INTERNET SAFETY Powerpoint Templates Page 1 WHAT IS





































- Slides: 57

INTERNET SAFETY Powerpoint Templates Page 1

WHAT IS INTERNET SAFETY? - it refers to the online security or safety of people and their information when using internet. Powerpoint Templates Page 2

NETIQUETTE - is network etiquette, the do's and don'ts of online communication. Powerpoint Templates Page 3

10 BEST RULES OF NETIQUETTE 1. The Golden Rule. - treat others as you would like to be treated. Powerpoint Templates Page 4

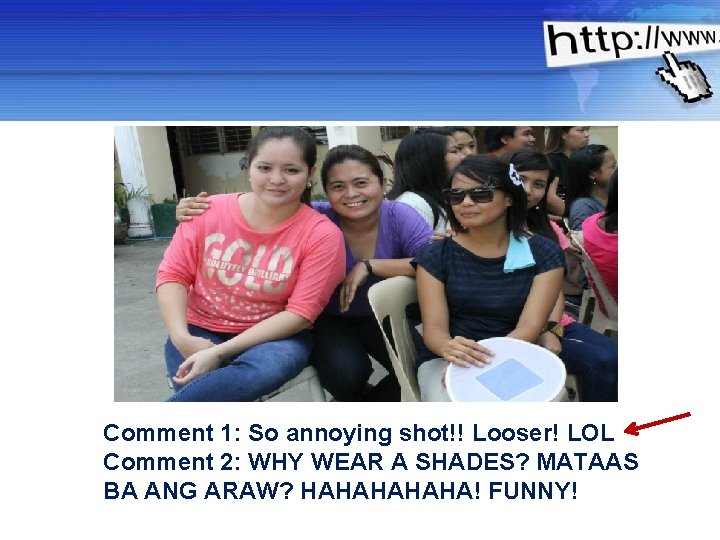
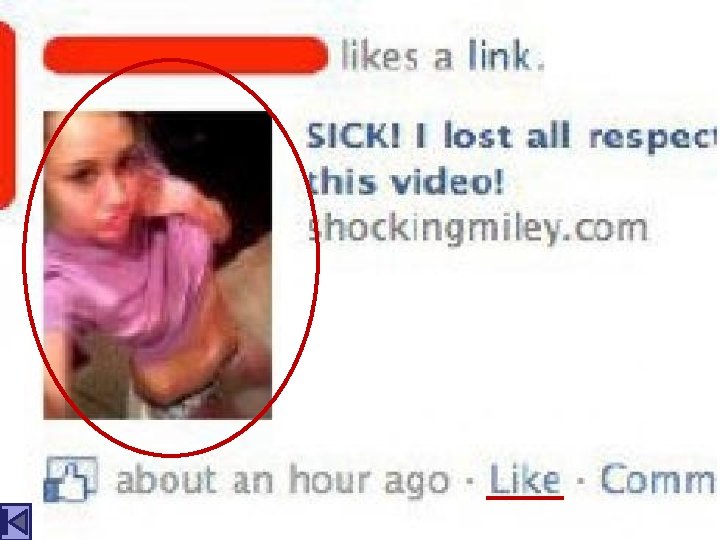
10 BEST RULES OF NETIQUETTE 2. NO Flaming FLAME – is a personal insult communicated through the internet. - watch your posts or comments Powerpoint Templates Page 5

Comment 1: So annoying shot!! Looser! LOL Comment 2: WHY WEAR A SHADES? MATAAS BA ANG ARAW? HAHAHA! FUNNY! Powerpoint Templates Page 6

Powerpoint Templates Page 7

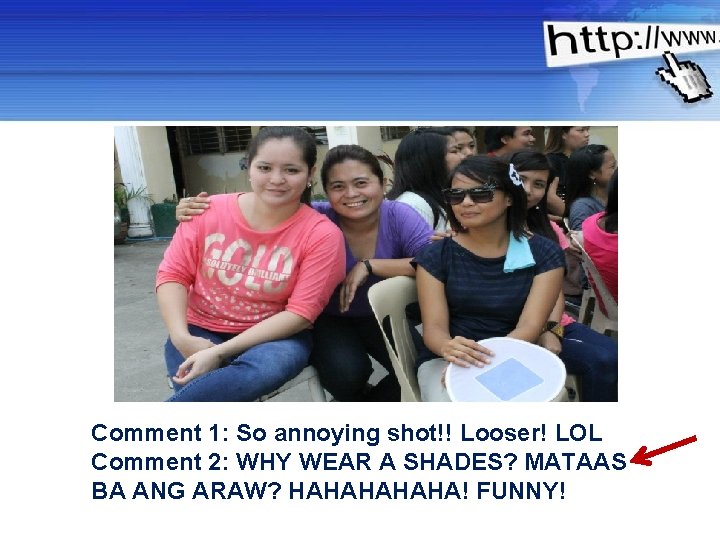
10 BEST RULES OF NETIQUETTE 3. Don’t Type in ALL CAPS - people may misinterpret it. Powerpoint Templates Page 8

