Instruction Set Architecture References Logic and Computer Design






- Slides: 28

Instruction Set Architecture References: Logic and Computer Design Fundamental By Mano and Kime Principles of Computer Architecture By Murdocca and Heuring • In general a machine Instruction has the following fields (parts): -An opcode field, which specifies the operation to be performed. -One or more of address fields, each one is either a memory address or a register address (register's number). -A mode field, which specifies the way the address field is to be interpreted.

Machine instruction fields • Other special fields are sometimes employed under certain circumstances. For example, a field that specifies the number of positions to shift in a shift-type instruction or an operand field in an immediate operand instruction.

Instruction execution cycle 1. Fetch the instruction from memory into the IR (instruction register or control register) and increment the register PC (program counter) by the length of instruction(# of bytes). Note that PC is a register that keeps track of the instruction in the program stored in memory. It holds the address of the instruction to be executed next and is incremented each time an instruction is fetched; 2. Decode the instruction, i. e. determine the operation to be performed and the addressing mode or modes; 3. Locate the operands used by instruction, which are specified by memory addresses or register addresses;

Instruction execution cycle (cont. ) 4. Fetch the operands from memory (if necessary). If the operands are in registers, no memory access is needed, however, the register content might be transferred to another register in the CPU. 5. Execute the operation by ALU. Note that CPU( or microprocessor processing unit MPU) is composed of ALU and the control unit. Some authors assume the memory unit is also part of CPU.

Instruction execution cycle (cont. ) 6. Store the results in the proper place( memory location or register); 7. Go back to Step#1 to fetch the next instruction.

Assembler and compiler • The Instruction Set Architecture (ISA) view of a machine corresponds to the machine and assembly language levels. • A compiler translates a high level language, which is architecture independent, into assembly language, which is architecture dependent. • An assembler translates assembly language programs into executable binary codes. • For fully compiled languages like C and Fortran, the binary codes are executed directly by the target machine. Java stops the translation at the byte code level. The Java virtual machine, which is at the assembly language level, interprets the byte codes (hardware implementations of the JVM also exist, in which Java byte codes are executed directly. )

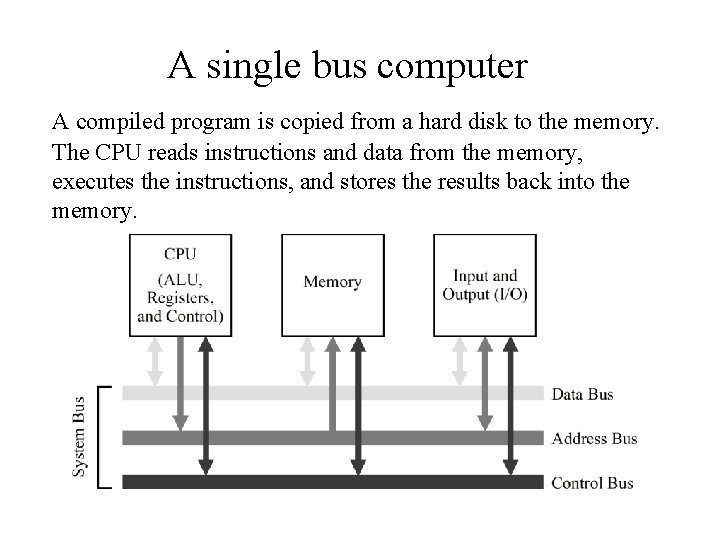
A single bus computer A compiled program is copied from a hard disk to the memory. The CPU reads instructions and data from the memory, executes the instructions, and stores the results back into the memory.

