Introduction of IACS Activities related to Maritime Cyber

Introduction of IACS Activities related to Maritime Cyber Systems / Cyber Security George Reilly IACS Cyber Systems Panel Chairman Joint Working Group / Cyber Systems Chairman

Introduction of IACS Activities related to Maritime Cyber Systems / Cyber Security Contents: • IMO and Goals of MSC. 1 Circ. 1526 - Review • IACS in Industry with a Non-Cyber Mind-Set • Activities of the Cyber Systems Panel • Activities of the Joint Working Group (JWG/CS) • Incorporating Cyber Systems/Security into the process

The Goal of Cyber Risk Management Support Safe and Secure Shipping which is Operationally Resilient to Cyber Risks (MSC. 1 Circ 1526)

Risk Maritime Cyber Risk = Measure of the extent a technology asset is threatened by • potential circumstance or event (JWG/CS) , which may • result in operational, safety or security failures (E 22) as a consequence of • information or systems being corrupted, lost or compromised (E 22)

Stakeholders → take the necessary steps to safeguard shipping from threats & vulnerabilities digitization, integration & automation of (E 22) processes and systems
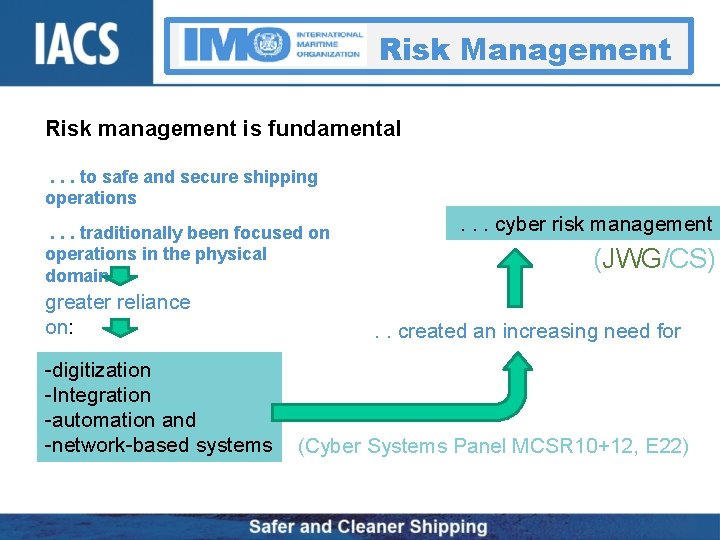
Risk Management Risk management is fundamental. . . to safe and secure shipping operations. . . traditionally been focused on operations in the physical domain greater reliance on: -digitization -Integration -automation and -network-based systems . . . cyber risk management (JWG/CS) . . created an increasing need for (Cyber Systems Panel MCSR 10+12, E 22)

Integrated Implementation Predicated on the goal of supporting safe and secure shipping which is • operationally resilient to cyber risks; these Guidelines provide recommendations that can be incorporated into existing risk management processes • The Guidelines are complementary to the safety and security management practices established by this Organization Complimentary to existing IACS processes (Cyber Systems Panel)

Distinctive IT vs OT Information technology • use of data as information Operational technology systems • data to control or monitor physical processes • information and data exchange within and between these systems (Cyber Systems Panel MCSR 4, 7, 11, 12)

Technologies Gains & Risks the technologies - provide efficiency gains and present risks - to critical systems and processes risks may result from vulnerabilities arising from - inadequate operation, - integration (Cyber Systems Panel MCSR 10) - maintenance (Cyber Systems Panel MCSR 1+11) - design ( Cyber Systems Panel MCSR 8) - intentional and unintentional cyberthreats ( Cyber Systems Panel MCSR 7)

IACS and Cyber Systems Challenges in an Industry with a non-Cyber tradition

00001111110001010 1110010101111010000101 001111110000100101 0000111010011100101000 011100001000110100 1100011111100000111111 1001010100101111 110001101101010001 101010101010

