Integrity for Activated Content Data Integrity in an









![Standards: Simple XML Example (Signature, Signed. Info, Methods, and References) ¯ [s 01] <Signature Standards: Simple XML Example (Signature, Signed. Info, Methods, and References) ¯ [s 01] <Signature](https://slidetodoc.com/presentation_image_h2/bd5a764d934361278e6268bbd9f30b74/image-17.jpg)
![[s 01] <Signature Id="My. First. Signature” xmlns="http: //www. w 3. org/2000/09/xmldsig#"> [s 02] <Signed. [s 01] <Signature Id="My. First. Signature” xmlns="http: //www. w 3. org/2000/09/xmldsig#"> [s 02] <Signed.](https://slidetodoc.com/presentation_image_h2/bd5a764d934361278e6268bbd9f30b74/image-19.jpg)
















- Slides: 36

Integrity for Activated Content Data Integrity in an Active Content System Active Middleware Workshop Hilarie Orman Volera, Inc. August 6, 2001

Trends in Web Content Activity ¯ Complex pages ¯ Multiple business interests ¯ Mechanisms ¯ ¯ Server side includes Edge Side includes Ad hoc markers URL naming tricks ¯ Efficiency ¯ Issue Minimize traffic, maximize cacheability

Data Integrity: It all depends ¯ Traditional ¯ ¯ ¯ IP ¯ ¯ ¯ Model Header, some fields immutable Content, immutable modulo accidents packets Packets might get to their destination but shouldn’t be ‘delivered’ anyplace else Security was TBD and emerged in IPsec Awkward and slow standardization ¯ Anything else ‘End-to-End’

Basic Page Options ¯ Prevailing semantic: ‘put a picture here’ <HTML> <BODY> <H 1>DOGTOWN NEWS</H 1> <HEADLINE>Dog Days</HEADLINE> <BYLINE>Fidelius Canine</BYLINE> <REGIONAL_AD h=640 w=480> <STORY>…. </STORY> DOGTOWN NEWS Dog Days Fidelius Canine SALE at FIDO FOODS Beef Dinners 65 cents all week A noontime high of 100 has local residents remembering the dog days of 1894, when temperatures were pegged at over the century mark for 45 consecutive days.

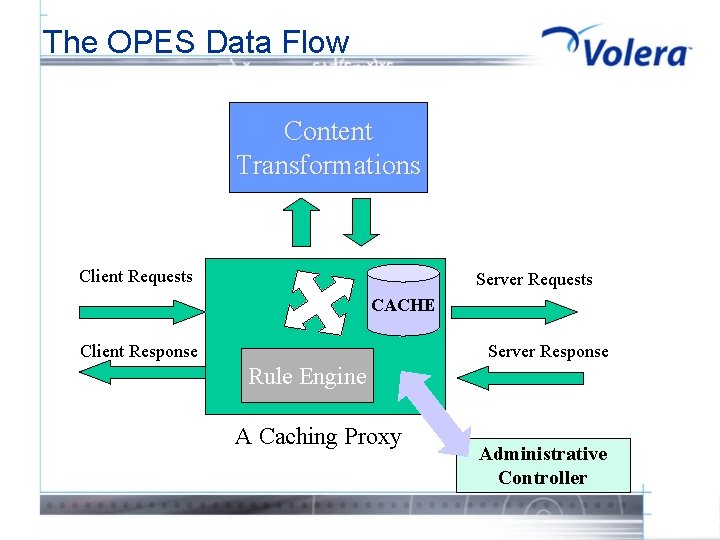
The OPES Data Flow Content Transformations Client Requests Server Requests CACHE Client Response Server Response Rule Engine A Caching Proxy Administrative Controller

