Internet Quarantine Requirements for Containing SelfPropagating Code David

















- Slides: 30

Internet Quarantine: Requirements for Containing Self-Propagating Code David Moore, Colleen Shannon, Geoffrey M. Voelker, Stefan Savage University of California, San Diego Published: IEEE Infocom 03, San Francisco Presented By: Darshan Purandare

Outline q Introduction q Background § What’s worm, especially Code-Red § Prevention, Treatment and Containment of the worm q Model § SI epidemic model and Code Red propagation model q Idealized Deployment q Practical Deployment q Conclusion

Introduction q Dramatic Increase of “worm” outbreaks q Code-Red recovery cost in excess of $2. 6 billion q Still unequipped to tackle such system and software vulnerabilities q Factors for the spread of epidemic infections § Vulnerability of population § Length of Infectious period § Rate of Infection q These map to § Prevention § Treatment § Containment

Prevention q Reduces the size of the vulnerable population q Limits the worm outbreak q Vulnerability == function (Insecure S/W Engg Practices) q System and Software security are widely researched q Pro-active prevention measures are not enough

Treatment q Virus detectors and system update feature in MS Windows q Reduces vulnerable population q Reduces rate of infection q Can’t provide short-term relief during acute outbreak q Time to design, develop and test security update q Insignificant for actively spreading worms q Took on an average 16 days to eliminate Code-Red vulnerability, many were pending till 6 weeks later

Containment q Containment is used to protect individual networks, and isolate infected hosts q Firewalls, Content Filters and Automated routing blacklists q Reduce/Stops spread of infection q During Code-Red epidemic § Blocking inbound access to TCP port 80 § Content filtering based on Code-Red specific signature § Isolating infected hosts (blocking hosts outbound access to TCP port 80) q These quarantine measures gave limited protection to portions of the internet, if not halt the spread of infection

Why Containment is so important ? ? ? q Most viable alternative among all three q It can be completely automated q Can be deployed in the network q Its possible to implement a solution w/o requiring universal deployment on every internet hosts

Aims and Approach q To investigate use of widespread containment mechanisms q Authors don’t propose any particular technology for detection and containment of worms “How effectively can any containment approach counter a worm epidemic on the internet? ”…… q Consider containment systems in 3 abstract properties § Detection and Reaction Time § Strategy for Identification and Containment of the pathogen § Breadth and Topological Placement of Containment System q Used Code-Red empirical Internet topology data for simulation and analysis of a worm spread under various defense mechanisms

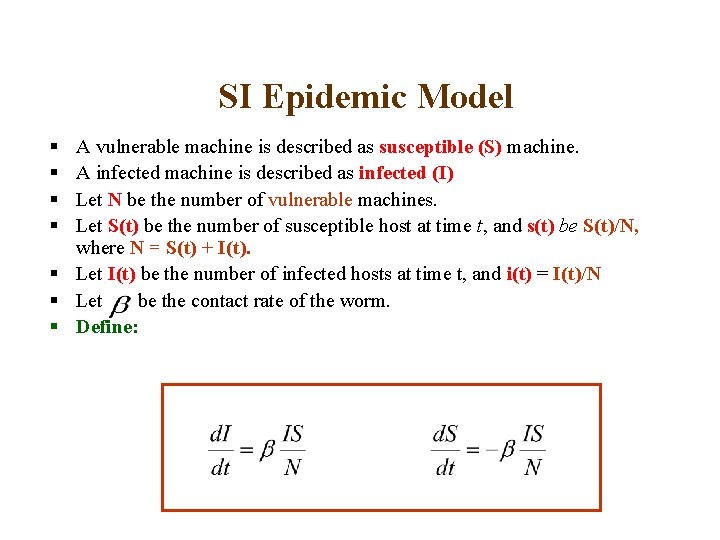
SI Epidemic Model § § A vulnerable machine is described as susceptible (S) machine. A infected machine is described as infected (I) Let N be the number of vulnerable machines. Let S(t) be the number of susceptible host at time t, and s(t) be S(t)/N, where N = S(t) + I(t). § Let I(t) be the number of infected hosts at time t, and i(t) = I(t)/N § Let be the contact rate of the worm. § Define:

