Intro to Info Sec Communication Protocols Nir Krakowski





![Demos • [Demo sniffing a cookie with wireshark. • [Demo using scapy]. Demos • [Demo sniffing a cookie with wireshark. • [Demo using scapy].](https://slidetodoc.com/presentation_image_h2/5a4f808e9d4262323d240409e3ccb389/image-15.jpg)

- Slides: 18

Intro to Info. Sec Communication Protocols Nir Krakowski (nirkrako at post. tau. ac. il) Itamar Gilad (infosec 15 at modprobe. net)

Today • • Into to new subject – communication protocols Common terminology Most useful protocols Tools of the trade.

Communication Protocols • A network is just a bunch of devices communicating. • There all sorts of protocols out there today being used: 3 GPP/GSM/SS 7, TCP/IP, Ethernet, W/LAN, Bluetooth, ATM, HDMI, USB, etc. • All protocols have been designed to serve different purposes, their purpose usually demands their structure and services they provide. • Of course the most important of all is the Internet Protocol (IP).

Secured Communication • Securing Transfer of Information is a problem of centuries. In the middle ages pigeons with notes were captured in order to intercept communication. • Our computer systems are valuable because they can communicate. Can you find a computer disconnected from the internet ? • Communications are an essential part of the security trust-base.

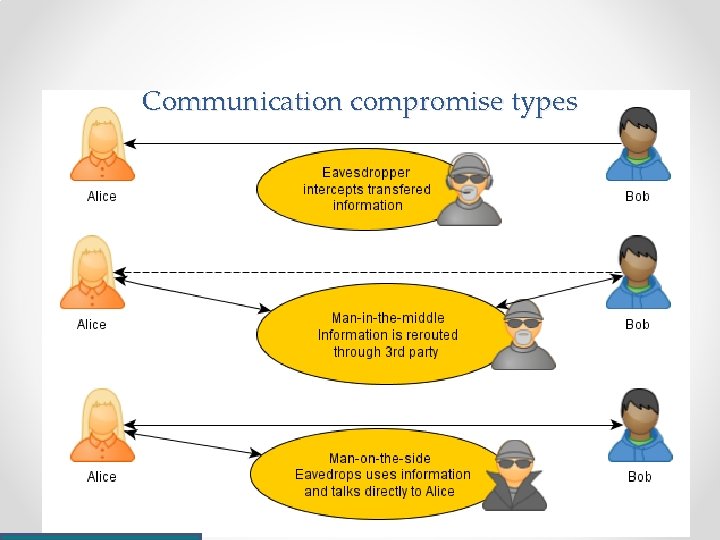
Communication compromise types

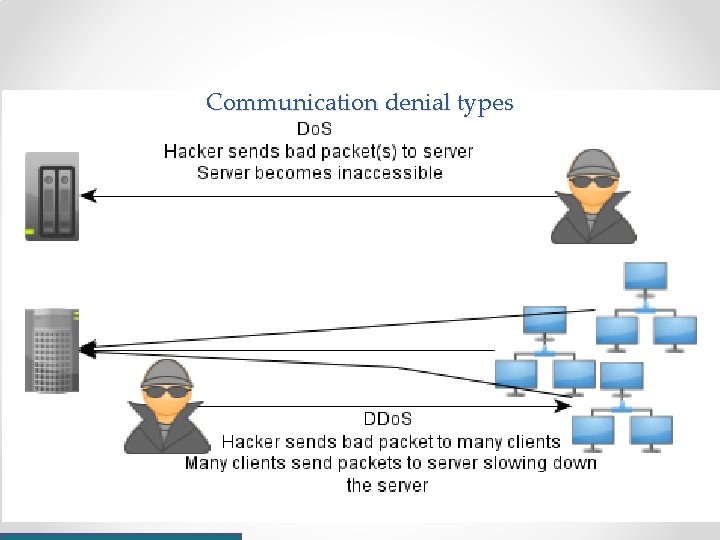
Communication denial types

Communication compromise types • Eavesdropping - information leaves a device it can be intercepted. • Man in the middle– communication is routed through a 3 rd party. • Man on the side– eavesdropping information is used to for impersonation. • Denial of Service (Do. S). • Distributed Denial of Service (DDo. S). • In other words, a hackers goals by priority is: o Divert traffic for man in the middle. o Eavesdrop on traffic. o Disturb traffic.