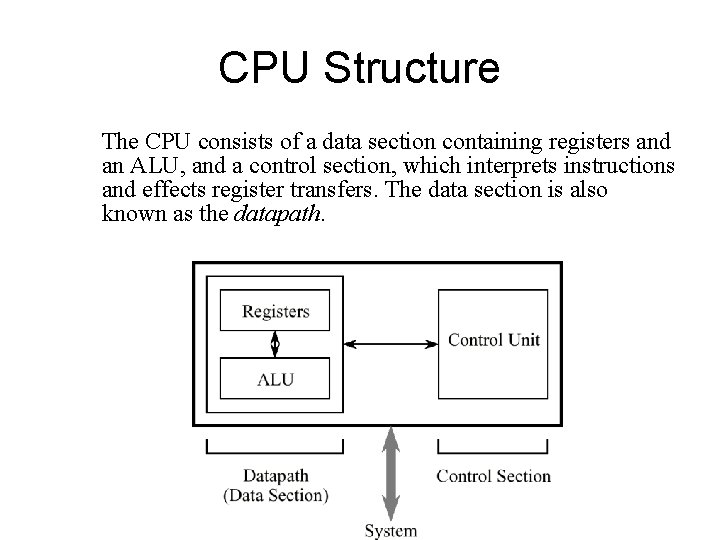
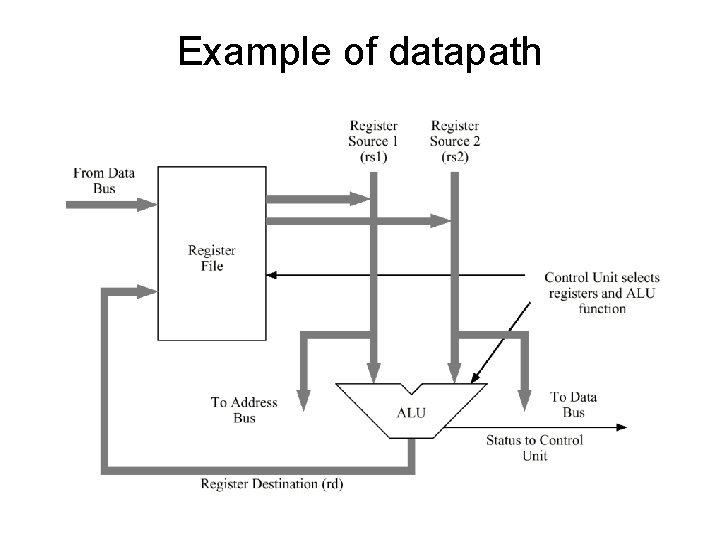
CPU Structure The CPU consists of a data section containing registers and an ALU, and a control section, which interprets instructions and effects register transfers. The data section is also known as the datapath.

Example of datapath

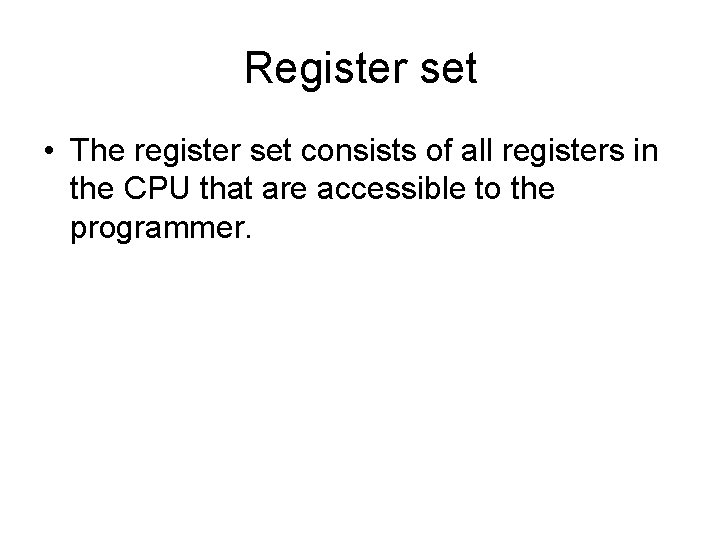
Register set • The register set consists of all registers in the CPU that are accessible to the programmer.

One, Two, Three-Address Machines • The address fields of an instruction may consist one or two or three memory or register addresses. • If all address fields of an instruction are register addresses, we call the machine 1 -, 2 -, or 3 -register address machine. • If all address fields of an instruction are memory addresses, we call the machine 1 -, 2 -, or 3 -memory address machine. • For two and three-address machine, the address fields may include both register and memory addresses. We call the machine 2 -(or 3 -)register-memory address machine.

