Introduction Computer Networks Dr K Raghava Rao Professor








- Slides: 77

Introduction Computer Networks Dr. K. Raghava Rao Professor & Head Dept. of ECSE raghavarao@kluniversity. in

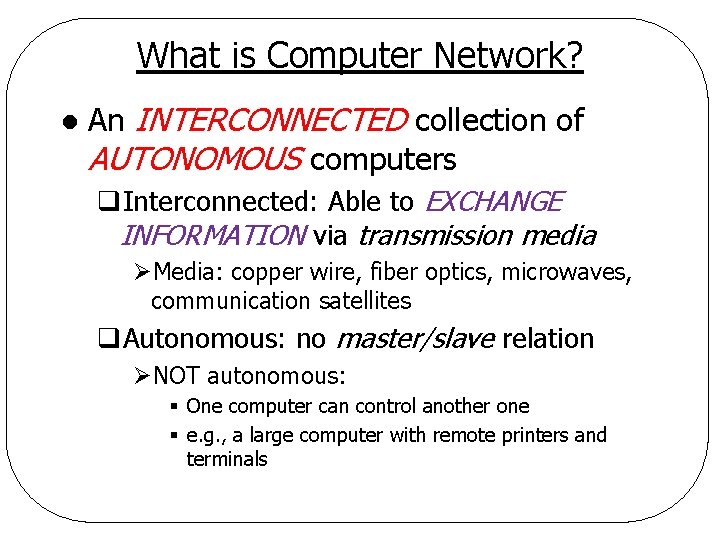
What is Computer Network? l An INTERCONNECTED collection of AUTONOMOUS computers q. Interconnected: Able to EXCHANGE INFORMATION via transmission media ØMedia: copper wire, fiber optics, microwaves, communication satellites q. Autonomous: no master/slave relation ØNOT autonomous: § One computer can control another one § e. g. , a large computer with remote printers and terminals

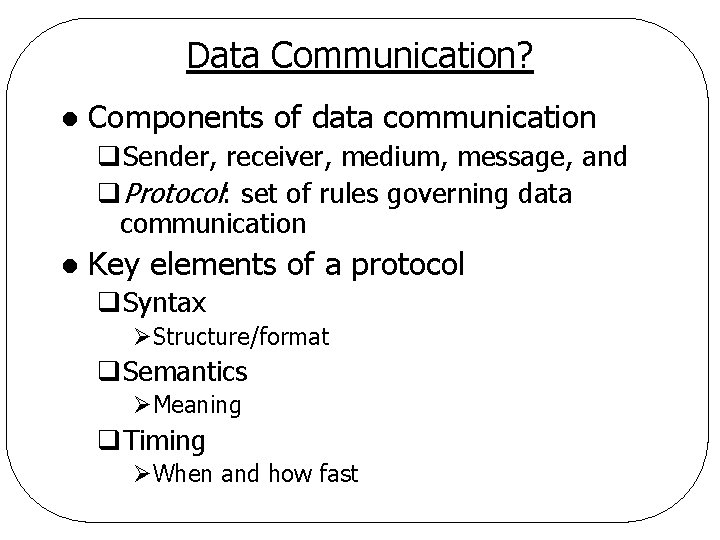
Data Communication? l Components of data communication q. Sender, receiver, medium, message, and q. Protocol: set of rules governing data communication l Key elements of a protocol q. Syntax ØStructure/format q. Semantics ØMeaning q. Timing ØWhen and how fast

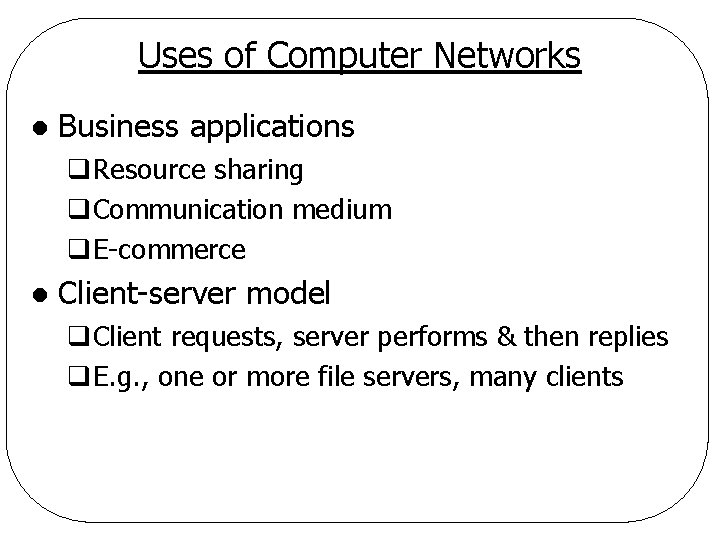
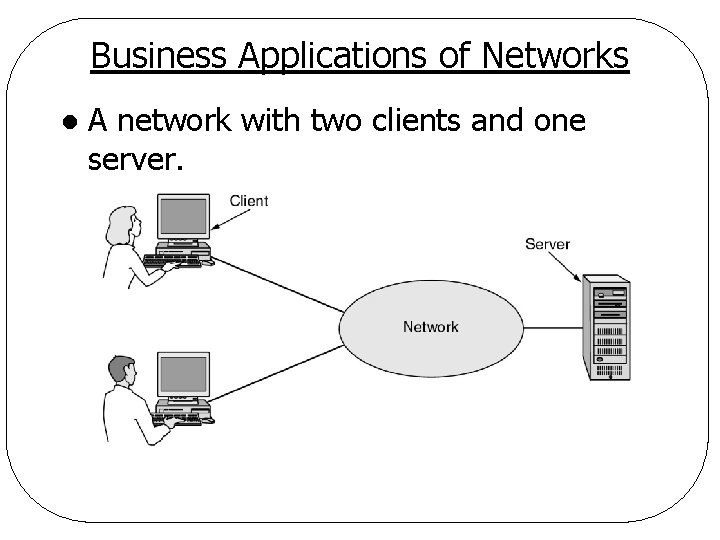
Uses of Computer Networks l Business applications q. Resource sharing q. Communication medium q. E-commerce l Client-server model q. Client requests, server performs & then replies q. E. g. , one or more file servers, many clients

Business Applications • Business – for information and resource sharing – many companies have a substantial number of computers – to monitor production, keep track of inventories, and do the payroll. They need to be connected to extract and correlate information about the entire company – resource sharing – for example - networked printer is often cheaper, faster, and easier to maintain than a large collection of individual printers

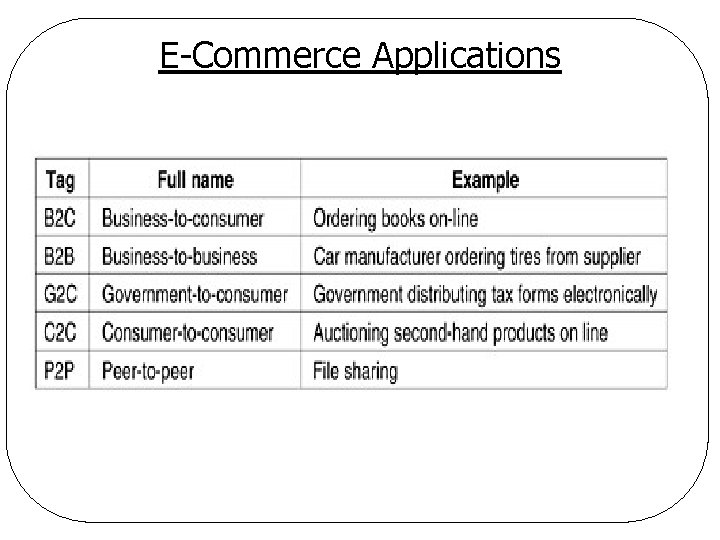
E-Commerce Applications

Business Applications of Networks l A network with two clients and one server.

Uses of Computer Networks l Home applications q. Access to remote information ØOn-line publishing, digital library, WWW q. Person-to-person communication ØEmail, instant messaging, peer-to-peer communication, videoconferencing, Internet phone, E-learning q. Interactive entertainment ØVideo on demand (VOD), games q. E-commerce ØHome shopping, electronic banking and investment, on-line auction

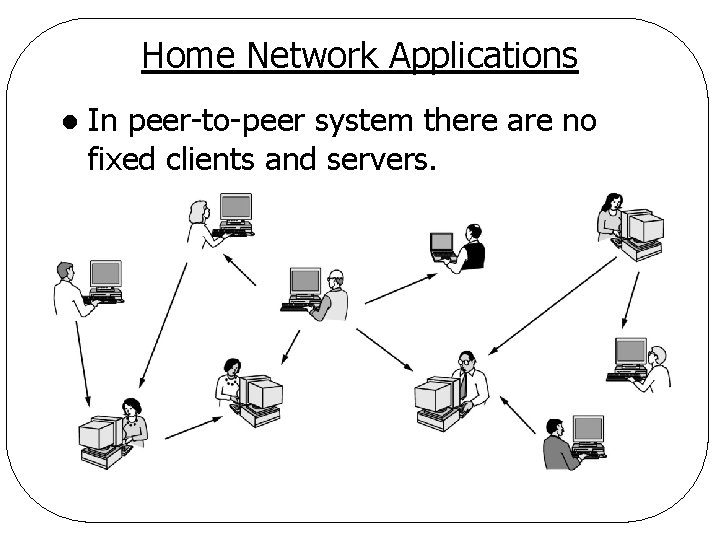
Home Network Applications l In peer-to-peer system there are no fixed clients and servers.

