Introduction to Information Security Lecture 3 Block and

Introduction to Information Security Lecture 3: Block and Stream Ciphers 2009. 6. Prof. Kwangjo Kim
Contents 1. 2. 3. 4. 5. 6. 7. Feistel Network DES SEED AES Mode of operation Cryptanalysis – DC, LC Stream ciphers 2
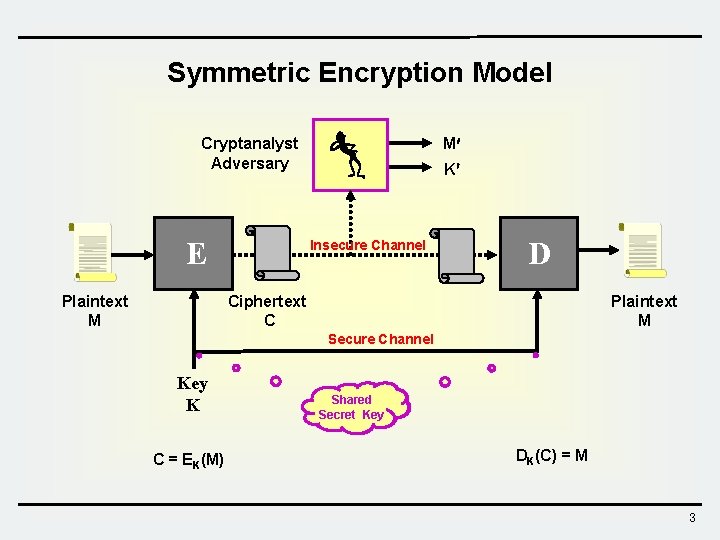
Symmetric Encryption Model M Cryptanalyst Adversary E Plaintext M K Insecure Channel D Ciphertext C Plaintext M Secure Channel Key K C = EK(M) Shared Secret Key DK(C) = M 3
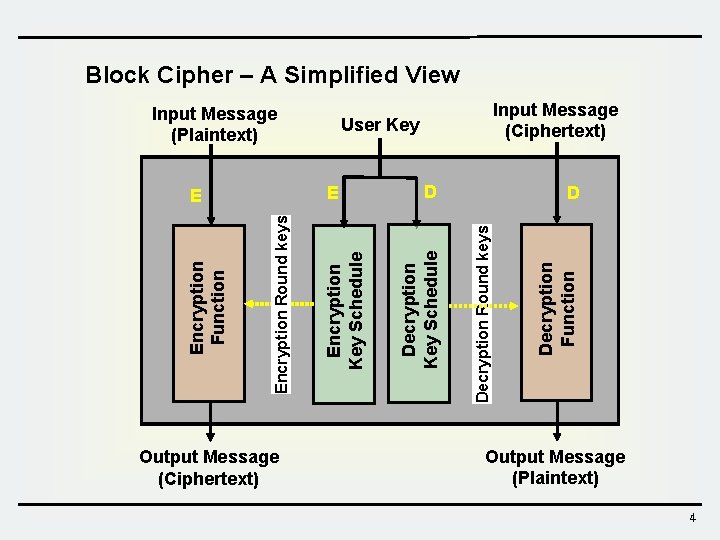
Block Cipher – A Simplified View Output Message (Ciphertext) D D Decryption Round keys Decryption Key Schedule Encryption Round keys Encryption Function User Key E E Input Message (Ciphertext) Decryption Function Input Message (Plaintext) Output Message (Plaintext) 4
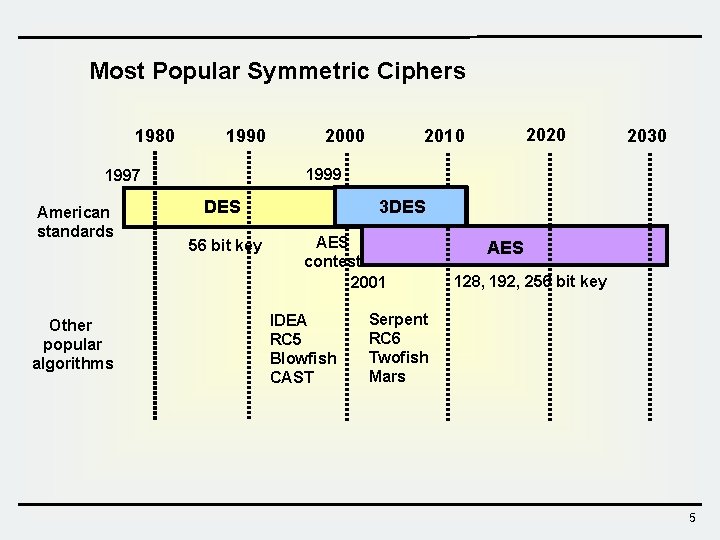
Most Popular Symmetric Ciphers 1980 1990 Other popular algorithms 2030 1999 1997 American standards 2020 2010 2000 DES 56 bit key 3 DES AES contest 2001 IDEA RC 5 Blowfish CAST AES 128, 192, 256 bit key Serpent RC 6 Twofish Mars 5
1. Feistel Network 6
Feistel-type Ciphers Ø Feistel network Ø An elegant variant of S-P networks that could be implemented using a single algorithm for both encryption and decryption Ø It is always a permutation regardless of the form of the F( ) function Ø F( ) does not need to be invertible Horst Feistel 7
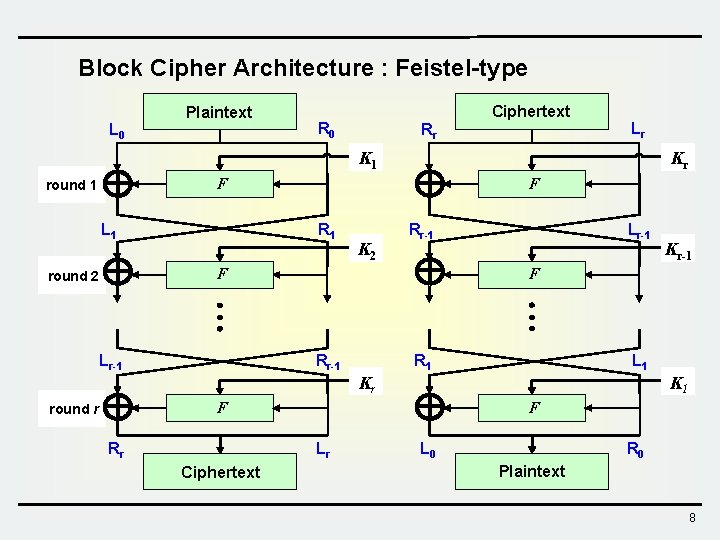
Block Cipher Architecture : Feistel-type L 0 round 1 Plaintext F R 1 K 2 F Lr-1 round r Rr K 1 L 1 round 2 R 0 Rr-1 F Rr Lr Ciphertext Kr F Rr-1 Lr-1 Kr-1 F R 1 Kr Lr L 1 K 1 F L 0 R 0 Plaintext 8
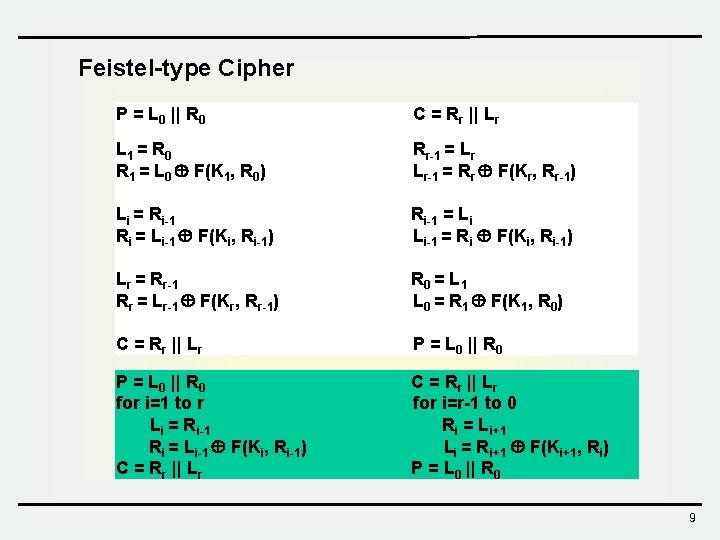
Feistel-type Cipher P = L 0 || R 0 C = Rr || Lr L 1 = R 0 R 1 = L 0 F(K 1, R 0) Rr-1 = Lr Lr-1 = Rr F(Kr, Rr-1) Li = Ri-1 Ri = Li-1 F(Ki, Ri-1) Ri-1 = Li Li-1 = Ri F(Ki, Ri-1) Lr = Rr-1 Rr = Lr-1 F(Kr, Rr-1) R 0 = L 1 L 0 = R 1 F(K 1, R 0) C = Rr || Lr P = L 0 || R 0 for i=1 to r Li = Ri-1 Ri = Li-1 F(Ki, Ri-1) C = Rr || Lr for i=r-1 to 0 Ri = Li+1 Li = Ri+1 F(Ki+1, Ri) P = L 0 || R 0 9
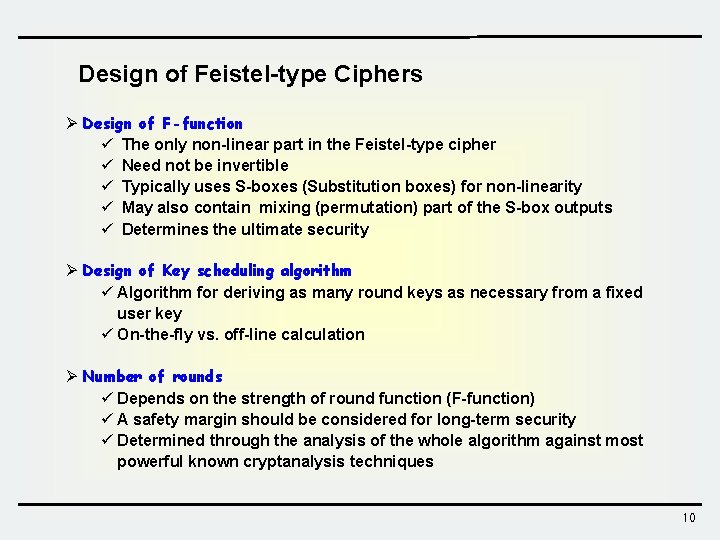
Design of Feistel-type Ciphers Ø Design of F-function ü The only non-linear part in the Feistel-type cipher ü Need not be invertible ü Typically uses S-boxes (Substitution boxes) for non-linearity ü May also contain mixing (permutation) part of the S-box outputs ü Determines the ultimate security Ø Design of Key scheduling algorithm ü Algorithm for deriving as many round keys as necessary from a fixed user key ü On-the-fly vs. off-line calculation Ø Number of rounds ü Depends on the strength of round function (F-function) ü A safety margin should be considered for long-term security ü Determined through the analysis of the whole algorithm against most powerful known cryptanalysis techniques 10
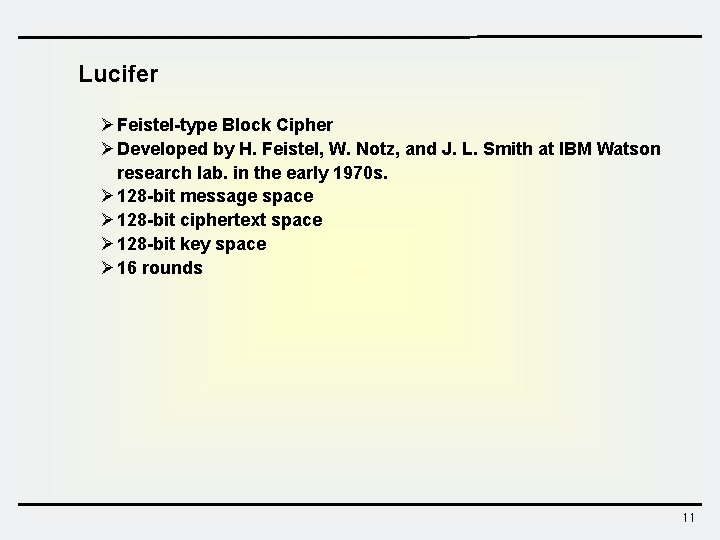
Lucifer Ø Feistel-type Block Cipher Ø Developed by H. Feistel, W. Notz, and J. L. Smith at IBM Watson research lab. in the early 1970 s. Ø 128 -bit message space Ø 128 -bit ciphertext space Ø 128 -bit key space Ø 16 rounds 11