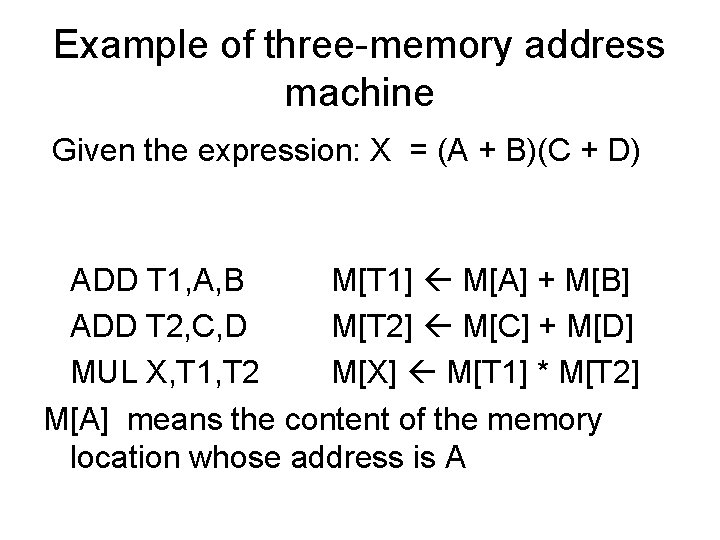
Example of three-memory address machine Given the expression: X = (A + B)(C + D) ADD T 1, A, B M[T 1] M[A] + M[B] ADD T 2, C, D M[T 2] M[C] + M[D] MUL X, T 1, T 2 M[X] M[T 1] * M[T 2] M[A] means the content of the memory location whose address is A

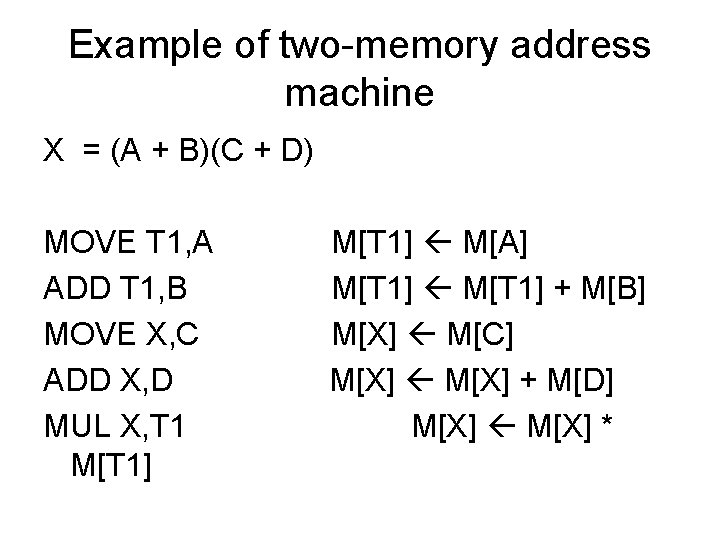
Example of two-memory address machine X = (A + B)(C + D) MOVE T 1, A ADD T 1, B MOVE X, C ADD X, D MUL X, T 1 M[T 1] M[A] M[T 1] + M[B] M[X] M[C] M[X] + M[D] M[X] *

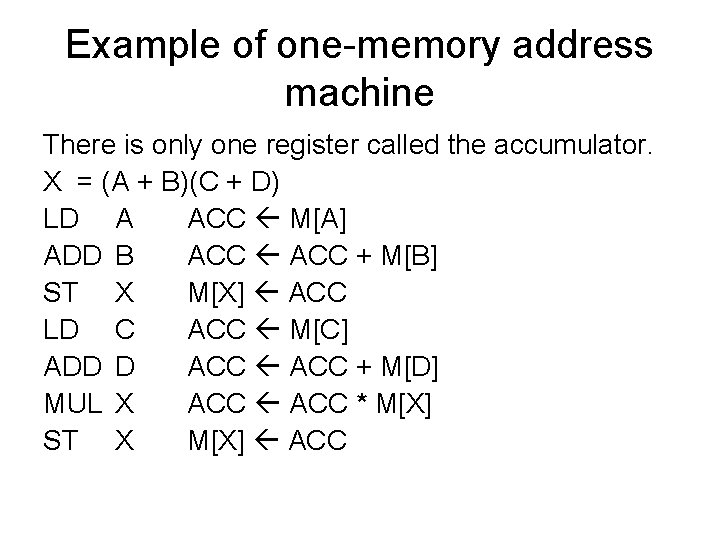
Example of one-memory address machine There is only one register called the accumulator. X = (A + B)(C + D) LD A ACC M[A] ADD B ACC + M[B] ST X M[X] ACC LD C ACC M[C] ADD D ACC + M[D] MUL X ACC * M[X] ST X M[X] ACC

