INTERMEDIATE CRIME SCENE SEARCH TCOLE Course 2106 32













































































- Slides: 94

INTERMEDIATE CRIME SCENE SEARCH TCOLE Course # 2106 32 to 40 hours AND BCCO PCT #4 Power. Point UNIT TEN

Learning Objectives Learning Objective 10. 1 The student will be able to summarize a process of identifying, documenting, securing, and processing potential computer and other electronic evidence. Learning Objective 10. 1. 1 The student will be able to list a basic guideline for identifying potential computer and/or other electronic evidence. Learning Objective 10. 1. 2 The student will be Objective able to identify a basic guideline for conducting preliminary interviews.

Learning Objective 10. 1. 3 The student will be able to explain the importance of maintaining a “chain of custody” when securing and processing all electronic date and evidence. Learning Objective 10. 1. 4 The student will be able to identify the methods for documenting computer and other electronic evidence. Learning Objective 10. 1. 5 The student will be able to identify the methods for securing and processing computer and other electronic evidence. Learning Objective 10. 1. 6 The student will be able to explain important considerations for securing and processing computers located in a complex environment.

Learning Objective 10. 1. 7 The student will be able to explain important considerations for securing and processing general electronic devices and peripheral evidence. Learning Objective 10. 1. 8 The student will be able to identify some common mistakes when handling electronic evidence. Learning Objective 10. 1. 9 The student will be able to demonstrate how to identify, document, secure, and process potential computer and other electronic evidence

10. 0 Computer and Other Electronic Evidence EVIDENCE TER PU COM N ATIO STIG INVE

10. 1 Computer & Other Electronic Evidence Process of identifying, documenting, securing, and processing potential computer and other electronic evidence. COMPUTER INVESTIGATION

10. 1. 1 Basic Guidelines for Identifying Computer & Other Electronic Evidence A. Search, locate, and clearly identify potential ____. B. The first responder should visually identify the potential ____, both conventional (physical) and electronic. Determine if perishable evidence (data that can be lost or deleted) exists.

D. Evaluate the scene and formulate a ______. If necessary, contact an a person who specializes in information technology, specifically computer forensics. 1. Specialized _____ is required to avoid damaging evidence while performing even such simple tasks as starting up the electronic device or opening a file or directory to inspect the contents.

D. 2. Different _____ and _____ are required for different operating systems and different software computer products. For instance, some e-mail systems save messages in a simple textual format that can be readily searched using keyword searches. Other e-mail products save messages in a compressed format to save disk space

D. 3. The investigator must know when to use normal _____, when to use the e-mail system itself, or when to use specialized utilities to examine message contents. F. Follow Agency policy, procedure, protocol and Texas State Laws.

10. 1. 2 Conducting Preliminary Interviews (Guidelines) A. Separate and identify all persons (witnesses, subjects, or others) at the scene and record their location at the COMPUTER time of entry. INVESTIGATION

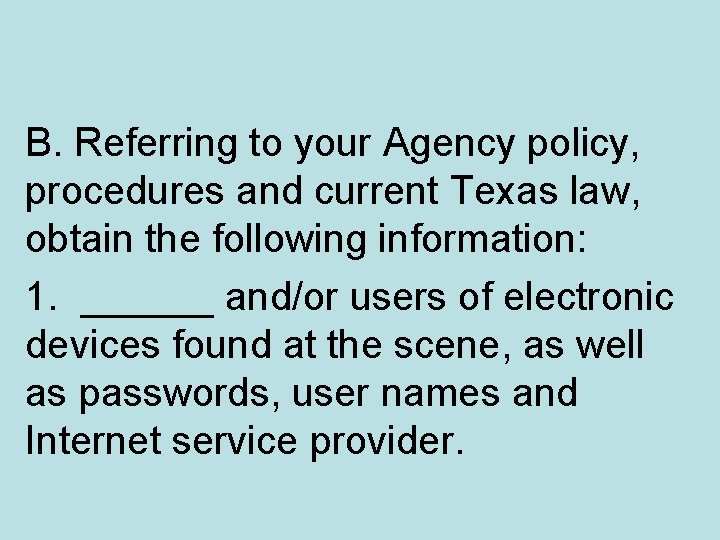
B. Referring to your Agency policy, procedures and current Texas law, obtain the following information: 1. ______ and/or users of electronic devices found at the scene, as well as passwords, user names and Internet service provider.

