Intel v Pro and Microsoft System Center Configuration















































- Slides: 172

Intel® v. Pro™ and Microsoft® System Center Configuration Manager 2007 SP 2 Training 1

Welcome • This step-by-step training guide is intended to get you familiar with managing Intel® v. Pro™ systems with Microsoft* System Center Configuration Manager 2007 Service Pack 2 (SCCM 2007 SP 2) • Please use this guide to do lab exercises in the virtual “training environment” assigned to you NOTE: This training guide is an updated version of the previously released SP 1. Please refer to SP 1 training guide if your environment has not been updated to SP 2. Intel Confidential 2

Training Objectives • Provide an overview of Intel® v. Pro™ Technology and discuss its capabilities • Provide students with hands-on experience configuring System Center Configuration Manager 2007 SP 2 environment to support Intel® v. Pro™ capable machines • Provide hands-on experience provisioning and managing Intel® v. Pro™ capable machines • Show Case “Real World” use cases of Intel® v. Pro™ systems within a SCCM environment • Provide Students with a better understanding and ability to discuss the components necessary in Configuration Manager 2007 SP 2 to support Intel® v. Pro™ systems (both native and legacy support) with their customers, management, partners, vendors, etc Intel Confidential 3

Training Agenda • What is Intel® v. Pro™ Technology? – High level overview (Skip slides 7 -11 if you are already familiar with Intel® v. Pro™) • What is Intel® v. Pro™ Provisioning? (Skip slides 12 -14 if you are already familiar with Intel ® v. Pro™ provisioning) • Steps to access Intel’s Remote Training Environment (skip slides 16 -19 if you are running a local copy of the training images) • Lab Module 1 – Infrastructure Preparation – Hands-on experience configuring the Enterprise Infrastructure (AD/PKI) to support Config. Mgr 2007 SP 2 and Intel® v. Pro™ systems • Lab Module 2 - Config. Mgr 2007 SP 2 OOB Service Point and Components – Hands-on experience setting up and configuring Out of Band Service Point in Config. Mgr 2007 SP 2 to support Intel® v. Pro™ systems • Lab Module 3 – Config. Mgr 2007 SP 2 Collections and In. Band Provisioning – Hands-on experience utilizing the Config. Mgr 2007 SP 2 client agent for in-band provisioning – Hands-on experience configuring Config. Mgr 2007 SP 2 Collection for Discovering and automatically provisioning Intel® AMT capable machines • Lab Module 4 – Config. Mgr 2007 SP 2 Out of Band Management Console – Hands-on experience utilizing the Config. Mgr 2007 SP 2 OOB Console to manage (OOB) Intel® v. Pro™ systems • Lab Module 5 – Real World Use Cases – Hands-on setting up and running actual use cases for a production environment Intel Confidential 4

Training Caveats • This is not a replacement for Microsoft’s documentation on installing and configuring Config. Mgr 2007 SP 2 • This presentation only focuses on the Intel® v. Pro™ related configuration components • It is highly recommended that you thoroughly review all of Microsoft’s documentation before activating Intel® v. Pro™ with Config. Mgr 2007 SP 2 Recommended Material (from Microsoft Tech. Net): – – – – – What's New in Configuration Manager 2007 SP 2 Fundamentals of Configuration Manager 2007 Configuration Manager Planning and Deployment Overview Configuration Manager Supported Configurations Planning and Deploying the Server Infrastructure for Configuration Manager 2007 Planning and Deploying Clients for Configuration Manager 2007 How to Configure Configuration Manager 2007 Out of Band Management in Configuration Manager 2007 SP 1 and later Administrator Checklist: Enabling Out of Band Management Intel Confidential 5

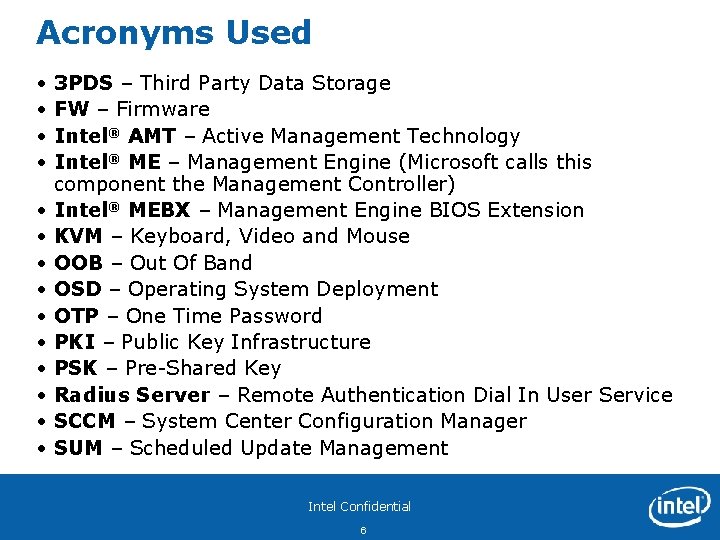
Acronyms Used • • • • 3 PDS – Third Party Data Storage FW – Firmware Intel® AMT – Active Management Technology Intel® ME – Management Engine (Microsoft calls this component the Management Controller) Intel® MEBX – Management Engine BIOS Extension KVM – Keyboard, Video and Mouse OOB – Out Of Band OSD – Operating System Deployment OTP – One Time Password PKI – Public Key Infrastructure PSK – Pre-Shared Key Radius Server – Remote Authentication Dial In User Service SCCM – System Center Configuration Manager SUM – Scheduled Update Management Intel Confidential 6

What is Intel® v. Pro™ Technology? Intel Confidential 7

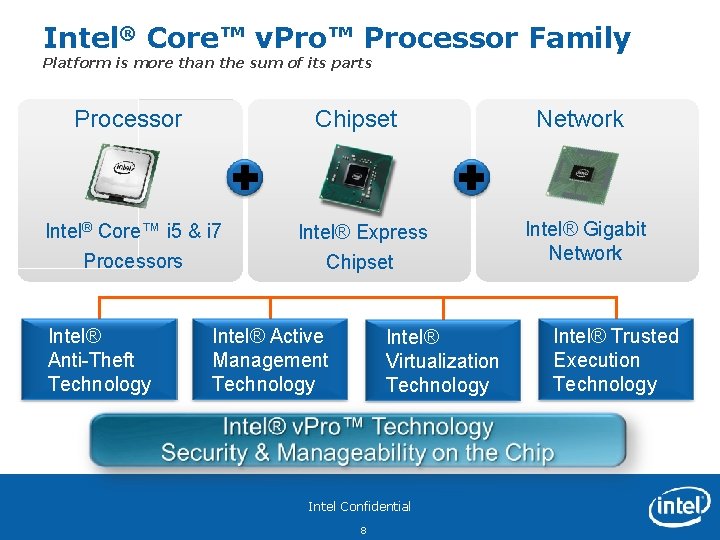
Intel® Core™ v. Pro™ Processor Family Platform is more than the sum of its parts Processor Chipset Intel® Core™ i 5 & i 7 Processors Intel® Anti-Theft Technology Intel® Express Chipset Intel® Active Management Technology Intel® Virtualization Technology Intel Confidential 8 Network Intel® Gigabit Network Intel® Trusted Execution Technology

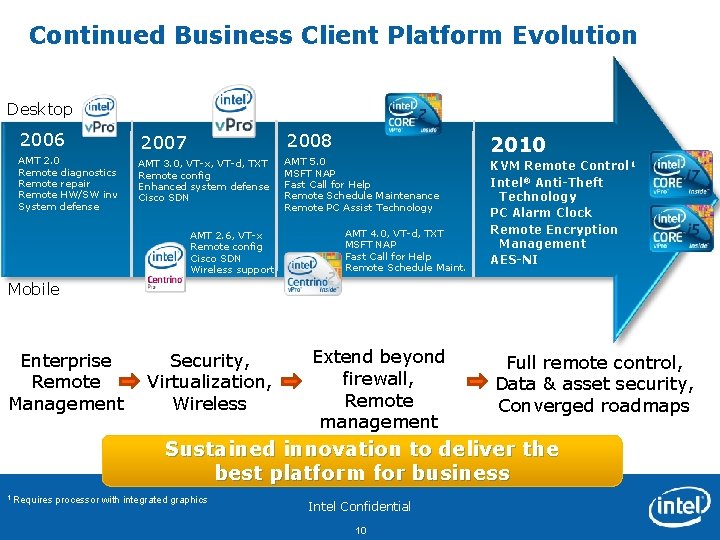
Continued Business Client Platform Evolution Desktop 2006 AMT 2. 0 Remote diagnostics Remote repair Remote HW/SW inv System defense 2008 2007 AMT 3. 0, VT-x, VT-d, TXT Remote config Enhanced system defense Cisco SDN AMT 2. 6, VT-x Remote config Cisco SDN Wireless support AMT 5. 0 MSFT NAP Fast Call for Help Remote Schedule Maintenance Remote PC Assist Technology AMT 4. 0, VT-d, TXT MSFT NAP Fast Call for Help Remote Schedule Maint. 2010 KVM Remote Control 1 Intel® Anti-Theft Technology PC Alarm Clock Remote Encryption Management AES-NI Mobile Enterprise Remote Management Extend beyond Full remote control, firewall, Data & asset security, Remote Converged roadmaps management Servicesto deliver the Sustained innovation Security, Virtualization, Wireless best platform for business 1 Requires processor with integrated graphics Intel Confidential 10

Intel Technology Business Impact ® ® PCs with Intel v. Pro TM Technology Actual Customer Experiences with Intel® v. Pro. TM Technology Up to 90% Reduction Software-Related Desk-Side Visits Indiana State Office of Technology Read case study 98% Up to 25% Less More 51% ROI Unintended PC Downtime due to Software Issues Power-Efficiency Improvement Advocate Health Care Value Space EDS Read case study View video on You. Tube http: //communities. intel. com/docs/DOC-1494/ Intel Confidential 11

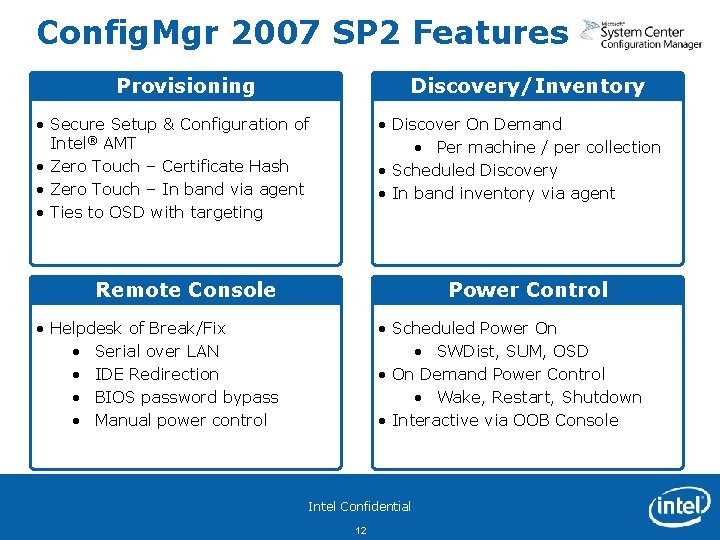
Config. Mgr 2007 SP 2 Features Provisioning Discovery/Inventory • Secure Setup & Configuration of Intel® AMT • Zero Touch – Certificate Hash • Zero Touch – In band via agent • Ties to OSD with targeting • Discover On Demand • Per machine / per collection • Scheduled Discovery • In band inventory via agent Remote Console Power Control • Helpdesk of Break/Fix • Serial over LAN • IDE Redirection • BIOS password bypass • Manual power control • Scheduled Power On • SWDist, SUM, OSD • On Demand Power Control • Wake, Restart, Shutdown • Interactive via OOB Console Intel Confidential 12

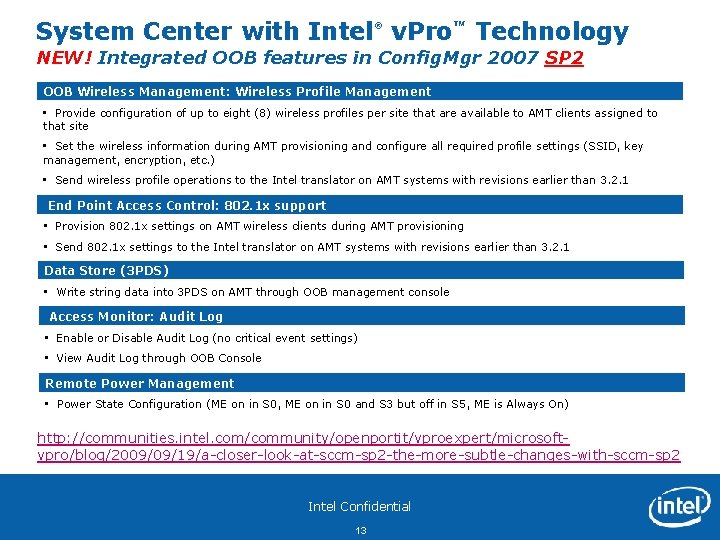
System Center with Intel® v. Pro™ Technology NEW! Integrated OOB features in Config. Mgr 2007 SP 2 OOB Wireless Management: Wireless Profile Management • Provide configuration of up to eight (8) wireless profiles per site that are available to AMT clients assigned to that site • Set the wireless information during AMT provisioning and configure all required profile settings (SSID, key management, encryption, etc. ) • Send wireless profile operations to the Intel translator on AMT systems with revisions earlier than 3. 2. 1 End Point Access Control: 802. 1 x support • Provision 802. 1 x settings on AMT wireless clients during AMT provisioning • Send 802. 1 x settings to the Intel translator on AMT systems with revisions earlier than 3. 2. 1 Data Store (3 PDS) • Write string data into 3 PDS on AMT through OOB management console Access Monitor: Audit Log • Enable or Disable Audit Log (no critical event settings) • View Audit Log through OOB Console Remote Power Management • Power State Configuration (ME on in S 0, ME on in S 0 and S 3 but off in S 5, ME is Always On) http: //communities. intel. com/community/openportit/vproexpert/microsoftvpro/blog/2009/09/19/a-closer-look-at-sccm-sp 2 -the-more-subtle-changes-with-sccm-sp 2 Intel Confidential 13

Intel® v. Pro™ Provisioning Intel Confidential 14

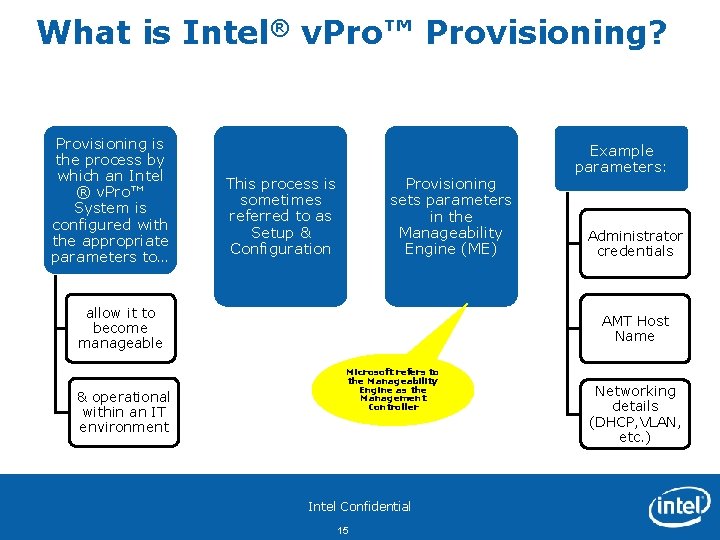
What is Intel® v. Pro™ Provisioning? Provisioning is the process by which an Intel ® v. Pro™ System is configured with the appropriate parameters to… This process is sometimes referred to as Setup & Configuration Provisioning sets parameters in the Manageability Engine (ME) allow it to become manageable & operational within an IT environment Example parameters: Administrator credentials AMT Host Name Microsoft refers to the Manageability Engine as the Management Controller Intel Confidential 15 Networking details (DHCP, VLAN, etc. )

Intel® v. Pro™ Manageability Engine BIOS Extension (MEBx) • The MEBx is the user interface to the Manageability Engine (ME); it allows for the configuration of settings that control the operation of the ME • The MEBx is an option ROM module provided to the OEM by Intel that is an extension to the system BIOS • The Manageability Engine runs on an embedded processor inside the Memory Controller Hub (MCH) and is responsible for executing the various AMT functions (Remote Power, IDE-Redirection, etc. ) Intel Confidential 16

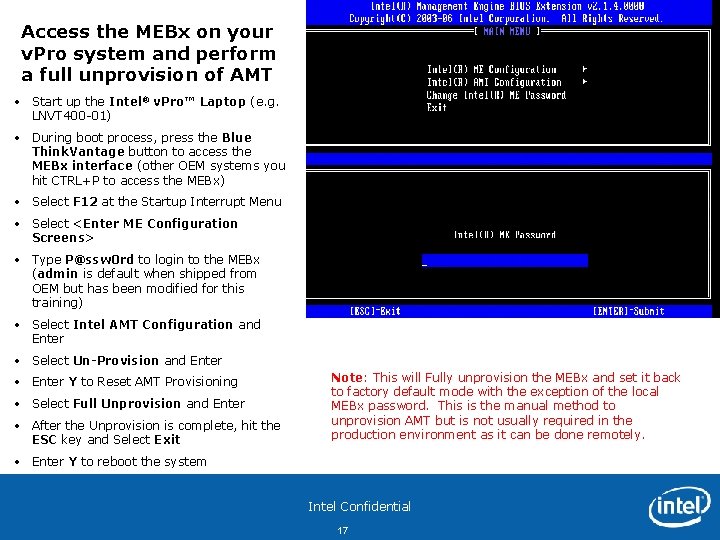
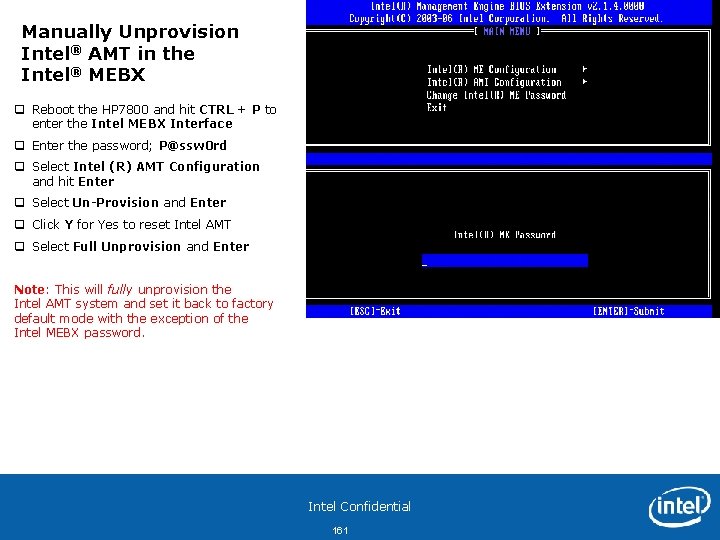
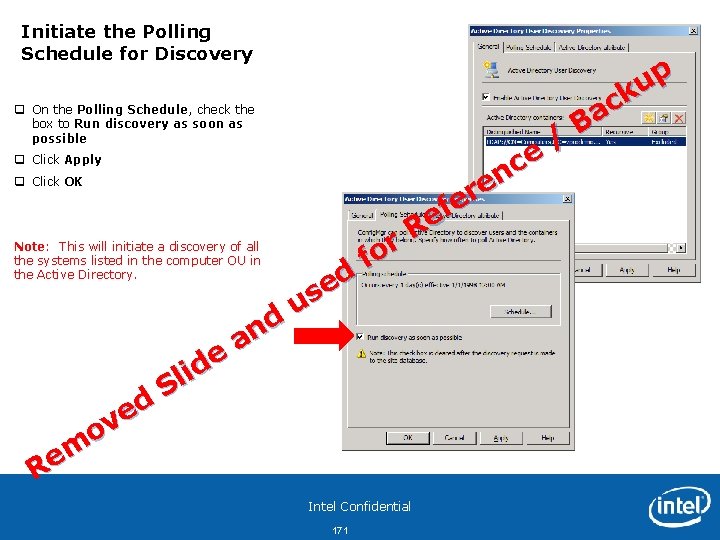
Access the MEBx on your v. Pro system and perform a full unprovision of AMT • Start up the Intel® v. Pro™ Laptop (e. g. LNVT 400 -01) • During boot process, press the Blue Think. Vantage button to access the MEBx interface (other OEM systems you hit CTRL+P to access the MEBx) • Select F 12 at the Startup Interrupt Menu • Select <Enter ME Configuration Screens> • Type P@ssw 0 rd to login to the MEBx (admin is default when shipped from OEM but has been modified for this training) • Select Intel AMT Configuration and Enter • Select Un-Provision and Enter • Enter Y to Reset AMT Provisioning • Select Full Unprovision and Enter • After the Unprovision is complete, hit the ESC key and Select Exit Note: This will Fully unprovision the MEBx and set it back to factory default mode with the exception of the local MEBx password. This is the manual method to unprovision AMT but is not usually required in the production environment as it can be done remotely. • Enter Y to reboot the system Intel Confidential 17

