Integrating Mobile IP with Ad Hoc Networks YuChee

Integrating Mobile IP with Ad Hoc Networks 作者:Yu-Chee Tseng, Chia-Ching Shen(nctu) Wen-Tsuen Chen(nthu) 報告者:王生見 1
content n n 1. Abstract 2. Mobile IP and MANETS q n n n Related work in internet computing 3. Network architecture 4. Communication scenarios 5. Intra-Manet and inter-Manet routing scenarios 6. Broadcast routing scenario 7. Integration and implementation q q q q TTL in IP packets Agent advertisement Agent solicitation ARP Broadcast Destination address and TTL Configuration of IEEE 802. 11 b NICs 2

Abstract n n Ubiquitous computing has added a new feature, mobility, to the world of computing and communications. Mobile IP and mobile ad-hoc network(MAnet) Application Integrating 3
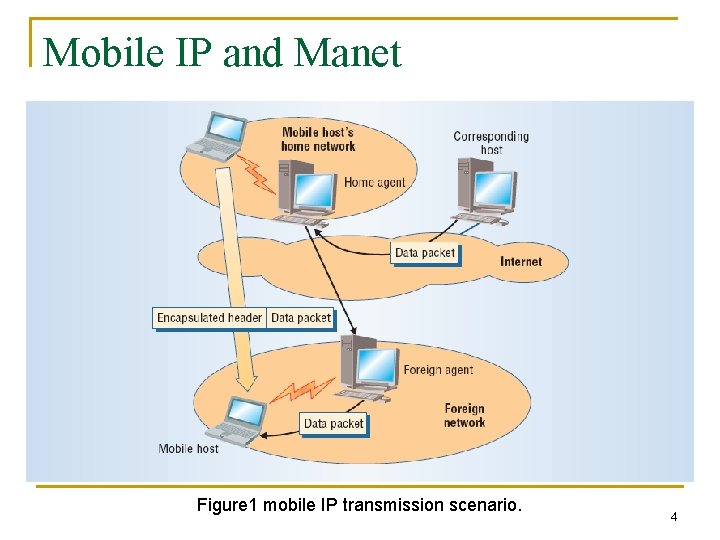
Mobile IP and Manet Figure 1 mobile IP transmission scenario. 4
Related work in internet computing(1/5) n n Mobile IP was originally designed to support macro mobileity Researchers have developed two other internet protocols q Cellular IP and the handoff-aware wireless access internet infrastructure (Hawaii) 5
Related work in internet computing(2/5) n Cellular IP q q q Uses a hierarchical approach to minimize registrations to home agents as a mobile host roaming around. A foreign agent can provide services to multiple base station. As long as the same foreign agent’s base stations cover the mobile host, no reregistration is required, thereby significantly reducing handoff delay. 6

名詞解釋(home agents and foreign agent) n Home Agent: q n 主要是傳遞資訊給從這個Home network離開的 Mobile Nodes,並且維護mobile node目前的位置 資訊。 Foreign Agent: q 與Home Agent合作,完整地去傳遞資訊給從home network離開的mobile node。 7
Related work in internet computing(3/5) n Hawaii protocol q q q Adopts a domain-based approach in which base stations can be connected as a tree. It uses specialized path setup schemes that install host-based forwarding entries in specific routers to support intradomain routing. Unlike cellular IP n Hawaii breaks the gateway-foreign-agent tie and thus is more tolerant to gateway failure, which simplifies gateway design. 8

Related work in internet computing(4/5) n Other research has addressed using Manet to provide continuous internet access via mobile IP. q q This includes extending mobile IP to let mobile hosts use a care-of address even if they are more than one hop away from a foreign agent. It also resolves the conflict between mobile IP and Manets in managing routing tables. 9

