Intro to Software System Modeling Model vs Design



- Slides: 23

Intro to Software System Modeling

Model vs Design o Model n may be used in the SRS o o n o used by the software designers may be useful as an overview for the programmers may be used for validation with the customer Design n what the programmers are told to build

What info is modeled? o Relationships between Data Process Flow Data Transformation o Control Flow within the source code o Format of the Database o Timing constraints (real-time systems) User Interface Flow etc… o o

Major Modeling and Design Diagrams o UML o Data Flow Diagrams o State Transition Diagrams o Structure Charts o Entity Relationship Diagrams o Use Cases

Data Flow Diagrams o o o Illustrate how processes transform data Very good for modeling a system at a high level, e. g. for the SRS Poor at conveying design of software, except a few cases such as distributed systems process external entity data file data flow

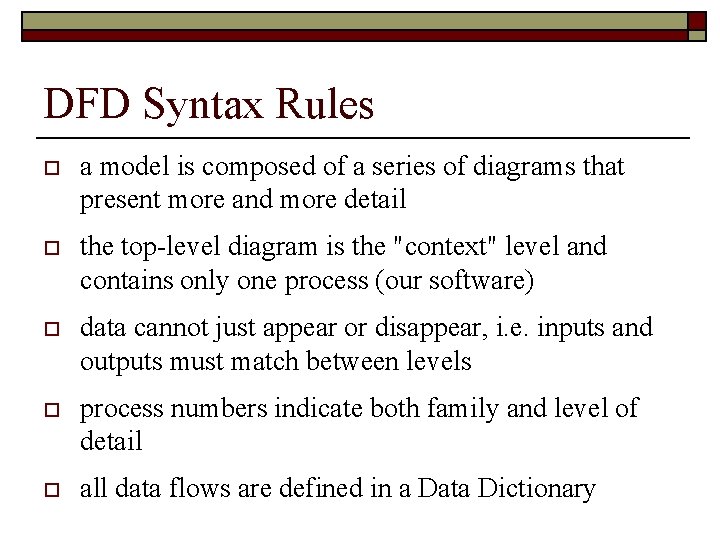
DFD Syntax Rules o a model is composed of a series of diagrams that present more and more detail o the top-level diagram is the "context" level and contains only one process (our software) o data cannot just appear or disappear, i. e. inputs and outputs must match between levels o process numbers indicate both family and level of detail o all data flows are defined in a Data Dictionary

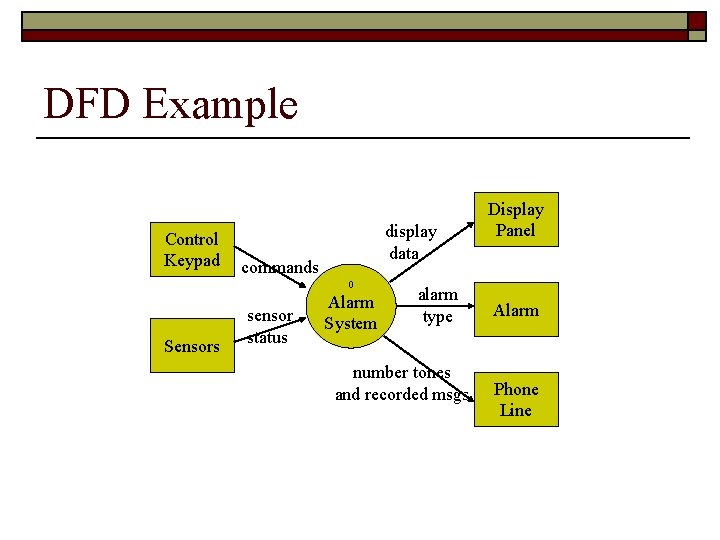
DFD Example Control Keypad display data commands 0 Sensors sensor status Alarm System alarm type number tones and recorded msgs Display Panel Alarm Phone Line