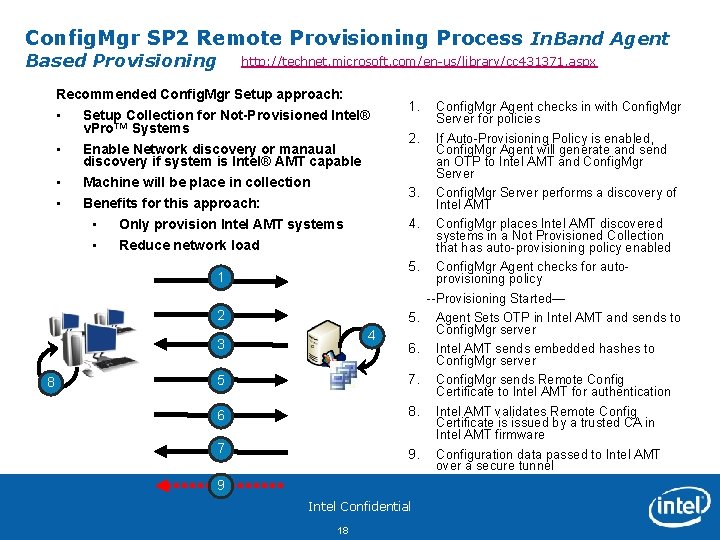
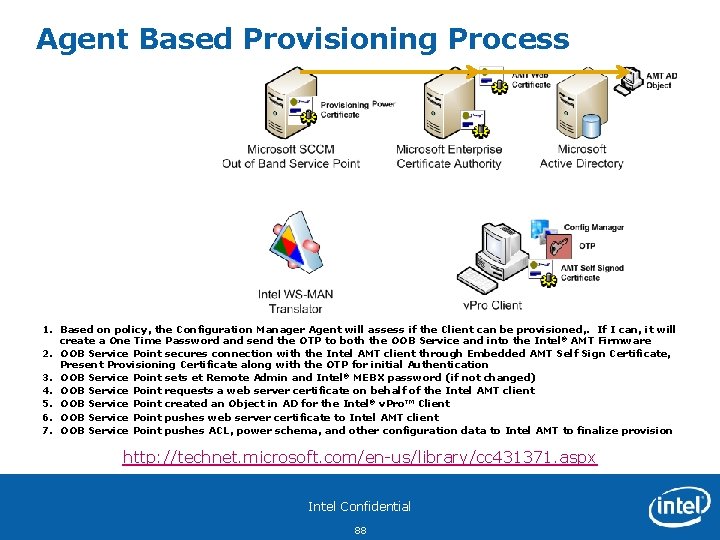
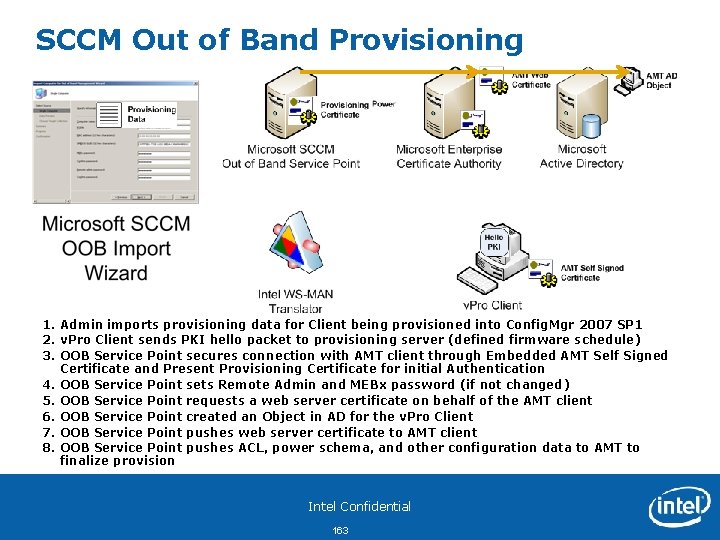
Config. Mgr SP 2 Remote Provisioning Process In. Band Agent Based Provisioning http: //technet. microsoft. com/en-us/library/cc 431371. aspx Recommended Config. Mgr Setup approach: • • Setup Collection for Not-Provisioned Intel® v. Pro™ Systems Enable Network discovery or manaual discovery if system is Intel® AMT capable Machine will be place in collection 2 5 4 SCCM Primary Site Server Config. Mgr places Intel AMT discovered systems in a Not Provisioned Collection that has auto-provisioning policy enabled 5. Config. Mgr Agent checks for autoprovisioning policy --Provisioning Started— 5. Agent Sets OTP in Intel AMT and sends to Config. Mgr server 6. 7. 6 8. 7 9. 9 Intel Confidential 18 Config. Mgr Agent checks in with Config. Mgr Server for policies If Auto-Provisioning Policy is enabled, Config. Mgr Agent will generate and send an OTP to Intel AMT and Config. Mgr Server performs a discovery of Intel AMT 4. 1 8 Intel® v. Pro™ Clients 2. 3. Benefits for this approach: • Only provision Intel AMT systems • Reduce network load 3 1. Intel AMT sends embedded hashes to Config. Mgr server Config. Mgr sends Remote Config Certificate to Intel AMT for authentication Intel AMT validates Remote Config Certificate is issued by a trusted CA in Intel AMT firmware Configuration data passed to Intel AMT over a secure tunnel

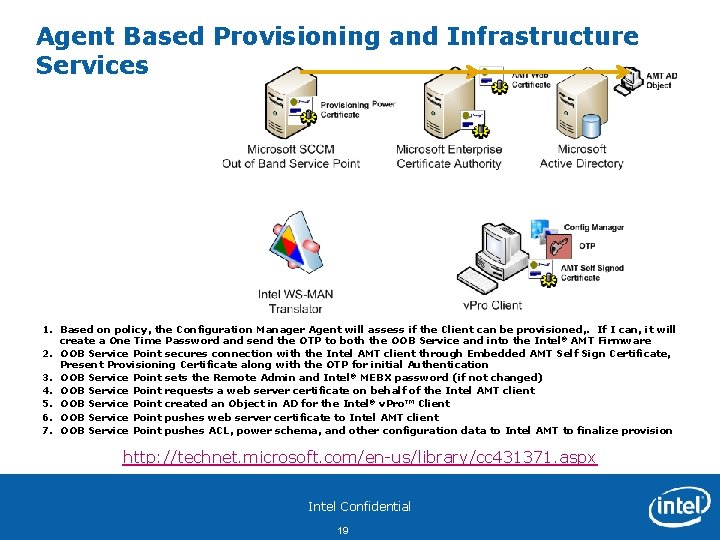
Agent Based Provisioning and Infrastructure Services 1. Based on policy, the Configuration Manager Agent will assess if the Client can be provisioned, . If I can, it will create a One Time Password and send the OTP to both the OOB Service and into the Intel® AMT Firmware 2. OOB Service Point secures connection with the Intel AMT client through Embedded AMT Self Sign Certificate, Present Provisioning Certificate along with the OTP for initial Authentication 3. OOB Service Point sets the Remote Admin and Intel® MEBX password (if not changed) 4. OOB Service Point requests a web server certificate on behalf of the Intel AMT client 5. OOB Service Point created an Object in AD for the Intel® v. Pro™ Client 6. OOB Service Point pushes web server certificate to Intel AMT client 7. OOB Service Point pushes ACL, power schema, and other configuration data to Intel AMT to finalize provision http: //technet. microsoft. com/en-us/library/cc 431371. aspx Intel Confidential 19

Physical Hands-on Training Lab Environment Intel Confidential 23

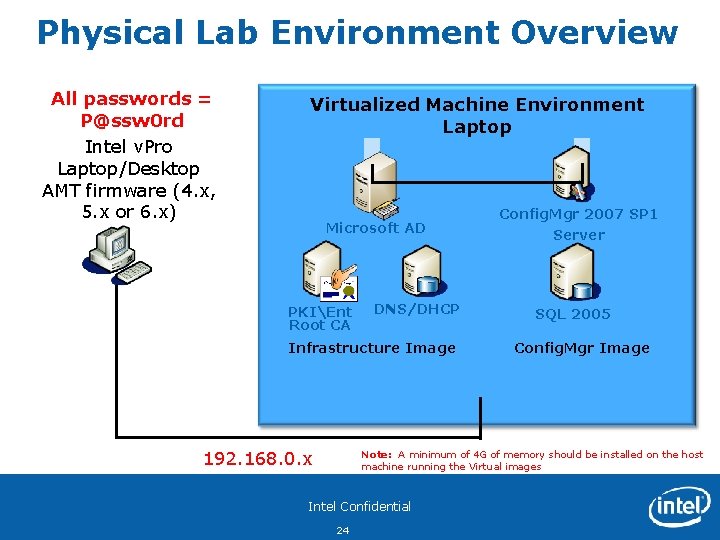
Physical Lab Environment Overview All passwords = P@ssw 0 rd Intel v. Pro Laptop/Desktop AMT firmware (4. x, 5. x or 6. x) Virtualized Machine Environment Laptop Microsoft AD PKIEnt Root CA DNS/DHCP Infrastructure Image 192. 168. 0. x Config. Mgr 2007 SP 1 Server SQL 2005 Config. Mgr Image Note: A minimum of 4 G of memory should be installed on the host machine running the Virtual images Intel Confidential 24

Launch the Microsoft Virtual Infrastructure Image q Start the laptop (e. g. HP 6930 P) hosting the Virtual Images q Double Click the shortcut DC 1 on the Desktop of the host OS to start the Infrastructure VM image Note: • To Maximize/Minimize the Virtual Image window CTRL + ALT + ENTER • As needed, Use CTRL+ ALT + Insert to login • Login Information • Domain Admin: ITproadmin • Password: P@ssw 0 rd • Domain: VPRODEMO Note: Make sure you have not started your Config. Mgr 2007 SP 1 Server Image up until after completing the configuration of your infrastructure image. Intel Confidential 25

Lab Module 1 Configure the Active Directory and PKI Infrastructure to support Configuration Manger 2007 SP 2 and Intel® v. Pro™ Systems Intel Confidential 26

Prepare Active Directory Domain Services for Out of Band Management Intel Confidential 27

Active Directory Configuration • Active Directory OU container must be created to store Intel® AMT device objects – Recommended Name: Out of Band Management Controllers – Primary site server computer account (Config. Mgr 2007 SP 2 Server) must be granted Full Control permissions on the OU and all child objects in the OU – http: //technet. microsoft. com/en-us/library/cc 161814. aspx – Schema Extension not required for Intel® v. Pro™ support – However Schema Extension is required for other Config. Mgr 2007 SP 2 features and make Config. Mgr 2007 SP 2 Client Agent Deployments easier (required for Agent Based provisioning) • Extend AD Schema (optional): http: //technet. microsoft. com/en- us/library/bb 633121(Tech. Net. 10). aspx Intel Confidential 28

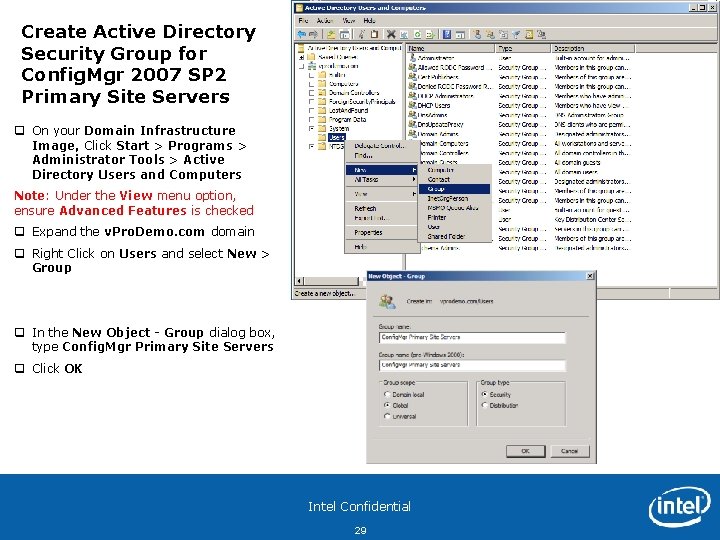
Create Active Directory Security Group for Config. Mgr 2007 SP 2 Primary Site Servers q On your Domain Infrastructure Image, Click Start > Programs > Administrator Tools > Active Directory Users and Computers Note: Under the View menu option, ensure Advanced Features is checked q Expand the v. Pro. Demo. com domain q Right Click on Users and select New > Group q In the New Object - Group dialog box, type Config. Mgr Primary Site Servers q Click OK Intel Confidential 29

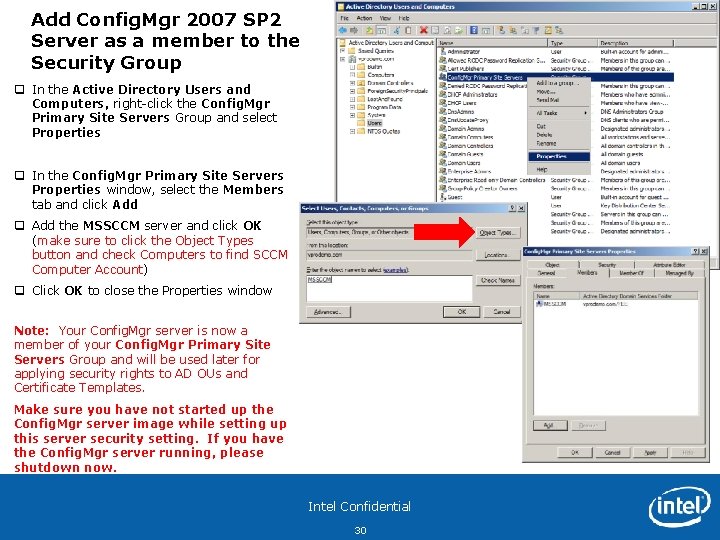
Add Config. Mgr 2007 SP 2 Server as a member to the Security Group q In the Active Directory Users and Computers, right-click the Config. Mgr Primary Site Servers Group and select Properties q In the Config. Mgr Primary Site Servers Properties window, select the Members tab and click Add q Add the MSSCCM server and click OK (make sure to click the Object Types button and check Computers to find SCCM Computer Account) q Click OK to close the Properties window Note: Your Config. Mgr server is now a member of your Config. Mgr Primary Site Servers Group and will be used later for applying security rights to AD OUs and Certificate Templates. Make sure you have not started up the Config. Mgr server image while setting up this server security setting. If you have the Config. Mgr server running, please shutdown now. Intel Confidential 30

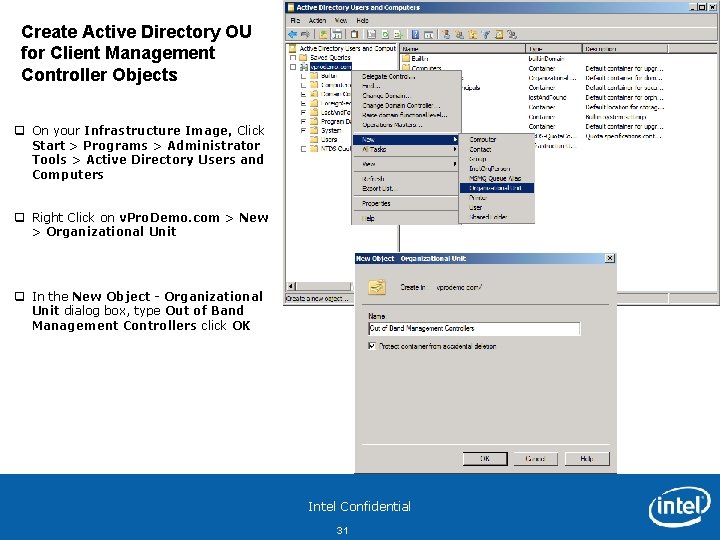
Create Active Directory OU for Client Management Controller Objects q On your Infrastructure Image, Click Start > Programs > Administrator Tools > Active Directory Users and Computers q Right Click on v. Pro. Demo. com > New > Organizational Unit q In the New Object - Organizational Unit dialog box, type Out of Band Management Controllers click OK Intel Confidential 31

Add Config. Mrg Primary Site Servers Security group to the Management Controller OU q Right-click Out of Band Management Controllers OU and click Properties q In the Out of Band Management Controllers Properties window, click the Security tab q Click Add and select the Config. Mgr Primary Site Servers group q Click OK to add the group, but DO NOT close the Properties window…continue to next slide to set full control for this group. Intel Confidential 32

Give Full Control for Config. Mrg Primary Site Servers Security group to the Management Controllers OU q Check Full Control for Config. Mgr Primary Site Servers Security Group q With Config. Mgr Primary Site Servers selected, click Advanced q Highlight Config. Mgr Primary Site Servers group, and click Edit q In the Apply to drop down, select This object and all descendant objects q Click OK 3 times Note: We have now created an AD OU and given the Config. Mgr 2007 SP 2 proper permission to create AMT objects for each v. Pro system during the provisioning phase. Intel Confidential 33

Create RADIUS Security Group for AMT devices q On your Infrastructure Image, Click Start > Programs > Administrator Tools > Active Directory Users and Computers q Expand v. Pro. Demo. com and Right Click on Users and select New > Group q In the New Object – Group Windows, enter AMT RADIUS Clients in the Group name field q Click OK Intel Confidential 34

Set Permissions on RADIUS Security Group q Right Click on AMT RADIUS Clients Group and select Properties q In the AMT RADIUS Clients Properties Window, Click the Security Tab and Click the Add button q In the Select Users, Computers, or Groups Window, add Config. Mgr Primary Site Servers q Click OK q Select the Config. Mgr Primary Site Servers and select Full control q Click OK COMPLETED: We have now created an AD OU, AMT Radius Group, and given the Security Group that Config. Mgr 2007 SP 2 Server is a member of, the proper permission to create Management Controllers objects for each Intel® v. Pro™ system during the provisioning phase. Intel Confidential 35

Configure PKI Web Server Certificates for each Management Controller Intel Confidential 36

Closer look at Certificates with Config. Mgr 2007 SP 2 and Intel® v. Pro™ • There are three types of Certificates that are used in association to Intel v. Pro client provisioning and management within Config. Mgr 2007 SP 2 • Intel® AMT Self Signed Certificate • Used during PKI provisioning to secure the connection • Transparent to process • Intel® AMT Provisioning Certificate • Used for Remote Configuration authentication by the Out of Band Service Point • Can be generated from Internal PKI Infrastructure or purchased from 3 rd Party CA (Veri. Sign*, Go. Daddy*, Comodo, Starfield) • Provisioning certificate can be generated from internal PKI environment • Require Internal Root hash to be imported into the MEBx • Requires Option 15 set on DHCP to support “Zero Touch” Configuration • Intel® AMT Web Server Certificate • Used to secure a connection to Intel AMT client by the management console • Issued to the Intel AMT client during the provisioning process • Config. Mgr 2007 SP 2 requires the certificate to be issued by a Microsoft Enterprise CA • PKI certificate key sizes <=2048 -bits Intel Confidential 37

Enterprise CA & Provision Certificate Configuration • Assumes that a Microsoft Enterprise CA exists and is already configured • Two Certificates Required: Intel ® AMT Provisioning & Intel AMT TLS Web Server Cert • Intel AMT Provisioning Certificate (Used for Provisioning) • Determine 3 rd party or Self Generated • 3 rd Party CA (Veri. Sign*, Go Daddy*, Comodo, Starfield) • http: //technet. microsoft. com/en-us/library/cc 161804. aspx#BKMK_AMTprovisioning 1 • Self Generated from Internal PKI infrastructure • http: //technet. microsoft. com/en-us/library/cc 161804. aspx#BKMK_AMTprovisioning 2 • Export Cert for Config. Mgr 2007 SP 2 / WS-MAN Translator in later configuration step • http: //technet. microsoft. com/en-us/library/cc 161804. aspx#BKMK_AMTprovisioning 3 • Web Server Certificate (Intel AMT TLS Cert used for securely managing v. Pro) • Create New Web server Template • Recommend certificate name: Config. Mgr AMT Web Server Certificate • Primary site server computer account (Config. Mgr 2007 SP 2 Server) must have Read/Enroll permissions • http: //technet. microsoft. com/en-us/library/cc 161804. aspx#BKMK_AMTwebserver • 802. 1 x RADIUS Certificate (Optional for 802. 1 x networks) • Create New RADIUS Client Template for 802. 1 x network • Allows AMT to securely authenticate to an 802. 1 x network without an OS present • Recommend certificate name: Config. Mgr AMT 802. 1 X Client Authentication Certificate • Ensure you select Supply in the request to provide the Subject Name • Primary site server computer account (Config. Mgr 2007 SP 2 Server) must have Read/Enroll permissions • http: //technet. microsoft. com/en-us/library/cc 431417. aspx#BKMK_AMTClient. Certificate Intel Confidential 38

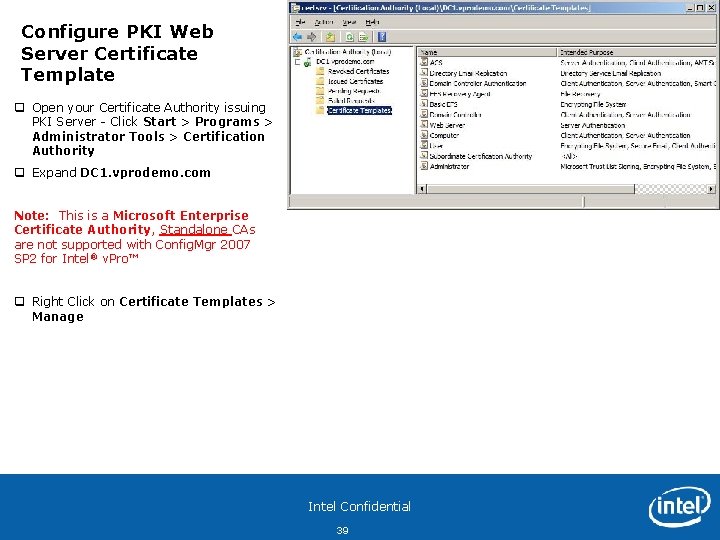
Configure PKI Web Server Certificate Template q Open your Certificate Authority issuing PKI Server - Click Start > Programs > Administrator Tools > Certification Authority q Expand DC 1. vprodemo. com Note: This is a Microsoft Enterprise Certificate Authority, Standalone CAs are not supported with Config. Mgr 2007 SP 2 for Intel® v. Pro™ q Right Click on Certificate Templates > Manage Intel Confidential 39

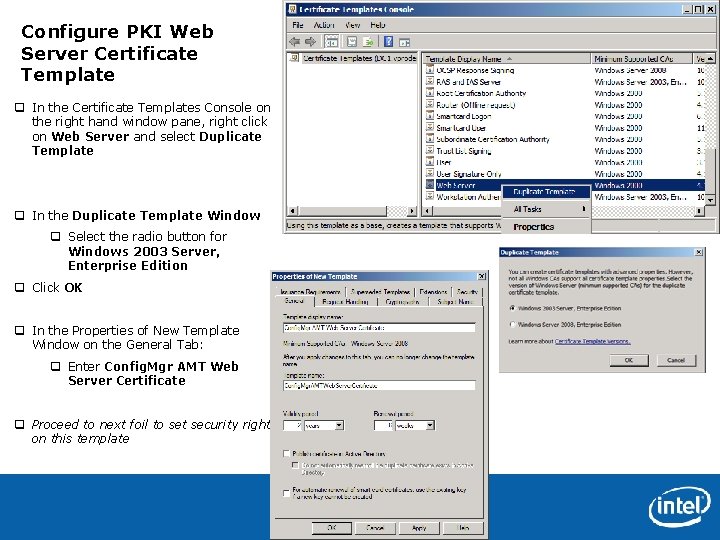
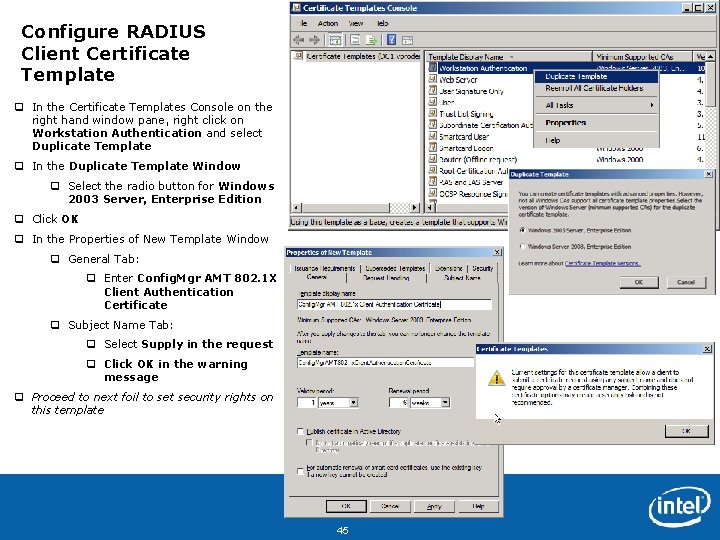
Configure PKI Web Server Certificate Template q In the Certificate Templates Console on the right hand window pane, right click on Web Server and select Duplicate Template q In the Duplicate Template Window q Select the radio button for Windows 2003 Server, Enterprise Edition q Click OK q In the Properties of New Template Window on the General Tab: q Enter Config. Mgr AMT Web Server Certificate q Proceed to next foil to set security rights on this template Intel Confidential 40