2. Data Encryption Standard 12
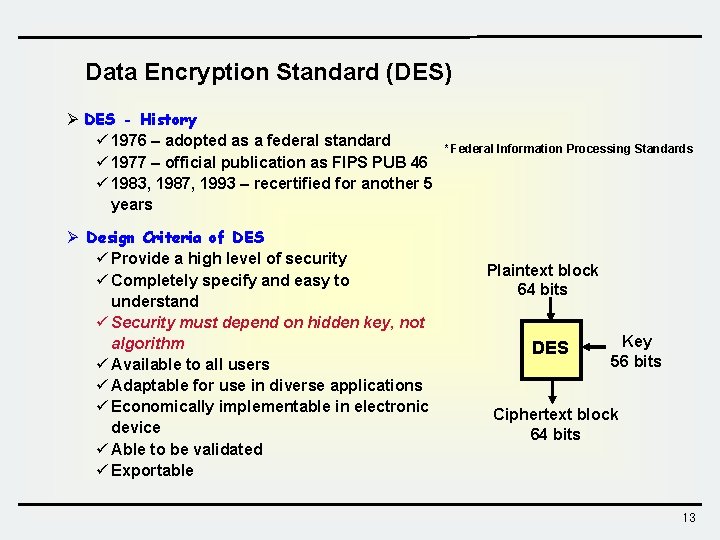
Data Encryption Standard (DES) Ø DES - History ü 1976 – adopted as a federal standard ü 1977 – official publication as FIPS PUB 46 ü 1983, 1987, 1993 – recertified for another 5 years Ø Design Criteria of DES ü Provide a high level of security ü Completely specify and easy to understand ü Security must depend on hidden key, not algorithm ü Available to all users ü Adaptable for use in diverse applications ü Economically implementable in electronic device ü Able to be validated ü Exportable * Federal Information Processing Standards Plaintext block 64 bits DES Key 56 bits Ciphertext block 64 bits 13
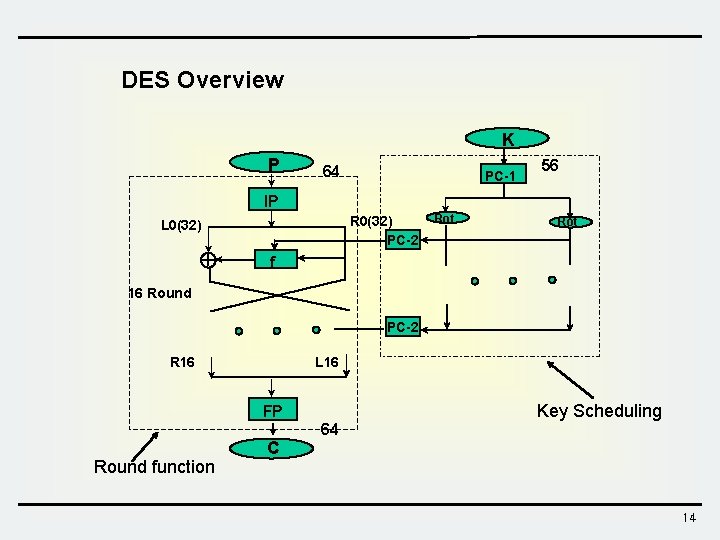
DES Overview K P 64 PC-1 56 IP R 0(32) PC-2 L 0(32) Rot f 16 Round PC-2 R 16 L 16 FP 64 Round function Key Scheduling C 14
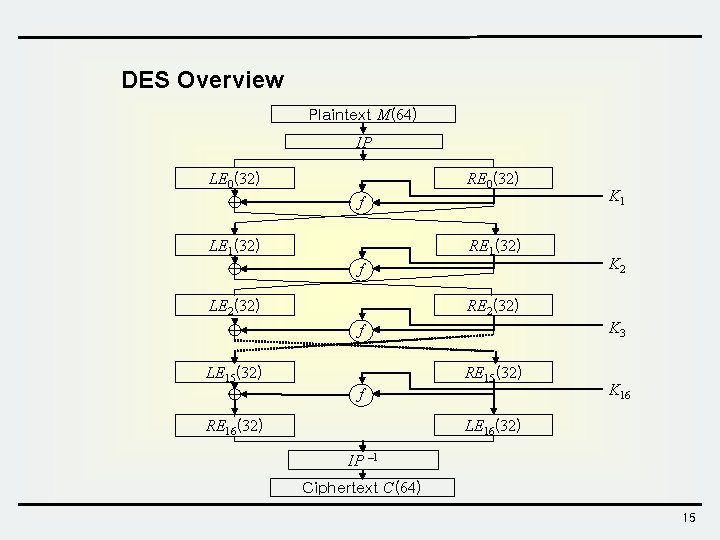
DES Overview Plaintext M(64) IP LE 0(32) RE 0(32) f LE 1(32) RE 1(32) f LE 2(32) K 1 K 2 RE 2(32) K 3 f LE 15(32) RE 15(32) f K 16 LE 16(32) RE 16(32) IP – 1 Ciphertext C(64) 15
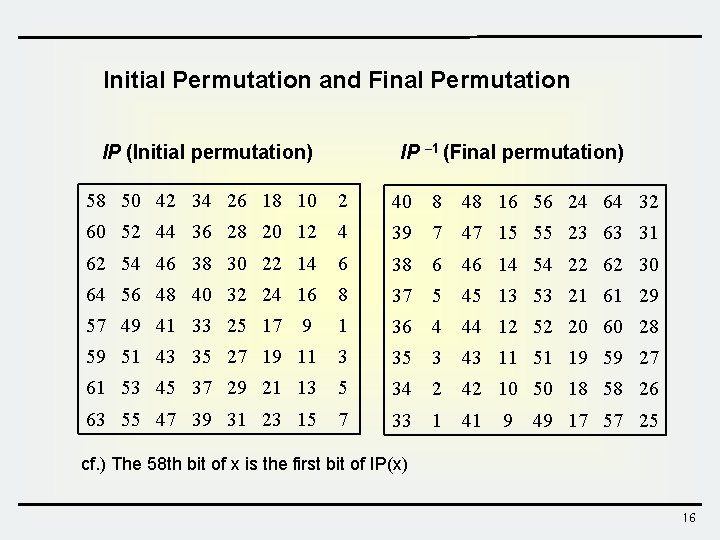
Initial Permutation and Final Permutation IP – 1 (Final permutation) IP (Initial permutation) 58 50 42 34 26 18 10 2 40 8 48 16 56 24 64 32 60 52 44 36 28 20 12 4 39 7 47 15 55 23 63 31 62 54 46 38 30 22 14 6 38 6 46 14 54 22 62 30 64 56 48 40 32 24 16 8 37 5 45 13 53 21 61 29 57 49 41 33 25 17 9 1 36 4 44 12 52 20 60 28 59 51 43 35 27 19 11 3 35 3 43 11 51 19 59 27 61 53 45 37 29 21 13 5 34 2 42 10 50 18 58 26 63 55 47 39 31 23 15 7 33 1 41 9 49 17 57 25 cf. ) The 58 th bit of x is the first bit of IP(x) 16
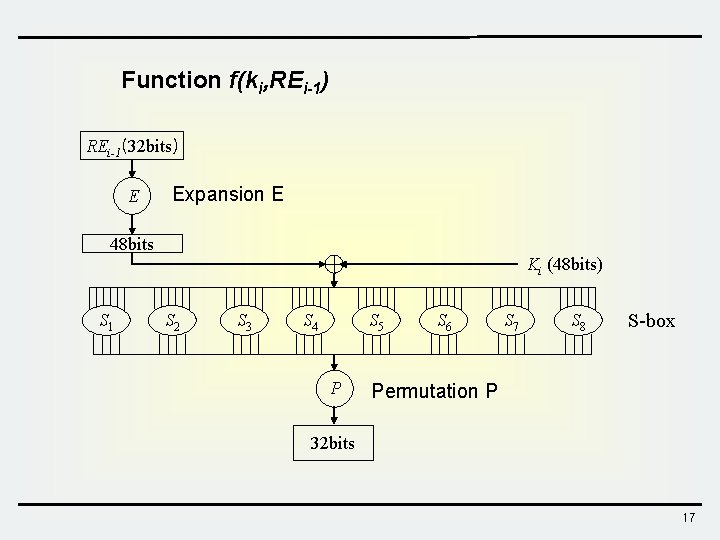
Function f(ki, REi-1) REi-1(32 bits) E Expansion E 48 bits Ki (48 bits) S 1 S 2 S 3 S 4 S 5 P S 6 S 7 S 8 S-box Permutation P 32 bits 17
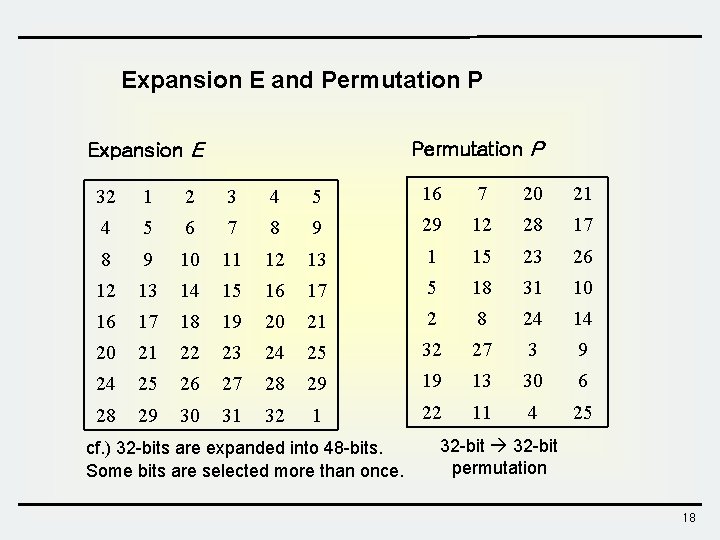
Expansion E and Permutation P Expansion E 32 1 2 3 4 5 16 7 20 21 4 5 6 7 8 9 29 12 28 17 8 9 10 11 12 13 1 15 23 26 12 13 14 15 16 17 5 18 31 10 16 17 18 19 20 21 2 8 24 14 20 21 22 23 24 25 32 27 3 9 24 25 26 27 28 29 19 13 30 6 28 29 30 31 32 1 22 11 4 25 cf. ) 32 -bits are expanded into 48 -bits. Some bits are selected more than once. 32 -bit permutation 18
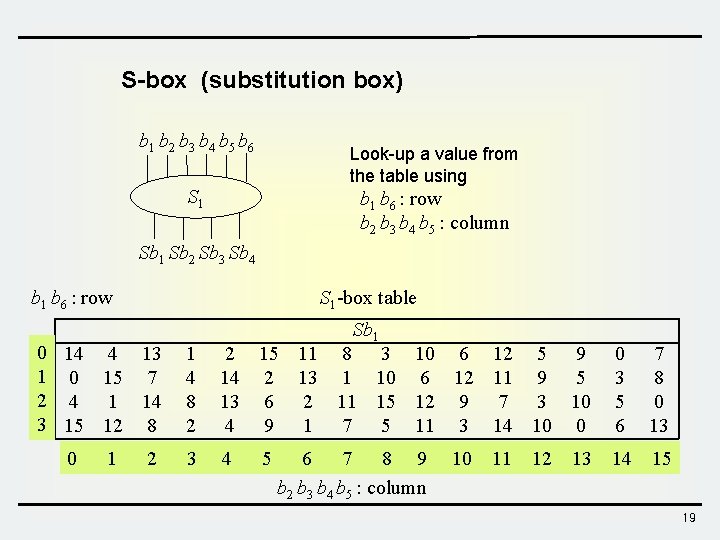
S-box (substitution box) b 1 b 2 b 3 b 4 b 5 b 6 Look-up a value from the table using S 1 b 6 : row b 2 b 3 b 4 b 5 : column Sb 1 Sb 2 Sb 3 Sb 4 S 1 -box table b 1 b 6 : row 0 14 4 13 1 0 15 7 2 4 1 14 3 15 12 8 0 1 2 Sb 1 1 4 8 2 2 15 11 8 3 10 6 12 5 9 14 2 13 1 10 6 12 11 9 5 13 6 2 11 15 12 9 7 3 10 4 9 1 7 5 11 3 14 10 0 0 3 5 6 7 8 0 13 3 4 14 15 5 6 7 8 9 b 2 b 3 b 4 b 5 : column 10 11 12 13 19
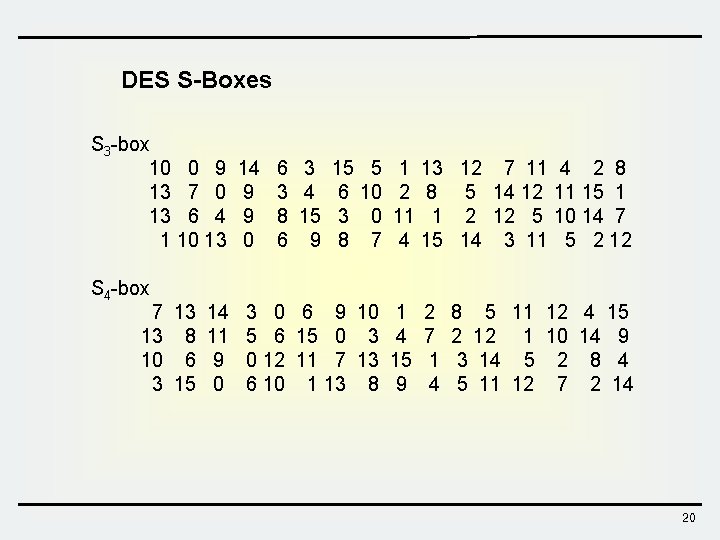
DES S-Boxes S 3 -box 10 0 9 13 7 0 13 6 4 1 10 13 S 4 -box 14 9 9 0 6 3 3 4 8 15 6 9 15 5 6 10 3 0 8 7 1 13 12 7 11 4 2 8 5 14 12 11 15 1 11 1 2 12 5 10 14 7 4 15 14 3 11 5 2 12 7 13 14 3 0 6 9 10 1 13 8 11 5 6 15 0 3 4 10 6 9 0 12 11 7 13 15 0 6 10 1 13 8 9 2 7 1 4 8 5 11 12 4 15 2 12 1 10 14 9 3 14 5 2 8 4 5 11 12 7 2 14 20