B. 2. Any ________ required accessing the system, software, or data. (Example: multiple passwords, multiple e. g. , BIOS, system login, network or ISP, application files, encryption pass phrase, e-mail, access, token, scheduler, or contact list. )

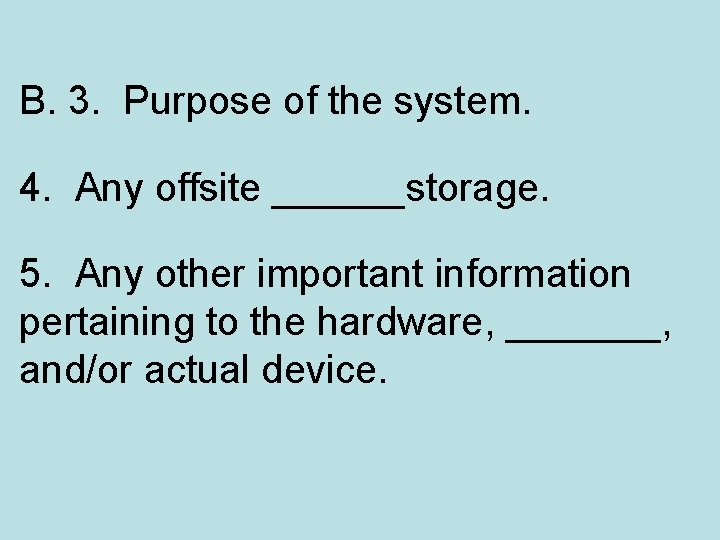
B. 3. Purpose of the system. 4. Any offsite ______storage. 5. Any other important information pertaining to the hardware, _______, and/or actual device.

10. 1. 3 “CHAIN of CUSTODY” Securing & Processing Electronic Evidence COMPUTER INVESTIGATION A. The key point is to keep a _____ of individuals who had control of the evidence at any point, from collection to final disposition.

B. It is in the best interest of the investigator and the agency to treat all investigations with the mindset that every action taken during the search may one day be under the _______ of individuals who desire to discredit techniques used, the officer’s testimony, and basic fact finding skills used

C. Start maintaining a _______ of potential evidence early in the response process. D. Create _____ for each hard drive or media identified and seized: 1. _____ and _____ of the action. 2. ________ assigned. 3. Number of particular evidence _____ (i. e. in sequential order).

D. 4. Whether or not ____ is required and the signature of the person who owns the information being seized. 5. The _______ of the evidence before it was seized, or who provided the information. 6. A complete _____ of the evidence, including the quantity, if necessary.

7. ______ of individual, crime laboratory, and/or storage facility who received the evidence from the investigator, and the signature of the recipient. 8. Date of ____. 9. _____ the evidence was given to another person.

E. Each time the evidence exchanges ______ from one person to another, or moves from one _____ to another, the investigator must record this transaction. For instance, if the officer moves the initial forensic duplication from a hard drive to many CD-ROMS, the officer must _______ this transfer.

F. It is also important to ____________ about the items that ______ are being seized. For instance, if the investigator decides to make forensic duplications of several mail servers located in a single office, document the following information: 1. _____ who occupy the office.

F. 2. Names of _____ that may have access to the office. 3. Location of the _____ systems in the room. 4. State of ____ (whether it is powered on, and what is visible on the screen. ) 5. Network connects or ______ connections.

F. 6. Individuals present at the time, the ____ duplication was performed. 7. ____ numbers, models, and makes of the hard drives and the components of the system. 8. _____ attached to the system.

G. It is critical to ______ all pertinent information possible and maintain the chain of custody. H. A well _____ evidence tag only takes a few minutes to create. I. Follow Agency policy, procedure and protocol.

10. 1. 4 Documenting Computer & Other Electronic EVIDENCE COMPUTER EVIDENCE A. The scene should be documented in ______. B. Initial documentation of the physical scene: 1. _______ and ____ the physical scene, such as the position of the mouse and the location of

B. 1. (Cont’d): components relative to each other (e. g. , a _______ on the left side of the computer may indicate a left-handed user). 2. Document the condition and location of the _______ or other electronic device , including its power status (on, off, or in sleep mode

B. 3. Most electronic devices have status _____ that indicate that it is on. 4. If _______ is heard on a computer, the system is probably on. 5. If the device (especially a computer system) is ____, this may also indicate that it is on or was recently turned off.