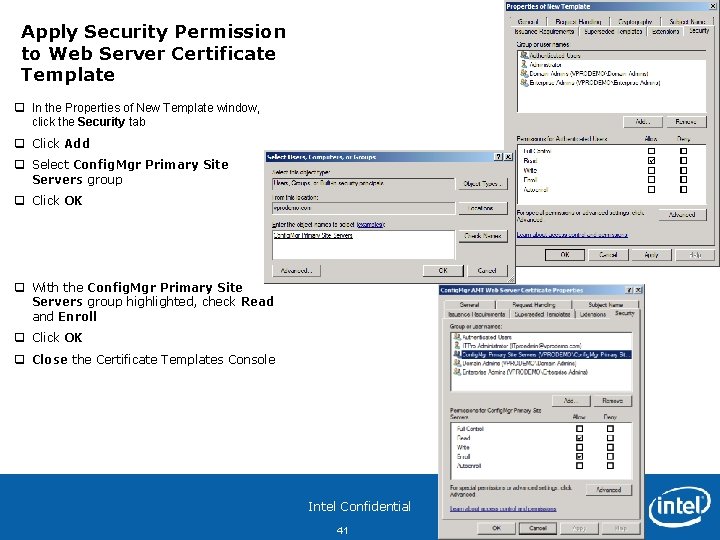
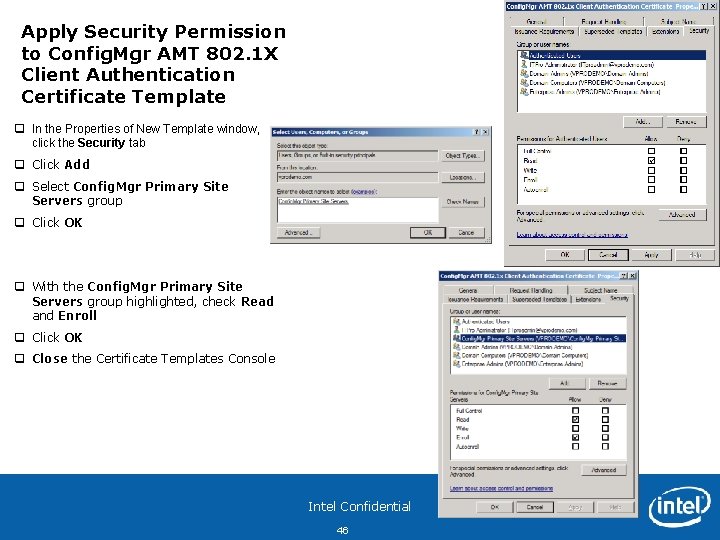
Apply Security Permission to Web Server Certificate Template q In the Properties of New Template window, click the Security tab q Click Add q Select Config. Mgr Primary Site Servers group q Click OK q With the Config. Mgr Primary Site Servers group highlighted, check Read and Enroll q Click OK q Close the Certificate Templates Console Intel Confidential 41

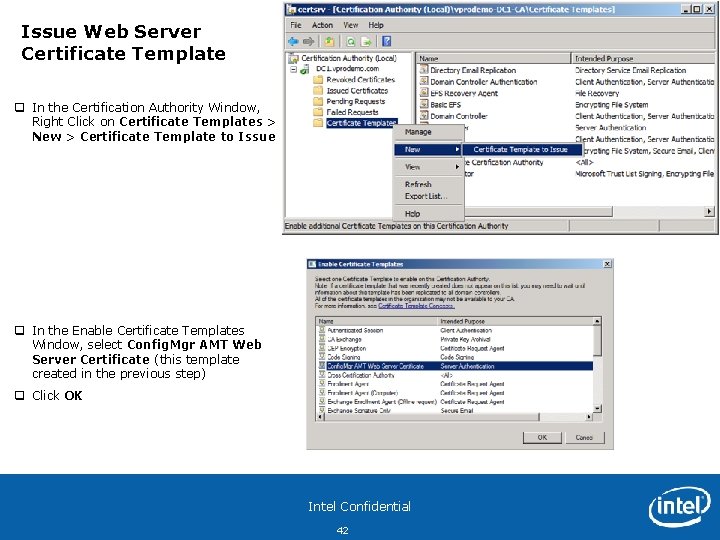
Issue Web Server Certificate Template q In the Certification Authority Window, Right Click on Certificate Templates > New > Certificate Template to Issue q In the Enable Certificate Templates Window, select Config. Mgr AMT Web Server Certificate (this template created in the previous step) q Click OK Intel Confidential 42

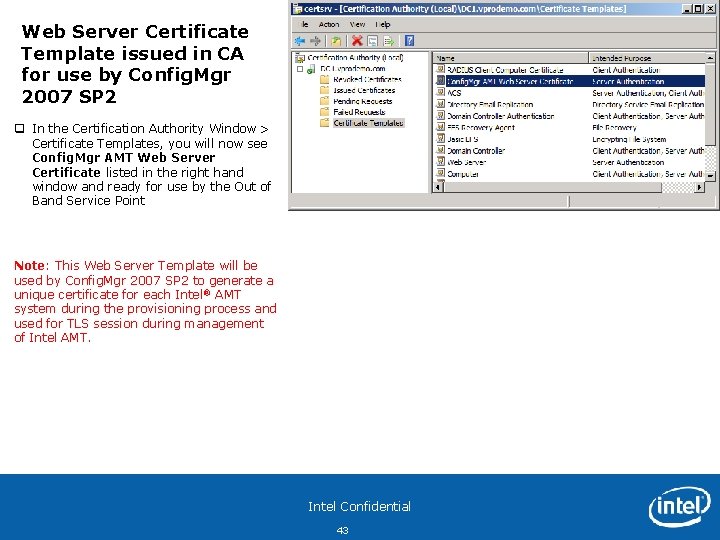
Web Server Certificate Template issued in CA for use by Config. Mgr 2007 SP 2 q In the Certification Authority Window > Certificate Templates, you will now see Config. Mgr AMT Web Server Certificate listed in the right hand window and ready for use by the Out of Band Service Point Note: This Web Server Template will be used by Config. Mgr 2007 SP 2 to generate a unique certificate for each Intel ® AMT system during the provisioning process and used for TLS session during management of Intel AMT. Intel Confidential 43

Configure RADIUS Client Certificate Template q Open your Certificate Authority issuing PKI Server - Click Start > Programs > Administrator Tools > Certification Authority q Expand DC 1. vprodemo. com q Right Click on Certificate Templates > Manage Intel Confidential 44

Configure RADIUS Client Certificate Template q In the Certificate Templates Console on the right hand window pane, right click on Workstation Authentication and select Duplicate Template q In the Duplicate Template Window q Select the radio button for Windows 2003 Server, Enterprise Edition q Click OK q In the Properties of New Template Window q General Tab: q Enter Config. Mgr AMT 802. 1 X Client Authentication Certificate q Subject Name Tab: q Select Supply in the request q Click OK in the warning message q Proceed to next foil to set security rights on this template Intel Confidential 45

Apply Security Permission to Config. Mgr AMT 802. 1 X Client Authentication Certificate Template q In the Properties of New Template window, click the Security tab q Click Add q Select Config. Mgr Primary Site Servers group q Click OK q With the Config. Mgr Primary Site Servers group highlighted, check Read and Enroll q Click OK q Close the Certificate Templates Console Intel Confidential 46

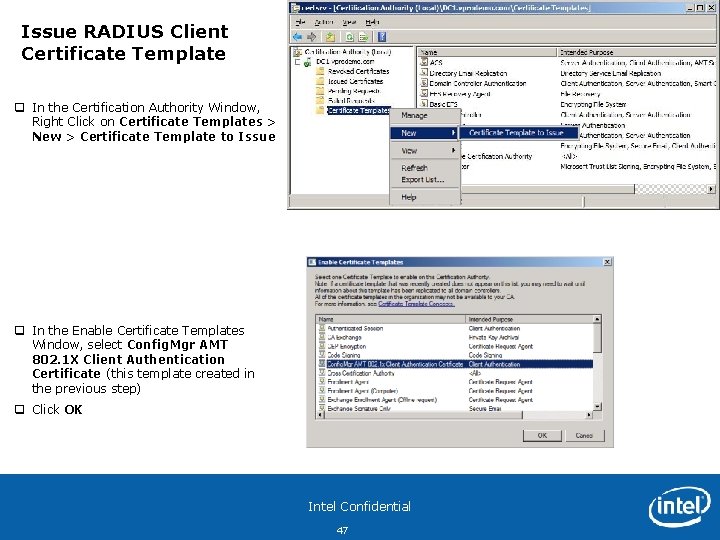
Issue RADIUS Client Certificate Template q In the Certification Authority Window, Right Click on Certificate Templates > New > Certificate Template to Issue q In the Enable Certificate Templates Window, select Config. Mgr AMT 802. 1 X Client Authentication Certificate (this template created in the previous step) q Click OK Intel Confidential 47

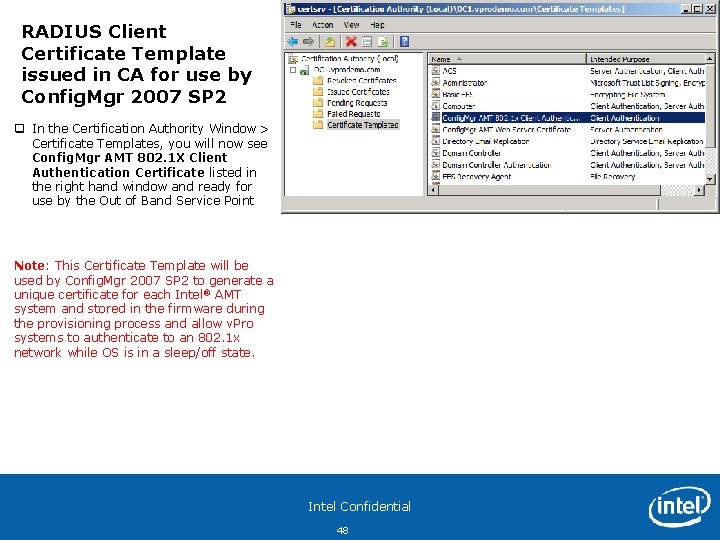
RADIUS Client Certificate Template issued in CA for use by Config. Mgr 2007 SP 2 q In the Certification Authority Window > Certificate Templates, you will now see Config. Mgr AMT 802. 1 X Client Authentication Certificate listed in the right hand window and ready for use by the Out of Band Service Point Note: This Certificate Template will be used by Config. Mgr 2007 SP 2 to generate a unique certificate for each Intel ® AMT system and stored in the firmware during the provisioning process and allow v. Pro systems to authenticate to an 802. 1 x network while OS is in a sleep/off state. Intel Confidential 48

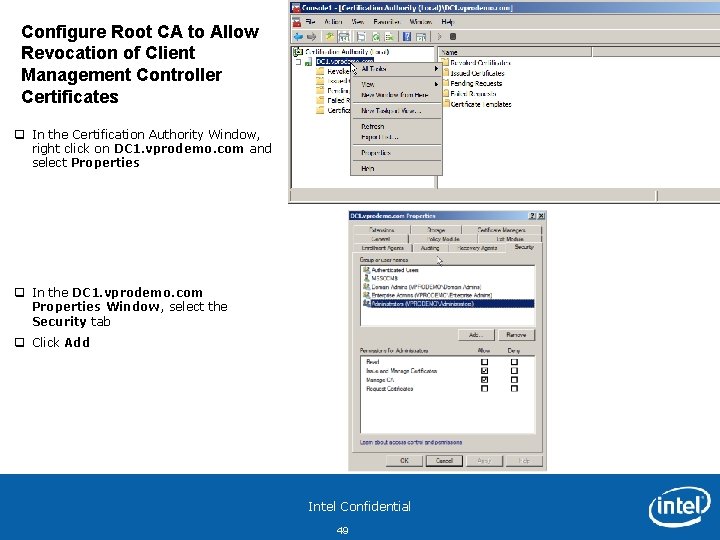
Configure Root CA to Allow Revocation of Client Management Controller Certificates q In the Certification Authority Window, right click on DC 1. vprodemo. com and select Properties q In the DC 1. vprodemo. com Properties Window, select the Security tab q Click Add Intel Confidential 49

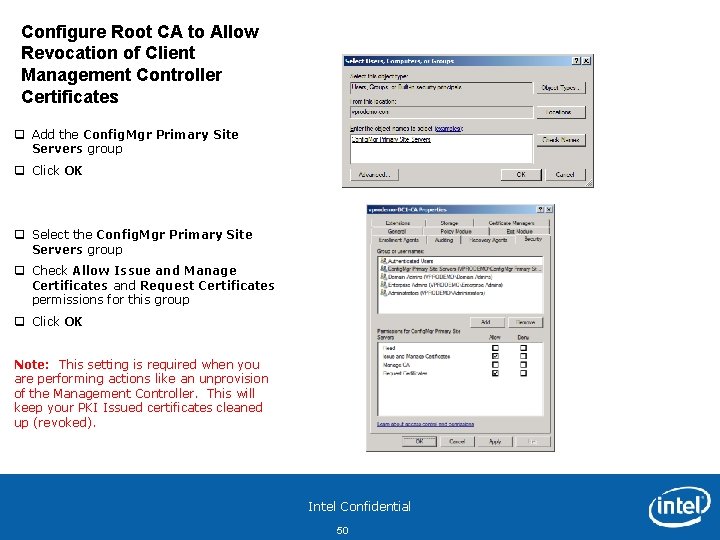
Configure Root CA to Allow Revocation of Client Management Controller Certificates q Add the Config. Mgr Primary Site Servers group q Click OK q Select the Config. Mgr Primary Site Servers group q Check Allow Issue and Manage Certificates and Request Certificates permissions for this group q Click OK Note: This setting is required when you are performing actions like an unprovision of the Management Controller. This will keep your PKI Issued certificates cleaned up (revoked). Intel Confidential 50

Lab 1 Exercise Review Active Directory Changes Enterprise PKI Changes • Created Active Directory Security Group for Config. Mgr 2007 SP 2 Primary Site Servers • Added Config. Mgr 2007 SP 2 Server as a member to the Security Group • Created Active Directory OU for Client Management Controller Objects • Added Config. Mgr Primary Site Servers Security group to the Management Controller OU • Gave Full Control for Config. Mgr Primary Site Servers Security group to the Management Controllers OU • Configured PKI Web Server Certificate Template • Applied Security Permission to Web Server Certificate Template • Issued Web Server Certificate Template for use by Config. Mgr 2007 SP 2 • Created RADIUS Client Template and issued for RADIUS certificates • Configure Root CA to Allow Revocation of Client Management Controller Certificates Intel Confidential 51

Lab Module 2 Install and Configure Configuration Manager 2007 SP 2 Out of Band Service Point to support Intel® v. Pro™ Systems Intel Confidential 52

Launch the Microsoft Virtual PC Config. Mgr Image q Double Click the shortcut SCCM SP 2 on the host OS to start the SCCM SP 2 VM image (leaving the Infrastructure running in parallel) Note: • To Maximize/Minimize the Virtual Image window CTRL + ALT + ENTER • As needed, Use CTRL+ ALT + Insert to login • Login Information • Domain Admin: ITproadmin • Password: P@ssw 0 rd • Domain: VPRODEMO Intel Confidential 53

Config. Mgr 2007 SP 2 Out-of-Band Management Service Point • OOB Management : Out of band management allows an administrator to connect to a computer's management controller (a. k. a. Management Engine) when the computer is turned off, in sleep or hibernate modes, or otherwise unresponsive through the operating system. (http: //technet. microsoft. com/en-us/library/cc 161963. aspx) • OOB Service Point – Config. Mgr 2007 SP 2 Service component (role) responsible for provisioning and managing Management Controllers (aka Intel® AMT). – Installing: http: //technet. microsoft. com/enus/library/cc 161863. aspx Intel Confidential 54

Config. Mgr 2007 SP 2 Prerequisites http: //technet. microsoft. com/en-us/library/cc 161785. aspx • Prior to Config. Mgr 2007 SP 2 install, ensure ALL prerequisites are met (see link above of complete list) – Telnet is installed on computers running the OOB management console with Vista and Windows 2008 (used for So. L) – IE / Kerberos authentication on non-standard port Hot. Fix (KB 908209) – hotfix is for IE 6 but registry key applies to all IE versions – http: //support. microsoft. com/kb/908209 • If Config. Mgr 2007 SP 2 is not installed, install prior to Config. Mgr 2007 SP 2 setup and config – Refer to Microsoft’s Install and Configuration documentation – http: //technet. microsoft. com/en-us/library/bb 735860 • Download and Install Config. Mgr 2007 SP 2: – http: //www. microsoft. com/downloads/details. aspx? familyid=BAD 49573 -6 AD 74521 -A 898 -2 EF 99 BC 868 C 4&displaylang=en • Create a Config. Mgr 2007 SP 2 Site Boundary – http: //technet. microsoft. com/en-us/library/bb 693530. aspx Intel Confidential 55

Install Out of Band Service Point q Open the Config. Mgr Console (shortcut located on the desktop of the SCCM image) q Navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Primary Site > Site Settings > Site Systems q Right-click \MSSCCM and click New Roles to launch the New Site Roles Wizard http: //technet. microsoft. com/en-us/library/cc 161863. aspx Intel Confidential 56

Install Out of Band Service Point q On the General page, click Next (default settings) Intel Confidential 57

Install Out of Band Service Point q On the System Role Selection page, check Out of band service point, and click Next Intel Confidential 58

Install Out of Band Service Point q On the Out of Band Service Point page, click Next q Click Next again on Summary page Intel Confidential 59

Install Out of Band Service Point q Once the Wizard completes, click Close You have now added the required Service Role to support Intel® v. Pro™ Systems through Config. Mgr 2007 SP 2. Intel Confidential 60

Install Out of Band Service Point q You will now see Config. Mgr out of band service point listed under the \MSSCCM Roles Note: After installing the Config. Mgr 2007 SP 2 Out of Band Service Point, the log file C: Program FilesMicrosoft Configuration ManagerLogsAMTSPSetup. Log can be reviewed to inspect the success or failure of the installation. Intel Confidential 61

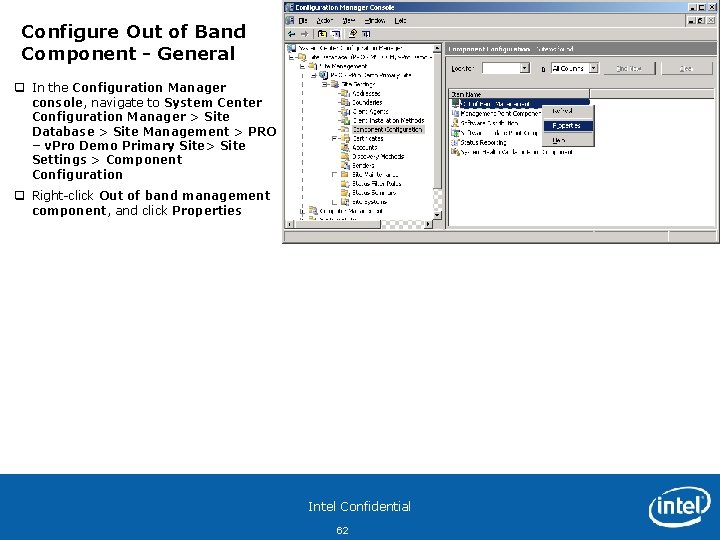
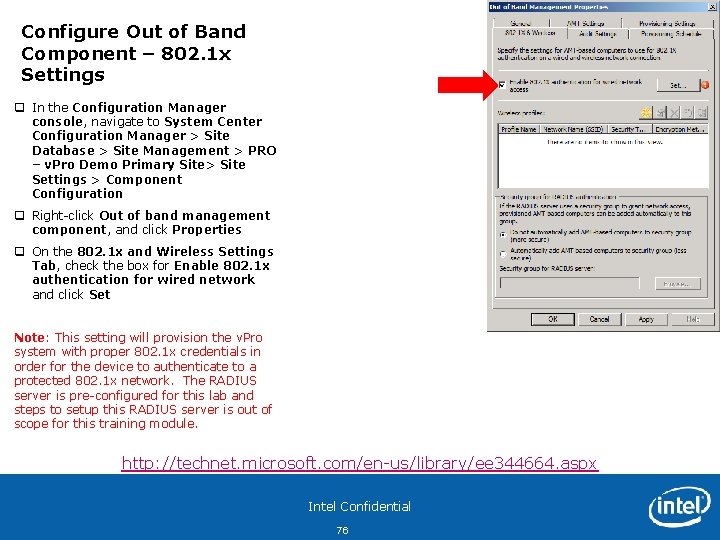
Configure Out of Band Component - General q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Primary Site> Site Settings > Component Configuration q Right-click Out of band management component, and click Properties Intel Confidential 62

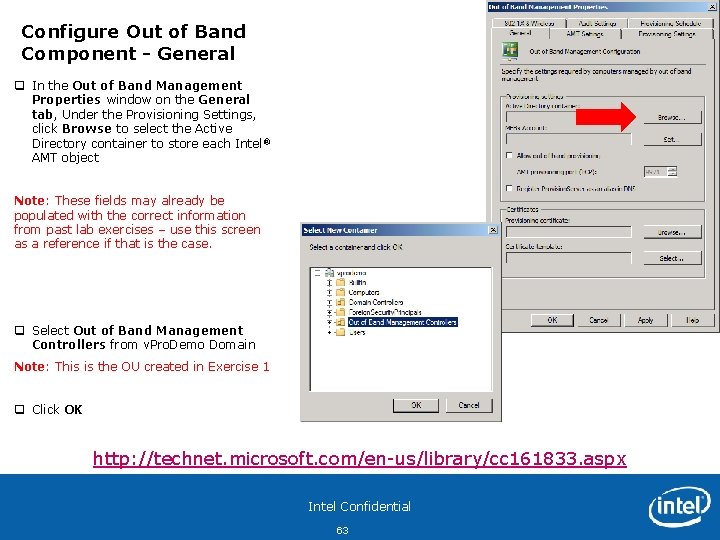
Configure Out of Band Component - General q In the Out of Band Management Properties window on the General tab, Under the Provisioning Settings, click Browse to select the Active Directory container to store each Intel ® AMT object Note: These fields may already be populated with the correct information from past lab exercises – use this screen as a reference if that is the case. q Select Out of Band Management Controllers from v. Pro. Demo Domain Note: This is the OU created in Exercise 1 q Click OK http: //technet. microsoft. com/en-us/library/cc 161833. aspx Intel Confidential 63

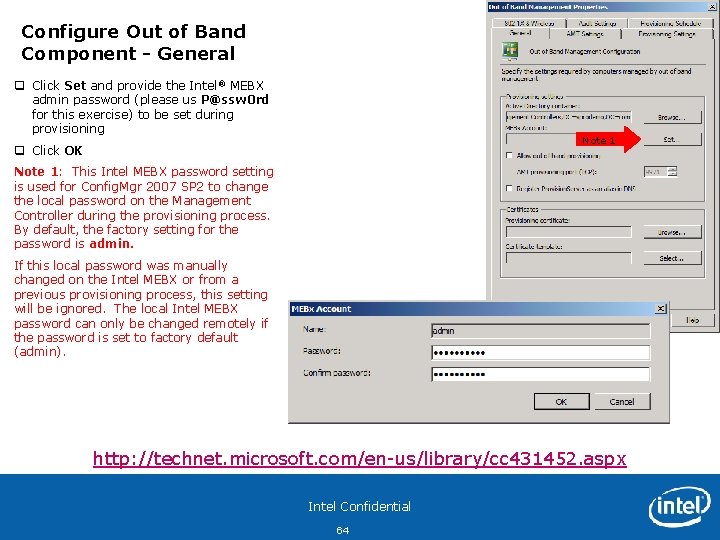
Configure Out of Band Component - General q Click Set and provide the Intel® MEBX admin password (please us P@ssw 0 rd for this exercise) to be set during provisioning Note 1 q Click OK Note 1: This Intel MEBX password setting is used for Config. Mgr 2007 SP 2 to change the local password on the Management Controller during the provisioning process. By default, the factory setting for the password is admin. If this local password was manually changed on the Intel MEBX or from a previous provisioning process, this setting will be ignored. The local Intel MEBX password can only be changed remotely if the password is set to factory default (admin). http: //technet. microsoft. com/en-us/library/cc 431452. aspx Intel Confidential 64