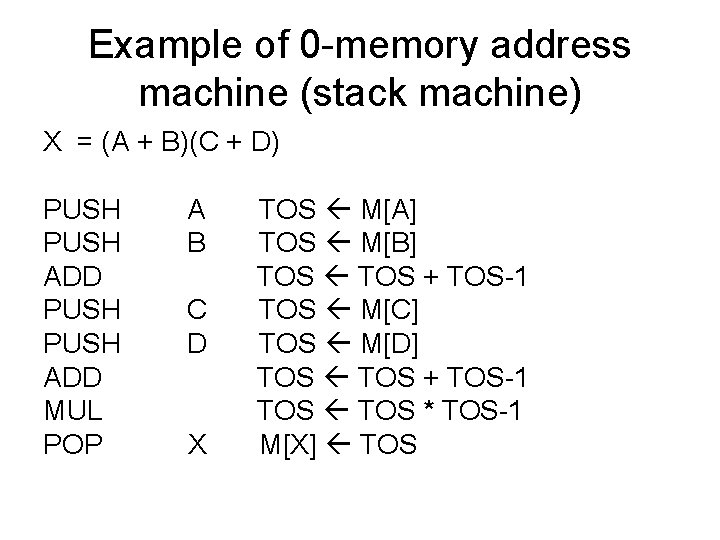
Example of 0 -memory address machine (stack machine) X = (A + B)(C + D) PUSH ADD MUL POP A B C D X TOS M[A] TOS M[B] TOS + TOS-1 TOS M[C] TOS M[D] TOS + TOS-1 TOS * TOS-1 M[X] TOS

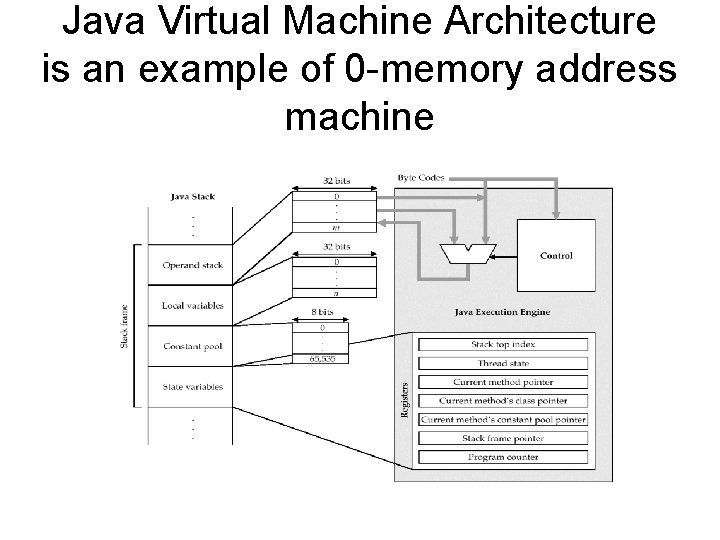
Java Virtual Machine Architecture is an example of 0 -memory address machine

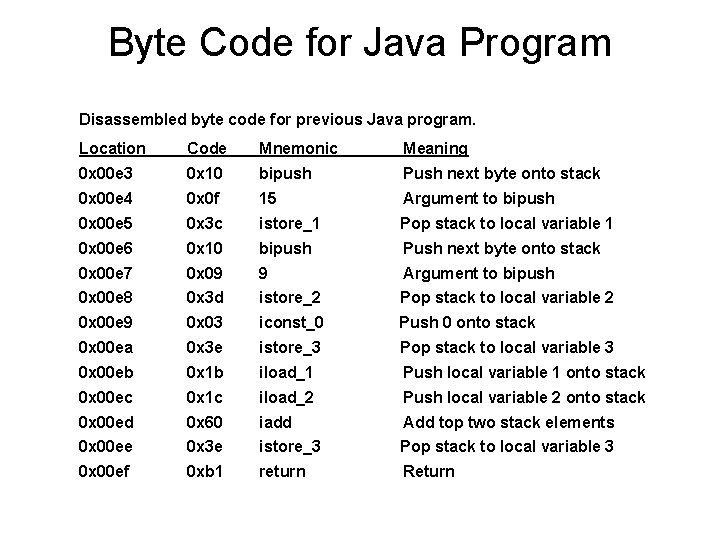
Byte Code for Java Program Disassembled byte code for previous Java program. Location Code Mnemonic Meaning 0 x 00 e 3 0 x 10 bipush Push next byte onto stack 0 x 00 e 4 0 x 0 f 15 Argument to bipush 0 x 00 e 5 0 x 3 c istore_1 Pop stack to local variable 1 0 x 00 e 6 0 x 10 bipush Push next byte onto stack 0 x 00 e 7 0 x 09 9 Argument to bipush 0 x 00 e 8 0 x 3 d istore_2 Pop stack to local variable 2 0 x 00 e 9 0 x 03 iconst_0 Push 0 onto stack 0 x 00 ea 0 x 3 e istore_3 Pop stack to local variable 3 0 x 00 eb 0 x 1 b iload_1 Push local variable 1 onto stack 0 x 00 ec 0 x 1 c iload_2 Push local variable 2 onto stack 0 x 00 ed 0 x 60 iadd Add top two stack elements 0 x 00 ee 0 x 3 e istore_3 Pop stack to local variable 3 0 x 00 ef 0 xb 1 return Return

