Intercept X Early Access Program Sophos Tester Karl









- Slides: 16

Intercept X Early Access Program Sophos Tester Karl Ackerman Principal Product Manager – Endpoint Security Group July 2017

Agenda Overview FAQ Tests described Platform Results

Overview FAQ What is Sophos Tester? o Demonstration of attack techniques from exploits and ransomware to atom bombing Is this safe to use? o Sophos tester will not harm your PC - It performs the techniques for multiple attack methods but does not deliver malware, communicate with command control servers, or encrypt your documents - NOTE running the tool with Intercept X will create detection events and they will show in Sophos Central so if that console is monitored by another team, they may wonder what the heck you are doing. Can I run Sophos Tester on a machine with a competitors AV? o o The tool is not intended for competitive comparisons, and was built to confirm detection methods available in Intercept X Some AV Vendors block the tool as malicious, or unknown, others may block some of the techniques of the attack as well What platforms does the tool run on? o o Sophos tester was built for Windows 7 32 bit and should run on Windows XP, 7, 8, 10 for 32 and 64 bit systems Some issues with OS’s other than windows 7 32 bit are known with tests failing to run correctly

Overview FAQ (continued) Does the test tool have a test for ALL the mitigations in Intercept X o No this tool does not validate all exploit methods, just the most common ones Why don’t I see any tests for Disk-Wiping, Credential Theft of Process Protection? o o For these tests the test tool needs to be run as administrator Right click on the Sophos Tester. exe and select “Run as Administrator” When run with Intercept X, do detections generate events in the console? o Yes, when run with Intercept X, the admin console will show the detection events and an Root Cause Analysis may also be generated Will Sophos Clean remove the test tool on detection? o o No Sophos Clean will allow sophos tester to remain after detections Ransomware detections by Intercept will identify the target application and block similar attacks until a reboot or sufficient time has elapsed for Intercept to unblock the application. 4

Agenda Overview FAQ Tests described Platform Results

Attack Targets Target o We look for common infection vectors (Applications) used by malware on the machine and display these as target applications - Using a target application will launch the application to perform the attack tecnique o Dummy (Default) - This is the sophos tester executable itself and can be used to demonstrate attacks o Note some attacks on a protected system will identify the Sophos tester or target application and lock its use for a period of time - A good way to avoid having to reboot is to try each ransomware test with a different target application 6

Category Attack Techniques Code exploits Attacks that take advantage of vulnerabilities in the software being used Memory exploits Attacks that manipulate process and system memory to execute their code Logic Flaws Preventing malicious behaviors even when the application is ‘allowed’ to perform them Safe Browsing Detect man in the browser activity that present one view to the user and another to the site Ransomware Malicious rapid file encryption Often the application target is now blocked from similar activity, reboot to clear this state on Intercept protected devices See Settings for additional configurations Run Sophos Tester as Administrator Disk-wiping Attacks on the master boot record Credential Theft Attacks that steal authentication credentials Process Protection Newer exploits using Asynchronous Procedure Calls (Wanacry, eternal blue, double pulsar) 7

