InternetIntranet firewall security policy architecture and transaction services









- Slides: 12

Internet/Intranet firewall security – policy, architecture and transaction services Written by Ray Hunt This presentation will Examines Policies that influence the design, installation and use of a firewall. It also takes a quick look at two different types of firewalls Presented by Hosein Derhamy

Content • • • Introduction Business policies Network Service Access Policies Firewall Design Policies Firewall Architecture Packet level firewalls Application level firewalls Conclusion Question

Introduction • We have seen from previous presentations that day by day as the world becomes more interconnected Network Security becomes more important. • A firewall is a method of achieving security between trusted and untrusted networks • The objective of the firewall policy is to minimize the organization’s zone of risk by removing the possibility of attack from an external network

Business Policy • The Network Service Access Policies should extend existing business policies. The business policies that are of interest are: • – – Information value – what value does the management place on information Responsibility - who is responsible for ensuring the protection of the organisation information Commitment – what is the organisations commitment to protecting its information Domains – what domains should or should not be protected

Network Service Access Policy(NSAP) • • The NSAP defines which services are to be explicitly allowed or denied between trusted and untrusted networks. The NSAP must be drafted before the firewall is implemented. It must provide a balance between protecting the trusted network from known risks while providing users with convenient access to the untrusted network.

Firewall Design Policy (FDP) • FDP defines how the firewall implements restricted access and service filtering specified by the NSAP. • It must take into account capabilities and limitations of the particular firewall platform as well as the threats and vulnerabilities associated with TCP/IP. • • Permit any service unless it is specifically disallowed Deny any service unless it is specifically permitted

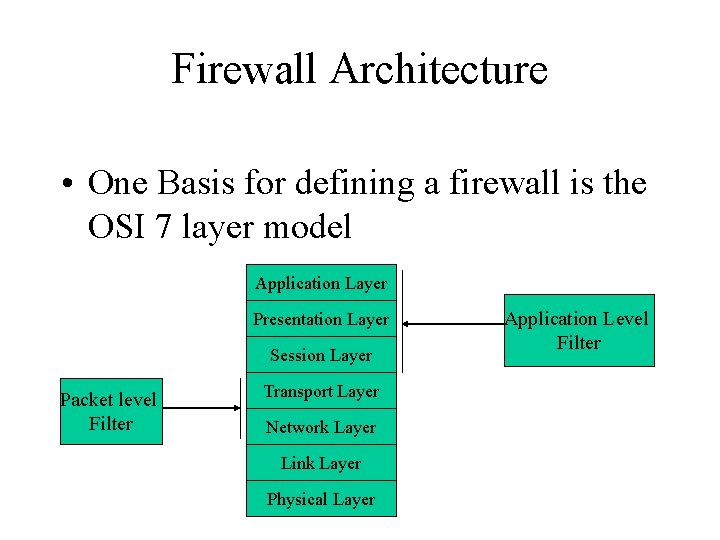
Firewall Architecture • One Basis for defining a firewall is the OSI 7 layer model Application Layer Presentation Layer Session Layer Packet level Filter Transport Layer Network Layer Link Layer Physical Layer Application Level Filter

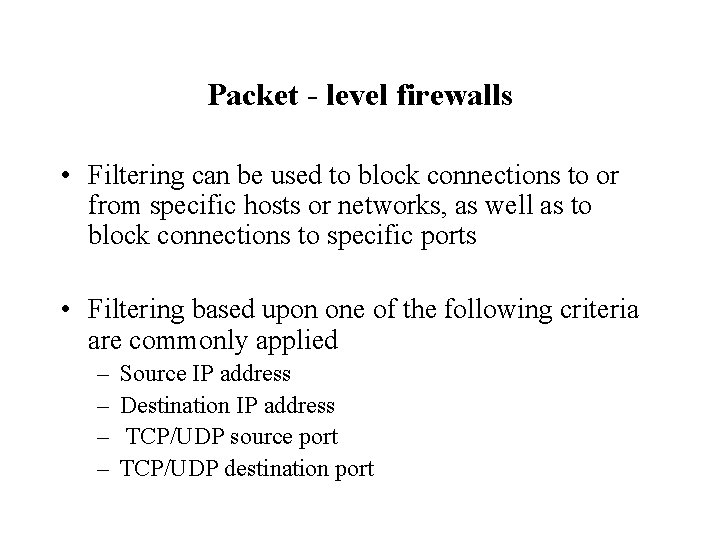
Packet - level firewalls • Filtering can be used to block connections to or from specific hosts or networks, as well as to block connections to specific ports • Filtering based upon one of the following criteria are commonly applied – – Source IP address Destination IP address TCP/UDP source port TCP/UDP destination port

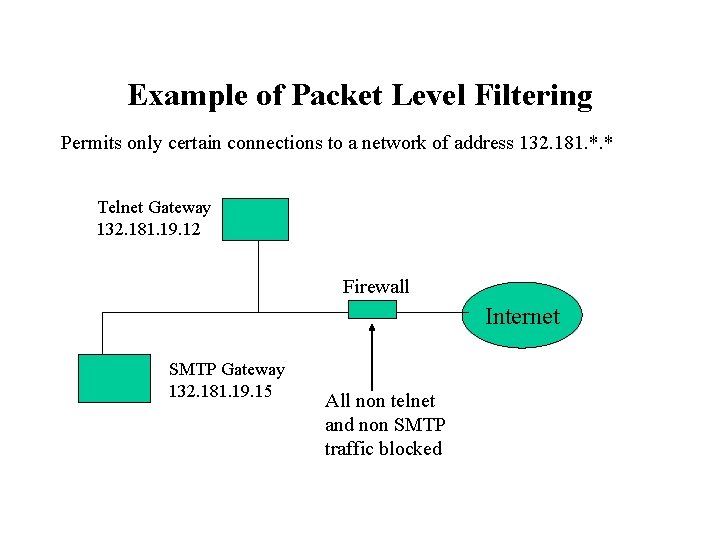
Example of Packet Level Filtering Permits only certain connections to a network of address 132. 181. *. * Telnet Gateway 132. 181. 19. 12 Firewall Internet SMTP Gateway 132. 181. 19. 15 All non telnet and non SMTP traffic blocked

Application – level firewalls • Application level firewalls are more flexible, easier to configure and update. • Advantages of application level firewalls or gateways are: – Information hiding – Robust authentication – Cost – effectiveness – Less - complex

Conclusion • This article has examined policies that effect the design, installation and use of a firewall. The policies can be looked as a top down procedure. First come the Business policies they generate the Network Service Access Policies and then followed by the Firewall Design Policies. • It is the Business Policies that require the security of the firewall.

Question • Is the NSAP dependant on the type of firewall used, Why?