Internet Security ECT 582 Robin Burke Outline Homework

Internet Security ECT 582 Robin Burke

Outline Homework #5 ¢ Host security ¢ Firewalls ¢ IPsec / VPN ¢
Homework #5 ¢ solution

Host security ¢ Every Internet host is vulnerable to attack l ¢ Network port is a front door to the whole world How to make hosts more secure? attacks l defenses l

Attacks on Hosts ¢ ¢ ¢ Do. S l flood host with requests to tie up resources Authentication breach l attack authentication system to gain access Application vulnerability l attack application program to inject foreign code Virus/Trojan Horse l attack OS with a malicious program (malware) Social Engineering l attack organization to obtain authentication or other information
Denial of Service ¢ Attacks take different forms bogus requests l abuse of Internet protocols l ¢ Characteristics sudden change in system load l services unavailable or very slow l • may cause system crash l particular hosts targeted

Defenses ¢ ¢ Turn off unused services l if bogus packets never received, fewer resources used Request throttling l only accept requests at a certain rate • prevent server overload, but may hamper legitimate users ¢ Request filtering l only allow requests from certain hosts l allow a fixed number of requests from a given host in a certain period • doesn't work against distributed attack ¢ Most other approaches applied elsewhere in network

Authentication breach ¢ Characteristics l ¢ attacker tries to get access by masquerading as legitimate user Needs user id and password brute-force attack l sniffing attack l cracking attack l

Authentication: brute force ¢ Execution l l ¢ user ids typically easy to find (email address, user directory on web) attempt all passwords Defense l l request throttling lock-out • stop allowing authentication after n failed trials • can create denial of service

Authentication: sniffing ¢ Execution l l ¢ copy all network traffic look for packets with authentication information Defense l use protocols in which authentication information is encrypted • FTPS instead of FTP • SSH instead of telnet • HTTPS instead of HTTP

Authentication: cracking ¢ Execution l l ¢ steal copy of encrypted password file attempt to decrypt passwords Defense l access control measures to prevent access to password files • vary by system l good passwords • more than 8 characters • combinations of numeric and non-alphanumeric, upper- and lower-case

Application attack ¢ Characteristics l application bug is exploited • often buffer overflow l inject attacker's code into system • code executes with application privileges l can be used to launch additional attacks • classic "worm" behavior ¢ Needs l l ¢ knowledge of application needs to know OS Often downloadable tools can be used

Application attack cont'd ¢ Defenses attention to software security patches l subscribe to CERT mailing list l investigate vendor's coding practices l incorporate security into development methodology l examine application logs for unexpected activities l

Malware ¢ Characteristics l user deceived into executing malicious code • Many avenues: Active. X controls, binary email attachments, web scripts Many tools exist to create l Worm behavior possible l • email replication
Malware, cont'd ¢ Defenses l anti-virus software • signatures must be updated regularly l email scanning • server-based best l application settings • IE scripting • MS Office macros • very problematic l l user education better solution • less vulnerable applications / OSes • finer grainer control

Social Engineering ¢ ¢ Scenario l Call up individual in company (typically a secretary or switchboard person) Alice l Ask for name of tech support person (Bob) l Calls 2 nd secretary Eve, claiming to work for Bob. l Tell Eve to reset her account password to the one he will give her. l Eve complies and now hacker has account access Result l 2 phone calls = security hole

Social Engineering, cont'd ¢ Characteristics l very easy to do • Kevin Mitnick's favorite method l many kinds of information are sensitive • names, job descriptions, hardware/software configuration ¢ Defense l need to know • don't give information to everyone • what they don't know, they can't reveal l security policies • "Let me call you back. " l user education

Problematic fact ¢ Many avenues for host security to be compromised simple user error is enough l a large organization will have many hosts l
![Sun Tzu on firewalls ¢ ¢ "If [the enemy] sends reinforcements everywhere, he will Sun Tzu on firewalls ¢ ¢ "If [the enemy] sends reinforcements everywhere, he will](http://slidetodoc.com/presentation_image/08ee7294b5728025a24ca0ab211f166b/image-19.jpg)
Sun Tzu on firewalls ¢ ¢ "If [the enemy] sends reinforcements everywhere, he will everywhere be weak" -- The Art of War Translation l ¢ enforcing perfect host security everywhere is impossible Solution l l force the confrontation to take place at a single known location concentrate defense at that point

