INTRO TO SECURING WINDOWS OS OVERVIEW Set up







- Slides: 19

INTRO TO SECURING WINDOWS OS

OVERVIEW • Set up. iso in VM • User names/ passwords • File permissions • Anti virus • Firewall

SETUP ISO IN VM • Open vmware • Drag iso file to vm • Load iso with default setting • Input windows key

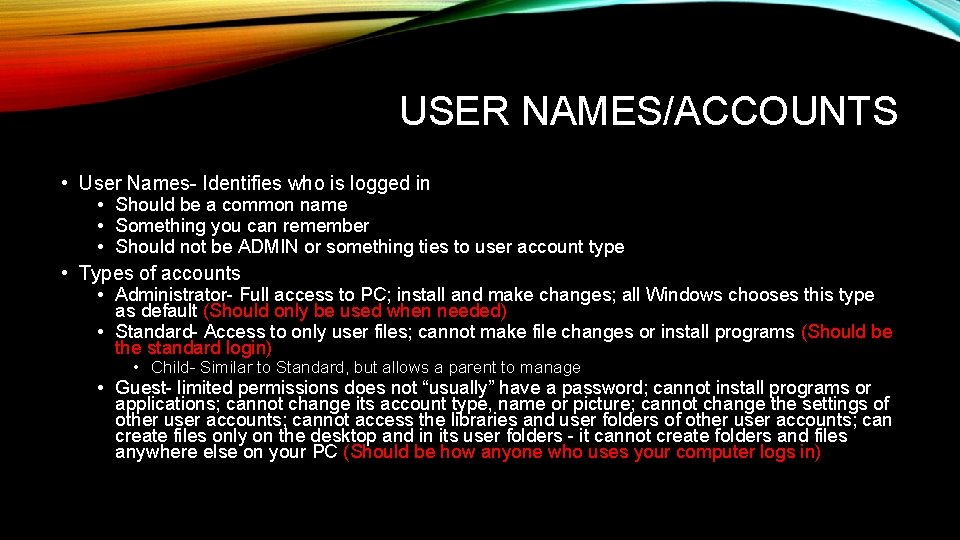
USER NAMES/ACCOUNTS • User Names- Identifies who is logged in • Should be a common name • Something you can remember • Should not be ADMIN or something ties to user account type • Types of accounts • Administrator- Full access to PC; install and make changes; all Windows chooses this type as default (Should only be used when needed) • Standard- Access to only user files; cannot make file changes or install programs (Should be the standard login) • Child- Similar to Standard, but allows a parent to manage • Guest- limited permissions does not “usually” have a password; cannot install programs or applications; cannot change its account type, name or picture; cannot change the settings of other user accounts; cannot access the libraries and user folders of other user accounts; can create files only on the desktop and in its user folders - it cannot create folders and files anywhere else on your PC (Should be how anyone who uses your computer logs in)