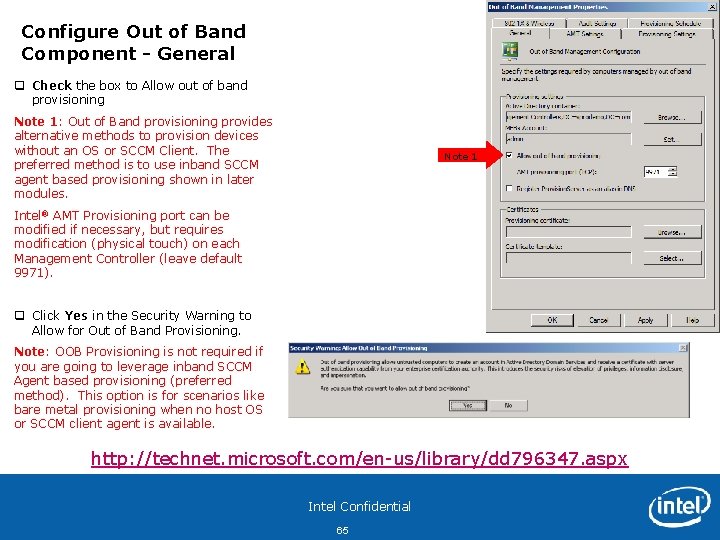
Configure Out of Band Component - General q Check the box to Allow out of band provisioning Note 1: Out of Band provisioning provides alternative methods to provision devices without an OS or SCCM Client. The preferred method is to use inband SCCM agent based provisioning shown in later modules. Note 1 Intel® AMT Provisioning port can be modified if necessary, but requires modification (physical touch) on each Management Controller (leave default 9971). q Click Yes in the Security Warning to Allow for Out of Band Provisioning. Note: OOB Provisioning is not required if you are going to leverage inband SCCM Agent based provisioning (preferred method). This option is for scenarios like bare metal provisioning when no host OS or SCCM client agent is available. http: //technet. microsoft. com/en-us/library/dd 796347. aspx Intel Confidential 65

Configure Out of Band Component - General q Check the box to Register Provision. Server as an alias in DNS Note: This creates an Alias in your DNS environment to allow provisioning hello packets from AMT to get routed to the Config. Mgr 2007 SP 2 server used in PSK / Bare Metal Provisioning and SCS -> Config. Mgr 2007 SP 2 migration. This would not apply or be necessary for in-band Config. Mgr 2007 SP 2 Agent initiated Provisioning. Intel Confidential 66

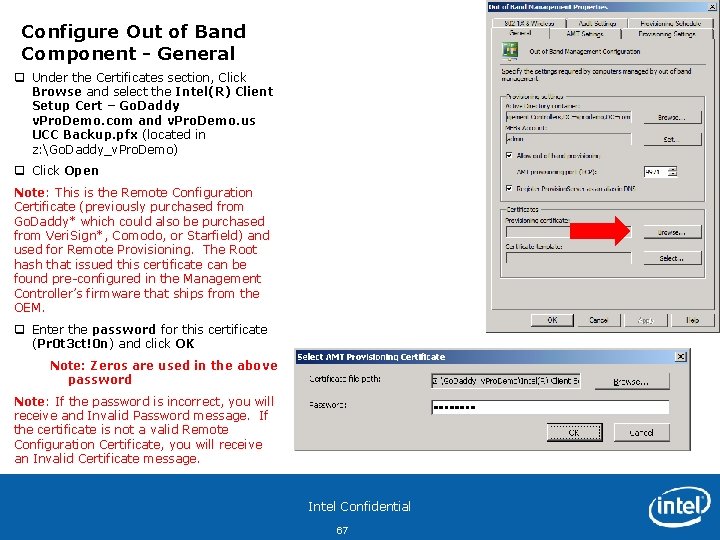
Configure Out of Band Component - General q Under the Certificates section, Click Browse and select the Intel(R) Client Setup Cert – Go. Daddy v. Pro. Demo. com and v. Pro. Demo. us UCC Backup. pfx (located in z: Go. Daddy_v. Pro. Demo) q Click Open Note: This is the Remote Configuration Certificate (previously purchased from Go. Daddy* which could also be purchased from Veri. Sign*, Comodo, or Starfield) and used for Remote Provisioning. The Root hash that issued this certificate can be found pre-configured in the Management Controller’s firmware that ships from the OEM. q Enter the password for this certificate (Pr 0 t 3 ct!0 n) and click OK Note: Zeros are used in the above password Note: If the password is incorrect, you will receive and Invalid Password message. If the certificate is not a valid Remote Configuration Certificate, you will receive an Invalid Certificate message. Intel Confidential 67

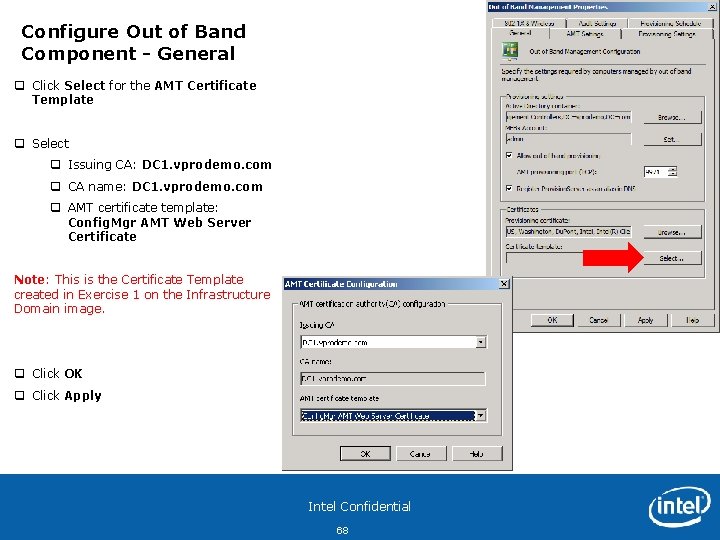
Configure Out of Band Component - General q Click Select for the AMT Certificate Template q Select q Issuing CA: DC 1. vprodemo. com q CA name: DC 1. vprodemo. com q AMT certificate template: Config. Mgr AMT Web Server Certificate Note: This is the Certificate Template created in Exercise 1 on the Infrastructure Domain image. q Click OK q Click Apply Intel Confidential 68

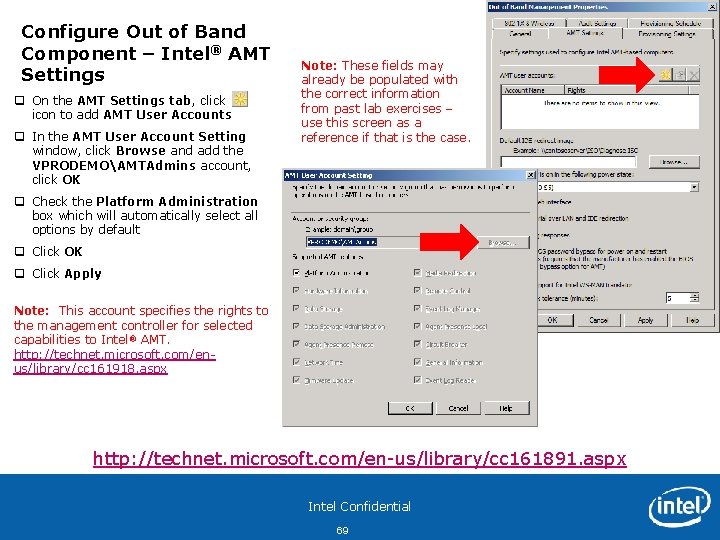
Configure Out of Band Component – Intel® AMT Settings q On the AMT Settings tab, click icon to add AMT User Accounts q In the AMT User Account Setting window, click Browse and add the VPRODEMOAMTAdmins account, click OK Note: These fields may already be populated with the correct information from past lab exercises – use this screen as a reference if that is the case. q Check the Platform Administration box which will automatically select all options by default q Click OK q Click Apply Note: This account specifies the rights to the management controller for selected capabilities to Intel® AMT. http: //technet. microsoft. com/enus/library/cc 161918. aspx http: //technet. microsoft. com/en-us/library/cc 161891. aspx Intel Confidential 69

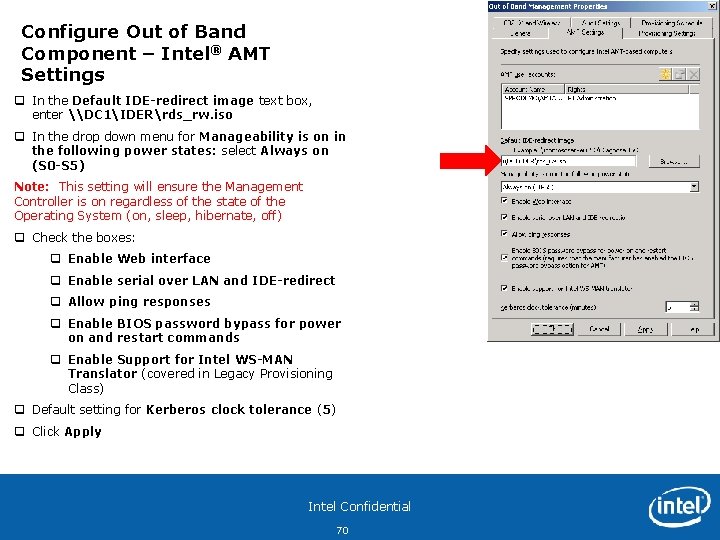
Configure Out of Band Component – Intel® AMT Settings q In the Default IDE-redirect image text box, enter \DC 1IDERrds_rw. iso q In the drop down menu for Manageability is on in the following power states: select Always on (S 0 -S 5) Note: This setting will ensure the Management Controller is on regardless of the state of the Operating System (on, sleep, hibernate, off) q Check the boxes: q Enable Web interface q Enable serial over LAN and IDE-redirect q Allow ping responses q Enable BIOS password bypass for power on and restart commands q Enable Support for Intel WS-MAN Translator (covered in Legacy Provisioning Class) q Default setting for Kerberos clock tolerance (5) q Click Apply Intel Confidential 70

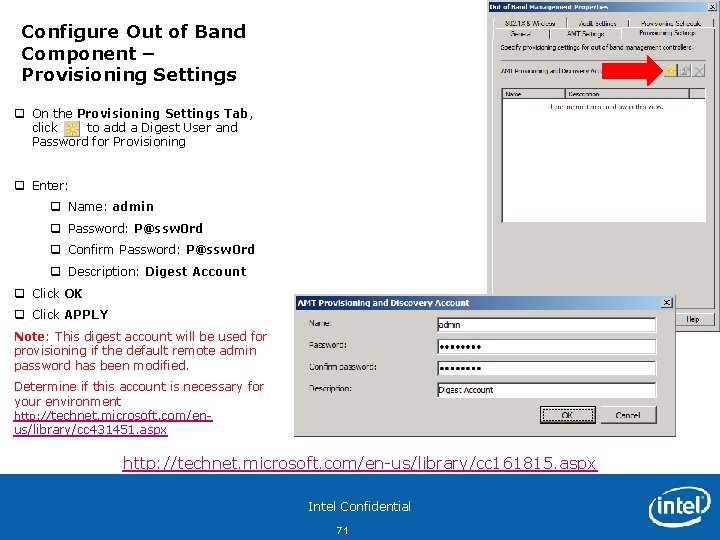
Configure Out of Band Component – Provisioning Settings q On the Provisioning Settings Tab, click to add a Digest User and Password for Provisioning q Enter: q Name: admin q Password: P@ssw 0 rd q Confirm Password: P@ssw 0 rd q Description: Digest Account q Click OK q Click APPLY Note: This digest account will be used for provisioning if the default remote admin password has been modified. Determine if this account is necessary for your environment http: //technet. microsoft. com/enus/library/cc 431451. aspx http: //technet. microsoft. com/en-us/library/cc 161815. aspx Intel Confidential 71

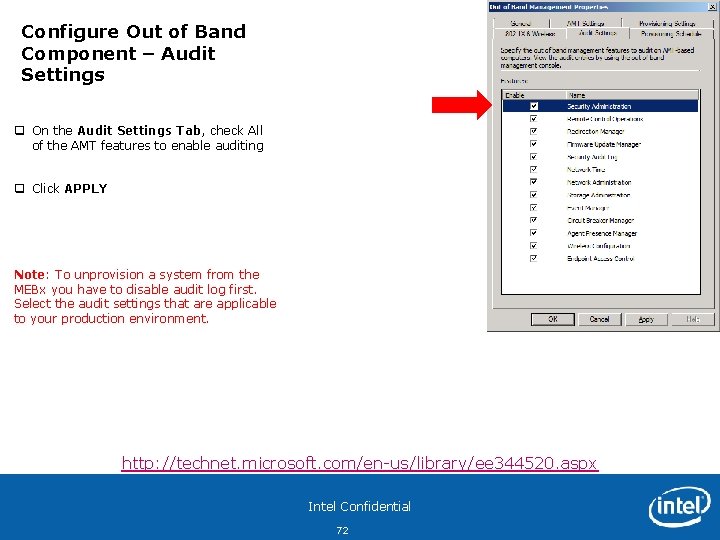
Configure Out of Band Component – Audit Settings q On the Audit Settings Tab, check All of the AMT features to enable auditing q Click APPLY Note: To unprovision a system from the MEBx you have to disable audit log first. Select the audit settings that are applicable to your production environment. http: //technet. microsoft. com/en-us/library/ee 344520. aspx Intel Confidential 72

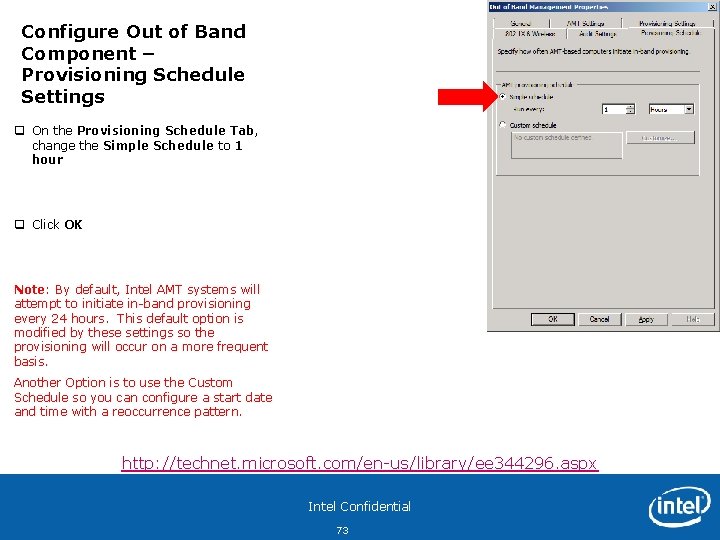
Configure Out of Band Component – Provisioning Schedule Settings q On the Provisioning Schedule Tab, change the Simple Schedule to 1 hour q Click OK Note: By default, Intel AMT systems will attempt to initiate in-band provisioning every 24 hours. This default option is modified by these settings so the provisioning will occur on a more frequent basis. Another Option is to use the Custom Schedule so you can configure a start date and time with a reoccurrence pattern. http: //technet. microsoft. com/en-us/library/ee 344296. aspx Intel Confidential 73

Lab Module 2. 1 Advanced Out of Band Configuration The following 2. 1 module is an advanced topic on 802. 1 x and Wireless Profiles Intel Confidential 74

802. 1 x and Wireless Profiles Requirements: http: //technet. microsoft. com/en-us/library/ee 344543. aspx • This section is for advanced v. Pro users that are familiar with 802. 1 x networking and RADIUS server for authentication – Wireless AP = Linksys Dual-Band Wireless N Gigabit router that supports 802. 1 x – There are many options available for wireless and 802. 1 x profiles and this training will only cover one set (refer to Microsoft Tech. Net for complete list of supported protocols) – The RADIUS Server (Microsoft NPS – Windows 2008 Server) has been Pre-Configured for training How to: http: //technet. microsoft. com/en-us/library/ee 344378. aspx Intel Confidential 75

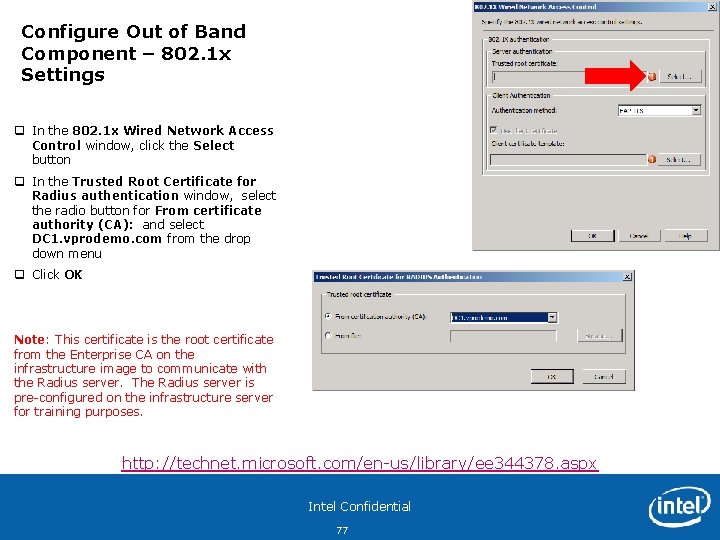
Configure Out of Band Component – 802. 1 x Settings q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Primary Site> Site Settings > Component Configuration q Right-click Out of band management component, and click Properties q On the 802. 1 x and Wireless Settings Tab, check the box for Enable 802. 1 x authentication for wired network and click Set Note: This setting will provision the v. Pro system with proper 802. 1 x credentials in order for the device to authenticate to a protected 802. 1 x network. The RADIUS server is pre-configured for this lab and steps to setup this RADIUS server is out of scope for this training module. http: //technet. microsoft. com/en-us/library/ee 344664. aspx Intel Confidential 76

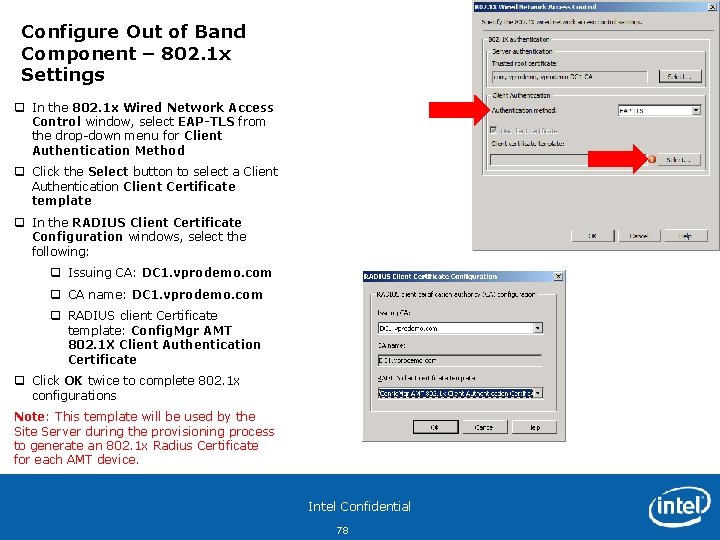
Configure Out of Band Component – 802. 1 x Settings q In the 802. 1 x Wired Network Access Control window, click the Select button q In the Trusted Root Certificate for Radius authentication window, select the radio button for From certificate authority (CA): and select DC 1. vprodemo. com from the drop down menu q Click OK Note: This certificate is the root certificate from the Enterprise CA on the infrastructure image to communicate with the Radius server. The Radius server is pre-configured on the infrastructure server for training purposes. http: //technet. microsoft. com/en-us/library/ee 344378. aspx Intel Confidential 77

Configure Out of Band Component – 802. 1 x Settings q In the 802. 1 x Wired Network Access Control window, select EAP-TLS from the drop-down menu for Client Authentication Method q Click the Select button to select a Client Authentication Client Certificate template q In the RADIUS Client Certificate Configuration windows, select the following: q Issuing CA: DC 1. vprodemo. com q CA name: DC 1. vprodemo. com q RADIUS client Certificate template: Config. Mgr AMT 802. 1 X Client Authentication Certificate q Click OK twice to complete 802. 1 x configurations Note: This template will be used by the Site Server during the provisioning process to generate an 802. 1 x Radius Certificate for each AMT device. Intel Confidential 78

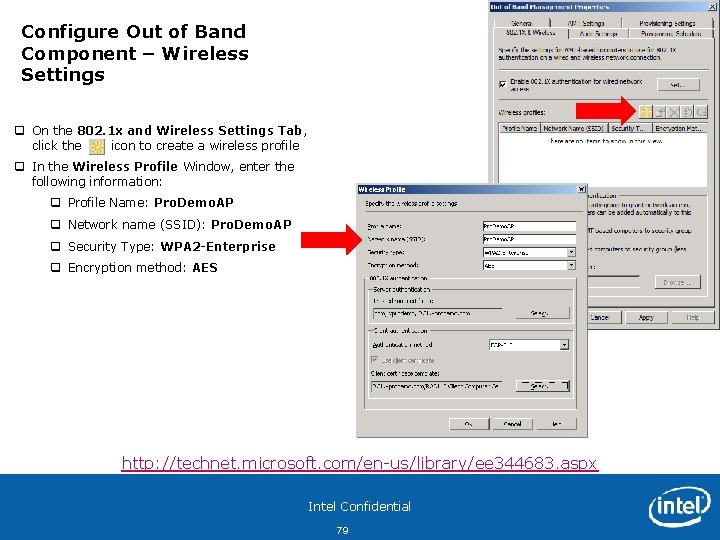
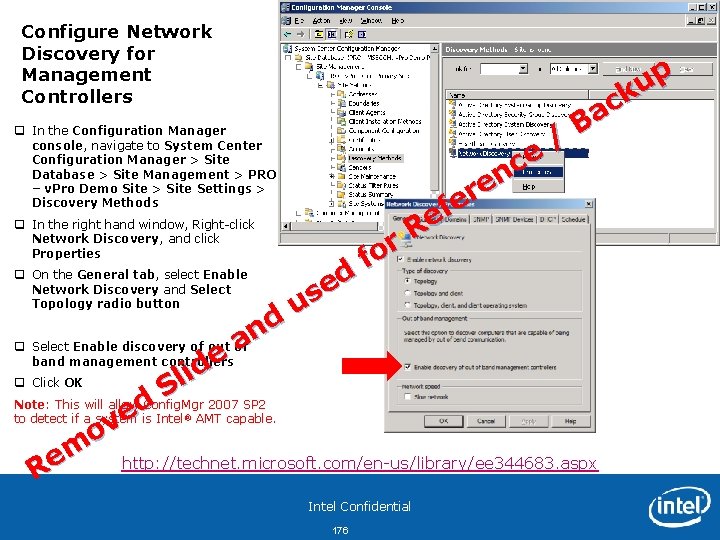
Configure Out of Band Component – Wireless Settings q On the 802. 1 x and Wireless Settings Tab, click the icon to create a wireless profile q In the Wireless Profile Window, enter the following information: q Profile Name: Pro. Demo. AP q Network name (SSID): Pro. Demo. AP q Security Type: WPA 2 -Enterprise q Encryption method: AES http: //technet. microsoft. com/en-us/library/ee 344683. aspx Intel Confidential 79