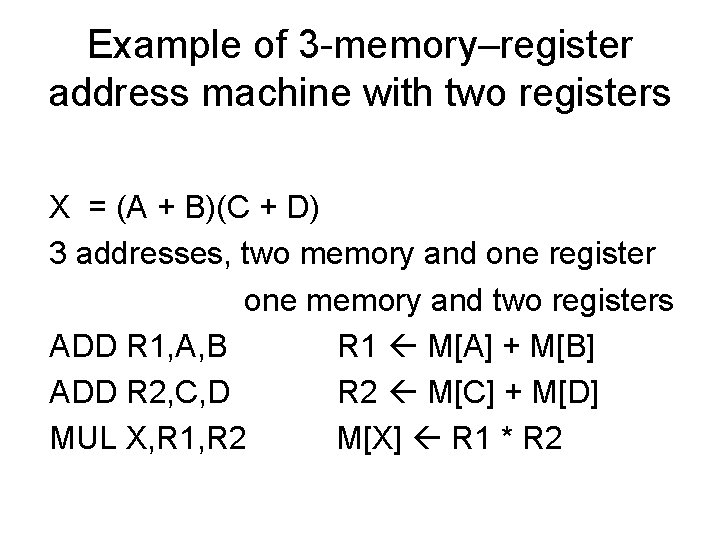
Example of 3 -memory–register address machine with two registers X = (A + B)(C + D) 3 addresses, two memory and one register one memory and two registers ADD R 1, A, B R 1 M[A] + M[B] ADD R 2, C, D R 2 M[C] + M[D] MUL X, R 1, R 2 M[X] R 1 * R 2

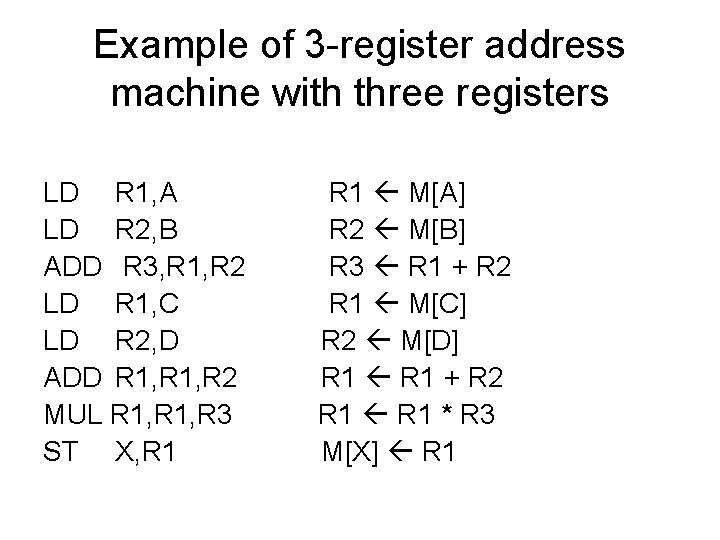
Example of 3 -register address machine with three registers LD R 1, A LD R 2, B ADD R 3, R 1, R 2 LD R 1, C LD R 2, D ADD R 1, R 2 MUL R 1, R 3 ST X, R 1 M[A] R 2 M[B] R 3 R 1 + R 2 R 1 M[C] R 2 M[D] R 1 + R 2 R 1 * R 3 M[X] R 1