B. 6. Identify/document related electronic _____ that will not be collected. 7. Photograph the entire scene to create a ______as noted by the first responder. The complete room should be recorded with ____ degrees of coverage, when possible.

B. 8. Photograph the _____ of the computer as well as the _______ and other components. This applies to other electronic devices that are seized. 9. Take _______ on what appears on the monitor screen, or screen of any other electronic device

B. 10. Active programs may require ________ or more extensive documentation of monitor screen activity. 11. Additional documentation of the system will be required during the ______.

CAUTION Note: Movement of a computer system while the system is running may cause changes to system data. Therefore, data the system should not be moved until it has been safely __ ____. This is detailed in Chapter 5 of the Electronic Crime Scene Investigation. (July 2001). U. S. Dept. of Justice, Office of Justice Programs.

10. 1. 5 Securing & Processing Computers & Other Electronic EVIDENCE SECURING COMPUTER EVIDENCE A. Evaluating the scene 1. Follow Agency policy and protocol for securing the crime scene. a. This would include ensuring that all _______ are ____ from the immediate crime scene area from which evidence is to be collected.

A. Evaluating the scene 1. b. At this point in the investigation do not alter the condition of any ______: c. Protect ____ data physically and electronically.

A. Evaluating the scene 1. d. Perishable data may be found on pagers, ______ ID ______, electronic organizers (PDAs), cell phones, and other similar devices, as well as other electronic devices, see Objective 7. 7. 6.

A. Evaluating the scene 1. e. The first responder should always keep in mind that any device containing ____ should be immediately secured, documented, and/or photographed.

A. Evaluating the scene 2. Identify _____ attached to electronic devices, such as caller ID boxes. a. ____, disconnect, and label each telephone line from the wall rather than the device, when possible.

A. Evaluating the scene 2. b. There may also be other communication lines present for ____/______ connections. c. Consult appropriate personnel or agency in these cases. For us call Deputy Constable John Terry

A. Evaluating the scene 3. Latent fingerprints a. Keyboards, computer mouse, diskettes, CDs, or other components may have ____________ or other ____ evidence that should be preserved. b. _____ used in processing latent prints can damage equipment and data

A. Evaluating the scene 3. c. Therefore, ______ should be collected after electronic evidence recovery is complete. B. Collecting electronic evidence 1. Should be collected according to Agency _______, procedure and protocol

B. Collecting electronic evidence 2. In the absence of departmental guidelines outlining procedures for collecting electronic evidence, the following methods are suggested. a. Prior to the collection of evidence, it is assumed that ____ and ______ has been done as described above

B. Collecting electronic evidence 2. b. Recognize that other types of evidence such as ____, or latent prints may exist. c. Destructive techniques (e. g. , use of ______ processing _____) should be postponed until after electronic evidence recovery is done.

B. Collecting electronic evidence 3. Making ______-___ _______ of information stored in computers reduces the possibility that evidence will be altered of destroyed.

C. Evidence 1. ______ of non-electronic evidence can be crucial in the investigation of electronic crime. 2. Proper care should be taken to ensure that such ______ is recovered and preserved.

C. Non-electronic evidence 3. Items relevant to subsequent examination of electronic evidence may exist in other forms (e. g. , written _____ and other handwritten notes, notes blank pads of paper with indented writing, hardware and software manuals, calendars, literature, text or graphical computer printouts and photographs) and should be secured and preserved for future analysis

C. Non-electronic evidence 4. These items frequently are in close proximity to the _____ or related hardware items. 5. All _______ should be identified, secured, and preserved in compliance with Agency policies, procedures & protocols.

D. Stand-alone and laptop computer evidence. CAUTION: Multiple computers may indicate a _____. Likewise, computers located at businesses are often networked. In these situations, specialized knowledge about the system is required to effectively recover evidence and reduce your potential

D. Stand-alone and laptop computer evidence. CAUTION: for civil liability. When a computer network is encountered, contact the __________ expert in your Agency or outside consultant identified by your Agency for assistance.

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 1. A “stand-alone” ______________ is a computer not connected to a _____ or other computer. Stand-alones may consist of desktop machines or laptops.