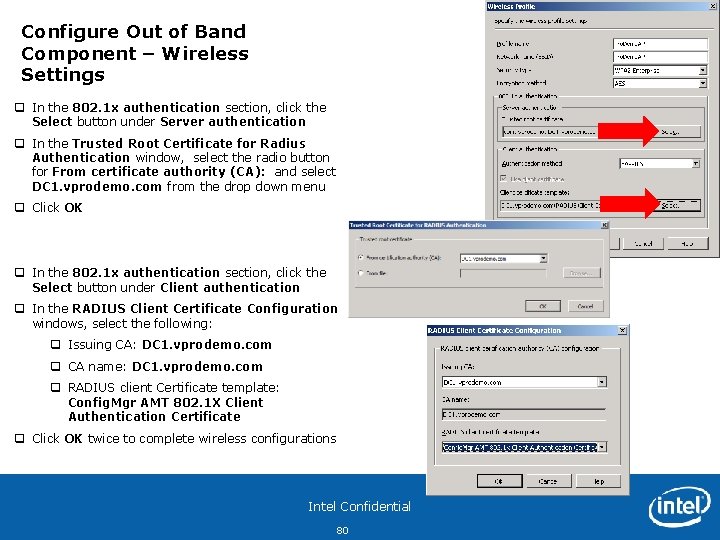
Configure Out of Band Component – Wireless Settings q In the 802. 1 x authentication section, click the Select button under Server authentication q In the Trusted Root Certificate for Radius Authentication window, select the radio button for From certificate authority (CA): and select DC 1. vprodemo. com from the drop down menu q Click OK q In the 802. 1 x authentication section, click the Select button under Client authentication q In the RADIUS Client Certificate Configuration windows, select the following: q Issuing CA: DC 1. vprodemo. com q CA name: DC 1. vprodemo. com q RADIUS client Certificate template: Config. Mgr AMT 802. 1 X Client Authentication Certificate q Click OK twice to complete wireless configurations Intel Confidential 80

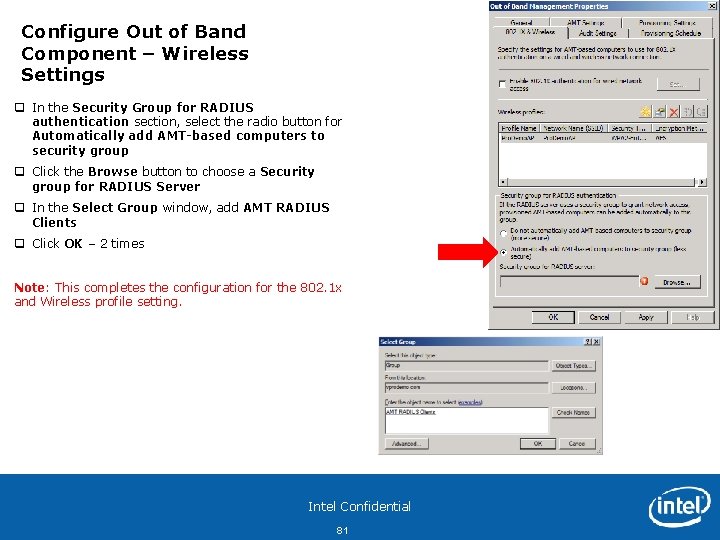
Configure Out of Band Component – Wireless Settings q In the Security Group for RADIUS authentication section, select the radio button for Automatically add AMT-based computers to security group q Click the Browse button to choose a Security group for RADIUS Server q In the Select Group window, add AMT RADIUS Clients q Click OK – 2 times Note: This completes the configuration for the 802. 1 x and Wireless profile setting. Intel Confidential 81

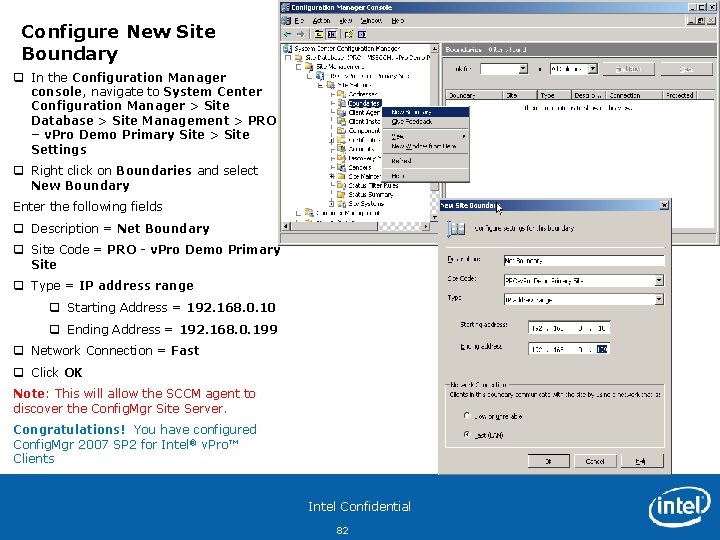
Configure New Site Boundary q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Primary Site > Site Settings q Right click on Boundaries and select New Boundary Enter the following fields q Description = Net Boundary q Site Code = PRO - v. Pro Demo Primary Site q Type = IP address range q Starting Address = 192. 168. 0. 10 q Ending Address = 192. 168. 0. 199 q Network Connection = Fast q Click OK Note: This will allow the SCCM agent to discover the Config. Mgr Site Server. Congratulations! You have configured Config. Mgr 2007 SP 2 for Intel® v. Pro™ Clients Intel Confidential 82

Lab 2 Exercise Review Installed OOB Service Component and configured Properties • Used to Configure General OOB Properties and Intel® AMT Client Profile • http: //technet. microsoft. com/en-us/library/cc 161960. aspx • Configured General Tab • Provisioning Settings - Active Directory container • Stores Intel AMT Objects • Select AD Container previously created: Out of Band Management Controllers • Provisioning Settings – Intel® MEBx Account • What to set the Intel MEBx Password (if not already set) and remote admin account to during Provisioning • Register Provision. Server as an alias in DNS (used for PKI/PSK (Bare Metal) hello packet routing to OOB Service Point) • Certificate – Provisioning Certificate • PKI / Remote Configuration Certificate • Configure with certificate exported during Enterprise CA & Provision Certificate configuration • Certificate – Certificate Template • Configure with template created during Enterprise CA & Provision Certificate configuration: Config. Mgr AMT Web Server Certificate and RADIUS Certificate http: //technet. microsoft. com/en-us/library/cc 161833. aspx Intel Confidential 83

Lab 2 Exercise Review • Configured Intel® AMT Settings Tab • Intel AMT User Accounts • Allows you to define Kerberos user who can invoke Intel AMT features • Define which accounts have which Intel AMT realm permissions • Default IDE-redirect image • Default location of image files • Manageability Power States • Sets power state for when you want to manage the AMT-based computer out of band (S 0 – S 5) • Enable Web interface • Enables / Disables Intel AMT web interface for provisioned Intel AMT clients • Enable Serial Over LAN and IDE redirection • Enables / Disables SOL and IDER for provisioned Intel AMT clients • Allow ping responses • Enables / Disables ping responses for provisioned Intel AMT clients • Enable support for Intel® WS-MAN translator • Enables support within Config. Mgr 2007 SP 2 to forward Provisioning and Intel AMT operation command to the Intel WS-MAN Translator firmware less than 3. 2. 1 • http: //technet. microsoft. com/en-us/library/cc 161891. aspx Intel Confidential 84

Lab 2 Exercise Review • Configured Provisioning Settings Tab • Add Provisioning and Discovery Accounts • Allows you to define additional Digest accounts that can be used to provision and discover AMT systems if the standard default account has been modified • http: //technet. microsoft. com/en-us/library/cc 161815. aspx • Configured 802. 1 X and Wireless Tab • Created wired and wireless profiles to be added to AMT during the provisioning process to allow AMT to authenticate to an 802. 1 x protected network • Automatically added AMT devices to a security group for RADIUS authentication • http: //technet. microsoft. com/en-us/library/ee 344664. aspx • Configured Audit Settings Tab • Enabled the features to be audited by AMT • http: //technet. microsoft. com/en-us/library/ee 344520. aspx • Configured Provisioning Schedule Tab • Specified a specific schedule for AMT systems to initiate provisioning • http: //technet. microsoft. com/en-us/library/ee 344296. aspx • Configured Site Boundary for Agent discovery • http: //technet. microsoft. com/en-us/library/bb 693530. aspx Intel Confidential 85

Lab Module 3 Configuration Manager 2007 SP 2 Collections and In-Band Provisioning Intel Confidential 86

Config. Mgr 2007 SP 2 Agent Installation and In. Band Provisioning • In this exercise, you will – Install the Config. Mgr 2007 SP 2 Client Agent on an Intel® v. Pro™ system (e. g. Intel v. Pro Laptop/Desktop) – Create an Unprovisioned v. Pro Client Collection to place discovered Unprovisioned systems and enable the autoprovisioning policy on this collection – Initiate an In. Band remote configuration provisioning of an Intel v. Pro system with native Config. Mgr 2007 SP 2 support – NOTE: Bare Metal / Out-of-Band provisioning (No OS or SCCM Client) is supported but not covered in this training) – for information on this process see: SCCM Out of Band Provisioning (Bare Metal Provisioning) Intel Confidential 87

Agent Based Provisioning Process 1. Based on policy, the Configuration Manager Agent will assess if the Client can be provisioned, . If I can, it will create a One Time Password and send the OTP to both the OOB Service and into the Intel® AMT Firmware 2. OOB Service Point secures connection with the Intel AMT client through Embedded AMT Self Sign Certificate, Present Provisioning Certificate along with the OTP for initial Authentication 3. OOB Service Point sets et Remote Admin and Intel® MEBX password (if not changed) 4. OOB Service Point requests a web server certificate on behalf of the Intel AMT client 5. OOB Service Point created an Object in AD for the Intel® v. Pro™ Client 6. OOB Service Point pushes web server certificate to Intel AMT client 7. OOB Service Point pushes ACL, power schema, and other configuration data to Intel AMT to finalize provision http: //technet. microsoft. com/en-us/library/cc 431371. aspx Intel Confidential 88

Install Config. Mgr 2007 SP 2 Client Agent on local system q Login to the Intel® v. Pro™ Laptop q User: ITproadmin q Password: P@ssw 0 rd q Domain: VPRODEMO q Once logged into the Intel® v. Pro™ client, map a drive to \mssccmc$ q Go to Program FilesMicrosoft Configuration ManagerClient q In the Client folder, double click ccmsetup. exe Note: This will install the SCCM SP 2 client from you SCCM Site server. This Intel v. Pro system must be joined to the infrastructure domain – Prior to the client setup. http: //technet. microsoft. com/en-us/library/bb 693546. aspx Intel Confidential 89

Monitor Config. Mgr 2007 SP 2 Client Agent Install q Track the setup by monitoring the Process ccmsetup. exe in Task Manager q Installation is complete once the Ccm. Exec. exe process is running in Task Manager q You can track the agent installation on the client in c: windowssystem 32ccmsetupccm setup. log (for Vista 64 bit file is located in c: windowsSys. WOW 64CCM) Note: Once the installation is complete, you will see Ccm. Exec Service running in Task Manager. A reboot of the v. Pro system will help speed up the SCCM agent to check in with the Site Server. Intel Confidential 90

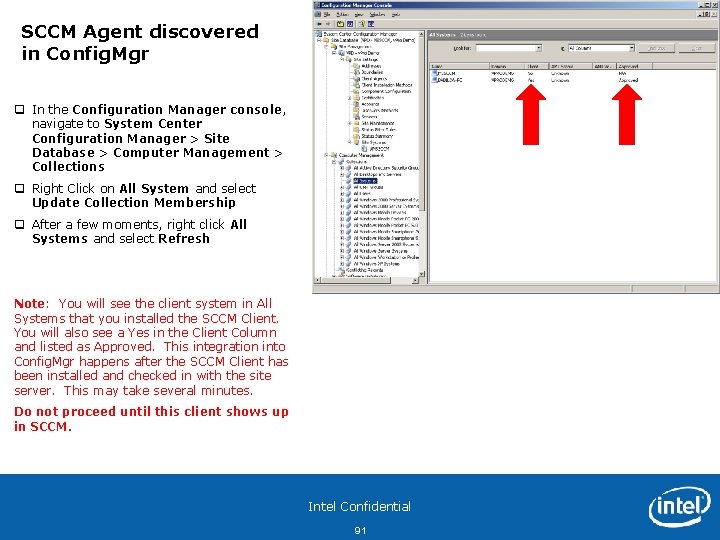
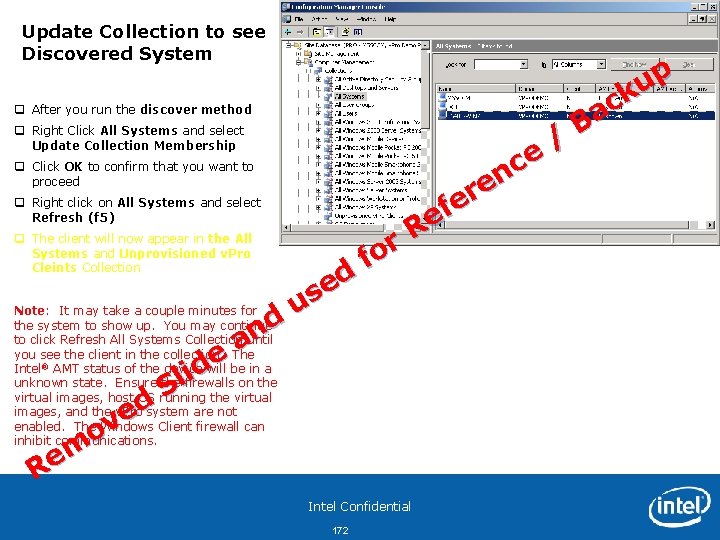
SCCM Agent discovered in Config. Mgr q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections q Right Click on All System and select Update Collection Membership q After a few moments, right click All Systems and select Refresh Note: You will see the client system in All Systems that you installed the SCCM Client. You will also see a Yes in the Client Column and listed as Approved. This integration into Config. Mgr happens after the SCCM Client has been installed and checked in with the site server. This may take several minutes. Do not proceed until this client shows up in SCCM. Intel Confidential 91

Configuration Manager 2007 SP 2 Collection Configuration for Automatic Provisioning of Management Controllers Intel Confidential 92

Collection Configuration • In this exercise, you will – Create an Intel® AMT Collection to group Intel AMT systems that are AMT Capable and unprovisioned – Configure an Intel AMT Collection to automatically provision Out of Band Management Controllers Intel Confidential 93

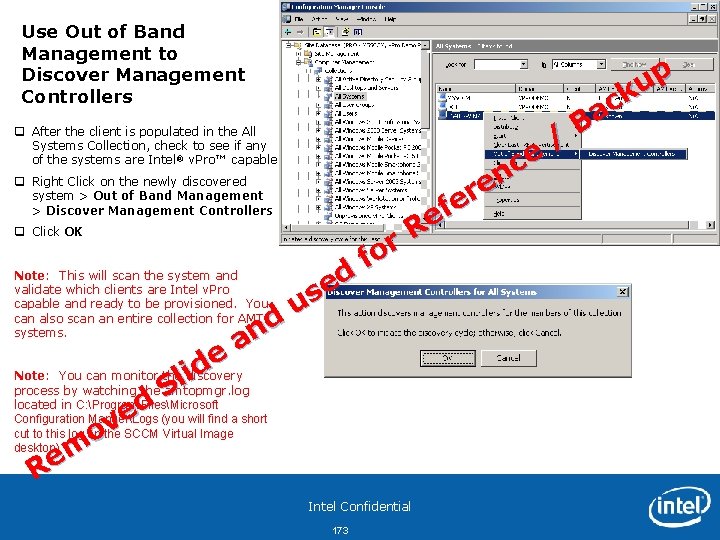
Agent Based Provisioning Configuration Overview • To provision via the Config. Mgr 2007 SP 2 Client Agent, you must configure Config. Mgr 2007 SP 2 to allow agent integration • Requirements for Agent • Prerequisites for Configuration Manager Client Deployment • http: //technet. microsoft. com/en-us/library/bb 680537. aspx • Configure Collection for Automatic Provisioning • Recommend Collection Created for “Unprovisioned v. Pro Clients” • Create Collection Membership Rules based on Intel® AMT Hardware Inventory • http: //technet. microsoft. com/en-us/library/cc 431387. aspx • Ensure “Enable Automatic out of band management controller provisioning” checked in Collection Name Settings: Out of Band Tab for Collection • http: //technet. microsoft. com/en-us/library/cc 161955. aspx • Install Config. Mgr 2007 SP 2 client on Intel AMT Client • http: //technet. microsoft. com/en-us/library/bb 632762. aspx Intel Confidential 94

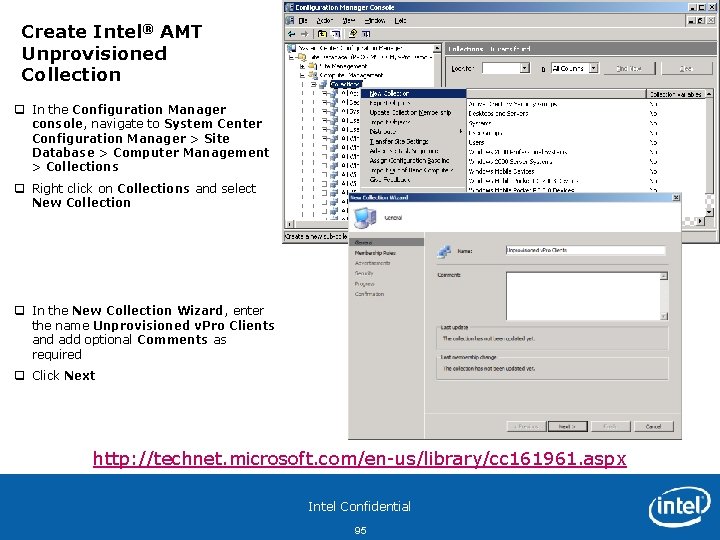
Create Intel® AMT Unprovisioned Collection q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections q Right click on Collections and select New Collection q In the New Collection Wizard, enter the name Unprovisioned v. Pro Clients and add optional Comments as required q Click Next http: //technet. microsoft. com/en-us/library/cc 161961. aspx Intel Confidential 95

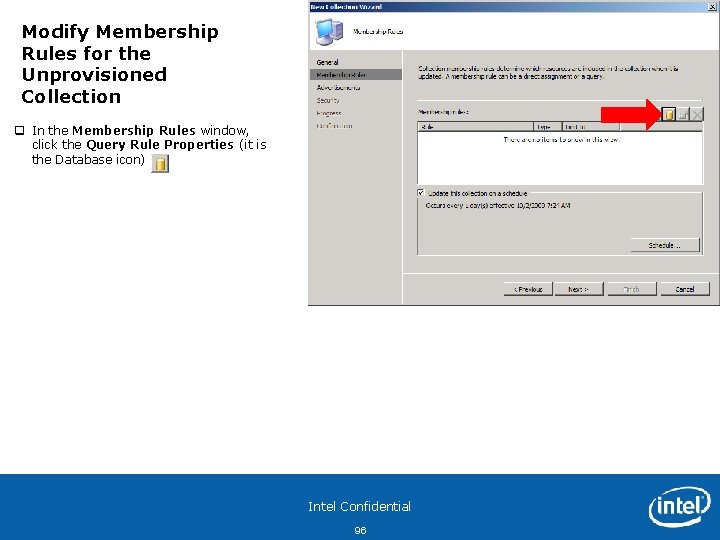
Modify Membership Rules for the Unprovisioned Collection q In the Membership Rules window, click the Query Rule Properties (it is the Database icon) Intel Confidential 96

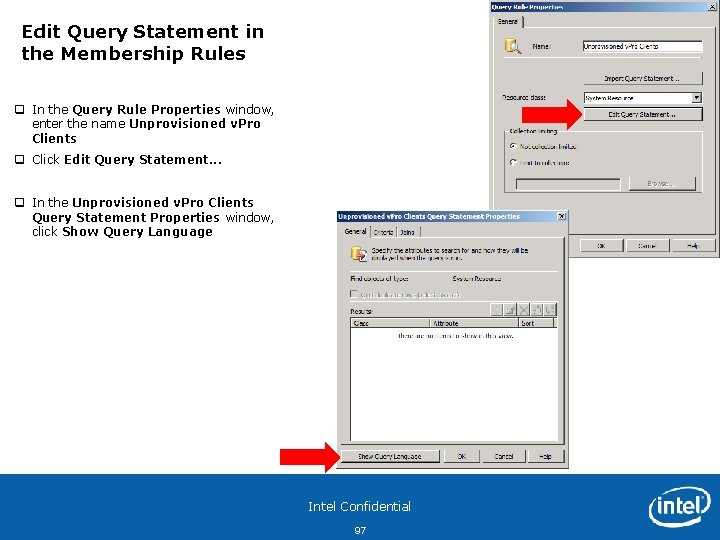
Edit Query Statement in the Membership Rules q In the Query Rule Properties window, enter the name Unprovisioned v. Pro Clients q Click Edit Query Statement. . . q In the Unprovisioned v. Pro Clients Query Statement Properties window, click Show Query Language Intel Confidential 97

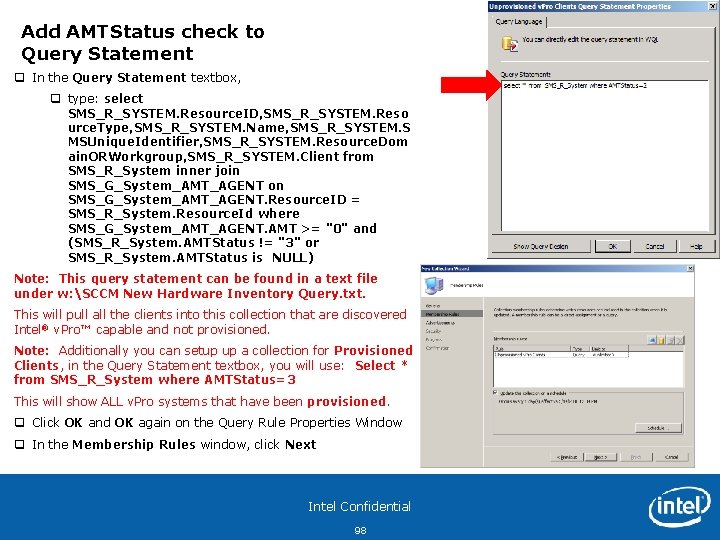
Add AMTStatus check to Query Statement q In the Query Statement textbox, q type: select SMS_R_SYSTEM. Resource. ID, SMS_R_SYSTEM. Reso urce. Type, SMS_R_SYSTEM. Name, SMS_R_SYSTEM. S MSUnique. Identifier, SMS_R_SYSTEM. Resource. Dom ain. ORWorkgroup, SMS_R_SYSTEM. Client from SMS_R_System inner join SMS_G_System_AMT_AGENT on SMS_G_System_AMT_AGENT. Resource. ID = SMS_R_System. Resource. Id where SMS_G_System_AMT_AGENT. AMT >= "0" and (SMS_R_System. AMTStatus != "3" or SMS_R_System. AMTStatus is NULL) Note: This query statement can be found in a text file under w: SCCM New Hardware Inventory Query. txt. This will pull all the clients into this collection that are discovered Intel® v. Pro™ capable and not provisioned. Note: Additionally you can setup up a collection for Provisioned Clients, in the Query Statement textbox, you will use: Select * from SMS_R_System where AMTStatus=3 This will show ALL v. Pro systems that have been provisioned. q Click OK and OK again on the Query Rule Properties Window q In the Membership Rules window, click Next Intel Confidential 98

Create Intel® AMT Unprovisioned Collection q In the Advertisements window, click Next Intel Confidential 99

Create Intel® AMT Unprovisioned Collection q In the Security window, add any appropriate users or groups and click Next (keep defaults for this exercise) q In the Confirmation window, click Close Note: Optional step - Repeat foils to create a collection for Provisioned v. Pro Clients. See note on foil 98 for Select * from SMS_R_System where AMTStatus=3 Intel Confidential 100

