InterNetwork Protocols Theory and Practice Lecture 4 Dr
















- Slides: 57

(Inter)Network Protocols: Theory and Practice Lecture 4 Dr. Michael Schapira

This Lecture 1. BGP security reminder • • Attacks against BGP How to secure the network 2. Routing within an AS • • The AS as a network Routing protocols 3. Traffic engineering • MPLS, ECMP, …

BGP Security (Reminder)

BGP security • BGP designed based on trust • … and is consequently very vulnerable to attacks • Every few years a serious BGP-related failure makes the news

1. BGP Session Security BGP session physical link

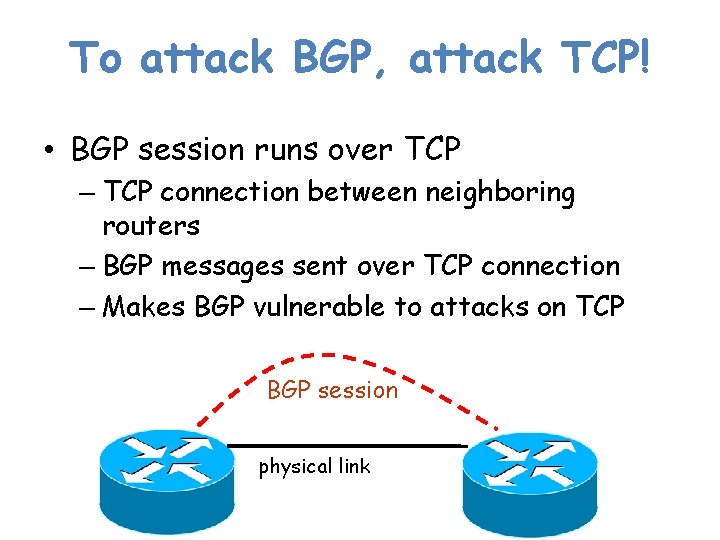
To attack BGP, attack TCP! • BGP session runs over TCP – TCP connection between neighboring routers – BGP messages sent over TCP connection – Makes BGP vulnerable to attacks on TCP BGP session physical link

Defending the BGP Session is Easy • Two end-points can – Use known IP addresses and ports to communicate – Can agree to sign and encrypt messages • Limited physical access to the link – Direct physical link, often in same building • Low volume of special traffic – Filter packets from unexpected senders – Filter packets that travel more than one hop – Can give BGP packets higher priority

2. Manipulating BGP No, I’m You. Tube! AS 1 AS 2 I’m You. Tube

Prefix Hijacking • IP address block assignment – Regional Internet Registries (ARIN, RIPE, APNIC) – Internet Service Providers • Proper origination of a prefix into BGP – by the AS who owns the prefix – … or, by its upstream provider(s) in its behalf • However, what’s to stop someone else? – prefix hijacking: another AS originates the prefix – BGP does not verify that the AS is authorized – registries of prefix ownership are inaccurate

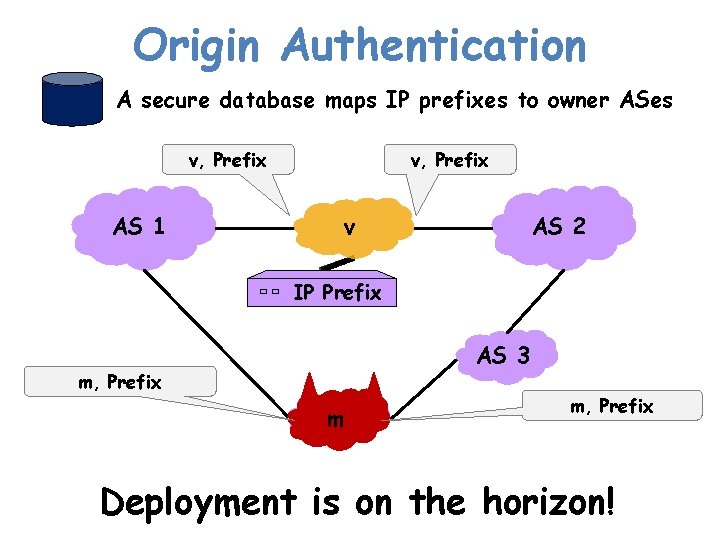
Origin Authentication A secure database maps IP prefixes to owner ASes v, Prefix AS 1 AS 2 v IP Prefix IP AS 3 m, Prefix m m, Prefix Deployment is on the horizon!

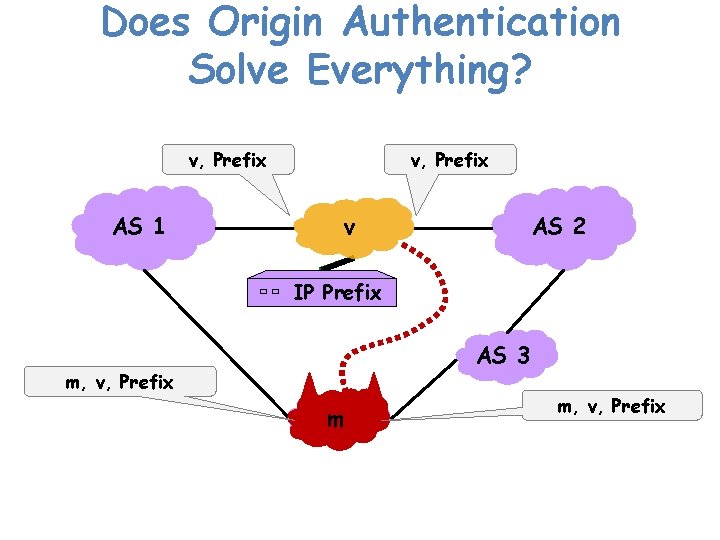
Does Origin Authentication Solve Everything? v, Prefix AS 1 AS 2 v IP Prefix IP AS 3 m, v, Prefix m m, v, Prefix

Bogus AS Paths • Path-shortening attacks: Remove ASes from the AS path – e. g. , turn “ 1 2 3” into “ 1 3” • Why? – to make the AS path look shorter than it is – to attract sources that try to avoid AS 2 • Other attacks – e. g. , adding ASes to the path to trigger loop AS 1 AS 2 AS 3 detection ?