Comment 1: So annoying shot!! Looser! LOL Comment 2: WHY WEAR A SHADES? MATAAS BA ANG ARAW? HAHAHA! FUNNY! Powerpoint Templates Page 9

Powerpoint Templates Page 10

10 BEST RULES OF NETIQUETTE Powerpoint Templates Page 11

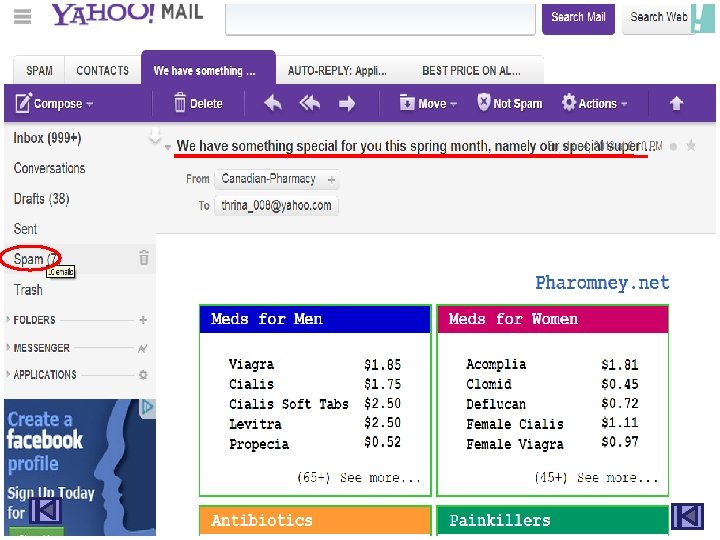
10 BEST RULES OF NETIQUETTE 4. Don’t Spam SPAM- it is any unsolicited email from unknown sources. Powerpoint Templates Page 12

Powerpoint Templates Page 13

10 BEST RULES OF NETIQUETTE 5. Don’t talk with people you do not know - do not arrange to met anyone you meet online Powerpoint Templates Page 14

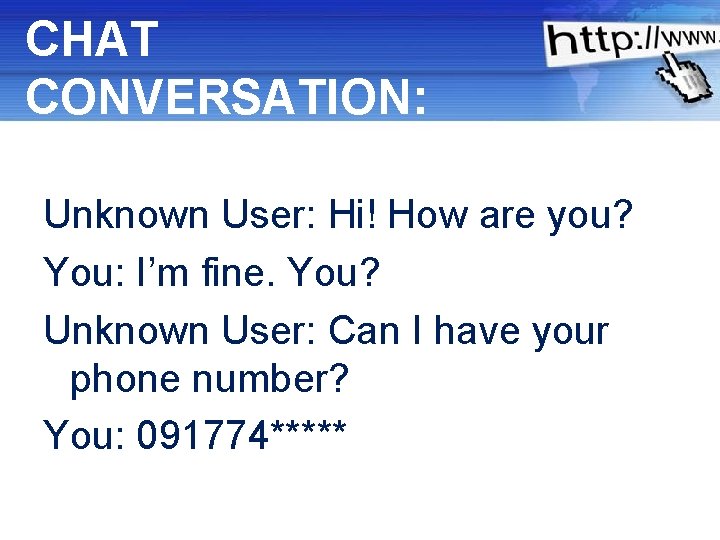
CHAT CONVERSATION: Unknown User: Hi! How are you? You: I’m fine. You? Unknown User: Can I have your phone number? You: 091774***** Powerpoint Templates Page 15

10 BEST RULES OF NETIQUETTE 6. Obey Copyright Laws - don’t steal someone else’s idea, property, and rights. Powerpoint Templates Page 16

10 BEST RULES OF NETIQUTTE 7. Use Proper Grammar and Spelling - errors diminish the credibility of the message Powerpoint Templates Page 17

10 BEST RULES OF NETIQUTTE Example: I leik these pecture so very nyss. Lol Powerpoint Templates Page 18

10 BEST RULES OF NETIQUETTE 8. Be HONEST / Be Yourself - tell the truth - do not pretend to be someone else. Powerpoint Templates Page 19

