Introduction to IT and Communications Technology Ethernet Fundamentals




- Slides: 29

Introduction to IT and Communications Technology Ethernet Fundamentals CE 00378 -1 Justin Champion C 208 – 3292

Content n What we are looking at ¨ Ethernet technology How did it develop n How and why it works n Features of the Technology n

Evolution of Ethernet n The most widely used technology LAN based network technology is Ethernet (IEEE 802. 2) ¨ This technology is based on broadcast radio, used within a cable ¨ The technology is widely used due Cheapness of installation n Reliability n Ease of expansion and extension of the networks n Ability to adapt to multi types of usage n

Evolution of Ethernet n One part of Ethernet is an extension of the Alohanet which was developed in the 1960’s ¨ This was a radio technique which was used to allow multiple people on a network, using radio technology to access computer systems n The access techniques used for this network was used for Ethernet

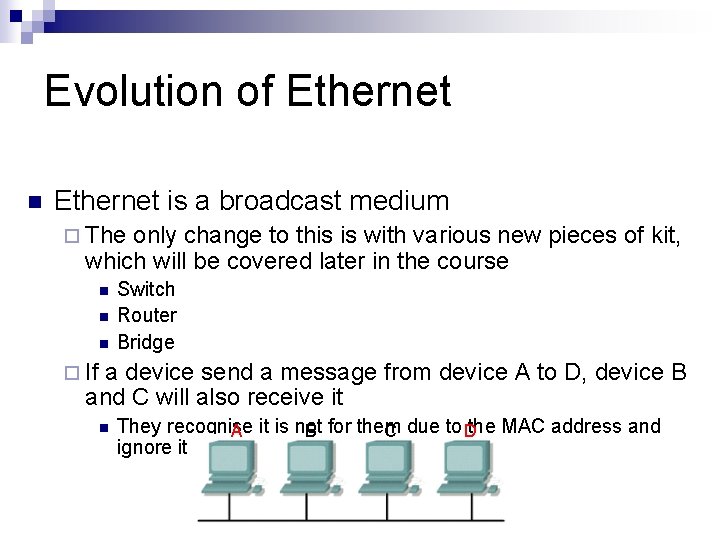
Evolution of Ethernet n Ethernet is a broadcast medium ¨ The only change to this is with various new pieces of kit, which will be covered later in the course n n n Switch Router Bridge ¨ If a device send a message from device A to D, device B and C will also receive it n They recognise A it is not B for them C due to Dthe MAC address and ignore it

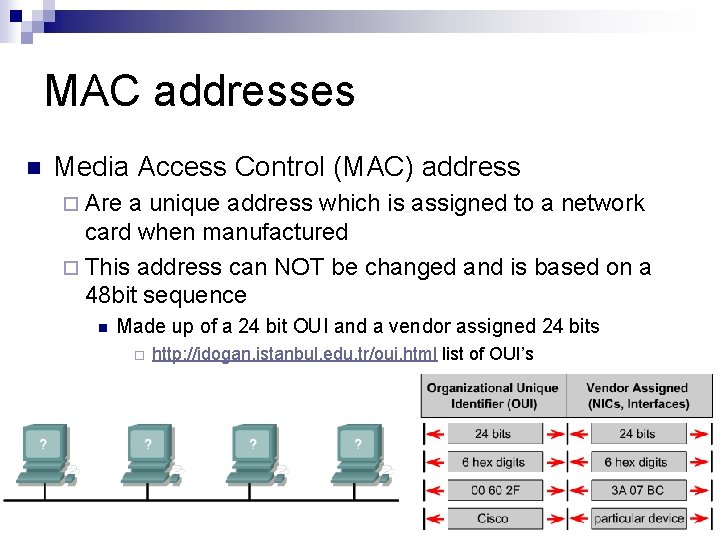
MAC addresses n Media Access Control (MAC) address ¨ Are a unique address which is assigned to a network card when manufactured ¨ This address can NOT be changed and is based on a 48 bit sequence n Made up of a 24 bit OUI and a vendor assigned 24 bits ¨ http: //idogan. istanbul. edu. tr/oui. html list of OUI’s