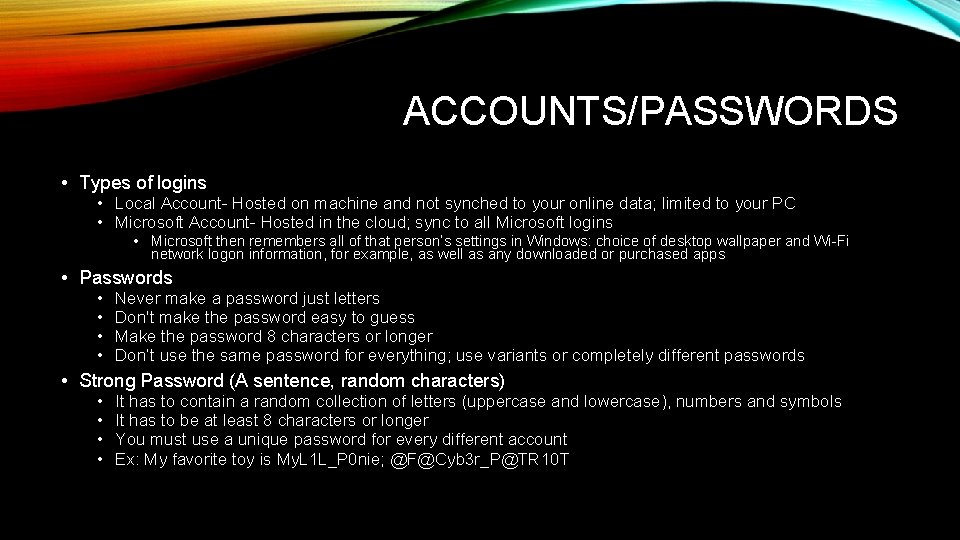
ACCOUNTS/PASSWORDS • Types of logins • Local Account- Hosted on machine and not synched to your online data; limited to your PC • Microsoft Account- Hosted in the cloud; sync to all Microsoft logins • Microsoft then remembers all of that person’s settings in Windows: choice of desktop wallpaper and Wi-Fi network logon information, for example, as well as any downloaded or purchased apps • Passwords • • Never make a password just letters Don't make the password easy to guess Make the password 8 characters or longer Don’t use the same password for everything; use variants or completely different passwords • Strong Password (A sentence, random characters) • • It has to contain a random collection of letters (uppercase and lowercase), numbers and symbols It has to be at least 8 characters or longer You must use a unique password for every different account Ex: My favorite toy is My. L 1 L_P 0 nie; @F@Cyb 3 r_P@TR 10 T

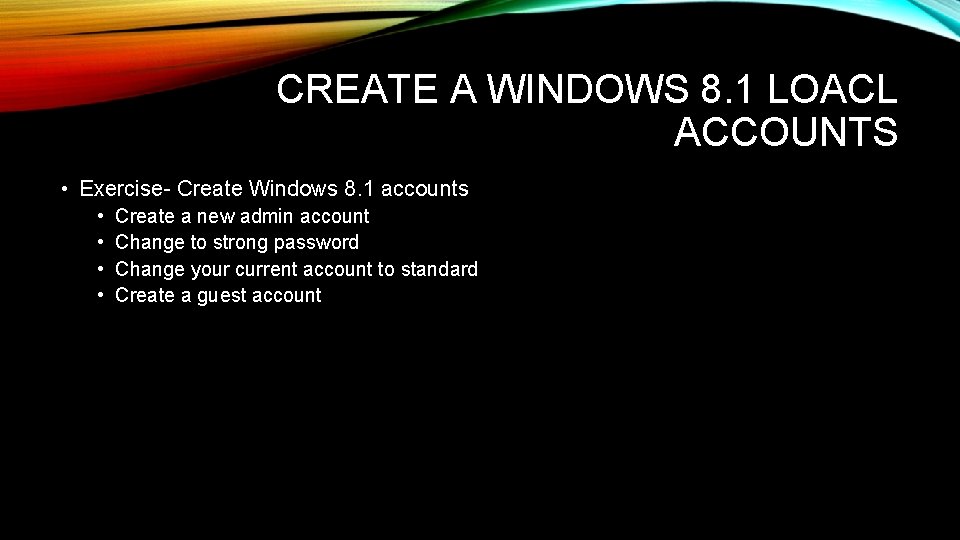
CREATE A WINDOWS 8. 1 LOACL ACCOUNTS • Exercise- Create Windows 8. 1 accounts • • Create a new admin account Change to strong password Change your current account to standard Create a guest account

