Internet Time Services and NTP The Network Time















- Slides: 42

Internet Time Services and NTP, The Network Time Protocol Judah Levine Time and Frequency Division NIST Boulder jlevine@boulder. nist. gov 303 497 -3903 Judah Levine, NIST, CENAM, Oct 2012 1

Components of NTP n n Message format and parameters Measurement protocol Typical Performance Traceability – Private NTP n n n Layered services and authentication Reference clocks Peer selection Clock discipline algorithm Hierarchy definition and realization Remote Administration and Monitoring Judah Levine, NIST, CENAM, Oct 2012 2

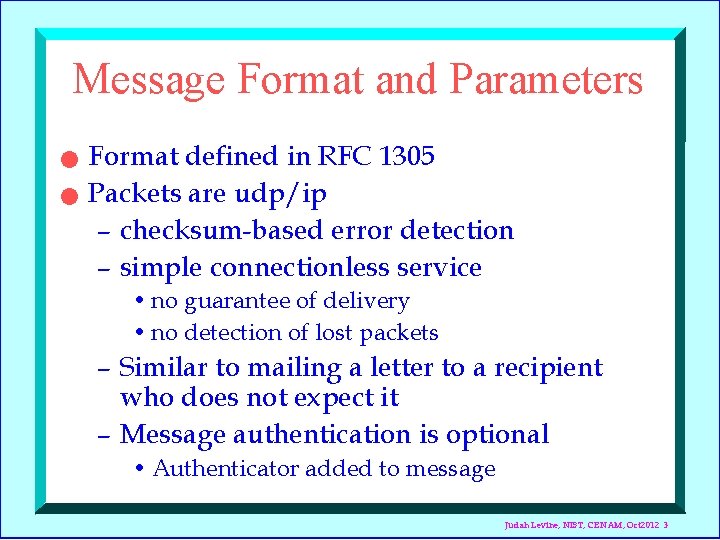
Message Format and Parameters n n Format defined in RFC 1305 Packets are udp/ip – checksum-based error detection – simple connectionless service • no guarantee of delivery • no detection of lost packets – Similar to mailing a letter to a recipient who does not expect it – Message authentication is optional • Authenticator added to message Judah Levine, NIST, CENAM, Oct 2012 3

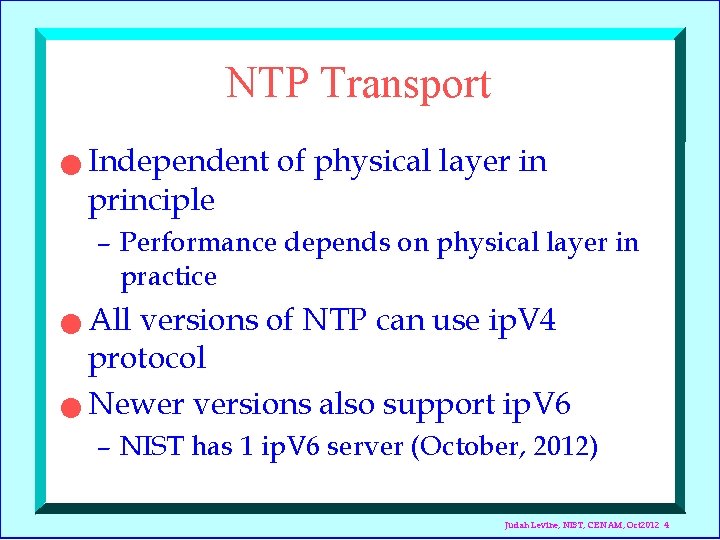
NTP Transport n Independent of physical layer in principle – Performance depends on physical layer in practice All versions of NTP can use ip. V 4 protocol n Newer versions also support ip. V 6 n – NIST has 1 ip. V 6 server (October, 2012) Judah Levine, NIST, CENAM, Oct 2012 4

