Intelligence and Security in the Digital Age Sir














- Slides: 21

Intelligence and Security in the Digital Age Sir David Omand GCB Visiting Professor, Department of War Studies, King’s College London Cambridge, Computing Society, 1 Mar 2012

“The further back you look, the further ahead you can see” Winston Churchill o Offence/defence race o Technology drivers o Demand: modern national security? o Supply: new means o Cyber security o An additional factor: individual rights and social attitudes 2

Role of Intelligence o Intelligence enables action to be optimised by reducing ignorance; and secret intelligence achieves this objective in respect of information that others wish to remain hidden. o o Continuous offence/defence competition for… § Situational awareness § Explanation § Prediction and modelling Strategic notice of possible futures

4 revolutions in intelligence o The legacy of Maxwell, Herz and Marconi: The discovery and exploitation of the electromagnetic spectrum: radio, direction finding, traffic analysis, agent communications, radio deception o The legacy of Turing and Shockley: process engineering, The first quantum revolution: radar, programmable computers, transistors, minaturisation, into Space… o The legacy of Feynman and Moore: The second quantum revolution: electro-optics, lasers, micro-electronics, packet switching, mobile communications, o The legacy of Berners-Lee: the internet and web, “electronic exhaust”, Intelligence Agencies become ‘knowledge industries’, massive data storage

Balancing three sets of pressures Demand: new strategic requirements Supply: new technological possibilities

Balancing three sets of pressures Demand: new strategic requirements Supply: new technological possibilities Social attitudes and ethical issues

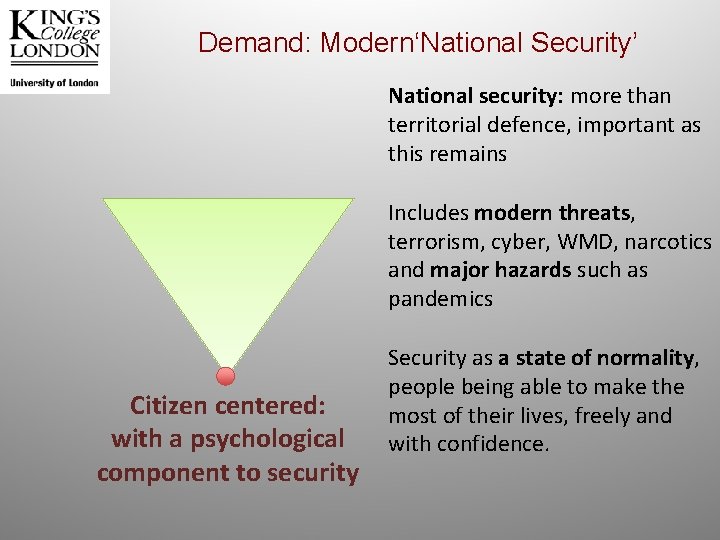
Demand: Modern‘National Security’ National security: more than territorial defence, important as this remains Includes modern threats, terrorism, cyber, WMD, narcotics and major hazards such as pandemics Citizen centered: with a psychological component to security Security as a state of normality, people being able to make the most of their lives, freely and with confidence.

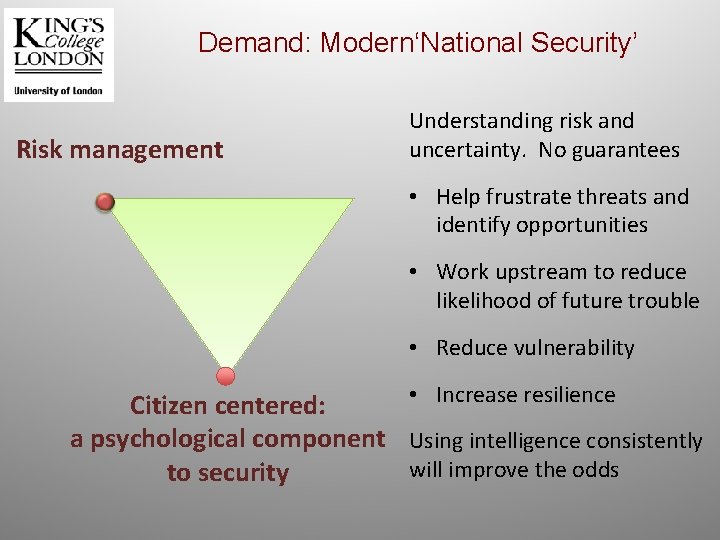
Demand: Modern‘National Security’ Risk management Understanding risk and uncertainty. No guarantees • Help frustrate threats and identify opportunities • Work upstream to reduce likelihood of future trouble • Reduce vulnerability • Increase resilience Citizen centered: a psychological component Using intelligence consistently will improve the odds to security