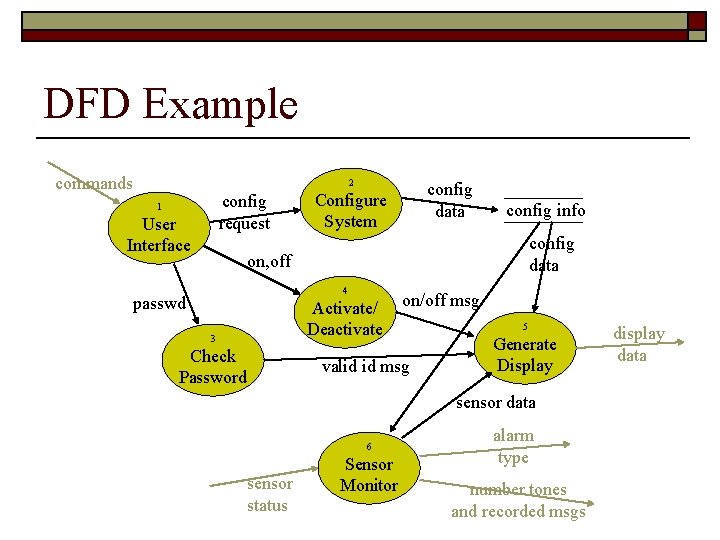
DFD Example commands 2 config request 1 User Interface config data Configure System config info config data on, off 4 passwd Activate/ Deactivate 3 Check Password on/off msg valid id msg 5 Generate Display sensor data 6 sensor status Sensor Monitor alarm type number tones and recorded msgs display data

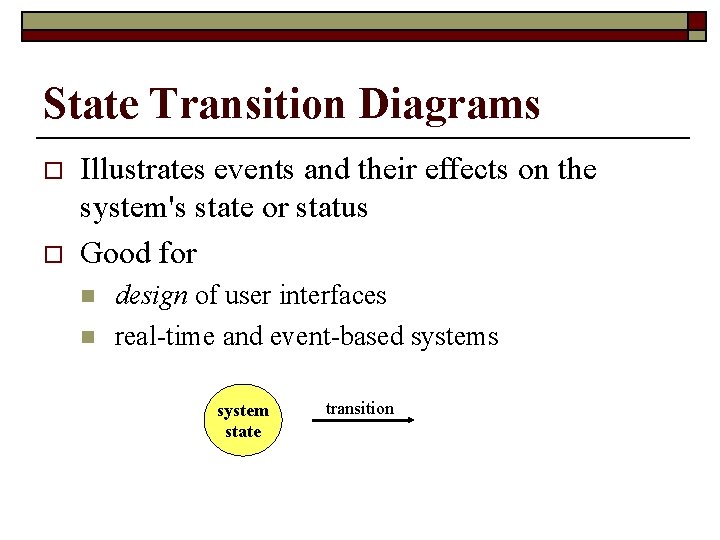
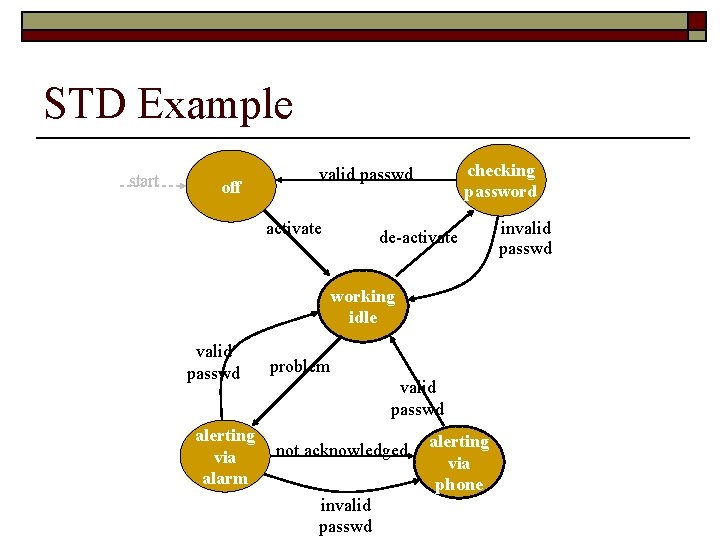
State Transition Diagrams o o Illustrates events and their effects on the system's state or status Good for n n design of user interfaces real-time and event-based systems system state transition