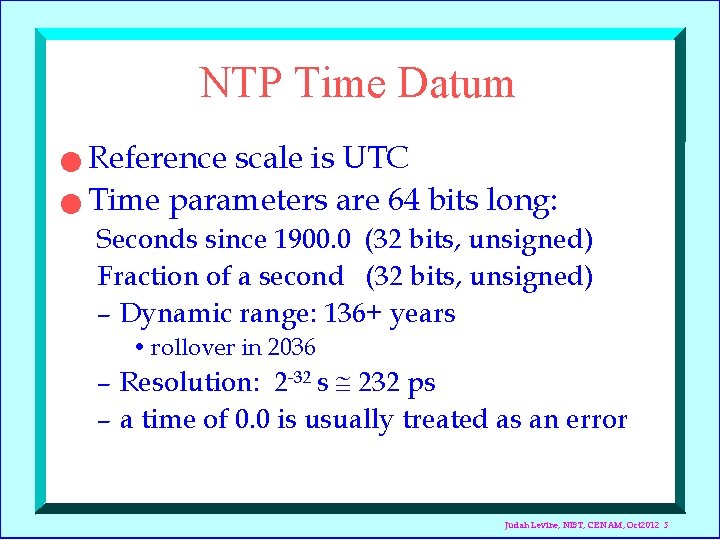
NTP Time Datum Reference scale is UTC n Time parameters are 64 bits long: n Seconds since 1900. 0 (32 bits, unsigned) Fraction of a second (32 bits, unsigned) – Dynamic range: 136+ years • rollover in 2036 – Resolution: 2 -32 s 232 ps – a time of 0. 0 is usually treated as an error Judah Levine, NIST, CENAM, Oct 2012 5

Some Other Parameters n Advance notice of leap second – leap second at end of today when set n Positive leap second in progress – Transmit 23: 59 twice • Effectively stop the system clock – Slewing methods (Google) n Clock unsynchronized flag • don’t trust the time message n Health and leap second use same bits. Judah Levine, NIST, CENAM, Oct 2012 6

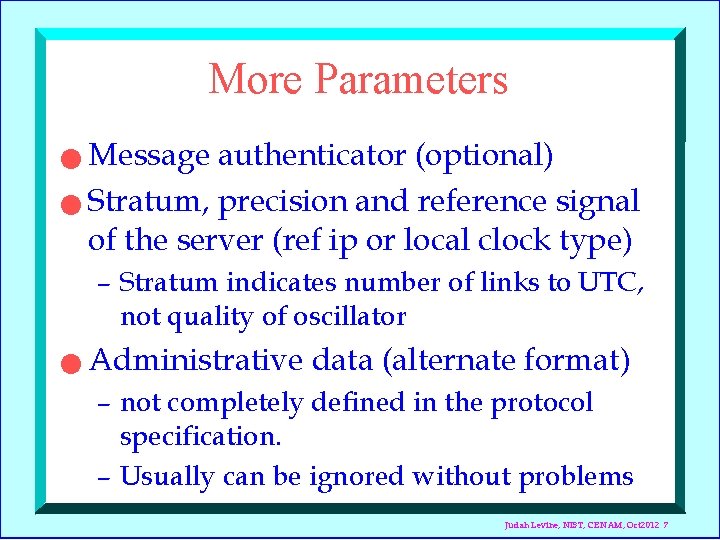
More Parameters Message authenticator (optional) n Stratum, precision and reference signal of the server (ref ip or local clock type) n – Stratum indicates number of links to UTC, not quality of oscillator n Administrative data (alternate format) – not completely defined in the protocol specification. – Usually can be ignored without problems Judah Levine, NIST, CENAM, Oct 2012 7

Authentication - 1 n Keys identified by index number into local file which has the key value. – <Key Number> M <key value> n Configuration – Trustedkey <Key Number> n n n MD 5 hash of the NTP key+packet XMT: Append result and key index RCV: Detects additional packet data – Compute hash using key specified by number, compare with received value n No decryption of received message – MD 5 algorithm has no known inverse n Distribution of keys is a headache Judah Levine, NIST, CENAM, Oct 2012 8

Authentication - 2 n Authentication only identifies server – Guarantees integrity Does not affect accuracy n Does not affect traceability n Possible “man in the middle” attacks n – Delay valid message – Replay old message Judah Levine, NIST, CENAM, Oct 2012 9

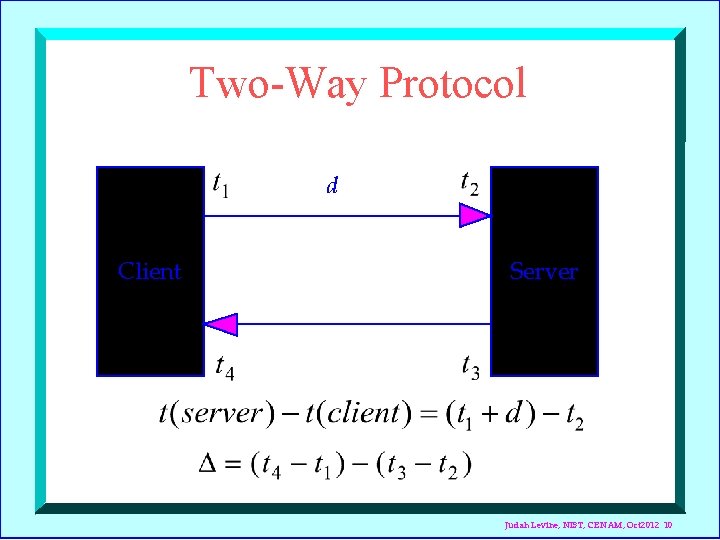
Two-Way Protocol d Client Server Judah Levine, NIST, CENAM, Oct 2012 10

