Introduction to IOT and Firmware Reversing Who Am
















- Slides: 28

Introduction to IOT and Firmware Reversing

Who. Am. I • Security Consultant with Payatu Technologies • Experience in Web Pentesting, VAPT and Mobile Appsec (Android Only) and currently learning IOT. • Twitter Handle – nitmalviya 03

Topics to be covered • • Introduction to IOT Applications Protocols in IOT system Components Involved IOT security Firmware Extraction and Reversing Topics for future session Automated Framework

What is Io. T ? ? • The internet of things (Io. T) is the network of physical devices, vehicles, buildings and other items—embedded with electronics, software, sensors, actuators, and network connectivity that enable these objects to collect and exchange data(Wikipedia) • Internet of things increases the connectedness of people and things on a scale that once was unimaginable.

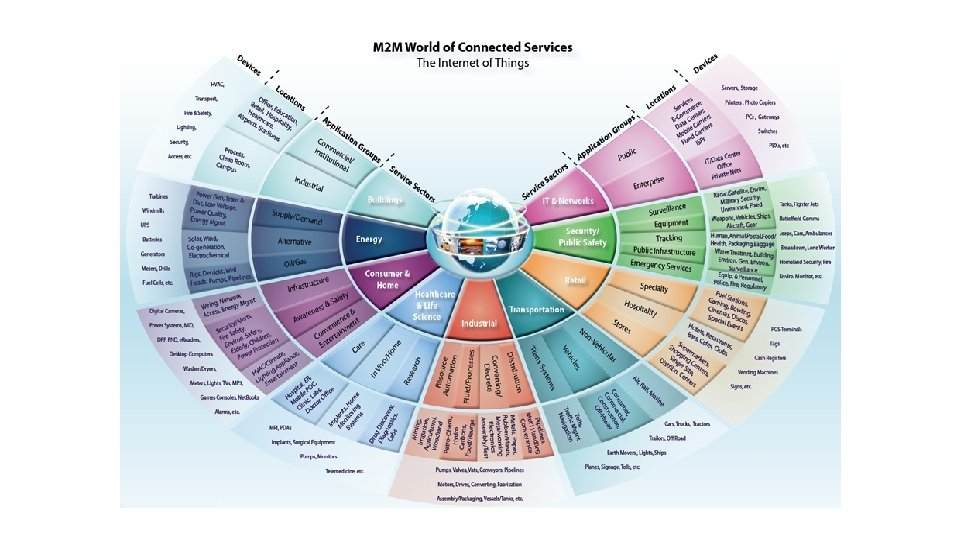
Devices like… • Networking devices(routers, firewalls, IDS) • Set-top boxes • Medical devices(Health monitors) • Mobile phones. • Home security systems • Vehicles, in-flight entertainment. • Thermostats, metering systems, consumer electronics Displays

Various Names, One Concept • M 2 M (Machine to Machine) • “Internet of Everything” (Cisco Systems) • “World Size Web” (Bruce Schneier) • “Skynet” (Terminator movie) Information Security Office of Budget and Finance Education – Partnership – Solutions

Where is Io. T? Information Security Office of Budget and Finance Education – Partnership – Solutions It’s everywhere!

Information Security Office of Budget and Finance Education – Partnership – Solutions