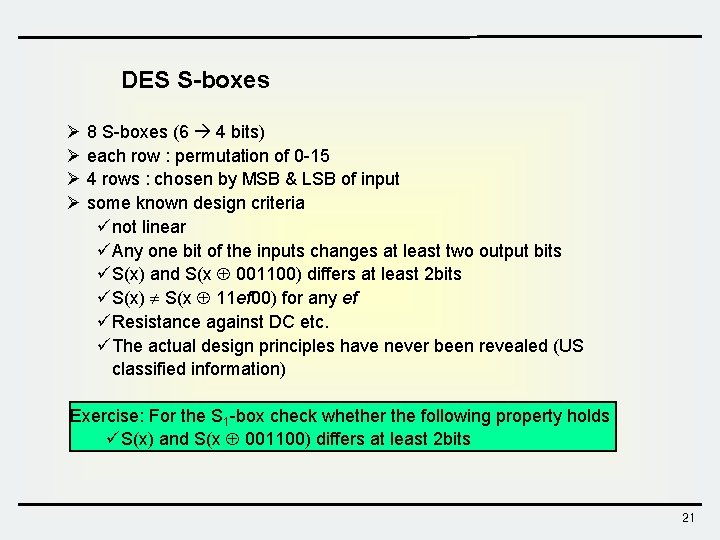
DES S-boxes Ø 8 S-boxes (6 4 bits) Ø each row : permutation of 0 -15 Ø 4 rows : chosen by MSB & LSB of input Ø some known design criteria ü not linear ü Any one bit of the inputs changes at least two output bits ü S(x) and S(x 001100) differs at least 2 bits ü S(x) S(x 11 ef 00) for any ef ü Resistance against DC etc. ü The actual design principles have never been revealed (US classified information) Exercise: For the S 1 -box check whether the following property holds üS(x) and S(x 001100) differs at least 2 bits 21
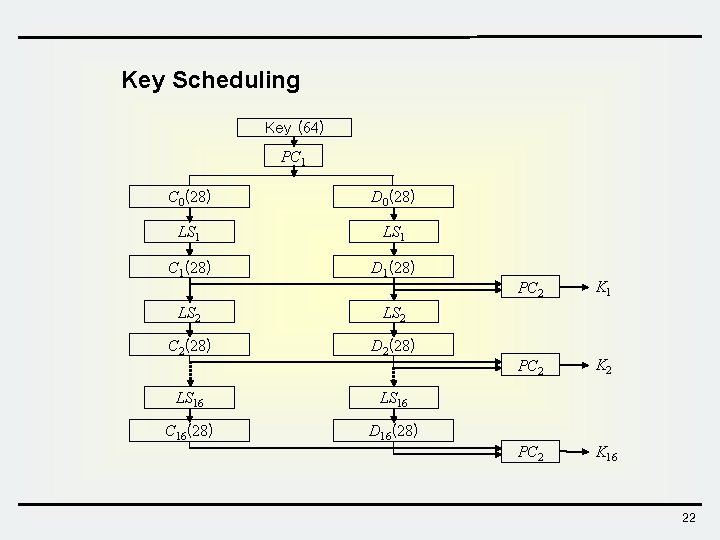
Key Scheduling Key (64) PC 1 C 0(28) D 0(28) LS 1 C 1(28) D 1(28) LS 2 C 2(28) D 2(28) LS 16 C 16(28) D 16(28) PC 2 K 1 PC 2 K 2 PC 2 K 16 22
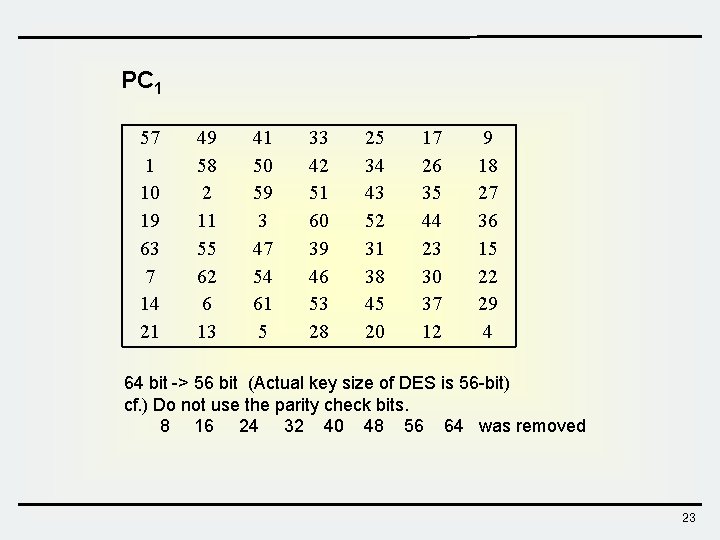
PC 1 57 1 10 19 63 7 14 21 49 58 2 11 55 62 6 13 41 50 59 3 47 54 61 5 33 42 51 60 39 46 53 28 25 34 43 52 31 38 45 20 17 26 35 44 23 30 37 12 9 18 27 36 15 22 29 4 64 bit -> 56 bit (Actual key size of DES is 56 -bit) cf. ) Do not use the parity check bits. 8 16 24 32 40 48 56 64 was removed 23
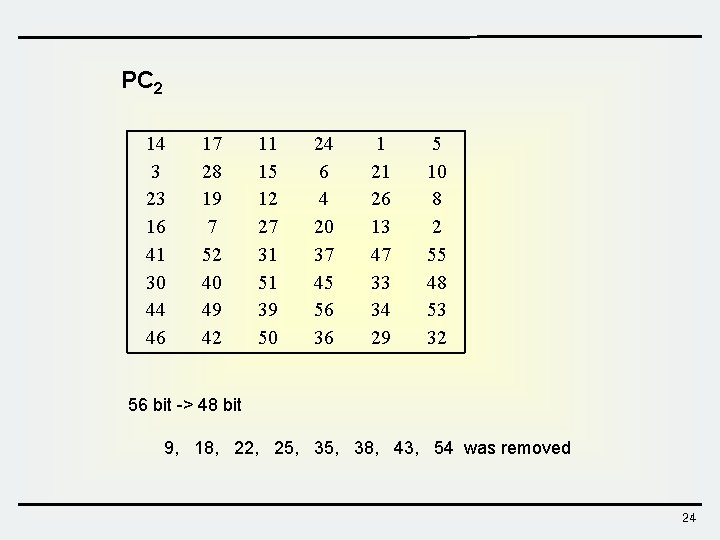
PC 2 14 3 23 16 41 30 44 46 17 28 19 7 52 40 49 42 11 15 12 27 31 51 39 50 24 6 4 20 37 45 56 36 1 21 26 13 47 33 34 29 5 10 8 2 55 48 53 32 56 bit -> 48 bit 9, 18, 22, 25, 38, 43, 54 was removed 24
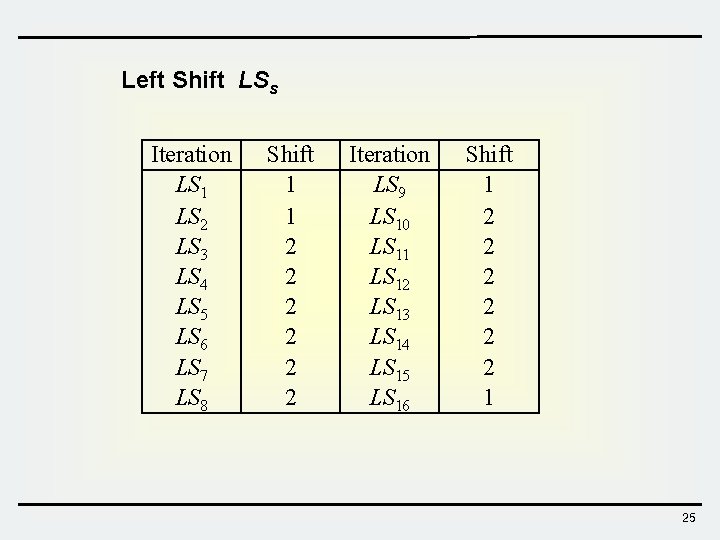
Left Shift LSs Iteration LS 1 LS 2 LS 3 LS 4 LS 5 LS 6 LS 7 LS 8 Shift 1 1 2 2 2 Iteration LS 9 LS 10 LS 11 LS 12 LS 13 LS 14 LS 15 LS 16 Shift 1 2 2 2 1 25
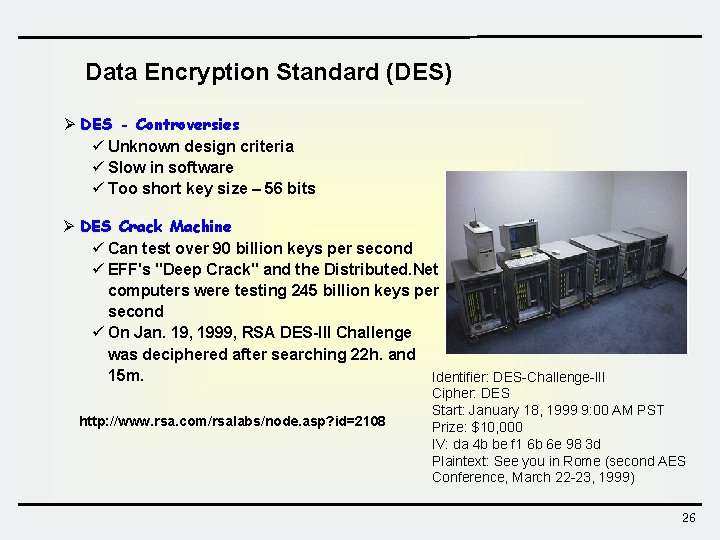
Data Encryption Standard (DES) Ø DES - Controversies ü Unknown design criteria ü Slow in software ü Too short key size – 56 bits Ø DES Crack Machine ü Can test over 90 billion keys per second ü EFF's "Deep Crack" and the Distributed. Net computers were testing 245 billion keys per second ü On Jan. 19, 1999, RSA DES-III Challenge was deciphered after searching 22 h. and 15 m. Identifier: DES-Challenge-III http: //www. rsa. com/rsalabs/node. asp? id=2108 Cipher: DES Start: January 18, 1999 9: 00 AM PST Prize: $10, 000 IV: da 4 b be f 1 6 b 6 e 98 3 d Plaintext: See you in Rome (second AES Conference, March 22 -23, 1999) 26
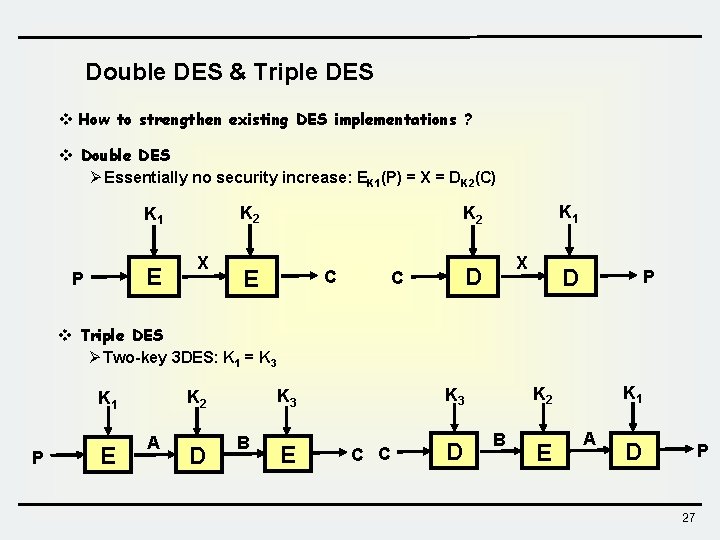
Double DES & Triple DES v How to strengthen existing DES implementations ? v Double DES Ø Essentially no security increase: EK 1(P) = X = DK 2(C) K 2 K 1 E P X K 1 K 2 E C X D C D P v Triple DES Ø Two-key 3 DES: K 1 = K 3 P E A D B E C C D K 1 K 2 K 3 K 2 K 1 B E A D P 27
3. SEED Korean standard encryption algorithm http: //www. cyberprivacy. or. kr/kisa/seed/data/Document_pdf/SEED_Specification_english. pdf 28
SEED Algorithm Features ØFeistel structure with 16 rounds Ø 128 -bits input-output data block size Ø 128 -bits key size ØTwo 8 x 8 S-Boxes ØMixed operation of XOR and modular addition 29
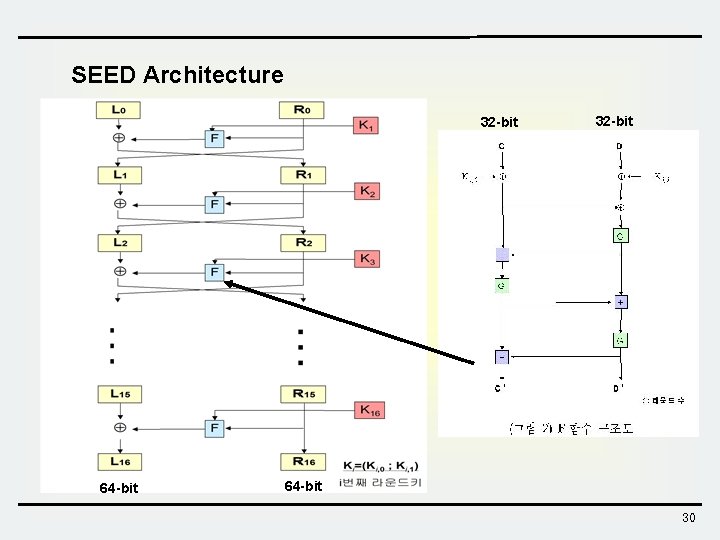
SEED Architecture 32 -bit 64 -bit 30
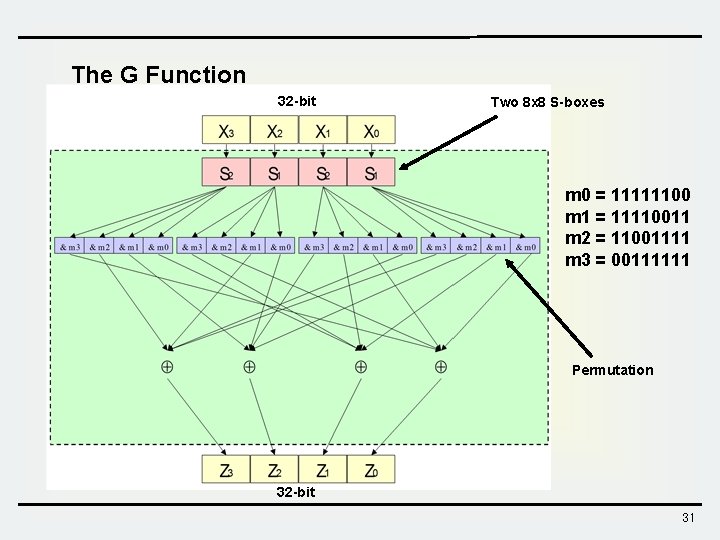