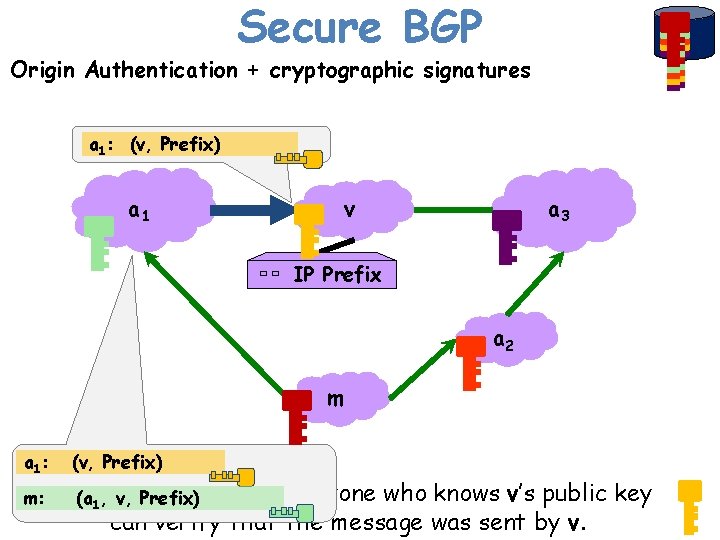
Secure BGP Origin Authentication + cryptographic signatures a 1: (v, Prefix) a 1 a 3 v IP Prefix a 2 m a 1: (v, Prefix) Key Signature: m: Public (a 1, v, Prefix) Anyone who knows v’s public key can verify that the message was sent by v.

BGP is So Hard to Fix • Complex system – large – decentralized control among competitive ASes – critical • Hard to reach agreement on the right solution – S-BGP with public key infrastructure, registries, crypto? – who should be in charge of running PKI and registries? • Hard to deploy the solution once you pick it – hard enough to get ASes to apply route filters – now you want them to upgrade to a new protocol?

3. Data-Plane Attacks

Control Plane vs. Data Plane • Control plane – BGP is a routing protocol, i. e. , it computes routes • Data plane – Routers forward data packets – …supposedly along the path chosen in the control plane…

Data-Plane Attacks • Drop packets – … while still sending the routing announcements – maybe just some (Bit. Torrent? Skype? ) • Send packets on a different path or to a different destination • …

BGP Security: Summary • BGP is amazingly vulnerable to configuration errors and deliberate attacks • Three types of attacks: 1. attacks on the BGP session 2. manipulating the routing protocol itself 3. data-plane attacks • Security measures: – today’s (unsatisfactory) best common practices – proposed security mechanisms (Origin Authentication, S-BGP, …)

Routing Within an AS

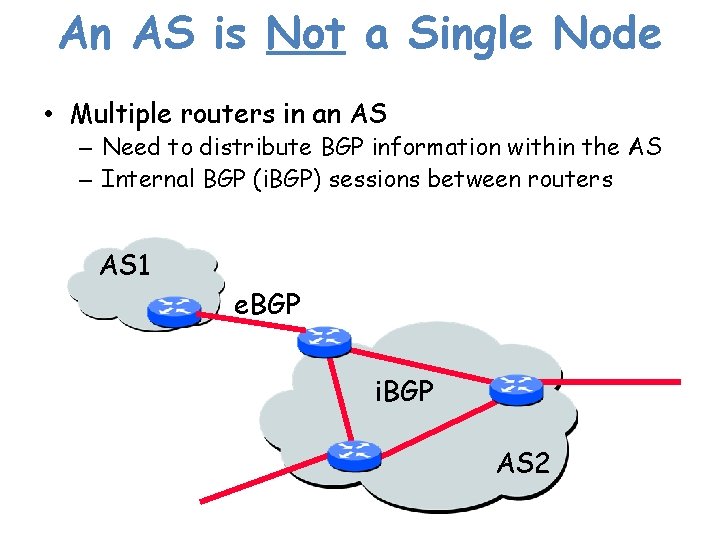
An AS is Not a Single Node • Multiple routers in an AS – Need to distribute BGP information within the AS – Internal BGP (i. BGP) sessions between routers AS 1 e. BGP i. BGP AS 2

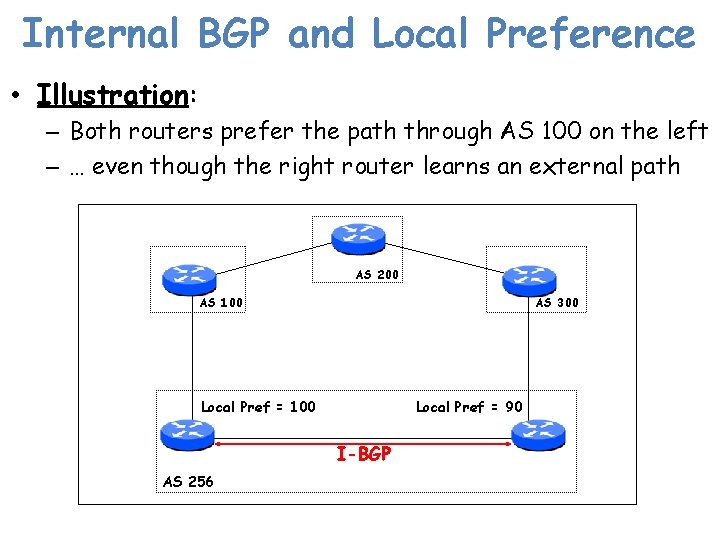
Internal BGP and Local Preference • Illustration: – Both routers prefer the path through AS 100 on the left – … even though the right router learns an external path AS 200 AS 100 AS 300 Local Pref = 90 Local Pref = 100 I-BGP AS 256