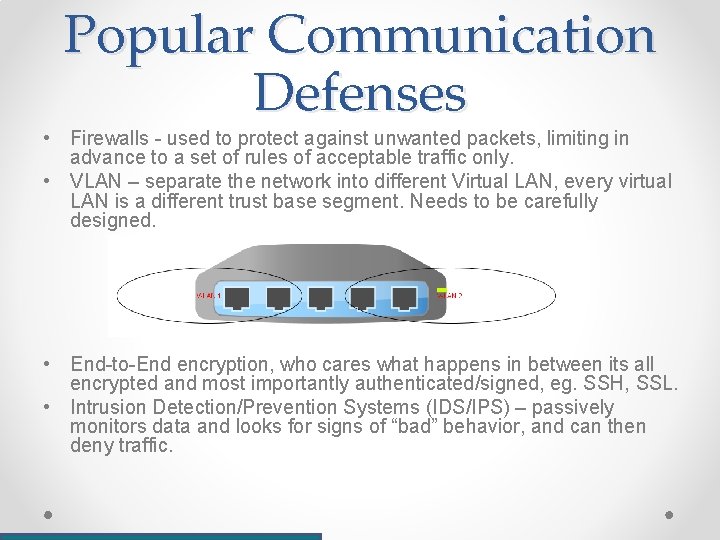
Popular Communication Defenses • Firewalls - used to protect against unwanted packets, limiting in advance to a set of rules of acceptable traffic only. • VLAN – separate the network into different Virtual LAN, every virtual LAN is a different trust base segment. Needs to be carefully designed. • End-to-End encryption, who cares what happens in between its all encrypted and most importantly authenticated/signed, eg. SSH, SSL. • Intrusion Detection/Prevention Systems (IDS/IPS) – passively monitors data and looks for signs of “bad” behavior, and can then deny traffic.

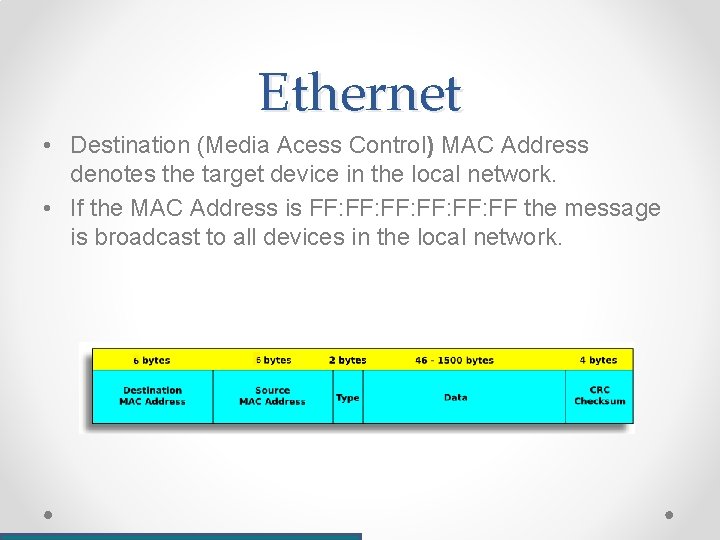
Ethernet • Destination (Media Acess Control) MAC Address denotes the target device in the local network. • If the MAC Address is FF: FF: FF: FF the message is broadcast to all devices in the local network.