The G Function 32 -bit Two 8 x 8 S-boxes m 0 = 11111100 m 1 = 11110011 m 2 = 11001111 m 3 = 00111111 Permutation 32 -bit 31
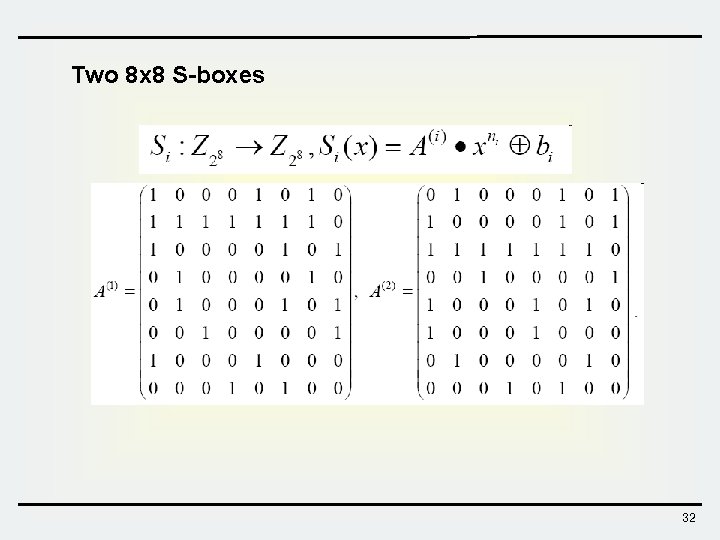
Two 8 x 8 S-boxes 32
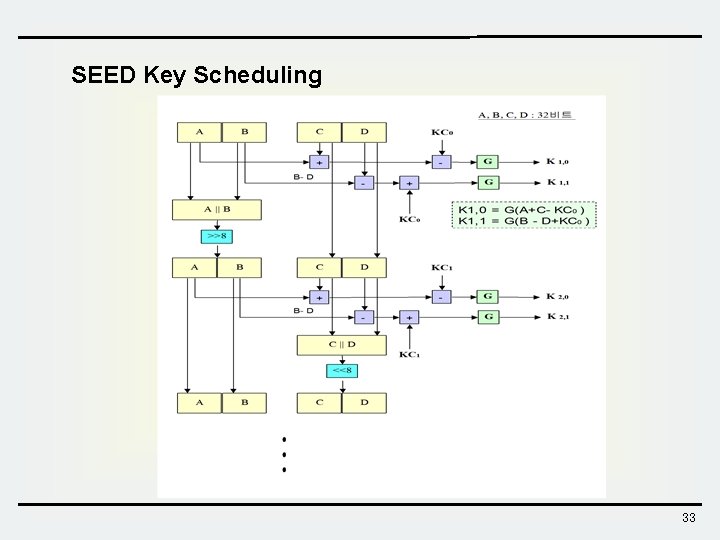
SEED Key Scheduling 33

4. Advanced Encryption Standard http: //csrc. nist. gov/Crypto. Toolkit/aes/rijndael/ 34

AES Contest q AES Contest Calendar Ø 1997 : Call For AES Candidate Algorithms by NIST Ø 1998 : 1 st Round Candidates – 15 Algorithms § Mars, Twofish, RC 6, SAFER+, HPC, CAST 256, DEAL, Frog, Magenta, Rijndael, DFC, Serpent, Crypton, E 2, LOKI 97 Ø 1999 : 2 nd Round Candidates – 5 Algorithms § MARS, RC 6, Rijndael, Serpent, and Twofish Ø 2000. 10 : Rijndael selected as the finalist Ø 2001. 12: official publication as FIPS PUB 197 * National Institute of Standards and Technology 35
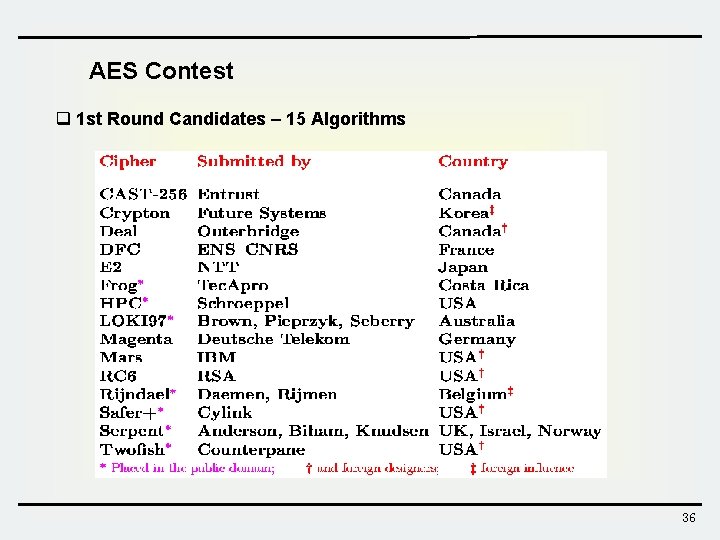
AES Contest q 1 st Round Candidates – 15 Algorithms 36
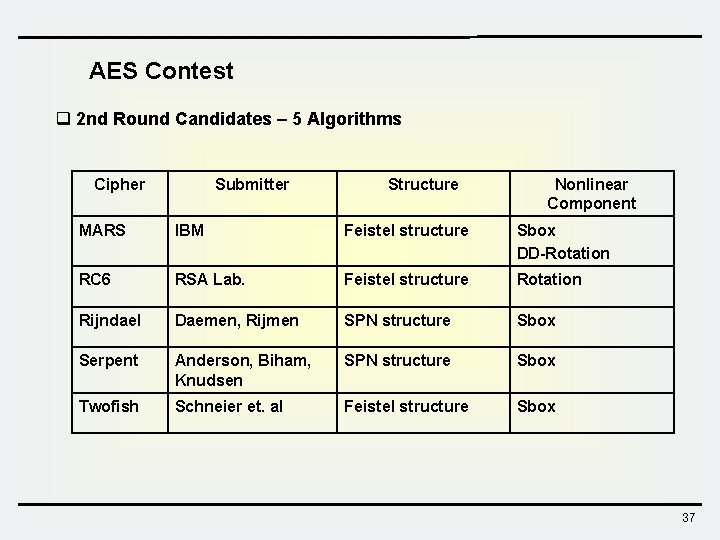
AES Contest q 2 nd Round Candidates – 5 Algorithms Cipher Submitter Structure Nonlinear Component MARS IBM Feistel structure Sbox DD-Rotation RC 6 RSA Lab. Feistel structure Rotation Rijndael Daemen, Rijmen SPN structure Sbox Serpent Anderson, Biham, Knudsen SPN structure Sbox Twofish Schneier et. al Feistel structure Sbox 37

AES Contest q AES Contest Ø 2000. 10 : Rijndael selected as the finalist Ø 2001. 12: official publication as FIPS PUB 197 Joan Daemen and Vincent Rijmen, “ The Design of Rijndael, AES – The Advanced Encryption Standard”, Springer, 2002, ISBN 3 -540 -42580 -2 Vincent Rijmen 38
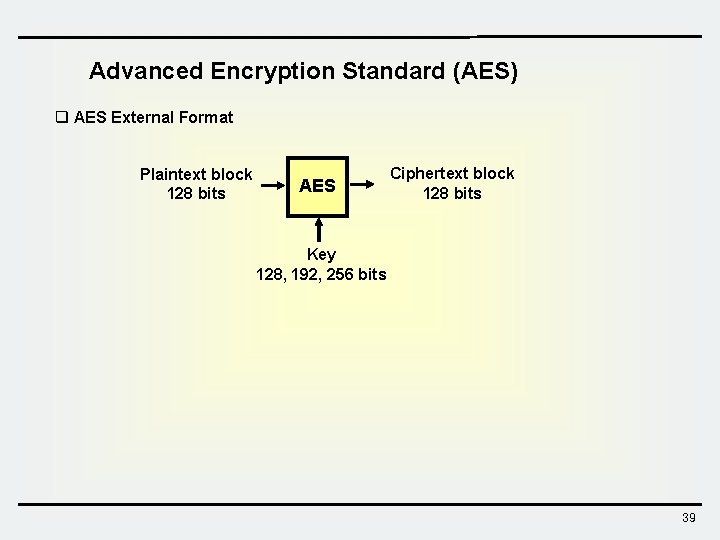
Advanced Encryption Standard (AES) q AES External Format Plaintext block 128 bits AES Ciphertext block 128 bits Key 128, 192, 256 bits 39
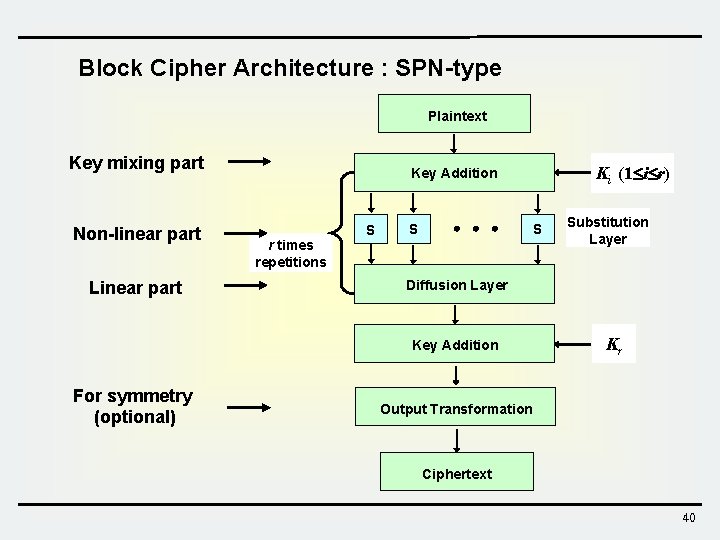
Block Cipher Architecture : SPN-type Plaintext Key mixing part Non-linear part Linear part r times repetitions S Substitution Layer Diffusion Layer Key Addition For symmetry (optional) Ki (1 i r) Key Addition Kr Output Transformation Ciphertext 40
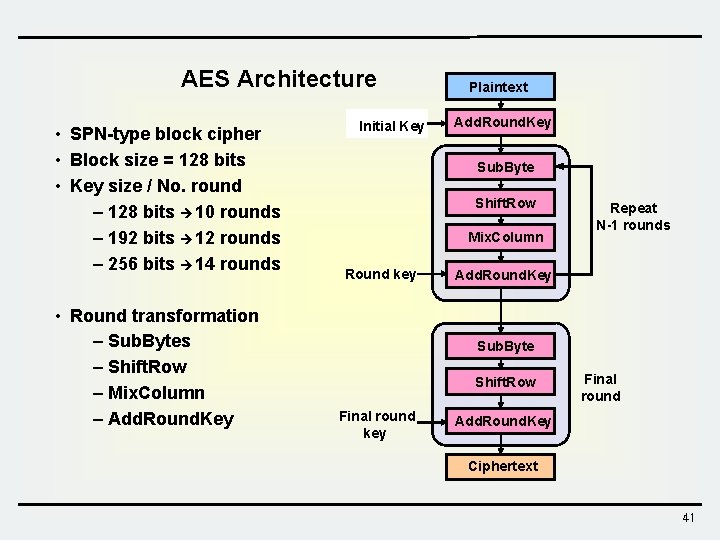
AES Architecture • SPN-type block cipher • Block size = 128 bits • Key size / No. round – 128 bits 10 rounds – 192 bits 12 rounds – 256 bits 14 rounds • Round transformation – Sub. Bytes – Shift. Row – Mix. Column – Add. Round. Key Initial Key Plaintext Add. Round. Key Sub. Byte Shift. Row Mix. Column Round key Repeat N-1 rounds Add. Round. Key Sub. Byte Shift. Row Final round key Final round Add. Round. Key Ciphertext 41
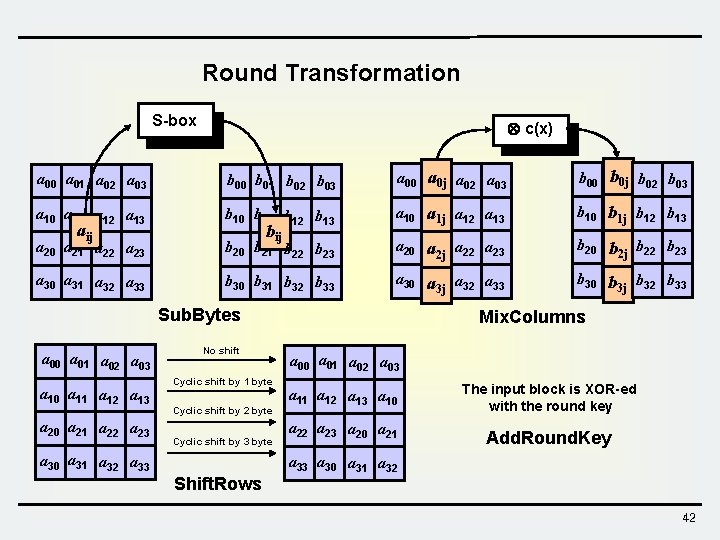
Round Transformation S-box c(x) a 00 a 01 a 02 a 03 b 00 b 01 b 02 b 03 a 00 a 0 j a 02 a 03 b 00 b 0 j b 02 b 03 a 10 a 11 a 12 a 13 b 10 b 11 b 12 b 13 a 10 a 1 j a 12 a 13 b 10 b 1 j b 12 b 13 a 20 a 21 a 22 a 23 b 20 b 21 b 22 b 23 a 20 a a 22 a 23 2 j b 20 b b 22 b 23 2 j a 30 a 31 a 32 a 33 b 30 b 31 b 32 b 33 a 30 a a 32 a 33 3 j b 30 b b 32 b 33 3 j aij bij Sub. Bytes a 00 a 01 a 02 a 03 a 10 a 11 a 12 a 13 a 20 a 21 a 22 a 23 No shift Cyclic shift by 1 byte Cyclic shift by 2 byte Cyclic shift by 3 byte a 30 a 31 a 32 a 33 Shift. Rows Mix. Columns a 00 a 01 a 02 a 03 a 11 a 12 a 13 a 10 a 22 a 23 a 20 a 21 The input block is XOR-ed with the round key Add. Round. Key a 33 a 30 a 31 a 32 42