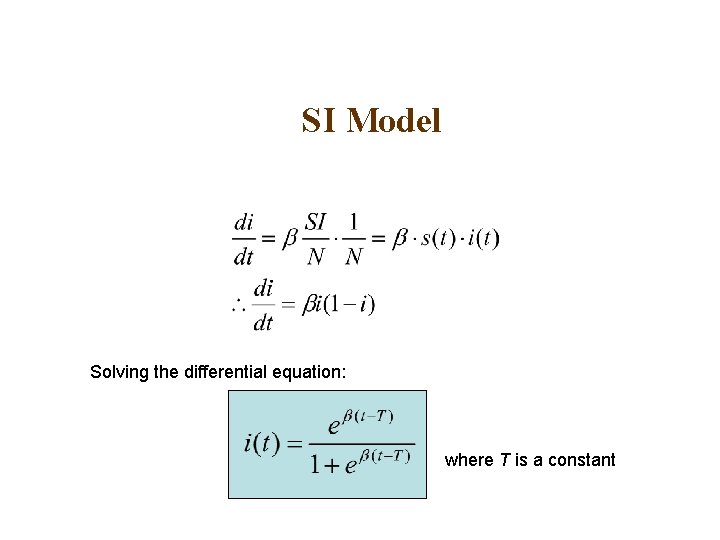
SI Model Solving the differential equation: where T is a constant

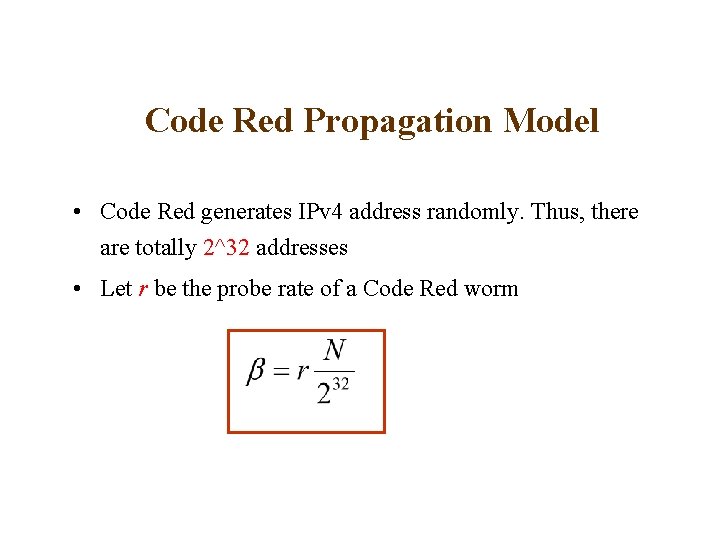
Code Red Propagation Model • Code Red generates IPv 4 address randomly. Thus, there are totally 2^32 addresses • Let r be the probe rate of a Code Red worm

Code Red Propagation Model q Two problems § Cannot model preferential targeting algorithm e. g. select targets form address ranges closer to the infected host § The rate only represents average contact rate e. g. a particular epidemic may grow significantly more quickly by making a few lucky targeting decisions in early phase.

