Introduction to Cryptographic Key Management Outline n Context







- Slides: 20

Introduction to Cryptographic Key Management

Outline n Context n Definitions n Description n Principles n Illustrations and Demonstrations n Recommendations

Context -- Cryptography is: n use of secret codes to hide and authenticate data n suited to open and hostile environments n broadly applicable n portable n composable n can emulate any media or environment control n arbitrarily strong n effective n efficient

Context n cost of crypto is low n falling with the cost of computing n relative strength is rising n strong as we need it to be n stronger than other security mechanisms n strong link in the security chain n robust, resilient, not likely to break n very unlikely to collapse n advantage is to the cryptographer

Modern Cryptography - the great inventions n automatic encoding and decoding n the large independent key variable n complexity-based encryption (DES) n asymmetric key n automatic key management

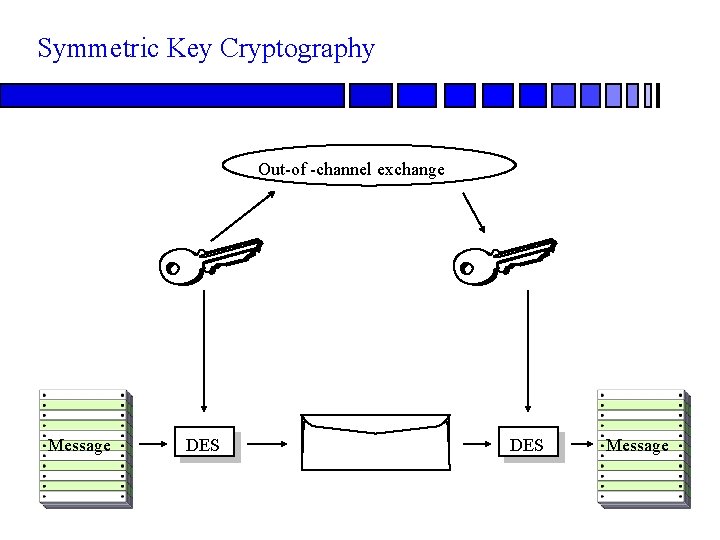
Symmetric Key Cryptography Out-of -channel exchange Message DES Message

Key Management n generation n recording n transcription n distribution n installation n storage n change n disposition n and control

Key Management n generation n recording n transcription n distribution n installation n storage n change n disposition n and control

Key Management n is very important n must be rigorous and disciplined n principal point of attack n not intuitive n easy to screw up

Modern Key Management n fully automated, (i. e. , no manual operations) n permits frequent key change (e. g. , file, session, message, transaction, or other data object) n increases the effective key length or security n balances the interests in the key of multiple parties n application of RSA n and smart cards n may be integrated or stand-alone

Applications of Key Management n increase effective strength n compensate for limitations of algorithm n involve multiple people in sensitive duties n personal security environments

Principles of Key Management n No key may ever appear in the clear n All keys must be randomly generated by a crypto engine n Keys must be chosen evenly from the entire key space n Must not have any (visible) structure n Key-encrypting keys are separate from data keys n Everything encrypted under a key-encrypting key must originate within a crypto engine n Key management must be automated

Asymmetric Key Cryptography n key has two parts n what is encrypted with one part may only be decrypted with the other n only one part need be kept secret n requires a minimum of prearrangement

Public Key Issues n public key need not be kept secret n must be the right key n i. e. , association between public key and legal person n encapsulated in a certificate n signed by someone who knows

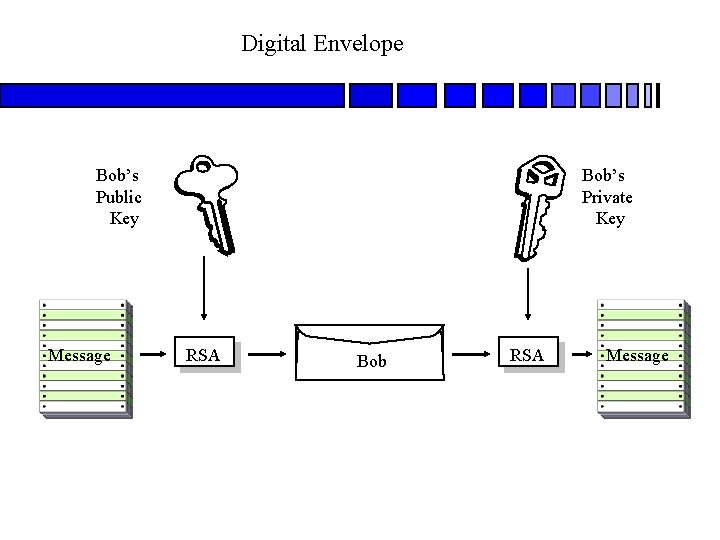
Digital Envelope Bob’s Public Key Message Bob’s Private Key RSA Bob RSA Message