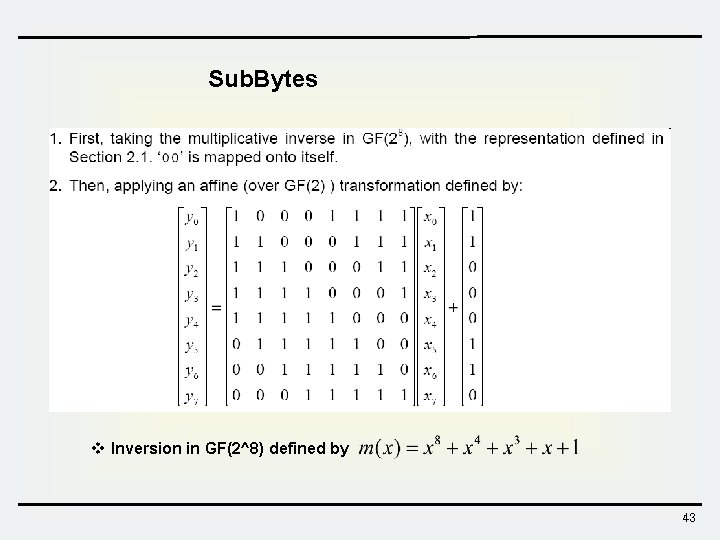
Sub. Bytes v Inversion in GF(2^8) defined by 43
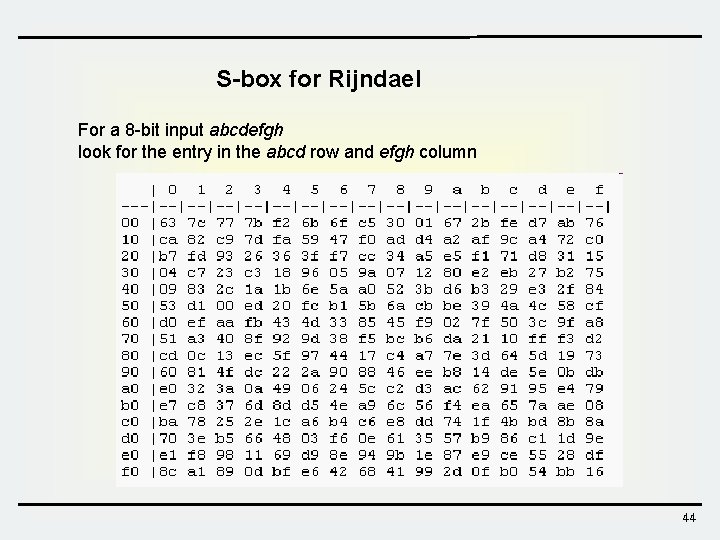
S-box for Rijndael For a 8 -bit input abcdefgh look for the entry in the abcd row and efgh column 44
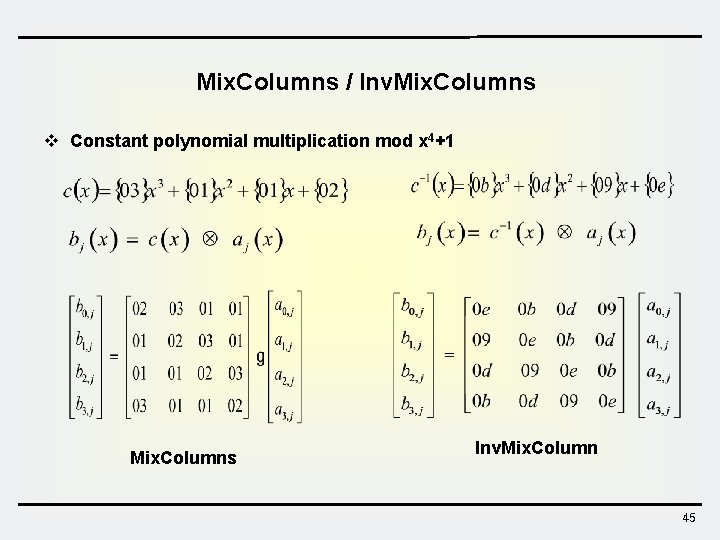
Mix. Columns / Inv. Mix. Columns v Constant polynomial multiplication mod x 4+1 Mix. Columns Inv. Mix. Column 45
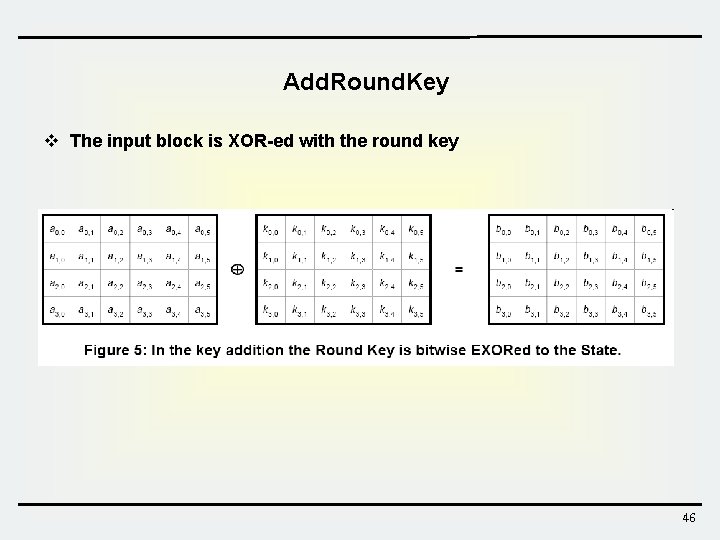
Add. Round. Key v The input block is XOR-ed with the round key 46
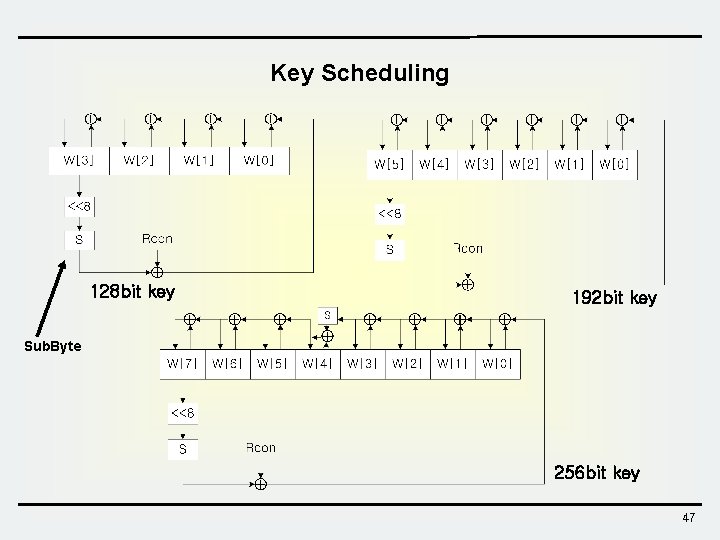
Key Scheduling 128 bit key 192 bit key Sub. Byte 256 bit key 47
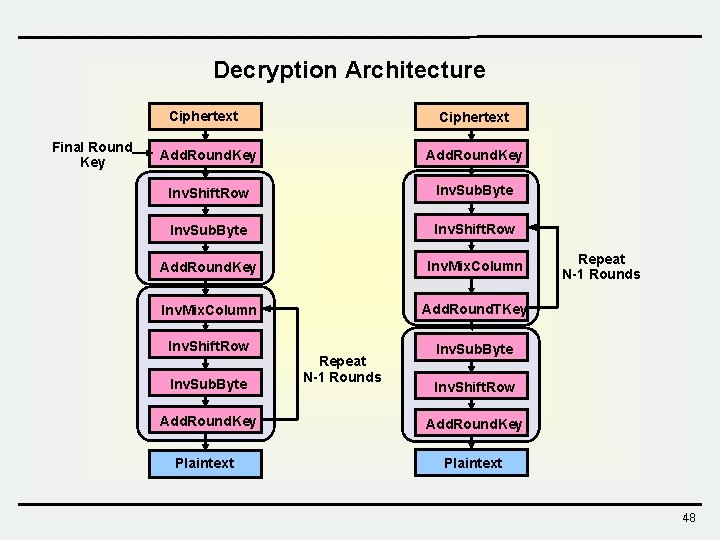
Decryption Architecture Ciphertext Final Round Key Ciphertext Add. Round. Key Inv. Shift. Row Inv. Sub. Byte Inv. Shift. Row Add. Round. Key Inv. Mix. Column Add. Round. TKey Inv. Shift. Row Inv. Sub. Byte Add. Round. Key Plaintext Repeat N-1 Rounds Inv. Sub. Byte Inv. Shift. Row Add. Round. Key Plaintext 48
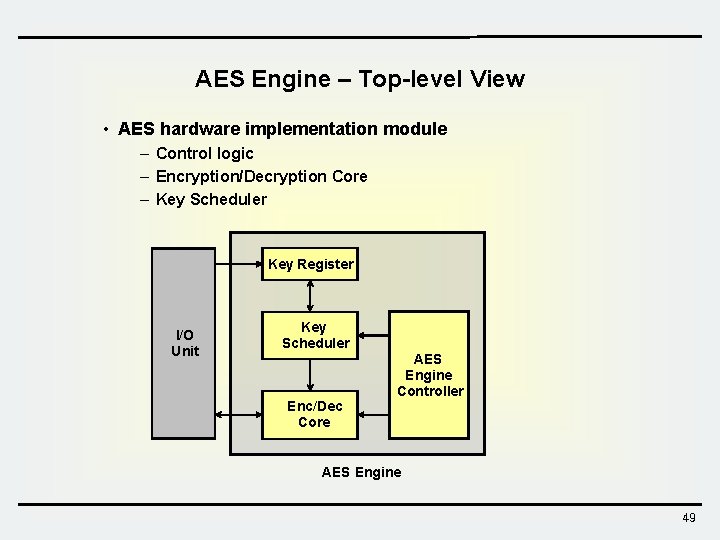
AES Engine – Top-level View • AES hardware implementation module – Control logic – Encryption/Decryption Core – Key Scheduler Key Register I/O Unit Key Scheduler Enc/Dec Core AES Engine Controller AES Engine 49
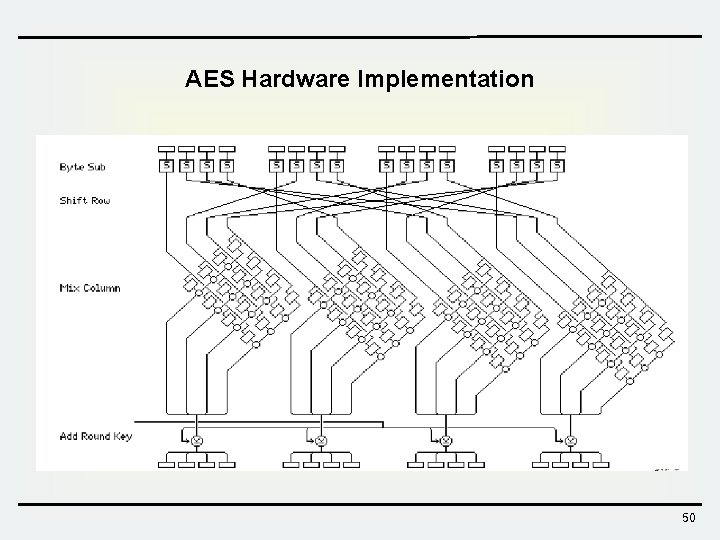
AES Hardware Implementation 50
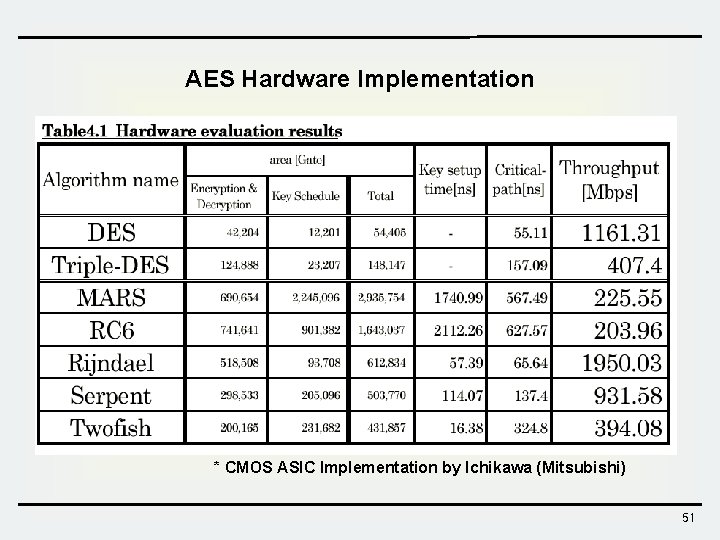
AES Hardware Implementation * CMOS ASIC Implementation by Ichikawa (Mitsubishi) 51
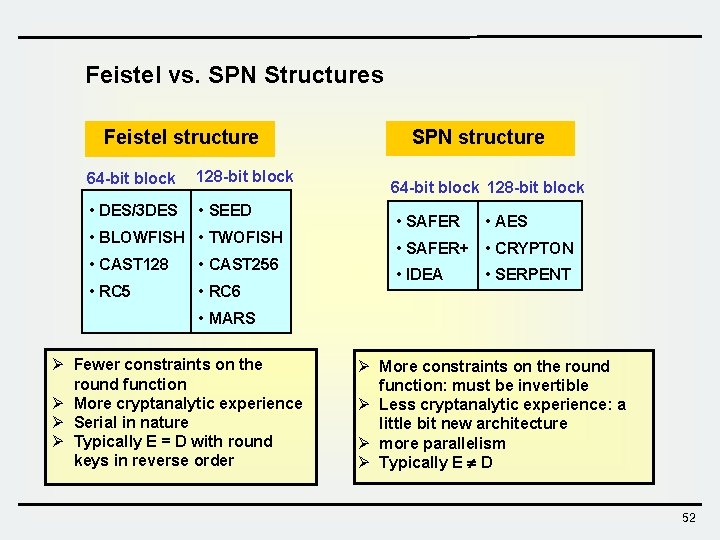
Feistel vs. SPN Structures Feistel structure 64 -bit block 128 -bit block • DES/3 DES • SEED • BLOWFISH • TWOFISH • CAST 128 • CAST 256 • RC 5 • RC 6 SPN structure 64 -bit block 128 -bit block • SAFER • AES • SAFER+ • CRYPTON • IDEA • SERPENT • MARS Ø Fewer constraints on the round function Ø More cryptanalytic experience Ø Serial in nature Ø Typically E = D with round keys in reverse order Ø More constraints on the round function: must be invertible Ø Less cryptanalytic experience: a little bit new architecture Ø more parallelism Ø Typically E D 52
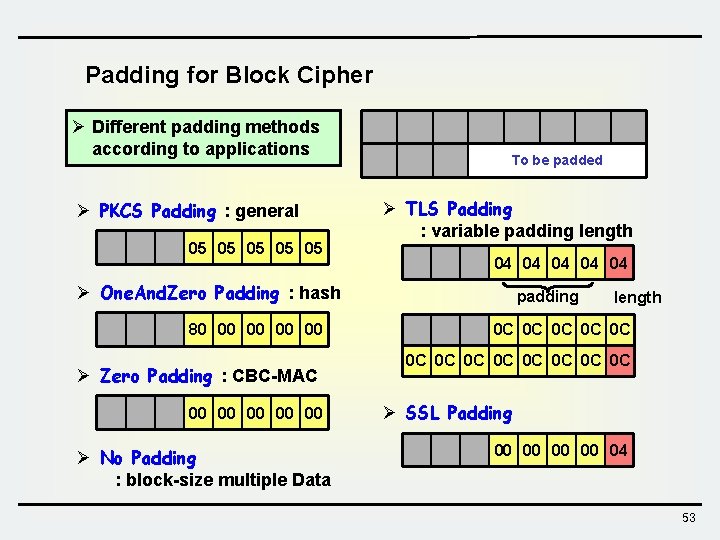
Padding for Block Cipher Ø Different padding methods according to applications Ø PKCS Padding : general 05 05 05 To be padded Ø TLS Padding : variable padding length 04 04 04 Ø One. And. Zero Padding : hash 80 00 00 Ø Zero Padding : CBC-MAC 00 00 00 Ø No Padding : block-size multiple Data padding length 0 C 0 C 0 C 0 C Ø SSL Padding 00 00 04 53
5. Mode of Operation 54
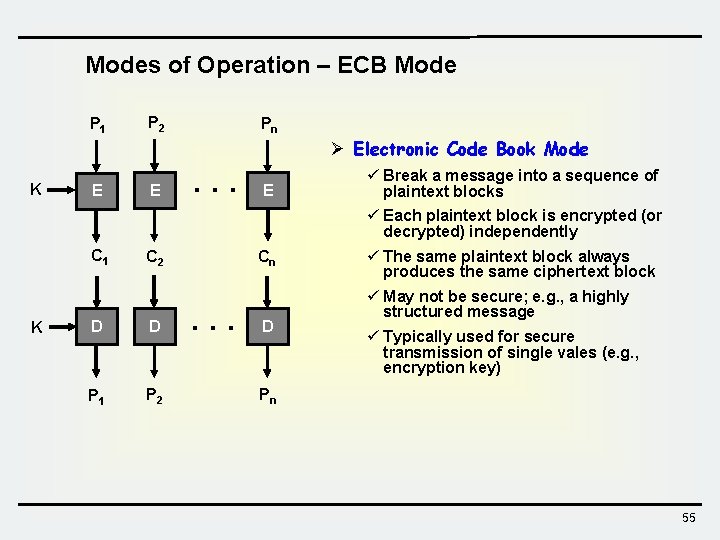
Modes of Operation – ECB Mode P 1 K E P 2 E Pn . . . E Ø Electronic Code Book Mode ü Break a message into a sequence of plaintext blocks ü Each plaintext block is encrypted (or decrypted) independently C 1 K Cn C 2 D D P 1 P 2 . . . D ü The same plaintext block always produces the same ciphertext block ü May not be secure; e. g. , a highly structured message ü Typically used for secure transmission of single vales (e. g. , encryption key) Pn 55
