Int Scope Automatically Detecting Integer overflow vulnerability in
Int. Scope: Automatically Detecting Integer overflow vulnerability in X 86 Binary Using Symbolic Execution • Tielei Wang, Tao. Wei, Zhingiang. Lin, wei. Zou • Purdue University and Peking University • Annapurna Sagi

Contents • • • Introduction Overview of Intscope Implementation Evaluation and results Strengths Weakness

Introduction • What is an integer overflow? An integer overflow occurs when an arithmetic operation attempts to create a numeric value that is too large to be represented within the available storage space.
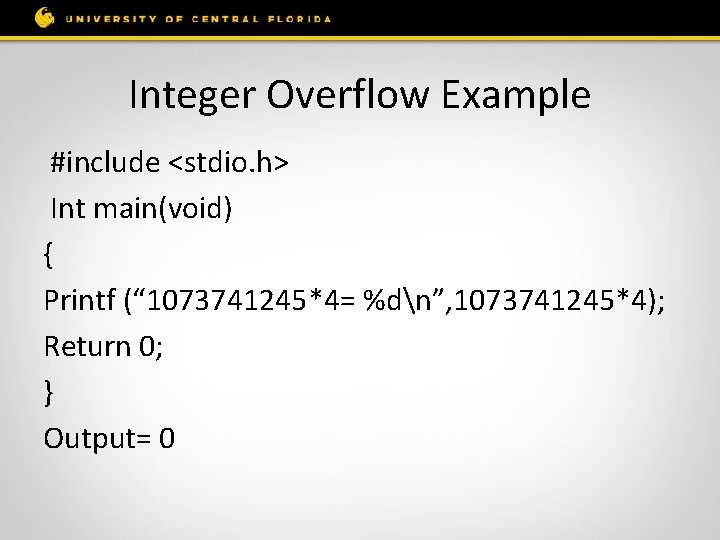
Integer Overflow Example #include <stdio. h> Int main(void) { Printf (“ 1073741245*4= %dn”, 1073741245*4); Return 0; } Output= 0
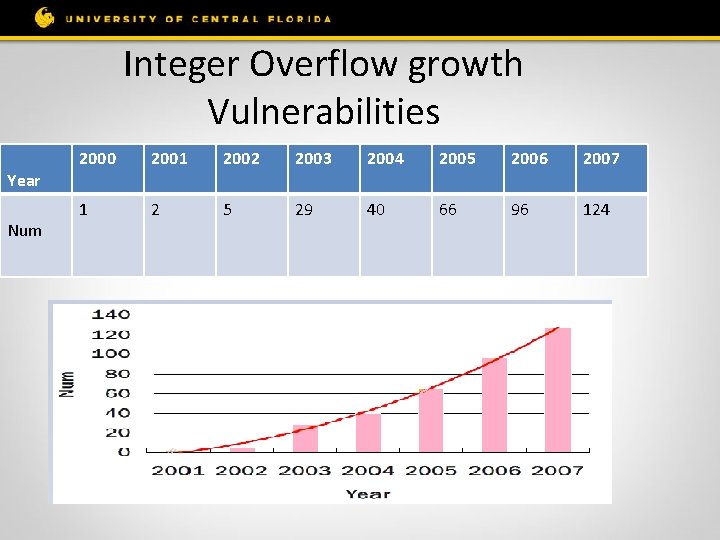
Integer Overflow growth Vulnerabilities Year Num 2000 2001 2002 2003 2004 2005 2006 2007 1 2 5 29 40 66 96 124