Firewall A dedicated gateway machine with special security precautions on it, used to service outside network, especially Internet connections and dial-in lines. The idea is to protect a cluster of more loosely administered machines hidden behind it. . . --- FOLDOC

Firewalls ¢ Idea l l ¢ Build security measures into a single host Force all inbound and outbound Internet traffic to pass through Enables l l l establishing a single security policy that all machines share machines behind the firewall have some protection firewall machine can be specially configured

Firewall policies ¢ Both in-bound and out-bound l l ¢ what the outside world can do what local users can do Applications l which applications are accessible • boils down to port numbers ¢ Hosts l ¢ which hosts are accessible Users l which users have access

Firewall features ¢ Minimal l l ¢ Better l l ¢ port blocking host blocking configurable logging user authentication / blocking Best l stateful inspection • track the progress of individual sessions • allow only legal actions
Other features ¢ ¢ Often implemented at the firewall NAT l network address translation l internal machines can "illegal" IP addresses • can't be reached by routing l ¢ firewall pretends to originate requests VPN l virtual private network l encrypted traffic between firewall and external host authenticates and then is "inside" the firewall

Limitations ¢ Firewall only defends the connection it is on l l l ¢ ¢ dial-in not protected wireless LAN not protected walking out with a CD-ROM, etc. Firewall can't protect against malware Firewalls can't protect against malicious insiders Firewalls must be carefully configured and closely monitored Firewalls can lead to a false sense of security

Firewall types Packet-filtering ¢ Application-level gateway ¢ Circuit-level gateway ¢
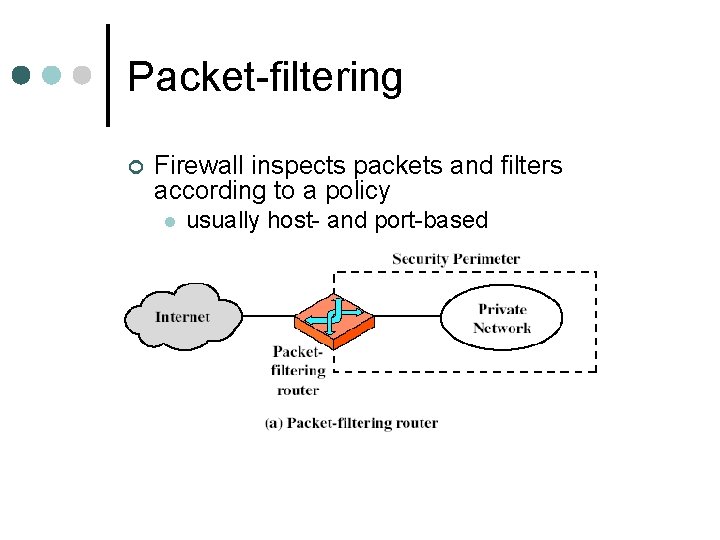
Packet-filtering ¢ Firewall inspects packets and filters according to a policy l usually host- and port-based
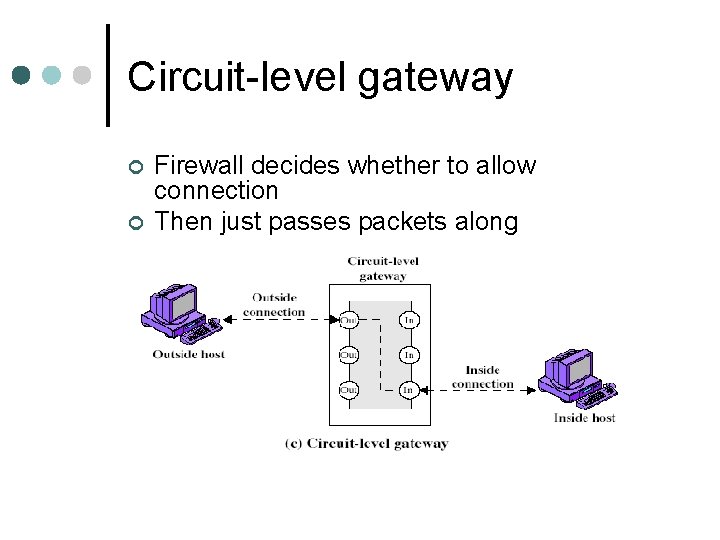
Circuit-level gateway ¢ ¢ Firewall decides whether to allow connection Then just passes packets along
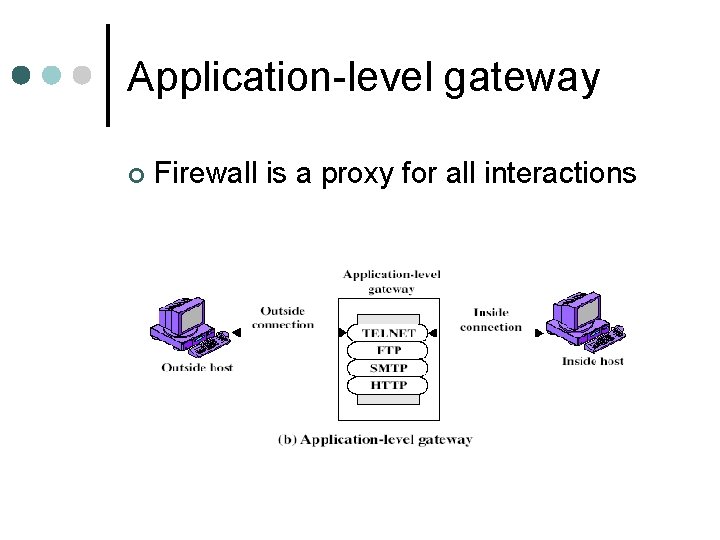
Application-level gateway ¢ Firewall is a proxy for all interactions
TCP/IP Packet ¢ Internet communication is done through packets l ¢ A packet is a fixed-size set of bytes with a specific format A typical TCP/IP packet contains: l l Source IP, Source Port, Destination IP, Destination Port Payload • message part
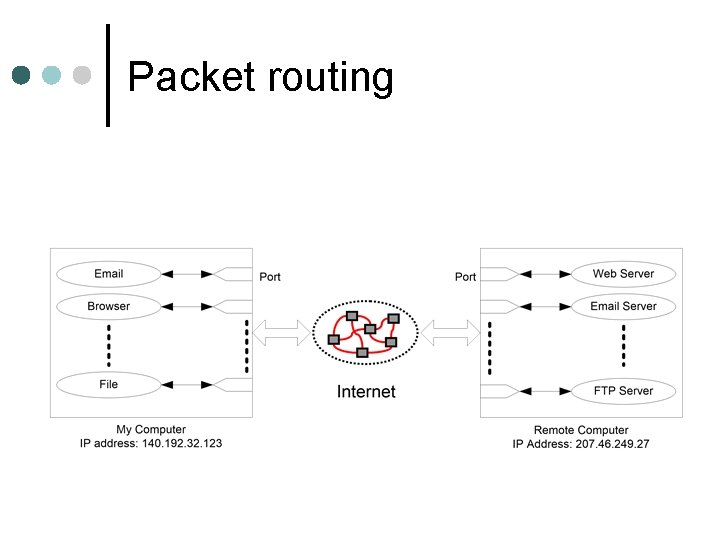
Packet routing