STD Example start off checking password valid passwd activate de-activate working idle valid passwd alerting via alarm problem valid passwd not acknowledged invalid passwd alerting via phone invalid passwd

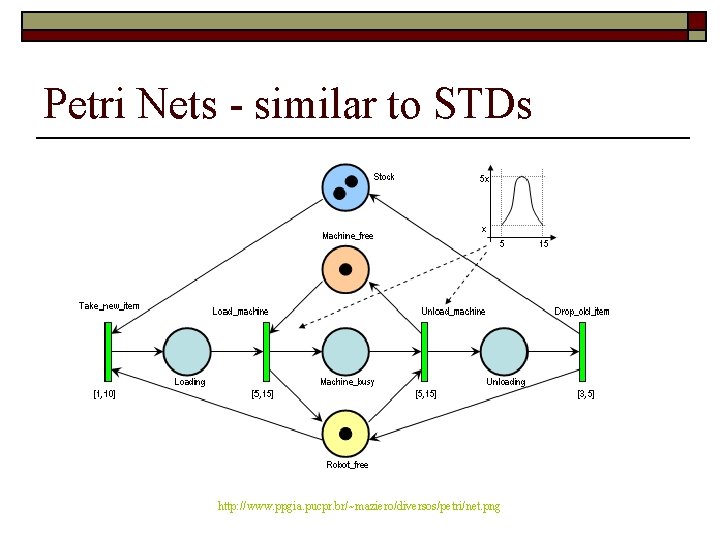
Petri Nets - similar to STDs http: //www. ppgia. pucpr. br/~maziero/diversos/petri/net. png

Structure Charts o o o Illustrates Control Flow Very good for conveying the design of source code Very inappropriate for modeling a system in a SRS module

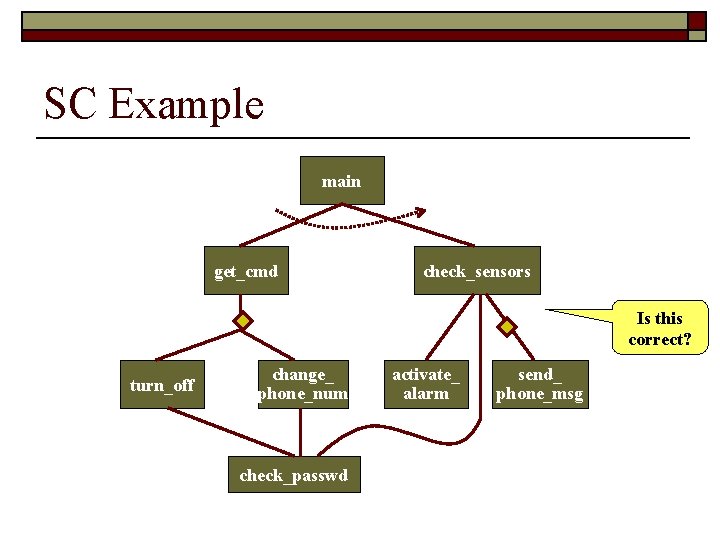
SC Syntax Rules o o o o one single tree for entire system tree has one node at the top nodes are individual code units / modules nodes call nodes below them nodes are called left to right leaf nodes are usually utility modules may show data flow may show conditionals and loops

SC Example main get_cmd check_sensors Is this correct? turn_off change_ phone_num check_passwd activate_ alarm send_ phone_msg

SC Example main get_cmd turn_off change_ phone check_passwd check_sensors activate_ alarm send_ phone_msg