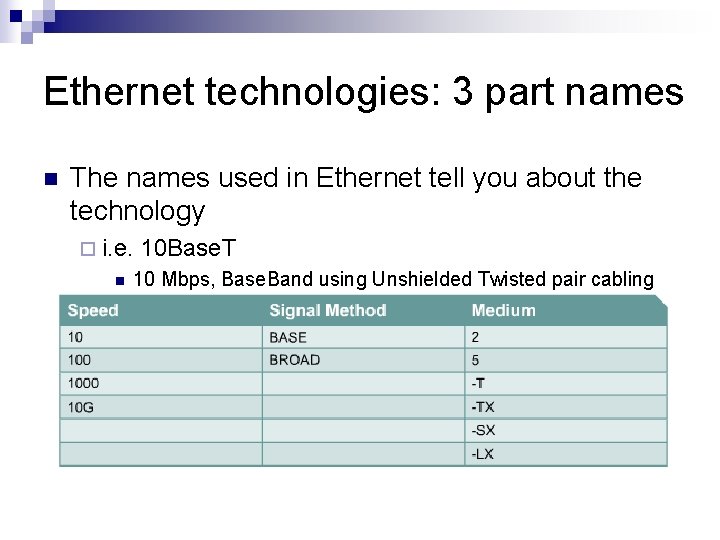
Ethernet technologies: 3 part names n The names used in Ethernet tell you about the technology ¨ i. e. n 10 Base. T 10 Mbps, Base. Band using Unshielded Twisted pair cabling

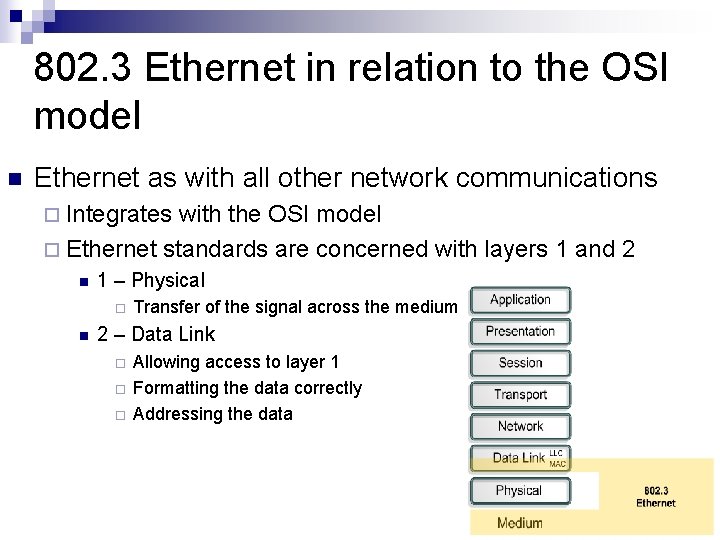
802. 3 Ethernet in relation to the OSI model n Ethernet as with all other network communications ¨ Integrates with the OSI model ¨ Ethernet standards are concerned with layers 1 and 2 n 1 – Physical ¨ n Transfer of the signal across the medium 2 – Data Link ¨ ¨ ¨ Allowing access to layer 1 Formatting the data correctly Addressing the data

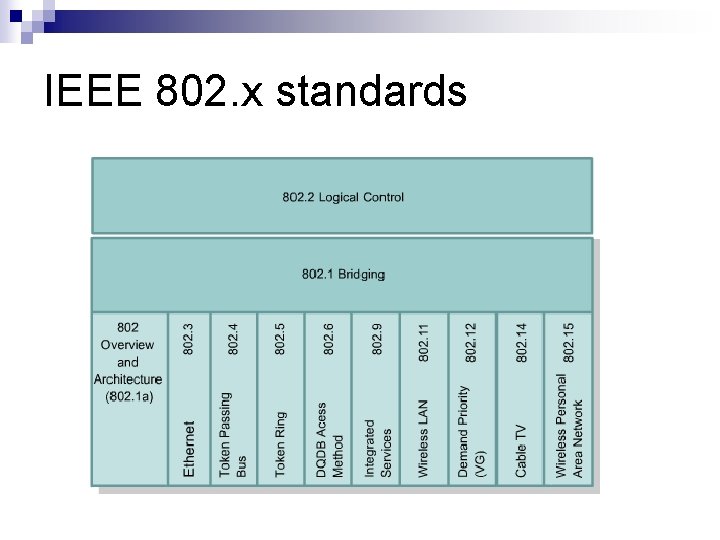
IEEE ? n Institute of Electrical and Electronic Engineers (IEEE) These are not for profit group with a worldwide base ¨ They develop standards for electrical and electronic products ¨ n n The standards are based on the input of the members of the IEEE, to agree on the best standards Currently there are 900 IEEE standards with many more being developed ¨ ¨ n IEEE 802. 3 - Ethernet IEEE 1284 – Parallel Port IEEE 802. 11 b – Wireless LAN http: //wally. rit. edu/pubs/guides/ieeestds. html list of standard groups The peer review methods allow for standards to be developed that take account of worldwide concerns for a technology