Packet-Filtering Router ¢ ¢ A router applies a set of rules to each IP packet and forward or discards the packet The filter is typically set up as a list of rules based on matches to fields in the IP or TCP header l The fields are source/destination IP address, port number, etc. l If there is a match to one of the rules, that rules is invoked to determine whether to forward or discard the packet l If there is no match, the a default action is taken • Default discard policy • Default forward policy
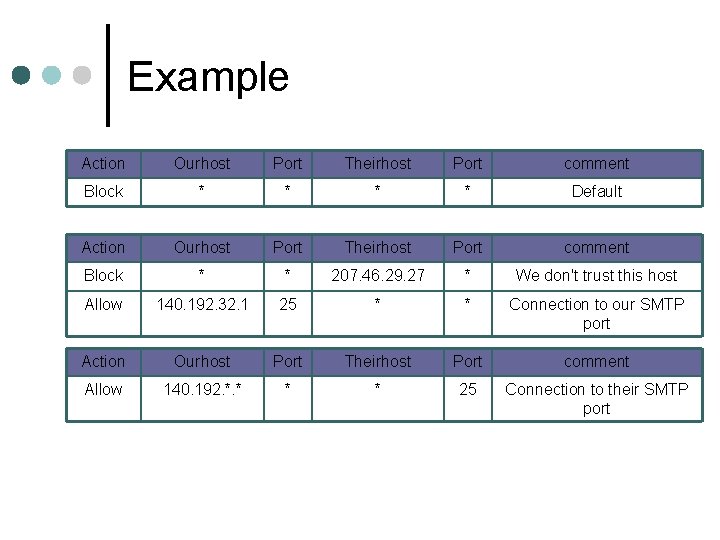
Example Action Ourhost Port Theirhost Port comment Block * * Default Action Ourhost Port Theirhost Port comment Block * * 207. 46. 29. 27 * We don't trust this host Allow 140. 192. 32. 1 25 * * Connection to our SMTP port Action Ourhost Port Theirhost Port comment Allow 140. 192. *. * * * 25 Connection to their SMTP port
Windows Firewall ¢ Note this is a software firewall l not a dedicated firewall machine