10 BEST RULES OF NETIQUETTE 9. Follow the TOS – Terms of Service - rules and policy of the sites. Powerpoint Templates Page 20

10 BEST RULES OF NETIQUETTE 10. Shop Secure Sites - these are sites with Transport Layer Security (TLS) or Socket Layer Security (SLS) Powerpoint Templates Page 21

10 BEST RULES OF NETIQUETTE Powerpoint Templates Page 22

CYBER BULLYING ‘Demystifying and Deescalating Cyber Bullying’ Barbara Trolley, Ph. D. CRC Connie Hanel, M. S. E. d Linda Shields, M. S. E. d. Powerpoint& Templates Page 23

WORKSHOP GOALS • • Terminology Assessment Issues & Protocol Decision Tree ‘PEAS’ PROGRAM: Psychological, Educational and Social School Response Powerpoint Templates Page 24

CYBER BULLYING IS… Being cruel to others by sending or posting harmful material using technological means; an individual or group that uses information and communication involving electronic technologies to facilitate deliberate and repeated harassment or threat to an individual or group. Also known as: ‘Electronic Bullying’ & ‘Online Social Cruelty’ Powerpoint Templates Page 25

CYBER BULLIES’ TECHNOLOGY q. E-mail q. Cell phones q. Pager text messages q. Instant messaging q. Defamatory personal web sites q. Defamatory online personal polling web sites q. Chat rooms Powerpoint Templates Page 26

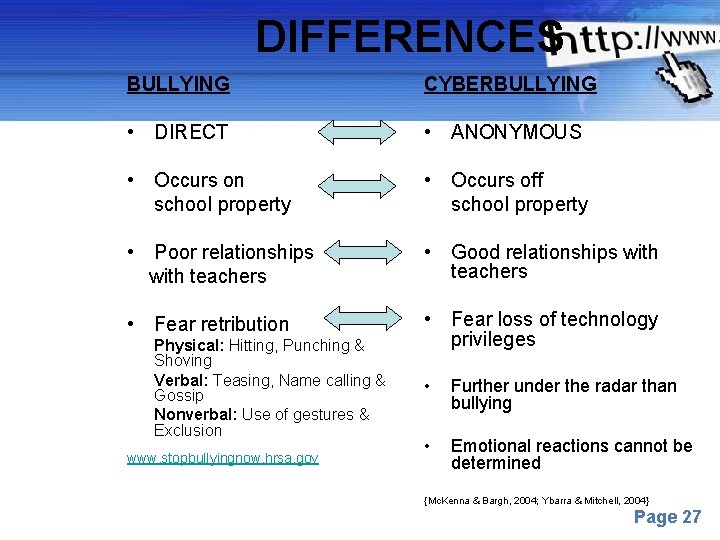
DIFFERENCES BULLYING CYBERBULLYING • DIRECT • ANONYMOUS • Occurs on school property • Occurs off school property • Poor relationships with teachers • Good relationships with teachers • Fear retribution • Fear loss of technology privileges Physical: Hitting, Punching & Shoving Verbal: Teasing, Name calling & Gossip Nonverbal: Use of gestures & Exclusion www. stopbullyingnow. hrsa. gov • Further under the radar than bullying • Emotional reactions cannot be determined {Mc. Kenna & Bargh, 2004; Ybarra & Mitchell, 2004} Powerpoint Templates Page 27

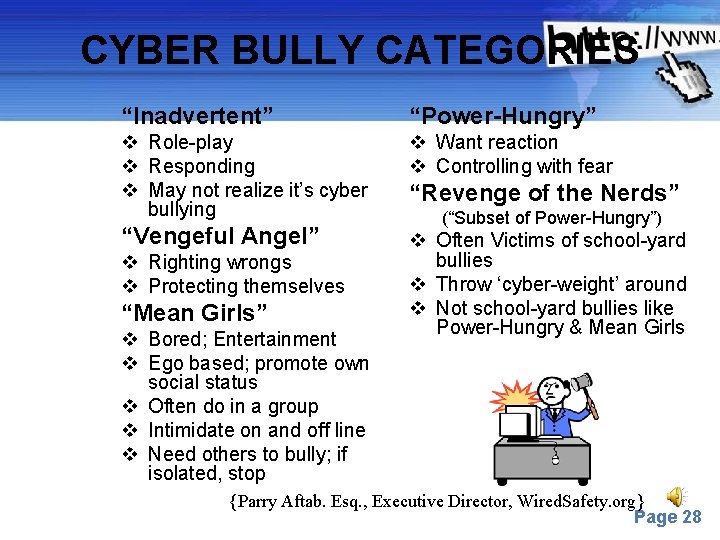
CYBER BULLY CATEGORIES “Inadvertent” “Power-Hungry” v Role-play v Responding v May not realize it’s cyber bullying v Want reaction v Controlling with fear “Vengeful Angel” v Often Victims of school-yard bullies v Throw ‘cyber-weight’ around v Not school-yard bullies like Power-Hungry & Mean Girls v Righting wrongs v Protecting themselves “Mean Girls” v Bored; Entertainment v Ego based; promote own social status v Often do in a group v Intimidate on and off line v Need others to bully; if isolated, stop “Revenge of the Nerds” (“Subset of Power-Hungry”) {Parry. Powerpoint Aftab. Esq. , Templates Executive Director, Wired. Safety. org} Page 28

