and 80 -bit IV into 288 -bit initial state • set all remaining bits to 0, except for s 286, s 287, and s 288, which are set to 1 • state is rotated over 4 full cycles of the for look, but no bits are output (for i = 1 to 4 288) 45

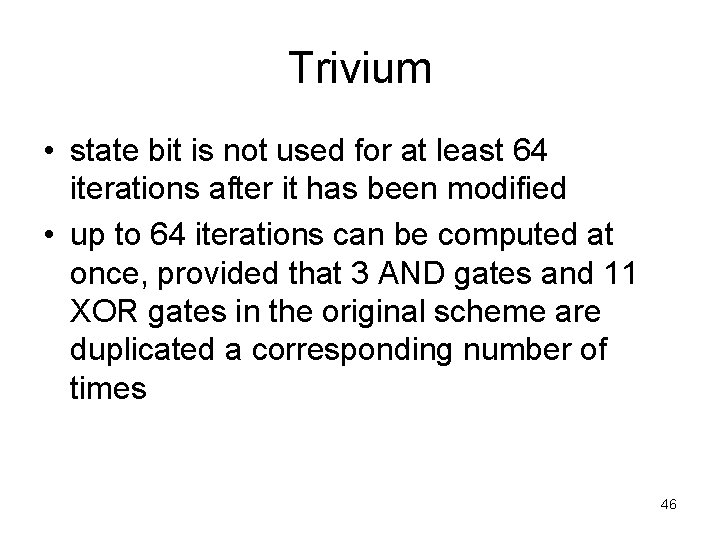
Trivium • state bit is not used for at least 64 iterations after it has been modified • up to 64 iterations can be computed at once, provided that 3 AND gates and 11 XOR gates in the original scheme are duplicated a corresponding number of times 46

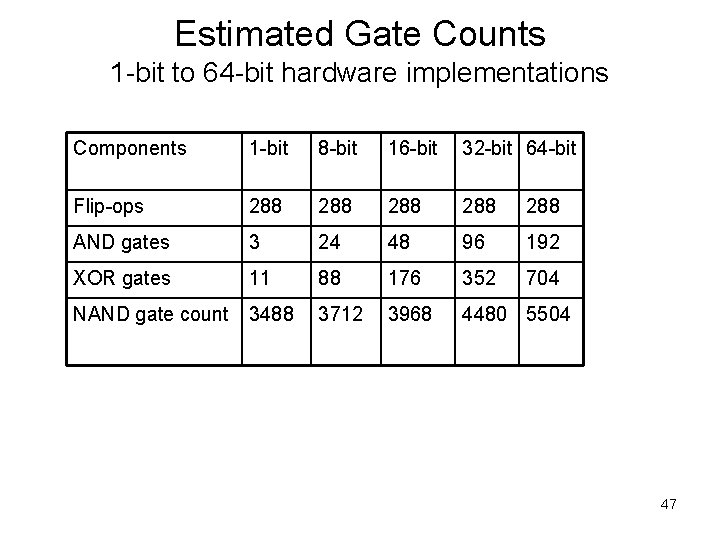
Estimated Gate Counts 1 -bit to 64 -bit hardware implementations Components 1 -bit 8 -bit 16 -bit 32 -bit 64 -bit Flip-ops 288 288 288 AND gates 3 24 48 96 192 XOR gates 11 88 176 352 704 NAND gate count 3488 3712 3968 4480 5504 47

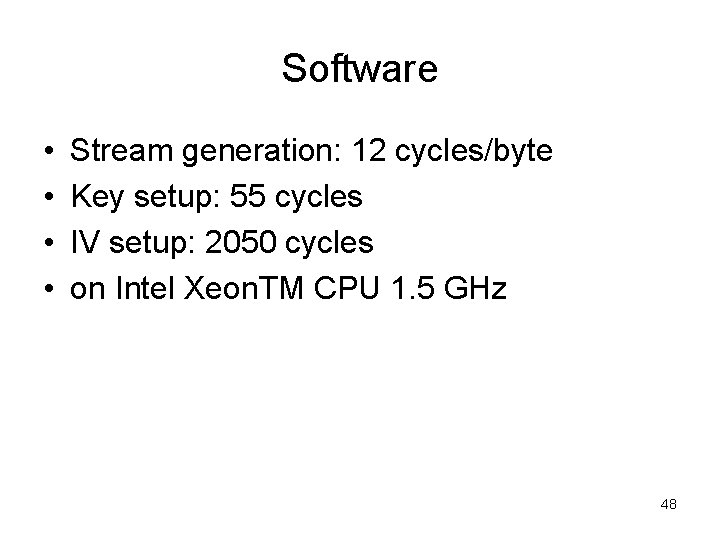
Software • • Stream generation: 12 cycles/byte Key setup: 55 cycles IV setup: 2050 cycles on Intel Xeon. TM CPU 1. 5 GHz 48