Mobile Users l Notebook, PDA, cellular phone l Two aspects of mobility: l –user mobility: users communicate (wireless) “anytime, l anywhere, with anyone” –device portability: devices can be connected anytime, anywhere to the network l Wireless networking and mobile computing -GPS

Social Issues • • • Network neutrality Net neutrality (also network neutrality or Internet neutrality) is the principle internet service providers and governments should treat all data on the internet equally, not discriminating or charging differentially by user, content, site, platform, application, type of attached equipment, and modes of communication. Digital Millennium Copyright Act The Digital Millennium Copyright Act (DMCA) is a United states copyright law that implements two 1996 treaties of the World intellectual property organization (WIPO). It criminalizes production and dissemination of technology, devices, or services intended to circumvent measures (commonly known as digital rights management or DRM) that control access to copyrighted works Profiling users • A user profile is a visual display of personal data associated with a specific user, or a customized desktop environment • Phishing is the attempt to acquires senstive information such as usernames passwordsandcredit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication. hing

Social Issues l l l Computer networks offer the potential for sending anonymous messages – in some cases this may be desirable. Lot of the information available on Internet is illinformed, misleading, or downright wrong Computer networks have also introduced new kinds of antisocial and criminal behavior – E-mail messages or some sites may contain active content (basically programs or macros that execute on the receiver's machine) with viruses Identity theft is becoming a big problem - thieves collect information about a victim and can obtain credit cards details and other private data Copyright violations is also carried out – music and video are digitally transmitted.

Network Topologies l By transmission technology q. Broadcast links Øsmaller, geographically localized networks q. Point-to-point links Ølarger networks l By scale q. PAN q. LAN q. MAN q. WAN

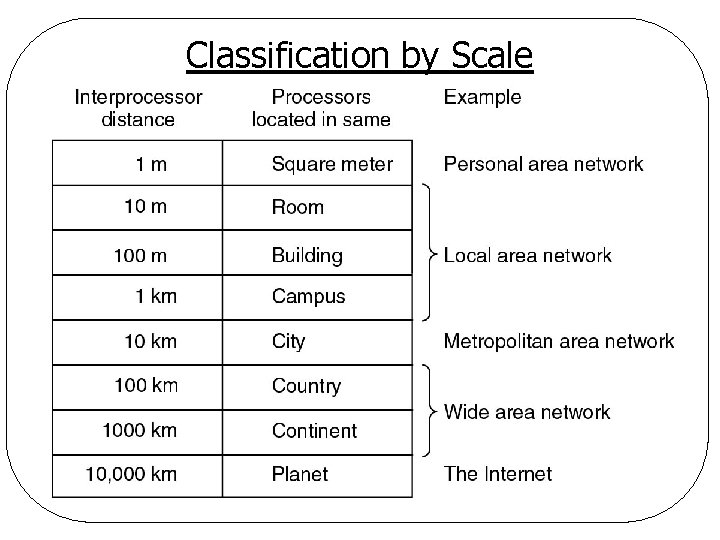
Classification by Scale

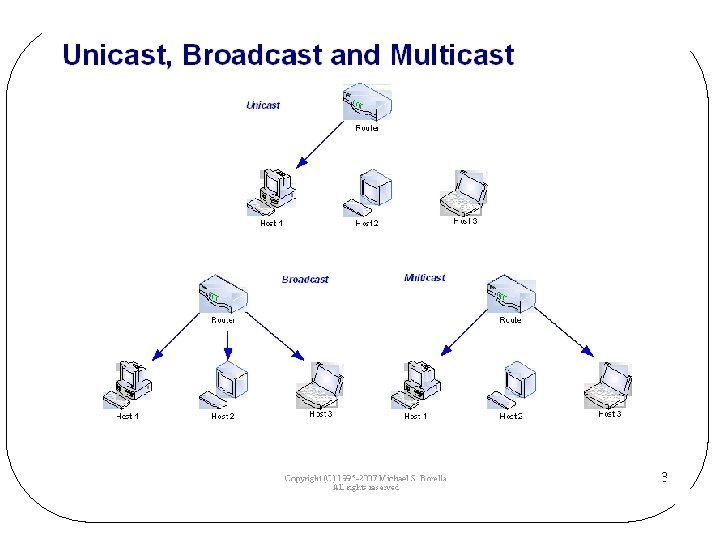
Broadcast Network A single communication channel shared by all machines on the network l Packets (short messages) sent by any machine are “received” by all the others l q. Address field of packet: whom it is intended l Message transmission q. Unicast: one sends, one receives q. Broadcasting: one sends, all receive q. Multicasting: one sends, a group receives


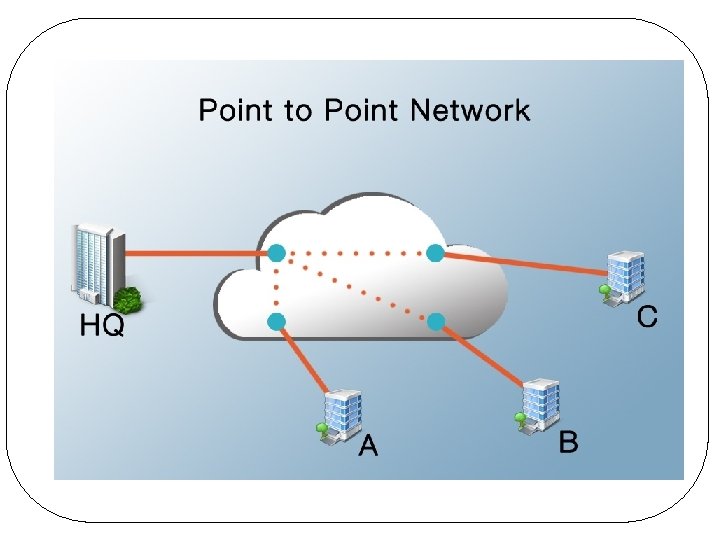
Point-to-Point Networks Many connections between pairs of machines l Intermediate machines (called routers) might have to be visited by a packet from source to destination – more than one path is possible l Routing algorithms are important l q. Routing: process of finding a path from a source to the destination(s) in the network


Local Area Network (LAN) Private-owned Networks l Within a single building/campus l Size: up to a few kilometers l Characteristics l q. Size ØRestricted by size worst-case transmission time bounded and known in advance network management simplified

LAN l Characteristics q. Transmission technology ØMachines attached to a single cable ØSpeed/capacity (High): 10 - 100 Mbps, Gbps § Mbps/Gbps: Megabit/Gigabit per second § 1 megabit=1, 000 (not 220=1, 048, 576) bits ØDelay (low): microseconds, nanoseconds ØErrors: very few

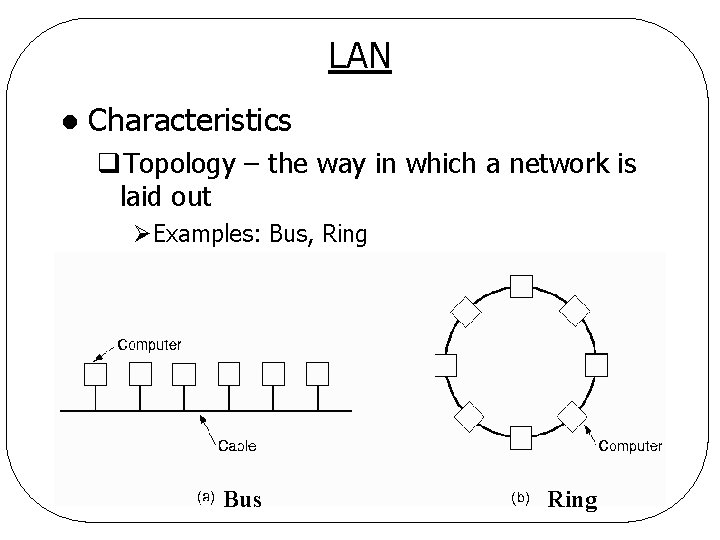
LAN l Characteristics q. Topology – the way in which a network is laid out ØExamples: Bus, Ring Bus Ring