. ppt IACS 00110011010110 Failures 0 in 10101101 01 circuits 1 may 0 not 101110 1100 appear 0 to 1 create 101010 significant 0101101 0101 maritime 0 safety 11010 111 or 1 environmental 01011 0000110 threats 1011011001 01000110101000
We transferred the power
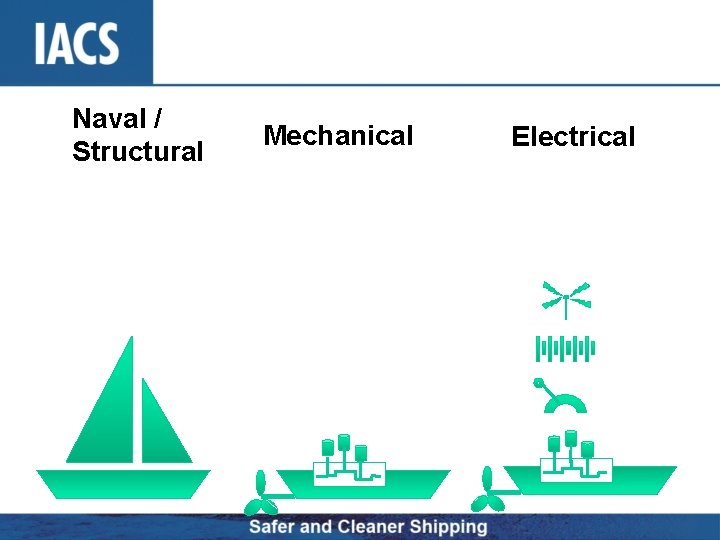
Naval / Structural Mechanical Electrical
Electrical / Electronic WWW 100101110 1001101100010100
The parts that have been introduced over the past 5 to 10 years have not been so visible Those in the industry understand the principles of Naval Architecture, Structures and Machinery very well.
We want to get back to a more comfortable time The Maritime industry would prefer this Cyber issue would simply pass and go away
To better understand the problem To deal with the problem everybody needs let go of an outdated mental model to accept the reality The apparent ‘GAP’ is not small and it is not empty. . .
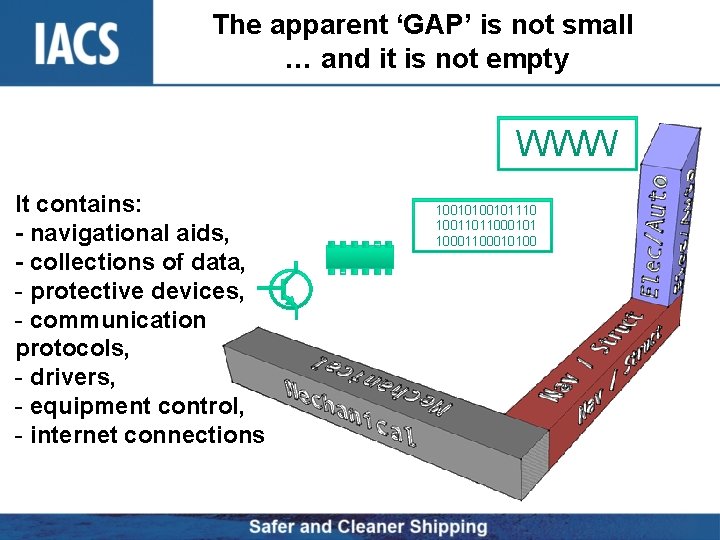
The apparent ‘GAP’ is not small … and it is not empty WWW It contains: - navigational aids, - collections of data, - protective devices, - communication protocols, - drivers, - equipment control, - internet connections 100101110 1001101100010100
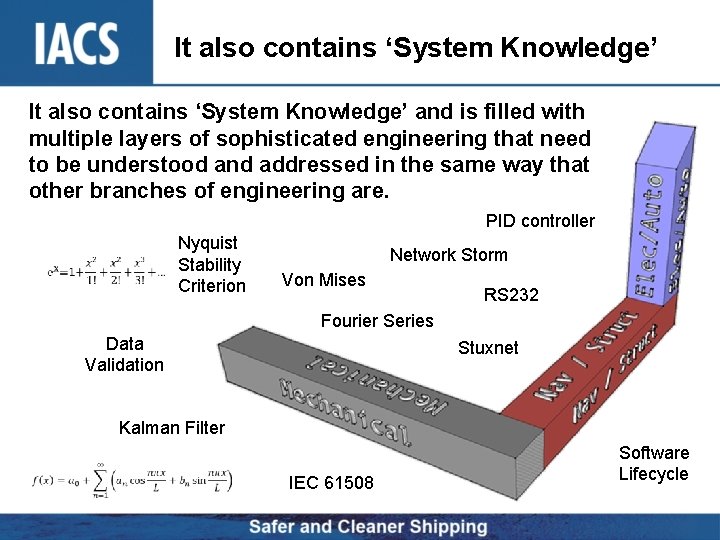
It also contains ‘System Knowledge’ and is filled with multiple layers of sophisticated engineering that need to be understood and addressed in the same way that other branches of engineering are. PID controller Nyquist Stability Criterion Network Storm Von Mises RS 232 Fourier Series Data Validation Stuxnet Kalman Filter IEC 61508 Software Lifecycle
However, the Maritime industry must now also face the problems that have come to affect all industries around the world.
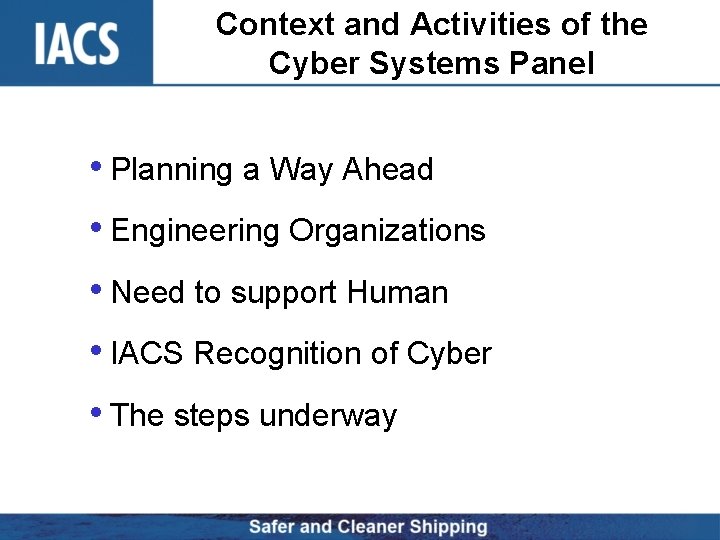
Context and Activities of the Cyber Systems Panel • Planning a Way Ahead • Engineering Organizations • Need to support Human • IACS Recognition of Cyber • The steps underway