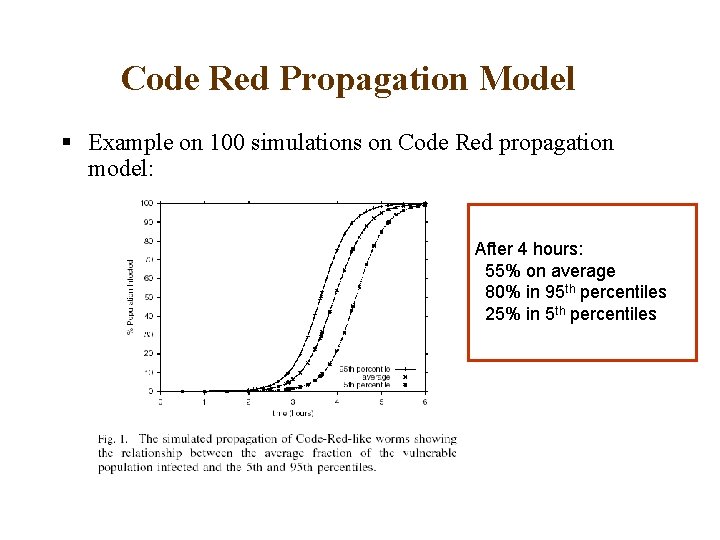
Code Red Propagation Model § Example on 100 simulations on Code Red propagation model: After 4 hours: 55% on average 80% in 95 th percentiles 25% in 5 th percentiles

Modeling Containment Systems A containment system has three important properties: § Reaction Time § Containment Strategy § Deployment Scenario

Reaction Time § Detection of malicious activity § Propagation of the containment information to all hosts participating the system § Activating any containment strategy

Containment Strategy I. Address blacklisting § Maintain a list of IP addresses that have been identified as being infected. § Drop all the packets from one of the addresses in the list. § E. g. Mail filter. § Advantage: can be implemented easily with existing firewall technology § Limitation: Needs to be updated continuously

Containment Strategy II Content filtering § Requires a database of content signatures known to represent particular worms § This approach requires additional technology to automatically create appropriate content signatures § Advantage: a single update is sufficient to describe any number of instances of a particular worm implementation § Works well with unintended Do. S attack

Deployment scenarios § Ideally, a global deployment is preferable. § Practically, a global deployment is impossible. § Can be deployed § At the edge of the corporate networks like firewalls § By ISPs at the access points and exchange points in the network

Idealized Deployment Simulation goal To find how short the reaction time is necessary to effectively contain the Code-Red style worm. Simulation Parameters § 360, 000 vulnerable hosts out of 232 hosts. § Probe rate of a worm : 10 per sec Containment strategy implementation – Address blacklisting Send IP addresses of infected hosts to all participating hosts. – Content filtering Send signature of the worm to all participating hosts.

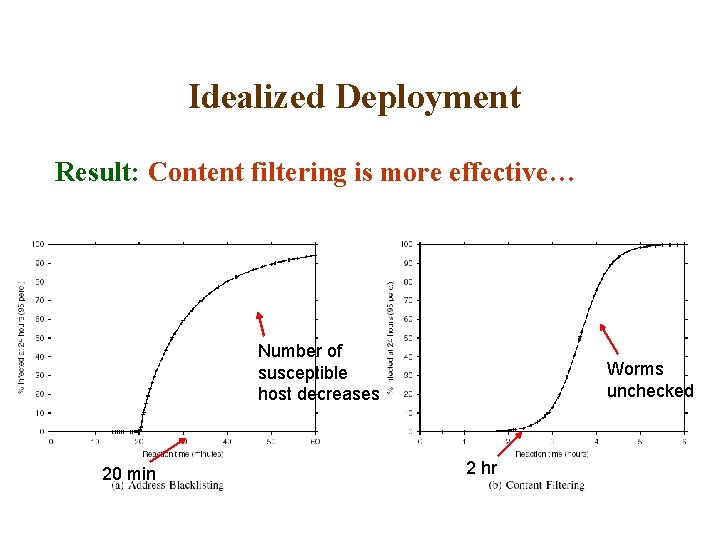
Idealized Deployment Result: Content filtering is more effective… Number of susceptible host decreases 20 min Worms unchecked 2 hr