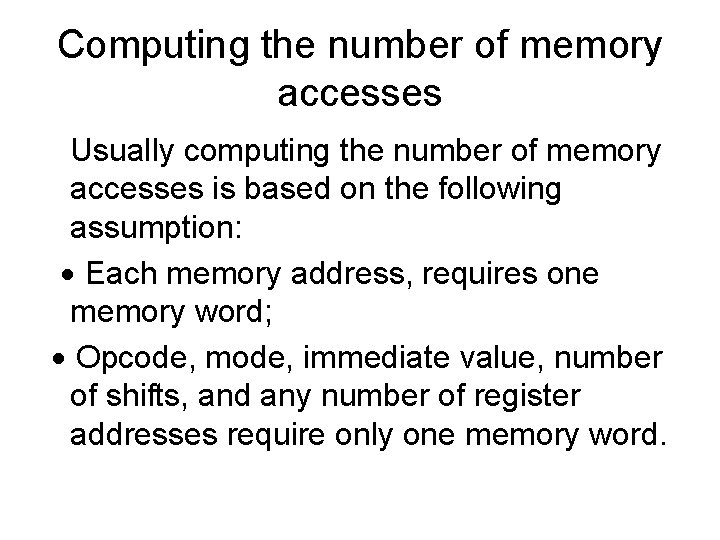
Computing the number of memory accesses Usually computing the number of memory accesses is based on the following assumption: Each memory address, requires one memory word; Opcode, mode, immediate value, number of shifts, and any number of register addresses require only one memory word.

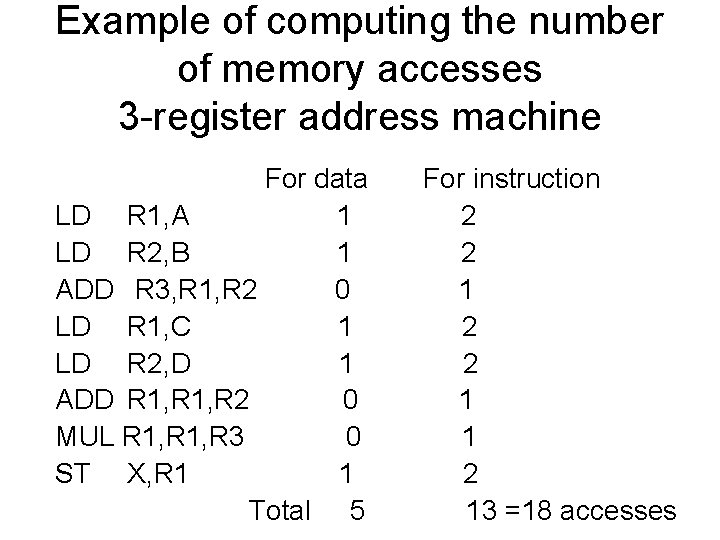
Example of computing the number of memory accesses 3 -register address machine For data LD R 1, A 1 LD R 2, B 1 ADD R 3, R 1, R 2 0 LD R 1, C 1 LD R 2, D 1 ADD R 1, R 2 0 MUL R 1, R 3 0 ST X, R 1 1 Total 5 For instruction 2 2 1 1 2 13 =18 accesses

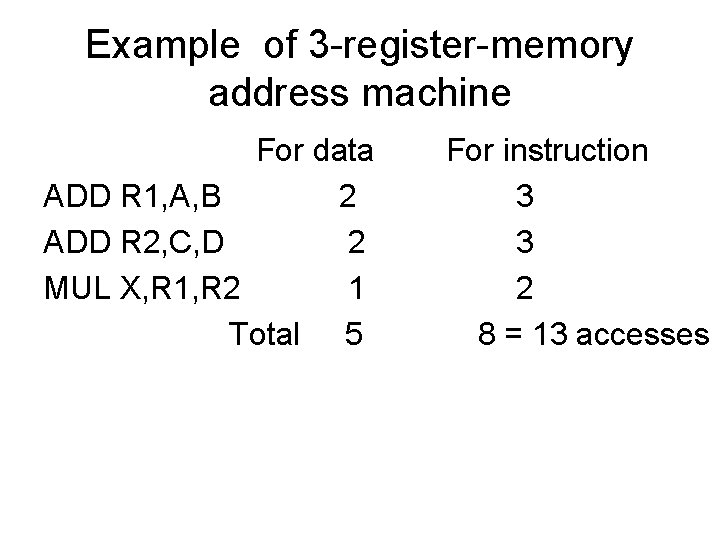
Example of 3 -register-memory address machine For data ADD R 1, A, B 2 ADD R 2, C, D 2 MUL X, R 1, R 2 1 Total 5 For instruction 3 3 2 8 = 13 accesses