Outbound policies ¢ ¢ Typically less restrictive than in-bound But – good citizenship l make it more difficult for hackers A packet filter can reject outbound packets with illegal IP addresses l could not have been legally generated inside the network Example l 140. 192. *. * are De. Paul IP addresses l if an outbound packet has a source address of 207. 34. 102. 2 • it is probably forged

Characteristics ¢ ¢ Pluses l Packet-filtering routers are simple, transparent to users, and fast Minuses l The router cannot prevent attacks that employ application-specific vulnerabilities or functions l The logging functionality in the router is limited l Most routers do not support advanced user authentication schemes l The router is vulnerable to attacks and exploits that take advantage of flaws in TCP/IP l The routers are susceptible to security breaches caused by improper configurations
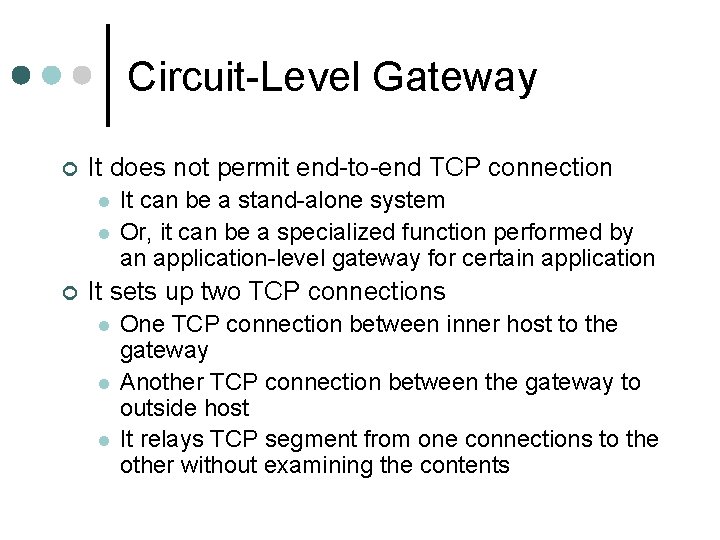
Circuit-Level Gateway ¢ It does not permit end-to-end TCP connection l l ¢ It can be a stand-alone system Or, it can be a specialized function performed by an application-level gateway for certain application It sets up two TCP connections l l l One TCP connection between inner host to the gateway Another TCP connection between the gateway to outside host It relays TCP segment from one connections to the other without examining the contents

Characteristics ¢ Pluses l l ¢ Each established connection can be logged Can protect against some Do. S attacks Minuses l l May slow establishment of TCP connections Does not protect against attack to legal services • buffer overflow
Application-level gateway ¢ ¢ Also "proxy server" The firewall relays application-level traffic l l ¢ external host contacts gateway contacts internal host If the gateway does not support a specific application l the service cannot be forwarded across the firewall

Characteristics ¢ Pluses l l l ¢ every operation can be inspected and logged user authentication can be done at the gateway identity of internal system is hidden Minuses l l l slowest firewall hardest to configure costliest
Asymmetric gateway Application-level gateway on inbound connections ¢ Circuit-level gateway on outbound connections ¢ internal users implicitly trusted l lower overhead l

Bastion host ¢ From firewall definition "dedicated gateway machine" l "special security precautions" l ¢ Precondition for gateway firewalls need a computer to perform gateway operations l but this computer is the first thing hackers will attack l

Host ¢ Secure operating system l Open. BSD Minimal services installed ¢ Very restrictive authentication ¢ l ¢ one-time passwords Often some type of write-once logging l CD-ROM, uni-directional tape

Proxy software ¢ ¢ ¢ Specialized proxy software for each service being gatewayed Relay only to specific internal hosts Each proxy process runs without disk access l ¢ ¢ except for startup Each proxy process runs with minimal system privileges Each proxy process maintains detailed logs