Categories of topology

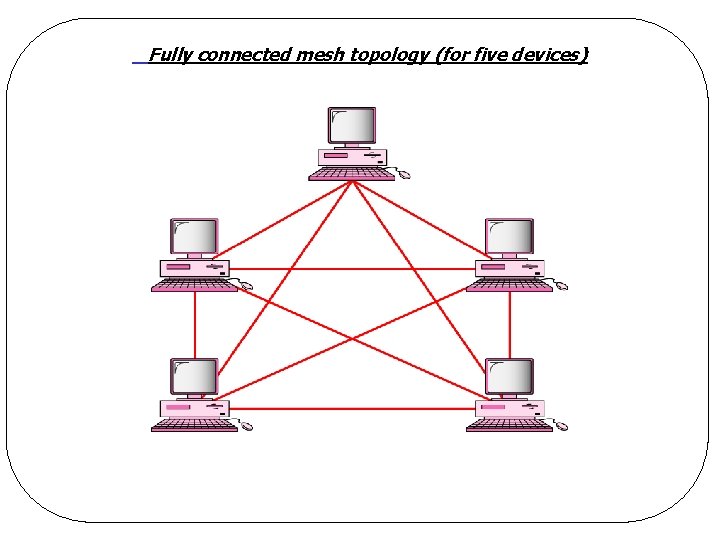
Fully connected mesh topology (for five devices)

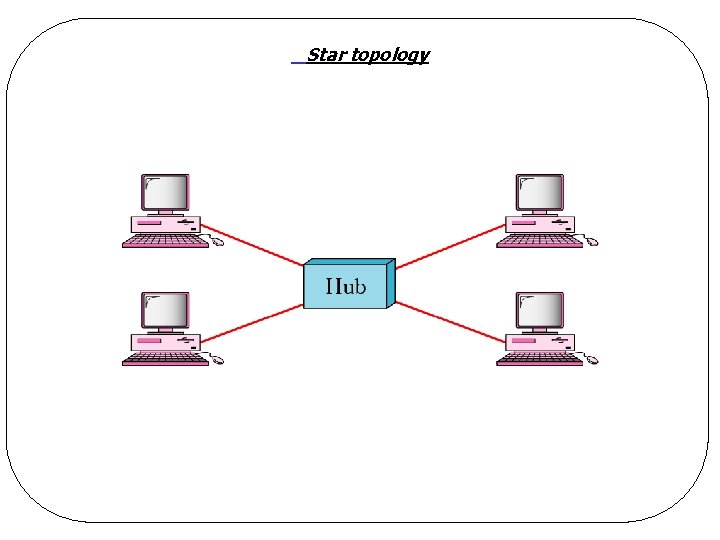
Star topology

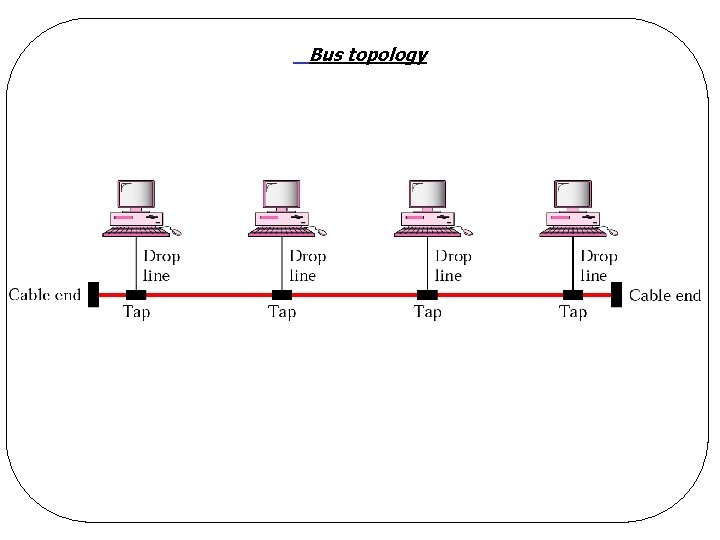
Bus topology

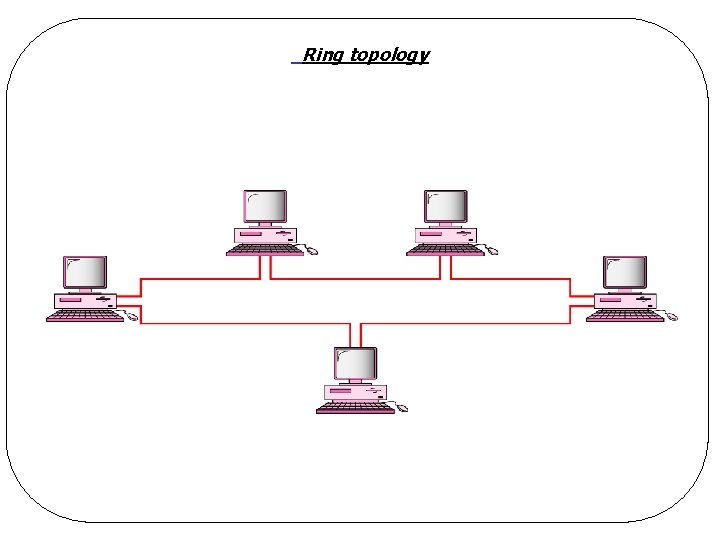
Ring topology

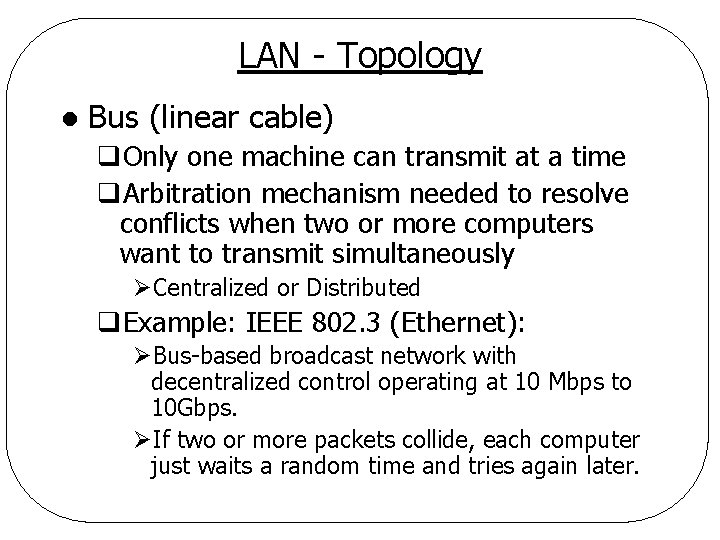
LAN - Topology l Bus (linear cable) q. Only one machine can transmit at a time q. Arbitration mechanism needed to resolve conflicts when two or more computers want to transmit simultaneously ØCentralized or Distributed q. Example: IEEE 802. 3 (Ethernet): ØBus-based broadcast network with decentralized control operating at 10 Mbps to 10 Gbps. ØIf two or more packets collide, each computer just waits a random time and tries again later.

LAN - Topology l Ring q. Bits propagate around the ring q. Arbitration mechanism is needed, too q. Example: IEEE 802. 5 (IBM Token Ring) ØRing-based LAN operating at 4 and 16 Mbps ØArbitration is based on “token” § Only token holder can transmit

LAN - Channel Allocation Needed as all computers share one communication pathway l Static channel allocation l q. Divide up time into discrete intervals q. Run a round robin algorithm q. Allow each machine to broadcast only when its time slot comes up q. Problem: Wasting channel capacity

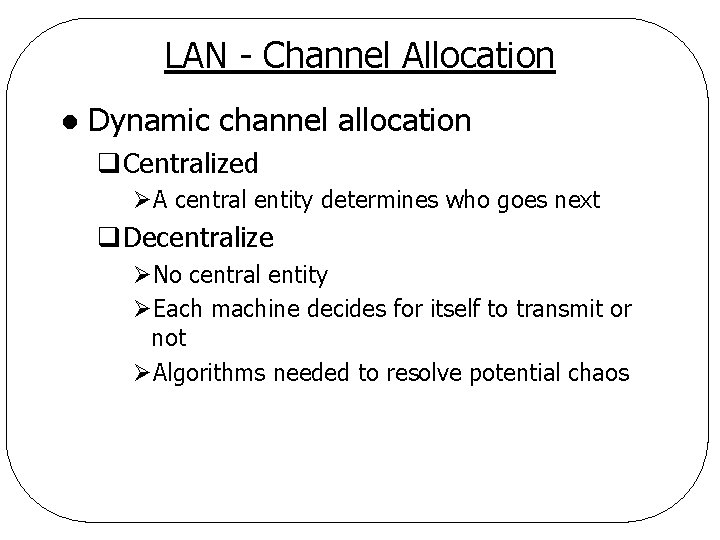
LAN - Channel Allocation l Dynamic channel allocation q. Centralized ØA central entity determines who goes next q. Decentralize ØNo central entity ØEach machine decides for itself to transmit or not ØAlgorithms needed to resolve potential chaos