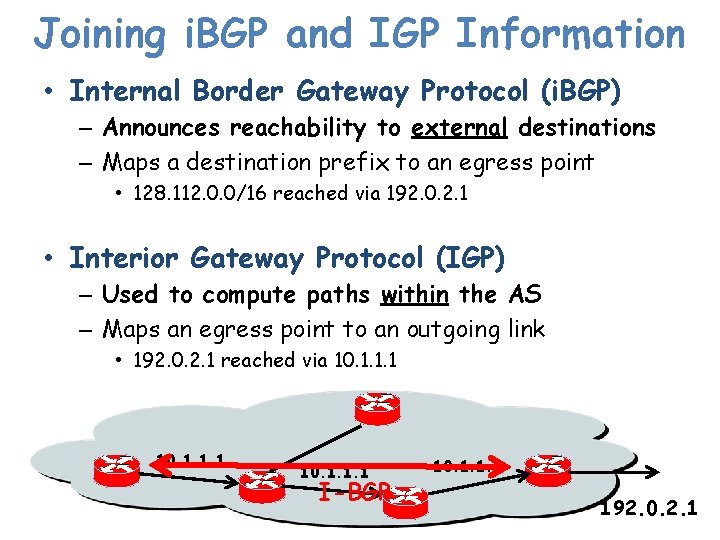
Joining i. BGP and IGP Information • Internal Border Gateway Protocol (i. BGP) – Announces reachability to external destinations – Maps a destination prefix to an egress point • 128. 112. 0. 0/16 reached via 192. 0. 2. 1 • Interior Gateway Protocol (IGP) – Used to compute paths within the AS – Maps an egress point to an outgoing link • 192. 0. 2. 1 reached via 10. 1. 1. 1 I-BGP 10. 1. 1. 1 192. 0. 2. 1

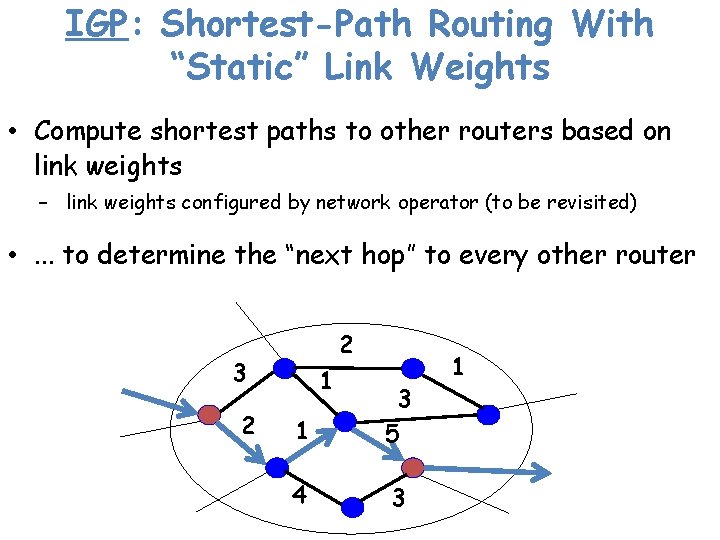
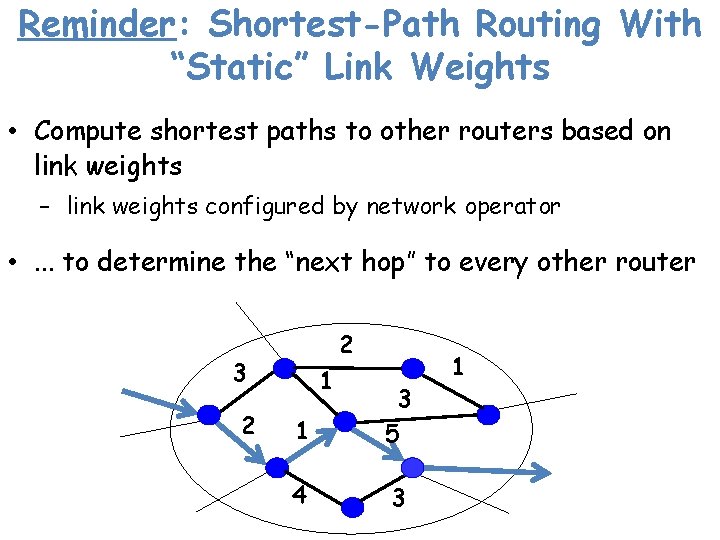
IGP: Shortest-Path Routing With “Static” Link Weights • Compute shortest paths to other routers based on link weights – link weights configured by network operator (to be revisited) • . . . to determine the “next hop” to every other router 2 3 2 1 1 3 5 4 3 1

IGP: Shortest-Path Routing Schemes • Distance Vector Routing – iterative process – Bellman-Ford algorithm • Link-State Routing – routers flood information to learn topology – each router then applies Dijkstra’s algorithm to compute shortest paths

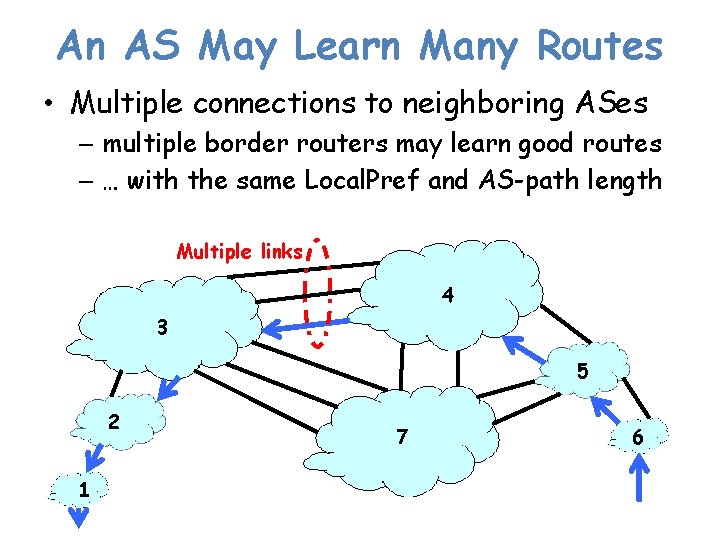
An AS May Learn Many Routes • Multiple connections to neighboring ASes – multiple border routers may learn good routes – … with the same Local. Pref and AS-path length Multiple links 4 3 5 2 1 7 6