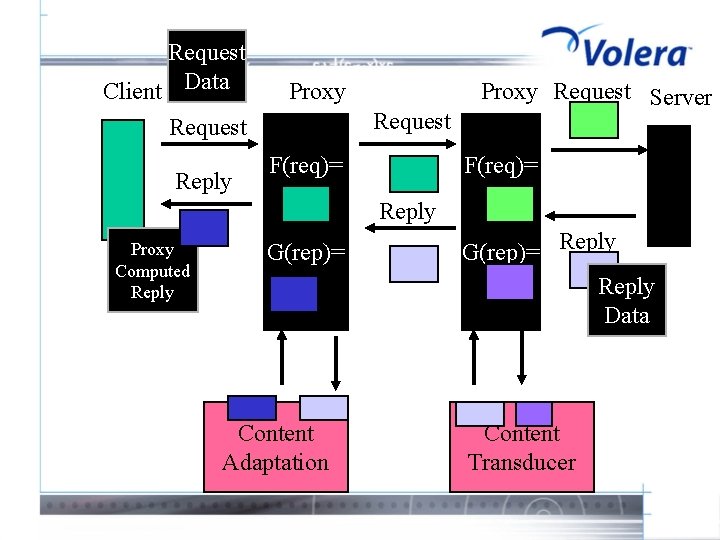
Request Client Data Proxy Request Reply F(req)= Proxy Request Server F(req)= Reply Proxy Computed Reply G(rep)= Content Adaptation G(rep)= Reply Data Content Transducer

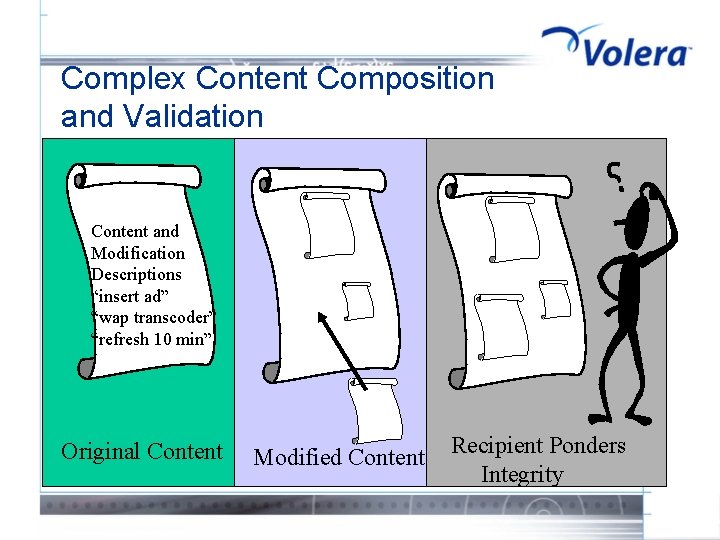
Complex Content Composition and Validation Content and Modification Descriptions “insert ad” “wap transcoder” “refresh 10 min” Original Content Modified Content Recipient Ponders Integrity

Hash-based Editing ¯ Document has a part index and content ¯ Index summarizes document by hash of each “part” ¯ Each part index entry has editing permissions ¯ Modification audit trail achieved by attaching ‘verifier’ for each editing action ¯ Recipient verifies the message by comparing the received message to the action list

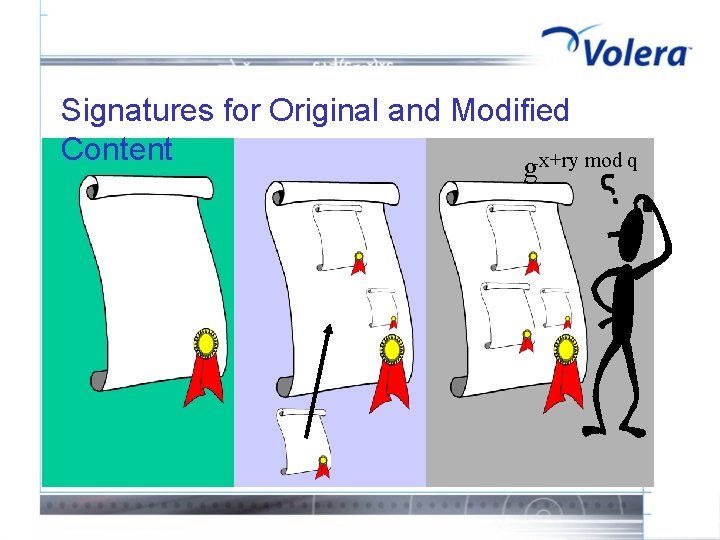
Signatures for Original and Modified Content gx+ry mod q