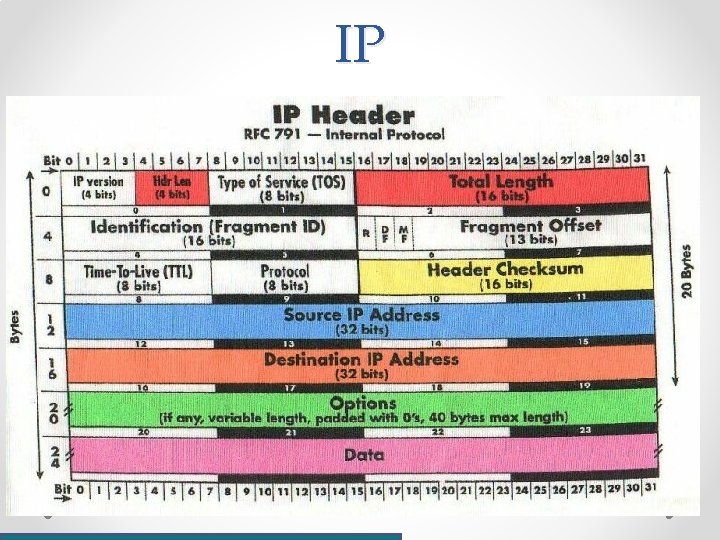
IP

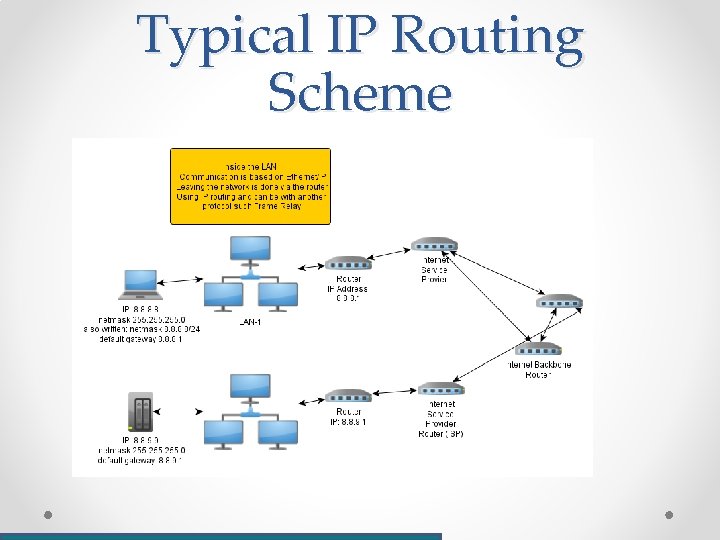
Typical IP Routing Scheme

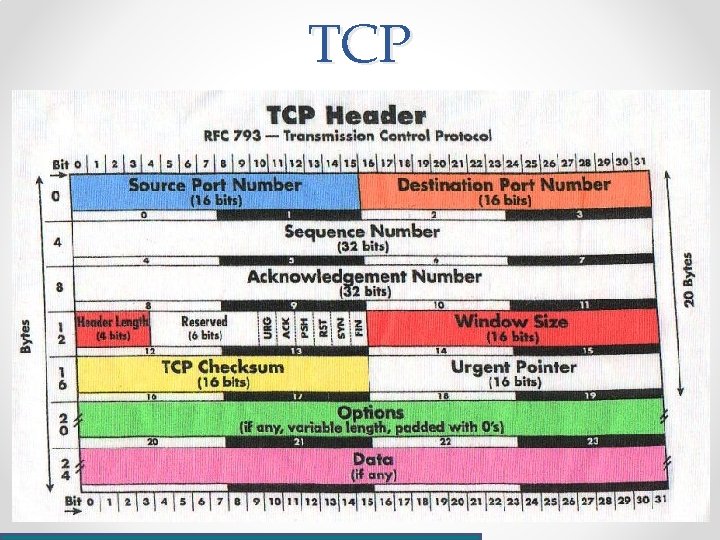
TCP

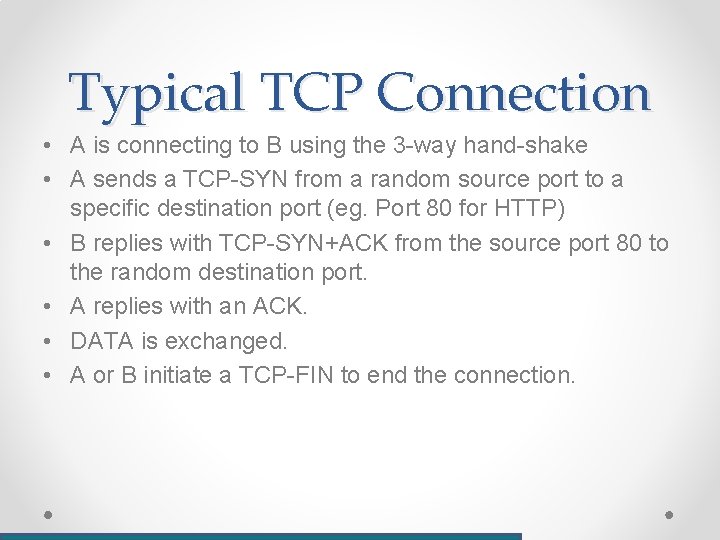
Typical TCP Connection • A is connecting to B using the 3 -way hand-shake • A sends a TCP-SYN from a random source port to a specific destination port (eg. Port 80 for HTTP) • B replies with TCP-SYN+ACK from the source port 80 to the random destination port. • A replies with an ACK. • DATA is exchanged. • A or B initiate a TCP-FIN to end the connection.