名詞解釋(care-of address) n 暫時位址(Care-of Address): q 一個表示當Mobile Host不在Home Network時,在 網路上接點的IP位址。 10
Related work in internet computing(5/5) n Compared to earlier efforts that focused on only a single Manet q Consider the existence of multiple Manets in same vicinity n q With mobile agents and mobile hosts negotiating foreign agents’ service ranges Improves Manets flexibility and reduces mobile agents’ service overhead 11
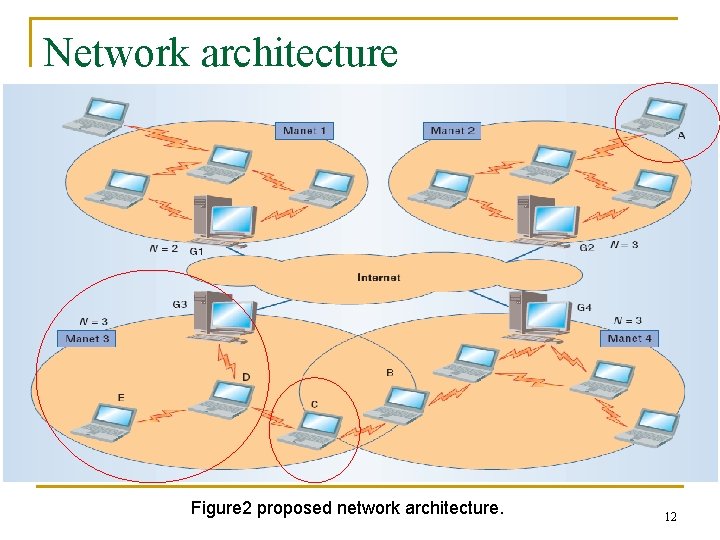
Network architecture Figure 2 proposed network architecture. 12

Communication scenarios n n Our proposed network architecture can accommodate several different communication scenarios. In discussing the possible combinations q q We assume that DSDV supports all corresponding Manet routings Although any proper routing protocol is applicable 13

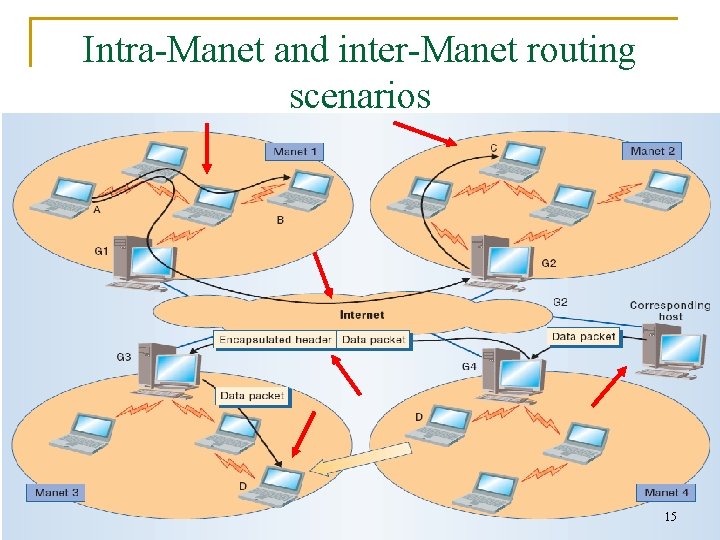
Intra-Manet and inter-Manet routing scenarios 15
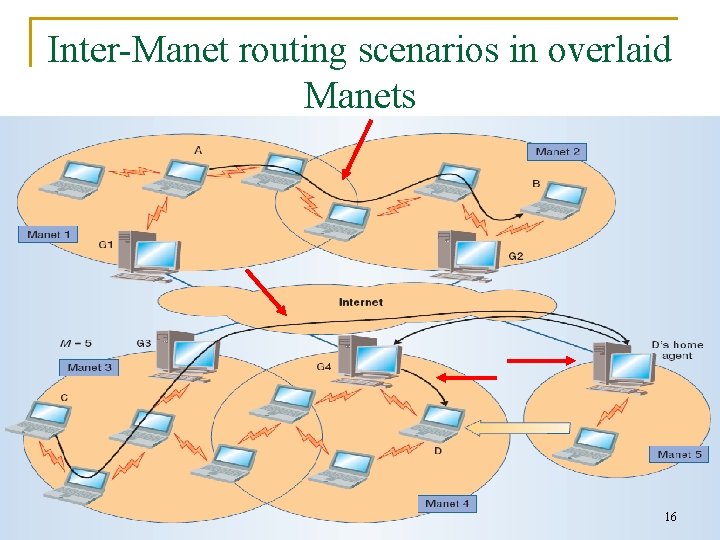
Inter-Manet routing scenarios in overlaid Manets 16
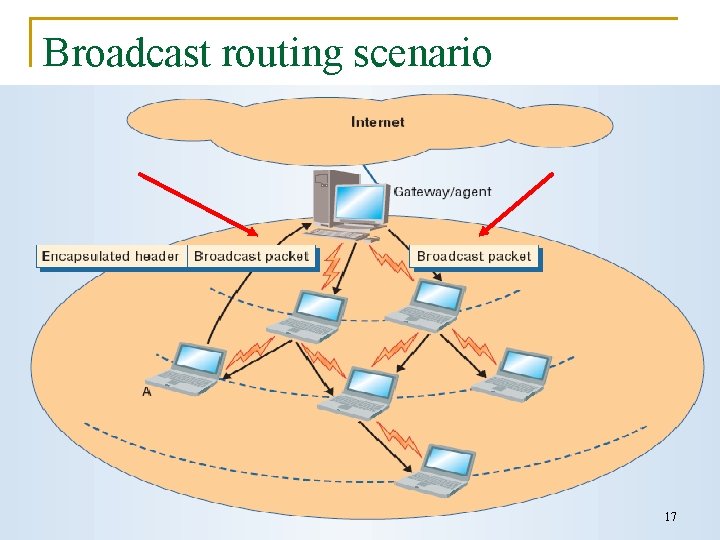
Broadcast routing scenario 17
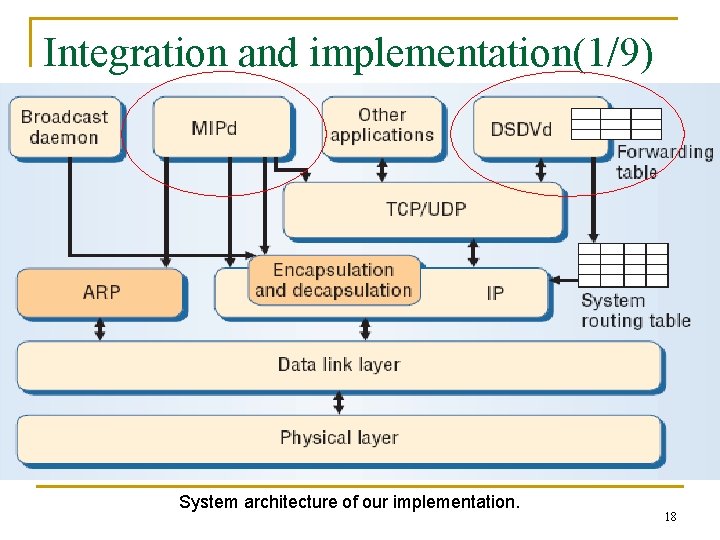
Integration and implementation(1/9) System architecture of our implementation. 18
Integration and implementation(2/9) n TTL in IP packets q n Each IP datagram has a TTL field to control its internet lifetime. Routing inside Manets q q q Implementation is based on the DSDV protocol. Each host maintains a forwarding table that lists all available destinations along with the next hop leading to each destination. Our prototype made some modifications to the DSDV protocol n Because Manets can overlap in our architecture. 19
Integration and implementation(3/9) n Agent advertisement q q Manets multihop nature requires setting the TTL to N and decreasing the value by one for each reboadcast No rebroadcast is necessary when the TTL is equal to 0 20
Integration and implementation(4/9) n Agent solicitation q q q A mobile host can multicast an Agent_Soliciation message to locate a nearby mobile agent. The original TTL value should be recorded in the packet’s payload so that when the gateway receives the packet. It can recover its distance to the requesting mobile host. 21