Planning a Way Ahead It is important to know the realities of: • ourselves – and our responsibilities • our industry – and its responsibilities • the world in which we operate In order to establish where we need to be and what steps we need to take to get there

Engineering Organizations IACS Members are Engineering organizations - Operate internationally - Regulate ship design - Verify construction - Verify components in the supply chain - Follow-up during regular Surveys - Widely recognized by port and flag states

Need to support Human IACS Members are Engineering organizations that appreciate the need for the process to support the ‘Human’: - Satisfies end user - Reduces degrees of freedom - System interfaces that minimise unplanned functions

IACS Recognition of Cyber IACS Members are Engineering organizations - Recognized Cyber Systems with a full Panel - Coordinating with industry - Initially developing recommendations: - For widest consultation with industry To create awareness prior to regulation To populate a framework for applying risk To create no more burden than necessary

IACS - The Steps Underway • Initially a set of 12 basic subjects • To be developed in 4 phases • Initially non-mandatory Recommendations • Industry advised of availability in order to encourage feedback • At end of 12 th document, decisions on how the 12 topics would be reformatted and combined to address risk levels • Practical application process implemented and validated

12 Maritime Cyber System Recommendations (MCSR 1 to 12) Four Phases A, B, C & D MCSR 1 Procedure for Software Maintenance MCSR 2 Manual Backup MCSR 3 Contingency Post Failure A B MCSR 4 Network Architecture MCSR 5 Data Assurance MCSR 6 Physical Security C D MCSR 7 Network Security MCSR 8 Vessels’ System Design MCSR 9 Programmable System Equipment Inventor MCSR 10 Integration MCSR 11 Remote Update / Access MCSR 12 Communications and Interfaces
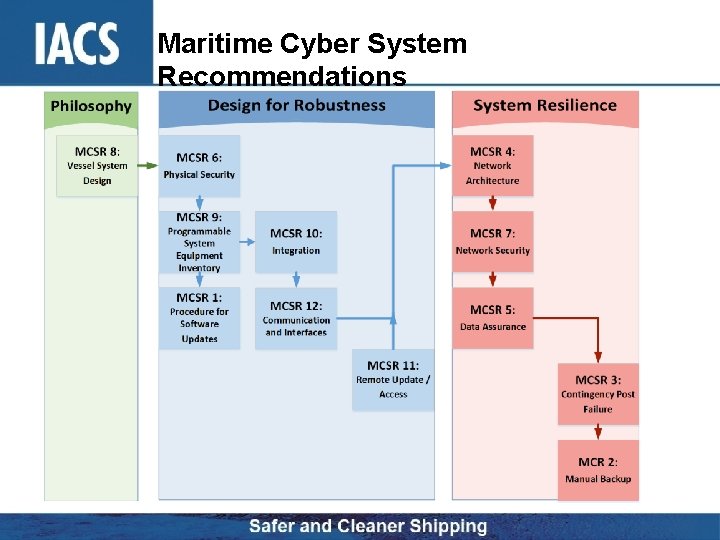
Maritime Cyber System Recommendations