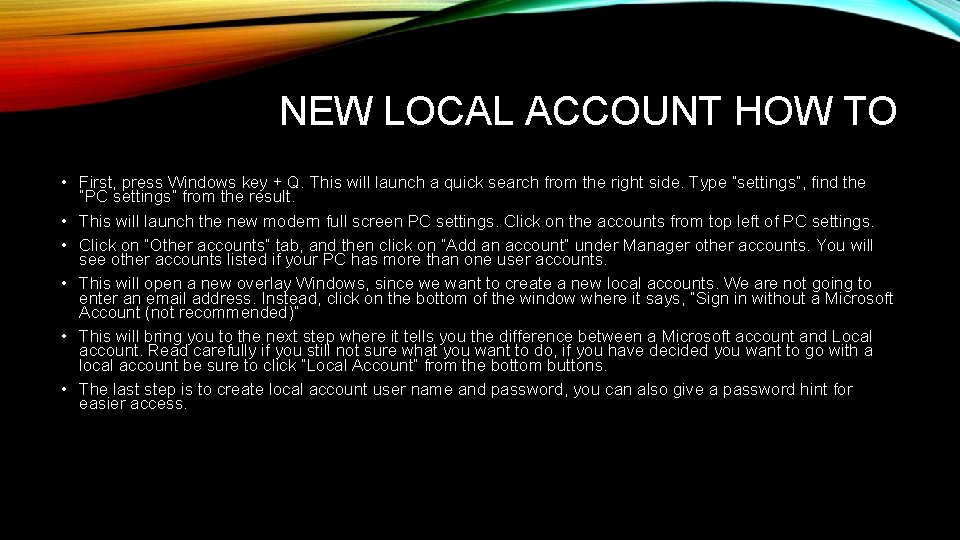
NEW LOCAL ACCOUNT HOW TO • First, press Windows key + Q. This will launch a quick search from the right side. Type “settings”, find the “PC settings” from the result. • This will launch the new modern full screen PC settings. Click on the accounts from top left of PC settings. • Click on “Other accounts” tab, and then click on “Add an account” under Manager other accounts. You will see other accounts listed if your PC has more than one user accounts. • This will open a new overlay Windows, since we want to create a new local accounts. We are not going to enter an email address. Instead, click on the bottom of the window where it says, “Sign in without a Microsoft Account (not recommended)” • This will bring you to the next step where it tells you the difference between a Microsoft account and Local account. Read carefully if you still not sure what you want to do, if you have decided you want to go with a local account be sure to click “Local Account” from the bottom buttons. • The last step is to create local account user name and password, you can also give a password hint for easier access.

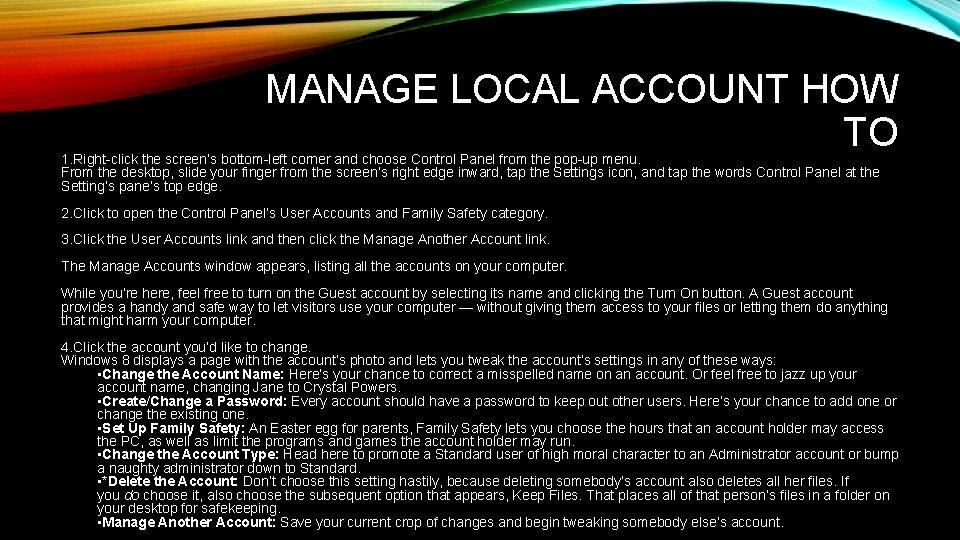
MANAGE LOCAL ACCOUNT HOW TO 1. Right-click the screen’s bottom-left corner and choose Control Panel from the pop-up menu. From the desktop, slide your finger from the screen’s right edge inward, tap the Settings icon, and tap the words Control Panel at the Setting’s pane’s top edge. 2. Click to open the Control Panel’s User Accounts and Family Safety category. 3. Click the User Accounts link and then click the Manage Another Account link. The Manage Accounts window appears, listing all the accounts on your computer. While you’re here, feel free to turn on the Guest account by selecting its name and clicking the Turn On button. A Guest account provides a handy and safe way to let visitors use your computer — without giving them access to your files or letting them do anything that might harm your computer. 4. Click the account you’d like to change. Windows 8 displays a page with the account’s photo and lets you tweak the account’s settings in any of these ways: • Change the Account Name: Here’s your chance to correct a misspelled name on an account. Or feel free to jazz up your account name, changing Jane to Crystal Powers. • Create/Change a Password: Every account should have a password to keep out other users. Here’s your chance to add one or change the existing one. • Set Up Family Safety: An Easter egg for parents, Family Safety lets you choose the hours that an account holder may access the PC, as well as limit the programs and games the account holder may run. • Change the Account Type: Head here to promote a Standard user of high moral character to an Administrator account or bump a naughty administrator down to Standard. • *Delete the Account: Don’t choose this setting hastily, because deleting somebody’s account also deletes all her files. If you do choose it, also choose the subsequent option that appears, Keep Files. That places all of that person’s files in a folder on your desktop for safekeeping. • Manage Another Account: Save your current crop of changes and begin tweaking somebody else’s account.