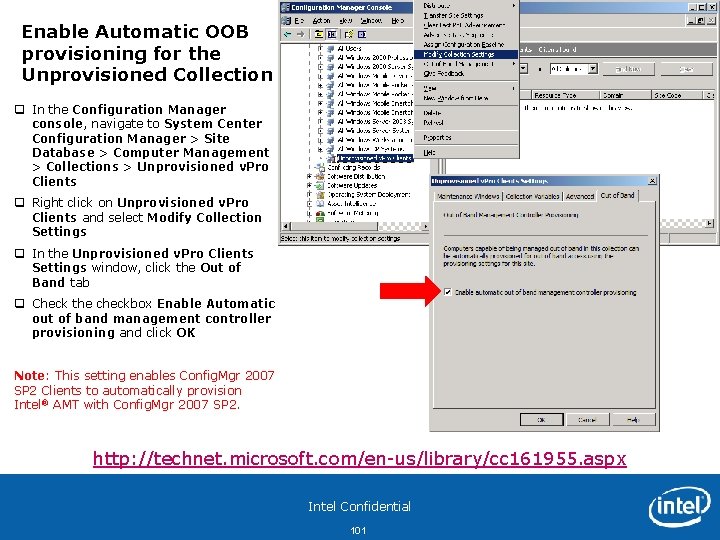
Enable Automatic OOB provisioning for the Unprovisioned Collection q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections > Unprovisioned v. Pro Clients q Right click on Unprovisioned v. Pro Clients and select Modify Collection Settings q In the Unprovisioned v. Pro Clients Settings window, click the Out of Band tab q Check the checkbox Enable Automatic out of band management controller provisioning and click OK Note: This setting enables Config. Mgr 2007 SP 2 Clients to automatically provision Intel® AMT with Config. Mgr 2007 SP 2. http: //technet. microsoft. com/en-us/library/cc 161955. aspx Intel Confidential 101

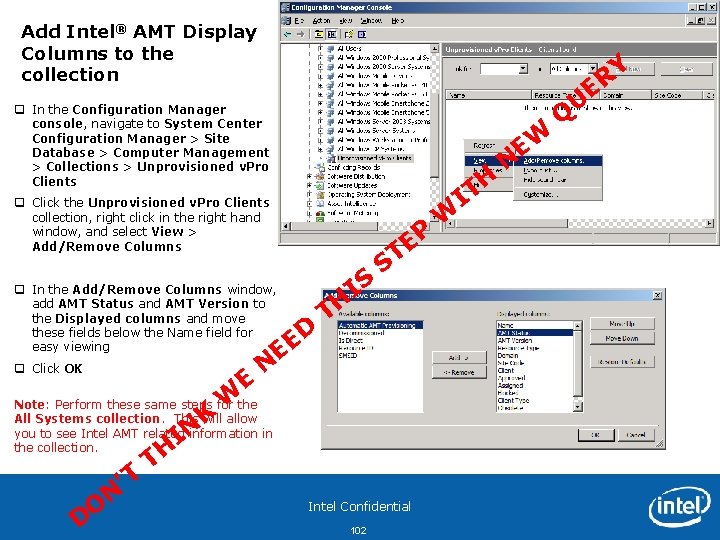
Add Intel® AMT Display Columns to the collection U q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections > Unprovisioned v. Pro Clients EW q Click the Unprovisioned v. Pro Clients collection, right click in the right hand window, and select View > Add/Remove Columns q In the Add/Remove Columns window, add AMT Status and AMT Version to the Displayed columns and move these fields below the Name field for easy viewing q Click OK W E IS D E E N P E T S TH Note: Perform these same steps for the All Systems collection. This will allow you to see Intel AMT related information in the collection. D O ’T N IN TH K ER Intel Confidential 102 W H T I N Q Y

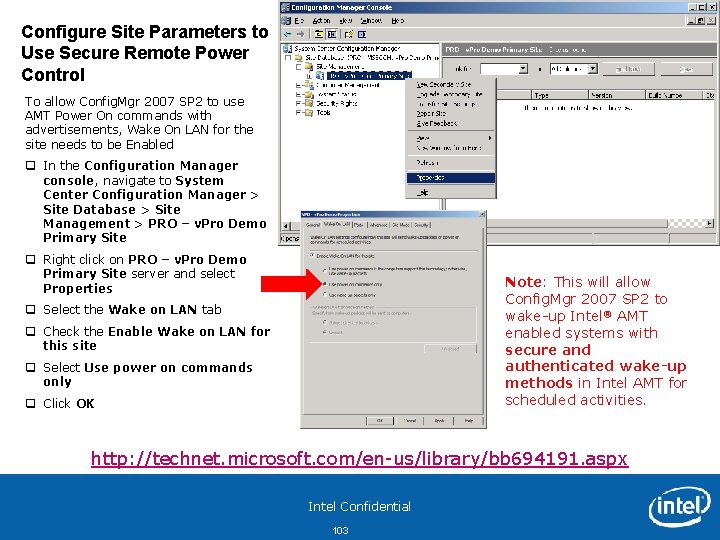
Configure Site Parameters to Use Secure Remote Power Control To allow Config. Mgr 2007 SP 2 to use AMT Power On commands with advertisements, Wake On LAN for the site needs to be Enabled q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Primary Site q Right click on PRO – v. Pro Demo Primary Site server and select Properties Note: This will allow Config. Mgr 2007 SP 2 to wake-up Intel® AMT enabled systems with secure and authenticated wake-up methods in Intel AMT for scheduled activities. q Select the Wake on LAN tab q Check the Enable Wake on LAN for this site q Select Use power on commands only q Click OK http: //technet. microsoft. com/en-us/library/bb 694191. aspx Intel Confidential 103

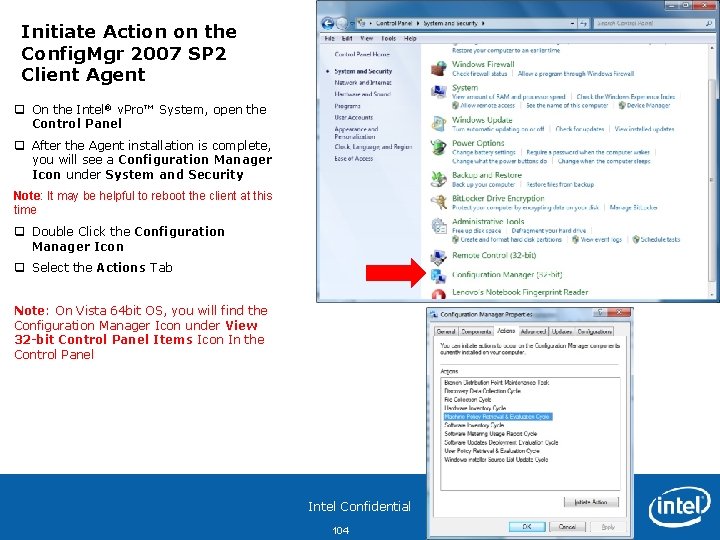
Initiate Action on the Config. Mgr 2007 SP 2 Client Agent q On the Intel® v. Pro™ System, open the Control Panel q After the Agent installation is complete, you will see a Configuration Manager Icon under System and Security Note: It may be helpful to reboot the client at this time q Double Click the Configuration Manager Icon q Select the Actions Tab Note: On Vista 64 bit OS, you will find the Configuration Manager Icon under View 32 -bit Control Panel Items Icon In the Control Panel Intel Confidential 104

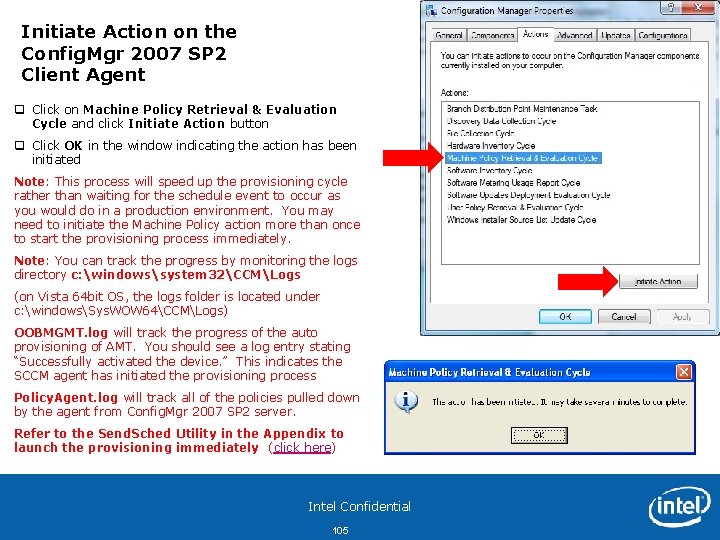
Initiate Action on the Config. Mgr 2007 SP 2 Client Agent q Click on Machine Policy Retrieval & Evaluation Cycle and click Initiate Action button q Click OK in the window indicating the action has been initiated Note: This process will speed up the provisioning cycle rather than waiting for the schedule event to occur as you would do in a production environment. You may need to initiate the Machine Policy action more than once to start the provisioning process immediately. Note: You can track the progress by monitoring the logs directory c: windowssystem 32CCMLogs (on Vista 64 bit OS, the logs folder is located under c: windowsSys. WOW 64CCMLogs) OOBMGMT. log will track the progress of the auto provisioning of AMT. You should see a log entry stating “Successfully activated the device. ” This indicates the SCCM agent has initiated the provisioning process Policy. Agent. log will track all of the policies pulled down by the agent from Config. Mgr 2007 SP 2 server. Refer to the Send. Sched Utility in the Appendix to launch the provisioning immediately (click here) Intel Confidential 105

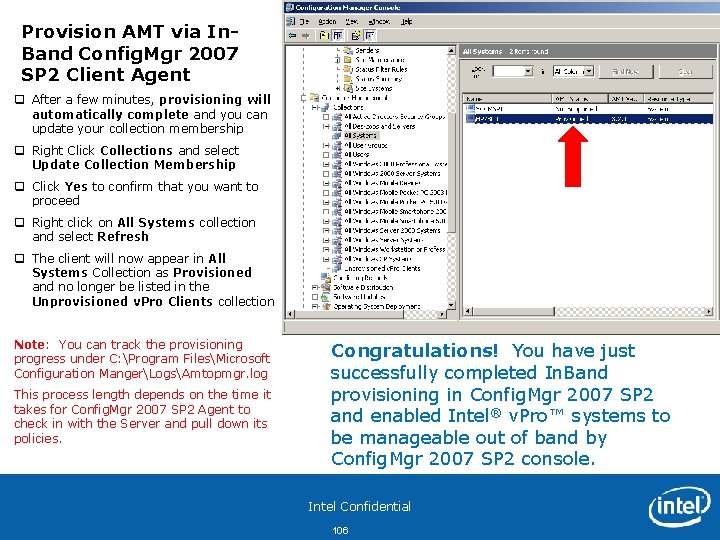
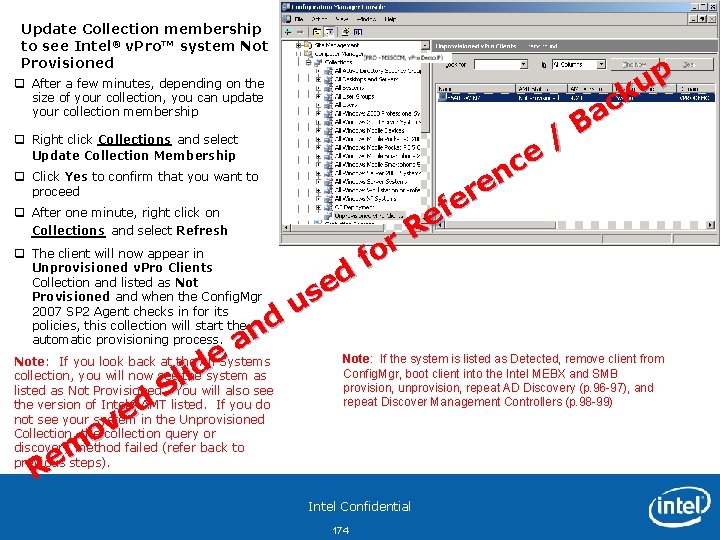
Provision AMT via In. Band Config. Mgr 2007 SP 2 Client Agent q After a few minutes, provisioning will automatically complete and you can update your collection membership q Right Click Collections and select Update Collection Membership q Click Yes to confirm that you want to proceed q Right click on All Systems collection and select Refresh q The client will now appear in All Systems Collection as Provisioned and no longer be listed in the Unprovisioned v. Pro Clients collection Note: You can track the provisioning progress under C: Program FilesMicrosoft Configuration MangerLogsAmtopmgr. log This process length depends on the time it takes for Config. Mgr 2007 SP 2 Agent to check in with the Server and pull down its policies. Congratulations! You have just successfully completed In. Band provisioning in Config. Mgr 2007 SP 2 and enabled Intel® v. Pro™ systems to be manageable out of band by Config. Mgr 2007 SP 2 console. Intel Confidential 106

Lab Module 3 Review • • Installed the SCCM Client Agent on the Intel v. Pro system Created Intel® AMT Unprovisioned Collection Modify Membership Rules for the Unprovisioned Collection Added AMT Hardware Inventory check to Query Statement Enabled Automatic OOB provisioning on the Collection Added Intel AMT Display Columns to the collections Configured Site Parameters to Use Secure Remote Power Control (used in Real World Use Cases module) • Initiated an In. Band agent based provisioning • Updated Collections to see Provisioned AMT System Intel Confidential 107

Lab Module 4 Configuration Manger 2007 SP 2 Out of Band Management Console Intel Confidential 108

Using the Out Of Band Management Console in Config. Mgr 2007 SP 2 to manage Intel® v. Pro™ Systems Intel Confidential 109

Config. Mgr 2007 SP 2 OOB Mgt Console • The following screen captures show the Config. Mgr 2007 SP 2 OOB console interfaces for each of the OOB management capabilities. http: //technet. microsoft. com/en-us/library/cc 161766. aspx Intel Confidential 110

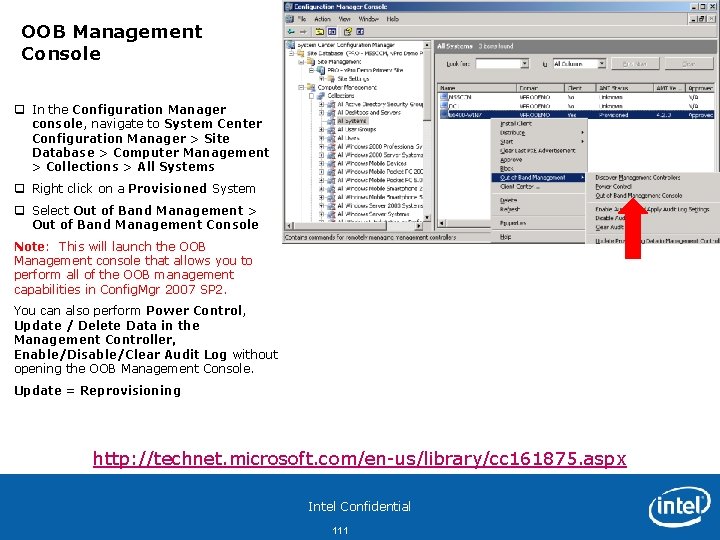
OOB Management Console q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections > All Systems q Right click on a Provisioned System q Select Out of Band Management > Out of Band Management Console Note: This will launch the OOB Management console that allows you to perform all of the OOB management capabilities in Config. Mgr 2007 SP 2. You can also perform Power Control, Update / Delete Data in the Management Controller, Enable/Disable/Clear Audit Log without opening the OOB Management Console. Update = Reprovisioning http: //technet. microsoft. com/en-us/library/cc 161875. aspx Intel Confidential 111

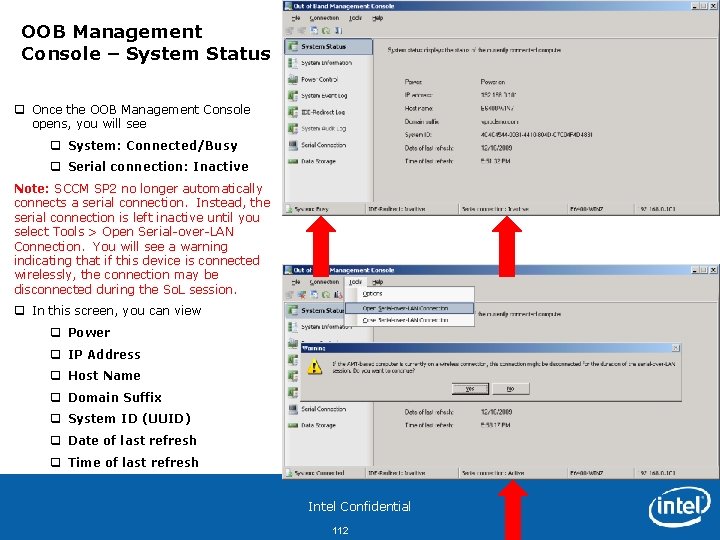
OOB Management Console – System Status q Once the OOB Management Console opens, you will see q System: Connected/Busy q Serial connection: Inactive Note: SCCM SP 2 no longer automatically connects a serial connection. Instead, the serial connection is left inactive until you select Tools > Open Serial-over-LAN Connection. You will see a warning indicating that if this device is connected wirelessly, the connection may be disconnected during the So. L session. q In this screen, you can view q Power q IP Address q Host Name q Domain Suffix q System ID (UUID) q Date of last refresh q Time of last refresh Intel Confidential 112

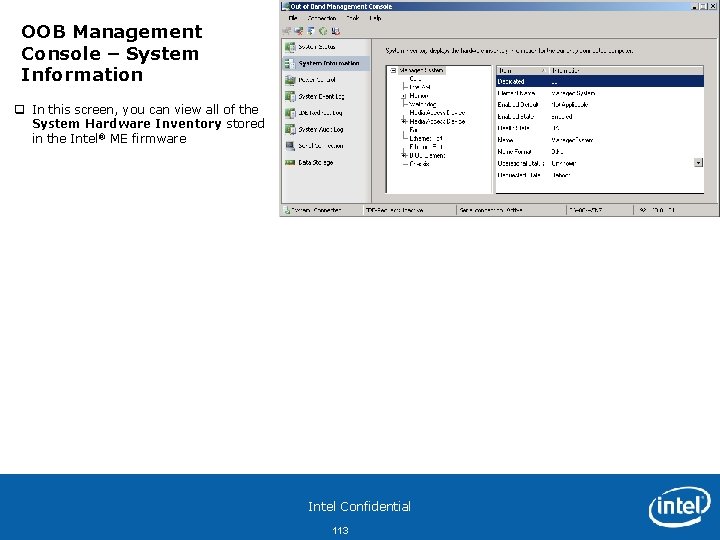
OOB Management Console – System Information q In this screen, you can view all of the System Hardware Inventory stored in the Intel® ME firmware Intel Confidential 113

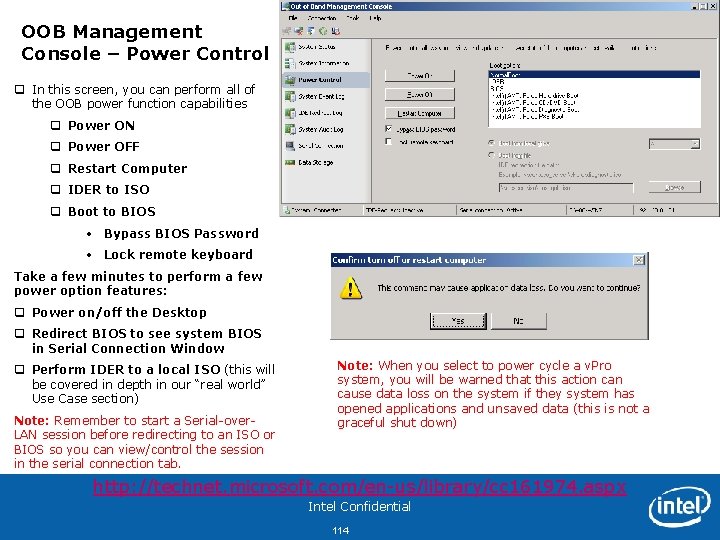
OOB Management Console – Power Control q In this screen, you can perform all of the OOB power function capabilities q Power ON q Power OFF q Restart Computer q IDER to ISO q Boot to BIOS • Bypass BIOS Password • Lock remote keyboard Take a few minutes to perform a few power option features: q Power on/off the Desktop q Redirect BIOS to see system BIOS in Serial Connection Window q Perform IDER to a local ISO (this will be covered in depth in our “real world” Use Case section) Note: Remember to start a Serial-over. LAN session before redirecting to an ISO or BIOS so you can view/control the session in the serial connection tab. Note: When you select to power cycle a v. Pro system, you will be warned that this action cause data loss on the system if they system has opened applications and unsaved data (this is not a graceful shut down) http: //technet. microsoft. com/en-us/library/cc 161974. aspx Intel Confidential 114

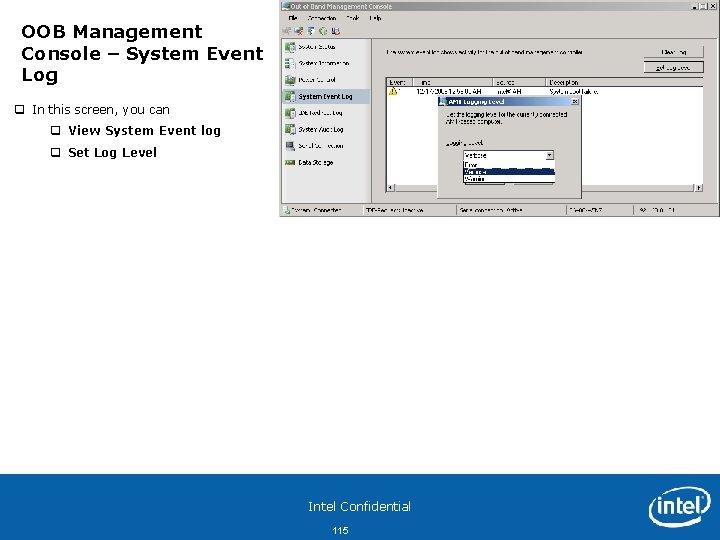
OOB Management Console – System Event Log q In this screen, you can q View System Event log q Set Log Level Intel Confidential 115

OOB Management Console – IDE-Redirect Log q In this screen, you can view the IDERedirect log Intel Confidential 116

OOB Management Console – System Audit Log q In this screen, you can view the System Audit log and can Export this information to a file http: //technet. microsoft. com/en-us/library/ee 344294. aspx Intel Confidential 117

OOB Management Console – Serial Connection q In this screen, you can view and control the Serial Connection of the remote screen (e. g. Bios or DOS based ISO image) Intel Confidential 118

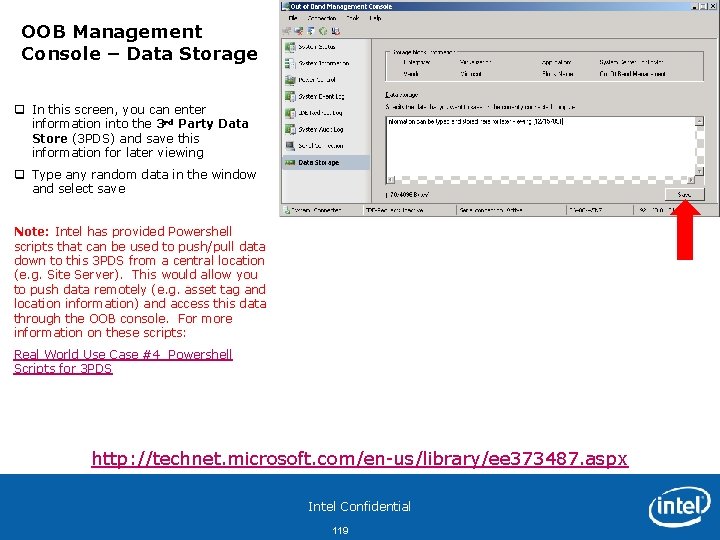
OOB Management Console – Data Storage q In this screen, you can enter information into the 3 rd Party Data Store (3 PDS) and save this information for later viewing q Type any random data in the window and select save Note: Intel has provided Powershell scripts that can be used to push/pull data down to this 3 PDS from a central location (e. g. Site Server). This would allow you to push data remotely (e. g. asset tag and location information) and access this data through the OOB console. For more information on these scripts: Real World Use Case #4 Powershell Scripts for 3 PDS http: //technet. microsoft. com/en-us/library/ee 373487. aspx Intel Confidential 119