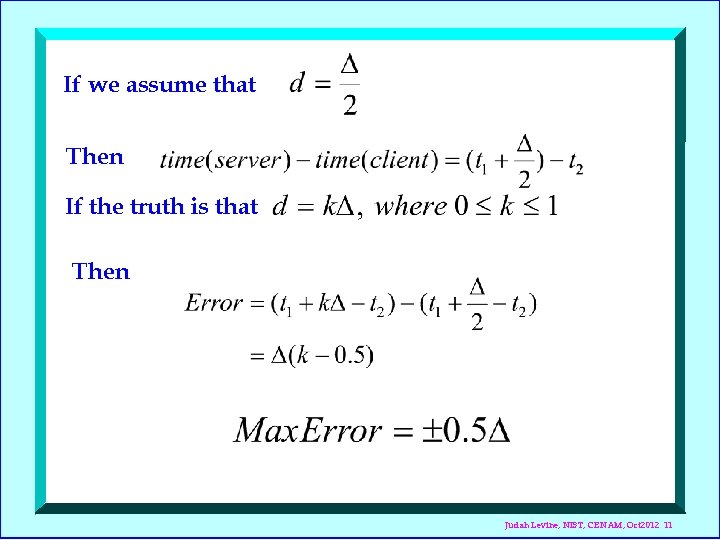
If we assume that Then If the truth is that Then Judah Levine, NIST, CENAM, Oct 2012 11

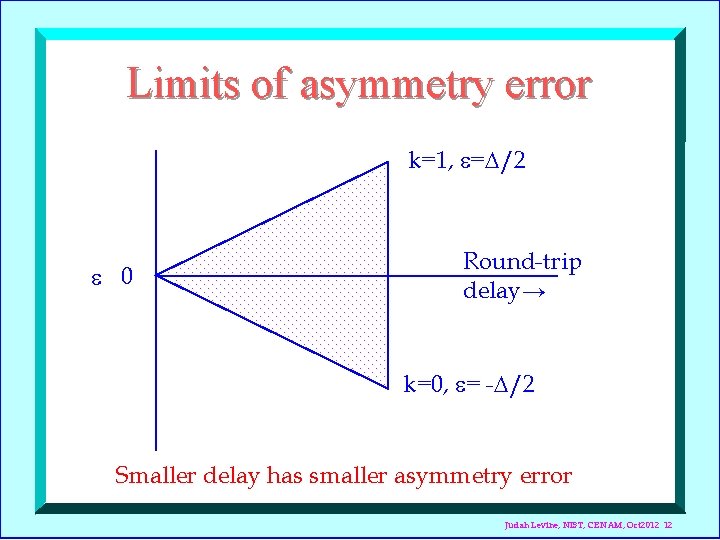
Limits of asymmetry error k=1, = /2 0 Round-trip delay→ k=0, = - /2 Smaller delay has smaller asymmetry error Judah Levine, NIST, CENAM, Oct 2012 12

Measurement Protocols n Two-way daemon with measured delay – uses udp/ip port 123 on server and client – Periodic queries to multiple servers – Client-server or peer to peer n Broadcast mode, no measured delay – Single server, multiple clients – Local LAN or Internet multi-cast n Single-shot client, e. g. ntpdate and sntp – port on server is udp/ip port 123 – any port on client is okay – measures delay using usual 2 -way method Judah Levine, NIST, CENAM, Oct 2012 13

Typical Performance - 1 n n n Typical asymmetry few percent of delay Small LAN – 10 ms best case ever on 2 -node LAN – 220 ms on real-world small LAN Typical large-building LAN – 2 ms RMS typical Internet with few hops – 10 – 20 ms Long distance and/or slow or busy link – 100 ms – 1 s Judah Levine, NIST, CENAM, Oct 2012 14

Typical Performance - 2 n Accuracy determined by accuracy of network delay measurement – not a function of message format • PTP/1588 not better on same network n Accuracy degraded on network with asymmetric traffic delays – Web server – David Mills “huff-n-puff” filter • Minimal delay implies minimal asymmetry Judah Levine, NIST, CENAM, Oct 2012 15