Activities with the Joint Working Group (JWG/CS) Primary aim of the Industry Joint Working Group is to facilitate active cooperation and communication amongst industry groups that have an interest in the production, use and operation of cyber systems. The experience of the JWG members will assist as direction and strategy are developed by providing a practical and expert input. The IACS Cyber Systems Panel will also benefit from the availability of the JWG expertise and will be able to assist in the review of early drafts of recommendations and requirements as the are developed.
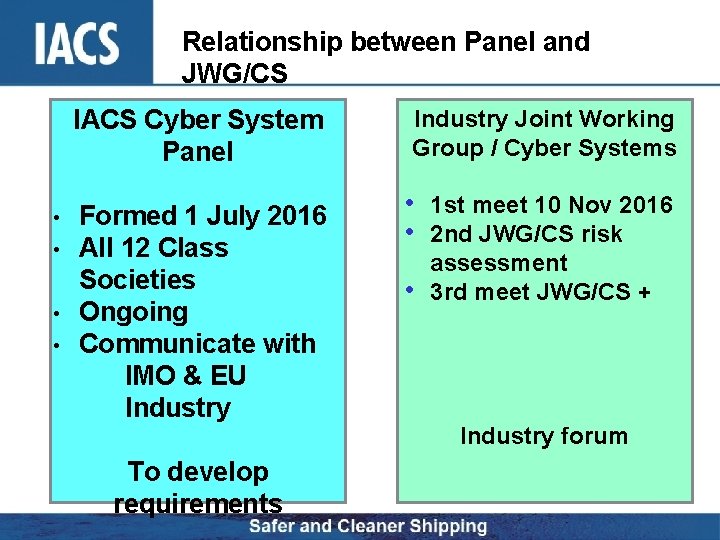
Relationship between Panel and JWG/CS IACS Cyber System Panel • • Formed 1 July 2016 All 12 Class Societies Ongoing Communicate with IMO & EU Industry To develop requirements Industry Joint Working Group / Cyber Systems • 1 st meet 10 Nov 2016 • 2 nd JWG/CS risk • assessment 3 rd meet JWG/CS + Industry forum
Relationship between Panel and JWG/CS

Activities with the Joint Working Group (JWG/CS) One of the first activities of the JWG is to participate in a Risk Assessment to consider aspects such as: - criticality focus and priorities, - threat focus and priorities Industry risk framework goals and resulting requirements Suggested security levels (e. g. security level 1, 2, 3 and 4) and mapping into IACS and other standards work The risk assessments are being led by Professor Paul Dorey who also undertook a similar role in the UK Energy Sector covering generation and distribution for both Gas and Electricity. Prof. Dorey is retained by Inmarsat and it is planned that Risk Assessment work with the JWG will be the subject of a White Paper later this year.
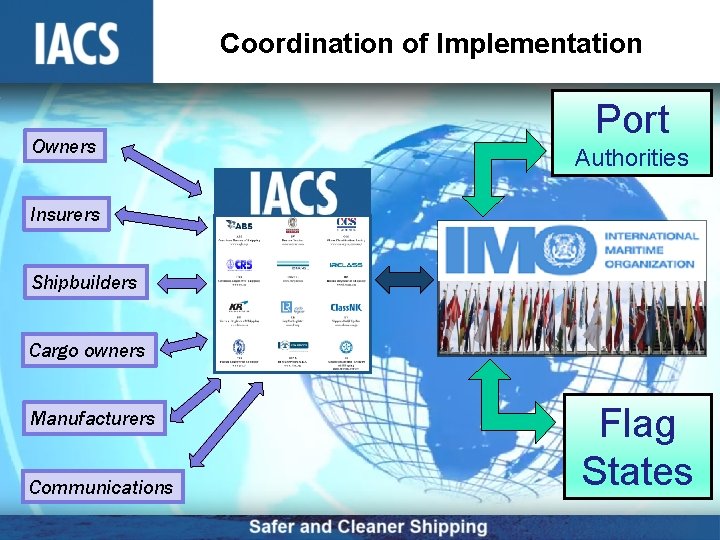
Coordination of Implementation Owners Port Authorities Insurers Shipbuilders Cargo owners Manufacturers Communications Flag States

Thank you! contacts: ABCyber. Chair@Eagle. org
- Slides: 36