Agenda Overview FAQ Tests described Platform Results

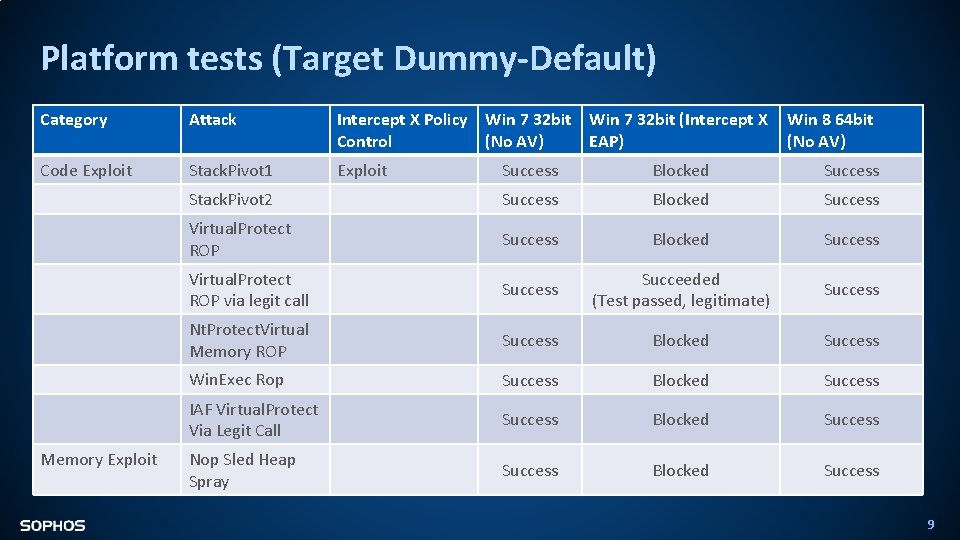
Platform tests (Target Dummy-Default) Category Attack Intercept X Policy Win 7 32 bit (Intercept X Control (No AV) EAP) Code Exploit Stack. Pivot 1 Exploit Memory Exploit Win 8 64 bit (No AV) Success Blocked Success Stack. Pivot 2 Success Blocked Success Virtual. Protect ROP via legit call Success Succeeded (Test passed, legitimate) Success Nt. Protect. Virtual Memory ROP Success Blocked Success Win. Exec Rop Success Blocked Success IAF Virtual. Protect Via Legit Call Success Blocked Success Nop Sled Heap Spray Success Blocked Success 9

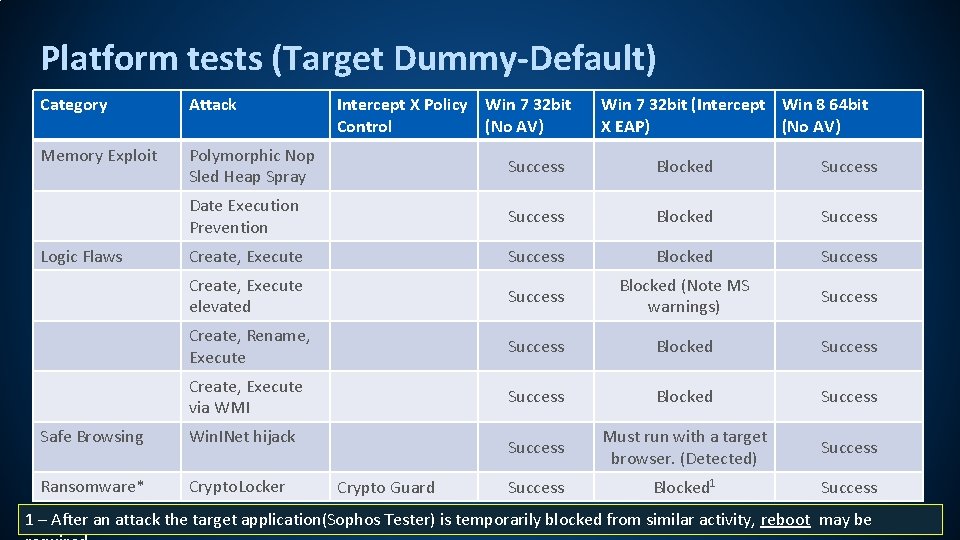
Platform tests (Target Dummy-Default) Category Attack Memory Exploit Polymorphic Nop Sled Heap Spray Success Blocked Success Date Execution Prevention Success Blocked Success Create, Execute elevated Success Blocked (Note MS warnings) Success Create, Rename, Execute Success Blocked Success Create, Execute via WMI Success Blocked Success Must run with a target browser. (Detected) Success Blocked 1 Success Logic Flaws Safe Browsing Win. INet hijack Ransomware* Crypto. Locker Intercept X Policy Win 7 32 bit Control (No AV) Crypto Guard Win 7 32 bit (Intercept Win 8 64 bit X EAP) (No AV) 1 – After an attack the target application(Sophos Tester) is temporarily blocked from similar activity, reboot may be 10