Goals of Active Data Integrity ¯ Publisher defines document and modification permissions ¯ Delegates can modify the document ¯ Anyone can validate the modified document ¯ Document ¯ can be cached anywhere Even with partial modifications ¯ Recipient can delegate modifications on his behalf ¯ Recipient can validate document

The Verifiable Editing Language ¯ Delete ¯ Refresh ¯ Add ¯ Permute ¯ Replaces ¯ Cache ¯ (Delete and Add) ¯ Delegate ¯ If-Else, Select ¯ Boolean combinations ¯ Replicate ¯ Append control ¯ ‘Exec’ ¯ Enduser Policy ¯ Enforcement delegation

Message Structure ¯ Publisher’s ¯ Signature ¯ Editor’s index of content and permissions of Publisher on index indices of actions, delegations ¯ Signature ¯ Optional of each editor on own index intermediate validation signatures (“this message was valid when at ibm. com”)

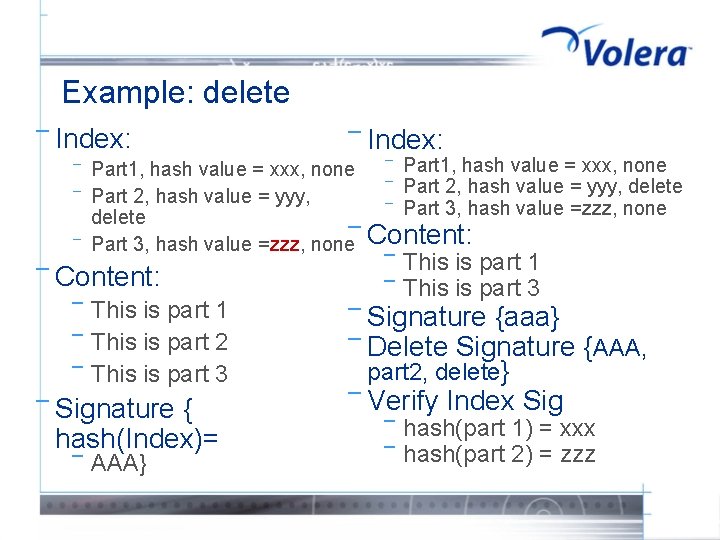
Example: delete ¯ Index: ¯ ¯ ¯ Part 1, hash value = xxx, none Part 2, hash value = yyy, delete Part 3, hash value =zzz, none¯ ¯ Content: ¯ ¯ ¯ This is part 1 This is part 2 This is part 3 ¯ Signature { hash(Index)= ¯ ¯ Index: AAA} ¯ ¯ ¯ Part 1, hash value = xxx, none Part 2, hash value = yyy, delete Part 3, hash value =zzz, none Content: ¯ ¯ This is part 1 This is part 3 ¯ Signature {aaa} ¯ Delete Signature {AAA, part 2, delete} ¯ Verify ¯ ¯ Index Sig hash(part 1) = xxx hash(part 2) = zzz

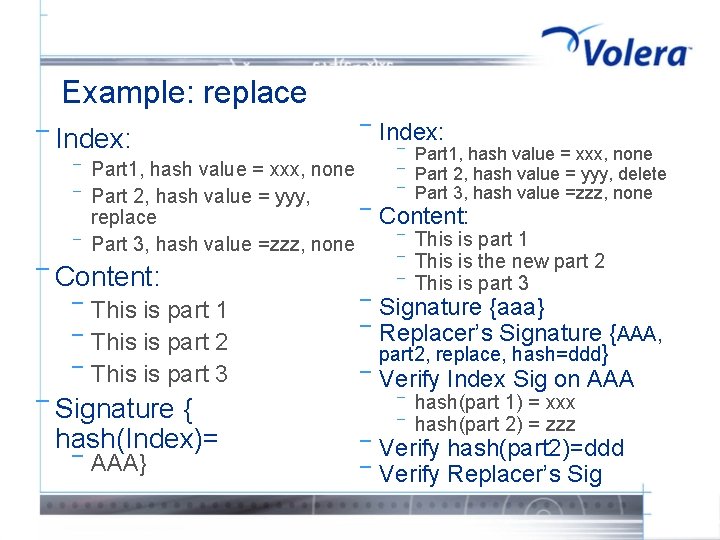
Example: replace ¯ Index: ¯ ¯ Part 1, hash value = xxx, none Part 2, hash value = yyy, replace ¯ Part 3, hash value =zzz, none ¯ Content: ¯ ¯ ¯ This is part 1 This is part 2 This is part 3 { hash(Index)= ¯ ¯ Signature ¯ AAA} Index: ¯ ¯ ¯ Content: ¯ ¯ ¯ This is part 1 This is the new part 2 This is part 3 Signature {aaa} Replacer’s Signature {AAA, part 2, replace, hash=ddd} Verify Index Sig on AAA ¯ ¯ Part 1, hash value = xxx, none Part 2, hash value = yyy, delete Part 3, hash value =zzz, none hash(part 1) = xxx hash(part 2) = zzz Verify hash(part 2)=ddd Verify Replacer’s Sig