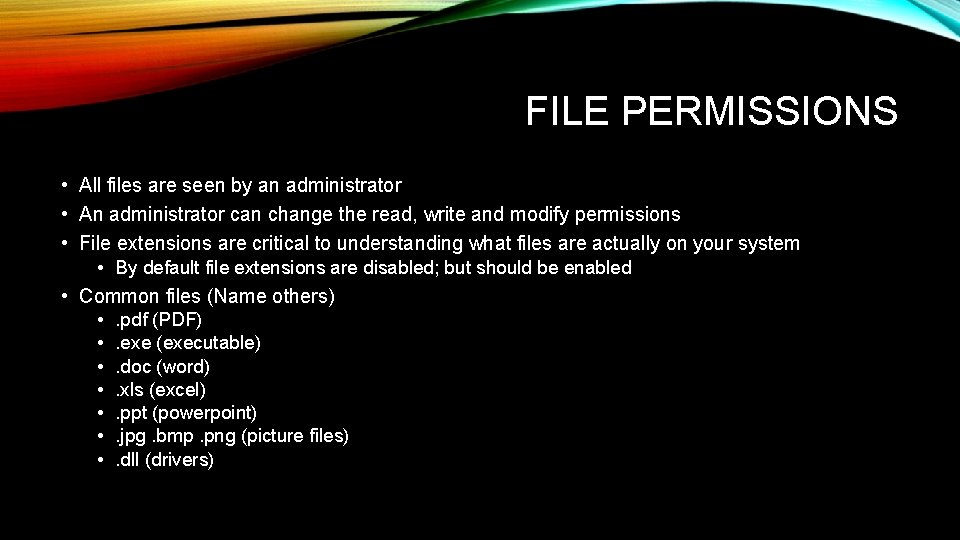
FILE PERMISSIONS • All files are seen by an administrator • An administrator can change the read, write and modify permissions • File extensions are critical to understanding what files are actually on your system • By default file extensions are disabled; but should be enabled • Common files (Name others) • . pdf (PDF) • . exe (executable) • . doc (word) • . xls (excel) • . ppt (powerpoint) • . jpg. bmp. png (picture files) • . dll (drivers)

SHOW FILE EXTENSIONS • Exercise- Enable show file extensions • Show file extensions on admin account