IEEE 802. x standards

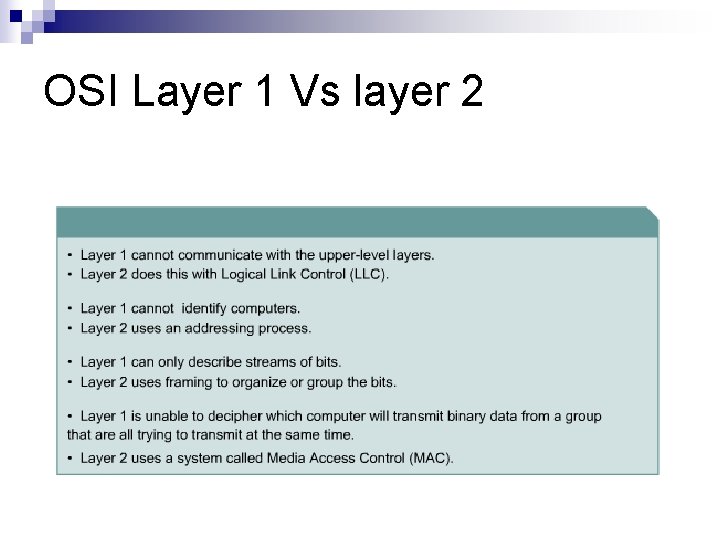
OSI Layer 1 Vs layer 2

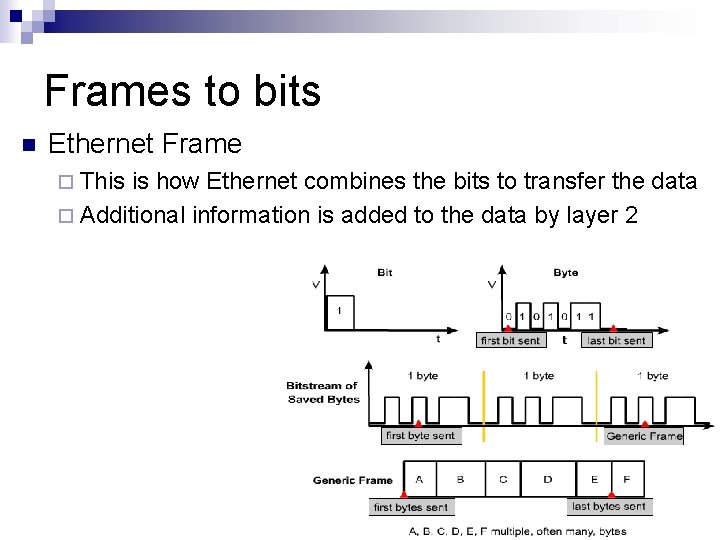
Frames to bits n Ethernet Frame ¨ This is how Ethernet combines the bits to transfer the data ¨ Additional information is added to the data by layer 2