CYBER BULLYING TYPES • “Flaming’: Online fights using electronic messages with angry and vulgar language • “Harassment”: Repeatedly sending offensive, rude, and insulting messages • “Cyber stalking”: Repeatedly sending messages that include threats of harm or are highly intimidating. Engaging in other on-line activities that make a person afraid for his or her own safety • “Denigration”: ‘Dissing’ someone online. Sending or posting cruel gossip or rumors about a person to damage his or her reputation or friendships Powerpoint Templates Page 29

CYBER BULLYING TYPES • “Impersonation”: Pretending to be someone else and sending or posting material online that makes that person look bad, gets that person in trouble or danger, or damages that person’s reputation or friendships • “Outing and Trickery”: Sharing someone’s secret or embarrassing information online. Tricking someone into revealing secrets or embarrassing information which is then shared online • “Exclusion”: Intentionally excluding someone from an on-line group, like a ‘buddy list’ {Nancy Willard, M. S. , J. D. , Director of the Center for Safe and Responsible Internet Use} Powerpoint Templates Page 30

CYBER BULLYING PREVALENCE • Cyber bullying typically starts at about 9 years of age and usually ends after 14 years of age; after 14, it becomes cyber or sexual harassment due to nature of acts and age of actors {Aftab} • Affects 65 -85% of kids in the core group directly or indirectly through close friends (Aftab) Powerpoint Templates Page 31

CYBER BULLYING PREVALENCE • Aftab’s statistics: v 90% of middle school students they polled had their feelings hurt online v 65% of their students between 8 -14 have been involved directly or indirectly in a cyber bullying incident as the cyber bully, victim or friend v 50% had seen or heard of a website bashing of another student v 75% had visited a website bashing v 40% had their password stolen and changed by a bully (locking them out of their own account) or sent communications posing as them v Problems in studies: not assessing the ‘real thing’ i. e. Only 15% of parent polled knew what cyber bullying Powerpoint Templates was Page 32

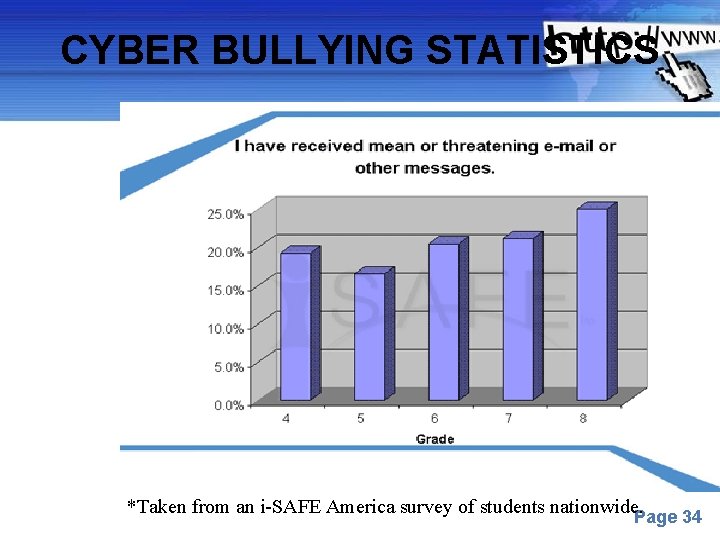
CYBER BULLYING PREVALENCE In the 2003 -04 school year, i-SAFE America surveyed students from across the country on a new topic: Cyber Bullying It is a topic that not many adults were talking about but one that is all too familiar with students. • 42% of kids have been bullied while online. 1 in 4 have had it happen more than once. • 35% of kids have been threatened online. Nearly 1 in 5 have had it happen more than once. • 21% of kids have received mean or threatening e-mail or other messages. • 58% of kids admit someone has said mean or hurtful things to them online. More than 4 out of 10 say it has happened more than once. • 53% of kids admit having said something mean or hurtful to another person online. More than 1 in 3 have done it more than once. • 58% have not told their parents or an adult about something mean or hurtful that happened to them online. Powerpoint Templates Based on 2004 i-SAFE survey of 1, 500 students grades 4 -8 Page 33 http: //www. isafe. org