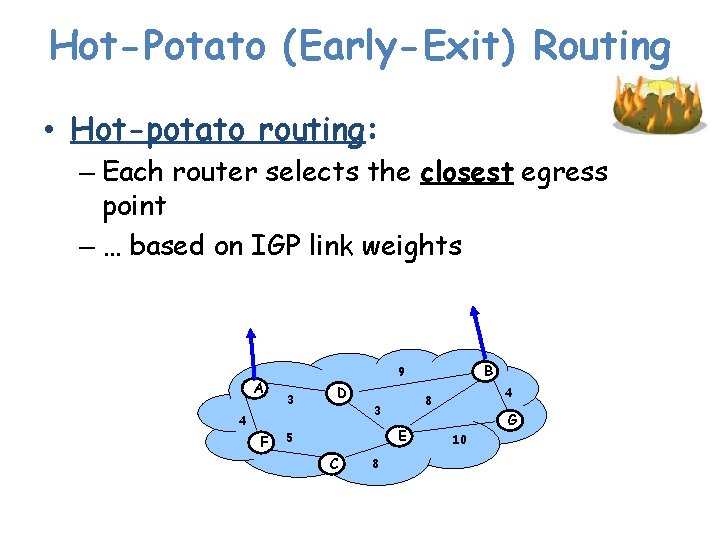
Hot-Potato (Early-Exit) Routing • Hot-potato routing: – Each router selects the closest egress point – … based on IGP link weights A 3 D 4 F B 9 3 E 5 C 8 4 8 G 10

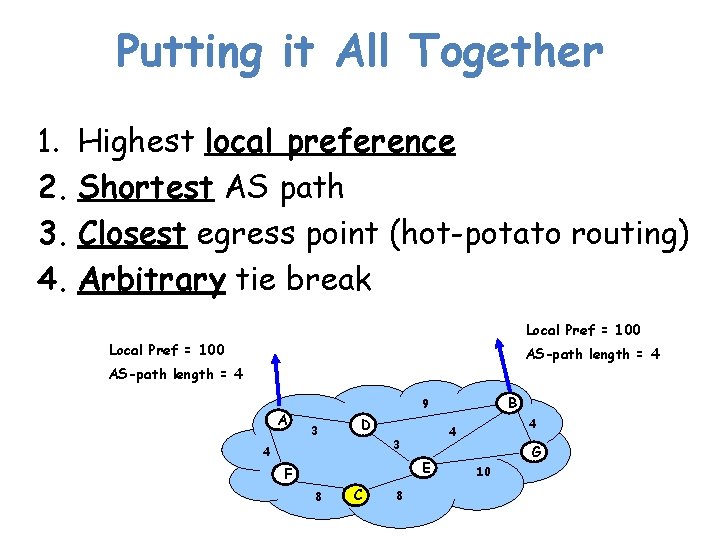
Putting it All Together 1. Highest local preference 2. Shortest AS path 3. Closest egress point (hot-potato routing) 4. Arbitrary tie break Local Pref = 100 AS-path length = 4 A B 9 3 D 3 4 E F 8 C 8 4 4 G 10

Routing Within an AS: Summary • An AS is a network of routers • Combining i. BGP and IGP routing – i. BGP announces reachability to external destinations – IGP computes routes within the AS • IGP schemes: – Distance Vector – Link State

Traffic Engineering

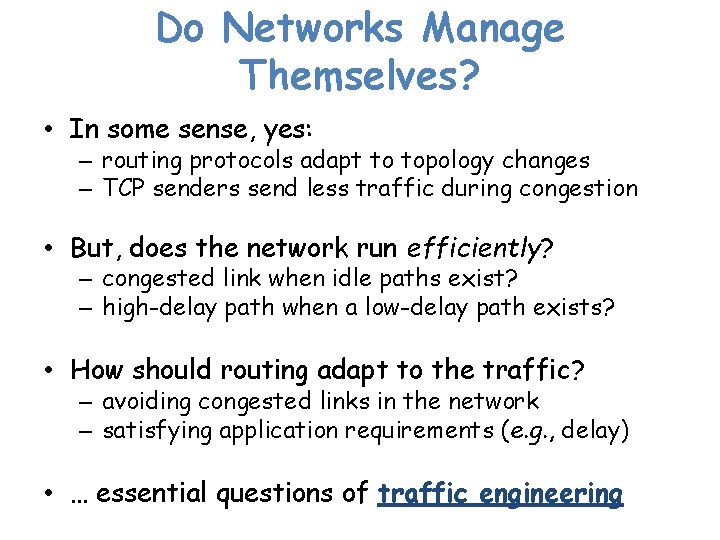
Do Networks Manage Themselves? • In some sense, yes: – routing protocols adapt to topology changes – TCP senders send less traffic during congestion • But, does the network run efficiently? – congested link when idle paths exist? – high-delay path when a low-delay path exists? • How should routing adapt to the traffic? – avoiding congested links in the network – satisfying application requirements (e. g. , delay) • … essential questions of traffic engineering

Traffic Engineering • Tuning routing protocol configuration – tuning IGP link weights within the AS network – tuning BGP policies on edge routers • … to optimize network performance

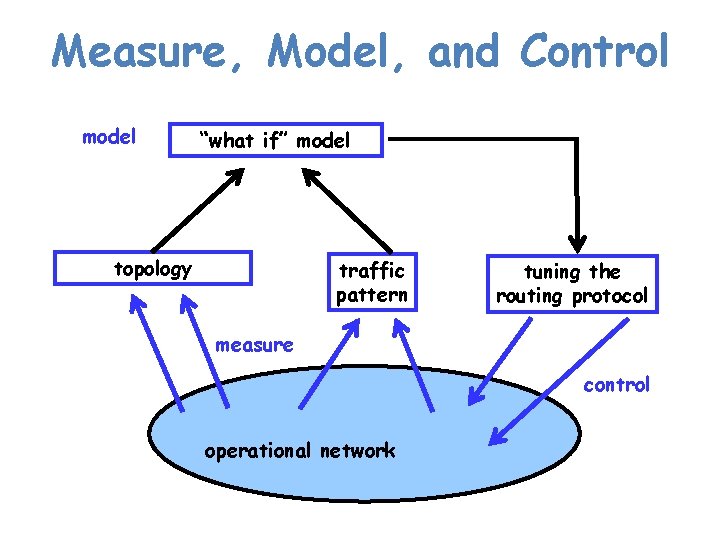
Measure, Model, and Control model “what if” model topology traffic pattern tuning the routing protocol measure control operational network