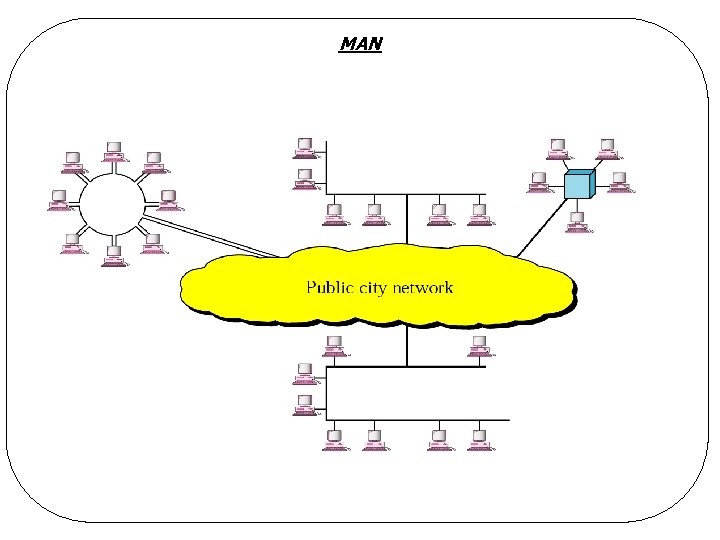
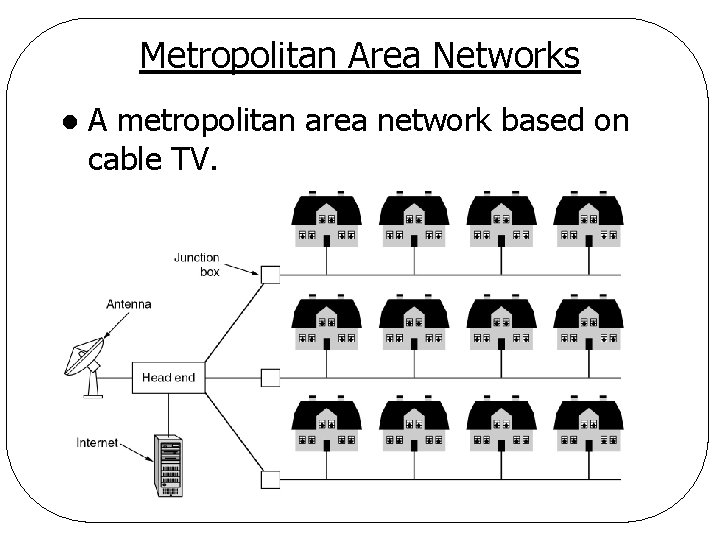
Metropolitan Area Network (MAN) Covers city l Examples l q. Cable TV network q. IEEE 802. 16 high-speed wireless Internet access

MAN

Metropolitan Area Networks l A metropolitan area network based on cable TV.

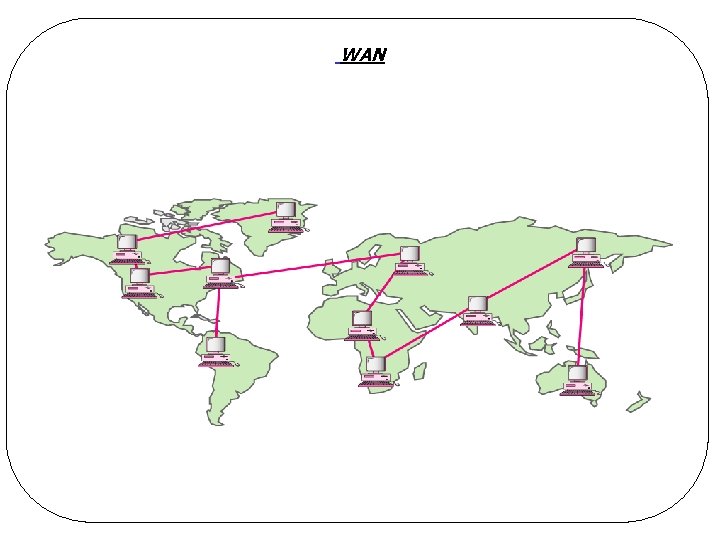
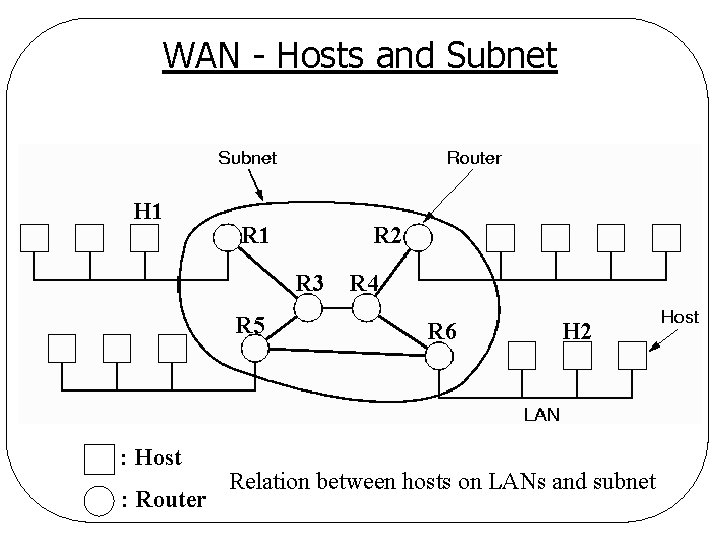
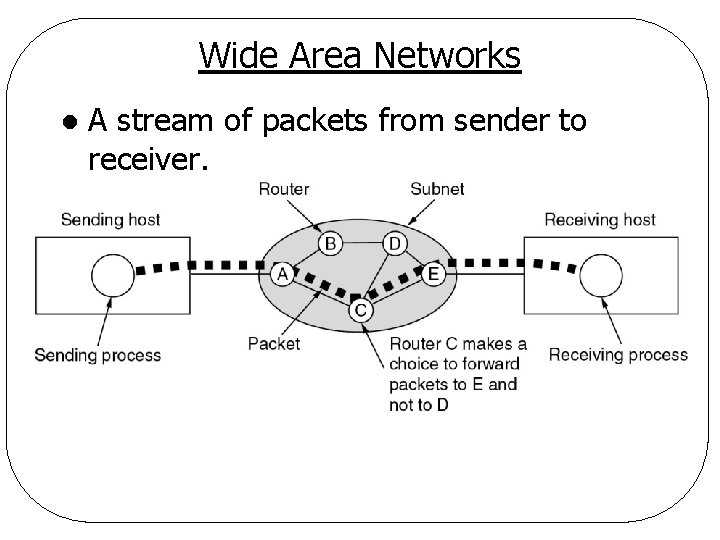
Wide Area Network (WAN) Country or continent l Components l q. Host (end system) ØMachine running user (application) programs q. Communication subnet (subnet) ØConnecting hosts ØCarrying messages from host to host

WAN

WAN - Subnet Components l Transmission lines q. Move bits between machines l Switching elements q. Specialized computers that connect two or more transmission lines q. Determine out going line for incoming data q. ROUTER

WAN - Hosts and Subnet H 1 R 2 R 3 R 5 : Host : Router R 4 R 6 H 2 Relation between hosts on LANs and subnet

WAN - Architecture Contains numerous cables or telephone lines l Each cable connects a pair of routers l Two routers must communicate indirectly if they are not connected by a cable l There might be more than one route between two hosts and it might change from time to time l q. E. g. , Route from H 1 to H 2

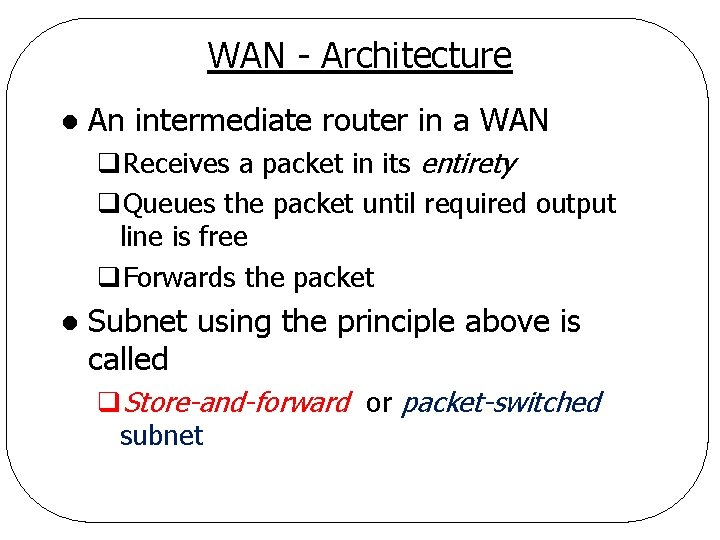
WAN - Architecture l An intermediate router in a WAN q. Receives a packet in its entirety q. Queues the packet until required output line is free q. Forwards the packet l Subnet using the principle above is called q. Store-and-forward or packet-switched subnet

Wide Area Networks l A stream of packets from sender to receiver.