CYBER BULLYING STATISTICS Powerpoint Templates *Taken from an i-SAFE America survey of students nationwide. Page 34

CYBER BULLYING LEGAL ISSUES Who May Be Involved: School Limits: Schools have policies against bullying § School Counselor § Principal § Resource Officer § Police § Attorney (School or Private) Civil Law Limits: Cyber bullying may also meet standards for ‘institutional torts’ (wrongdoings) § Superintendent Defamation § Internet Service Provider Material that Constitutes an Invasion of Privacy (1 st Amendment) General (Willard, 2005) Powerpoint Templates. Intentional Infliction of Emotional Distress Page 35

CYBER BULLYING LEGAL ISSUES Criminal Law Limits The following kinds of speech can lead to arrest & prosecution: • Making threats of violence to people or their property • Engaging in coercion • Making obscene or harassing phone calls • Harassment or stalking • Hate or bias crimes • Creating or sending sexually explicit images of teens • Sexual exploitation • Taking a photo of someone in place where privacy expected Powerpoint Templates General (Willard, 2005) Page 36

CYBER BULLYING LEGAL ISSUES ‘Educator’s Guide To Cyber bullying: Addressing the Harm of On-line Social Cruelty’ (Nancy Willard, 2005) Law Enforcement should be contacted if educator becomes aware of: • Death threats or threats of other forms of violence to a person or property • Excessive intimidation or extortion • Threats or intimidation that involve any form of bias or discrimination • Any evidence of sexual exploitation Powerpoint Templates Page 37

CYBER BULLYING LEGAL ISSUES ‘Offsite Internet Activities and Schools’ (Copyright 2005 Parry Aftab, Esq. All rights reserved) Conflicting decisions in regard to school’s authority with respect to cases under state and federal jurisdictions School should seek legal consult often beyond regular school attorney (e. g. , a constitutional or cyber-free speech lawyer) • • • ‘Within School Authority’ Guidelines: Clear-cut threats Clearly disruptive of school discipline encouraged to visit website; student accesses or works on website in school School owned website or school-sponsored project website Any proof of in-school impact (e. g. , materials on grounds; psychosocial, behavioral or academic impact on others) Proof the student’s website or harassment has had impact on staff (e. g. , quits, leave of absence, medical TX for emotional issues)otherwise seek outside legal recourse Powerpoint Templates Page 38

CYBER BULLYING LEGAL ISSUES ‘What Everyone Needs to Know About Cyber Bullying’ (Aftab) Many cases of child cyber bullying, like adult counterparts of cyber-harassment, not criminal Law Enforcement needs to be aware of: • Difference between annoying and dangerous communications • How to investigate a cyber crime • How to obtain information from an ISP Powerpoint Templates Page 39

CURRENT ANTI-BULLYING PROGRAMS Traditional Program Concerns (Fleming, Towey, Limber, Gross, Rubin, Wright & Anderson, 2002) Zero Tolerance & “ 3 Strikes & Out” Negatively impacts on willingness to report Casts large net Bullies need pro-social role models Anger Management, Skill Building, Empathy Building, Self-Esteem Enhancement Group members serve as role models & reinforcers of bullying, anti-social behavior Bullies don’t need self-esteem boosted Mediation Appropriate in cases of equal power, not bully & victim Parallels possible in doing mediation in domestic violence Appropriate message to bullies: Your behavior is inappropriate, won’t be tolerated Message to victim: No one Powerpoint deserves to be bullied and we’re going to try to Templates stop it Page 40

CURRENT ANTI-BULLYING PROGRAMS Articles: § § § “Zero Tolerance Policies Encourage ‘Lockdown Environment’ in Schools”(Fuentes, 2003) “One Strike and You’re Out of School” (Joiner, 2004) Youthful suicide, financial ruin, families torn apart for minor infractions. : How post Columbine hysteria is wrecking lives “Every Child is Worth Saving” (http: //endzeroltolerance. com) Additional Lists of Articles & Commentaries § ‘News” (http: //www. jlc. org/EZT/News/default/html? id=Jan 05) Summary Children taught to not fight back Frequently have adults such as teachers ‘protect’ them Those being bullied often want friends or are fearful so don’t ‘narc’ Having been bullied, may have poor self-esteem All involved in cyber bullying not caught, assessed or disciplined Powerpoint Templates Adults may be seemingly unresponsive …. . retaliation on-line Page 41