Measure, Model, and Control (Cont. ) • Measurement – topology – traffic pattern: passive traffic measurement • Network-wide models – representations of topology and traffic – “what if” model of routing • Network optimization – algorithms to find good configurations – operational experience to identify constraints

Theory: Flow Optimization

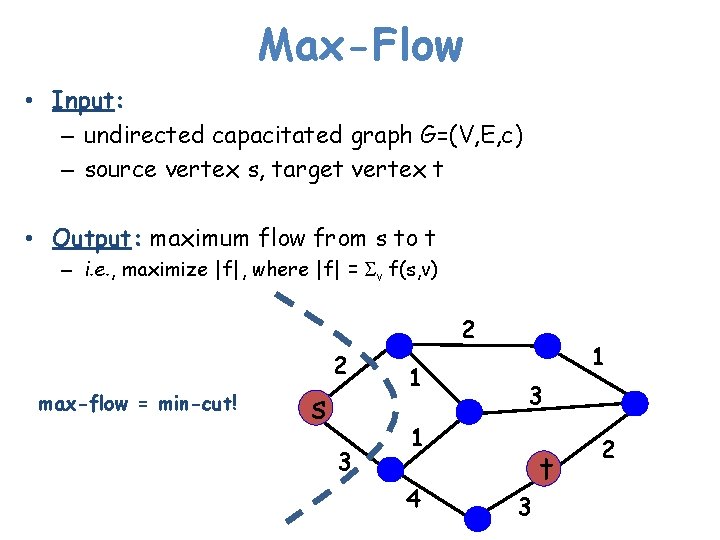
Max-Flow • Input: – undirected capacitated graph G=(V, E, c) – source vertex s, target vertex t • Output: maximum flow from s to t – i. e. , maximize |f|, where |f| = Sv f(s, v) 2 2 max-flow = min-cut! s 3 1 1 3 1 4 3 t 2

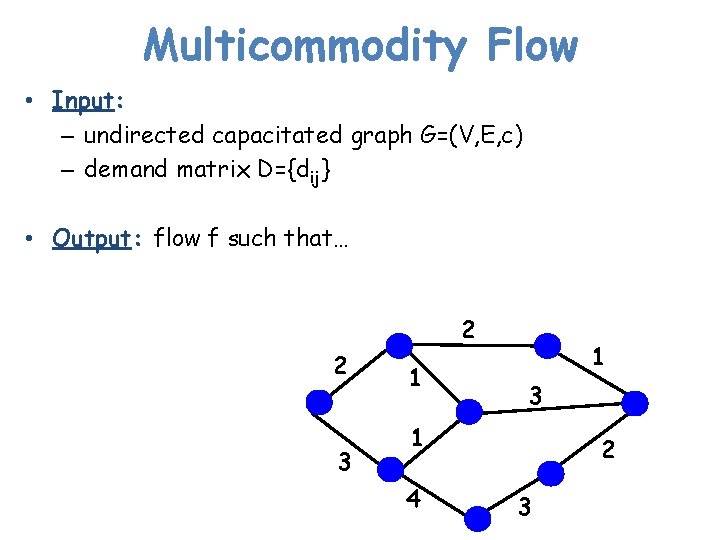
Multicommodity Flow • Input: – undirected capacitated graph G=(V, E, c) – demand matrix D={dij} • Output: flow f such that… 2 2 3 1 1 3 1 4 2 3

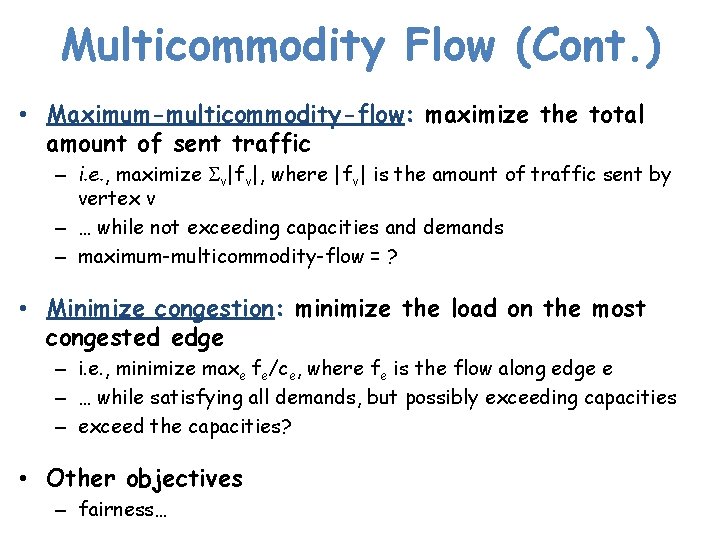
Multicommodity Flow (Cont. ) • Maximum-multicommodity-flow: maximize the total amount of sent traffic – i. e. , maximize Sv|fv|, where |fv| is the amount of traffic sent by vertex v – … while not exceeding capacities and demands – maximum-multicommodity-flow = ? • Minimize congestion: minimize the load on the most congested edge – i. e. , minimize maxe fe/ce, where fe is the flow along edge e – … while satisfying all demands, but possibly exceeding capacities – exceed the capacities? • Other objectives – fairness…

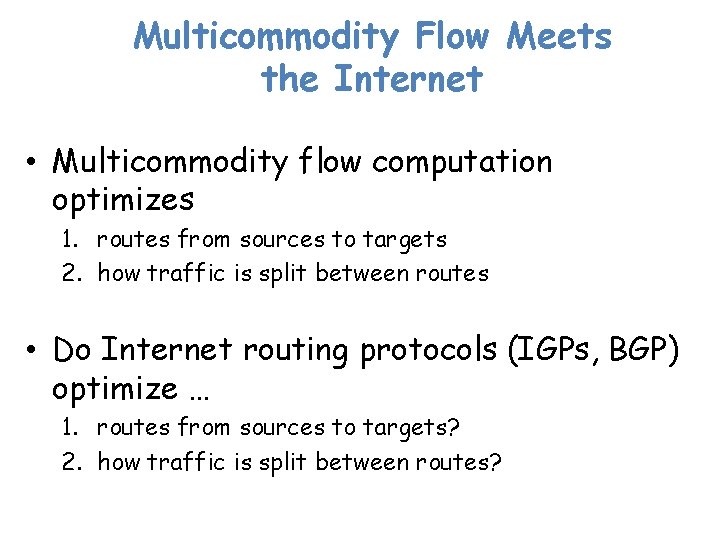
Multicommodity Flow Meets the Internet • Multicommodity flow computation optimizes 1. routes from sources to targets 2. how traffic is split between routes • Do Internet routing protocols (IGPs, BGP) optimize … 1. routes from sources to targets? 2. how traffic is split between routes?