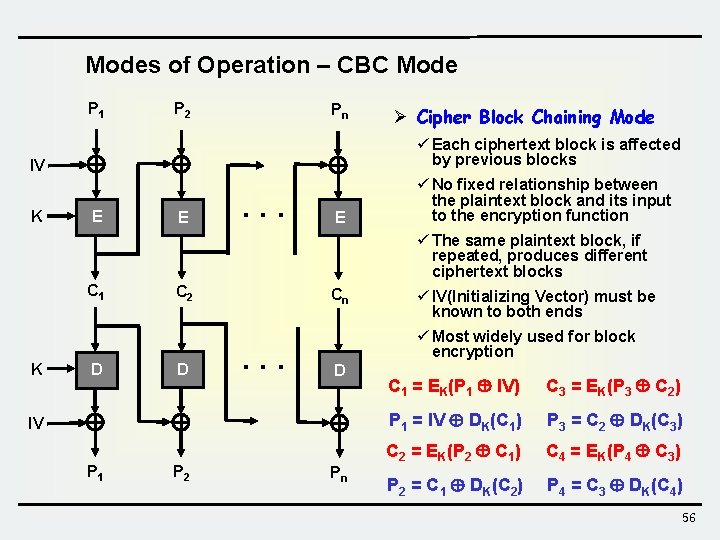
Modes of Operation – CBC Mode P 1 P 2 Pn Ø Cipher Block Chaining Mode IV ü Each ciphertext block is affected by previous blocks K ü No fixed relationship between the plaintext block and its input to the encryption function E E . . . E ü The same plaintext block, if repeated, produces different ciphertext blocks C 1 K D C 2 D Cn . . . ü Most widely used for block encryption D IV P 1 P 2 ü IV(Initializing Vector) must be known to both ends Pn C 1 = EK(P 1 IV) C 3 = EK(P 3 C 2) P 1 = IV DK(C 1) P 3 = C 2 DK(C 3) C 2 = EK(P 2 C 1) C 4 = EK(P 4 C 3) P 2 = C 1 DK(C 2) P 4 = C 3 DK(C 4) 56
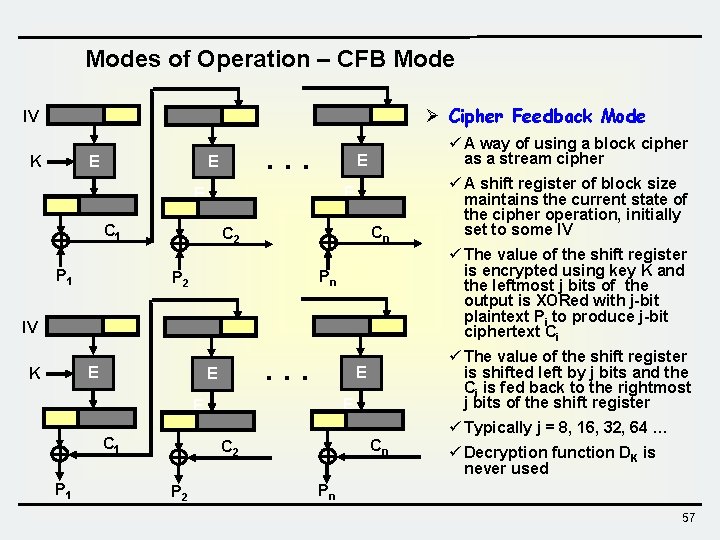
Modes of Operation – CFB Mode Ø Cipher Feedback Mode IV E K . . . E E C 1 P 1 ü A way of using a block cipher as a stream cipher Cn C 2 ü The value of the shift register is encrypted using key K and the leftmost j bits of the output is XORed with j-bit plaintext Pi to produce j-bit ciphertext Ci Pn P 2 IV E K . . . E E ü Typically j = 8, 16, 32, 64 … C 1 P 1 ü The value of the shift register is shifted left by j bits and the Ci is fed back to the rightmost j bits of the shift register E E ü A shift register of block size maintains the current state of the cipher operation, initially set to some IV Cn C 2 P 2 ü Decryption function DK is never used Pn 57
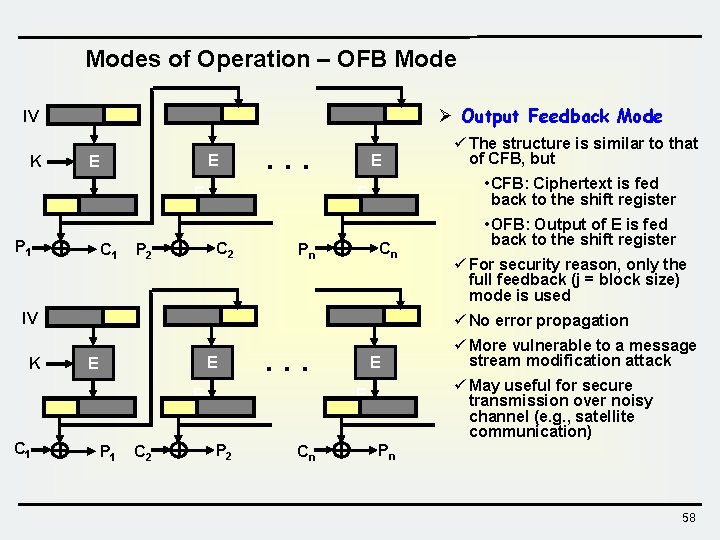
Modes of Operation – OFB Mode Ø Output Feedback Mode IV K E E . . . E P 1 C 1 • CFB: Ciphertext is fed back to the shift register E C 2 P 2 E Cn Pn IV K • OFB: Output of E is fed back to the shift register ü For security reason, only the full feedback (j = block size) mode is used ü No error propagation E E . . . E C 1 ü The structure is similar to that of CFB, but P 1 C 2 E ü May useful for secure transmission over noisy channel (e. g. , satellite communication) E P 2 Cn ü More vulnerable to a message stream modification attack Pn 58
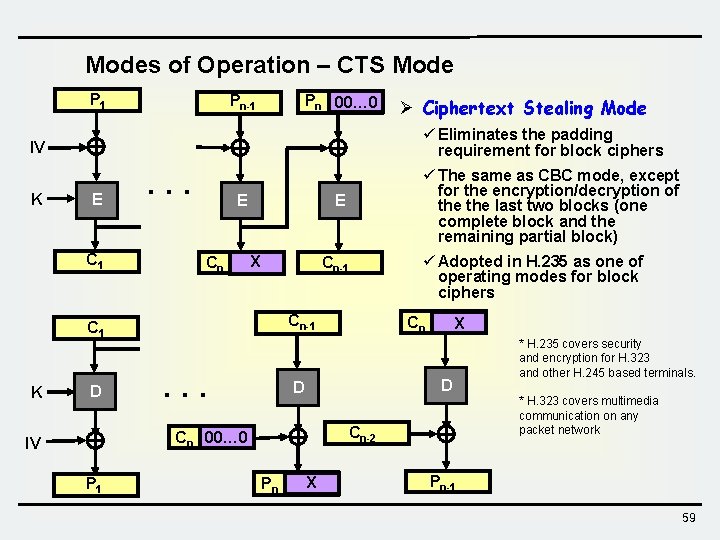
Modes of Operation – CTS Mode P 1 Pn-1 Pn 00… 0 ü Eliminates the padding requirement for block ciphers IV K E C 1 . . . Cn IV D E P 1 ü The same as CBC mode, except for the encryption/decryption of the last two blocks (one complete block and the remaining partial block) E E X Cn-1 C 1 K Ø Ciphertext Stealing Mode . . . Cn E Pn X D D Cn 00… 0 ü Adopted in H. 235 as one of operating modes for block ciphers Cn-2 X E * H. 235 covers security and encryption for H. 323 and other H. 245 based terminals. * H. 323 covers multimedia communication on any packet network Pn-1 59
6. Cryptanalysis 60
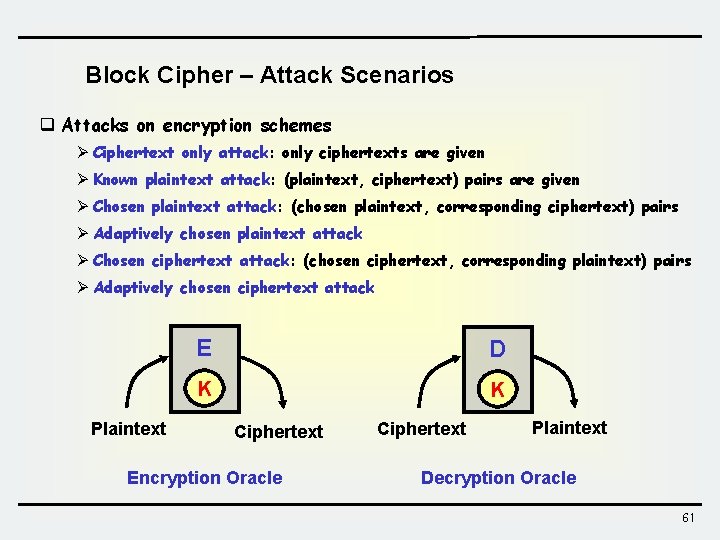
Block Cipher – Attack Scenarios q Attacks on encryption schemes Ø Ciphertext only attack: only ciphertexts are given Ø Known plaintext attack: (plaintext, ciphertext) pairs are given Ø Chosen plaintext attack: (chosen plaintext, corresponding ciphertext) pairs Ø Adaptively chosen plaintext attack Ø Chosen ciphertext attack: (chosen ciphertext, corresponding plaintext) pairs Ø Adaptively chosen ciphertext attack Plaintext E D K K Ciphertext Encryption Oracle Ciphertext Plaintext Decryption Oracle 61