Features of Integer Overflow. • Untrusted Source • Various types of sinks ØMemory allocation ØMemory access ØBranch statement • Incomplete or improper sanitization checks
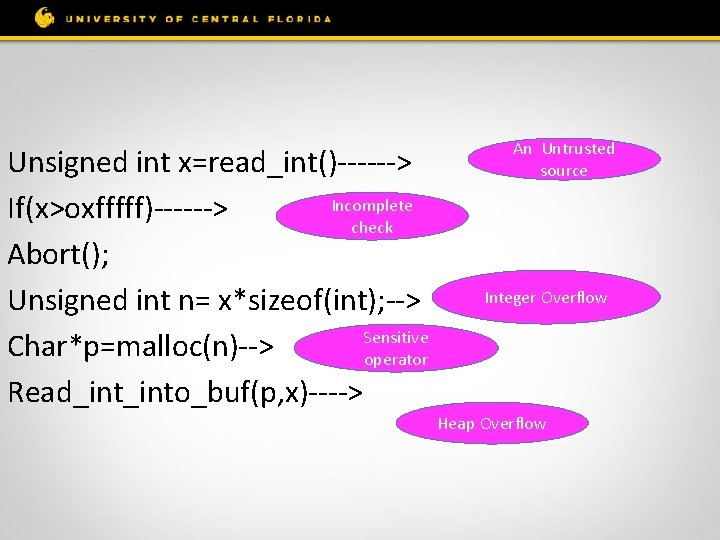
Unsigned int x=read_int()------> Incomplete If(x>oxfffff)------> check Abort(); Unsigned int n= x*sizeof(int); --> Sensitive Char*p=malloc(n)--> operator Read_into_buf(p, x)----> An Untrusted source Integer Overflow Heap Overflow
Idea of Int. Scope • Symbolically executing the x 86 Binary on an intermediate representation. • Using Taint analysis • Using Lazy Checking
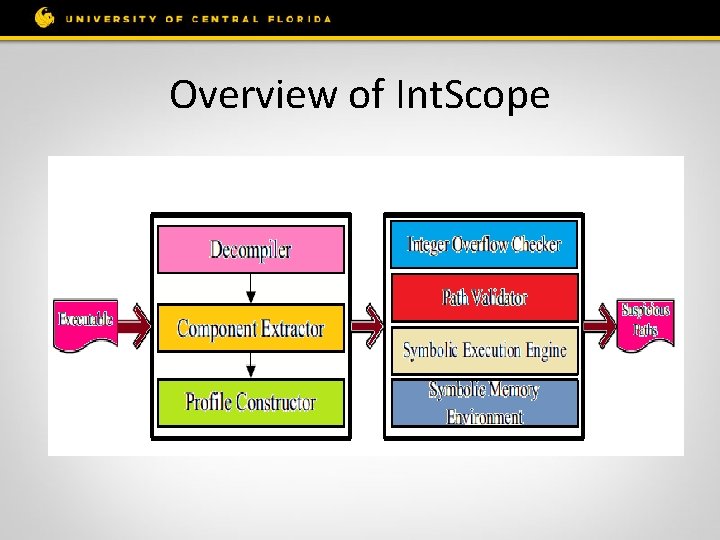
Overview of Int. Scope
Pre-Process procedure • De compiler Translate it into Intermediate Representation (PANDA) Constructs the control flow graph (G) and call graph (C) • Component Extractor Extract from C the candidate functions that are common ancestors connecting source to a sink • Profile Constructor Computes a chop flow graph G’ based on G, that includes only source-sink paths in candidate sub-graphs.
Detection Procedure • Symbolically execute each path in the components Collect path constraints, and check the feasibility of the path (constraint solver) Track the propagation of untrusted (tainted) data Only check whether untrusted data causes integer overflows at sink points
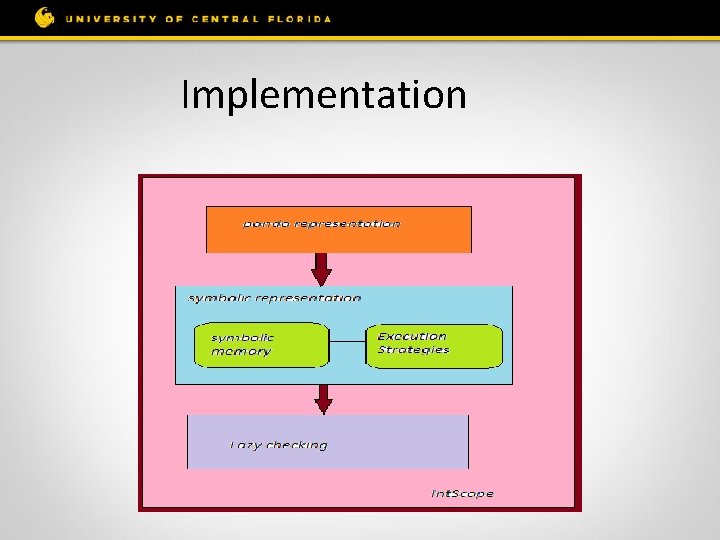
Implementation
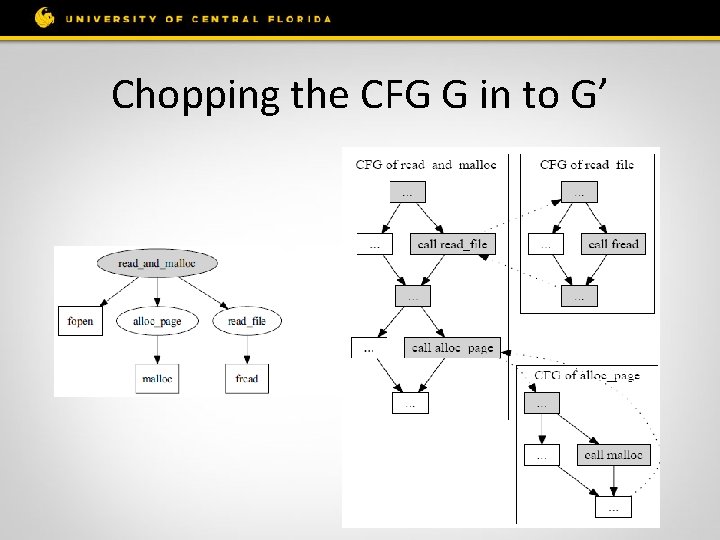
Chopping the CFG G in to G’
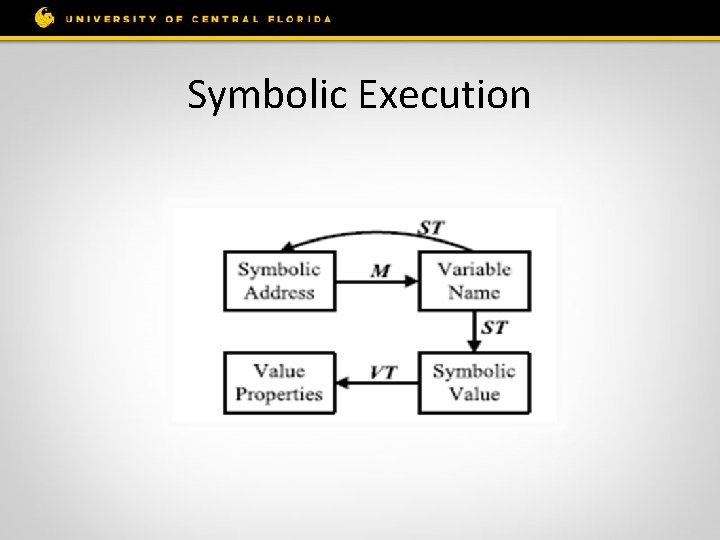
Symbolic Execution