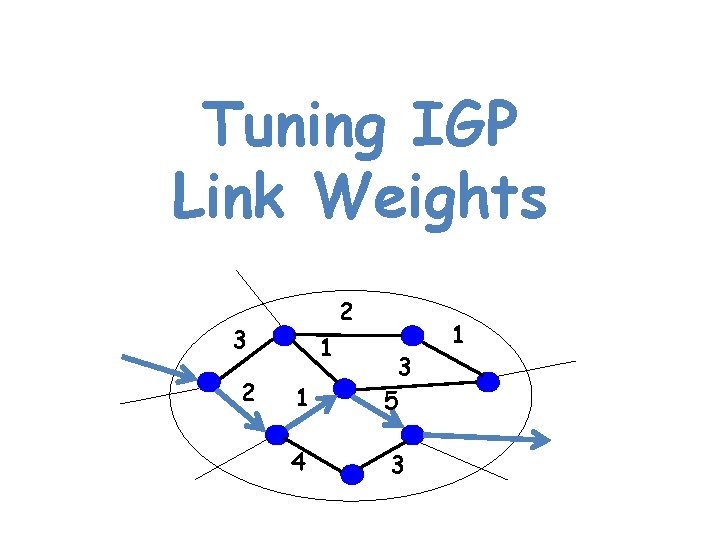
Tuning IGP Link Weights 2 3 2 1 1 3 5 4 3 1

Reminder: Shortest-Path Routing With “Static” Link Weights • Compute shortest paths to other routers based on link weights – link weights configured by network operator • . . . to determine the “next hop” to every other router 2 3 2 1 1 3 5 4 3 1

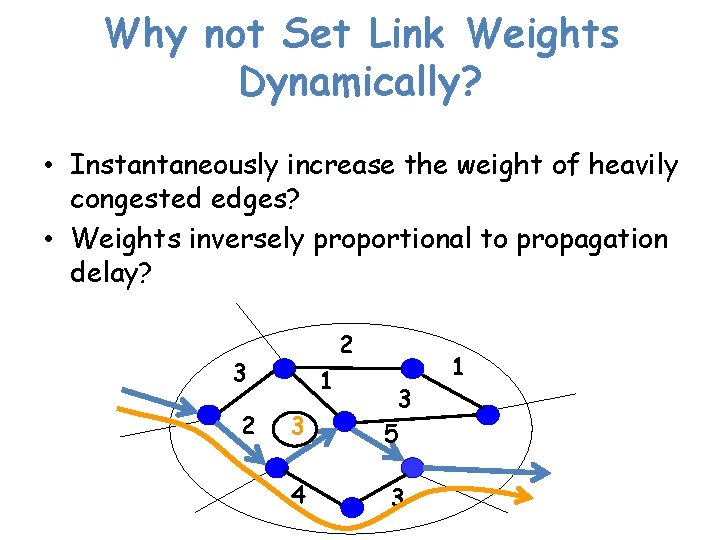
Why not Set Link Weights Dynamically? • Instantaneously increase the weight of heavily congested edges? • Weights inversely proportional to propagation delay? 2 3 2 1 3 5 4 3 1

Why not Set Link Weights Dynamically? • Instantaneously increase the weight of heavily congested edges? • Weights inversely proportional to propagation delay? • Well actually…

1. The Story of ARPAnet Routing

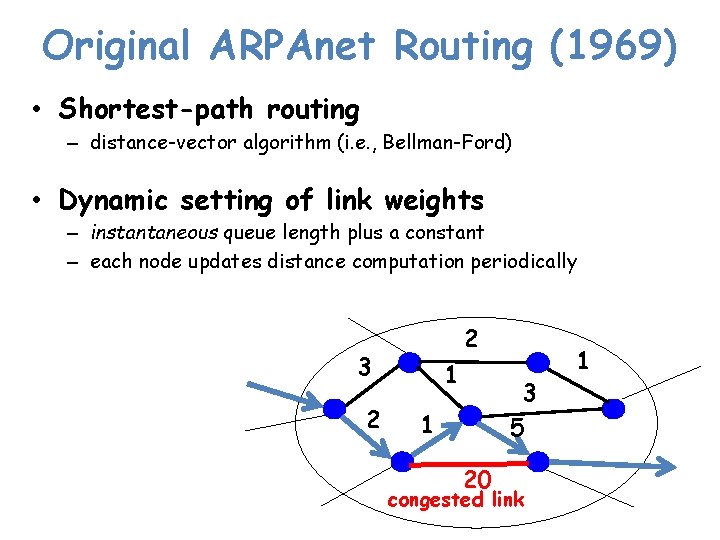
Original ARPAnet Routing (1969) • Shortest-path routing – distance-vector algorithm (i. e. , Bellman-Ford) • Dynamic setting of link weights – instantaneous queue length plus a constant – each node updates distance computation periodically 2 3 2 1 3 5 1 20 congested link 1

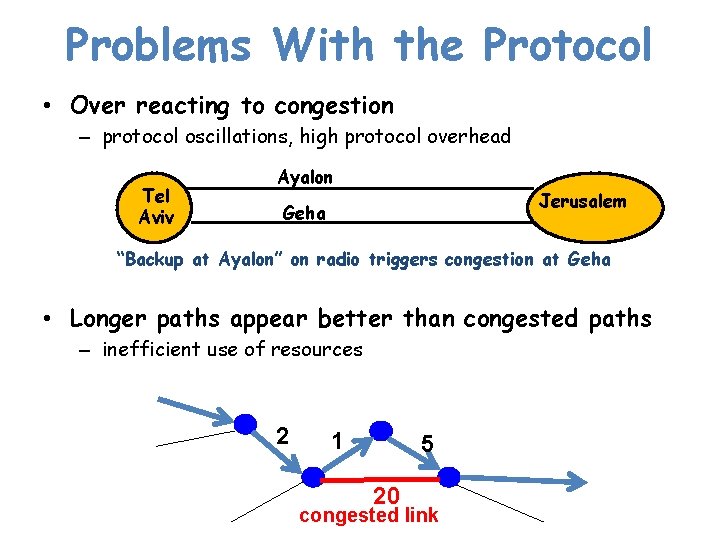
Problems With the Protocol • Over reacting to congestion – protocol oscillations, high protocol overhead Tel Aviv Ayalon Jerusalem Geha “Backup at Ayalon” on radio triggers congestion at Geha • Longer paths appear better than congested paths – inefficient use of resources 2 1 5 20 congested link