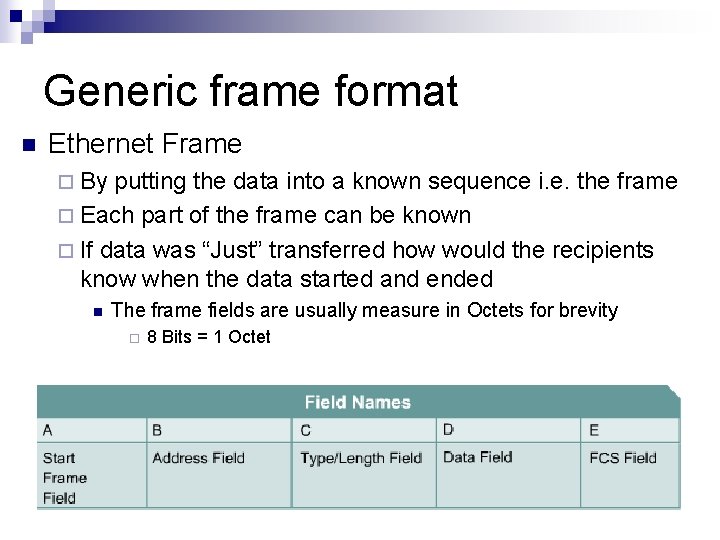
Generic frame format n Ethernet Frame ¨ By putting the data into a known sequence i. e. the frame ¨ Each part of the frame can be known ¨ If data was “Just” transferred how would the recipients know when the data started and ended n The frame fields are usually measure in Octets for brevity ¨ 8 Bits = 1 Octet

