Introduction Of System Security Slide Prepared and Presented











- Slides: 18

Introduction Of System Security Slide Prepared and Presented By: Mr. Ankit S. Didwania (RC-1093) Open Education Resource (OER) by Ankit S. Didwania is licensed under a Creative Commons Attribution-Share. Alike 4. 0 International License. This is a Free Culture License! You are free to use, distribute and modify it, including for commercial purposes, provided you acknowledge the source and share-alike.

Learning Outcomes • Learner should be able to detect the process of Symmetric Cipher Model • Learner should be able to understand the basics of Cryptography and Cryptanalysis

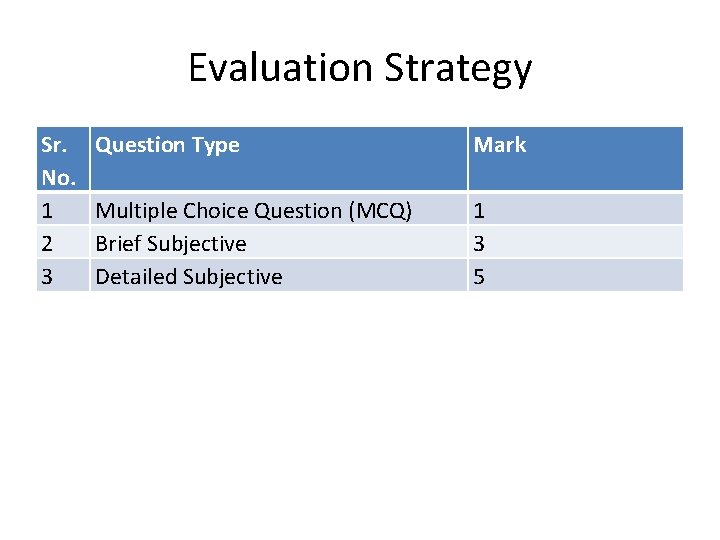
Evaluation Strategy Sr. No. 1 2 3 Question Type Mark Multiple Choice Question (MCQ) Brief Subjective Detailed Subjective 1 3 5

Le. D 2. 0: Learning Dialogues Activity

Symmetric Encryption • Also referred as conventional / privatekey / single-key encryption algorithm • In it, same key is shared by both the sender and receiver • Its classical algorithm, but still widely used • Modern algorithm uses public-key algorithm, invented in 1970’s

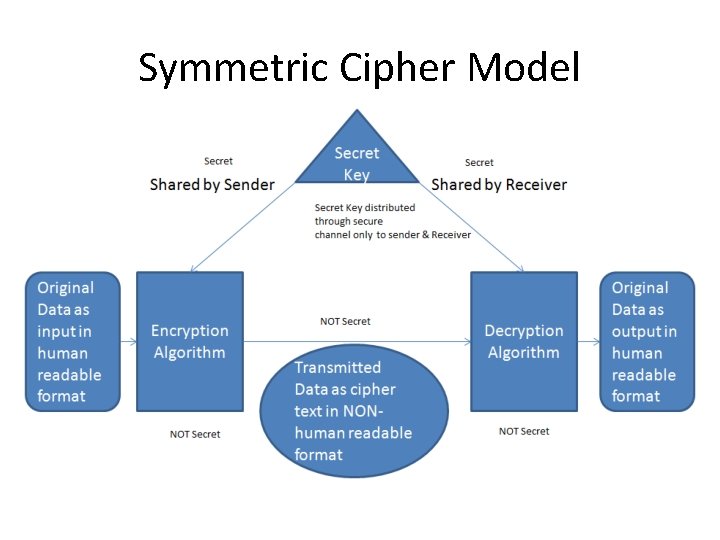
Some Basic Terminology • plaintext - original message • ciphertext - coded message • cipher - algorithm for transforming plaintext to ciphertext • key - info used in cipher known only to sender/receiver • encipher (encrypt) - converting plaintext to ciphertext • decipher (decrypt) - recovering ciphertext from plaintext • cryptography - study of encryption principles/methods • cryptanalysis (codebreaking) - study of principles/ methods of deciphering ciphertext without knowing key • cryptology - field of both cryptography and cryptanalysis

Symmetric Cipher Model

Cryptography • characterize cryptographic system by: – type of encryption operations used • substitution / transposition / product – number of keys used • single-key or private / two-key or public – way in which plaintext is processed • block / stream

Cryptanalysis • objective to recover key not just message • general approaches: – cryptanalytic attack – brute-force attack

Cryptanalytic Attacks • ciphertext only – only know algorithm & ciphertext, is statistical, know or can identify plaintext • known plaintext – know/suspect plaintext & ciphertext • chosen plaintext – select plaintext and obtain ciphertext • chosen ciphertext – select ciphertext and obtain plaintext • chosen text – select plaintext or ciphertext to en/decrypt

More Definitions • unconditional security – no matter how much computer power or time is available, the cipher cannot be broken since the ciphertext provides insufficient information to uniquely determine the corresponding plaintext • computational security – given limited computing resources (eg time needed for calculations is greater than age of universe), the cipher cannot be broken

Brute Force Search • • always possible to simply try every key most basic attack, proportional to key size assume either known / recognise plaintext A brute-force attack involves trying every possible key until an intelligible translation of the ciphertext into plaintext is obtained. On average, half of all possible keys must be tried to achieve success.

Summary Learner should have understood the following: • working of Symmetric Cipher Model • the types of Cryptography • the basics of cryptanalysis

Acknowledgement • Book –“Cryptography and Network Security”, 4 th edition, by William Stallings, Chapter 2 “Classical Encryption Techniques”

Lb. D 2. 0: Learning by Doing Activity

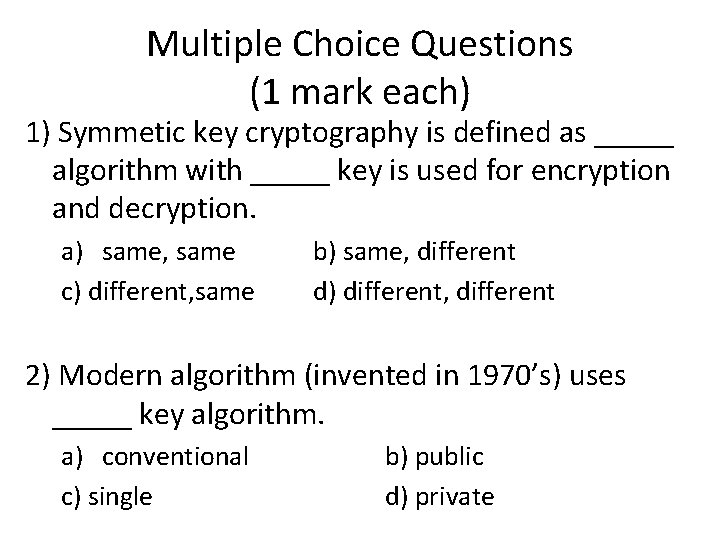
Multiple Choice Questions (1 mark each) 1) Symmetic key cryptography is defined as _____ algorithm with _____ key is used for encryption and decryption. a) same, same c) different, same b) same, different d) different, different 2) Modern algorithm (invented in 1970’s) uses _____ key algorithm. a) conventional c) single b) public d) private

Subjective Questions • Brief Subjective (3 marks each) : 1) What do you mean by brute-force attack? 2) What do you mean by cryptology? • Detailed Subjective (5 marks each) : 1) Give the requirement for secure use of conventional encryption 2) Which three dimension are used for characterizing cryptographic techniques

THANK YOU