Cryptanalysis of Block Ciphers q Statistical Cryptanalysis Ø Differential cryptanalysis (DC) Ø Linear Cryptanalysis (LC) Ø Various key schedule cryptanalysis q Algebraic Cryptanalysis Ø Interpolation attacks q Side Channel Cryptanalysis Ø timing attacks Ø differential fault analysis Ø differential power analysis, etc. 62
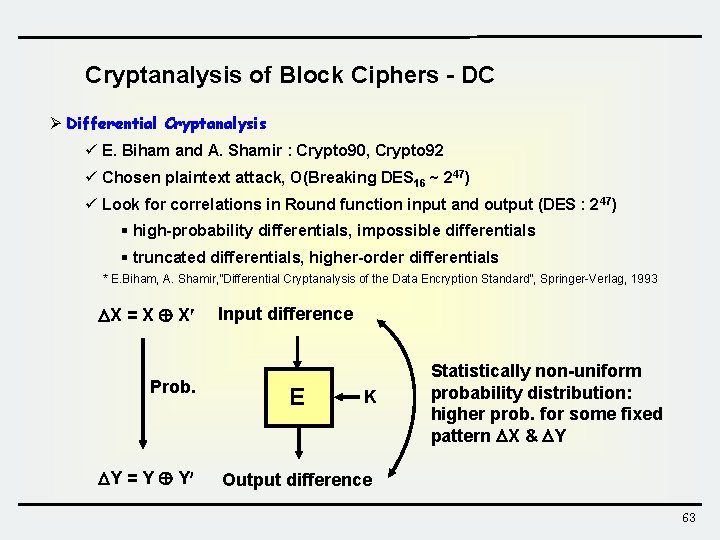
Cryptanalysis of Block Ciphers - DC Ø Differential Cryptanalysis ü E. Biham and A. Shamir : Crypto 90, Crypto 92 ü Chosen plaintext attack, O(Breaking DES 16 ~ 247) ü Look for correlations in Round function input and output (DES : 2 47) § high-probability differentials, impossible differentials § truncated differentials, higher-order differentials * E. Biham, A. Shamir, ”Differential Cryptanalysis of the Data Encryption Standard”, Springer-Verlag, 1993 X = X X Prob. Y = Y Y Input difference E K Statistically non-uniform probability distribution: higher prob. for some fixed pattern X & Y Output difference 63
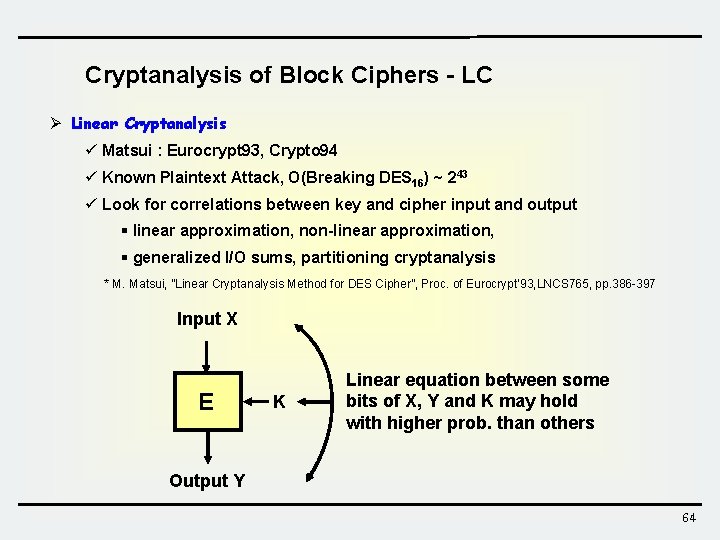
Cryptanalysis of Block Ciphers - LC Ø Linear Cryptanalysis ü Matsui : Eurocrypt 93, Crypto 94 ü Known Plaintext Attack, O(Breaking DES 16) ~ 243 ü Look for correlations between key and cipher input and output § linear approximation, non-linear approximation, § generalized I/O sums, partitioning cryptanalysis * M. Matsui, ”Linear Cryptanalysis Method for DES Cipher”, Proc. of Eurocrypt’ 93, LNCS 765, pp. 386 -397 Input X E K Linear equation between some bits of X, Y and K may hold with higher prob. than others Output Y 64
Other Attacks on Block Ciphers Ø Algebraic Cryptanalysis ü deterministic/probabilistic interpolation attacks Ø Key Schedule Cryptanalysis ü Look for correlations between key changes & cipher input/output § equivalent keys, weak or semi-weak keys § related key attacks Ø Side-Channel Cryptanalysis ü timing attacks ü differential fault analysis ü differential power analysis, etc. 65
7. Stream Ciphers 66
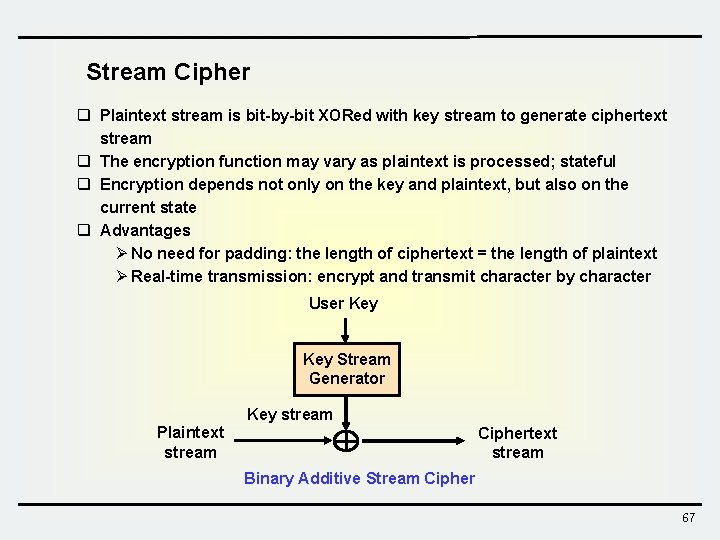
Stream Cipher q Plaintext stream is bit-by-bit XORed with key stream to generate ciphertext stream q The encryption function may vary as plaintext is processed; stateful q Encryption depends not only on the key and plaintext, but also on the current state q Advantages Ø No need for padding: the length of ciphertext = the length of plaintext Ø Real-time transmission: encrypt and transmit character by character User Key Stream Generator Key stream Plaintext stream Ciphertext stream Binary Additive Stream Cipher 67
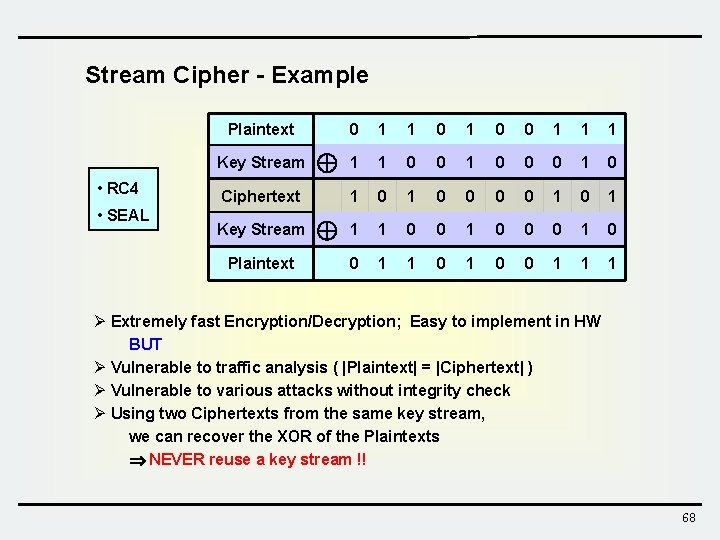
Stream Cipher - Example Plaintext Key Stream • RC 4 • SEAL Ciphertext Key Stream Plaintext 0 1 1 0 0 1 1 1 0 0 0 1 0 1 1 1 0 0 0 1 1 1 Ø Extremely fast Encryption/Decryption; Easy to implement in HW BUT Ø Vulnerable to traffic analysis ( |Plaintext| = |Ciphertext| ) Ø Vulnerable to various attacks without integrity check Ø Using two Ciphertexts from the same key stream, we can recover the XOR of the Plaintexts NEVER reuse a key stream !! 68