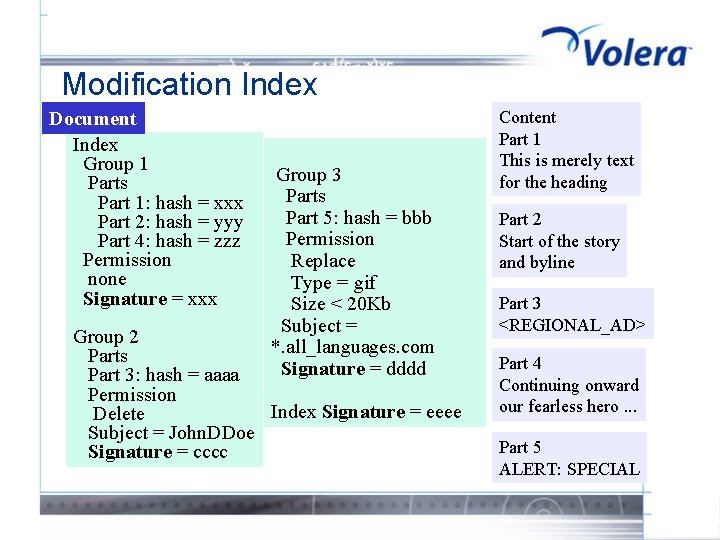
Modification Index Document Index Group 1 Parts Part 1: hash = xxx Part 2: hash = yyy Part 4: hash = zzz Permission none Signature = xxx Group 3 Parts Part 5: hash = bbb Permission Replace Type = gif Size < 20 Kb Subject = *. all_languages. com Signature = dddd Group 2 Parts Part 3: hash = aaaa Permission Index Signature = eeee Delete Subject = John. DDoe Signature = cccc Content Part 1 This is merely text for the heading Part 2 Start of the story and byline Part 3 <REGIONAL_AD> Part 4 Continuing onward our fearless hero. . . Part 5 ALERT: SPECIAL

Basis for Content Descriptors ¯ XML-Signature Syntax and Processing ¯ W 3 C Candidate Recommendation 19 -April 2001 ¯ http: //www. w 3. org/TR/xmldsig-core/
![Standards Simple XML Example Signature Signed Info Methods and References s 01 Signature Standards: Simple XML Example (Signature, Signed. Info, Methods, and References) ¯ [s 01] <Signature](https://slidetodoc.com/presentation_image_h2/bd5a764d934361278e6268bbd9f30b74/image-17.jpg)
Standards: Simple XML Example (Signature, Signed. Info, Methods, and References) ¯ [s 01] <Signature Id="My. First. Signature” xmlns="http: //www. w 3. org/2000/09/xmldsig#"> ¯ [s 02] <Signed. Info> ¯ ¯ ¯ [s 03] <Canonicalization. Method xml-c 14 n-20010315"/> Algorithm="http: //www. w 3. org/TR/2001/REC- [s 04] <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#dsa-sha 1"/> ¯ [s 05] <Reference URI="http: //www. w 3. org/TR/2000/REC-xhtml 1 -20000126/"> ¯ [s 11] </Reference> ¯ [s 12] </Signed. Info> ¯ [s 13] <Signature. Value>MC 0 CFFr. VLt. Rlk=. . . </Signature. Value>