Example firewalls singled-homed screened host ¢ dual-homed screen host ¢ screened-subnet ¢
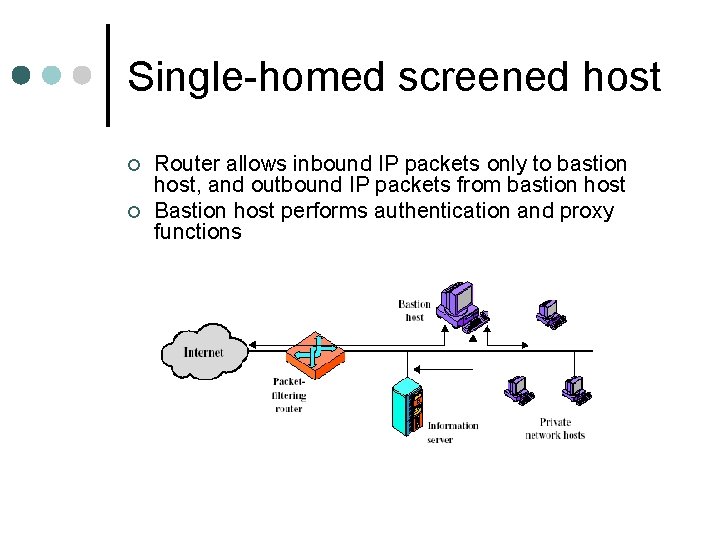
Single-homed screened host ¢ ¢ Router allows inbound IP packets only to bastion host, and outbound IP packets from bastion host Bastion host performs authentication and proxy functions
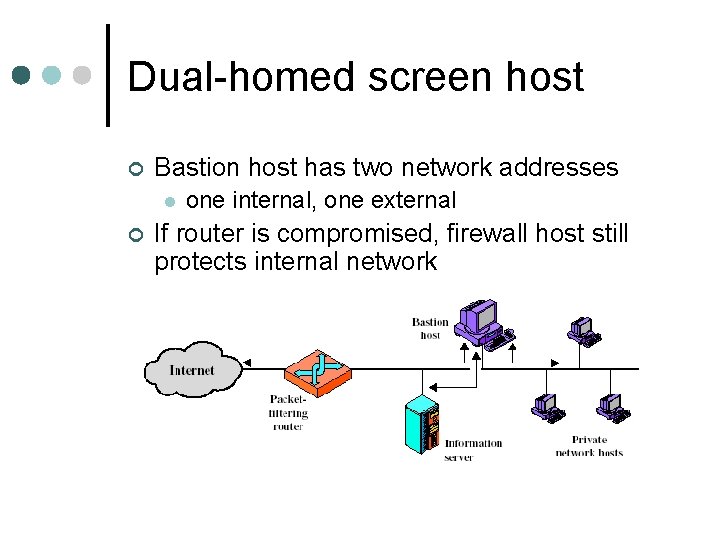
Dual-homed screen host ¢ Bastion host has two network addresses l ¢ one internal, one external If router is compromised, firewall host still protects internal network
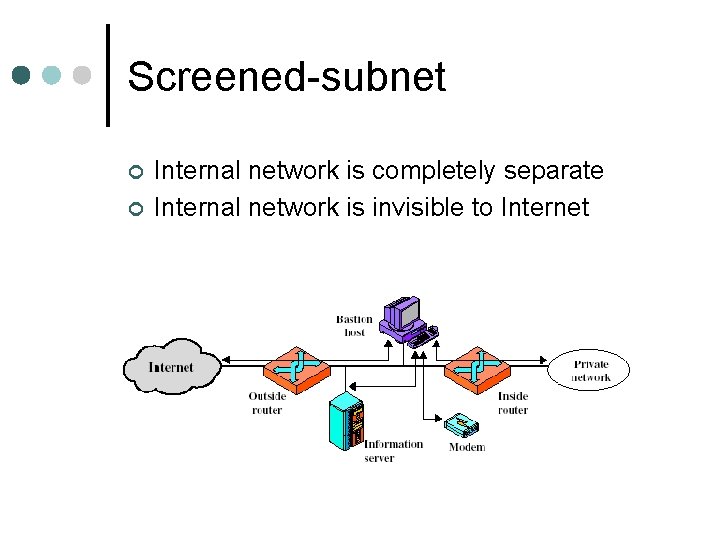
Screened-subnet ¢ ¢ Internal network is completely separate Internal network is invisible to Internet
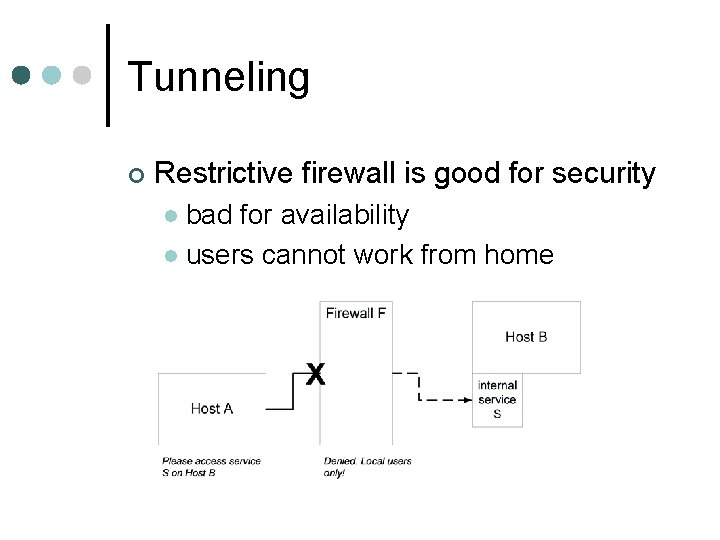
Tunneling ¢ Restrictive firewall is good for security bad for availability l users cannot work from home l
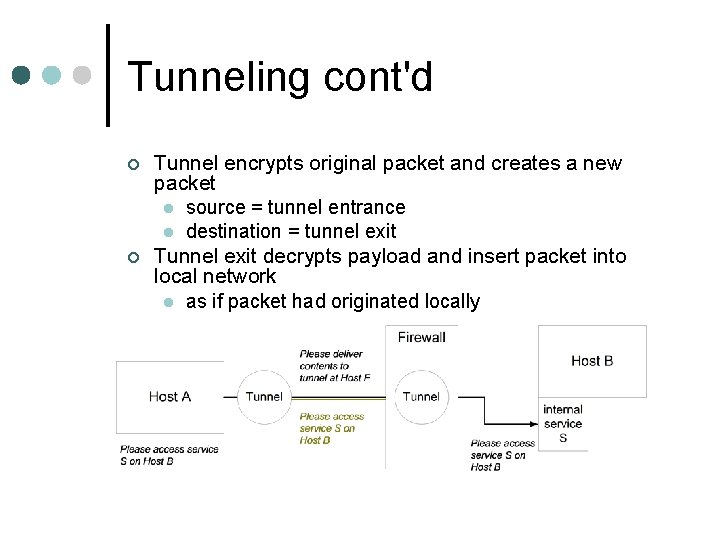
Tunneling cont'd ¢ ¢ Tunnel encrypts original packet and creates a new packet l source = tunnel entrance l destination = tunnel exit Tunnel exit decrypts payload and insert packet into local network l as if packet had originated locally