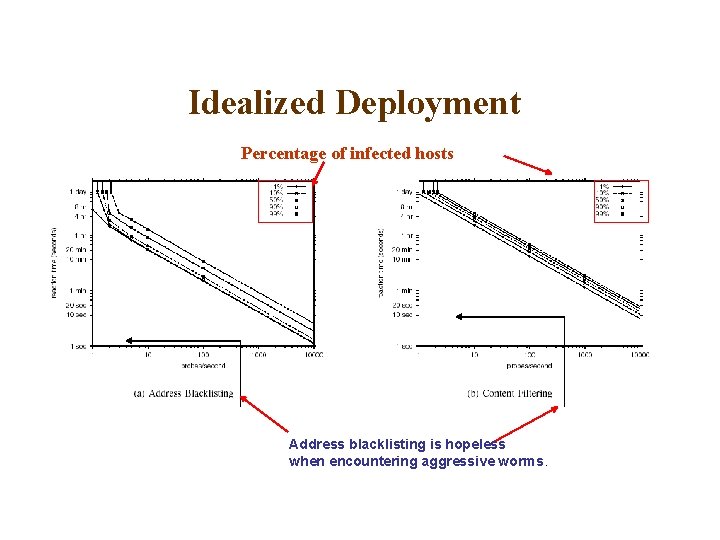
Idealized Deployment Next goal § To find the relationship between containment effectiveness and worm aggressiveness. § Figures are in log-log scale.

Idealized Deployment Percentage of infected hosts Address blacklisting is hopeless when encountering aggressive worms.

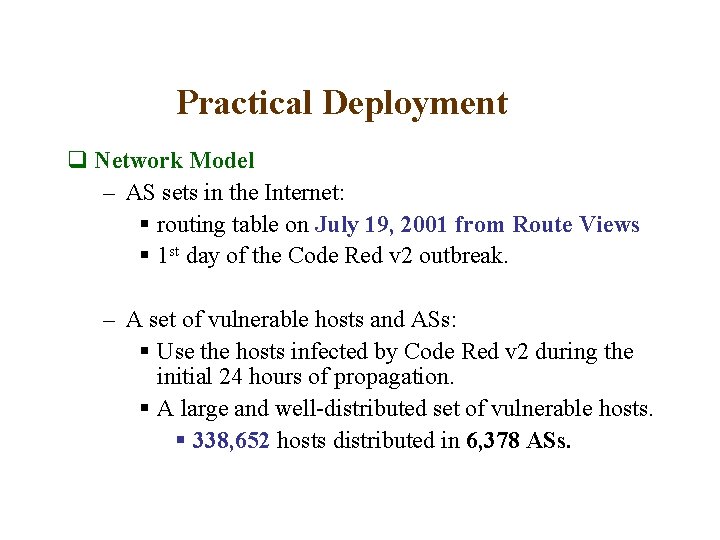
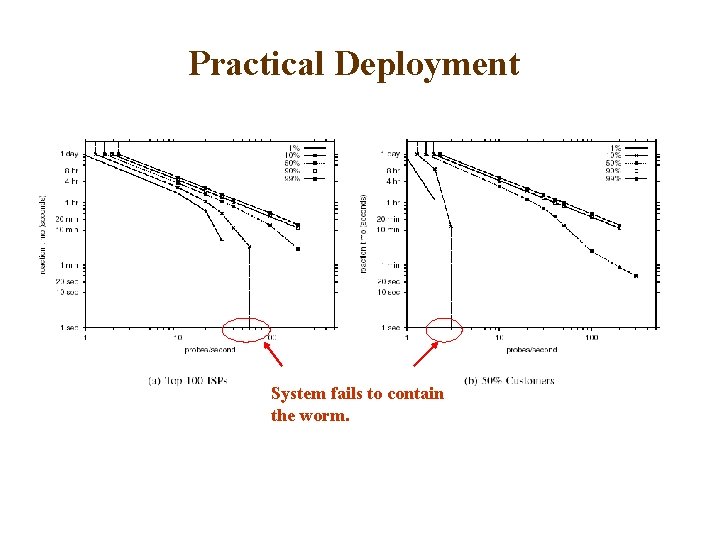
Practical Deployment q Network Model – AS sets in the Internet: § routing table on July 19, 2001 from Route Views § 1 st day of the Code Red v 2 outbreak. – A set of vulnerable hosts and ASs: § Use the hosts infected by Code Red v 2 during the initial 24 hours of propagation. § A large and well-distributed set of vulnerable hosts. § 338, 652 hosts distributed in 6, 378 ASs.