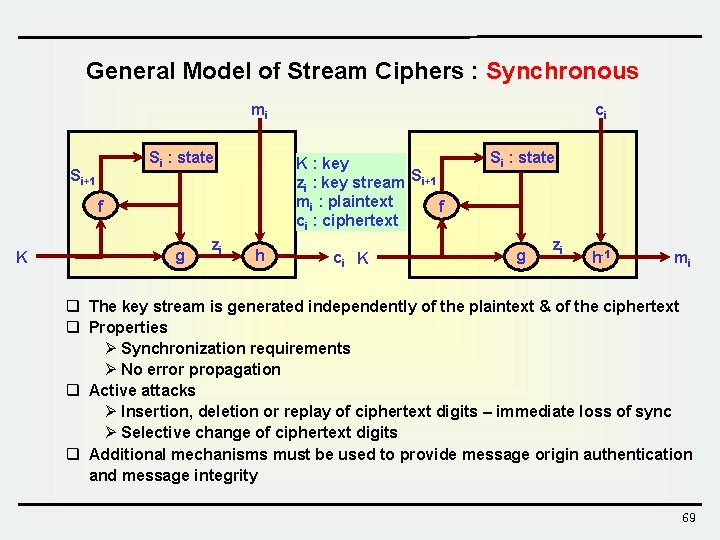
General Model of Stream Ciphers : Synchronous mi Si : state Si+1 K : key zi : key stream Si+1 mi : plaintext f ci : ciphertext f K g zi ci h ci K Si : state g zi h-1 mi q The key stream is generated independently of the plaintext & of the ciphertext q Properties Ø Synchronization requirements Ø No error propagation q Active attacks Ø Insertion, deletion or replay of ciphertext digits – immediate loss of sync Ø Selective change of ciphertext digits q Additional mechanisms must be used to provide message origin authentication and message integrity 69
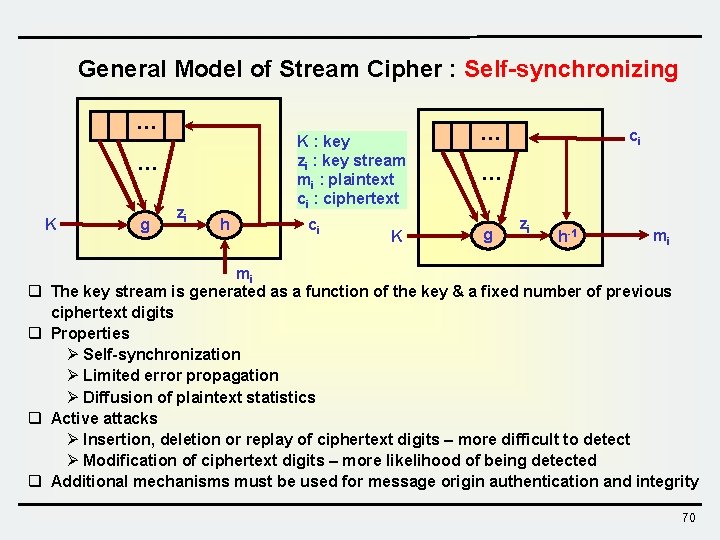
General Model of Stream Cipher : Self-synchronizing … K : key zi : key stream mi : plaintext ci : ciphertext … K q q g zi h ci K … ci … g zi h-1 mi mi The key stream is generated as a function of the key & a fixed number of previous ciphertext digits Properties Ø Self-synchronization Ø Limited error propagation Ø Diffusion of plaintext statistics Active attacks Ø Insertion, deletion or replay of ciphertext digits – more difficult to detect Ø Modification of ciphertext digits – more likelihood of being detected Additional mechanisms must be used for message origin authentication and integrity 70
Stream Cipher vs. Block Cipher Ø Stream Cipher ü Encrypt individual character (often 1 bit) ü Have memory; stateful cipher ü Generally extremely faster than block ciphers ü Suitable for multimedia streaming data (audio, video) ü Limited / No error propagation ü Problem : Re-sync. of key stream generator state ü Problem : insertion/deletion, replay of ciphertext digits Need additional Integrity Check Ø Block Cipher ü Encrypt simultaneously a group of characters (64 / 128 bits) Need Padding ü Memoryless ü Substitution Permutation Networks(SPN) or Feistel-type ü Various modes of operation : ECB, CBC, OFB, CTS, etc… 71
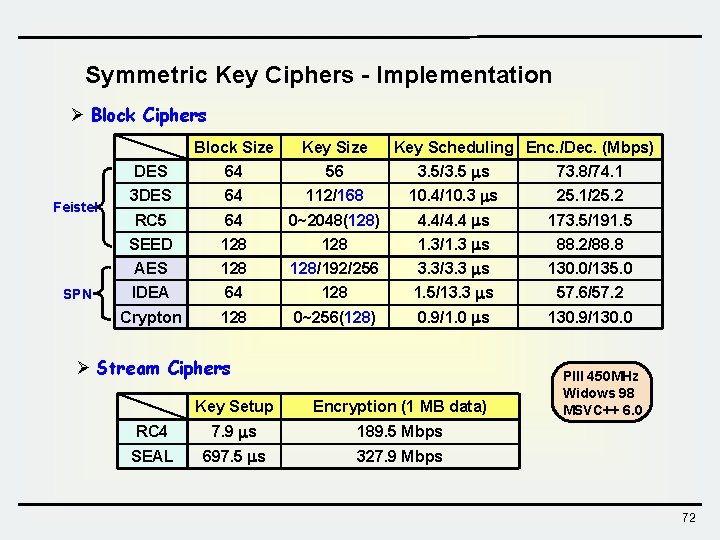
Symmetric Key Ciphers - Implementation Ø Block Ciphers Feistel SPN Block Size Key Scheduling Enc. /Dec. (Mbps) DES 64 56 3. 5/3. 5 s 73. 8/74. 1 3 DES 64 112/168 10. 4/10. 3 s 25. 1/25. 2 RC 5 64 0~2048(128) 4. 4/4. 4 s 173. 5/191. 5 SEED 128 1. 3/1. 3 s 88. 2/88. 8 AES 128/192/256 3. 3/3. 3 s 130. 0/135. 0 IDEA 64 128 1. 5/13. 3 s 57. 6/57. 2 Crypton 128 0~256(128) 0. 9/1. 0 s 130. 9/130. 0 Ø Stream Ciphers Key Setup Encryption (1 MB data) RC 4 7. 9 s 189. 5 Mbps SEAL 697. 5 s 327. 9 Mbps PIII 450 MHz Widows 98 MSVC++ 6. 0 72
Homework #1 Ø Block Cipher Design and Implementation 1 st Half : Select one of 15 AES candidates after round 2 except Rijndael and program it with your favorite language. (Test: encryption and decryption of given test vector) Deadline : 7/3, 2009 1. 2. 3. Describe why you choose X-algorithm Implement a C program (or use any language you prefer) which can encrypt and decrypt message in your algorithm Provide a performance analysis of your algorithm and your implementation 73
- Slides: 73