IPsec ¢ Goals authenticate packet origins l provide integrity for packet contents l encrypt packets l tunnel packets l

IPsec, cont'd Two protocols ¢ Authentication Header Protocol ¢ authentication + integrity Packet Encryption Protocol l authentication + integrity + confidentiality

Authentication Header Protocol ¢ source IP cannot be spoofed depends on secret key agreement l based on public key certificates l ¢ message contents cannot be modified secure hash of payload is computed by sender l verified by receiver l

Packet Encryption Protocol Use AHP and ¢ Symmetric encryption of packet payload ¢ Diffie-Helman key agreement is part of protocol ¢

Security association ¢ Endpoints of tunnel must agree on protocol type l cryptographic algorithms l keys l duration of key l ¢ Each packet contains an identifier l labeling the particular security association used for that packet
VPN ¢ Establish a tunnel between l l ¢ remote user (or site) local firewall Requires l l availability of IPsec installing VPN software on each remote client VPN server at firewall, called the gateway public key certificate for gateway

VPN, cont'd ¢ Users access Internet normally (dial-up, DSL, etc. ) l then turn on VPN l VPN has authentication procedure l User's machine becomes part of the internal network l • inside the firewall

VPN, cont'd ¢ ¢ Need good authentication of users l because once authenticated, machine becomes virtually local l "trusted" Tunnel is reasonably secure l IPsec cryptographic hash protects against modification l DH key exchange provides mechanism to share secret keys l secret key exchange prevents session hijacking l server public key certificate protects against man-inthe-middle

Next week ¢ Web application security l online reading
- Slides: 59