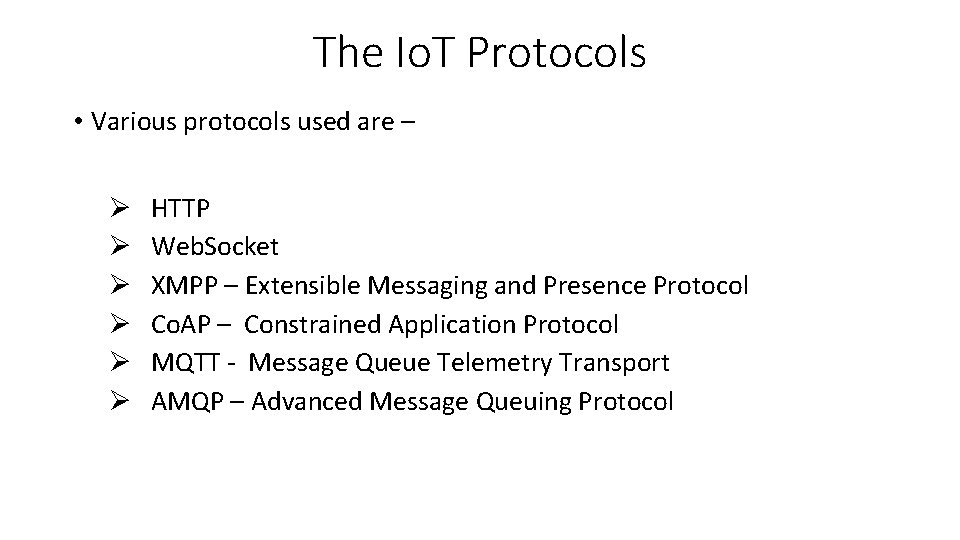
The Io. T Protocols • Various protocols used are – Ø HTTP Ø Web. Socket Ø XMPP – Extensible Messaging and Presence Protocol Ø Co. AP – Constrained Application Protocol Ø MQTT - Message Queue Telemetry Transport Ø AMQP – Advanced Message Queuing Protocol


Why be concerned about Io. T? • It’s just another computer, right? • All of the same issues we have with access control, vulnerability management, patching, monitoring, etc. • Imagine your network with 1, 000 more devices • Any compromised device is a foothold on the network

Attacking Io. T Devices Education – Partnership – Solutions • Default, weak, and hardcoded credentials • Difficult to update firmware and OS • Lack of vendor support for repairing vulnerabilities • Vulnerable web interfaces (SQL injection, XSS) • Coding errors (buffer overflow) • Clear text protocols and unnecessary open ports • Do. S / DDo. S • Physical theft and tampering

What we going to discuss Firmware Reversing

What is Firmware • Ascher Opler coined the term "firmware" in 1967. • Firmware is data that is stored on a computer or other hardware device's read-only memory that provides instruction on how that device should operate. • Unlike normal software, firmware cannot be changed or deleted by an without the aid of special programs and remains on that device whether or not it's on or off.

Firmware Extraction • Firmware Extraction - Process of extracting firmware from the embedded device • Method – Embedded Device Firmware Extraction via hardware Interfaces Hex File Conversion to Bin File Extraction NOTE - We will be learning bin file extraction and not hardware extraction part.


Tools of the trade • Binwalk (will be using this) • Firmwalk • Firmware Modification Kit • Firmdyne • ERESI Framework • FRAK – Firmware Reverse Analysis Konsole

What to do ? • Get the firmware • Reconnaisannce • Unpack • Localize point of interest • Pentest

Any vulnerable bin file for analysis/pentest ? ? • DVRF - Damn Vulnerable Router Firmware • Get it here - https: //github. com/praetorian-inc/DVRF • For our demo will use dlink firmware -DIR 412 A 1_FW 114 WWb 02. bin • Link - http: //www. filewatcher. com/m/DIR 412 A 1_FW 114 WWb 02. bin. 35349 83 -0. html

DEMO TIME

Any website for automated binary analysis ? ? • Upload your binary file here - http: //firmware. re/ • Many times it does not work. Thus, not much reliable.

What needs to be covered/learn…. • QEMU – Emulator for running binaries based on MIPS/ARM architecture. • Reversing binaries using IDA pro (Useful in login bypass and key extraction) • IOT components and its functionalities in depth. • IOT protocols

• OWASP IOT TOP 10 • Various file systems used in IOT devices. • Firmware extraction using Hardware Interfaces (UART, JTAG, I 2 C etc) • Firmware Reversing tools apart from binwalk. • Common Processor Architectures

• Types of memory in embedded devices. • Types of storage. • Common Operating systems used in embedded devices. • Various Bootloaders. • Common libraries. .

And last but not the least ……a final and small demo on….

Is there any automated Framework? ? • Like metasploit we have routersploit • Get it here - https: //github. com/reverse-shell/routersploit • Just run rsf. py and enjoy!!! • A very Small Demo

Thank You

References • http: //www. devttys 0. com/ • https: //www. coursera. org/ • http: //resources. infosecinstitute. com/