D. Stand-alone and laptop computer evidence. CAUTION 2. ____ incorporate a computer, monitor, keyboard, and mouse into a single portable unit. Laptops differ portable from other computers in that they can be powered by electricity or a battery source. Therefore, they require the removal of the battery in addition to stand-alone power- down procedures. (Cont’d):

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 3. If the computer is on, document existing _____ and call your expert or consultant.

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 4. If an ______ or _____ is not available, and after securing the scene, review all steps below before taking any action (otherwise, evidentiary data may be altered

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 4. a. Record in notes all _______ you take and any changes that changes you ______ in the monitor, computer, printer, or other peripherals that result from your actions.

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 4. b. _______ the ____ and determine if it is on, off, or in sleep mode (blank screen). Then decide which of the following situations applies and follow the steps for that situation.

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 4. b. Situation 1: Monitor is on and work product and/or desktop are visible. Photograph _______ and _____ information displayed. Perform steps under Objective 7. 7. 3.

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 4. b. Situation 2: Monitor is on and screen is blank (sleep mode) or screen saver (picture) is visible. Move the ______ slightly (without pushing buttons). The screen should change and show work ______ or request a password. If

D. Stand-alone and laptop computer evidence. CAUTION – Cont’d): 4. b. Situation 2: the mouse movement does not cause a change in the screen, DO NOT perform any other _______ or ______ operations. Photograph the screen and record the information displayed. Perform steps under Objective 7. 7. 3.

D. Stand-alone and laptop computer evidence. CAUTION – CAUTION Cont’d): 4. b. Situation 3: Monitor is off. Make a note of “off” status. Turn the _______ __, then determine if the monitor status is as described in either situation 1 or 2 above and follow those steps.

D. Stand-alone and laptop computer evidence. 5. Regardless of the power state of the computer (on, off, or sleep mode), remove the ______ cable from the computer – NOT from the wall outlet. If dealing with a laptop, in addition to removing the power cord, remove the battery pack. The battery is removed to prevent any power

D. Stand-alone and laptop computer evidence. 5. Cont’d: the system. Some laptops Cont’d: have a second ______ in the multipurpose bay instead of a floppy drive or CD drive. Check for this possibility and remove that battery as well.

D. Stand-alone and laptop computer evidence. 6. Check for ____________ (e. g. , telephone modem, cable, ISDN, DSL). If a telephone connection is present, attempt to identify the telephone number.

D. Stand-alone and laptop computer evidence. 7. To avoid damage to potential evidence, remove any ______ that are present, package the disk separately, and label the package. If available, insert either a seizure disk or a blank floppy disk. Do NOT remove CDs or touch the CD drive.

D. Stand-alone and laptop computer evidence. 8. Place ____ over all the drive slots and over the power connector. 9. Record make, _____, and _______. 10. Photograph and _____ the connections of the computer and the corresponding cables.

D. Stand-alone and laptop computer evidence. 11. Label all ______ and cable _____ (including connections to peripheral devices) to allow for exact reassembly at a later time. Label unused connection ports as “unused. ” 12. Identify laptop computer ________ in an effort to identify other storage media.

D. Stand-alone and laptop computer evidence. 13. Record or log the ______ according to Agency policy & procedures. 14. If transport is required, package the ______ as fragile cargo.

10. 1. 6 Considerations for Securing & Processing Computers (In a Complex Environment)

A. Business environments frequently have multiple computers connected to each other, to a central server, or both.

B. Securing and processing a crime scene where the computer systems are networked poses special problems, as improper ____ may destroy data. This can result in a loss of ____ and potential _____ civil liability

C. When investigating criminal activity in a known business environment, the presence of a computer ______ should be planned for in advance, if possible, and appropriate expert assistance obtained. D. It should be noted that computer ______ can also be found in a home environment and the same concerns exist.

E. The possibility of various operating _____ and complex _____ configurations requiring different shutdown procedures make the processing of a network crime scene beyond the scope of this guide. However, it is important that computer networks be recognized and identified, so that expert assistance can be obtained if one is encountered

F. Provide a list of technical resources that can be contacted for assistance. Indications that a computer network may be present include: 1. The presence of ______ computer systems.

F. 2. The presence of ____ and _____, such as those depicted in the pictures at left, running between computers or central devices such as hubs. 3. Information provided by _____ or individuals at the scene. 4. The presence of ______ components.