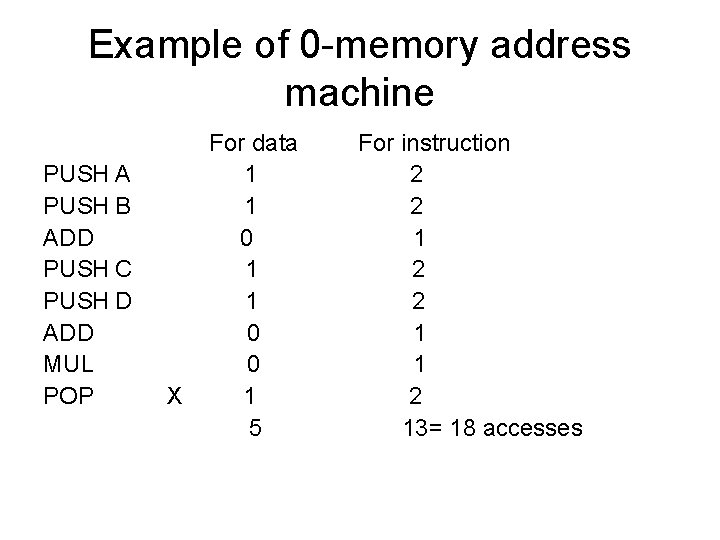
Example of 0 -memory address machine PUSH A PUSH B ADD PUSH C PUSH D ADD MUL POP X For data 1 1 0 0 1 5 For instruction 2 2 1 1 2 13= 18 accesses

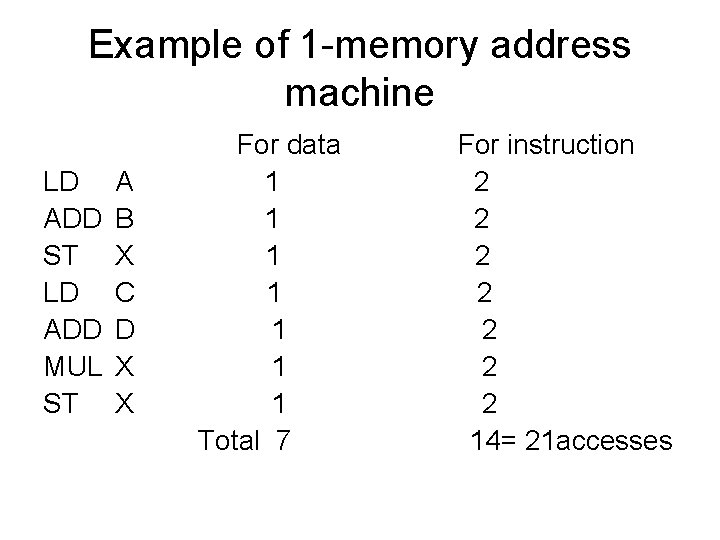
Example of 1 -memory address machine LD ADD ST LD ADD MUL ST A B X C D X X For data 1 1 1 1 Total 7 For instruction 2 2 2 2 14= 21 accesses