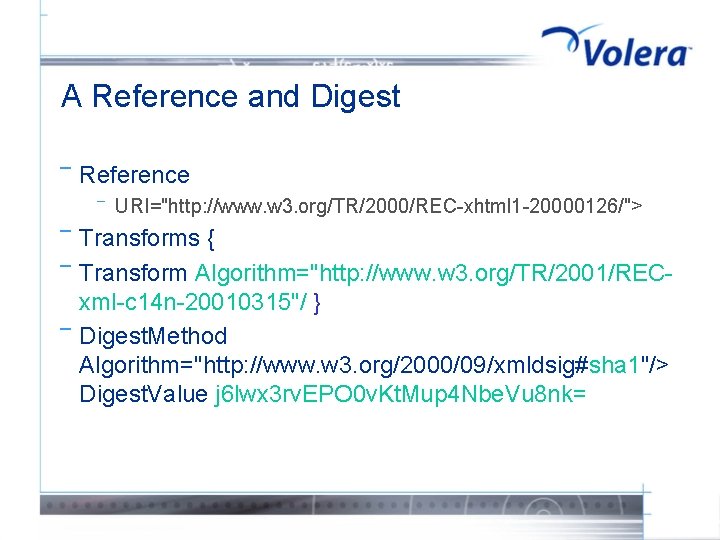
A Reference and Digest ¯ Reference ¯ ¯ URI="http: //www. w 3. org/TR/2000/REC-xhtml 1 -20000126/"> Transforms { Transform Algorithm="http: //www. w 3. org/TR/2001/RECxml-c 14 n-20010315"/ } Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> Digest. Value j 6 lwx 3 rv. EPO 0 v. Kt. Mup 4 Nbe. Vu 8 nk=
![s 01 Signature IdMy First Signature xmlnshttp www w 3 org200009xmldsig s 02 Signed [s 01] <Signature Id="My. First. Signature” xmlns="http: //www. w 3. org/2000/09/xmldsig#"> [s 02] <Signed.](https://slidetodoc.com/presentation_image_h2/bd5a764d934361278e6268bbd9f30b74/image-19.jpg)
[s 01] <Signature Id="My. First. Signature” xmlns="http: //www. w 3. org/2000/09/xmldsig#"> [s 02] <Signed. Info> [s 03] <Canonicalization. Method Algorithm="http: //www. w 3. org/TR/2001/REC-xml-c 14 n 20010315"/> [s 04] <Signature. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#dsa-sha 1"/> [s 05] <Reference URI="http: //www. w 3. org/TR/2000/REC-xhtml 1 -20000126/"> [s 06] [s 07] <Transforms> <Transform Algorithm="http: //www. w 3. org/TR/2001/REC-xml-c 14 n-20010315"/> [s 08] </Transforms> [s 09] <Digest. Method Algorithm="http: //www. w 3. org/2000/09/xmldsig#sha 1"/> [s 10] <Digest. Value>j 6 lwx 3 rv. EPO 0 v. Kt. Mup 4 Nbe. Vu 8 nk=</Digest. Value> [s 11] </Reference> [s 12] </Signed. Info> [s 13] <Signature. Value>MC 0 CFFr. VLt. Rlk=. . . </Signature. Value> [s 14] <Key. Info> [s 15 a] [s 15 b] [s 15 c] [s 15 e] <Key. Value> <DSAKey. Value> <P>. . . </P><Q>. . . </Q><G>. . . </G><Y>. . . </Y> [s 15 d] </Key. Value> [s 16] </Key. Info> [s 17] </Signature> </DSAKey. Value>

Trust Model for Mutable Content ¯ Subjects: Author, Editors, Enduser Delegates ¯ Objects: Content and content subparts ¯ Author (aka Publisher) creates ¯ ¯ ¯ Content Modification Policy Signature on Entirety ¯ Modification ¯ Non-modifiable parts require separate signature ¯ Content ¯ ¯ policy based on content structure modifiers (e. g. OPES) Append signed actions to message Change original message ¯ Recipient validates content wrt index, mods

Modification Permissions ¯ ¯ Delete Replace ¯ ¯ ¯ Append/Prepend ¯ ¯ Restrictions: same type; size Delegate (monotonicity) ¯ ¯ Restrictions: Content type Size URL Allowable subjects Execute

Modification Index ¯ Part ¯ ¯ identifier Reference or Digest ¯ Action ¯ Subjects ¯ ¯ pairs Namespace, name Public key Cert Privilege ¯ Limitations