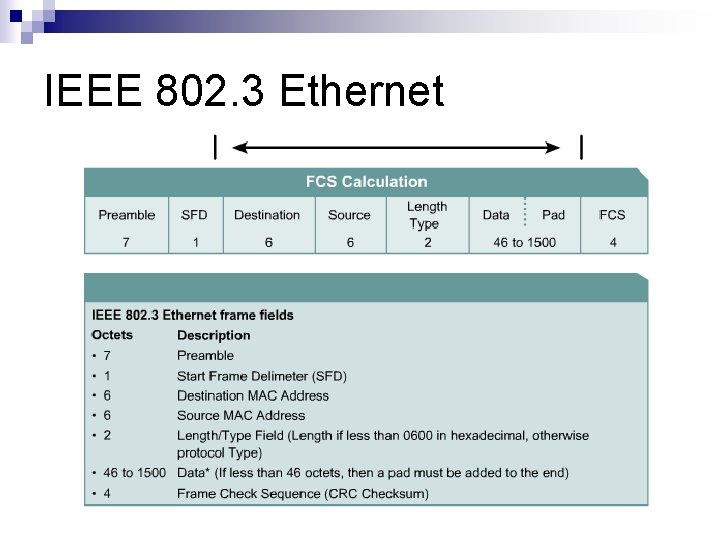
IEEE 802. 3 Ethernet

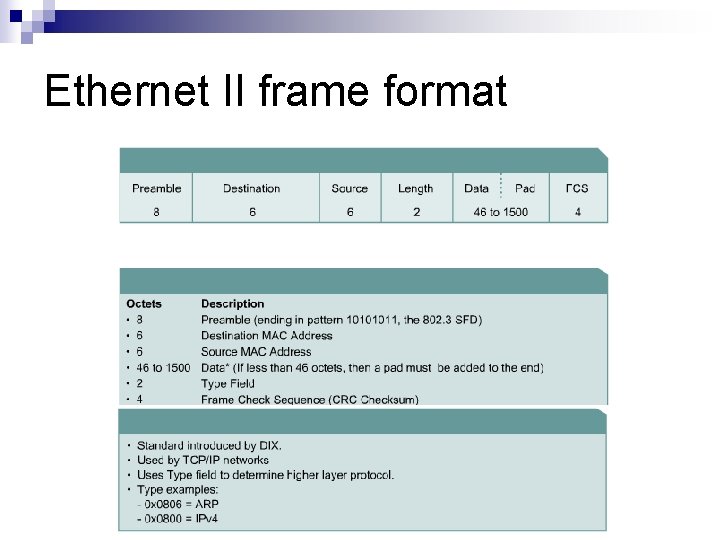
Ethernet II frame format

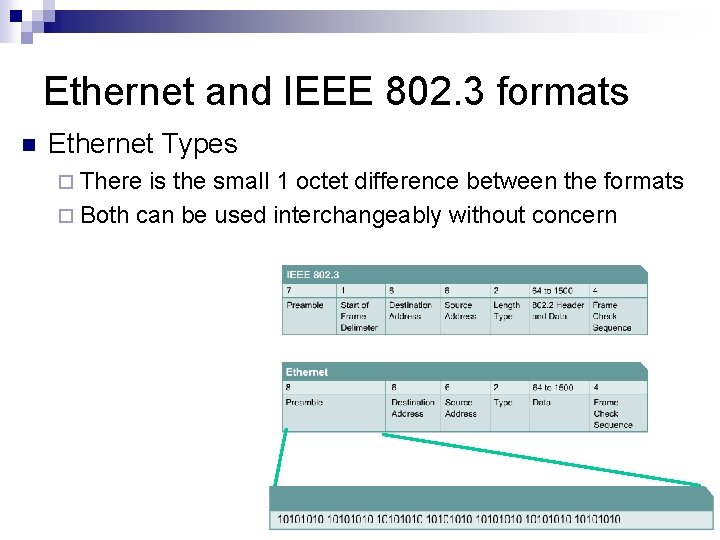
Ethernet and IEEE 802. 3 formats n Ethernet Types ¨ There is the small 1 octet difference between the formats ¨ Both can be used interchangeably without concern

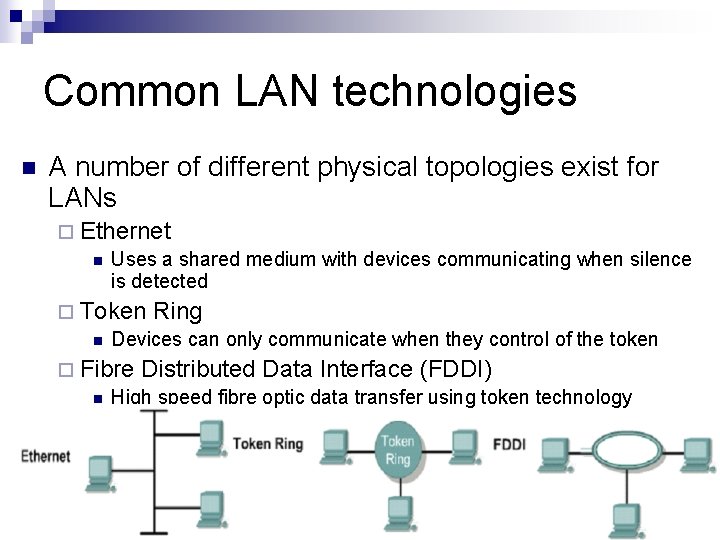
Common LAN technologies n A number of different physical topologies exist for LANs ¨ Ethernet n Uses a shared medium with devices communicating when silence is detected ¨ Token Ring n Devices can only communicate when they control of the token ¨ Fibre Distributed Data Interface (FDDI) n High speed fibre optic data transfer using token technology

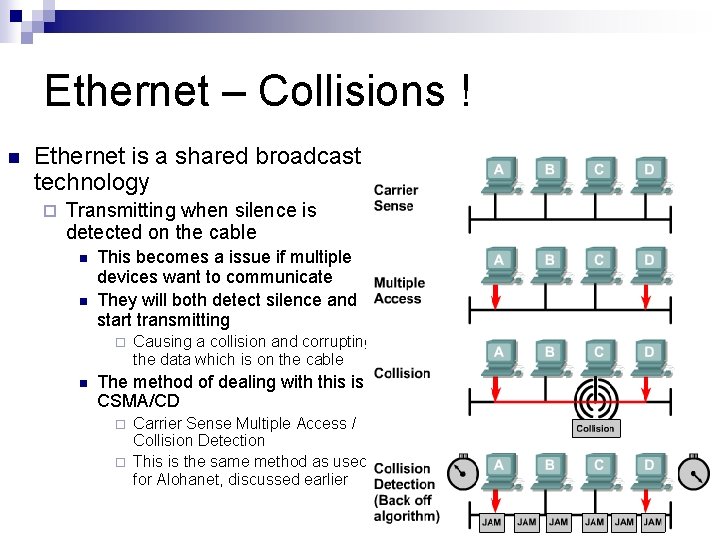
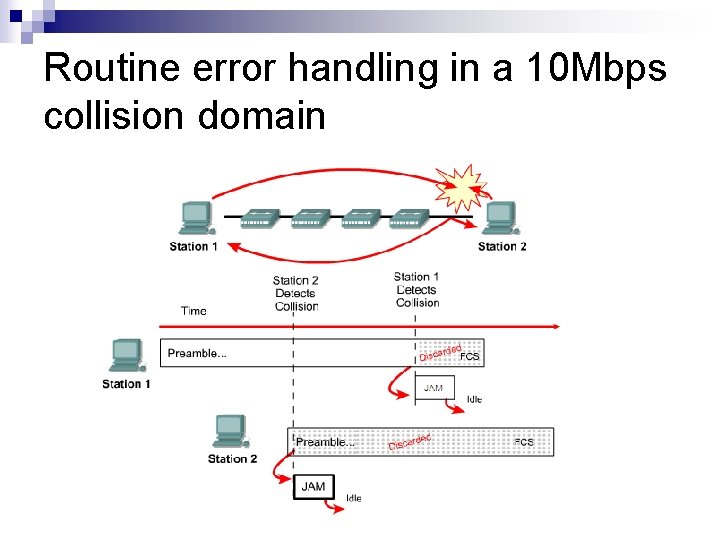
Ethernet – Collisions ! n Ethernet is a shared broadcast technology ¨ Transmitting when silence is detected on the cable n n This becomes a issue if multiple devices want to communicate They will both detect silence and start transmitting ¨ n Causing a collision and corrupting the data which is on the cable The method of dealing with this is CSMA/CD ¨ ¨ Carrier Sense Multiple Access / Collision Detection This is the same method as used for Alohanet, discussed earlier