WAN - Broadcast Systems l Satellite system q. Each router has an antenna q. Sometimes routers are connected to a substantial point-to-point subnet, with some of them having a satellite antenna q. Inherently broadcast

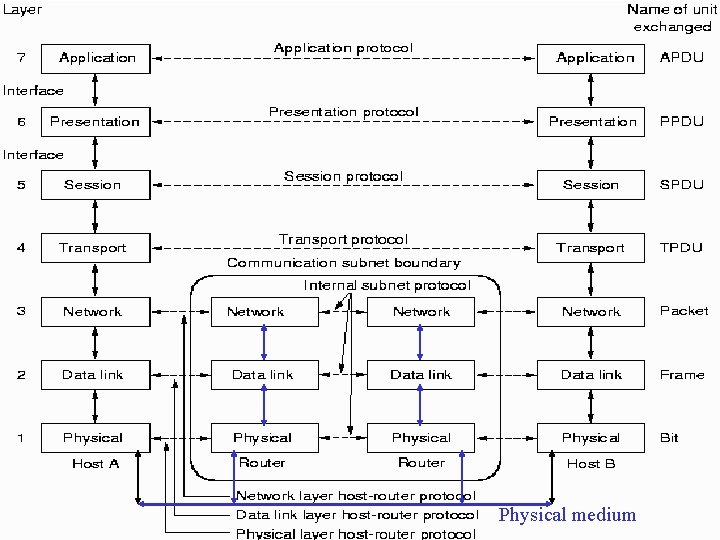
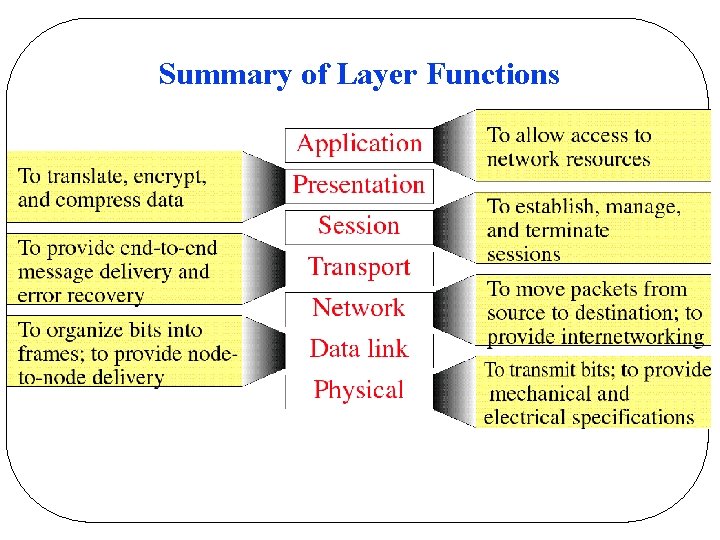
Protocol Hierarchies l Peers q. Entities comprising corresponding layers on different machines q. Virtual communication using protocol q. Peer process abstraction make network design becomes that of individual layers l Physical communication q. Sender: Data and control passed to layer below q. Data transmitted via physical media q. Receiver: Data and control passed to layer above

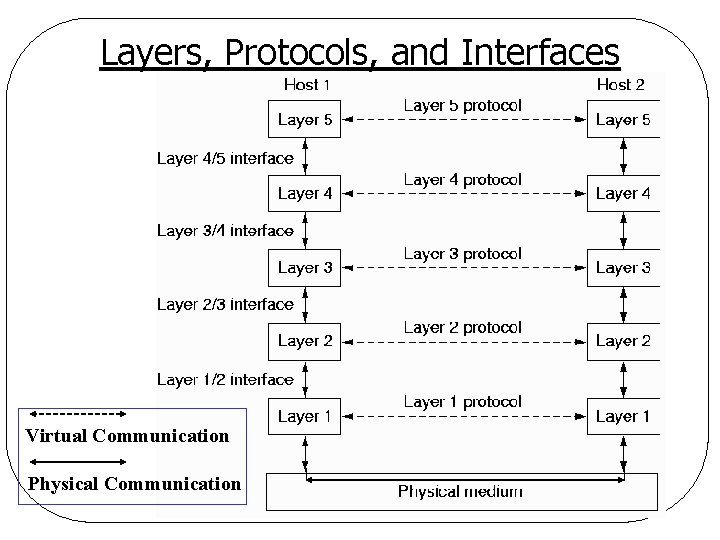
Layers, Protocols, and Interfaces Virtual Communication Physical Communication

Protocol Hierarchies l Interface between two adjacent layers q. Defines primitive operations and services a lower layer offers to the upper one q. Minimizes amount of information passed between two layers q. Simplifies replacement of implementation ØE. g. , telephone lines satellite channels

Protocol Hierarchies l Network architecture q. Set of layers and protocols q. Implementation and interface specification not included l Protocol stack q. A list of protocols used by a certain system, one protocol per layer

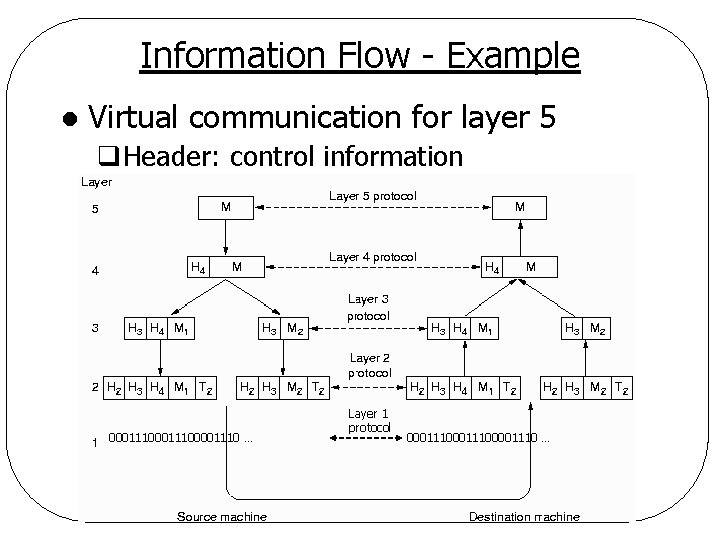
Information Flow - Example l Virtual communication for layer 5 q. Header: control information 00011100001110 … Layer 1 protocol 00011100001110 …

Reference Models l Two reference models will be discussed q. OSI reference model q. TCP/IP model

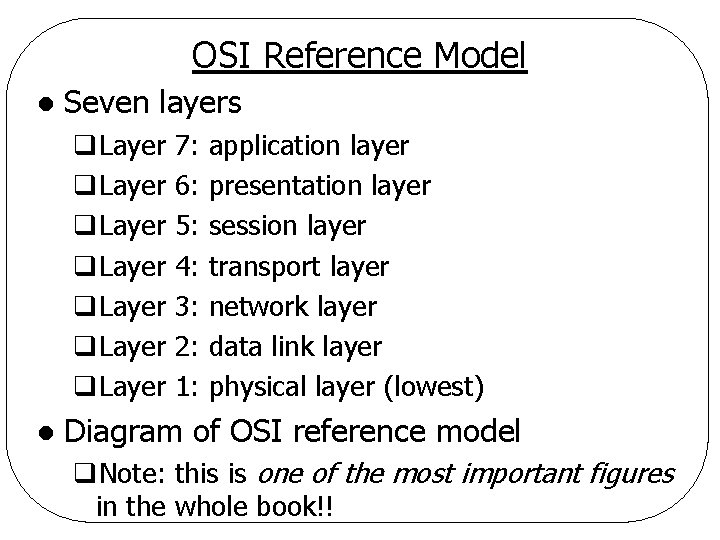
OSI Reference Model ISO/OSI (Open Systems Interconnection) Reference Model l NOT a network architecture itself l q. Exact services and protocols are not specified q. Just "what should be done" in each layer q. However, standards are produced for all layers

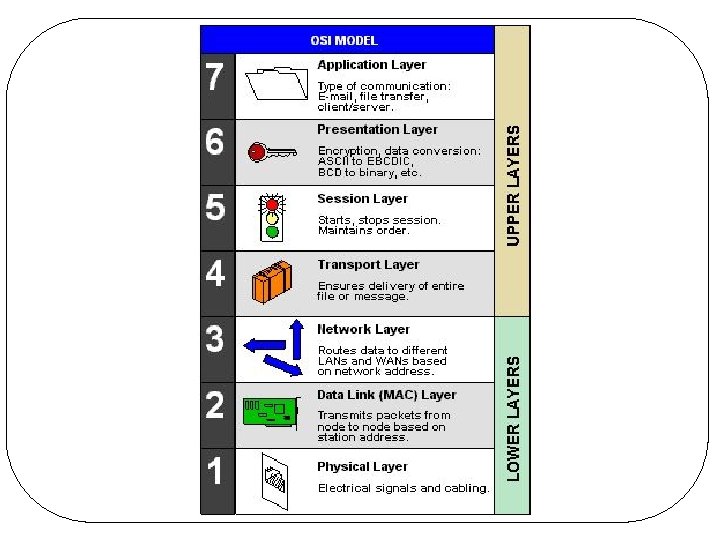
OSI Reference Model l Seven layers q. Layer q. Layer l 7: 6: 5: 4: 3: 2: 1: application layer presentation layer session layer transport layer network layer data link layer physical layer (lowest) Diagram of OSI reference model q. Note: this is one of the most important figures in the whole book!!