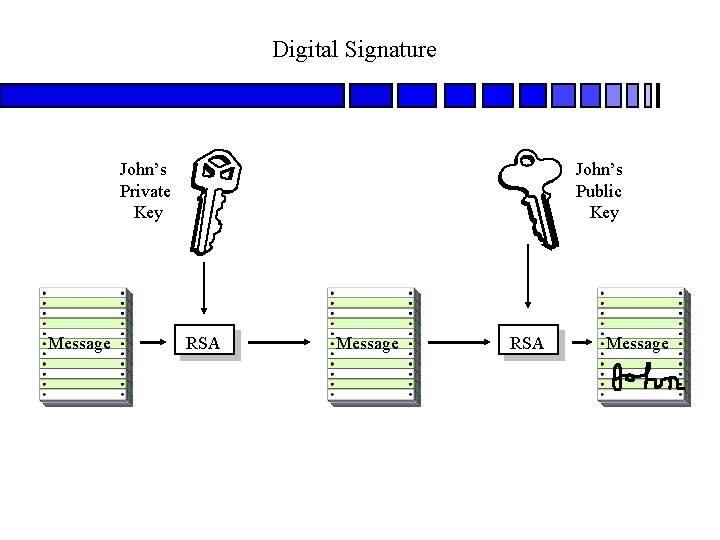
Digital Signature John’s Private Key Message John’s Public Key RSA Message

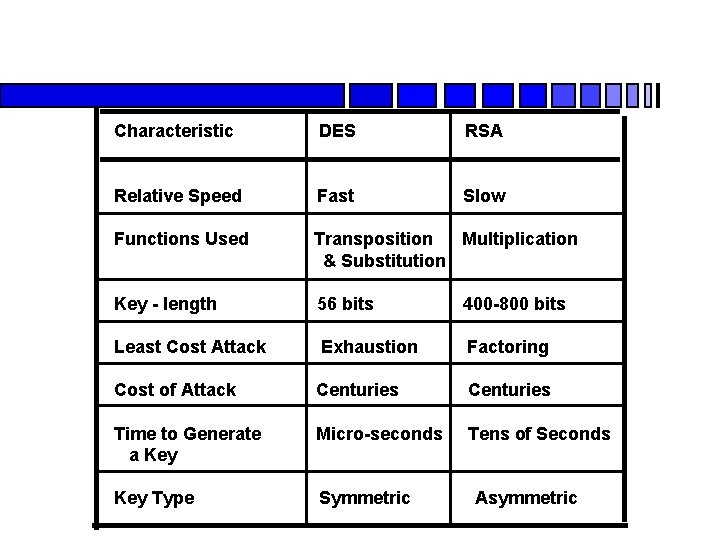
Characteristic DES RSA Relative Speed Fast Slow Functions Used Transposition Multiplication & Substitution Key - length 56 bits 400 -800 bits Least Cost Attack Exhaustion Factoring Cost of Attack Centuries Time to Generate a Key Micro-seconds Tens of Seconds Key Type Symmetric Asymmetric

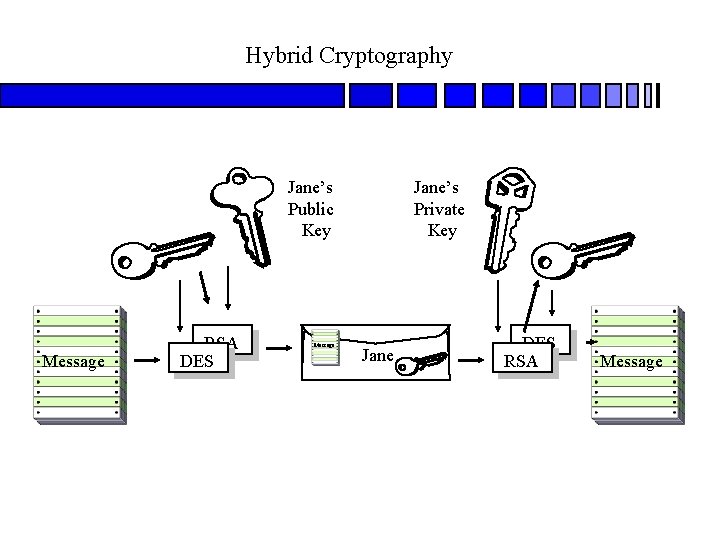
Hybrid Cryptography Jane’s Public Key Message RSA DES Message Jane’s Private Key Jane DES RSA Message

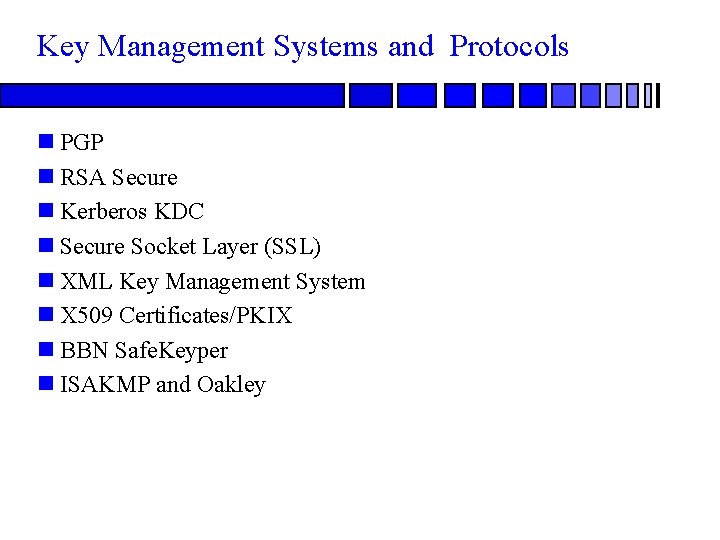
Key Management Systems and Protocols n PGP n RSA Secure n Kerberos KDC n Secure Socket Layer (SSL) n XML Key Management System n X 509 Certificates/PKIX n BBN Safe. Keyper n ISAKMP and Oakley