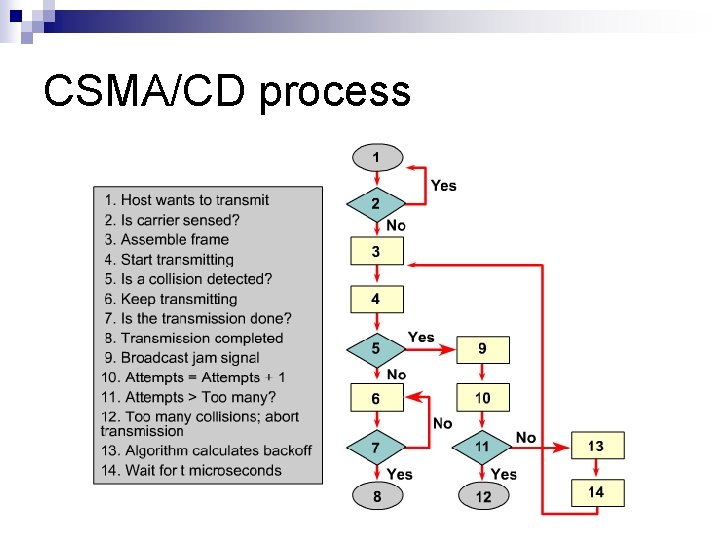
CSMA/CD process

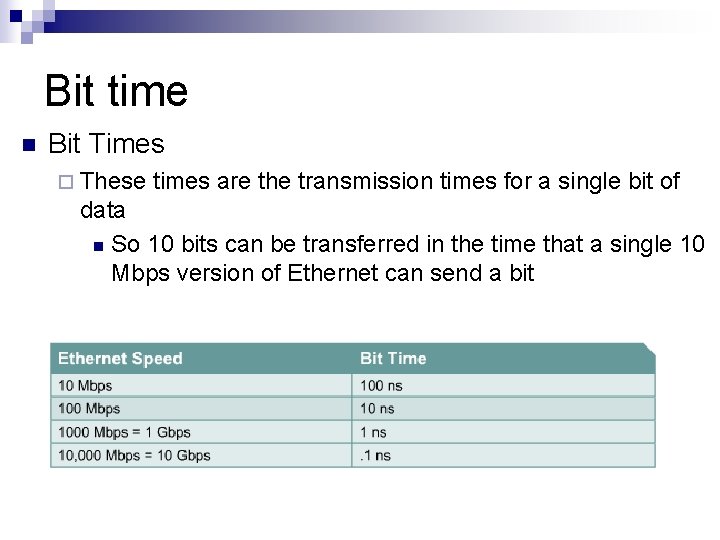
Bit time n Bit Times ¨ These times are the transmission times for a single bit of data n So 10 bits can be transferred in the time that a single 10 Mbps version of Ethernet can send a bit