Modifier’s Actions ¯ Entity performing the modification must sign a modification notification: ¯ ¯ Original message’s index hash Modification index entry Modifier’s ID Hash of new value (none if Delete) ¯ Example: ¯ ¯ ¯ Reference 5, Delete Modifier removes part 5 from message body Modification manifest unchanged Modifier attaches notification to message

Recipient Validation ¯ Optional ¯ Get message index ¯ Valid each part against permission and signature ¯ Simple case: Delete ¯ Author name and signature ¯ Modifier case: check permission subject and modifier signature ¯ Complex case: follow delegation chain

Dynamic Content ¯ New permission: refresh ¯ Applies only to a message part ¯ Included content, not referenced ¯ Permission can require both modifier and location identifier ¯ Stockquotes: only from Nasdaq. com ¯ User profile info: refresh every 30 minutes ¯ Etc.

Conditional Modifications cf: Edge Side Includes, www. edge-side. com ¯ Simple ¯ ¯ If URL Else ¯ ¯ conditionals ; URL can be fetched without error Another URL Endif ¯ Modification ¯ ¯ Part reference for embedded conditional Subreferences for options ¯ Modifier ¯ ¯ ¯ Index signs reference and selection Removes embedded conditional Inserts selected option (e. g. URL) Signs Notification including hash of selection

Authenticated Includes ¯ Signed message ¯ { If URL else Other_URL by cdn. cnn. com } ¯ Signature ¯ Appended data: ¯ { Original message hash, byte offset of ¯ { If URL else Other_URL by cdn. cnn. com } ¯ Signature of cdn. cnn. com }

Dynamic and Active Content ¯A distributed computing model ¯ Definition of end-to-end integrity ¯ Allows complex content composition ¯ Merges local and remote concepts ¯ Based on known technologies

Active Content ¯ Permission type: execute ¯ Additional parameters: locality ¯ “who” can execute it, “where” they are ¯ Arguments: message parts and environment info ¯ Output replaces the message part ¯ Notification same as ‘replace’ ¯ but includes ‘location’ signature over message hash, part hash, output

Executable Content ¯ Two ¯ ¯ parts Input Program ¯ Modifier certifies to performing the replacement, ¯ Execution agent certifies to executing the program on the content ¯ Output replaces the message part

Further Delegation ¯ Modification Index may be extended by message editors ¯ Add Mod. Index part ¯ ¯ Sign Original Message (hash = AAA) and Hash of New Mod. Index ¯ Their permissions cannot exceed permissions granted to them ¯ ‘Downstream’ recipients must verify permissions before exercising delegation

Modifications based on Recipient Policy ¯ Recipient ¯ ¯ Content type, size, origin, freshness, price Delegates modification rights ¯ ¯ ¯ Might ¯ policies Delete, replace, select, translate, etc. “Delete *. badplace. com/*. gif” “Translate *. ru content-type/text to English” Redelegation to partner ISP, for example ban certain content parts “Never”, “always”

Rights Delegated from Recipients ¯ Enterprise policy, ISP service ¯ Generic policy delegation ¯ Enduser -> ISP, ¯ ¯ ¯ http, content-type/html, delete *. badstuff. com/*. gif enduser signs hash of policy Might result in deletion of entire message part ¯ ISP would delete part and add signed addendum ¯ includes hash of policy authorizing the action ¯ NB: No request integrity definition

Complex Policy ¯ ¯ ¯ Reordering Restrictions (“not valid in Indiana”) If part 4 is deleted then add a delegation to modify part 7 Refresh times, parameters Reuse of individual parts ¯ ¯ “over 18 only” “ 3 uses only” Billing Audit

Policy Resolution ¯ Publisher: do not delete ¯ Enduser: delete this junk ¯ Enduser delegate: delete or not? ¯ ¯ ¯ SLA’s with publishers SLA’s with publisher agents (CDN’s) Contract with endusers ¯ SEP (Douglas Adams)

msg, policy Data Integrity(m, p) ¯ Even for complex composition systems, there is a verifiably meaning to data integrity ¯ Overhead appears tolerable ¯ Caching is enhanced ¯ Scalable, layer 6 policy and mechanisms ¯ Consistent with emerging standards