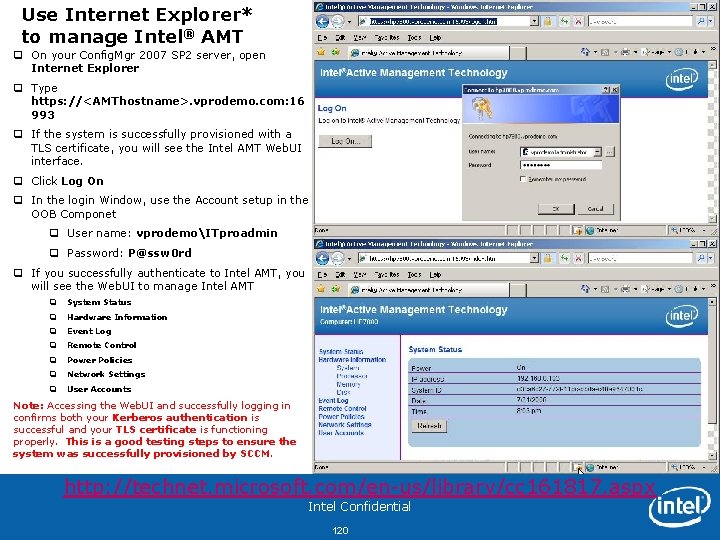
Use Internet Explorer* to manage Intel® AMT q On your Config. Mgr 2007 SP 2 server, open Internet Explorer q Type https: //<AMThostname>. vprodemo. com: 16 993 q If the system is successfully provisioned with a TLS certificate, you will see the Intel AMT Web. UI interface. q Click Log On q In the login Window, use the Account setup in the OOB Componet q User name: vprodemoITproadmin q Password: P@ssw 0 rd q If you successfully authenticate to Intel AMT, you will see the Web. UI to manage Intel AMT q System Status q Hardware Information q Event Log q Remote Control q Power Policies q Network Settings q User Accounts Note: Accessing the Web. UI and successfully logging in confirms both your Kerberos authentication is successful and your TLS certificate is functioning properly. This is a good testing steps to ensure the system was successfully provisioned by SCCM. http: //technet. microsoft. com/en-us/library/cc 161817. aspx Intel Confidential 120

Lab Module 4 Review • The Out of Band Management Console is the Config. Mgr 2007 SP 2 interface to perform Out of Band Management Features – Power Up/Down – Restart – Boot to BIOS – Redirect to an ISO – Hardware Inventory – System Information • You can also perform Power Up/Down and Management Controller reprovisioning/delete from within Config. Mgr 2007 SP 2 directly • Use the Web Interface in IE to manage Intel® AMT Systems Intel Confidential 121

Lab Module 5 Real World Use Cases for Intel v. Pro Systems with SCCM SP 2 Intel Confidential 122

Real World Use Cases • The following “Real World” Use Cases have been developed to help customers with drop-in solutions that will enable them to gain immediate value with Intel® v. Pro™ and SCCM within a production environment – Wake On Advertisements – Remote KVM – Remote Drive Share – Powershell Scripts for 3 PDS http: //communities. intel. com/docs/DOC-4080 Intel Confidential 123

Real World Use Case #1 Intel Wake-On Advertisement Intel Confidential 124

Using Intel® AMT Power Options to wake up a system with a SCCM Advertisement • When creating software distribution in Config. Mgr 2007 SP 2, you can leverage Intel AMT power options to wake up system (e. g. after hour patching scenarios). • Make sure your v. Pro Client is Powered Off for the next exercise. Intel Confidential 125

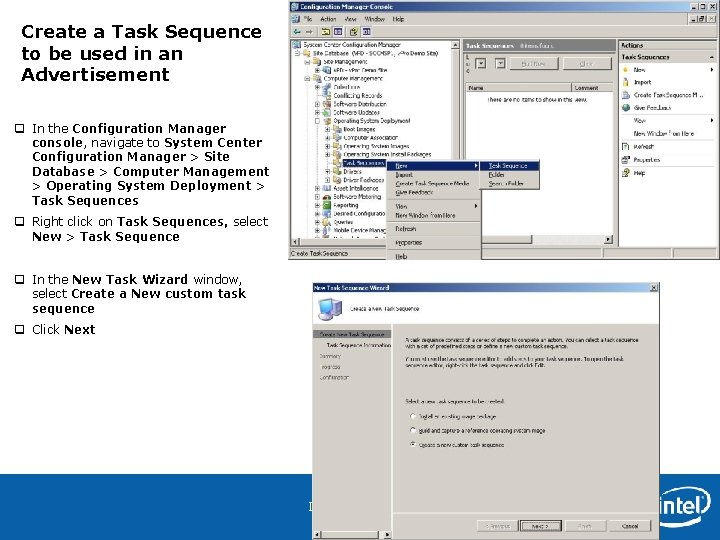
Create a Task Sequence to be used in an Advertisement q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Operating System Deployment > Task Sequences q Right click on Task Sequences, select New > Task Sequence q In the New Task Wizard window, select Create a New custom task sequence q Click Next Intel Confidential 126

Create a Task Sequence to be used in an Advertisement q In Task Sequence Information, Enter in Task Sequence Name: Just Shutdown and add appropriate Comments q Click Next q Confirm information in the Summary and click Next q Once the Wizard completes, click Close Intel Confidential 127

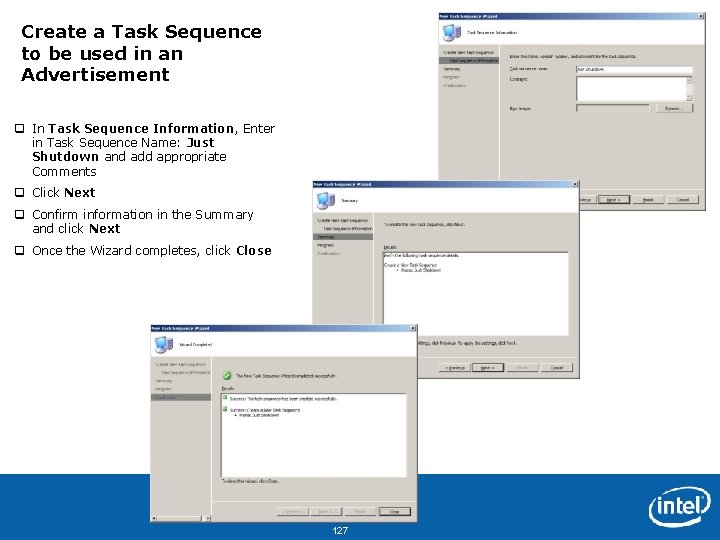
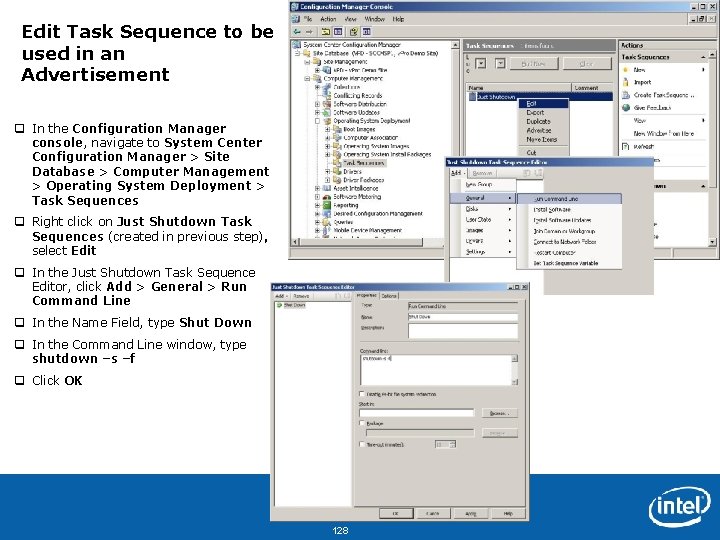
Edit Task Sequence to be used in an Advertisement q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Operating System Deployment > Task Sequences q Right click on Just Shutdown Task Sequences (created in previous step), select Edit q In the Just Shutdown Task Sequence Editor, click Add > General > Run Command Line q In the Name Field, type Shut Down q In the Command Line window, type shutdown –s –f q Click OK Intel Confidential 128

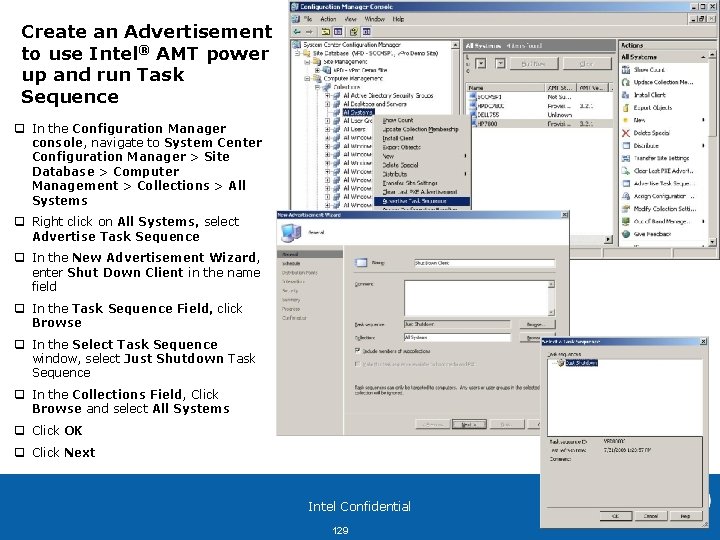
Create an Advertisement to use Intel® AMT power up and run Task Sequence q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections > All Systems q Right click on All Systems, select Advertise Task Sequence q In the New Advertisement Wizard, enter Shut Down Client in the name field q In the Task Sequence Field, click Browse q In the Select Task Sequence window, select Just Shutdown Task Sequence q In the Collections Field, Click Browse and select All Systems q Click OK q Click Next Intel Confidential 129

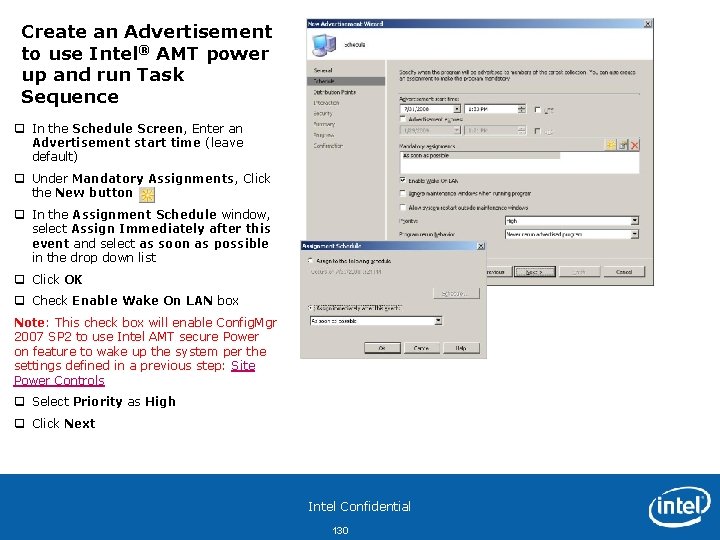
Create an Advertisement to use Intel® AMT power up and run Task Sequence q In the Schedule Screen, Enter an Advertisement start time (leave default) q Under Mandatory Assignments, Click the New button q In the Assignment Schedule window, select Assign Immediately after this event and select as soon as possible in the drop down list q Click OK q Check Enable Wake On LAN box Note: This check box will enable Config. Mgr 2007 SP 2 to use Intel AMT secure Power on feature to wake up the system per the settings defined in a previous step: Site Power Controls q Select Priority as High q Click Next Intel Confidential 130

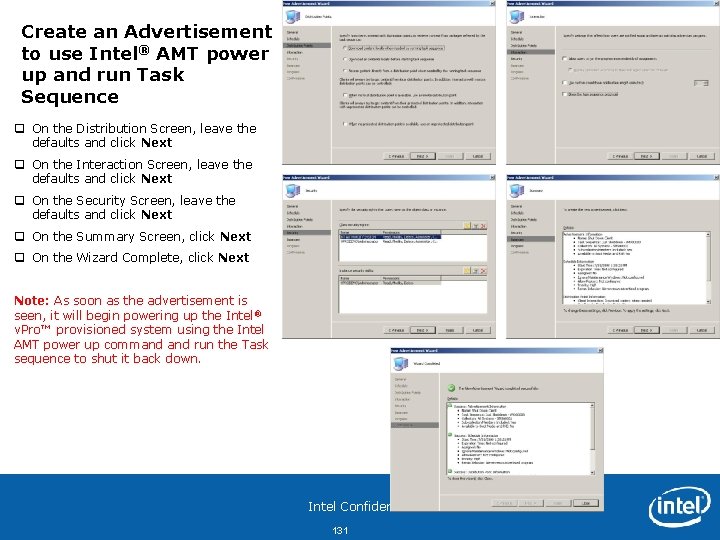
Create an Advertisement to use Intel® AMT power up and run Task Sequence q On the Distribution Screen, leave the defaults and click Next q On the Interaction Screen, leave the defaults and click Next q On the Security Screen, leave the defaults and click Next q On the Summary Screen, click Next q On the Wizard Complete, click Next Note: As soon as the advertisement is seen, it will begin powering up the Intel ® v. Pro™ provisioned system using the Intel AMT power up command run the Task sequence to shut it back down. Intel Confidential 131

Real World Use Case #2 Intel KVM integrated into SCCM SP 2 and Microsoft Diagnostic and Recovery Tools Intel Confidential 132

Intel® v. Pro™ KVM • Keyboard, Video and Mouse Redirection over IP • Intel® AMT 6. 0 platform (Piketon and Calpella) with integrated graphics • Similar to a full IP-KVM experience, without expensive hardware • ISV Support: • Real. VNC will be shipping soon: http: //communities. intel. com/community/openportit/vproexpert/blog/2010/02/04/vnc-viewer-plus -enabling-remote-access-to-the-2010 -intel-core-vpro-processor-family • Others to be announced Intel Confidential 133

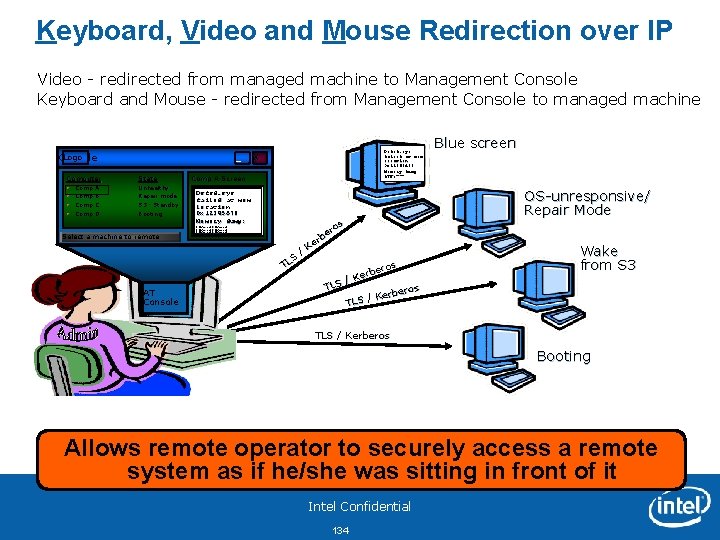
Keyboard, Video and Mouse Redirection over IP Video - redirected from managed machine to Management Console Keyboard and Mouse - redirected from Management Console to managed machine Logo Console Computer Comp A Comp B Comp C Comp D _ State Unhealthy Repair mode S 3 - Standby Booting Select a machine to remote AT Console Dsfsd. sys failed at mem location 0 x 12345678 Memory dump: X Comp A Screen Dsfsd. sys failed at mem location 0 x 12345678 Memory dump: 3409 afed 3409 afed Blue screen 3409 afed 3409 afed s ro e b er K / S TL ros rbe e K / TLS os erber K / TLS OS-unresponsive/ Repair Mode Wake from S 3 TLS / Kerberos Booting Allows remote operator to securely access a remote system as if he/she was sitting in front of it Intel Confidential 134

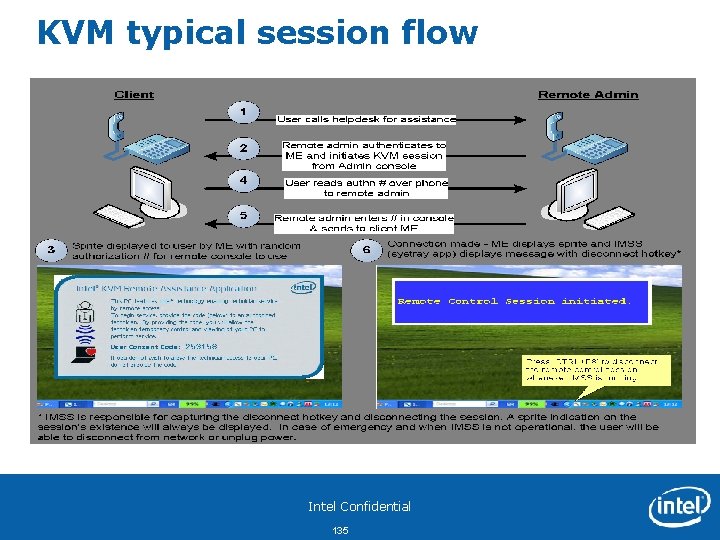
KVM typical session flow Intel Confidential 135

Install KVM Viewer on SCCM Site Server q On the MSSCCM VM image, double click KVMView. Setup. exe to install the KVM Viewer q In the KVMView Setup Wizard, click Next q In the Select Installation Folder window, click Next q In the Confirmation Installation window, click Next q In the Installation Complete window, click Close Note: This installation will install the KVMViewer application in c: program filesIntelKVMView q After installation is complete, delete the KVMCerts. PEM file in the KVMView Folder q Recreate a KVMCerts. PEM file by creating a new text file (New Text Document. txt) and renaming it to KVMCerts. PEM (file size will now be 0 KB) Intel Confidential 136

Integrating KVM into SCCM Site Server q Close the Config. Mgr Console in the VM image q Copy the file vpro_client. xml and place into c: Program FilesMicrosoft Configuration ManagerAdmin. UIxmlstorageExte nsionsActions7 ba 8 bf 44 -23444035 -bdb 4 -16630291 dcf 6 Note: This file will give you the ability to right click on a provisioned v. Pro KVM system and launch the KVMViewer from within the Config. Mgr Console. Intel Confidential 137

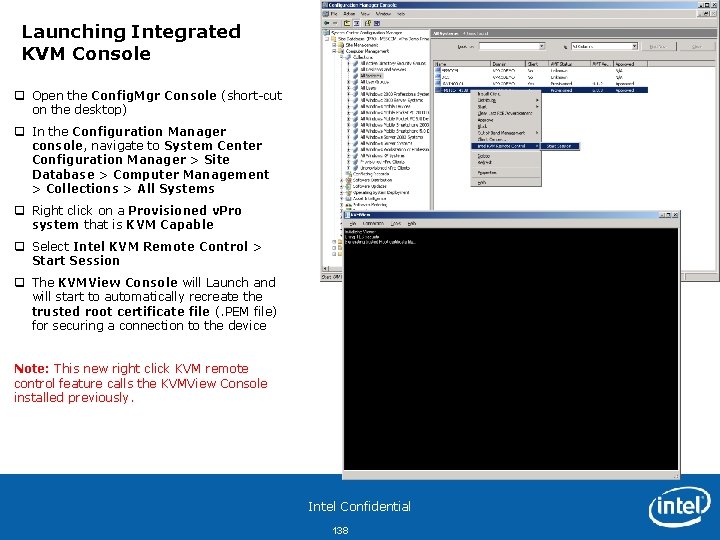
Launching Integrated KVM Console q Open the Config. Mgr Console (short-cut on the desktop) q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Computer Management > Collections > All Systems q Right click on a Provisioned v. Pro system that is KVM Capable q Select Intel KVM Remote Control > Start Session q The KVMView Console will Launch and will start to automatically recreate the trusted root certificate file (. PEM file) for securing a connection to the device Note: This new right click KVM remote control feature calls the KVMView Console installed previously. Intel Confidential 138

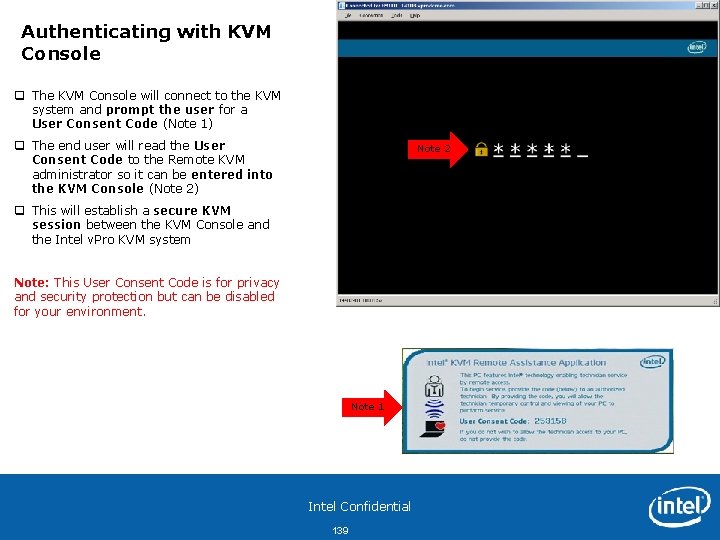
Authenticating with KVM Console q The KVM Console will connect to the KVM system and prompt the user for a User Consent Code (Note 1) q The end user will read the User Consent Code to the Remote KVM administrator so it can be entered into the KVM Console (Note 2) Note 2 q This will establish a secure KVM session between the KVM Console and the Intel v. Pro KVM system Note: This User Consent Code is for privacy and security protection but can be disabled for your environment. Note 1 Intel Confidential 139

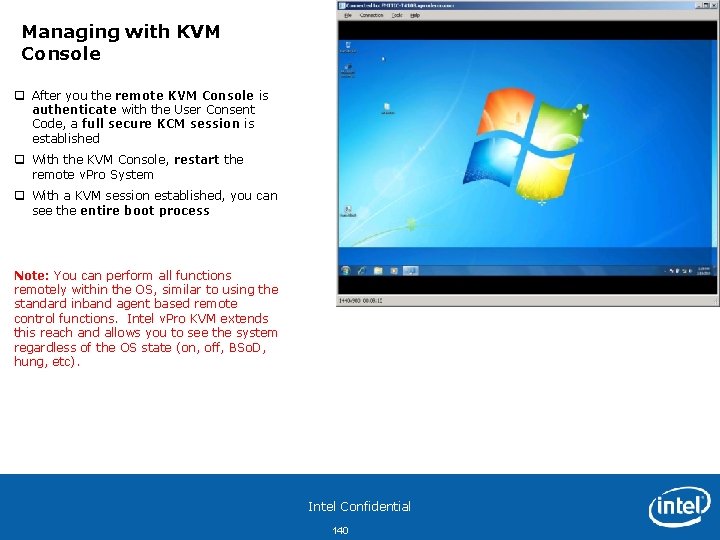
Managing with KVM Console q After you the remote KVM Console is authenticate with the User Consent Code, a full secure KCM session is established q With the KVM Console, restart the remote v. Pro System q With a KVM session established, you can see the entire boot process Note: You can perform all functions remotely within the OS, similar to using the standard inband agent based remote control functions. Intel v. Pro KVM extends this reach and allows you to see the system regardless of the OS state (on, off, BSo. D, hung, etc). Intel Confidential 140