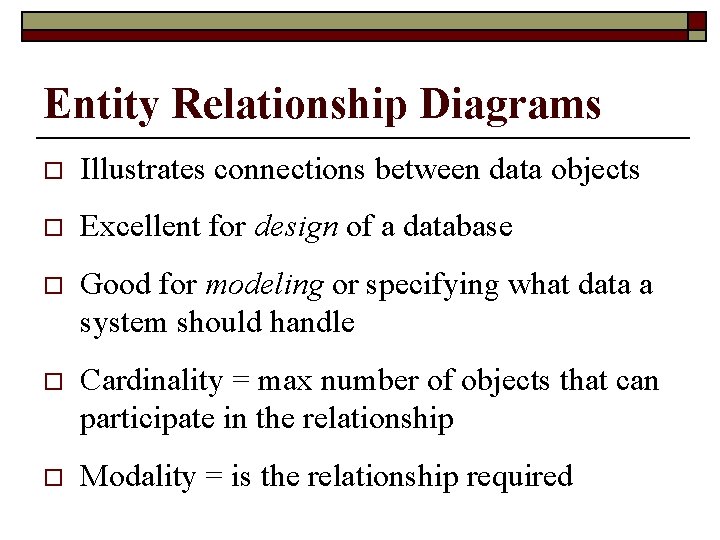
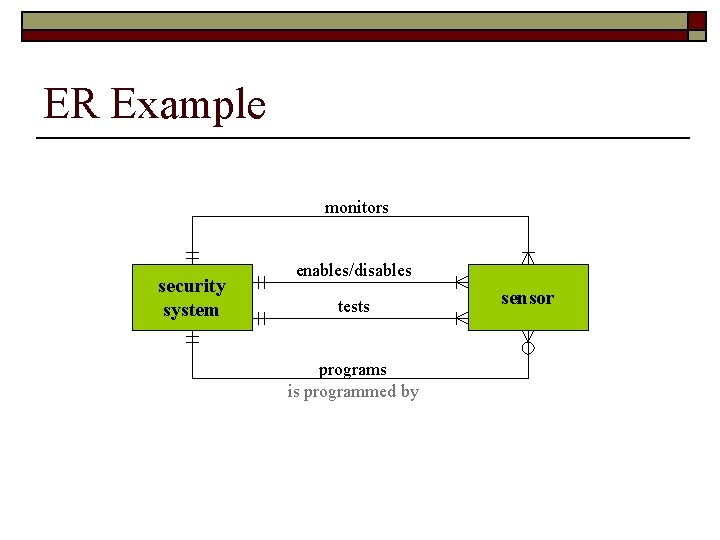
Entity Relationship Diagrams o Illustrates connections between data objects o Excellent for design of a database o Good for modeling or specifying what data a system should handle o Cardinality = max number of objects that can participate in the relationship o Modality = is the relationship required

ER Example monitors security system enables/disables tests programs is programmed by sensor

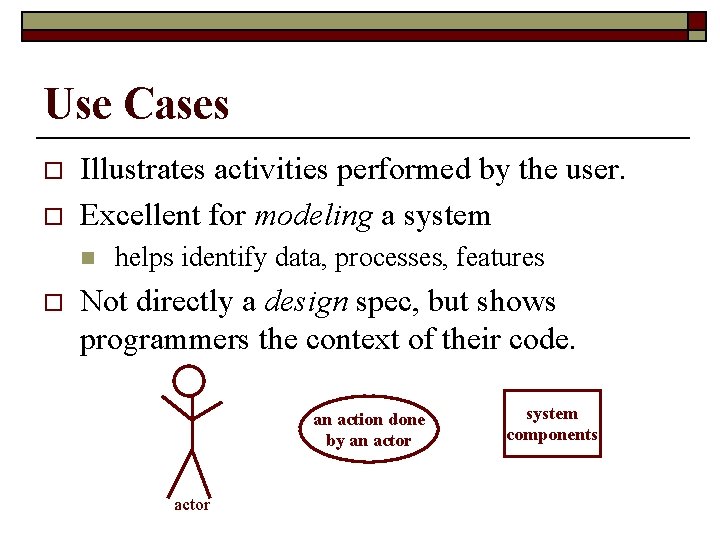
Use Cases o o Illustrates activities performed by the user. Excellent for modeling a system n o helps identify data, processes, features Not directly a design spec, but shows programmers the context of their code. an action done by an actor system components