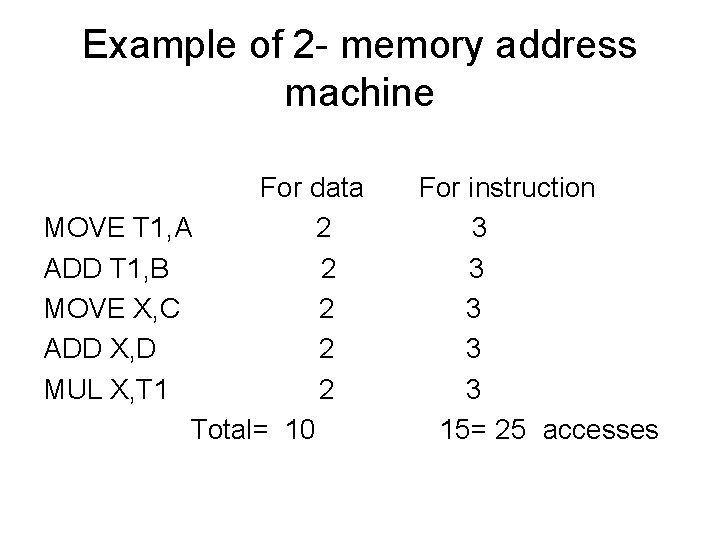
Example of 2 - memory address machine For data MOVE T 1, A 2 ADD T 1, B 2 MOVE X, C 2 ADD X, D 2 MUL X, T 1 2 Total= 10 For instruction 3 3 3 15= 25 accesses

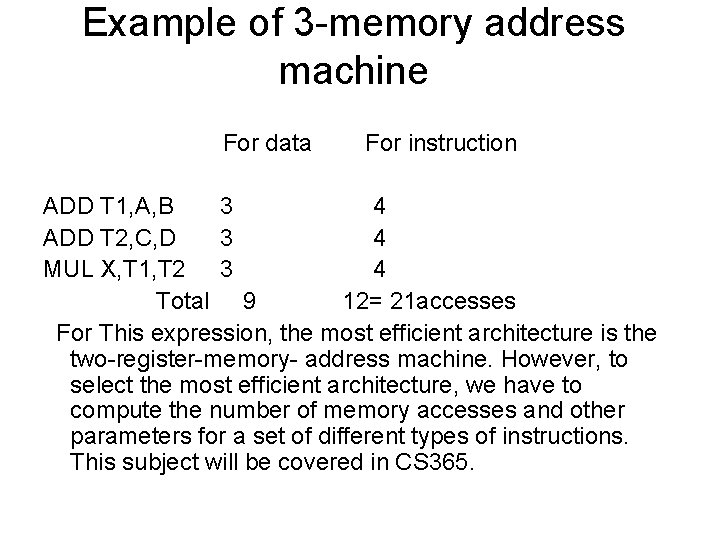
Example of 3 -memory address machine For data For instruction ADD T 1, A, B 3 4 ADD T 2, C, D 3 4 MUL X, T 1, T 2 3 4 Total 9 12= 21 accesses For This expression, the most efficient architecture is the two-register-memory- address machine. However, to select the most efficient architecture, we have to compute the number of memory accesses and other parameters for a set of different types of instructions. This subject will be covered in CS 365.

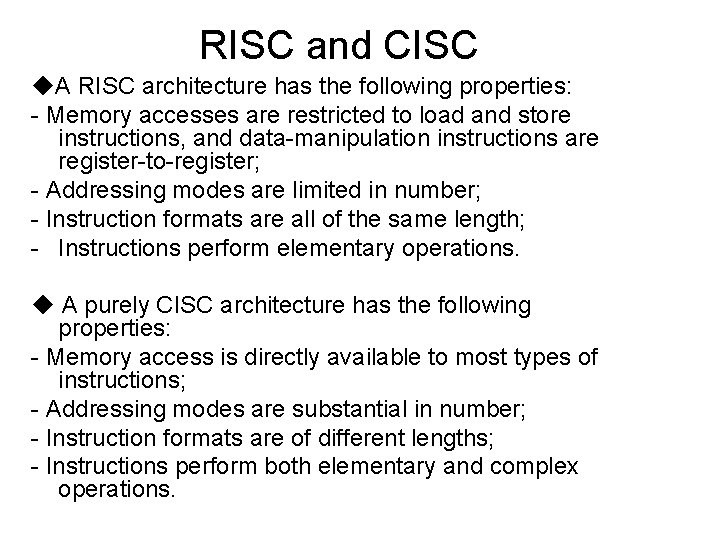
RISC and CISC ◆A RISC architecture has the following properties: - Memory accesses are restricted to load and store instructions, and data-manipulation instructions are register-to-register; - Addressing modes are limited in number; - Instruction formats are all of the same length; - Instructions perform elementary operations. ◆ A purely CISC architecture has the following properties: - Memory access is directly available to most types of instructions; - Addressing modes are substantial in number; - Instruction formats are of different lengths; - Instructions perform both elementary and complex operations.