Platform tests (Target Dummy-Default) Category Attack Intercept X Policy Win 7 32 bit Control (No AV) Ransomware* CTB-Locker Crypto Guard Success Blocked 1 Success Torrent. Locker Crypto Guard Success Blocked 1 Success Crypto. Wall 3 Crypto Guard Success Blocked 1 Success Locky Crypto Guard Success Blocked 1 Success Hydra. Crypto Guard Success Blocked 1 Success Cerber 3 Crypto Guard Success Blocked 1 Success Dharma Alternative Crypto Guard Success Blocked 1 Success Crypto. Shield Crypto Guard Success Blocked 1 Success Master Boot Record Disk and Boot Protection Success Blocked Success Disk-wiping Win 7 32 bit (Intercept Win 8 64 bit X EAP) (No AV) 1 – After an attack the target application(Sophos Tester) is temporarily blocked from similar activity, reboot may be required 11

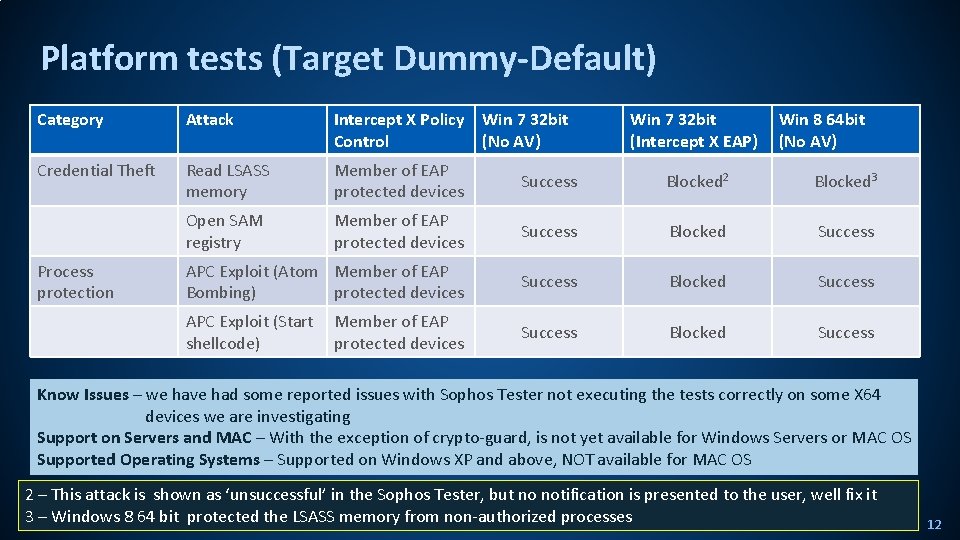
Platform tests (Target Dummy-Default) Category Attack Intercept X Policy Win 7 32 bit Control (No AV) Credential Theft Read LSASS memory Member of EAP protected devices Success Blocked 2 Blocked 3 Open SAM registry Member of EAP protected devices Success Blocked Success APC Exploit (Atom Member of EAP Bombing) protected devices Success Blocked Success APC Exploit (Start shellcode) Success Blocked Success Process protection Member of EAP protected devices Win 7 32 bit (Intercept X EAP) Win 8 64 bit (No AV) Know Issues – we have had some reported issues with Sophos Tester not executing the tests correctly on some X 64 devices we are investigating Support on Servers and MAC – With the exception of crypto-guard, is not yet available for Windows Servers or MAC OS Supported Operating Systems – Supported on Windows XP and above, NOT available for MAC OS 2 – This attack is shown as ‘unsuccessful’ in the Sophos Tester, but no notification is presented to the user, well fix it 3 – Windows 8 64 bit protected the LSASS memory from non-authorized processes 12