Trivium Security • Linear correlations between key stream bits and internal state bits are easy to find because zi is simply defined to be equal to s 66 s 93 s 162 s 177 s 243 s 288. • But, as opposed to LFSR based ciphers, Trivium's state evolves in a nonlinear way – not clear how an attacker should combine these equations in order to efficiently recover the state – Estimate: follow linear trails through the cipher and approximate the outputs of all encountered AND gates by 0. However, the positions of the taps in Trivium have been chosen in such a way that any trail of this specific type is forced to approximate at least 72 AND gate outputs – If assume that the correlation of linear combination is completely explained by a specific trail considered, then it would have a correlation coefficient of 2 -72 • Detecting such a correlation would require at least 2144 bits of key stream • Other more complicated types of linear trails with larger correlations might exist, estimate that no correlations will exceed 2 -40 49

Lex • Alex Biryukov • Leak EXtraction • Software category – Uses AES – reuse if application has AES implementation 50

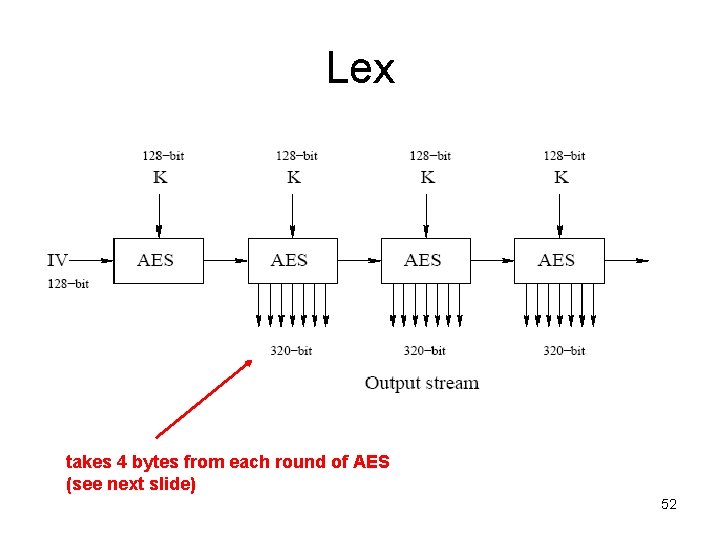
Lex • Initialize: – Key AES: 128 -bit key, K, run through standard AES key-schedule – State: 128 -bit IV is encrypted by AES S = AESK(IV ) • Generate key stream – Repeatedly encrypt (starting with S) • Rekey every 500 AES applications 51

Lex takes 4 bytes from each round of AES (see next slide) 52

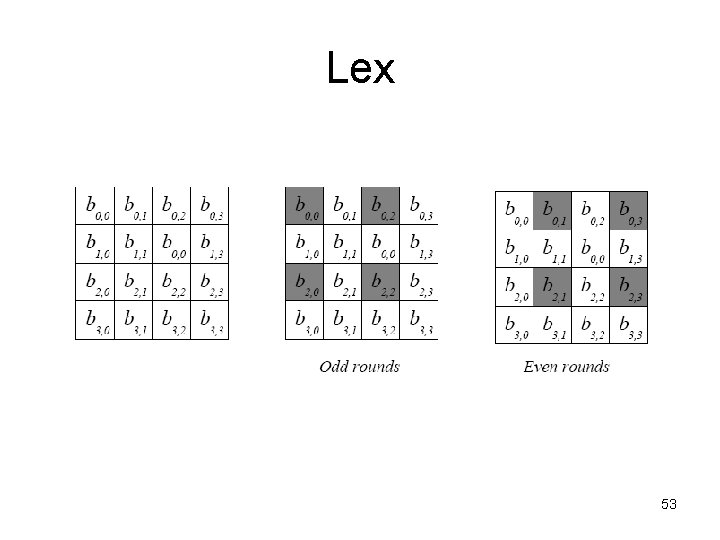
Lex 53

Lex • order of bytes – not relevant for security – relevant for fast software implementation • allows extraction of a 32 -bit value from two 32 -bit rows in four steps ((t 0&0 x. FF 00 FF) << 8) (t 2&0 x. FF 00 FF) t 0 = 1 st row, t 2 = 3 rd row in 4 x 4 matrix 54