Introduction CSCI 283172 Fall 2006 GWU Sources Bishops

Introduction CSCI 283/172 Fall 2006 GWU Sources: Bishop’s slides, Chapter 1 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set

Introduction • • Goals of computer security Threats Policies and mechanisms The role of trust Assurance Operational Issues Human Issues 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 2
Basic Components • Confidentiality – Keeping data and resources hidden • Integrity – Data integrity (integrity) – Origin integrity (authentication) • Availability – Enabling access to data and resources 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 3

Examples: Confidentiality • Secret communication • Salaries are kept confidential • Not exact value of data, but property of data is kept confidential – not how many with SARS in the neighborhood, but is there SARS at all • Not exact value of data but interest in, or knowledge of is kept confidential – why does this employee want to know about jobs at other places? – does the US govt. have a file on John Doe? • Confidentiality of resources: – what computer systems are used, what configurations, what highend equipment is available 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 4

Examples: Integrity Violation • When personal information is incorrectly maintained by a service provider (for example, a loan has been repaid but this is noted in my credit rating) • When information is changed by an entity that does not have the authority to do so – can be malicious (origin and data integrity violation) • Libel/defamation • Incorrect source cited (Integrity violations can be prevented – more difficult – or detected) 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 5

Examples: Availability Violation Denial of service attacks in: E-commerce, News sites, Government information, Remote electronic voting, Cryptographic protocols that require the participation of a specific entity or group of entities Can be caused at – origin (preventing server from accessing resources required to send info. ) – destination (blocking communication from server) – Intermediate path (by dropping communication from either origin or destination) Difficult to detect because system behavior might be due to genuine system overload 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 6

Classes of Threats (Potential Security Violations) • Disclosure – Snooping • Deception – Modification, spoofing (masquerading, identity theft), repudiation of origin, denial of receipt • Disruption – Modification • Usurpation: unauthorized control – Modification, spoofing, delay, denial of service 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 7

Policies and Mechanisms Eg: system access control and DRM • Policy says what is, and is not, allowed – This defines “security” for the site/system/etc. – Can be in machine language • Mechanisms (technical or procedural, can use crypto) enforce policies • Composition of policies – If policies conflict, discrepancies may create security vulnerabilities 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 8

Goals of Security • Prevention – Prevent attackers from violating security policy – Elaborate prevention can hamper legitimate use (e. g. DRM) • Detection – Detect attackers’ violation of security policy – Typically required because prevention is not always successful • Recovery – Stop attack, assess and repair damage – Continue to function correctly even if attack succeeds 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 9

Trust and Assumptions • Underlie all aspects of security • Policies – Unambiguously partition system states into secure and nonsecure – Correctly capture security requirements • Mechanisms, assumed to: – Together enforce/implement policy (i. e. prevent entry into nonsecure state) – Be implemented, installed and administered correctly 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 10
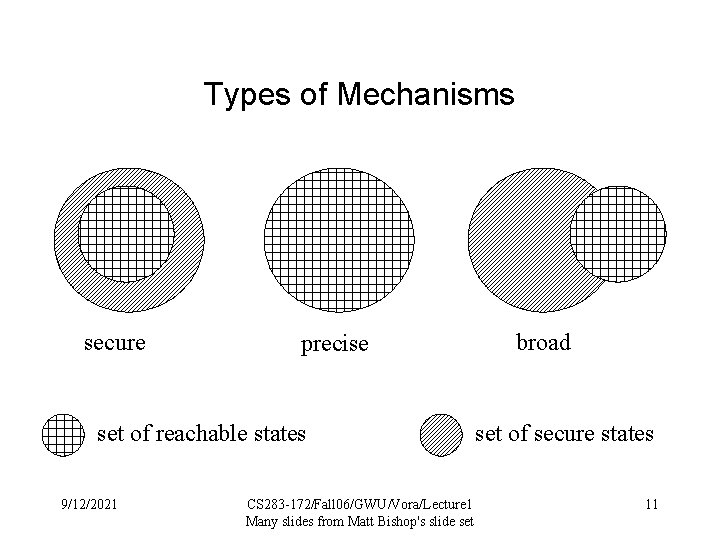
Types of Mechanisms secure precise set of reachable states 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set broad set of secure states 11

Definition 1. 3 Let P be the set of all possible states. Let Q be the set of secure states specified by the security policy. Let the security mechanisms restrict the system to some set of states R. A security mechanism is Secure if Precise if Broad if Security policy characterizes Q, security mechanism prevents entry into P Q 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 12
Assurance How much a system can be trusted • Specification – Requirements analysis – Statement of desired functionality • Design – How system will meet specification • Implementation – Programs/systems that carry out design – Difficult to prove correctness of implementation 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 13

Operational Issues • Cost-Benefit Analysis – Is it cheaper to prevent or recover? • Risk Analysis – Should we protect something? – How much should we protect this thing? (What is the likelihood of a successful attack? ) • Laws and Customs – Are desired security measures illegal? – Will people do them? 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 14

Human Issues • Organizational Problems – Power and responsibility – Financial benefits • People problems – Outsiders and insiders – Social engineering attacks 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 15
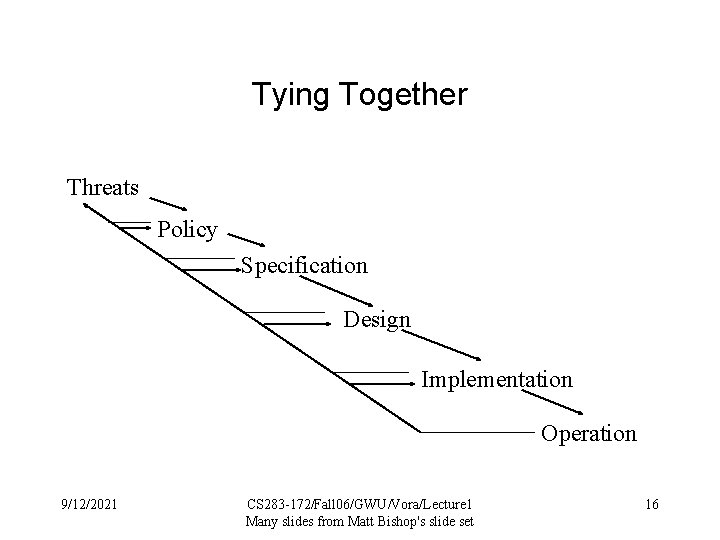
Tying Together Threats Policy Specification Design Implementation Operation 9/12/2021 CS 283 -172/Fall 06/GWU/Vora/Lecture 1 Many slides from Matt Bishop's slide set 16
- Slides: 16