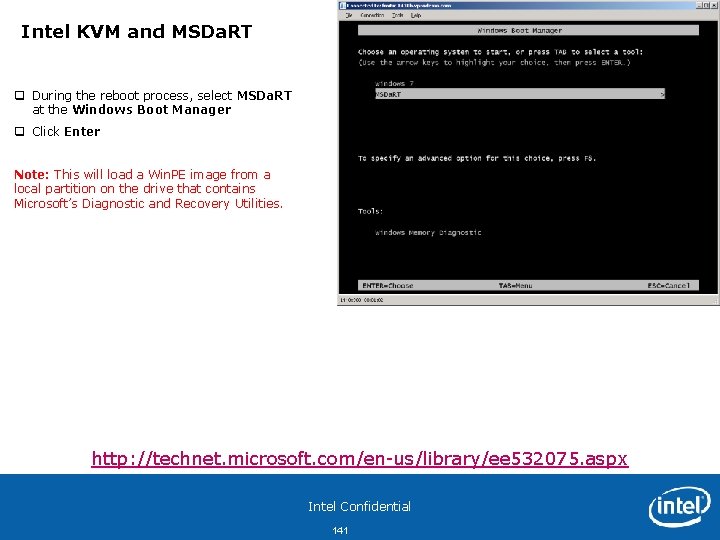
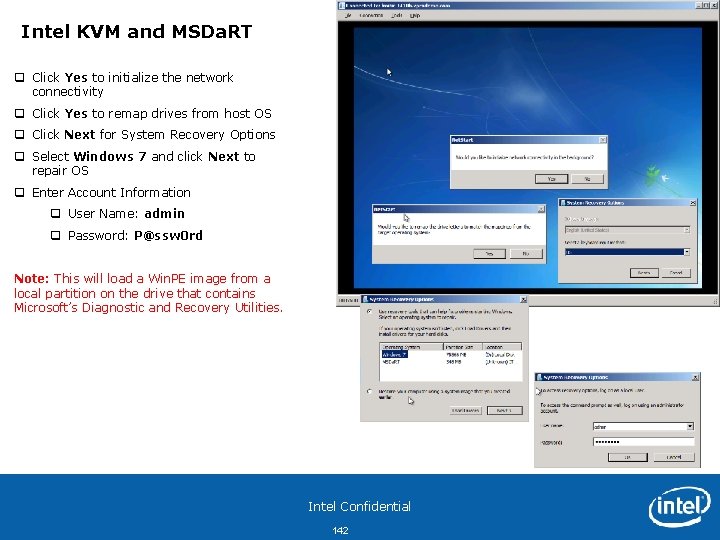
Intel KVM and MSDa. RT q During the reboot process, select MSDa. RT at the Windows Boot Manager q Click Enter Note: This will load a Win. PE image from a local partition on the drive that contains Microsoft’s Diagnostic and Recovery Utilities. http: //technet. microsoft. com/en-us/library/ee 532075. aspx Intel Confidential 141

Intel KVM and MSDa. RT q Click Yes to initialize the network connectivity q Click Yes to remap drives from host OS q Click Next for System Recovery Options q Select Windows 7 and click Next to repair OS q Enter Account Information q User Name: admin q Password: P@ssw 0 rd Note: This will load a Win. PE image from a local partition on the drive that contains Microsoft’s Diagnostic and Recovery Utilities. Intel Confidential 142

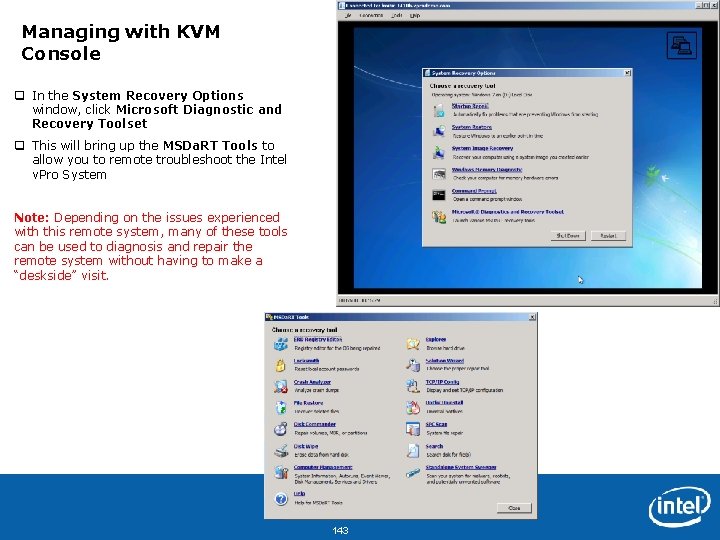
Managing with KVM Console q In the System Recovery Options window, click Microsoft Diagnostic and Recovery Toolset q This will bring up the MSDa. RT Tools to allow you to remote troubleshoot the Intel v. Pro System Note: Depending on the issues experienced with this remote system, many of these tools can be used to diagnosis and repair the remote system without having to make a “deskside” visit. Intel Confidential 143

Real World Use Case #3 IDER Remote Drive Share (RDS) Intel Confidential 144

IDE Redirection Remote Drive Share • Redirect to a small Linux based. iso that allows a remote share to the NTFS drive – http: //communities. intel. com/docs/DOC-4785 • Using Remote Drive Sharing and Intel v. Pro Technology to Perform a Remote Kernel Memory Dump Analysis – http: //communities. intel. com/docs/DOC-4826 • Using Remote Drive Sharing and Intel v. Pro Technology to Perform a Remote Virus Scan – http: //communities. intel. com/docs/DOC-4787 Intel Confidential 145

Real World Use Case #4 Powershell Scripts for 3 PDS Intel Confidential 146

Powerscript Shells for 3 PDS • http: //communities. intel. com/docs/DOC-4800 • Intel Confidential 147

Lab Module 6 Requirements and Prerequisites for Config. Mgr SP 2 2007 Intel Confidential 148

Requirements for Config. Mgr 2007 SP 2 requires… Intel® AMT v 3. 2. 1 systems and beyond (If your customer has Intel AMT systems prior to v 3. 2. 1, please talk to Intel/Microsoft about WS-Management Translator Utility: http: //software. intel. com/en-us/articles/intel-ws -management-translator/) Active Directory (AD) and Kerberos • For client authentication • Config. Mgr 2007 SP 2 AD schema extensions are not required to take advantage of Config. Mgr 2007 SP 2 Out of Band Management capability; however, it may be required for use non-Intel AMT related Config. Mgr 2007 SP 2 features TLS • For server authentication • Requires a Microsoft Enterprise Certificate Authority Remote Configuration • Zero Touch configuration or called PKI (public key infrastructure) • Standard remote configuration procedures apply from provisioning • Config. Mgr 2007 SP 2 provides its own remote agent provisioning support through the SCCM client agent • Provisioning authorization can also be done through OOB Import Wizard (no agent required Config. Mgr 2007 SP 2 does not require or support… Mutual TLS • This functionality is redundant with Kerberos for client authentication • Config. Mgr 2007 SP 2 only uses Mutual TLS during the Intel AMT set-up/provisioning Digest User Accounts • Microsoft only supports Kerberos user accounts • Although not used by Config. Mgr 2007 SP 2, Digest Accounts can be defined Pre-shared Keys (PSK) • Also referred to as PID/PPS provisioning • Config. Mgr 2007 SP 2 can support PID/PPS provisioning through the Intel® WS-Management Translator Intel Confidential 149

Prerequisites for Config. Mgr 2007 SP 2 OOB Management • Config. Mgr 2007 SP 2 Site Server – Windows Remote Management (Win. RM) version 1. 1 (or later) – http: //go. microsoft. com/fwlink/? Link. Id=105682 – If Windows 2003, – Service Pack 2 or Later – Hotfix KB 942841 http: //support. microsoft. com/kb/942841/en-us – MSXML 6. 0 is required on computers that run the out of band management console – If Windows 2008 or Vista running the OOB console, – Telnet Client installed to perform Serial-over-LAN • Active Directory – Intel® v. Pro™ Clients being managed must belong to the same AD Forest as the OOB Service Point – AD Schema Extensions are not required for Intel v. Pro support; however, are required for other Config. Mgr 2007 SP 2 features and make Config. Mgr 2007 SP 2 Client Agent Deployments easier (required for Agent Based provisioning) • Microsoft Enterprise Certification Authority – Issue and Manage certificates required for TLS based out of band management – Must automatically approve certificate request from the site server – Key Length not to exceed 2048 (4096 for newer AMT firmware) Intel Confidential 150

Prerequisites for Config. Mgr 2007 SP 2 OOB Management • Remote Configuration Certificate - http: //technet. microsoft. com/en- us/library/cc 161804. aspx#BKMK_AMTprovisioning 1 – Supported 3 rd party CA (Verisign, Godaddy, Comodo, Starfield) • DNS / DHCP / Network Ports – provisionserver associated to Config. Mgr 2007 SP 2 Out of Band Service Point – Active DCHP Scope with Option 6 (DNS servers) and Option 15 (Domain Name) configured – Open Network ports: 9971 - Provisioning Port; and 16992 through 16995 - OOB Management Ports – Dynamic updates to DNS from DHCP (Option 81) • Intel® v. Pro™ Client – Intel® AMT HECI and So. L Driver for Config. Mgr 2007 SP 2 Client Agent based Provisioning – Firmware >=3. 2. 1 for Native Support • Administrators Checklist and Prerequisties – http: //technet. microsoft. com/en-us/library/cc 161943. aspx – http: //technet. microsoft. com/en-us/library/cc 161785. aspx Intel Confidential 151

Intel AMT Firmware Requirements • Config. Mgr SP 2 can work with a mixed AMT Firmware environment – Any pre-3. 2. 1 firmware requires WS-MAN Translator; avoid if at all possible • Recommend to upgrade to latest AMT Firmware version made available by your OEM for your chosen platform – – – Typically systems won’t be shipped with latest firmware Depending on OEM, might be bundled with BIOS Firmware upgrade sometimes requires BIOS upgrade as well Download from OEM website If not available, contact OEM Distribute like any other software package Intel Confidential 152

Intel Confidential 153

Glossary • Legacy Provisioning/Managing – Provisioning and Managing Intel® v. Pro™ systems that are less than Intel® AMT firmware 3. 2. 1 • Native Provisioning/Managing – Provisioning and Managing Intel v. Pro systems that have Intel AMT firmware 3. 2. 1 (today) and higher (future releases) • Intel® Manageability Engine (Intel® ME) – microprocessor in Intel v. Pro platforms that perform the Intel AMT functions and capabilities • Intel® Manageability Engine BIOS Extension (Intel® MEBX) - the user interface to the Intel ME; it allows for the configuration of settings that control the operation of the Intel ME Intel Confidential 154

Lab Extras Config. Mgr 2007 SP 2 Logs and Troubleshooting Tips Intel Confidential 155

Send. Sched Utility to start provisioning In order to start the Inband agent based provisioning immediately, you can use the sendsched utility to initiate the process from the v. Pro Client • This is the Windows Management Instrumentation Tester Open a command prompt and type wbemtest After the Windows Management Instrumentation Tester Utility Opens, click Connect In the Namespace of the Connect Window, type the remote system name you want to force the check followed by rootccm (requires admin rights on the remote system) Click Connect • • After you successfully connect to the target system, click the Execute Method Button In the Get Object Path window, type sms_client in the Object Path field • • Click OK In the Execute Method Window, enter Trigger. Schedule in the Method Field Click the Edit In Parameters Button In the Object editor for _PARAMETERS window, Double Click the s. Schedule. ID in the Properties field In the Property Editor Window, change the Value to Not NULL and add the following {0000 -0000 -0000000120} • • • – – You can also simply run the command on the local system by simply leaving out the host name Example: rootccm • This value is the Object ID to initiate this OOB auto-provisioning check Click the Save Property button • • In the Object editor for _Parameters window, click the Save Object button In the Execute Method window, click the Execute Button After you Execute the method, you should see a message that the Method was executed successfully To confirm that your method was executed, look at the target systems c: windowssystem 32CCMLogsoobmgt. log You should now see a new entry in the log Get. Provisioning. Setting indicating that the policy has been re-evaluated Click Here to return http: //communities. intel. com/community/openportit/vproexpert/microsoft-vpro/blog/2008/09/30/using-wmi-to-force-the-sccm-agent -to-check-for-its-amt-auto-provisioning-policy; jsessionid=EFD 16 EF 6 C 2 DB 47 CFED 050 A 242 B 7 AFE 5 F. node 5 COMS Intel Confidential 156

Helpful Config. Mgr 2007 SP 2 Logs for Troubleshooting Intel® AMT Provisioning and Management q. C: Program FilesMicrosoft Configuration MangerLogs q. Amtopmgr. log - log for tracking provisioning process q. Amtproxymgr. log – log used for tracking activities like Certificate generation, OU creation, etc q. C: Program FilesMicrosoft Configuration MangerAdmin. UILog q. OOBConsole. log - Log for tracking OOB Management Console activity (note: for more detailed information - change "Error" to "Verbose" in the following file c: Program FilesMicrosoft Configuration ManagerAdmin. UIbinoobconsole. exe. config Intel Confidential 157

Helpful Config. Mgr 2007 SP 2 Logs for Troubleshooting on the Intel® v. Pro™ Client q. C: windowssystem 32ccmlogs qoobmgmt. log – log to track the provisioning of Intel® AMT q. C: windowssystem 32ccmsetup qccmsetup. log – log to track installation progress of Config. Mgr 2007 SP 2 Client Agent Intel Confidential 158

Troubleshooting Config. Mgr 2007 SP 2 Agent Auto-provisioning policy q If you do not see your system automatically provision in Config. Mgr 2007 SP 2, look in the c: windowssystem 32CCMLogs q (on Vista 64 bit OS, the logs folder is located under c: windowsSys. WOW 64CCMLog s) q OOBMGMT. log q If you see the log stating Auto Provision Policy Disabled, perform the following steps. q MORE TO BE ADDED • If you see the OOBMGMT. log showing autoprovisioning policy disabled, this indicates the agent has not found a collection that has enabled automatic provisioning. Intel Confidential 159

Config. Mgr 2007 SP 2 Resources • Intel® v. Pro™ Expert Center devoted to Microsoft products and Intel v. Pro Technology - http: //communities. intel. com/openport/blogs/micro soft-vpro • Intel® v. Pro™ Expert Center; Known Issues, Best Practices, and Workarounds - http: //communities. intel. com/docs/DOC 1247; jsessionid=4 ABCE 498498 C 0 EB 58 EBCAA 16 C 2 2 F 6250. node 5 COMS Intel Confidential 160

Manually Unprovision Intel® AMT in the Intel® MEBX q Reboot the HP 7800 and hit CTRL + P to enter the Intel MEBX Interface q Enter the password; P@ssw 0 rd q Select Intel (R) AMT Configuration and hit Enter q Select Un-Provision and Enter q Click Y for Yes to reset Intel AMT q Select Full Unprovision and Enter Note: This will fully unprovision the Intel AMT system and set it back to factory default mode with the exception of the Intel MEBX password. Intel Confidential 161

SCCM Out of Band Provisioning (Bare Metal Provisioning) • Out of Band Management Controller Import Wizard invoked from Collections menu • Wizard requests Computer Name, FQDN, MAC, UUID • Intel v. Pro client(s) imported into collection allowing additional non-AMT SCCM 2007 SP 1 related discovery • When Hello Packet received, SCCM 2007 SP 1 will perform the provisioning process • Process: OOB Import -> Hello Packet Received -> SCCM 2007 SP 1 Provisions Client Intel Confidential 162

SCCM Out of Band Provisioning 1. Admin imports provisioning data for Client being provisioned into Config. Mgr 2007 SP 1 2. v. Pro Client sends PKI hello packet to provisioning server (defined firmware schedule) 3. OOB Service Point secures connection with AMT client through Embedded AMT Self Signed Certificate and Present Provisioning Certificate for initial Authentication 4. OOB Service Point sets Remote Admin and MEBx password (if not changed) 5. OOB Service Point requests a web server certificate on behalf of the AMT client 6. OOB Service Point created an Object in AD for the v. Pro Client 7. OOB Service Point pushes web server certificate to AMT client 8. OOB Service Point pushes ACL, power schema, and other configuration data to AMT to finalize provision Intel Confidential 163

REMOVED SLIDES Intel Confidential 164

2010 Additions to Intel® v. Pro™ Technology Expanded Manageability Enhanced Security Manageable data protection with integration of drive encryption solutions Uninterrupted keyboard, video & mouse control Local wake capability to ensure local management tasks are executed Asset & data protection with anti-theft features and services Energy Efficient Performance Cross Client Consistency New micro-architecture and partitioning to support better application performance with continued energy savings Same security and manageability features for both desktop and notebook DASH 1. 1 and full IPv 6 support Lower TCO with more efficient, more secure, more manageable platforms Intel Confidential 165

Provision AMT via In. Band Config. Mgr 2007 SP 2 Client Agent q After a few minutes, provisioning will automatically complete and you can update your collection membership q Right Click Collections and select Update Collection Membership q Click Yes to confirm that you want to proceed q Right click on All Systems collection and select Refresh q The client will now appear in All Systems Collection Provisioned and no longer be listed in the Unprovisioned v. Pro Clients collection d n a Note: You can track the provisioning e progress under C: Program FilesMicrosoft d i l Configuration MangerLogsAmtopmgr. log S This process length depends on the time it d e takes for Config. Mgr 2007 SP 2 Agent to v check in with the Server and pull down its o policies. m Re d e us r o f / e c n e r e f e R p u k c Ba Congratulations! You have just successfully completed In. Band provisioning in Config. Mgr 2007 SP 2 and enabled Intel® v. Pro™ systems to be manageable out of band by Config. Mgr 2007 SP 2 console. Intel Confidential 166

/ p u k c Ba e c n e r e Lab Moduleef 4 R r fo d e us d. Configuration for Collection n a e In-Band Provisioning d i l S d e ov m e R Intel Confidential 167

Monitor Policies being applied to Config. Mgr 2007 SP 2 Client q After the Agent has pulled down the machine policies from the Config. Mgr 2007 SP 2 server, you will see more Actions listed in the Actions tab of the Configuration Manager d e ov m e R d n a e d i l S d e us r o f Intel Confidential 168 / e c n e r e f e R p u k c Ba

Discover Systems with Config. Mgr 2007 SP 2 Discovery q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Primary Site > Site Settings > Discovery Methods q Double Click on Active Directory System Discovery Note: With the collection defined, you can use any of the discover methods that Config. Mgr 2007 SP 2 provides (AD System Group, AD Security Group, AD System , AD User, Heartbeat, or Network) to discover the client. If you decide to use Network discovery (refer back to steps on required configuration) d e us r o f / e c n e r e f e R p u k c Ba d n a Note: For more information about e d network discovery and how to schedule it i l to run, see About Network Discovery and S How to Schedule Network Discovery. d e ov m http: //technet. microsoft. com/en-us/library/cc 161971. aspx e R Intel Confidential 169

Enable Active Directory System Discovery q In the Active Directory System Discovery Properties window General Tab, check Enable Active Directory System Discovery q Click the Button q In the New Active Directory Container window, select Local Domain and click OK d n a q In the Select New Container window, e select Computers d i l q Click OK…. proceed to next foil S d e ov m e R d e us r o f / e c n e r e f e R Intel Confidential 170 p u k c Ba

Initiate the Polling Schedule for Discovery q On the Polling Schedule, check the box to Run discovery as soon as possible q Click Apply q Click OK Note: This will initiate a discovery of all the systems listed in the computer OU in the Active Directory. d e ov m e R d n a e d i l S d e us r o f / e c n e r e f e R Intel Confidential 171 p u k c Ba

Update Collection to see Discovered System q After you run the discover method q Right Click All Systems and select Update Collection Membership Update Images q Click OK to confirm that you want to proceed q Right click on All Systems and select Refresh (f 5) q The client will now appear in the All Systems and Unprovisioned v. Pro Cleints Collection d n a e d i l S Note: It may take a couple minutes for the system to show up. You may continue to click Refresh All Systems Collection until you see the client in the collection. The Intel® AMT status of the device will be in a unknown state. Ensure the firewalls on the virtual images, host OS running the virtual images, and the v. Pro system are not enabled. The Windows Client firewall can inhibit communications. d e ov m e R / e c n e r e f e R p u k c Ba d e us r o f Intel Confidential 172

Use Out of Band Management to Discover Management Controllers q After the client is populated in the All Systems Collection, check to see if any of the systems are Intel® v. Pro™ capable Update Images q Right Click on the newly discovered system > Out of Band Management > Discover Management Controllers q Click OK Note: This will scan the system and validate which clients are Intel v. Pro capable and ready to be provisioned. You can also scan an entire collection for AMT systems. d n a e d Note: You can monitor the discovery i l process by watching the amtopmgr. log S located in C: Program d FilesMicrosoft e (you will find a short Configuration MangerLogs v cut to this log on the SCCM Virtual Image o desktop) m e R / e c n e r e f e R p u k c Ba d e us r o f Intel Confidential 173

Update Collection membership to see Intel® v. Pro™ system Not Provisioned q After a few minutes, depending on the size of your collection, you can update your collection membership q Right click Collections and select Update Collection Membership q Click Yes to confirm that you want to proceed q After one minute, right click on Collections and select Refresh q The client will now appear in Unprovisioned v. Pro Clients Collection and listed as Not Provisioned and when the Config. Mgr 2007 SP 2 Agent checks in for its policies, this collection will start the automatic provisioning process. d n a Note: If you look back at the All Systems e d collection, you will now see the system as i l listed as Not Provisioned. You will also see S the version of Intel AMT listed. If you do d e not see your system in the Unprovisioned v Collection, the collection query or o discovery method failed (refer back to m previous steps). e R ® d e us r o f / e c n e r e f e R p u k c Ba Note: If the system is listed as Detected, remove client from Config. Mgr, boot client into the Intel MEBX and SMB provision, unprovision, repeat AD Discovery (p. 96 -97), and repeat Discover Management Controllers (p. 98 -99) Intel Confidential 174

Lab Module 3 Review p u • Installed Config. Mgr 2007 SP 2 Client Agent on local k c system a B / • Initiated Action on the Config. Mgr 2007 SP 2 Client e. SP 2 server c Agent to check in with the Config. Mgr 2007 n e to receive its policies r e f to the Config. Mgr • Validated Policies were being applied e R logs 2007 SP 2 Client through associated r o f • Updated the Config. Mgr 2007 d SP 2®Collection e Membership and found s that Intel v. Pro™ system was u successfully provisioned d using Config. Mgr 2007 SP 2 n a Inband agent. e d i l S d e ov m e R Intel Confidential 175

Configure Network Discovery for Management Controllers q In the Configuration Manager console, navigate to System Center Configuration Manager > Site Database > Site Management > PRO – v. Pro Demo Site > Site Settings > Discovery Methods q In the right hand window, Right-click Network Discovery, and click Properties q On the General tab, select Enable Network Discovery and Select Topology radio button d e us r o f / e c n e r e f e R p u k c Ba d n a q Select Enable discovery of out of band management controllers e d i l q Click OK S Note: This will allow Config. Mgr 2007 SP 2 d AMT capable. e to detect if a system is Intel ov m http: //technet. microsoft. com/en-us/library/ee 344683. aspx e R ® Intel Confidential 176