CURRENT CYBER BULLYING PROGRAMS & RESONSES (Aftab, Power. Point communication) PROGRAM OFFERINGS: Ø Teenangels. org: trains teens & preteens to be part of solution Ø Wired. Kids and Wired. Teens” programs for schools and communities Ø Wiredsafety. org: one to one hotline and multiple resources Videos, Lesson Plans and Activities Ø Parent and Community Programs Ø Law enforcement training and briefings Ø Local county level summits on cyber bullying Ø Assistance on. Powerpoint technological software & tools to help Templates Page 42

CURRENT CYBER BULLYING PROGRAMS & RESPONSES What Everyone Needs to Know About Cyber bullying’ (Aftab) Education of Children: • All actions have consequences • Cyber bullying hurts • They are just being used and manipulated by cyber bully • Cyber bully and accomplices often become the target of cyber bullying themselves • Care about others and stand up for what’s right Powerpoint Templates Page 43

CURRENT CYBER BULLYING PROGRAMS & RESPONSES Comprehensive Plan (Willard, 2005) Schools Ø Policies concerning misuse of technology Ø Evaluate how staff is and can more effectively monitor Internet use Parents Ø Discuss cyber bullying Ø Supervise and increase effective monitoring of Internet use Since more adults supervise, more children will hide activities, strategies needed to change social norms in these on-line works, empower the victim with knowledge how to prevent & respond, & to discourage bullies from engaging in such activities Powerpoint Templates Page 44

CURRENT CYBER BULLYING PROGRAMS & RESPONSES Schools should: • Focus on values of kindness and respectful human relations • Enhancement of empathic awareness • Develop effective problem solving skills • Empowerment of bystanders Powerpoint Templates Page 45

CURRENT CYBER BULLYING ASSESSMENT (Willard, 2005) Specific Step Wise Plan: 1 Engage in participatory planning {Integrate into Safe Schools. District Technology Awareness; Non-school Participants} 2 Conduct needs assessment {Assessment available at Center for Safe & Responsible Internet Use} 3 Ensure that an effective anti--bullying program in place {core not authoritarian values; predictive empathy; peer norms vs. bullying; peer intervention skills, effective administrative responses} 4 Review policies & Procedures {Monitoring, report box, internet & other technological pp} 5 Conduct Professional Development {key individual sophisticated in the area; all administrators, librarians, counselors and technology educators basic understanding; all other staff alerted to existence, how to detect} 6 Provide Parent Education {prevention, detection & intervention strategies; alert child to potential consequences of school discipline, loss of family account, civil litigation, criminal prosecution} Powerpoint Templatesprograms} 7 Evaluate {prevention & intervention Page 46

CURRENT CYBER BULLYING PROGRAMS & RESPONSES Intervention Strategies for Cyber bullying Directed at Student 1 -Save the evidence 2 -Conduct a threat assessment {if cyber bullying poses substantial disruption, violence or suicide concerns; contact law enforcement if threats of violence} 3 -Assesss response options {direct school nexus may warrant school disciplinary action; if off campus and not substantial threat, no disciplinary action but help victim} 4 -Identify the Perpetrators {technical assistance; assess validity of person’s identity; offer technical assistance to parents} 5 -Supprt the victim {even if no disciplinary action, offer support and assistance to victim and parents; offer counseling mediation, technical assistance; direct to community resources} 6 -Provide guidance on how to remove the speech 7 -Seek to use informal resolution strategies {contact perpetrator parents, offer assistance, suggest legal consultation; offer counseling, mediation in school; recognize the cyber bully is a hurt kid and try to help both victim and perpetrator Intervention Strategies for Cyber bullying Directed at Staff 1 - Assess Type of Speech Powerpoint Templates Page 47 2 - Take action based on assessment

CURRENT CYBER BULLYING ASSESSMENT What Everyone Needs to Know About Cyber bullying’ (Aftab) Assessment to differentiate between ‘rude communications’ and ‘cyber bullying’: 1 - Kind of Threats 2 - Frequency of Threat 3 - Source of Threats 4 - Nature of the Threats … The more frequent, the greater the threat, the mention of more dangerous methods & the involvement of third parties tends to increase the seriousness of the threat Powerpoint Templates Knowing the cyber bully may increase or decrease threat Page 48