Traceability n Log files at stratum-1 server – Positive entries important – NIST servers maintain internal log files of each calibration cycle n Log files at end user necessary and may be sufficient – Queries to multiple servers are useful n Log files shift the legal burden of proof – “best practices” argument n Commercial equipment very poor and inadequate Judah Levine, NIST, CENAM, Oct 2012 16

Traceability and private NTP n Private NTP uses special hardware or software at both ends of link – “Trusted Master Clock” at NMI – “Trusted Reference Clock” at end user n Monitoring of user system using separate system – Issuing calibration certificates Judah Levine, NIST, CENAM, Oct 2012 17

NIST Position n Time from a private NTP systems is not traceable to NIST even if hardware is at NIST – Traceability ends at the signal connector NIST does not accept integrity or availability requirements n Some computer security issues not resolved n Judah Levine, NIST, CENAM, Oct 2012 18

Layered services - 1 n Document time stamping using Public/Private key pair – Hash code of document submitted to NIST • Document itself not transmitted or revealed – NIST adds NTP time stamp and signs combination with private key – Validity and time stamp can be verified using public key – NIST does not have to archive transaction Judah Levine, NIST, CENAM, Oct 2012 19

Layered Services - 2 n Certified Mail – NIST receives e-mail message from sender • Message can be encrypted – NIST adds time stamp and signature – NIST forwards mail to recipient n Support for Kerberos ticket system – Time-based method to validate users and applications Judah Levine, NIST, CENAM, Oct 2012 20

NIST position Layered services will be realized by private companies only n NIST service ends at time-service portal n – NTP stratum-1 server, ACTS, … n NIST provides authenticated stratum-1 time service to registered users – Registration linked to ip address of user – Unique key for each user Judah Levine, NIST, CENAM, Oct 2012 21

References n RFC literature for NTP – 958, 1059, 1119, 1305, 1589, 1769, 2030, . . . n Other NTP literature – IEEE/ACM Trans. Networking, Jun 1995, pp. 245 -254. – IEEE Trans. Comm. , Oct. 1991, pp. 1482 -93 www. ee. udel. edu/~mills/ntp. html n David Mills: mills@udel. edu n Judah Levine, NIST, CENAM, Oct 2012 22

Other Methods n Lockclock: – IEEE/ACM Trans. Networks, 2/95, pp. 4250. n Interlock and Autolock: – IEEE Trans. UFFC, 7/99, pp. 888 -896. n Other (non-NTP) methods – IEEE Trans. Parallel Distributed Sys. , 3/94, pp. 474 -487. Judah Levine, NIST, CENAM, Oct 2012 23

Backup Slides Reference Clock Models n Peer Selection Method n Clock Discipline: PLL vs FLL n Polling Interval Considerations n NTP Administration n NTP Message Format and Parameters n Judah Levine, NIST, CENAM, Oct 2012 24

Reference Clock Models (NTP) n Local reference clock (radio clock. . . ) incorporated as a peer with a pseudo-ip address (127. t. u). – pseudo-ip points to internal driver n Relationship to clock looks like clientserver -- clock is polled periodically and time enters standard peer selection procedures. Judah Levine, NIST, CENAM, Oct 2012 25

Reference Clock (JL) n Local reference clock is a special device with its own driver – Separate from NTP – statistics tuned to clock type Better than standard NTP in normal operations n Worse in certain error situations n – Longer polling interval Judah Levine, NIST, CENAM, Oct 2012 26

NTP Peer Selection - 1 n Initial specification is in configuration file using ip address + keywords – server, peer, prefer n Typical configuration specifies multiple servers – All (or multiple) servers queried on every measurement cycle Judah Levine, NIST, CENAM, Oct 2012 27

NTP Peer Selection - 2 n n Method favors lowest stratum, lowest distance peer that claims to be healthy and does not appear to be an outlier with respect to the other systems. Best case – multiple queries improves accuracy by 1/ N – Cost increases as N n Statistics of local clock not used – Short-term stability better than network Judah Levine, NIST, CENAM, Oct 2012 28

JL Peer management n Algorithm normally queries only one server – Compare received time difference with expected value n Statistics of local clock used in algorithm – Weighted sum of local clock time and time received from remote server • Weighting based on previous variance n Query additional server only if error detected Judah Levine, NIST, CENAM, Oct 2012 29

NTP Clock Discipline - I n “Original recipe” NTP uses PLL – Local clock is steered primarily in frequency using filtered time difference. – goal of loop is to drive time error to 0 • approximate second-order loop. – Polling interval must be kept short so that variance is time noise – Discrimination implemented with queries to multiple servers – Cost ~ N, benefit ~ 1/ N – loop converts time noise to frequency noise Judah Levine, NIST, CENAM, Oct 2012 30