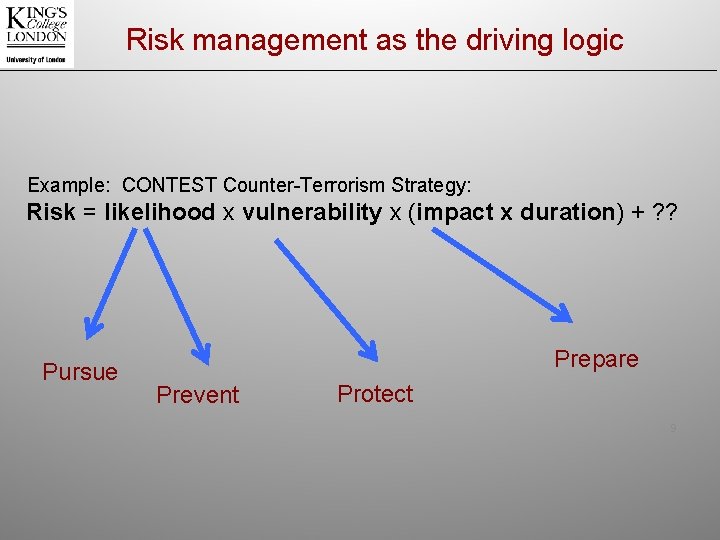
Risk management as the driving logic Example: CONTEST Counter-Terrorism Strategy: Risk = likelihood x vulnerability x (impact x duration) + ? ? Pursue Prepare Prevent Protect 9

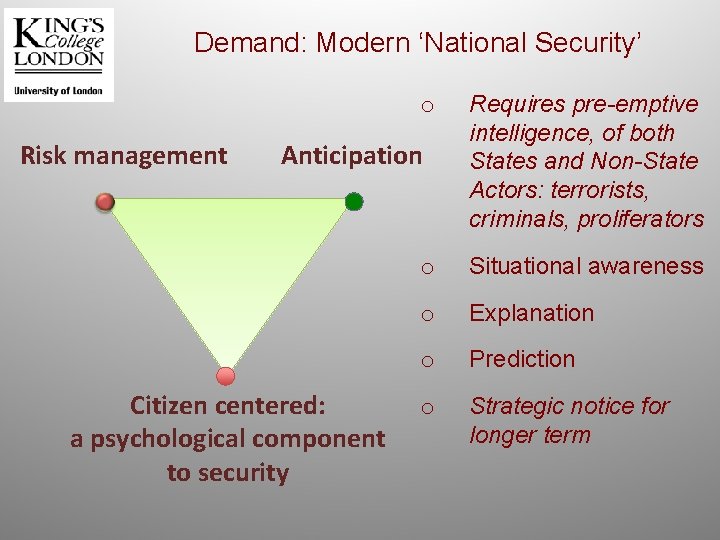
Demand: Modern ‘National Security’ o Risk management Anticipation Citizen centered: a psychological component to security Requires pre-emptive intelligence, of both States and Non-State Actors: terrorists, criminals, proliferators o Situational awareness o Explanation o Prediction o Strategic notice for longer term

Accessing relevant information o Sources: o Classic ‘ints’: HUMINT, SIGINT (including network exploitation), IMINT etc o Open source information, OSINT, including analysis of social networking o Developing a new ‘int’: PROTINT or data protected personal information 11

Examples of ‘PROTINT’ in the UK o E-Borders, Registrar General, social security, HMRC, electoral… o Advance passenger information o CCTV and ANPR (Automatic number plate readers) o Communications meta-data o Credit, debit and loyalty cards o Financial transactions including SWIFT o Social networking sites o Data matching and mining

New technical possibilities o Network and cyber attack o ‘Facilitated’ access using insiders o Fused multi-source operational intelligence using advanced visualisation techniques o Social networking and RSS feeds o DIGINT techniques – digitally manipulating data sets o Information retrieval – latent semantic search 13

UK cyber strategy depends upon intelligence o Ends: o Supporting economic prosperity, protecting national security and safeguarding the public o Ways: o Drivers are in the private not public sectors o Has to be international o Means: role of intelligence central: 80/20 rule

Operating in the Intelligence Space • The top 20% of Cold War threat – penetration agents (Cambridge ring; Enormoz; Portland ring) – technical attacks (bugs, implants, microwave resonating cavities) • Counter-measures – – 24/7 observation of KGB and GRU agents Agent comms interception (Venona decrypts) Double agents (Gordievsky - exposing Bettany) R&D into novel attack methods

Current developments in S&T o Cyber Network attack and defence o PROTINT and data mining o Stand-off range allied with precision (60, 00 ft to 1 m 2) o Remote surveillance streaming rates o Detectors at 1 or 2 parts/billion + rapid field results o Millimetric wave technology o Nano-engineering o Neuropharmacology and neuroscience o Quantum computing?

But also building public trust that we are not heading for the Panoptic State, or the tyranny of absolute knowledge

With the end of the Cold War came a change of intelligence paradigm for the UK “The Secret State” of the Cold War o Supporting nuclear deterrence and NATO, all kept secret from the public o Secret status of intelligence agencies o Domestic policing and external intelligence kept separate “The Protecting State” of modern national security o Intelligence Agencies are avowed and regulated o Use of intelligence for security of the public, who demand to know more about what is being done in their name o Cooperation in policing and intelligence

Public attitudes and ethical issues • The active use of secret intelligence for public protection: • puts secret world under unwelcome media spotlight • generates demands for accountability and oversight • increases importance of public (and staff) confidence • Issues arise for the security and intelligence community • over privacy and the use of technology and PROTINT • over the ethics of human intelligence work • in using intelligence as evidence in court • in justifying continuing secrecy over sources and methods

A ‘grand bargain between Government and the public The security and intelligence community accepts: o Terrorists get prosecuted under the law o Ethics matter; some opportunities have to be passed o Oversight by Parliament and judges The public has to accept: o Security of public is first responsibility of government o Managing the risks requires secret intelligence o Some loss of privacy has to be accepted to get it o Secret intelligence needs secrecy of sources/methods

Discussion 21