Integration and implementation(5/9) n ARP q q Instead, The host registers the MAC-to IP address mapping when it receives an Agent_Advertisement message. Our network architecture n n n Enabling the address resolution protocol in foreign networks to send requests and replies as usual. Because many nomadic hosts can exist in a Manet These networks should relay packets of any destination without using a subnetmask. 22
Integration and implementation(6/9) n Broadcast q q When it receives the packet, the gateway decapsulates it and broadcasts it with a TTL equal to N. To prevent broadcast datagram from looping back to the source host n The broadcast daemon also records broadcast datagram that it has encapsulated recently. 23
Integration and implementation(7/9) n Destination address and TTL q q In view of the fact that the M value that Manets use should be at least as large as the N (N->TTL, M->hop) We recommend setting M equal to 2 N n n n Which guarantees that intra-Manet communication can always occur directly without encapsulation. In the worst case, a packet has to travel from a Manet’s boundary to the gateway In addition, communication between nearby Manets is likely to occur without going through mobile IP q Thus the packet will not undergo encapsulation. 24
Integration and implementation(8/9) n In our frame work q q The network should function correctly, but some routes may not exist even if some hosts are physically neighbors. Our system is based on Linux Redhat and implements two daemons, DSDVd and MIPd. 25
Integration and implementation(9/9) q DSDVd n n q MIPd n n q periodically multicasts user datagram protocol packets to help maintain the hosts’ forwarding tables. System calls write proper entries from the forwarding table into the kernel’s routing table. Uses raw sockets for advertisement, encapsulation, and decapsulation, and it uses normal sockets for registration. Unix system calls perform proxy ARP. In addition, the IP forwarding option at each mobile hosts must be turned on. 26

- Slides: 27