• L 1 x=y=read_from_net() • L 2 if(x==c) • L 3 p=malloc(y);

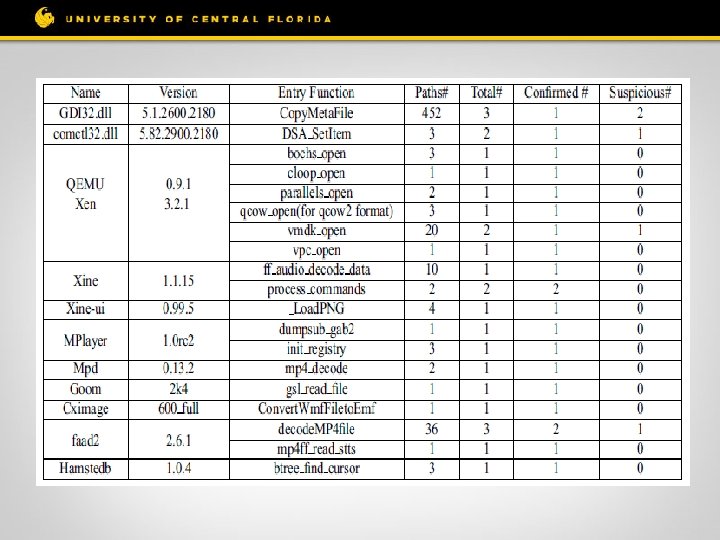
Evaluation and Results • Detected integer overflow bugs in Windows DLLs • Detected bugs in several widely used applications Media player VLC

Strengths • A systematic method of combining taint analysis and path-sensitive symbolic execution to detect integer overflow vulnerabilities in executable. • A prototype called Int. Scope to analyze realworld binaries, which shows the approach is highly effective

Weakness • Lack of information on global variables may lead to false positives • Lack of information on intrinsic constraints between inputs leads to false positives. • No accurately simulation of block memory functions
Thank you…!!
- Slides: 20