Evolution of ARPAnet Routing • New ARPAnet routing protocol in 1979 – from distance-vector to link-state routing to avoid loops – averaging the link weight over time to reduce fluctuations – reduce frequency of updates to reduce protocol overhead • Revision to ARPAnet routing protocol in 1987 – shed traffic gradually to prevent overreaction to congestion – upper bound on link weight to avoid excessively long paths

2. Optimizing (Static) Link Weights 2 3 2 1 1 3 5 4 3 1

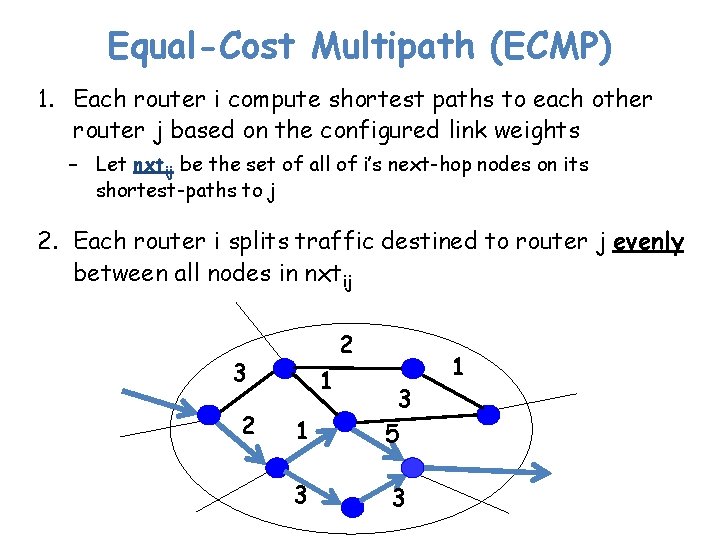
Equal-Cost Multipath (ECMP) 1. Each router i compute shortest paths to each other router j based on the configured link weights – Let nxtij be the set of all of i’s next-hop nodes on its shortest-paths to j 2. Each router i splits traffic destined to router j evenly between all nodes in nxtij 2 3 2 1 1 3 5 3 3 1

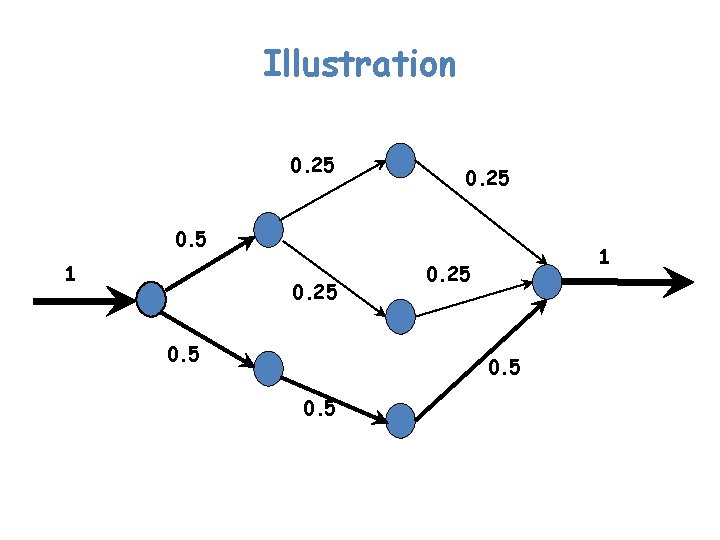
Illustration 0. 25 0. 5 1 0. 25 0. 5

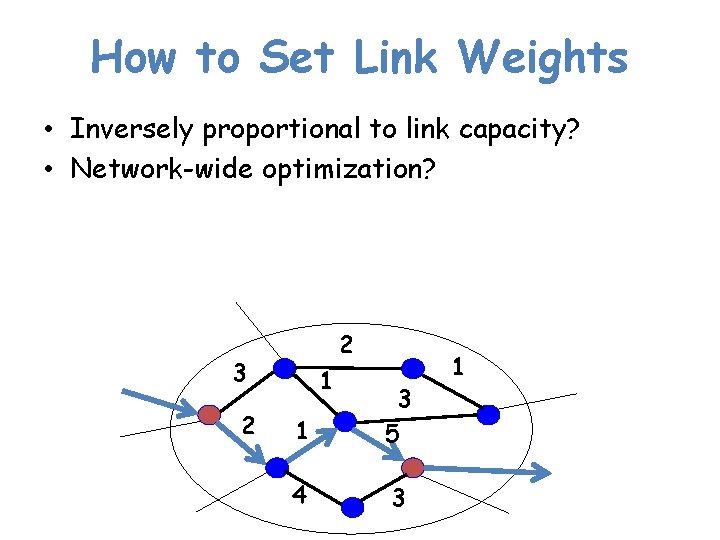
How to Set Link Weights • Inversely proportional to link capacity? • Network-wide optimization? 2 3 2 1 1 3 5 4 3 1