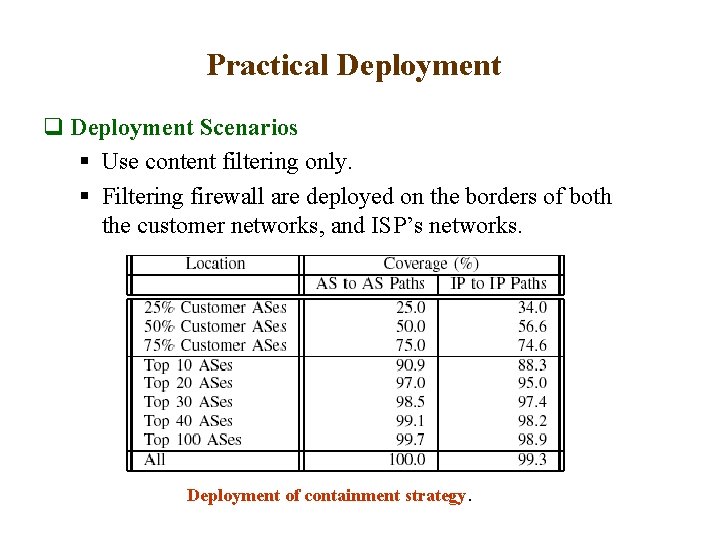
Practical Deployment q Deployment Scenarios § Use content filtering only. § Filtering firewall are deployed on the borders of both the customer networks, and ISP’s networks. Deployment of containment strategy.

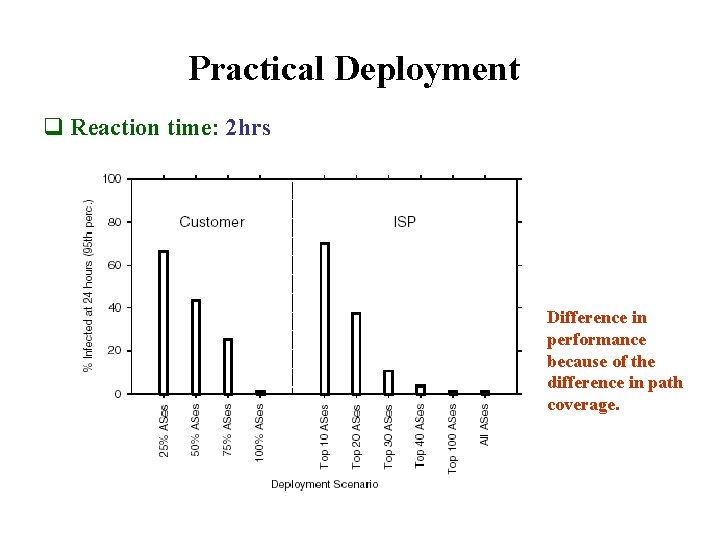
Practical Deployment q Reaction time: 2 hrs Difference in performance because of the difference in path coverage.

Practical Deployment System fails to contain the worm.

Conclusion ü Explored the properties of the containment system § Reaction time § Containment strategy § Deployment scenario ü In order to contain the worm effectively § Require automated and fast methods to detect and react to worm epidemics. § Content filtering is the most preferable strategy. § Have to cover all the Internet paths when deploying the containment systems

Strengths • Simple, very well written • Reasonable assumptions and real world data for simulation • Quantified the quarantine properties of worm epidemics • Gives head-start for developers and security people by quantifying reaction time at hand for various scenarios • Recommendations to ISPs and ASs, more cooperation and coordination among ISPs needed

Weak Links • Simulator details and source code not public • SI epidemic model doesn’t capture all the dynamics • Pessimistic picture ahead

Questions, Concerns, Issues ? ? ?