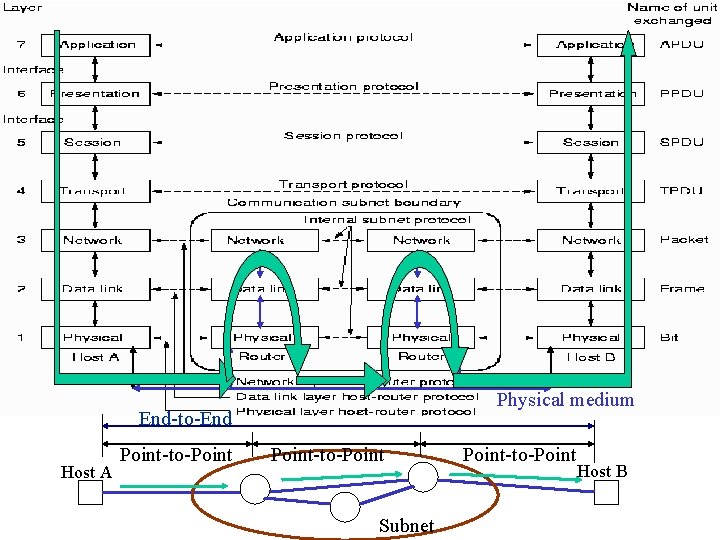
Physical medium


Physical medium End-to-End Host A Point-to-Point Subnet Point-to-Point Host B

Physical Layer Transmitting raw bits (0 s and 1 s) l Design issues l q. Representation of bits ØHow is 0/1 represented? q. Data rate: number of bits sent per second ØHow long does a bit last? q. Transmission mode q. Mechanical, electrical, procedural interfaces q. Underlying physical transmission medium

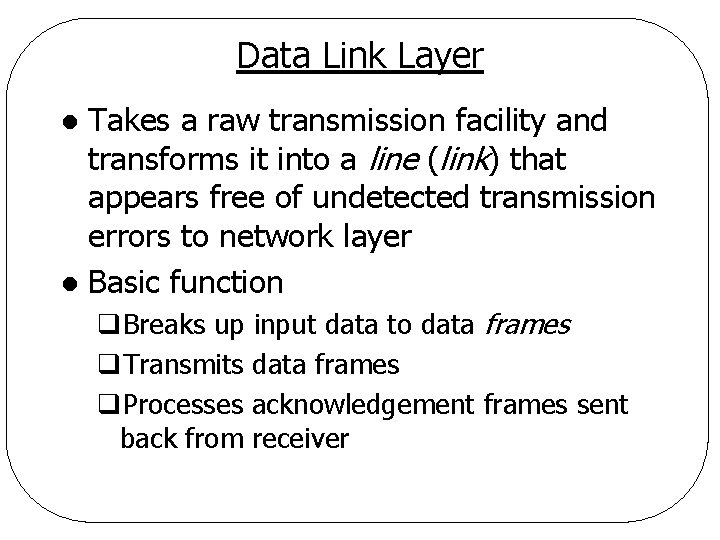
Data Link Layer Takes a raw transmission facility and transforms it into a line (link) that appears free of undetected transmission errors to network layer l Basic function l q. Breaks up input data to data frames q. Transmits data frames q. Processes acknowledgement frames sent back from receiver

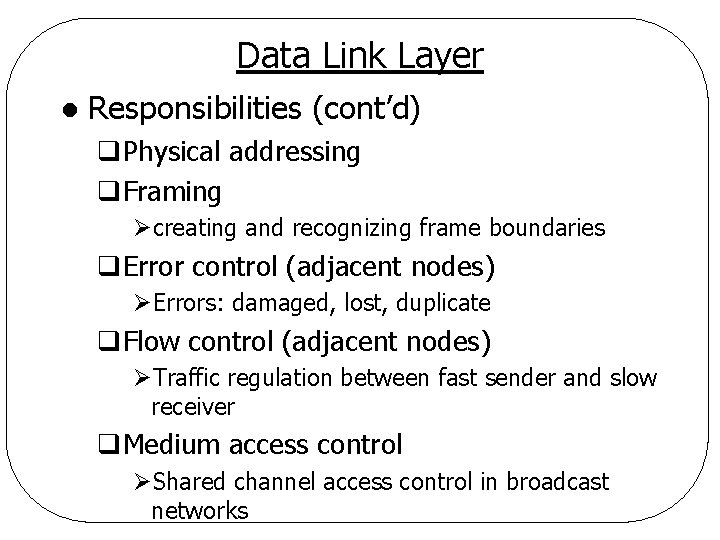
Data Link Layer l Responsibilities (cont’d) q. Physical addressing q. Framing Øcreating and recognizing frame boundaries q. Error control (adjacent nodes) ØErrors: damaged, lost, duplicate q. Flow control (adjacent nodes) ØTraffic regulation between fast sender and slow receiver q. Medium access control ØShared channel access control in broadcast networks

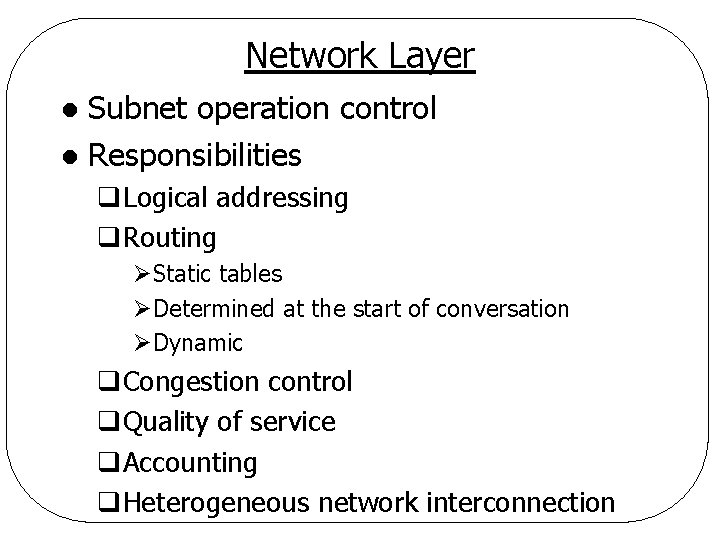
Network Layer Subnet operation control l Responsibilities l q. Logical addressing q. Routing ØStatic tables ØDetermined at the start of conversation ØDynamic q. Congestion control q. Quality of service q. Accounting q. Heterogeneous network interconnection

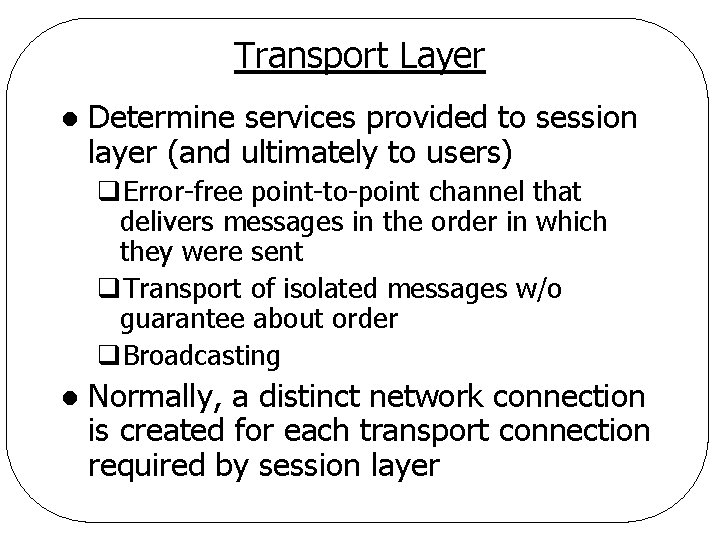
Transport Layer l End-to-end layer q. Talk to destination machine directly (virtually) q. Layers 4 through 7 are end-to-end q. Layers 1 through 3 are node-to-node l Basic function q. Split data from session layer into smaller units q. Pass units to network layer q. Ensure units arrive correctly at the other end

Transport Layer l Determine services provided to session layer (and ultimately to users) q. Error-free point-to-point channel that delivers messages in the order in which they were sent q. Transport of isolated messages w/o guarantee about order q. Broadcasting l Normally, a distinct network connection is created for each transport connection required by session layer