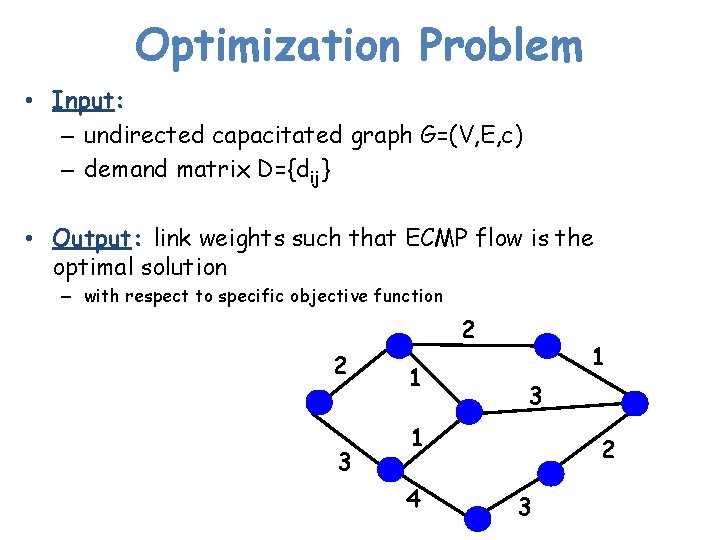
Optimization Problem • Input: – undirected capacitated graph G=(V, E, c) – demand matrix D={dij} • Output: link weights such that ECMP flow is the optimal solution – with respect to specific objective function 2 2 3 1 1 3 1 4 2 3

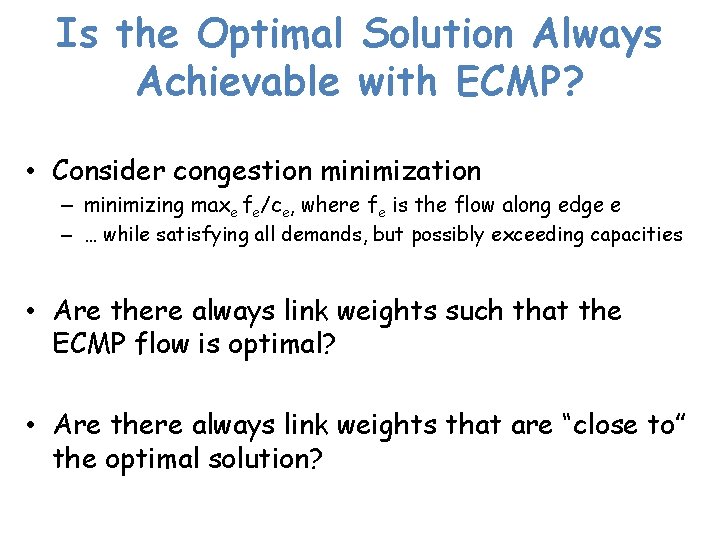
Is the Optimal Solution Always Achievable with ECMP? • Consider congestion minimization – minimizing maxe fe/ce, where fe is the flow along edge e – … while satisfying all demands, but possibly exceeding capacities • Are there always link weights such that the ECMP flow is optimal? • Are there always link weights that are “close to” the optimal solution?

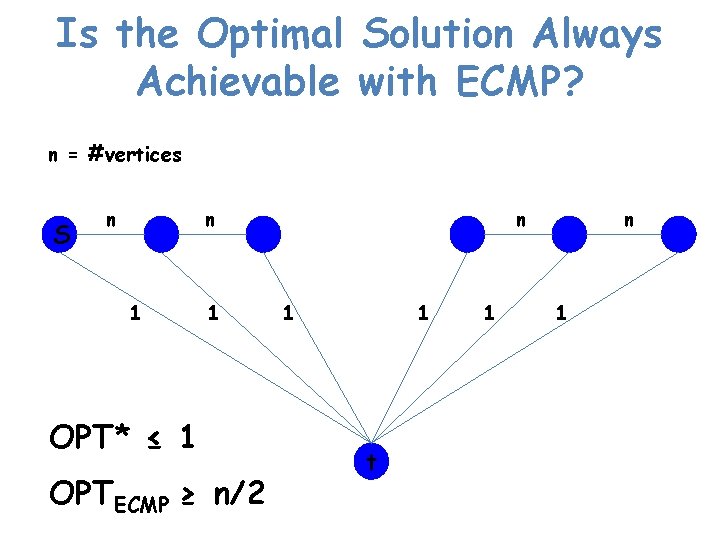
Is the Optimal Solution Always Achievable with ECMP? n = #vertices S n n 1 1 OPT* ≤ 1 OPTECMP ≥ n/2 n 1 1 t 1 n 1

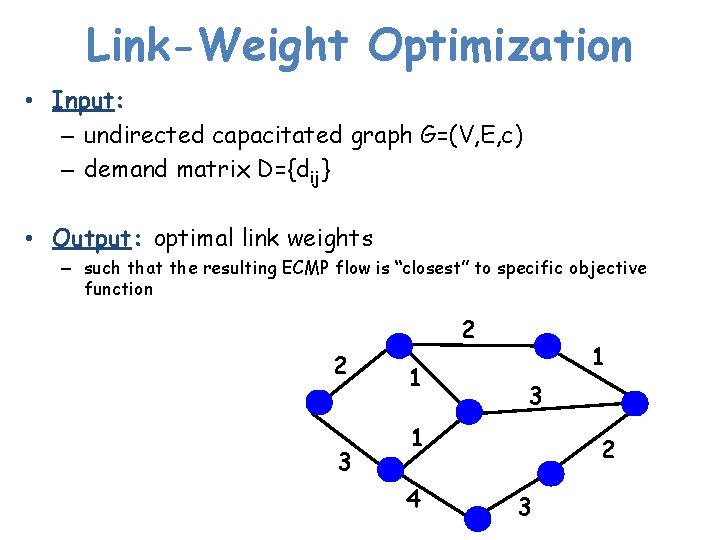
Link-Weight Optimization • Input: – undirected capacitated graph G=(V, E, c) – demand matrix D={dij} • Output: optimal link weights – such that the resulting ECMP flow is “closest” to specific objective function 2 2 3 1 1 3 1 4 2 3

Complexity of Link-Weight Optimization • NP-hard! – Even for simple objective functions • Theorem: Approximating the mincongestion flow within any constant factor is NP-hard. – even for a single source-target pair!

Proof Idea • Theorem: Approximating the mincongestion flow within factor a is NPhard for some constant a. – even for a single source-target pair! • Now, amplify the gap! – recursive construction…

So, What Do Network Operators Do? • Heuristics: searching through weight settings • Clearly suboptimal, but shown to effective in some real-life environments – fast computation of the link weights – good performance, compared to “optimal” solution – resilience to failures