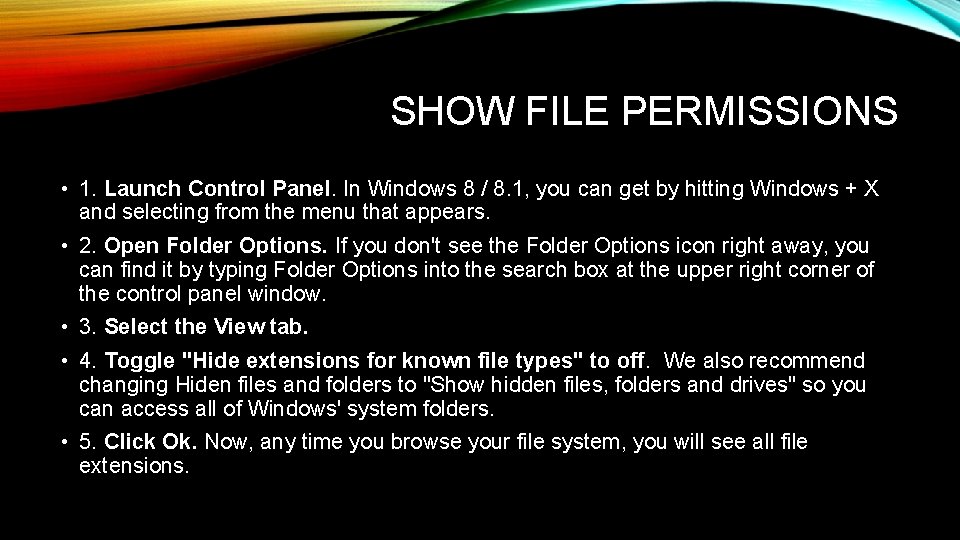
SHOW FILE PERMISSIONS • 1. Launch Control Panel. In Windows 8 / 8. 1, you can get by hitting Windows + X and selecting from the menu that appears. • 2. Open Folder Options. If you don't see the Folder Options icon right away, you can find it by typing Folder Options into the search box at the upper right corner of the control panel window. • 3. Select the View tab. • 4. Toggle "Hide extensions for known file types" to off. We also recommend changing Hiden files and folders to "Show hidden files, folders and drives" so you can access all of Windows' system folders. • 5. Click Ok. Now, any time you browse your file system, you will see all file extensions.

ANTI-VIRUS • Antivirus software is a program or set of programs that are designed to prevent, search for, detect, and remove software viruses, and other malicious software like worms, trojans, adware, and more. • Why Do I Need Antivirus Software? • These tools are critical for users to have installed and up-to-date because a computer without antivirus software protection will be infected within minutes of connecting to the internet. The bombardment is constant, which means antivirus companies have to update their detection tools regularly to deal with the more than 60, 000 new pieces of malware created daily. • Today's malware (an umbrella term that encompasses computer viruses) changes appearance quickly to avoid detection by older, definition-based antivirus software. Viruses can be programmed to cause damage to your device, prevent a user from accessing data, or to take control of your computer.

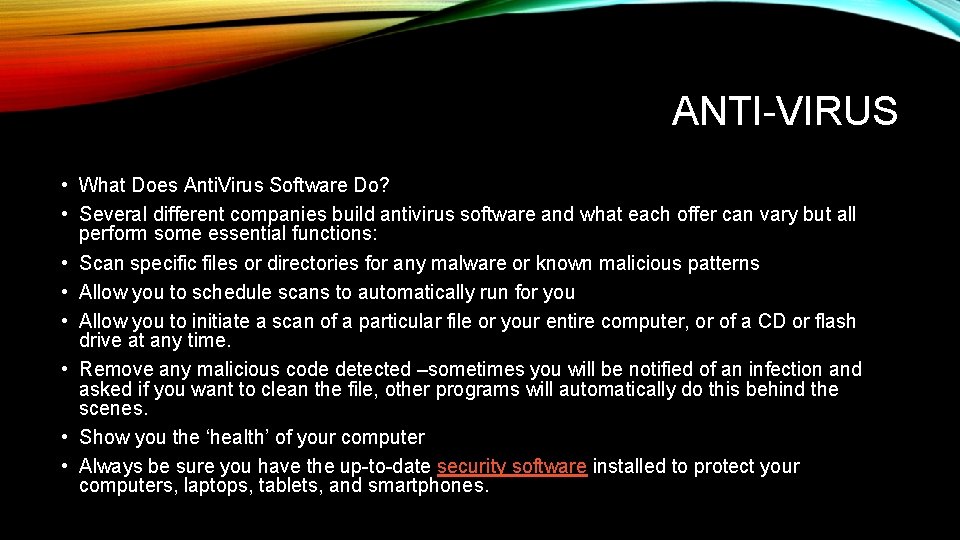
ANTI-VIRUS • What Does Anti. Virus Software Do? • Several different companies build antivirus software and what each offer can vary but all perform some essential functions: • Scan specific files or directories for any malware or known malicious patterns • Allow you to schedule scans to automatically run for you • Allow you to initiate a scan of a particular file or your entire computer, or of a CD or flash drive at any time. • Remove any malicious code detected –sometimes you will be notified of an infection and asked if you want to clean the file, other programs will automatically do this behind the scenes. • Show you the ‘health’ of your computer • Always be sure you have the up-to-date security software installed to protect your computers, laptops, tablets, and smartphones.