10. 1. 7 Securing & Processing General Electronic Devices & Peripheral EVIDENCE A. The electronic devices such as the ones in the list below may contain potential _____ associated with ______ activity. B. Unless an ______ exists, the device should not be operated.

C. Should it be necessary to access information from the device, all actions associated with the ________ of the _____ should be documented to preserve the authenticity of the information. authenticity D. Many of the items listed below may contain _______ that could be lost if not handled properly.

E. For more detailed information on these devices, read “Best Practices for Seizing Electronic Evidence”, Evidence” Appendix C. 1. Examples of other electronic devices or computer _______ include: a. _____ recorders b. _____ and ______ cassette tapes

E. 1. – Cont’d: c. ______ memory cards d. ______ machines e. ____ diskettes, & CD-ROMs f. _____ g. _____ devices h. _______ devices i. ____

E. 1. – Cont’d: j. _____ telephones k. ______/electronic organizers l. _______ (high quantities may indicate chip theft) m. ____ cards n. ____ (if active allow to complete printing)

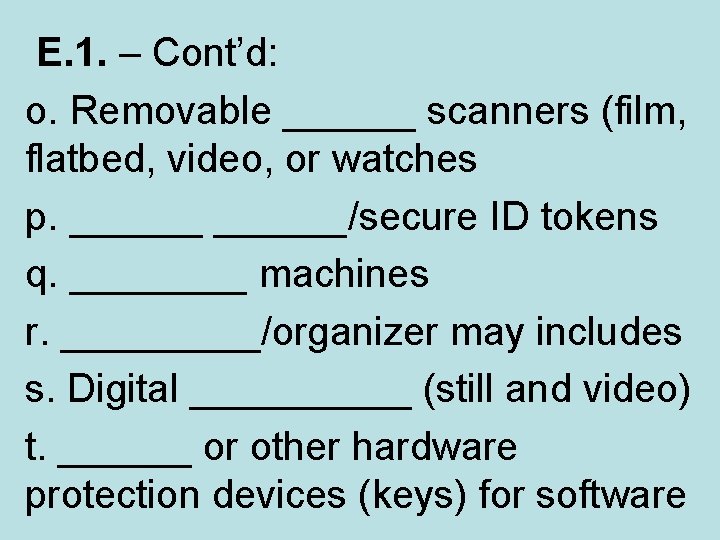
E. 1. – Cont’d: o. Removable ______ scanners (film, flatbed, video, or watches p. ______/secure ID tokens q. ____ machines r. _____/organizer may includes s. Digital _____ (still and video) t. ______ or other hardware protection devices (keys) for software

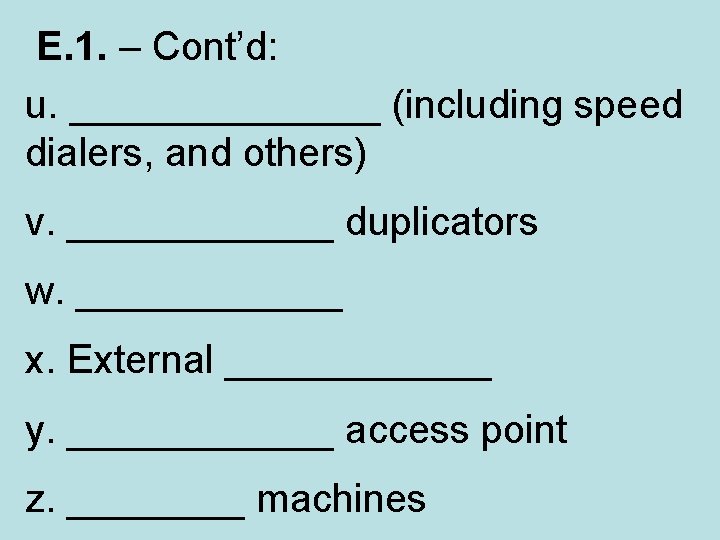
E. 1. – Cont’d: u. _______ (including speed dialers, and others) v. ______ duplicators w. ______ x. External ______ y. ______ access point z. ____ machines

Note: When seizing removable media, ensure that you take the associated device that created the media (e. g. , tape drive, cartridge drives such as Zip, Jaz, ORB, Clik!, Syquest, LS-120, and DAT Drives (High Capacity Data Storage Media)).