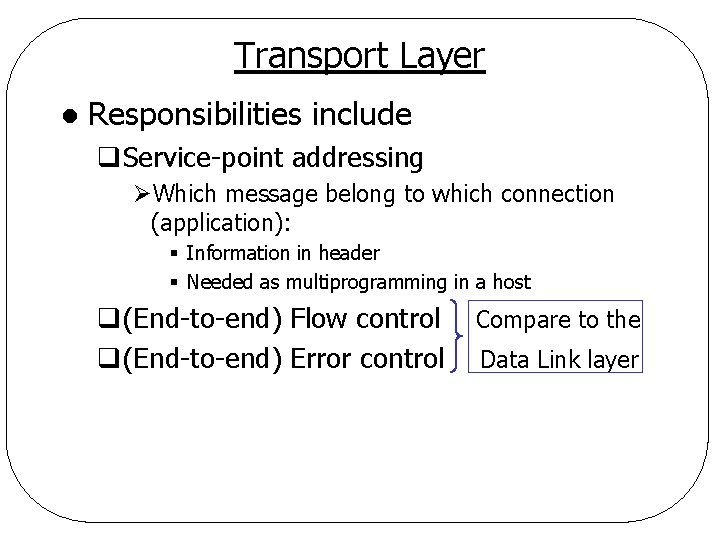
Transport Layer l Responsibilities include q. Service-point addressing ØWhich message belong to which connection (application): § Information in header § Needed as multiprogramming in a host q(End-to-end) Flow control q(End-to-end) Error control Compare to the Data Link layer

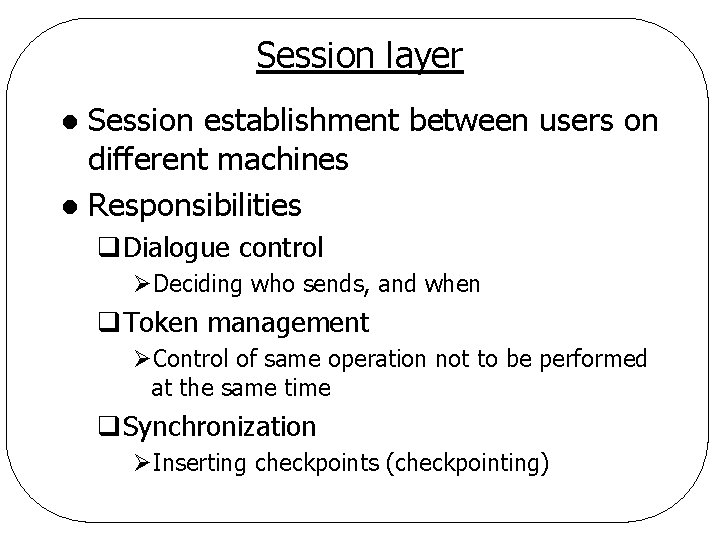
Session layer Session establishment between users on different machines l Responsibilities l q. Dialogue control ØDeciding who sends, and when q. Token management ØControl of same operation not to be performed at the same time q. Synchronization ØInserting checkpoints (checkpointing)

Presentation Layer Syntax/semantics of information l Responsibilities l q. Encoding ØConvert from data representation used in one host to the standard abstract data structure and back q. Encryption q. Compression

Application Layer Provides interface and support for services to users (human, software, robots) l Application services l q. Network virtual terminal (telnet) q. File transfer q. Email q. Network management q. Hypertext transfer

Summary of Layer Functions


TCP/IP Reference Model l Goals q. Internetworking q. Fault tolerance q. Flexible architecture l Four layers of TCP/IP Reference Model q. Host-to-network layer q. Internet layer q. Transport layer q. Application layer

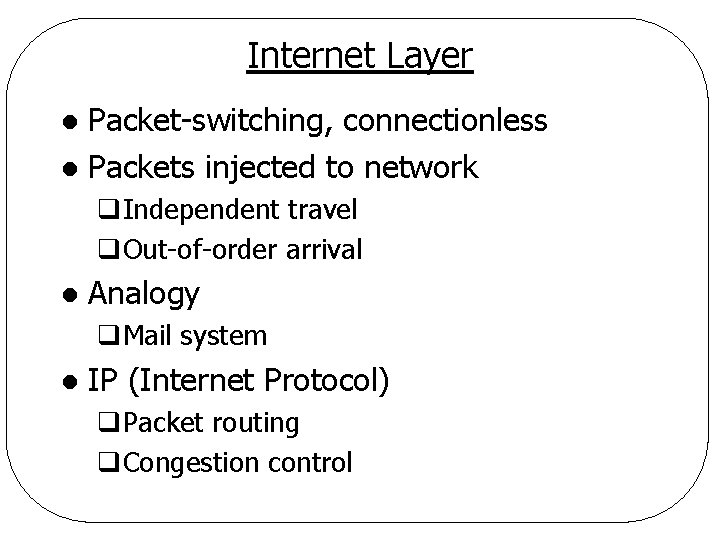
Internet Layer Packet-switching, connectionless l Packets injected to network l q. Independent travel q. Out-of-order arrival l Analogy q. Mail system l IP (Internet Protocol) q. Packet routing q. Congestion control

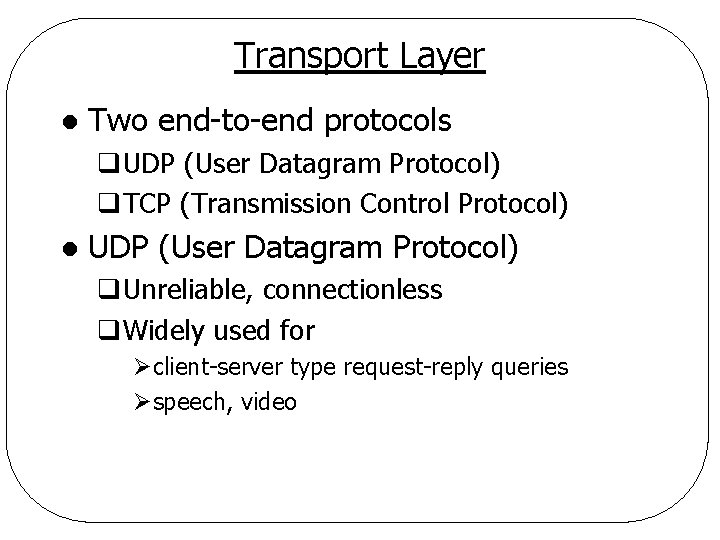
Transport Layer l Two end-to-end protocols q. UDP (User Datagram Protocol) q. TCP (Transmission Control Protocol) l UDP (User Datagram Protocol) q. Unreliable, connectionless q. Widely used for Øclient-server type request-reply queries Øspeech, video

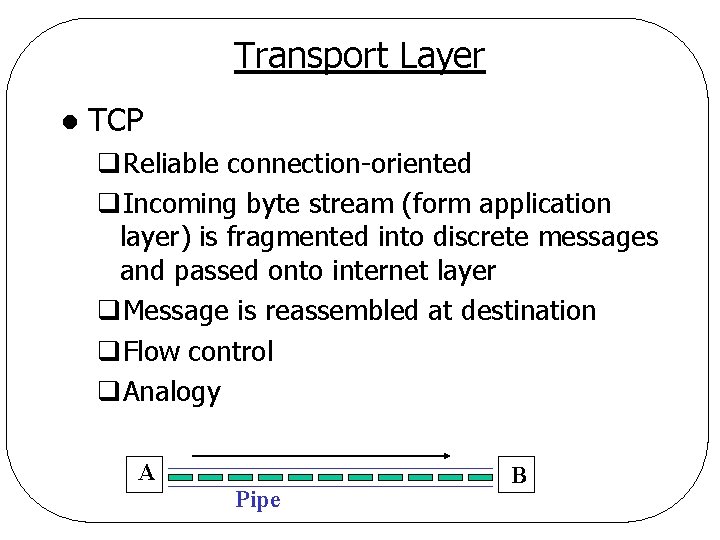
Transport Layer l TCP q. Reliable connection-oriented q. Incoming byte stream (form application layer) is fragmented into discrete messages and passed onto internet layer q. Message is reassembled at destination q. Flow control q. Analogy A Pipe B

Applications and Host-to-Network Layers l Application layer q. No session and presentation layers q. TELNET, FTP, SMTP, DNS, NNTP, HTTP l Host-to-network layer q. Host has to connect to to the network using some protocol so it can send IP packets