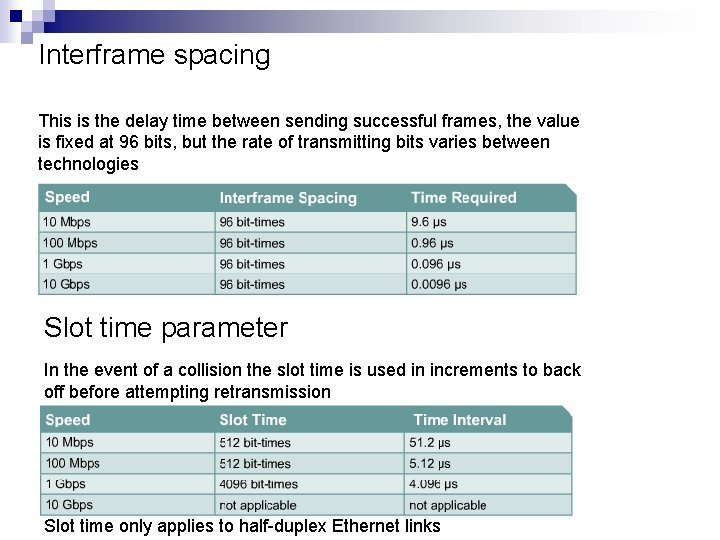
Interframe spacing This is the delay time between sending successful frames, the value is fixed at 96 bits, but the rate of transmitting bits varies between technologies Slot time parameter In the event of a collision the slot time is used in increments to back off before attempting retransmission Slot time only applies to half-duplex Ethernet links

Routine error handling in a 10 Mbps collision domain

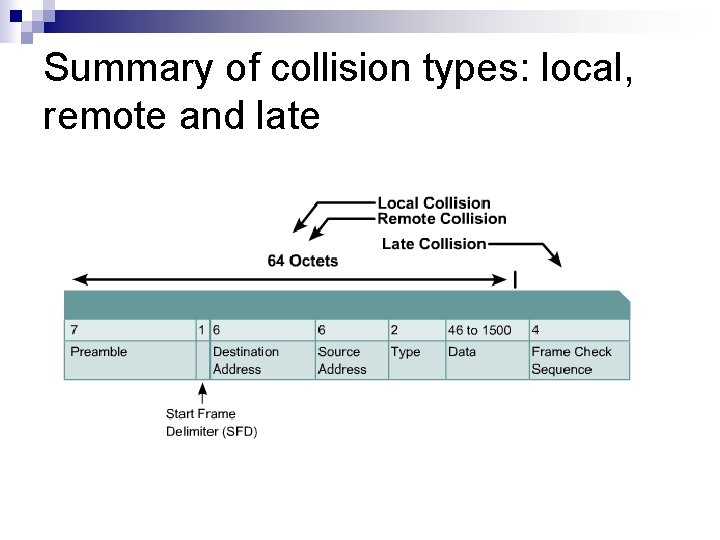
Summary of collision types: local, remote and late