ANTI-VIRUS • How Does Antivirus Software Work? • Many antivirus software programs still download malware definitions straight to your device and scan your files in search of matches. But since, as we mentioned, most malware regularly morphs in appearance to avoid detection, Webroot works differently. Instead of storing examples of recognized malware on your device, it stores malware definitions in the cloud. This allows us to take up less space, scan faster, and maintain a more robust threat library. • Free vs Paid Antivirus Software • From banking to baby photos, so much of our business and personal data live on our devices. If it were stored physically, paying for a security solution would be a no-brainer. Unfortunately, we often expect our online data to remain secure without lifting a finger or spending a cent. Companies claiming to do it for free are partly responsible for the confusion, to be sure. But consumers should insist on features like identity theft protection, mobile security, and support options when it comes to their data security, too—features usually lacking with free solutions

ENABLE WINDOWS DEFENDER • Exercise- enable windows defender • Step 1 To start, you will have to find the Defender app on your system. To do this, use the key combination of the Windows Key and Q. This combo will launch the search function on your system. Type “defender” into the resulting search bar. If you are using a tablet, you can find the search menu by swiping in from the right-hand side of the screen. Step 2 When Windows Defender shows up as a result for your search, tap or click on it to launch the program. If the program isn’t turned on, you will be greeted by a dialogue box telling you so. If the program is turned on, it will open and you will be able to edit the security settings. Step 3 If Defender is off, go back to the search function from step 1 and type in “action. ” Select Action Center from the results. A new menu will open where you can see your security settings, including options for spyware and virus protection. Both will tell you that Defender is turned off, and both will also feature a button that says “Turn on now. ” Click one of them to enable Defender. Recap Once Defender is enabled, you will be able to open the program, view your security settings, and update the software to make sure the antivirus definitions are up to date!

WINDOWS FIREWALL • The Windows Firewall is a silent tool that keeps our systems safe from all kinds of network threats and has been included in each version of Windows for the last decade. • Work in the background • security application created by Microsoft and built into Windows • designed to filter network data transmissions to and from your Windows system and block • • harmful communications and/or the programs that are initiating them computer or device with protection against attacks from your local network or the internet, while still giving you access to the network and the internet. can also stop types of malicious software that use network traffic to spread themselves, like Trojan horse attacks and worms. can filter both outgoing and incoming connections to your Windows computer and block those which are unwanted. predefined set of rules for both types of network traffic, but its rules can be edited and changed both by the user and the software that the user installs.

DEFAULT WINDOWS FIREWALL SETTINGS • selects the checkbox that is appropriate for the network connection that you are using. • You can select either of the options or both, depending on what you want to do. • If you want to allow a program to connect to the network and the internet, click or tap Allow Access. If you want to block access, press Cancel. • Windows Firewall cannot protect you against any malicious attacks. • Must be used in conjunction with Anti-virus (windows defender or others)

ENABLE/VIEW WINDOWS FIREWALL • Exercise- view the windows firewall

HOW TO VIEW FIREWALL • To open the Windows Firewall, you have several options. One of them is to go to “Control Panel -> System and Security -> Windows Firewall. ” • When you open it, you will see a window similar to the one below: showing the type of network you are connected to and whether the firewall is turned on or off. • To activate or deactivate the Windows Firewall, click or tap the “Turn Windows Firewall on or off” link, found on the left side of the Windows Firewall window.