NTP Clock Discipline - II n New version of NTP uses mixed PLL/FLL – crossover as function of interval between measurements and message quality n FLL drives frequency error to 0 – time is correct on the average • defined by Adev – better decoupling of time/frequency Judah Levine, NIST, CENAM, Oct 2012 31

JL Clock Discipline n Control loop is pure FLL – parameters set to Adev analysis Time step detector similar to AT 1 n Simplifies separation of time and frequency fluctuations n – allows time steps with no associated change in frequency Judah Levine, NIST, CENAM, Oct 2012 32

FLL vs. PLL Considerations n Server noise spectrum seen through channel vs. noise of local clock. – local clock often better at short times. Frequency noise and phase noise are not necessarily correlated n FLL generally cheaper n – makes better use of better hardware n FLL slower to remove time steps Judah Levine, NIST, CENAM, Oct 2012 33

Cost/Performance tradeoff n A PLL must operate in domain where phase noise is dominant problem – Degradation at longer times is not easily determined n FLL usually operates in white FM domain – Cheaper to start with (longer averaging) – Quantitative tradeoff based on AVAR • Implemented in Autolock Judah Levine, NIST, CENAM, Oct 2012 34

Polling Interval Statistics of remote clock seen through the network should be better than local clock variance n Cost/benefit analysis: n – White phase noise: • Cost ~ N, • Variance ~ 1/ N Judah Levine, NIST, CENAM, Oct 2012 35

Daemon Administration n NTP packet modes 6 and 7 – uses same udp/ip packets to same port – configure daemon parameters – monitor performance and usage – dangerous without authentication n NTP distribution provides utility tasks – ntpq – xntpdc Judah Levine, NIST, CENAM, Oct 2012 36

Network Administration Public servers identified in lists maintained by David Mills at the University of Delaware and ntp. org n RFC literature defines standards, etc. n newsgroup comp. protocols. time. ntp n “Free for all” typical of the Internet n – Almost all people are good citizens almost all of the time Judah Levine, NIST, CENAM, Oct 2012 37

NIST Server Administration All network-based administration disabled for security reasons n Each server maintains internal state variable history n Each server linked to alarm system via dial-up modem. n Separate monitoring and alarm system runs on system in Boulder n Judah Levine, NIST, CENAM, Oct 2012 38

Definition of Stratum n Lower stratum clocks are closer to a primary time source – WWVB, GPS, . . . Properties or quality of local oscillator do not influence stratum definition n NTP message format supports stratum, accuracy estimate and synch. source n Judah Levine, NIST, CENAM, Oct 2012 39

More Parameters Message authenticator (optional) n Stratum, precision and reference signal of the server (ref ip or local clock type) n – Stratum indicates number of links to UTC, not quality of oscillator n Administrative data (alternate format) – not completely defined in the protocol specification. – Usually can be ignored without problems Judah Levine, NIST, CENAM, Oct 2012 40

NTP Service model n Operate servers at many locations – Minimizes delay error for all users – No single point of failure – How are remote servers synchronized? • Time link to source of UTC(lab) Performance limited by delay jitter and asymmetry n Static asymmetry generally cannot be detected n Judah Levine, NIST, CENAM, Oct 2012 41

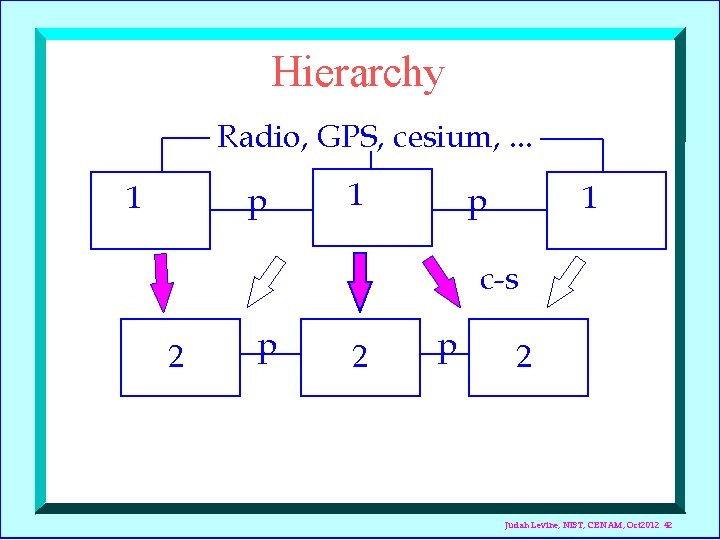
Hierarchy Radio, GPS, cesium, . . . 1 p 1 1 p c-s 2 p 2 Judah Levine, NIST, CENAM, Oct 2012 42