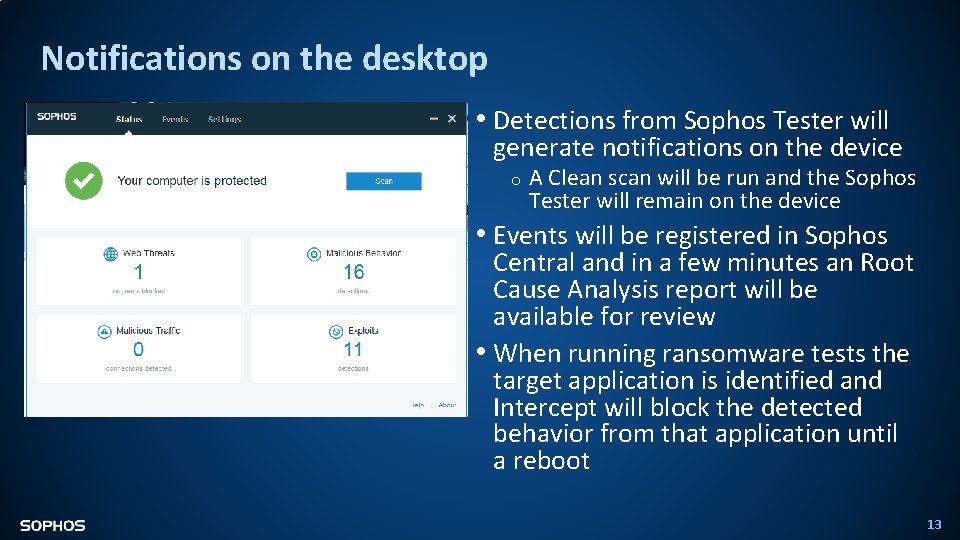
Notifications on the desktop • Detections from Sophos Tester will generate notifications on the device o A Clean scan will be run and the Sophos Tester will remain on the device • Events will be registered in Sophos Central and in a few minutes an Root Cause Analysis report will be available for review • When running ransomware tests the target application is identified and Intercept will block the detected behavior from that application until a reboot 13

Notifications in Sophos Central • Sophos test results in a notification to the end user and in Sophos Central 14

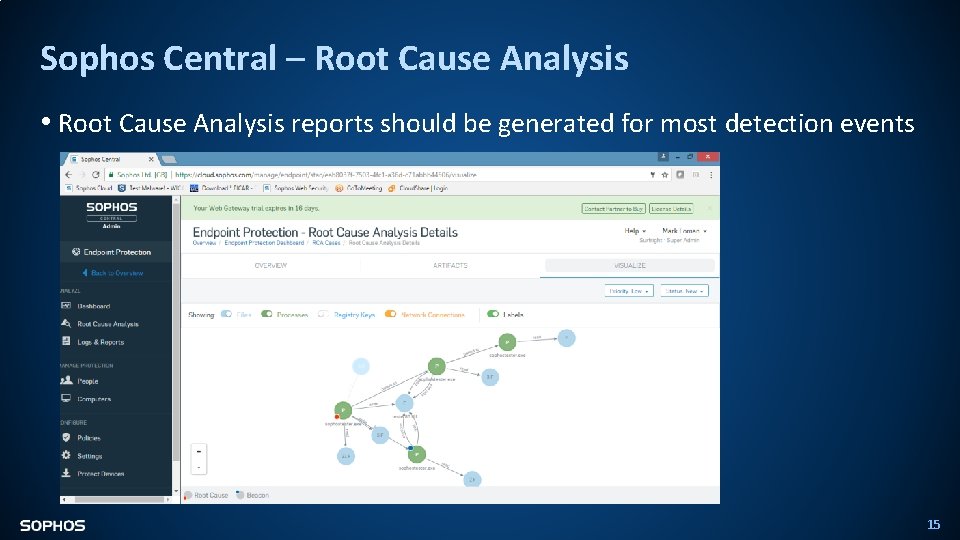
Sophos Central – Root Cause Analysis • Root Cause Analysis reports should be generated for most detection events 15