Our tools • Wireshark – a spin-off from ethereal which started as a GUI interface for tcpdump. o Wireshark sniffs communications and records them in capture files. cap or. pcap o Has many modules supporting enormous amount of protocol types. o Straight-forward interface. • Scapy – Another useful python module. o Also available for perl, don’t tell Itamar. (http: //sylv 1. tuxfamily. org/projects/scaperl. html) o But we’ll use python anyhow.
![Demos Demo sniffing a cookie with wireshark Demo using scapy Demos • [Demo sniffing a cookie with wireshark. • [Demo using scapy].](https://slidetodoc.com/presentation_image_h2/5a4f808e9d4262323d240409e3ccb389/image-15.jpg)
Demos • [Demo sniffing a cookie with wireshark. • [Demo using scapy].

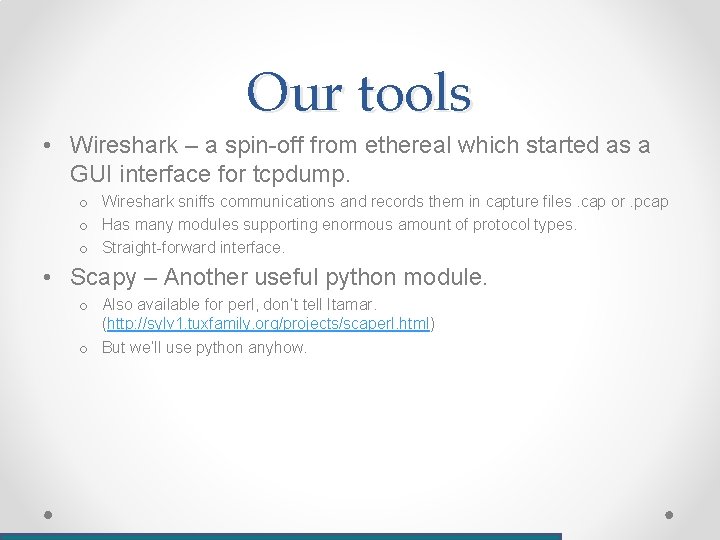
Wireshark – setup capture filter

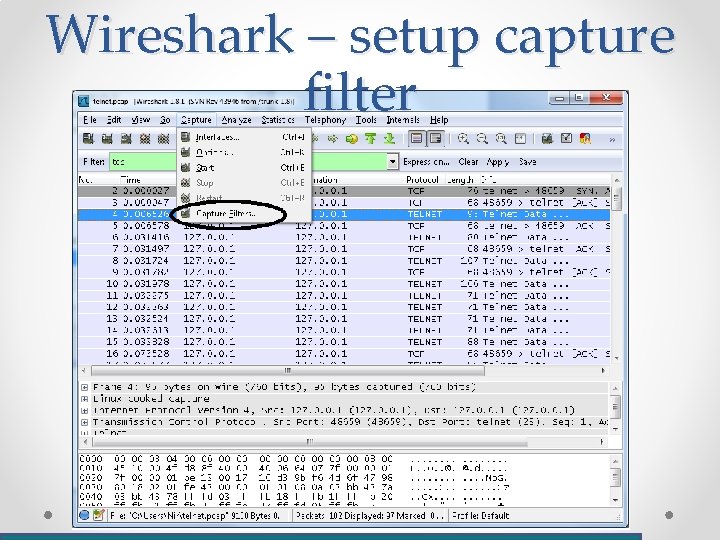
Wireshark – capture filter • Capture filter are very fast and tell wireshark which data to record.

Recording data • Alternatively you can also record. pcap files with tcpdump. • eg. : tcpdump –ni any –s 0 –w out. pcap • Reading files is also possible with scapy: o from scapy. all import * o all_packets = rdpcap(“data 01. pcap”)