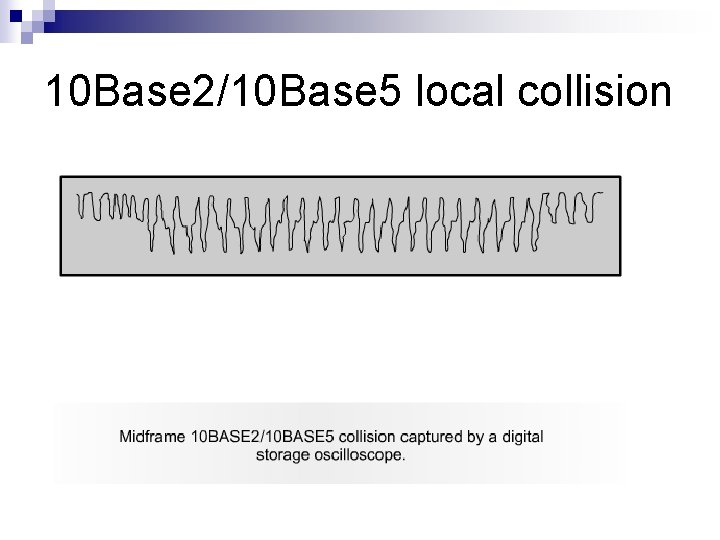
10 Base 2/10 Base 5 local collision

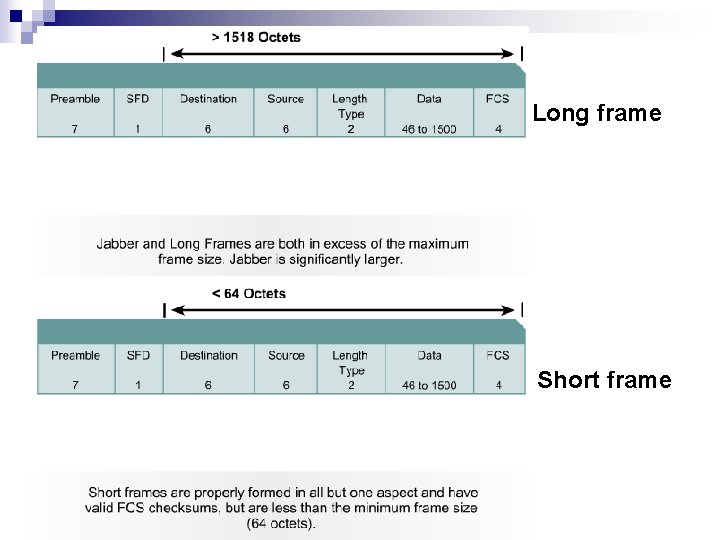
Long frame Short frame

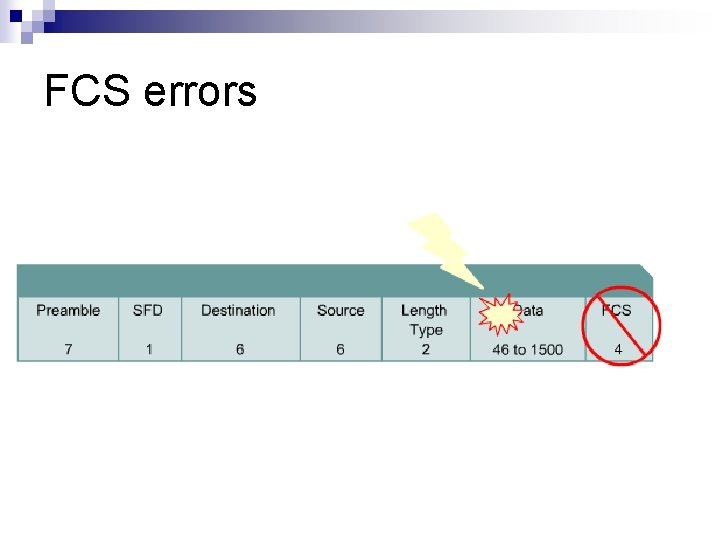
FCS errors

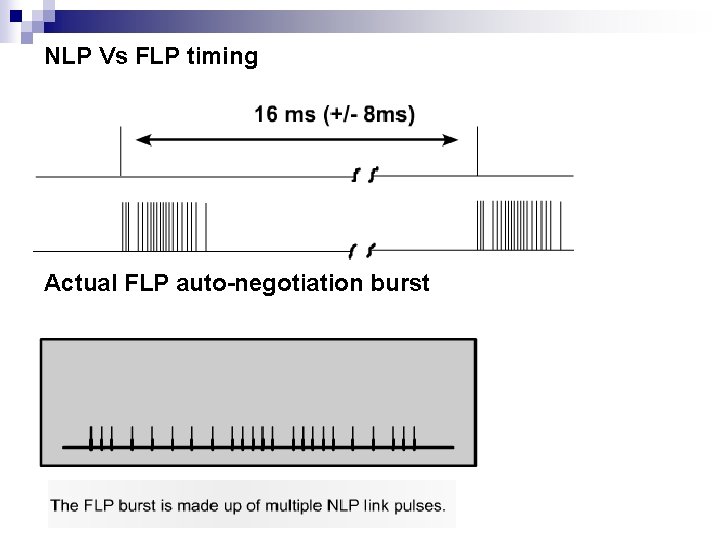
NLP Vs FLP timing Actual FLP auto-negotiation burst

Transmission priority rank

Summary of Today's lecture n What was looked at today ¨ Ethernet n n n technology How did it develop How and why it works Features of the Technology