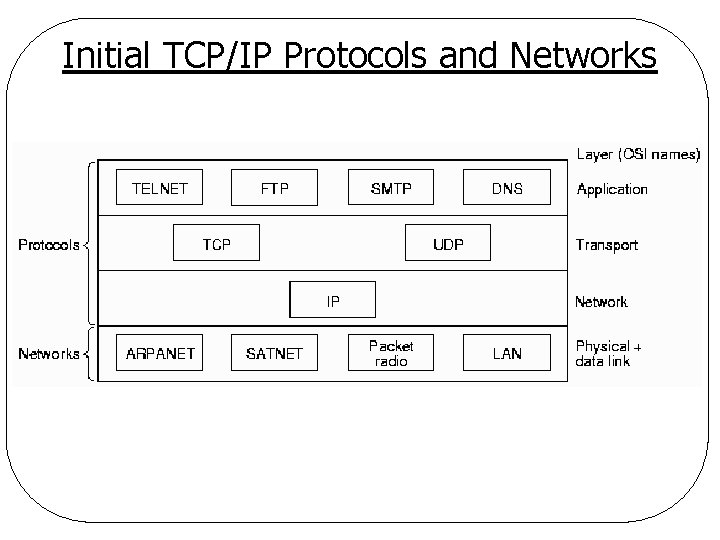
Initial TCP/IP Protocols and Networks

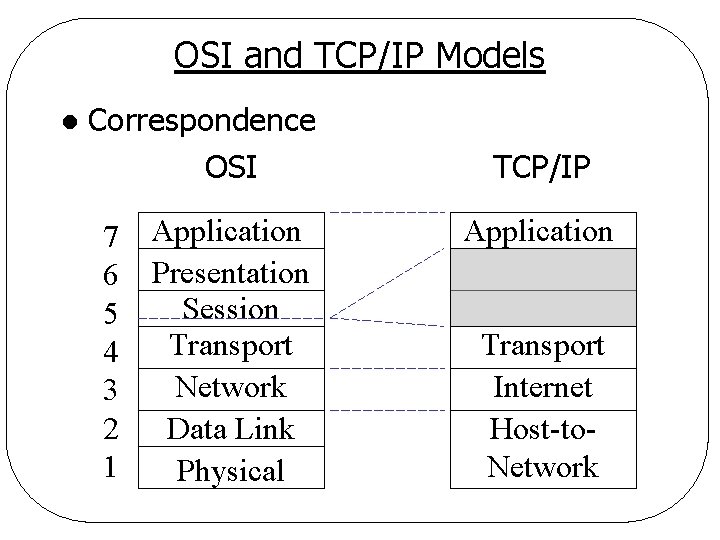
OSI and TCP/IP Models l Correspondence OSI 7 6 5 4 3 2 1 Application Presentation Session Transport Network Data Link Physical TCP/IP Application Transport Internet Host-to. Network

OSI and TCP/IP Models l Similarities q. Stack of independent protocols q. Layer functionality q. Transport layer q. Application layer

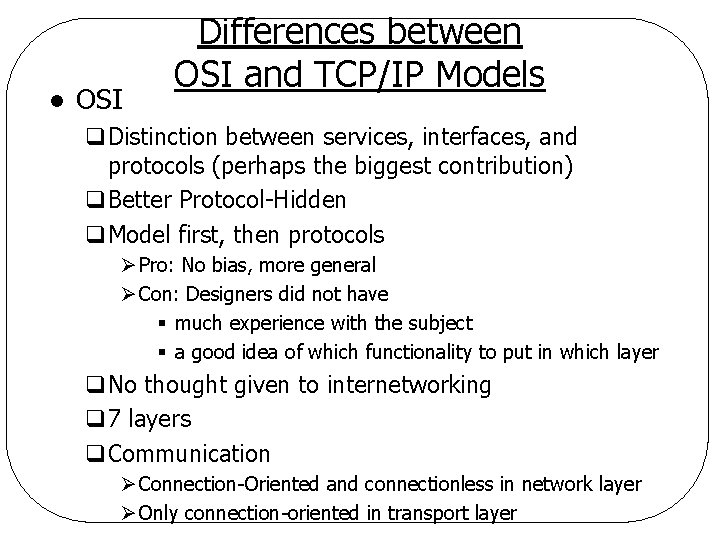
l OSI Differences between OSI and TCP/IP Models q. Distinction between services, interfaces, and protocols (perhaps the biggest contribution) q. Better Protocol-Hidden q. Model first, then protocols Ø Pro: No bias, more general Ø Con: Designers did not have § much experience with the subject § a good idea of which functionality to put in which layer q. No thought given to internetworking q 7 layers q. Communication Ø Connection-Oriented and connectionless in network layer Ø Only connection-oriented in transport layer

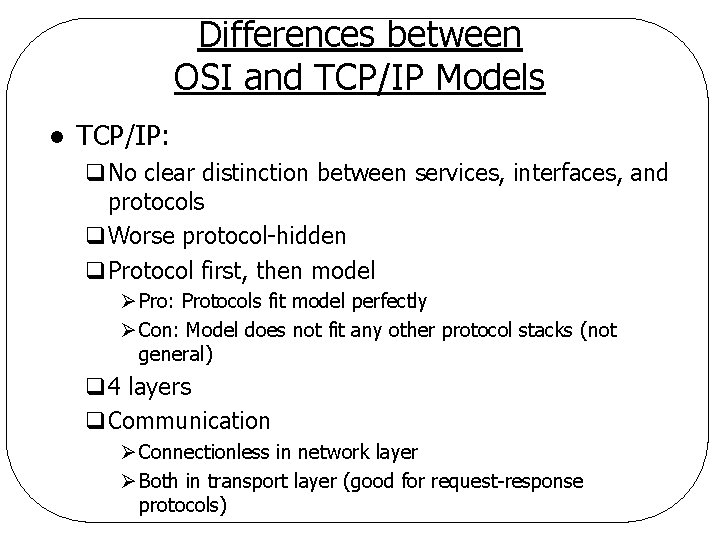
Differences between OSI and TCP/IP Models l TCP/IP: q. No clear distinction between services, interfaces, and protocols q. Worse protocol-hidden q. Protocol first, then model Ø Pro: Protocols fit model perfectly Ø Con: Model does not fit any other protocol stacks (not general) q 4 layers q. Communication Ø Connectionless in network layer Ø Both in transport layer (good for request-response protocols)

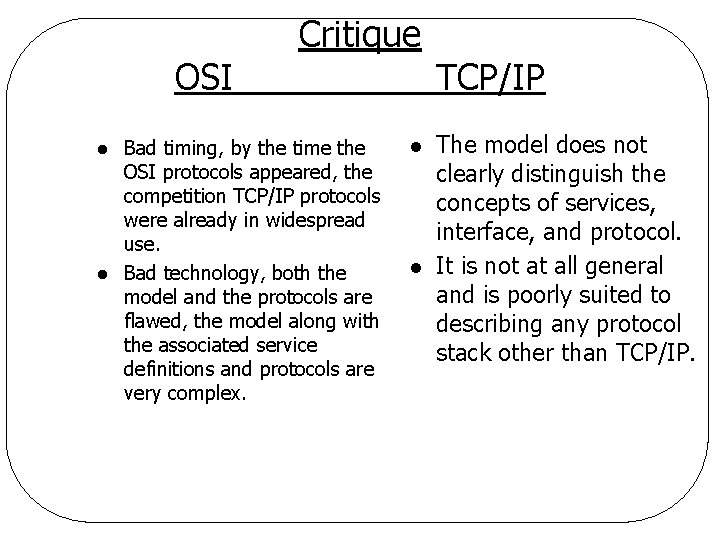
OSI l l Critique Bad timing, by the time the OSI protocols appeared, the competition TCP/IP protocols were already in widespread use. Bad technology, both the model and the protocols are flawed, the model along with the associated service definitions and protocols are very complex. l l TCP/IP The model does not clearly distinguish the concepts of services, interface, and protocol. It is not at all general and is poorly suited to describing any protocol stack other than TCP/IP.

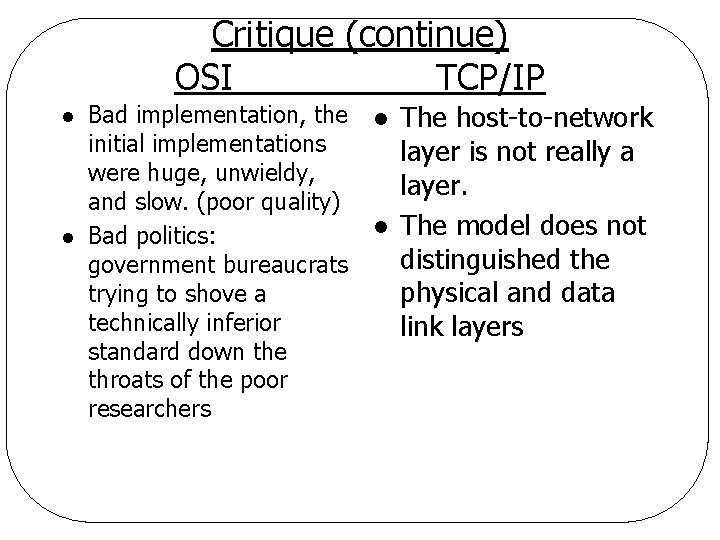
Critique (continue) OSI TCP/IP l l Bad implementation, the initial implementations were huge, unwieldy, and slow. (poor quality) Bad politics: government bureaucrats trying to shove a technically inferior standard down the throats of the poor researchers l l The host-to-network layer is not really a layer. The model does not distinguished the physical and data link layers

Example Networks ARPANET l NSFNET l The Internet l Connection-Oriented Networks l q. X. 25, Frame Relay, and ATM Ethernet l Wireless LANs: 802: 11 l