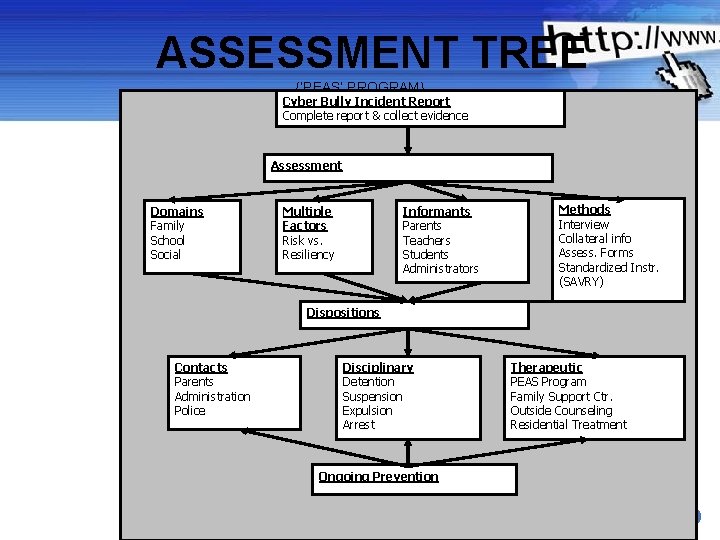
ASSESSMENT TREE {‘PEAS’ PROGRAM} Cyber Bully Incident Report Complete report & collect evidence Assessment Domains Family School Social Multiple Factors Risk vs. Resiliency Informants Parents Teachers Students Administrators Methods Interview Collateral info Assess. Forms Standardized Instr. (SAVRY) Dispositions Contacts Parents Administration Police Disciplinary Detention Suspension Expulsion Arrest Therapeutic PEAS Program Family Support Ctr. Outside Counseling Residential Treatment Ongoing Prevention Powerpoint Templates Page 49

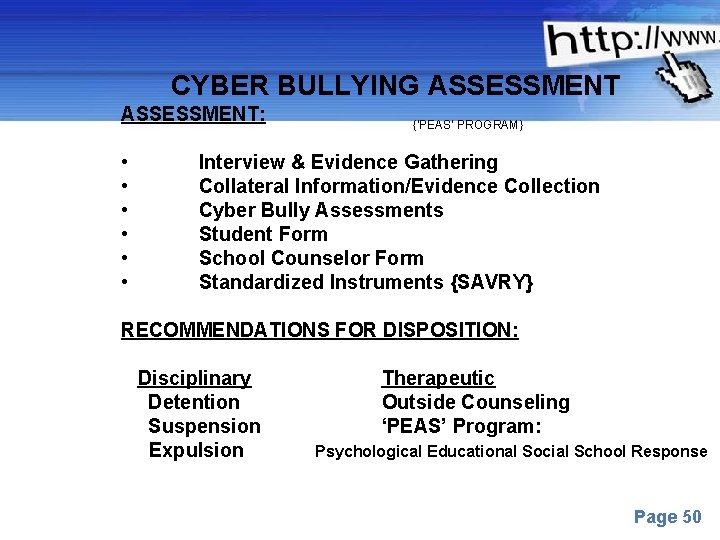
CYBER BULLYING ASSESSMENT: • • • {‘PEAS’ PROGRAM} Interview & Evidence Gathering Collateral Information/Evidence Collection Cyber Bully Assessments Student Form School Counselor Form Standardized Instruments {SAVRY} RECOMMENDATIONS FOR DISPOSITION: Disciplinary Detention Suspension Expulsion Therapeutic Outside Counseling ‘PEAS’ Program: Psychological Educational Social School Response Powerpoint Templates Page 50

‘PEAS’ PROGRAM Psychological-Educational-And-Social ‘P’-PSYCHOLOGICAL: 1. Outside Counseling Referral 2. Family Support Center Referral 3. In-School Counseling 4. Anger Management group 5. Peer Mediation & Conflict Resolution {cyber bullies} 6. Apology & Impact Statement 7. ‘On-Line Safe Box’ Powerpoint Templates Page 51