10. 1. 8 Common Mistakes Handling Electronic EVIDENCE COMPUTER INVESTIGATION A. Failure to maintain proper identification 1. Every action needs to be action clearly documented.

B. Failure to notify or provide accurate information to decision makers 1. _____ and _____ any security breaches to appropriate officials.

C. Failure to control access to digital evidence. 1. Not all personnel should be able to _______ or _____ with the evidence. 2. The evidence should be carefully ______. 3. The evidence should be maintained by a type of ____ system.

D. Failure to report the incident in a timely fashion to appropriate officials 1. The longer the investigator waits to perform a ____________ a system, the more the evidence will changing. In other words, the colder the evidence trail will become.

E. Underestimate the scope of the incident 1. Investigator (s) should understand the onset of an inquiry or investigation, one never knows what may be ______ later.

F. Failure to have a response plan in place. 1. ____ incidents are often incidents complex investigation requiring specialized skills and knowledge. 2. Execution, or lack of _____ staff, prior to planning staff can jeopardize the evidence and investigation entirely.

G. Specific technical mishaps: mishaps 1. Altering ____ and ____ stamps on evidence systems before recording them. 2. Killing (terminating) ____ processes. 3. _____ the system before investigator respond. 4. Not recording _______ executed on the system.

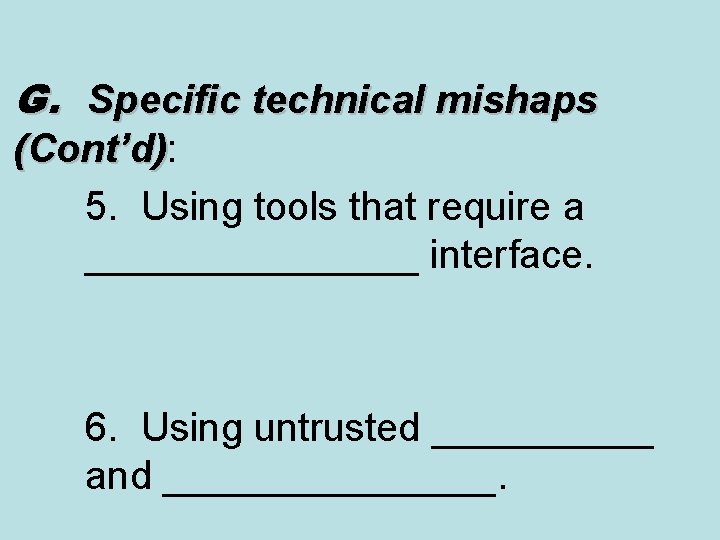
G. Specific technical mishaps (Cont’d): (Cont’d) 5. Using tools that require a ________ interface. 6. Using untrusted _____ and ________.

G. Specific technical mishaps (Cont’d): (Cont’d) 7. ______ over potential evidence by installing software on the evidence media (the original hard drive that needs to be investigated. ) 8. Writing over potential evidence by running _____ that store their output on the evidence media.

10. 1. 9 Practical Exercise A. Participant will demonstrate and explain to class how to: 1. Identify computer evidence, 2. Document computer evidence, 3. Secure, and process potential computer and other electronic evidence

Questions?

SOURCES • DOJ Research Report, Death Investigation: A Guide for the Scene Investigator, November 1999. • DOJ Research Report, Eyewitness Evidence: A Guide for Law Enforcement, October 1999.

COURSE & INSTRUCTOR EVALUATION Form • Please complete a course and instructor evaluation form. • If you rate 2 or below you must justify on reverse side. • Constructive Criticism helps all, being negative helps no one.

• Exam • Graduation Knowledge is “POWER” and Works only when “USED:

THANK YOU STAY SAFE & STAY VILIGANT This Power. Point and all associated lesson materials herein are the property of BCCO PCT#4
 Intermediate crime scene investigation tcole
Intermediate crime scene investigation tcole Intermediate crime scene tcole
Intermediate crime scene tcole 2106 crime scene investigation
2106 crime scene investigation Crime scene
Crime scene Tcole 2106
Tcole 2106 Cit tcole training
Cit tcole training Grid search police
Grid search police Linear search pattern crime scene
Linear search pattern crime scene Crime scene search patterns examples
Crime scene search patterns examples Basic instructor course #1014
Basic instructor course #1014 Basic instructor course texas
Basic instructor course texas Basic instructor course #1014
Basic instructor course #1014 Tcole 3737
Tcole 3737 Tcole 1014 basic instructor course
Tcole 1014 basic instructor course Tcole 3737
Tcole 3737 Tcole advanced instructor course
Tcole advanced instructor course Tcole advanced instructor course
Tcole advanced instructor course Basic instructor course tcole
Basic instructor course tcole Developmental criminology
Developmental criminology Life course theory crime
Life course theory crime West memphis 3 autopsy photos
West memphis 3 autopsy photos What are the seven s's of crime scene investigation
What are the seven s's of crime scene investigation Types of crime scene
Types of crime scene Dena schlosser case
Dena schlosser case Finished sketch
Finished sketch Baseline method crime scene sketch
Baseline method crime scene sketch What must be included on a crime scene sketch?
What must be included on a crime scene sketch? Graphsketch
Graphsketch Sketching the crime scene
Sketching the crime scene Crime scene basics crossword answer key
Crime scene basics crossword answer key Crime scene factoring and quadratic functions answer key
Crime scene factoring and quadratic functions answer key Crime scene vocabulary
Crime scene vocabulary Forensic science begins
Forensic science begins Triangulation method crime scene sketch
Triangulation method crime scene sketch Crime scene photography management
Crime scene photography management While the csi team is searching the crime scene, _____.
While the csi team is searching the crime scene, _____. Crime scene vocabulary
Crime scene vocabulary Cretaceous crime scene
Cretaceous crime scene Drawing of crime
Drawing of crime Vocabulary crime scene
Vocabulary crime scene A crime scene sketch should include
A crime scene sketch should include Crime scene storyboard
Crime scene storyboard Picktona
Picktona Deductive reasoning crime scene investigation
Deductive reasoning crime scene investigation Crime scene reconstruction definition
Crime scene reconstruction definition _____ is done with the first responding officer.
_____ is done with the first responding officer. Crime scene investigation background
Crime scene investigation background Crime clip
Crime clip Crime scene inference
Crime scene inference David carpenter serial killer
David carpenter serial killer Crime scene
Crime scene Crime scene notes
Crime scene notes Crime scene reconstruction involves forming a hypothesis
Crime scene reconstruction involves forming a hypothesis Small amounts of trace evidence can be conveniently
Small amounts of trace evidence can be conveniently Crime scene photography log
Crime scene photography log Druggist fold steps
Druggist fold steps Boston massacre csi
Boston massacre csi Seven s of crime scene
Seven s of crime scene Summarize locard's principle of exchange
Summarize locard's principle of exchange Subdatum point definition
Subdatum point definition Phil spector crime scene
Phil spector crime scene Crime scene
Crime scene Sketch of locality in crime scene
Sketch of locality in crime scene Cross-projection sketch
Cross-projection sketch Note taking crime scene investigation
Note taking crime scene investigation Can a crime scene sketch have probative value
Can a crime scene sketch have probative value A pair of latex gloves was found at a crime scene
A pair of latex gloves was found at a crime scene Dentist john yelenic
Dentist john yelenic Tcole 3939
Tcole 3939 Tcole 2105
Tcole 2105 Tcole 2105
Tcole 2105 Tcole 2108
Tcole 2108 Tcole 2107
Tcole 2107 Tcole 2105
Tcole 2105 Tcole 2105
Tcole 2105 Tcole 4068
Tcole 4068 Tcole 3737
Tcole 3737 Tcole 3275
Tcole 3275 Tcole 2105
Tcole 2105 One and a half brick wall
One and a half brick wall Course title and course number
Course title and course number Course interne moyenne externe
Course interne moyenne externe Summary macbeth act 1
Summary macbeth act 1 Act iv macbeth summary
Act iv macbeth summary Vtac preferences
Vtac preferences Difference between informed and uninformed search
Difference between informed and uninformed search Federated discovery
Federated discovery Local search vs global search
Local search vs global search Federated search vs distributed search
Federated search vs distributed search Informed and uninformed search
Informed and uninformed search Images search yahoo
Images search yahoo Best first search in ai
Best first search in ai Blind search adalah
Blind search adalah Video.search.yahoo.com search video
Video.search.yahoo.com search video Video.search.yahoo.com search video
Video.search.yahoo.com search video