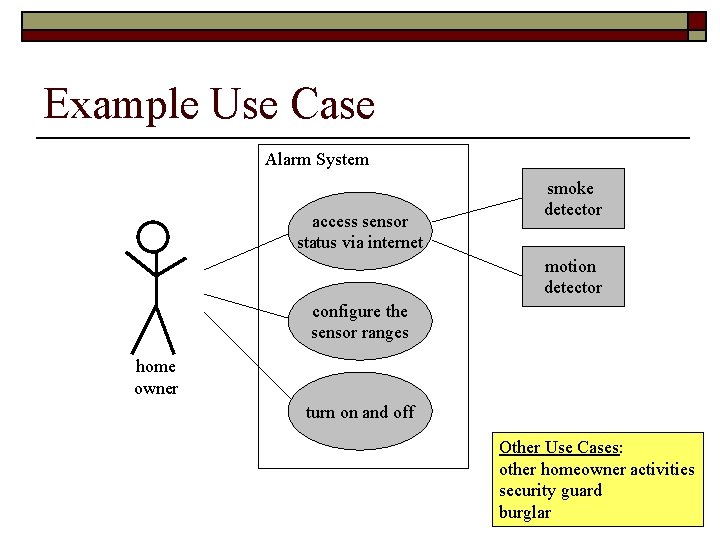
Example Use Case Alarm System access sensor status via internet smoke detector motion detector configure the sensor ranges home owner turn on and off Other Use Cases: other homeowner activities security guard burglar

Use Cases for System Modeling

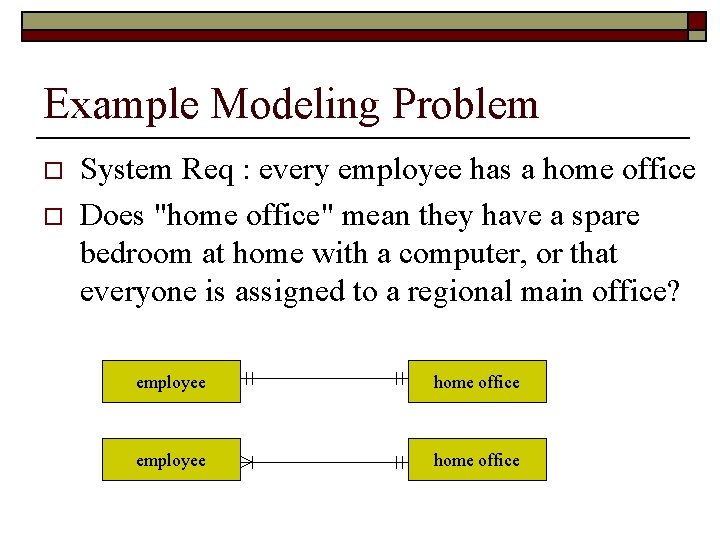
Example Modeling Problem o o System Req : every employee has a home office Does "home office" mean they have a spare bedroom at home with a computer, or that everyone is assigned to a regional main office? employee home office

Example Modeling Problem o o Any user can delete a regular file, but deleting a reserved file must require a password confirmation. Unclear : can any user delete a "reserved file"? How do we show that Requirement in the SRS? How do we show that in the Design?

Summary o Good for Modeling: n Use Cases n n DFDs n n process / how the data is transformed ERs n o what the user wants to do structure and nature of the data Good for Design: n n Structure Charts ERs