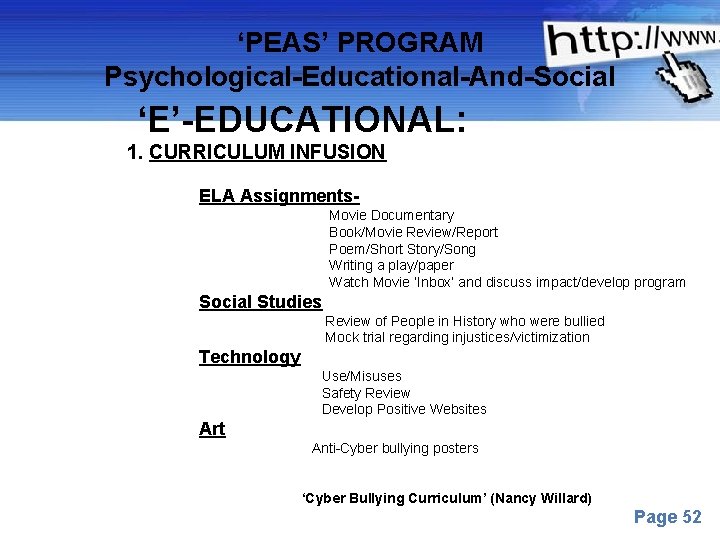
‘PEAS’ PROGRAM Psychological-Educational-And-Social ‘E’-EDUCATIONAL: 1. CURRICULUM INFUSION ELA Assignments. Movie Documentary Book/Movie Review/Report Poem/Short Story/Song Writing a play/paper Watch Movie ‘Inbox’ and discuss impact/develop program Social Studies Review of People in History who were bullied Mock trial regarding injustices/victimization Technology Use/Misuses Safety Review Develop Positive Websites Art Anti-Cyber bullying posters ‘Cyber Bullying Curriculum’ (Nancy Willard) Powerpoint Templates Page 52

‘PEAS’ PROGRAM Psychological-Educational-And-Social ‘E’-EDUCATIONAL: Continued 2. PEER MATCHING: Higher/lower grade reading, tutor Higher/lower grade play production Higher/lower grade cyber bully {‘recovered’/’charged’} Pen Pals Extracurricular Activities (match cyber bullyer/ee) 3. SCHOOL ASSEMBLIES: High school student small group discussion on impact/consequences of cyber bullying/being cyber bullied Lawyer to discuss possible legal consequences/ Former student, possibly at the high school, involved in cyber bullying, and/or legally charged for cyber bullying Current Teacher/Administrator/Parent involved in cyber bullying Powerpoint Templates Page 53

‘PEAS’ PROGRAM Psychological-Educational-And-Social ‘E’-EDUCATIONAL: Continued 4. DEVELOPMENT OF PUBLIC SERVICE ANNOUNCEMENTS: 5. PARENT EDUCATION: Uses/Misuses of Technology Supervision Strategies 6. SCHOOL STAFF IN-SERVICES: Types Assessment Responses Program Evaluation Powerpoint Templates Page 54

‘PEAS’ PROGRAM Psychological-Educational-And-Social ‘S’-SOCIAL: 1. EXTRACURRICULAR/PROJECTS: Intramural/Projects between Classes Beyond Sports Homework Completion & Pizza Party Fundraising & Award/Rewards School Socials Plays on Topic Art contest School/Community Newspaper article Visit to Foster care/geriatric settings 2. DRESS POLICY: Dress Code - Decrease Comparisons & Possibility of ‘Deviant Dress’ 3. PEER MATCHING: Higher/lower grade reading, tutor Higher/lower grade play production Higher/lower grade cyber bully {‘recovered’/’charged’} Pen Pals Powerpoint Templates Extracurricular Activities (match cyber bullyer/ee) Page 55

CONCLUDING THOUGHTS A Need For: Ø A better understanding of what cyber bullying is Ø Addressing appropriate computer protocol and specifically cyber bullying via the schools’ clearly defined and systematically implemented AUP so that schools can provide intervention even in instances that occur outside of school Ø Clearer delineation of school responsibility in responding to incidents, especially off school grounds Ø Clearer school policies and action plans; increased continuity in implementing school responses Ø Increased assessment of incidents and those involved Ø Decision making regarding the cyber bully and the individual being cyber bullied based on: A decision tree protocol Assessment process Ø Systematic, therapeutic responses, not isolated disciplinary reactions Ø Integration of educational, psycho-social interventions Ø Inclusion of prevention measures that are comprehensive and systemic in approach Ø Communication among students, counselors, teachers, administrators, parents & community Ø Individualized responses, with understanding that a wide degree of variation exists in motivation Ø Change needs to come from all levels and grades: Individual Classroom School culture Ø Victimization often occurs with both the person being cyber bullied and the cyber bully Ø Important to ‘not throw the baby out with the bathwater’… Our children are not disposable! Powerpoint Templates Page 56

THE END Powerpoint Templates Page 57